Abstract
The paper presents a distributed approach to online cyber risk assessment across the country, taking into account cyber threats and vulnerabilities identified by local services operators. It consists in distributed, asynchronous calculations of possible failure scenarios. They are a solution of a set of nonlinear, nonsmooth equations with locally assessed risk activation functions as inputs. These functions indicate whether a given threat is expected in some future period. The convergence condition of the mentioned algorithm is given in the theorem form. At the end, a case study concerning a system consisting of four entities is presented.
1. Introduction
The COVID-19 pandemic, during which many people started to work, learn, and study from home, has shown how important distributed systems are. It concerns especially clouds, their stability and reliability [1]. Microsoft TEAMS, Google Meet, and Zoom saw a very big increase of new people signing into them [1]. The importance of digital services has increased rapidly. Unfortunately, in this time of crisis, cyber criminals have become hyperactive and have been constantly preying on the sensitive data of both individual users and organizations. Because of that, cyber security needs to be upgraded to protect users against rising cyber crimes [2,3].
The distributed nature of the system implies that the underlying security controls and monitoring facilities should be also distributed, with the ability to apply filtering to minimize the exchange of information concerning security with the central node [4].
An alternative is a hierarchical approach: coordinator–local units, or master–workers, where there exists an entity responsible for national-level risk assessment—the Operations Center (CNT) and local entities (LE)—essential services operators, presented in the previous papers [5,6]. In such a system, local units participating in the calculations do not exchange information related to the risk assessment process for the whole or a part of the system; rather, they send data to the CNT after making their assessments.
A hierarchical approach can be embarrassing when a large amount of information is transferred to the CNT and when there are problems with connectivity to part of the system as a result of an attacker’s success. Moreover, when the CNT serves only to gather the data, calculate some aggregated values, and broadcast the results, the question arises whether the coordination is really necessary.
Therefore, it appears that a peer-to-peer system, closely related to the network topology, where different units perform calculations and exchange information with the direct neighbors [7,8,9], seems to be more appropriate.
The literature on the different approaches to dynamic risk assessment in critical infrastructure, including core IT systems, is very broad [10,11]. However, the models used for online calculations of possible event scenarios, based e.g., on attack graphs [12,13,14,15], system dynamics [16], Bayesian networks [17], and Markov chains [18,19], assume centralized processing. Just recently, an interesting decentralized model based on fuzzy Bayesian Games, looking for a consensus via delegated proof of stake (DPoS) and proof of work (PoW) algorithms was presented [20]. However, it was designed for multimicrogrid systems and uses the adequate low-level information.
The model presented here is the next step to work out a practical mechanism which is [21] “scenario-based, where actors are gathered together to consider scenarios in the round; such scenarios describe risks as a narrative and label them by applying simple categories of likelihood and impact”. However, unlike in references [5,6], likelihood does not have to take values from the interval (in some models it is more convenient to scale it to a different interval, e.g., ) and it is assumed that the influence of the neighbouring nodes is limited. The equations presented here are a little similar to those of studies [22,23,24] but they are nonlinear with saturation functions. In this paper, first such a model is presented in a detailed way, then the theorem concerning the convergence of the proposed iterative algorithm is formulated and proved. Finally, a case study concerning a system built from a power plant, a hospital, a railway operator, and a data center shows a scenario, that is the course of possible events, after an attack on the power plant.
2. Distributed Calculation of Iterated Possible-Failure Scenarios
Let us consider a distributed peer-to-peer system, where the LEs work asynchronously and send information to the CNT when a stable result (convergence) from their calculations is obtained, of course repeating the procedure when the situation changes (Figure 1).
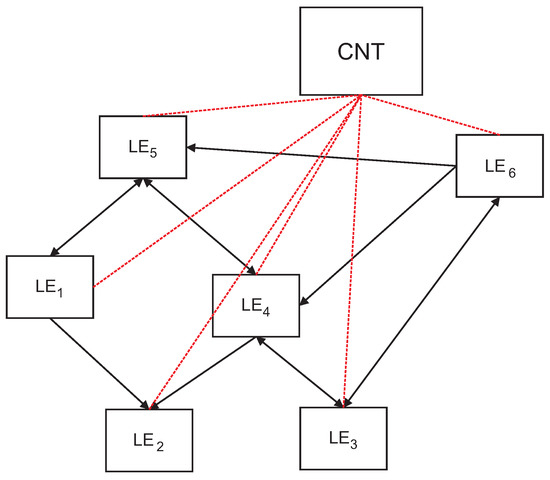
Figure 1.
Distributed system of online risk assessment: —local entities delivering services; CNT—Operations Center. Arrows on links show dependencies between services and the information flow during calculations. The red (dotted) lines represent exchange of information between subsequent computations.
Assume that the scenarios are calculated in a way similar to weather forecasts, that is they may be determined on different horizons and they are updated repetitively at times with a given frequency, e.g., for every 15 min, half an hour, etc. The calculations of these scenarios are performed before every , that is at the end of the interval . Assume also that an LE delivers a service s. The set of all services considered by us will be denoted by S. At a given time , while analyzing the risk of its malfunctioning, the s-th LE considers a future time interval , which is composed of a number of subintervals , , that is:
For each of these intervals, let us denote with the likelihood of a failure of a service s estimated at time . The possible failure scenario (PFS) of the service s estimated at time is defined as . We assume, of course, that every local entity, using its risk assessment method, which takes into account its current cyber-security situation and PFSs of the neighbouring LEs influencing its functioning, is able to determine its own PFS.
Intervals can have different lengths related to the different reaction times of various services. For example, for , may refer to a short nearest-future period in which the service s may be affected by current threats. The next, longer, intervals (mid term) and (long term) (Figure 2) may concern both the threats and reactions on them.
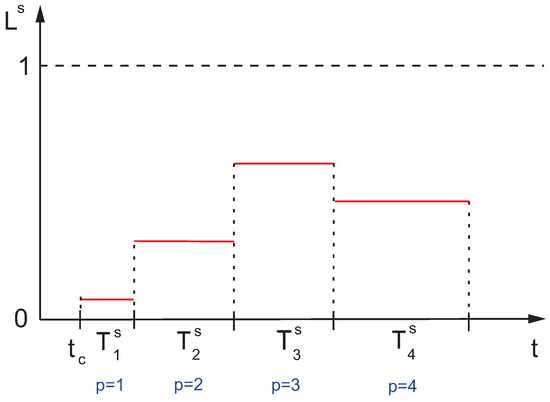
Figure 2.
Exemplary possible failure scenario; —level of likelihood of failure of the service s during time interval consisting of 4 subintervals: .
PFSs of essential services will deliver the most important information, and may be used, e.g., for analysis, graphical threat presentation, and, in cases when it is possible to determine numerical cost values for PFSs, for the optimization of different safety measures that may be applied during the incident.
3. LE Working Mode
Now, consider the risk assessment at the local unit level. Suppose that the s-th LE information system has multiple vulnerabilities , exploited by a number of cyber threats , where is the set of vulnerabilities, and is the set of cyber threats affecting the service s. The vulnerability is exploited with an impact factor on the likelihood of the failure/degradation of the service provided by LE. These impacts may be expressed with appropriate numbers attached, e.g., [25]: low (0, 0.1), medium (0.1, 0.5), and high (0.5, 1). For each threat , it is possible to assign a likelihood that this threat may exploit vulnerability , and to define the risk activation function as:
Moreover, except these local cyber threats, it may be that the external services influencing s-th LE can also be temporarily disrupted or substantially degraded. Let us denote the set of those entities by and the impact of the failure of the service u on the service s by . It is assumed that all compromised services can work in the safe mode, which implies that their likelihood of failure is restricted to .
Summing up, the likelihood that the service s will fail in the subinterval , issued at time , such that , can be be calculated as follows:
where . The argument , indicates the subinterval of relevant for the estimation of , the argument is the time from which the image of PFS of the service u possessed by the LE at time comes [7].
Iterations of the algorithm (3) are performed until convergence, which can be detected, e.g., by one of the protocol-free algorithms [26] or by the classical graph algorithm based on the acknowledgment messages [7]. During the iterations, it may happen that the information available at a LE level changes due to, for example, new incidents. This will affect the iterative process and the results until achieving a new stable forecast.
4. Convergence of the Algorithm
Let us analyze the conditions under which the algorithm (3) converges.
In fact, the first sum in (3) is constant in subsequent iterations, hence we may write this algorithm in the following way:
where is the vector of all variables for some t and for
Hence, in general, the algorithm (3) has the following form:
The mapping is nonsmooth, so we cannot use the convergence formula on the nonlinear mappings from reference [7], based on the properties of the Jacobian matrix. Instead, we derive a sufficient convergence condition using a general theory of convergence for asynchronous iterative algorithms [7,8,9].
The basic theory says that a sufficient condition for the (4) algorithm to converge when implemented totally asynchronously is that the mapping is contractive in the maximum norm [7], i.e.,:
Theorem 1.
We consider a mapping with the coordinate functions defined as:
where the coefficients are non-negative and such that:
The mapping F is a contraction in the maximum norm.
Proof.
Consider two arbitrary vectors and define as an index of the coordinate determining the value of the maximum norm of , that is:
Due to the definition (8) of functions and the assumption that all coefficients are non-negative, we will get for the mapping F:
Let us analyze deeper the term:
There are four combinations to analyze:
- We have here:
- We have here:
- We have here:
- We have here:
Thus, for all these cases there will be:
This means that F is a contractive mapping in the maximum norm. □
5. An Illustrative Example
To illustrate the ideas which were introduced above, let us consider an example of a system consisting of four service providers:
- Power company responsible for both a local power plant and the distribution grid (E);
- Railway transport company (T);
- Hospital (H);
- Data center (D).
All the services depend on electricity provided by the power company. In the case of a break in the energy supply, the hospital for few hours may use its own electricity generator and the data center has a UPS system, which holds its work for several dozen minutes. Except energy, some of the hospital and transport services depend also on access to the data center. The facility generating the electricity of the power plant is assumed to be coal fired and depends on the railway transport.
The graph of services and connections between them is presented in Figure 3.
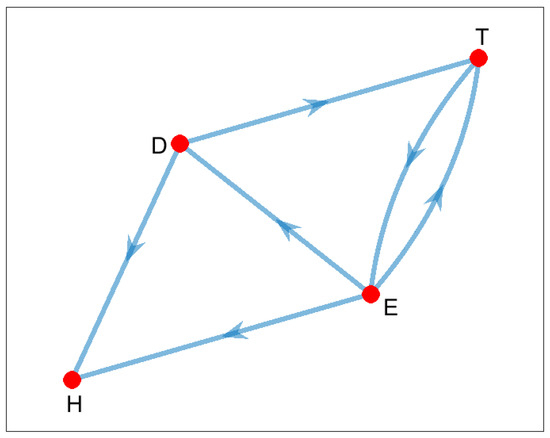
Figure 3.
Graph of services and dependencies: Notation: E—power company; T—transport company; H—hospital; D—data center.
Each local entity has its own information system that may be vulnerable and subject to various cyber threats, leading to the deterioration—in the extreme case to the safe mode level—of the service provided by this entity to its clients and to other entities. For example, the corruption of the control system of the power plant or the energy distribution network will lead to power outages in towns and in the countryside in the area served by the power company, including the hospital, the transport company, and the data center.
In all cases of the entities considered in the example, it is assumed that the Formula (3) is used to compute the possible service failure scenarios. The first term in (3), related to locally assessed threats, is aggregated to a given number:
Let us assume that one night at 4 a.m. cyber criminals started a DDOS attack on the IT system controlling the power plant. The abnormally growing traffic was noticed by the operator of the computer network of the company. His predicted scenario of the attack is presented in Figure 4. Namely, he suspects that such a situation may last longer, and if so, the risk factor will rise after the next half an hour from the current normal to a pre-alarm level until 6 a.m., and then to the alarm level until the end of the night shift at 8 a.m. At 8 a.m. the full IT staff will start their work and they will be gradually taking full control over the system and the local risk factors will decrease to .
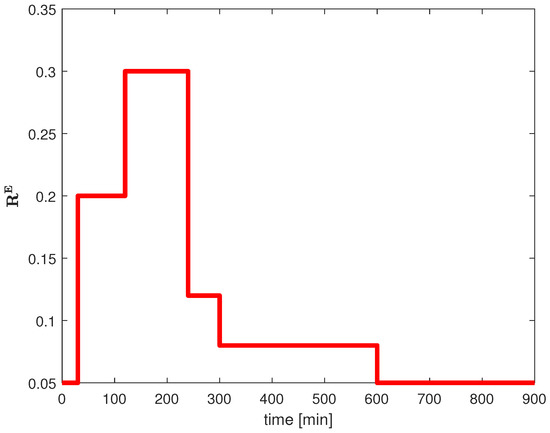
Figure 4.
Scenario of an attack on the power plant.
Now, starting from the power company (E), we assume the following timing and formulas defining the relevant scenarios:
The expressions for likelihoods and possible failure scenarios for the transport company (T) will be as follows:
The likelihoods and scenarios for the data center (D) are defined as:
And, finally, for the hospital (H), the likelihoods and scenarios are specified as:
Despite the overall time horizon being 15 h for all local units, the duration of time subintervals varies between the different entities.
The results of the computations are presented in Figure 5. The simulation shows that the rise of the risk of failure in the delivery of electricity results at about 4:30 a.m. in an almost immediate (more precisely, after 15 min) jump growth of the likelihood of failure of the railway transport system, and a little later we can see a similar, but smaller, effect for the data center (after an hour from the beginning of the incident, that is time “0”), and for the hospital (after 1.5 h from time “0”). Fortunately, when the day shift IT staff arrive to work at 8 a.m. (4 h from the beginning of the attack) this risk is attenuated, and this implies the decrease of the likelihood of failure, first of the power plant and then, in the same order as for the degradation, of the other services.
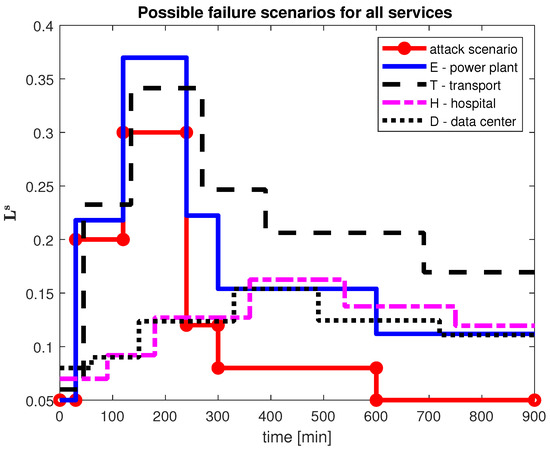
Figure 5.
Possible failure scenarios for the whole system after an attack on the power plant.
6. Conclusions
In the paper a distributed, predictive, online scheme for national-level risk assessments was proposed. In this scheme, local entities, delivering different important services, repetitively prepare their own assessments, taking into account the temporal dependencies of their services on local cyber threats and services provided by other entities. The iterative, asynchronously convergent algorithm, which calculates the local scenarios, takes into account interdependencies between different services as a linear combination of local and external components. Due to the restriction on the influence function of the external components, the resulting mapping is nonlinear and nonsmooth. It was proved that when the sum of the weights of the external units is less than one, this mapping is a contraction in the maximum norm and the algorithm is convergent. It was confirmed in a numerical case study concerning a system consisting of four entities. Particular attention was paid to the scenario of the external attack on one of the units. This scenario, that is its risk assessment, may depend on local decisions, e.g., the number of staff working in different hours. If this dependence can be described formally, the presented model with slight modifications can be used also for optimization and planning purposes. This will be the subject of future works. The deployment of these distributed, asynchronous mechanisms will speed up the development of decisions to protect the network from attacks and reduce their negative impacts on society and the economy.
Funding
This research received no external funding.
Conflicts of Interest
The author declares no conflict of interest.
Abbreviations
The following symbols were used in the manuscript:
| CNT | Operations Center |
| LE | local entity delivering a service |
| i-th local entity in the system | |
| PFS | possible failure scenario |
| time of calculation of the c-th set of possible failure scenarios | |
| for the whole system | |
| time of the k-th iteration of calculation of the PFS of the service s | |
| number of subintervals of the PFSs issued by the service (node) s | |
| the possible failure scenario (PFS) of the service s estimated at time | |
| p-th element of the scenario (sequence) | |
| time interval of the PFSs issued by the s-th LE | |
| p-th subinterval of | |
| set of vulnerabilities of the s -th LE information system | |
| set of cyber threats affecting the service s | |
| likelihood that the m-th threat may exploit vulnerability of the service s | |
| risk activation function of a threat for the service s | |
| in the p-th subinterval of its PFS | |
| aggregated risk activation function for the service s | |
| in the p-th subinterval of its PFS | |
| impact factor of the vulnerability on the failure/degradation | |
| of the service provided by the s-th LE | |
| set of the external services influencing s-th LE | |
| impact factor of the failure of the service u on the service s | |
| the subinterval of relevant for the estimation of | |
| time from which the image of PFS of the service u possessed by the s-th LE | |
| at time stems | |
| the maximal likelihood of failure of a service |
References
- Yadav, R. Cyber Security Threats During COVID-19 Pandemic. Int. Trans. J. Eng. Manag. Appl. Sci. Technol. 2021, 12, 12A3Q. [Google Scholar]
- Shah, A.; Ganesan, R.; Jajodia, S.; Samarati, P.; Cam, H. Adaptive Alert Management for Balancing Optimal Performance among Distributed CSOCs using Reinforcement Learning. IEEE Trans. Parallel Distr. Syst. 2020, 31, 16–33. [Google Scholar] [CrossRef]
- Baz, M.; Alhakami, H.; Agrawal, A.; Baz, A.; Khan, R.A. Impact of COVID-19 Pandemic: A Cybersecurity Perspective. Intell. Autom. Soft Comput. 2021, 27, 641–652. [Google Scholar] [CrossRef]
- European Commission, Joint Research Centre. Recommendations for National Risk Assessment for Disaster Risk Management in EU; Publications Office of the European Union: Luxembourg, 2021. [Google Scholar]
- Malinowski, K.; Karbowski, A. Real-Time Hierarchical Predictive Risk Assessment at National Level; Mutually Agreed Predicted Service Disruption Profiles. Int. J. Appl. Math. Comput. Sci. 2020, 30, 597–609. [Google Scholar]
- Karbowski, A.; Malinowski, K. Two-Level System of on-Line Risk Assessment in the National Cyberspace. IEEE Access 2020, 8, 181404–181410. [Google Scholar] [CrossRef]
- Bertsekas, D.P.; Tsitsiklis, J.N. Parallel and Distributed Computation: Numerical Methods; Athena Scientific: Belmont, MA, USA, 2015. [Google Scholar]
- Karbowski, A. Distributed, Asynchronous Algorithms for Data Networks Control—A State of the Art Review. In Artificial Intelligence and Computer Science; Shannon, S., Ed.; Nova Science Publishers, Inc.: Commack, NY, USA, 2005; pp. 59–82. [Google Scholar]
- Karbowski, A. Comments on Optimization Flow Control, I: Basic Algorithm and Convergence. IEEE/ACM Trans. Netw. 2003, 11, 338–339. [Google Scholar] [CrossRef]
- Mirzaei, O.; de Fuentes, J.M.; González Manzano, L. Dynamic Risk Assessment in IT Environments: A Decision Guide. In Handbook of Research on Information and Cyber Security in the Fourth Industrial Revolution; Fields, Z., Ed.; IGI Global: Hershey, PA, USA, 2018; pp. 234–261. [Google Scholar]
- Pirbhulal, S.; Gkioulos, V.; Katsikas, S. A Systematic Literature Review on RAMS analysis for critical infrastructures protection. Int. J. Crit. Infrastruct. Prot. 2021, 33, 100427. [Google Scholar] [CrossRef]
- Brændelanda, G.; Refsdal, A.; Stølen, K. Modular analysis and modelling of risk scenarios with dependencies. J. Syst. Softw. 2010, 83, 1995–2013. [Google Scholar] [CrossRef]
- Theoharidou, M.; Kotzanikolaou, P.; Gritzalis, D. Risk assessment methodology for interdependent critical infrastructures. Int. J. Risk Assess. Manag. 2011, 15, 128–148. [Google Scholar] [CrossRef]
- Gonzalez-Granadillo, G.; Dubus, S.; Motzek, A.; Garcia-Alfaro, J.; Alvarez, E.; Merialdo, M.; Papillon, S.; Debar, H. Dynamic risk management response system to handle cyber threats. Future Gener. Comput. Syst. 2018, 83, 535–555. [Google Scholar] [CrossRef]
- Bhuiyan, T.H.; Medal, H.R.; Nandi, A.K.; Halappanavar, M. Risk-averse bi-level stochastic network interdiction model for cyber-security risk management. Int. J. Crit. Infrastruct. Prot. 2021, 32, 100408. [Google Scholar] [CrossRef]
- Naumov, S.; Kabanov, I. Dynamic framework for assessing cyber security risks in a changing environment. In Proceedings of the 22nd International Conference on Information and Software Technologies ICIST 2016, Druskininkai, Lithuania, 13–15 October 2016. [Google Scholar]
- Amin, M.T.; Khan, F.; Ahmed, S.; Imtiaz, S. A novel data-driven methodology for fault detection and dynamic risk assessment. Can. J. Chem. Eng. 2020, 98, 2397–2416. [Google Scholar] [CrossRef]
- Ye, N.; Zhang, Y.; Borror, C.M. Robustness of the Markov-Chain Model for Cyber-Attack Detection. IEEE Trans. Reliab. 2004, 53, 116–123. [Google Scholar] [CrossRef]
- Karbowski, A.; Malinowski, K.; Szwaczyk, S.; Jaskóła, P. Critical Infrastructure Risk Assessment Using Markov Chain Model. J. Telecommun. Inf. Technol. 2019, 2019, 15–20. [Google Scholar] [CrossRef]
- Hu, B.; Zhou, C.; Tian, Y.-C.; Hu, X.; Junping, X. Decentralized Consensus Decision-Making for Cybersecurity Protection in Multimicrogrid Systems. IEEE Trans. Syst. Man Cybern. Syst. 2021, 51, 2187–2198. [Google Scholar] [CrossRef]
- European Union Agency for Network and Information Security. National-level Risk Assessments an Analysis Report—Executive Summary Nov. 2013; ENISA: Heraklion, Greece, 2013.
- Kure, H.I.; Islam, S.; Razzaque, M.A. An Integrated Cyber Security Risk Management Approach for a Cyber-Physical System. Appl. Sci. 2018, 8, 898. [Google Scholar] [CrossRef] [Green Version]
- Riesco, R.; Villagrá, V.A. Leveraging cyber threat intelligence for a dynamic risk framework. Int. J. Inf. Secur. 2019, 18, 715–739. [Google Scholar] [CrossRef]
- Kavallieratos, G.; Spathoulas, G.; Katsikas, S. Cyber Risk Propagation and Optimal Selection of Cybersecurity Controls for Complex Cyberphysical Systems. Sensors 2021, 21, 1691. [Google Scholar] [CrossRef] [PubMed]
- National Institute of Standards and Technology, U.S. Department of Commerce. Guide for Conducting Risk Assessments, Information Security. NIST Special Publication 800—30 Revision 1; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2012.
- Gbikpi-Benissan, G.; Magoulèsb, F. Protocol-free asynchronous iterations termination. Adv. Eng. Softw. 2020, 146, 102827. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
