Abstract
In the case of virtual wireless sensor networks, a link-failure-oriented survivable virtual sensor network mapping algorithm (F-SVNE) is proposed to address the issue of link failure in the underlying wireless sensor network. First, the algorithm utilizes the fast routing strategy and creates a backup route set based on a multi-path selection algorithm to reduce the delay in fault recovery caused by path selection. Second, the survivable virtual sensor network mapping algorithm is adopted based on the routing set. Finally, in the mapping stage, the efficiency and reliability of the algorithm are comprehensively considered, and the path with the largest survival probability is selected from the backup route set of the faulty link to remap the virtual link affected by the link failure. Empirical results demonstrate that the F-SVNE algorithm can efficaciously lessen the failure recovery delay, and improve the long-term average revenue–cost ratio and average failure recovery rate.
1. Introduction
With the desires of users of Internet of Things (IoT) applications continuing to grow, different application scenarios and business requirements have shown disparate performance indicators for IoT. The Wireless Sensor Network (WSN), which serves as the underlying sensing device of IoT, is typically deployed randomly in unattended areas and harsh environments to perform various complex tasks. Moreover, WSN plays an important role in smart cities, medical monitoring, intrusion detection, and emergency response fields [1]. However, the deployment of WSN is oriented around a specific domain and single user, resulting in the flexibility and scalability of task execution being greatly limited, which leads to the resource utilization of sensor nodes being less than 20%; they are therefore unable to meet the different Quality of Service (QoS) requirements of diverse applications. Traditional software embedding schemes that add new application components to the existing network architecture can cause the existing network architecture to become cumbersome and rigid. However, network virtualization technology [2,3,4] can effectively solve the above problem, and has the significant economic benefits (such as reduced investment and operating costs) of leasing resources (sensing services) to interested third parties. Network virtualization technology also provides the ability to rapidly configure and recover physical network resources from failure, as well as scale on demand. To enhance the potential of IoT, Virtual Sensor Network (VSN) technology for multi-task resource sharing was conceived of, in order to improve the effective use of sensing resources through the multi-user sharing of large heterogeneous sensing infrastructure resources.
Currently, virtualized WSN can be decoupled into two parts: the Wireless Sensor Network Infrastructure Provider (WSNInP) and the Virtual Sensor Network Service Provider (VSNSP) by means of the mode of node-level and network-level virtualization. WSNInP takes charge of the deployment and maintenance of WSN, while VSNSP needs to lease sensors from WSNInP to perform sensing tasks to acquire sensing data and create a Virtual Sensor Network Request (VSNR) to provide corresponding services to users [5]. The VSNR coordinates and collaborates with multiple VSNs through the mode of resource reuse, and each VSN has a certain application and performance level, which can relieve the issues of the low resource utilization and poor scalability of sensing nodes in the current WSN.
Each VSNR constitutes virtual sensor nodes that need to be mapped to the physical sensor nodes of the underlying WSN in order to provide services to users, and the same is true for links. However, current IoT mapping algorithms mostly assume the absence of physical failures [6], and they optimize the network model to improve resource utilization and increase revenue, but ignore the issue of link failures caused by the wireless communication characteristics of WSNs. Network virtualization enables the reuse and sharing of physical resources;however, it also introduces the problem of many virtual links failing due to the failure of a physical link, leading to the failure of multiple VSNs. When VSN requests arrive, the WSNInP needs to undertake the offset in the Service Level Agreement (SLA), which may cause significant economic and reputational losses to the WSNInP that leases the affected physical link. Therefore, while efficiently and reasonably mapping VSN, it is necessary to provide fault tolerance mechanisms for the tasks carried by VSNs, to ensure quick recovery to normal operation in case of network failures, maintain continuity of network services, and ensure the survivability of the VSN.
Currently, research on survivability mapping for virtualized WSNs is scarce and primarily focuses on scenarios involving physical node or single link failures. Given these limitations, this study specifically addresses the issue of link failures, particularly in scenarios involving multi-link failures. To tackle this challenge, an algorithm called the Survivable Virtual Network Embedding Algorithm for Link Failures (F-SVNE) is proposed in this paper. The contributions and innovations of this paper are as follows:
- A fast routing policy is established and a multi-path selection algorithm is used for physical link faults to establish a backup routing set for each physical link to reduce the fault recovery delay.
- A failure probability model is established to calculate the survival probability of the underlying links. Taking into account virtual network mapping cost and survival probability, the path with the maximum survival probability is selected from the backup routing set of faulty links to remap the virtual links affected by link failures.
The main body of this paper is divided into seven sections. The first section is the introduction, which describes the research background and contributions of virtualized WSN. The second section is the related work, which describes the current research status and existing problems of WSN. The third section deals with problem modeling for virtualized WSNs. The fourth section is the virtual network multi-link fault recovery strategy, including the construction of backup routes, the link survivability probability model and link remapping. The fifth section provides the simulation analysis, firstly by describing the parameter settings, and then showing the simulation results and result analysis. The sixth and seventh sections are the discussion and conclusion sections, respectively, summarizing the contributions and future developments of this research.
2. Related Work
With the rapid adoption of IoT applications, there is an increasing desire for the valid utilization of underlying physical network resources. Virtualization technology enables resource sharing among different users in the underlying physical network. The existing literature mainly focuses on Virtual Network Embedding (VNE) for fault-free virtual networks, with the goal of increasing the acceptance rate of virtual network requests [7] or minimizing embedding costs [3], and designing heuristic algorithms to approximate optimal solutions to enhance virtual network revenue. Table 1 lists the advantages and disadvantages of existing survivable virtual network mapping methods and the research method applied in this paper. Most of the current research on survivability focuses on mechanisms that ensure Survivable Virtual Network Embedding (SVNE) by reserving physical links for virtual links, and triggering datum repair when failures occur in the underlying physical network due to node or link failures. The multi-path selection link resource method in this paper not only reduces the possibility of the fragmentation of physical resources, but also improves the utilization of physical resources.
Rahman et al. [8] formulated a mixed integer linear programming method for survivable virtual network mapping in situations where a single link fails. In the following research work, different survivable virtual network mapping methods are derived from two aspects of physical node and link failure. Survivable virtual network mapping methods for the failures of physical nodes can be broadly categorized into two types, among them, the references [9,10] offer dedicated or shared underlying physical network backup resources under the circumstance of a single physical node or multiple physical node failures to improve the survivability of the virtual network; however, although this method improves the fault response rates, the excessive redundant backup wastes a lot of physical resources. In references [11,12], the passive restoration method is put forward to improve the survivability of the mapping algorithm, i.e., node backup resources are not reserved in advance to manage underlying physical networks experiencing one or more physical node failures after using the rest of the physical resources affected by virtual node mapping. Although this method avoids redundancy backup resource waste, it increases the recovery time delay and does not guarantee a good failure recovery rate.


Table 1.
Comparison of existing research methods of survivable virtual network mapping.
Table 1.
Comparison of existing research methods of survivable virtual network mapping.
| Methods | Advantage | Disadvantage |
|---|---|---|
| References [9,10] | Proactively provide dedicated or shared backup resources | Too many redundant backups cause a lot of waste of physical resources |
| References [11,12] | Remap affected virtual nodes with remaining physical resources | Prolonged failure recovery time, low failure recovery rate, high mapping cost |
| Reference [13] | Redundancy protection mechanism guarantees the survivability of multi-link virtual network | High resource overhead and low utilization of underlying resources |
| Reference [14] | Multipath restoration ensures the survivability of single-link virtual networks | Does not take into account the complexity of multi-link failures |
| Ours | Fast routing path selection, short fault recovery delay, high utilization of physical resources | Only involves single-domain virtual network mapping, and does not consider the problem of intra-domain and inter-domain link failures caused by multi-domain virtual network mapping |
Another direction of research in survivable virtual network embedding is to ensure the survivability of virtual networks during the occurrence of one or multiple physical link failures. A study in the literature [13] proposed using a heuristic algorithm that jointly optimizes the allocation of backup data provided by physical network and virtual network embedding, allowing for valid link repair during the occurrence of multiple physical link failures. Reference [10] considers the reliability of mapping theorized as a constraint and guarantees the survivability of theoretical networks through dedicated datum backup. To confirm the degree of importance of protection when multiple theoretical networks fail simultaneously, Ref. [12] proposed a fair recovery model and priority-based recovery model to address failures in the underlying reliability. However, these survivable theoretical network embedding algorithms often adopt redundant protection mechanisms that require additional resource overhead, resulting in a significant amount of resources being occupied and reducing the utilization rate of underlying resources. In [14], the use of multi-path repair and link remapping methods for link failure recovery is studied in the case of a single physical link failure to ensure the survivability of theoretical networks; however, this method is proposed for single link failures and does not consider the complexity of multiple link failures.
At present, in the WSN environment, the redundancy protection mechanism is usually adopted to improve the viability of virtual network mapping and provide backup mapping resources for virtual networks. However, this requires extra resource overhead and causes a large number of resources to be occupied. Furthermore, survivable virtual network mapping studies mainly focus on node failure and single link failure. For the above problems, a link-failure-oriented survivable virtual sensor network mapping algorithm is proposed in order to ensure the viability of virtual sensor network mapping for multi-link faults in virtual WSN scenarios. The algorithm adopts the expressway strategy, establishes physical link backup routing sets which reduces the fault recovery time delay caused by the path selection, and routes sets according to the virtual sensor network survivability mapping algorithm. The fault link backup routing option for the survival probability of the largest path is affected by the link failures and heavy mapping of virtual links is conducted one by one. Thus, the virtual network survivability is guaranteed to be effective, the probability of physical resource fragmentation is decreased, and the utilization rate of physical resources is increased.
3. System Modeling and Problem Modeling
3.1. Network Model
The architecture of virtualized wireless sensor networks is demonstrated in Figure 1: the infrastructure layer, the network services layer, and the application layer are part of the network. The infrastructure layer consists of a dense distribution of various types of sensor nodes that provide perceptual data and forward data services for theoreticality. The network services layer abstracts the physical resources and forms corresponding VSNs based on different user-requested tasks. Finally, each VSN is migrated and isolated to effectively coordinate multiple applications for sensing tasks. The application layer is responsible for receiving user-requested tasks and attaching the necessary QoS requirements. Table 2 lists all key symbols and their meanings for easy understanding.
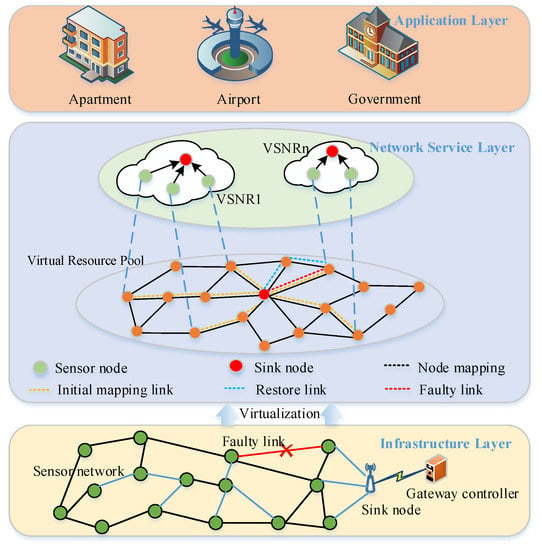
Figure 1.
The architecture of virtualized wireless sensor network.

Table 2.
Key symbol.
The underlying physical network is expressed by an undirected graph , where is the sensor node set, represents the CPU computing capability of the sensor node, denotes the geographical location of the sensor node, and indicates a physical link set, indicates the physical link between the corresponding sensor node pair on the physical network. The transmissibility of the homologous communication link between node pairs is , the path set between the source nodes and the sink node is , in the physical network.
VSN is still expressed using an undirected graph , where and virtual nodes and link sets. Since different VSN requests correspond to different services, the degree of demand for resources is also different. For any virtual node, , indicates the computational capability of the virtual node request of . indicates the sensing position of the virtual node . According to the location requested by each user, physical sensor nodes are selected within the one-hop communication range to perform sensing tasks. For any virtual link , the demanded transmission rate is , and the physical path is a route from the source to the sink node after the link is mapped.
3.2. Objective Function
For VSNR, the computing and storage resources required by virtual sensor nodes are fixed and do not vary with different physical sensing nodes, while the resource consumption of virtual links varies greatly with different physical mapping paths. Therefore, when mapping virtual sensor networks, minimizing link resource consumption should be considered. The objective function is calculated as follows:
The constraint is as follows:
where and are used as decision variables for node and link mapping, respectively, if the virtual space node is successfully mapped to the physical space as , ; otherwise, . Similarly, if the virtual link is mapped to a physical link , ; otherwise, . and indicate the communication resources consumed by the working link and the recovery link, respectively. Equation (2) is a node independence constraint, indicating that the same physical space node cannot be mapped to virtual space nodes from the same VSN. Equation (3) represents the computational capability constraint requested by the virtual space node. When the virtual space node performs node mapping, the residual computational datums of the chosen candidate mapping the reliability of space nodes should exceed the processing power of by the virtual node. Similarly, Equation (4) shows the link communication datum constraint of the virtual network. Equation (5) is the geographical location constraint demanded by the virtual node, that is, the geographical location demanded by the virtual node must be within the one-hop communication range of the mapped physical node.
3.3. Evaluation Index
In this paper, we employ five metrics of the VNE algorithm principally to evaluate the effectiveness of the algorithm, including long-term average revenue, long-term resource consumption cost, revenue cost ratio, virtual network request acceptance rate, and failure recovery success rate [15]. These metrics collectively provide a comprehensive assessment of the algorithm’s performance in terms of revenue generation, resource utilization, cost-effectiveness, and network reliability. The long-term average revenue–cost ratio means that the revenue of a virtual network request at time t is defined as its required resources, and the cost of accepting this virtual network request at time t is defined as its total physical resource consumption. The long-term resource consumption cost, and the revenue of WSNInP depends on the service time t requested by the VSN and the underlying WSN resources required; thus, the long-term revenue–cost ratio of WSNInP is the ratio of its long-term revenue to long-term cost within a given period, t. In order to improve the long-term benefits of WSNInP, it is necessary to consider the trade-off between the benefits of VSNR being successfully mapped and the penalty to be paid due to the failure of VSNR as a result of the failure of the underlying WSN. The virtual network request acceptance rate is an effective performance index that is used to measure the mapping efficiency of the algorithm. The larger the value, the higher the utilization rate of the underlying WSN resources, and the higher the benefits for WSNInP. The failure recovery success rate is the ratio of the number of VSN requests successfully recovered within a period to the total number of VSN requests that fail due to the failure of the underlying WSN. In addition, this paper uses the virtual network request acceptance rate and failure recovery success rate to evaluate the virtual sensor network.
The revenue of WSNInP is measured in terms of CPU resources expended by the virtual sensor network of IoT and communication link transfer rate resources, which are calculated as follows:
The long-term average return of WSNInP can be acquired from Equation (7), which is calculated as follows:
where represents the revenue from successfully mapping VSNR in the period .
The resource consumption cost of WSNInP is the sum of CPU resources and communication link transmission rate resources, which is calculated as:
where indicates the quantity of hops from the physical sensor node to the sink node after a virtual node is mapped to the physical sensor node .
Equations (9) and (10) can calculate the long-term average revenue-cost ratio, which can be calculated as:
During the VNE, if a physical link fails and the link fails to recover, the WSNInP shall bear the penalty specified in the SLA, which is computed as:
where is the penalty factor.
Therefore, the long-term average revenue-cost ratio is newly computed as:
where represents the physical links that fail and are not repaired within the period .
Assume that the quantity of all VSNRS is and the quantity of VSNRS accepted after mapping is . Therefore, the acceptance rate of VSNR is computed as:
The success rate of fault recovery is stipulated as the ratio of the quantity of VSNR requests that are successfully repaired from the initial time to time t to the sum total of VSNR asks that are invalid due to physical network faults. The ratio is calculated as:
4. Recovery Policy for Virtual Network Multi-Link Failures
4.1. Backup Route Collection Build
In the virtual wireless sensor network environment, the virtual to physical mapping issue can be settled by performing node mapping and link mapping. Firstly, in the node mapping phase, the most suitable physical sensor node is selected for the virtual node as the source node for mapping to discover the physical path between the source and the sink node. Node mapping helps to select suitable physical sensor nodes in the WSN perception tasks; thus, it should consider whether the current physical sensor nodes meet the request of virtual node resources while also taking into account the current node mapping after follow-up in terms of the influence of the virtual network, so that every node mapping instance can be used to consider the various aspects of performance, meet the overall delay, reduce resources and adhere to other requirements. To evaluate the suitability of candidate mapping physical sensor nodes, the distance among the mapped physical sensor nodes with the sink nodes should be taken into account.
Resources are limited because the physical sensor nodes in WSNs can undergo physical sensor node death due to rapidly depleted resources when multiple VSNs share the same physical sensor nodes, leading to virtual network service failure and to multiple virtual nodes competing for the same physical link resources, meaning the survivability of virtual networks cannot be guaranteed. Therefore, to prolong the lifetime of WSN and ensure load balance, selecting active nodes with a greater number of remaining resources can help to effectively alleviate this situation. Thus, the activity degree of each physical sensor node is:
where u represent the number of virtual nodes on the physical node, , is the physical node mapped successfully, and denotes the amount of hops among the source nodes with the sink node.
After the virtual node is successfully mapped to the physical node, a physical communication route to the sink node will be found for the physical sensing node. To improve the survivability of the virtual sensor network, the backup strategy of passive recovery is adopted for the underlying physical links. Compared with active mapping, which allocates an end-to-end backup route for every last virtual request link, passive mapping performs link remapping only when a link fails.
Due to the complexity of the path selection algorithm, the remapping of faulty links leads to a considerable delay, generating damage in user data. To enhance the service experience of users, and on the basis of the shortest path algorithm, a multi-path selection algorithm is proposed in this paper. Before the virtual sensor network request arrives, the multi-path selection algorithm is used to calculate the backup paths for every last underlying link, construct a backup routing set and shorten the link remapping delay. The multi-path selection algorithm considers multiple resource constraints in the specified path hops and the link mapping process contrasts the shortest path algorithm. By searching each physical link, it finds multiple paths that meet the constraints and forms a backup route set.
When the underlying physical link fails, a backup path must be provided for the virtual link to ensure service continuity. The backup path has the same source node as the faulty link. Due to the connectivity of the network, a virtual link has multiple backup routes to option from. On the underlying physical network, each additional hop consumes a greater bandwidth and introduces greater delay. Therefore, hop counts are used as an indicator to measure the merits of a backup path, and the paths that meet the hop count standard are included in the backup route set as follows:
We define a function , then, this function represents the path set that has the same source node as a physical link , does not intersect with the link , and hops from the source node to the sink node through .
Therefore, the backup route set meeting the conditions can be defined as . This function represents the set of all paths that have the same source node as a link , are disjointed with the link , and can reach the sink node from the source node within a specified h hop.
4.2. Link Survivability Probability Model
When the underlying physical link fails, whether the virtual link can be successfully remapped depends on the resource status of the backup route set of the underlying physical link. If the paths of the backup route set have enough available resources and are in good working status, the probability of successful remapping is high when a link fails. If the backup route set does not have enough resources to reroute traffic for the underlying link, the probability of successful rerouting of the underlying link is low. Therefore, during link mapping, mapping critical links to the underlying links of the backup routing set with a good resource status will improve the recovery rate of link faults.
Define the probability of survival of a physical link and indicate the probability of recovery by remapping when a link fails. During link mapping, the link survival probability is calculated to select the physical communication path with a higher survival probability and to boost the link survivability of virtual sensor network mapping. The size of depends on the relationship between the remaining communication link resources in the backup route set of a physical link and the used communication link resource . If is much larger than , when the physical link fails, its backup routing set can meet the re-routing requirements of the physical link , that is, the survival probability of the physical link is high. and are calculated as follows:
where represent the virtual link, and is mapped to the physical link . and denote the physical link which carries the active bandwidth required by the virtual link and the standby bandwidth used for link remapping, respectively; is the sum of those. indicates the minimum bottleneck bandwidth of each path in the path set that can be used for link remapping. When the underlying physical link fails and the available communication link resource of a standby path of the physical link is much greater than the used communication link resource of the physical link , the fault recovery rate of the physical link is 1. Otherwise, the fault recovery rate of the physical link is 0. Therefore, the normalized link survival probability is defined as:
According to the backup route set constructed, before virtual sensor network mapping, the backup link set with a hop limit of h hops is calculated for the physical link . Each backup path in x provides the remapping service for physical links. Therefore, the survival probability of the underlying physical link is calculated as follows:
If the backup link set of the physical link is empty, the link survival probability is 0 because no backup link can offer rerouting for the physical link . When the network request for the virtual sensor is achieved, the value of the update will be calculated first to provide a more accurate probability value for the virtual network mapping.
4.3. Link Remapping
The pseudo-code of the link failure-oriented survivable virtual sensor network mapping algorithm is shown in Algorithm 1. When the virtual sensor network reach, select the physical node to be mapped based on node activity , and then map the virtual node to the physical node. Then link mapping is performed and the backup routing set of physical link is calculated based on the multi-path selection algorithm. If the physical link is not faulty, the link with the highest survival probability is selected for mapping based on the link survival probability model. If the physical link fails, the statistics are influenced by the physical link set of virtual links, and the virtual link request link resources in descending order will result in the collection and calculation of the balance link resources, virtual link, in turn, heavy mapping in the link from the collective resources to balance the route of the largest.
When the underlying link fails, the link remapping algorithm is used to reroute the traffic from the faulty to the backup link set. Because one underlying link may carry multiple virtual requests, the failure of one underlying link will cause multiple virtual requests to be unavailable. The remapping algorithm is used to migrate the traffic of the virtual requests affected by the fault. However, if the backup route of the physical link cannot restore all the virtual links, some virtual requests still cannot run normally, which will result in a penalty. To minimize the loss of the underlying facility provider, the virtual links that generate more penalties should be remapped preferentially during link remapping. Based on this, the link resource balance degree is defined as:
where and indicate the minimum and maximum of the remaining real-time backup communication link resource links of physical path , is any path in the backup routing set of faulty link . The link resource degree of equilibrium is applied to equilibrium for the link resource consumption of physical links and lessens the feasibility of resource debris. The larger the link resource balance is, the less likely the resource fragmentation is to occur, thus improving the utilization of physical resources.
| Algorithm 1 Survivable virtual sensor network mapping algorithm for link failure |
| Input: , ; |
| Output: Mapping results |
| 1: for each virtual network request do |
| 2: for virtual network requests virtual nodes do |
| 3: Select a mapping node based on node activity |
| 4: end for |
| 5: Calculate a backup routing set of physical link based on the multipathing selection algorithm |
| 6: if the physical link is not faulty during virtual link mapping then |
| 7: According to the link survival probability model, the link with the highest survival probability is selected for mapping |
| 8: end if |
| 9: if the physical link is faulty then |
| 10: The system collects statistics on the set of virtual links impacted by physical link and sorts the link resources requested by the virtual links in descending order. The result is saved to set |
| 11: for the physical link is faulty do |
| 12: Backup routing set based on the physical link |
| 13: for set of all paths do |
| 14: The link resource balance degree is calculated, and the virtual links in set are successively remapped to the path with the largest link resource balance degree |
| 15: end for |
| 16: end for |
| 17: end if |
| 18: end for |
| 19: return |
5. Experiments and Analysis
5.1. Setting
In this chapter, Matlab R2018b is applied to verify the performance of the proposed algorithm. In the simulation experiment, VSNR arriving offline is considered in this paper. So as to realistically simulate the physical network, WSN is composed of 50 evenly distributed sensor nodes, the transmission radius of every last sensor node is 30 m, and the CPU resources of every last sensor node are evenly distributed [100, 200]. The link capacity between sensor nodes is evenly distributed [80, 100]. The arrival of link faults obeys the Poisson distribution with a parameter of 0.05 and a candidate set hop count of 4.
VSNR arrives according to Poisson distribution, and its effective reach is 8 arrivals per 100-time units. The service time of each VSNR obeys an exponential distribution, with an expectation of 100-time units. The magnitude of each virtual node is subject to the uniform allocation [3, 5], the CPU resources requested by the virtual node are subject to the uniform allocation [10, 20], and the link resources requested are subject to the uniform allocation [10, 25]. All cost and benefit parameters in VSNR are set to 1. Each simulation lasted 50,000-time units, and the simulation was executed 10 times in total. The average evaluation index was taken as the eventual experimental result to eliminate the influence of random factors. The specific simulation settings are shown in Table 3.

Table 3.
Parameter settings.
This paper extends the classical two-stage mapping algorithm [3] to the C-SVNE algorithm, applied to the link failure environment as the benchmark comparison algorithm, due to the imperfect research on link failure survivability in virtualization WSN. The algorithm experiment settings in [3,16] include four layers, namely the physical layer, access layer, sensor virtualization layer and application layer, but the algorithm in this paper has a three-layer structure, including the infrastructure layer, network service layer and application layer. In addition, based on reference [3], the link failure recovery algorithm N-SVNE in reference [16] is adopted as a further comparison algorithm for F-SVNE. The specific comparison is shown in Table 4.

Table 4.
Simulation algorithm feature comparison.
5.2. Main Results
In Figure 2 and Table 5, the trend of the VSNR acceptance rate over time for three comparison algorithms is shown. It can be seen that the acceptance rate of VSNR in the comparison algorithms begins to drop from 1 over time and eventually tends to become stable in dynamic equilibrium. In the initial stage of virtual network mapping, the nodes and links in the underlying physical WSN have rich resources, so the initial three algorithms have a high acceptance rate. As the underlying physical network resources occupied by previous VSNR requests increase, physical WSN resources are reduced, resulting in some VSNRs being rejected due to insufficient resources. The VSNRF-SVNE algorithm proposed in this paper finally accepts a rate that is steady at around 0.73, which is higher than that of other algorithms. This is because, during the node mapping stage, the F-SVNE algorithm, using the measurement of activity index, leads the task of physical nodes bearing selection to be relatively balanced, and the contrast algorithm is preferred in current physical network resources of nodes and links. As a result, a large number of key nodes and links are rapidly occupied, and subsequent VSN mapping fails.
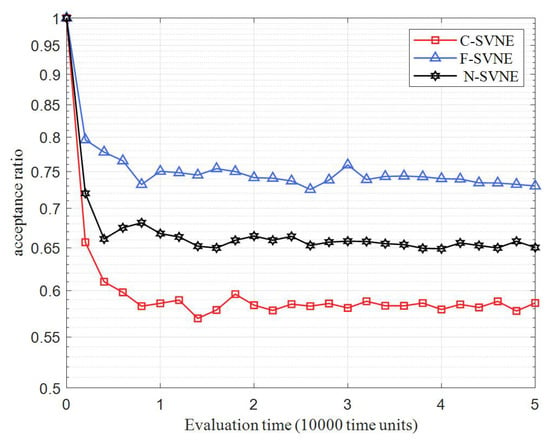
Figure 2.
Acceptance rate of VSNR.

Table 5.
Acceptance rate of VSNR.
In Figure 3 and Table 6, the average failure recovery rate for three comparison algorithms is shown. It can be seen that the average failure recovery rate of the comparison algorithms gradually decreases and tends to become stable with time. In the initial phase of virtual mapping the resources in the physical network are sufficient to recover faulty links. As the number of VSNRs increases, a large amount of underlying physical resources become occupied and the resources used for fault recovery decrease. As a result, the average fault recovery rate decreases. Among them, the F-SVNE average recovery rate is the highest. This is because the algorithm uses multiple path selection algorithms for backup routing collection, a collection of backup paths meets the resource constraints, and the priority use of link resources balances the large backup paths. Fragmentation occurs when reducing resources, the remaining backup resources are optimized at the same time, and the average recovery rate increases. The reason that C-SVNE has the lowest average failure recovery rate is that when a link failure occurs, it adopts the shortest path algorithm to recover the link failure. As the remaining available resources of the underlying physical network gradually decrease, it cannot discover the appropriate communication route for remapping the faulty link.
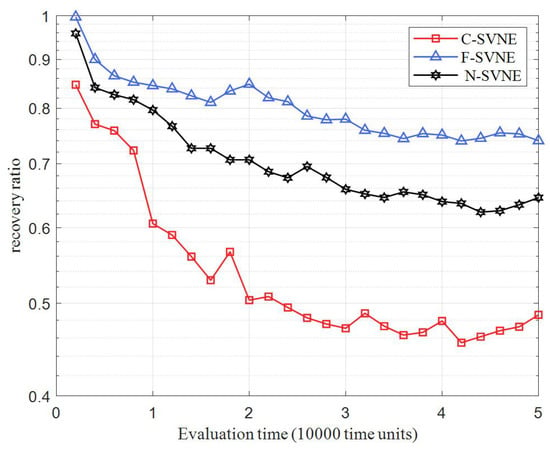
Figure 3.
VSNR failure recovery rate.

Table 6.
VSNR failure recovery rate.
In Figure 4 and Table 7, the average failure recovery delay for three comparison algorithms is shown. It can be seen that the C-SVNE algorithm has the longest average failure recovery delay, while the N-SVNE and F-SVNE algorithms have shorter average failure recovery delays. The longer average failure recovery delay of the C-SVNE algorithm is due to the fact that it does not have any backup link sets. When a physical link fails, the algorithm needs to spend additional time choosing an appropriate link for remapping on account of the remaining physical resources. On the other hand, both the N-SVNE and F-SVNE algorithms create backup link sets for physical links, which saves time for link remapping. Among the two algorithms with backup link sets, the F-SVNE algorithm exhibits the shortest average failure recovery delay. This is because the F-SVNE algorithm selects backup paths with a large link resource balance for virtual link remapping, which further shortens the path selection time and reduces the average failure recovery delay. In summary, the F-SVNE algorithm achieves the shortest average failure recovery delay among the three algorithms, followed by the N-SVNE algorithm, while the C-SVNE algorithm has the longest average failure recovery delay on account of the absence of backup link sets.
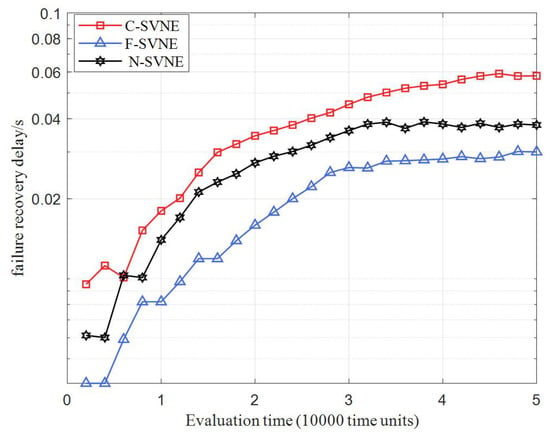
Figure 4.
Fault recovery delay.

Table 7.
Fault recovery delay.
In Figure 5 and Table 8, the long-term average revenue-cost ratio for three comparison algorithms is shown. From the diagram, we can observe that the long-term average cost of the three algorithms gradually decreases over time and reaches a stable state. This is because as a large number of physical network resources are being used, some physical link failures cannot be restored due to insufficient resources, resulting in lower average income than cost for a prolonged period, and a dynamic balance in a steady state is eventually achieved. The long-term average revenue-cost ratio of the F-SVNE algorithm is consistently higher than that of the other two algorithms, and finally stabilizes at around 0.6. This is because, on one hand, the F-SVNE algorithm reduces the fragmentation of physical resources, optimizes the remaining backup resources, and improves the acceptance rate of VSNRs, thereby increasing the revenue. On the other hand, when a physical link fails, the F-SVNE algorithm prioritizes the remapping of virtual links with high penalties based on link resource balance, reducing the penalties caused by failure recovery and improving the long-term average revenue–cost ratio.
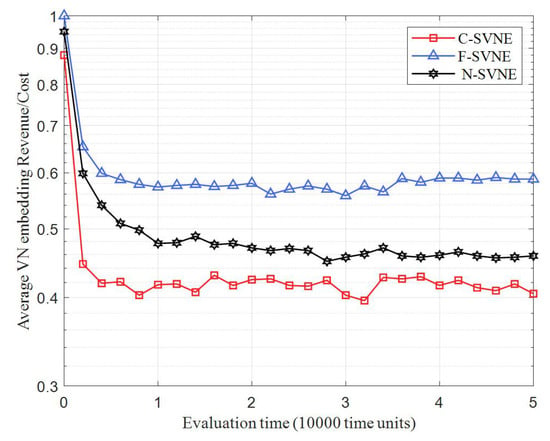
Figure 5.
Long-term average revenue-cost ratio.

Table 8.
Long-term average revenue-cost ratio.
6. Discussion
This paper proposes a new survivability mapping strategy for link faults in virtual wireless sensor networks, which can quickly select routing paths, shorten fault recovery delays, and improve physical resource utilization. However, since the current research only involves single-domain virtual network mapping, when multi-domain virtual network mapping is involved, link failure problems within and between domains will arise. Therefore, exploring the survivability virtual network mapping algorithm for multi-domain link faults will be the next research direction.
7. Conclusions
The paper addresses the issue of survivable virtual network mapping in a multi-link fault scenario and proposes a novel algorithm. The proposed algorithm incorporates a multi-path selection approach to create a backup routing set for physical links, with a preference for selecting paths with a high link resource balance for link remapping. This approach aims to reduce physical resource fragmentation and enhance the utilization of physical resources. The experiments presented in the paper show that the proposed algorithm provides improvements in terms of the long-term average revenue-cost ratio, average failure recovery rate, and failure recovery delay. The results suggest that the F-SVNE algorithm is valid in enhancing the survivability of virtual networks in the presence of multi-link faults. However, the current research is limited to single-domain virtual network mapping, and does not consider link failures in the intra-domain and inter-domain scenarios that may occur in multi-domain virtual network mapping.
Author Contributions
Conceptualization, S.L. and P.Z.; methodology, S.L.; validation, S.L., Y.Y. and L.W.; formal analysis, W.P.; investigation, Y.Y.; resources, Y.J.; data curation, Y.J.; writing—original draft preparation, P.Z.; writing—review and editing, L.W.; visualization, P.Z.; supervision, W.P.; project administration, W.P.; funding acquisition, Y.J. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by Key Research and Development Project of State Grid Chongqing Electric Power Company of funder grant number (2022 Chongqing Electric Science and Technology 2#) and National Natural Science Foundation of China (Grant 61901071).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| IoT | Internet of Things |
| VSN | Virtual Sensor Network |
| VNE | Virtual Network Embedding |
| SLA | Service Level Agreement |
| WSN | Wireless Sensor Network |
| WSNInP | Wireless Sensor Network Infrastructure Provider |
| VSNSP | Virtual Sensor Network Service Provider |
| VSNR | Virtual Sensor Network Request |
| SVNE | Survivable Virtual Network Embedding |
References
- Liang, W.; Ma, C.; Zheng, M.; Luo, L. Relay node placement in wireless sensor networks: From theory to practice. IEEE Trans. Mob. Comput. 2021, 20, 1602–1613. [Google Scholar] [CrossRef]
- Bera, S.; Misra; Vasilakos, A.V. Software-defined networking for internet of things: A survey. IEEE Internet Things J. 2017, 4, 1994–2008. [Google Scholar] [CrossRef]
- Zhang, P.; Yao, H.; Liu, Y. Virtual network embedding based on computing, network, and storage resource constraints. IEEE Internet Things J. 2018, 5, 3298–3304. [Google Scholar] [CrossRef]
- Ezdiani, S.; Acharyya, I.S.; Sivakumar, S.; Al-Anbuky, A. Wireless sensor network softwarization: Towards WSN adaptive QoS. IEEE Internet Things J. 2017, 4, 1517–1527. [Google Scholar] [CrossRef]
- Lu, M.; Gu, Y.; Xie, D. A Dynamic and collaborative multi-layer virtual network embedding algorithm in SDN based on reinforcement learning. IEEE Trans. Netw. Serv. Manag. 2020, 17, 2305–2317. [Google Scholar] [CrossRef]
- Pentelas, A.; Papathanail, G.; Fotoglou, I.; Papadimitriou, P. Network service embedding across multiple resource dimensions. IEEE Trans. Netw. Serv. Manag. 2021, 18, 209–223. [Google Scholar] [CrossRef]
- Chowdhury, M.; Rahman, M.R.; Boutaba, R. ViNEYard: Virtual network embedding algorithms with coordinated node and link mapping. IEEE/ACM Trans. Netw. 2012, 20, 206–219. [Google Scholar] [CrossRef]
- Rahman, M.R.; Boutaba, R. SVNE: Survivable virtual network embedding algorithms for network virtualization. IEEE Trans. Netw. Serv. Manag. 2013, 10, 105–118. [Google Scholar] [CrossRef]
- Yu, H.; Anand, V.; Qiao, C.; Sun, G. Cost efficient design of survivable virtual infrastructure to recover from facility node failures. In Proceedings of the 2011 IEEE International Conference on Communications (ICC), Kyoto, Japan, 5–9 June 2011; pp. 1–6. [Google Scholar]
- Chowdhury, S.R.; Ahmed, R.; Khan, M.M.A.; Shahriar, N.; Boutaba, R.; Mitra, J.; Zeng, F. Dedicated protection for survivable virtual network embedding. IEEE Trans. Netw. Serv. Manag. 2016, 13, 913–926. [Google Scholar] [CrossRef]
- Pourvali, M.; Bai, H.; Crichigno, J.; Ghani, N. Multicast virtual network services embedding for improved disaster recovery support. IEEE Commun. Lett. 2018, 22, 1362–1365. [Google Scholar] [CrossRef]
- Shahriar, N.; Ahmed, R.; Chowdhury, S.R.; Khan, A.; Boutaba, R.; Mitra, M. Generalized recovery from node failure in virtual network embedding. IEEE Trans. Netw. Serv. Manag. 2017, 4, 261–274. [Google Scholar] [CrossRef]
- Shahriar, N.; Chowdhury, S.R.; Ahmed, R.; Khan, A.; Fathi, S.; Boutaba, R.; Mitra, J.; Liu, L. Virtual network survivability through joint spare capacity allocation and embedding. IEEE J. Sel. Areas Commun. 2018, 36, 502–518. [Google Scholar] [CrossRef]
- Yang, Z.; Yeung, K.L. SDN candidate selection in hybrid IP/SDN networks for single link failure protection. IEEE/ACM Trans. Netw. 2020, 28, 312–321. [Google Scholar] [CrossRef]
- Fische, A.; Botero, J.F.; Beck, M.T.; Meer, H.; Hesselbach, X. Virtual network embedding: A survey. IEEE Commun. Surv. Tutor. 2013, 15, 1888–1906. [Google Scholar] [CrossRef]
- Kaiwartya, O.; Bai, H.; Crichigno, J.; Ghani, N. Virtualization in wireless sensor networks: Fault tolerant embedding for Internet of Things. IEEE Internet Things J. 2018, 5, 571–580. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).