A Proficient ZESO-DRKFC Model for Smart Grid SCADA Security
Abstract
1. Introduction
1.1. Motivation
1.2. Problem Statement
1.3. Objectives
- Data preprocessing is carried out to normalize the original SCADA benchmarking datasets, which includes the operations of content characterization, scalar calculation, and category transformation.
- An innovative Zaire Ebola Search Optimization (ZESO) method that offers the best option for producing the optimized feature set is used to extract the most pertinent features from the normalized dataset.
- A sophisticated Deep Random Kernel Forest Classification (DRKFC) mechanism is used to predict the normal and attack data flows from the SCADA dataset.
- Some of the well-known SCADA benchmarking datasets are used to evaluate the effectiveness and outcomes of the proposed ZESO-RKFC security framework.
1.4. Organization
2. Literature Review
- Risk management;
- Malware protection;
- Vulnerability assessment;
- Security control;
- Cyber-risk analysis;
- Physical security.
Research Gap
- High delay;
- Overfitting;
- Decreased detection accuracy;
- Ineffective handling of massive datasets;
- Complexity of computation.
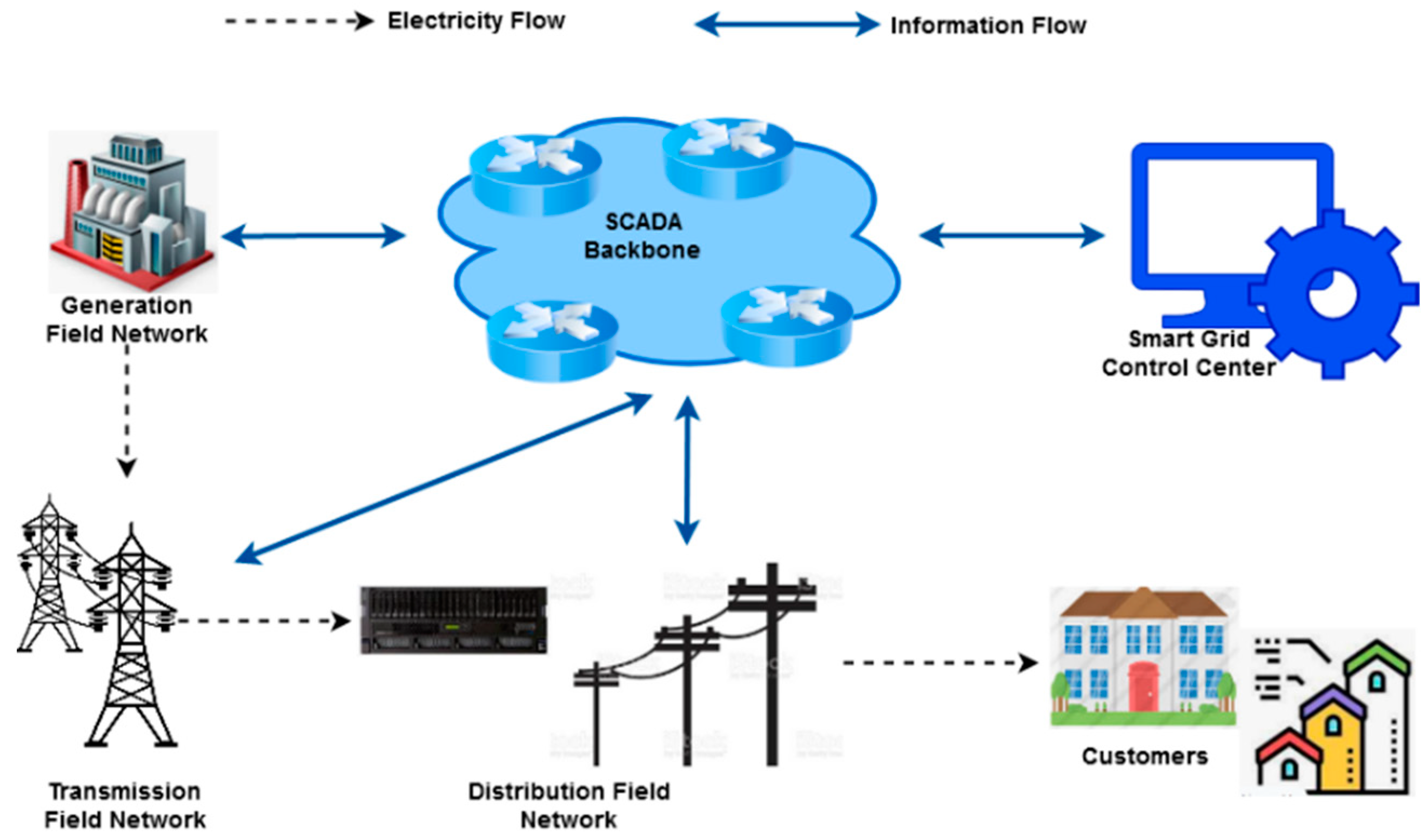
3. Materials and Methods
- SCADA benchmark dataset obtainment;
- Normalization;
- ZESO-based feature selection;
- DRKFC-based attack prediction;
- Performance evaluation.
3.1. Preprocessing
3.2. Zaire Ebola Search Optimization (ZESO)
- The newly infected persons (nP) are generated based on the set (s);
- Then, the generated persons are added in αc;
- According to the size of , the number of individuals is estimated and added to , , , , and .
- Consequently, update ,) based on ;
- Choose the current best value from , and compare it with the global best;
- Finally, return the global best solution with the optimal solution;
3.3. Deep Random Kernel Forest Classification (DRKFC)
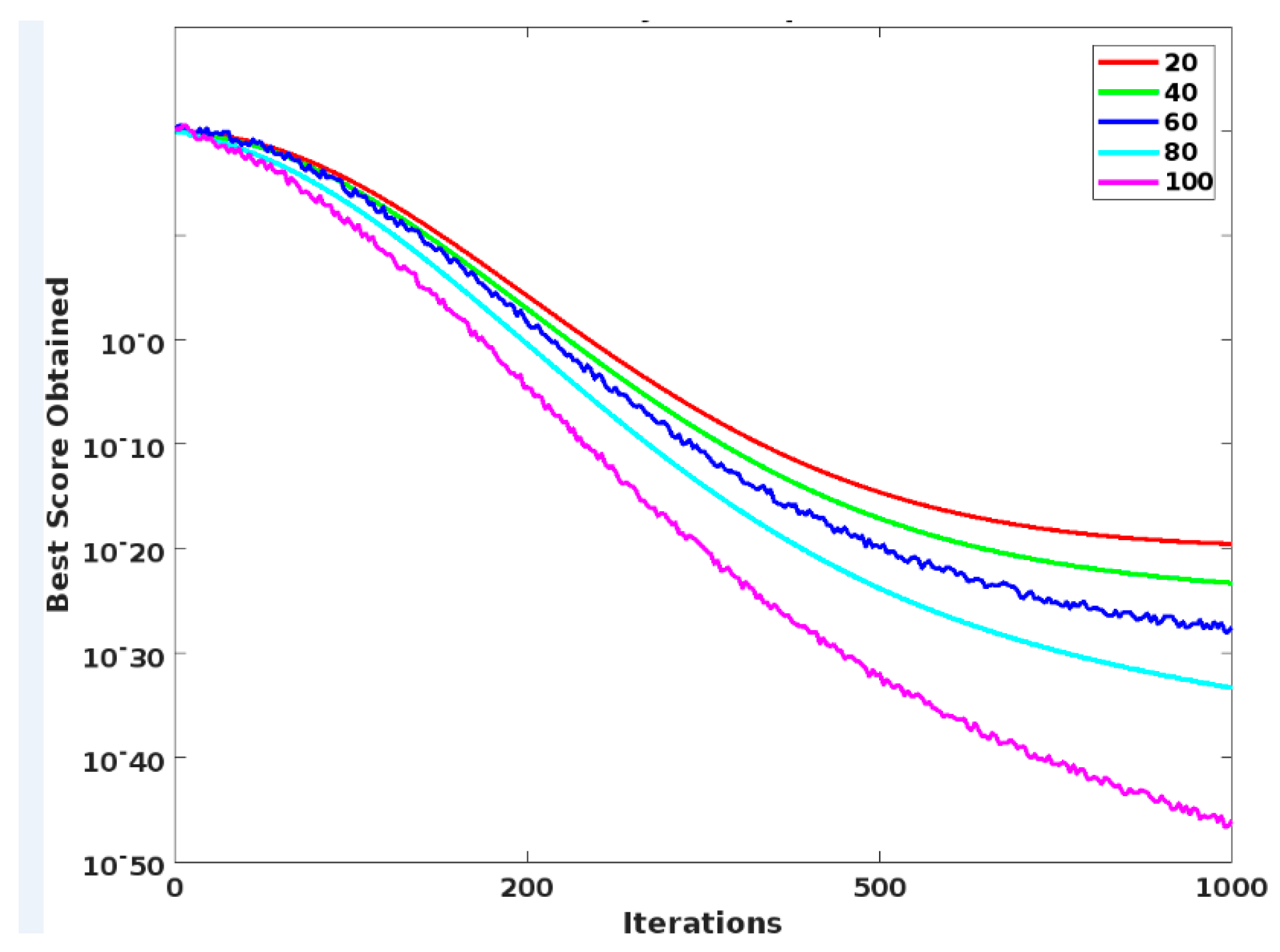
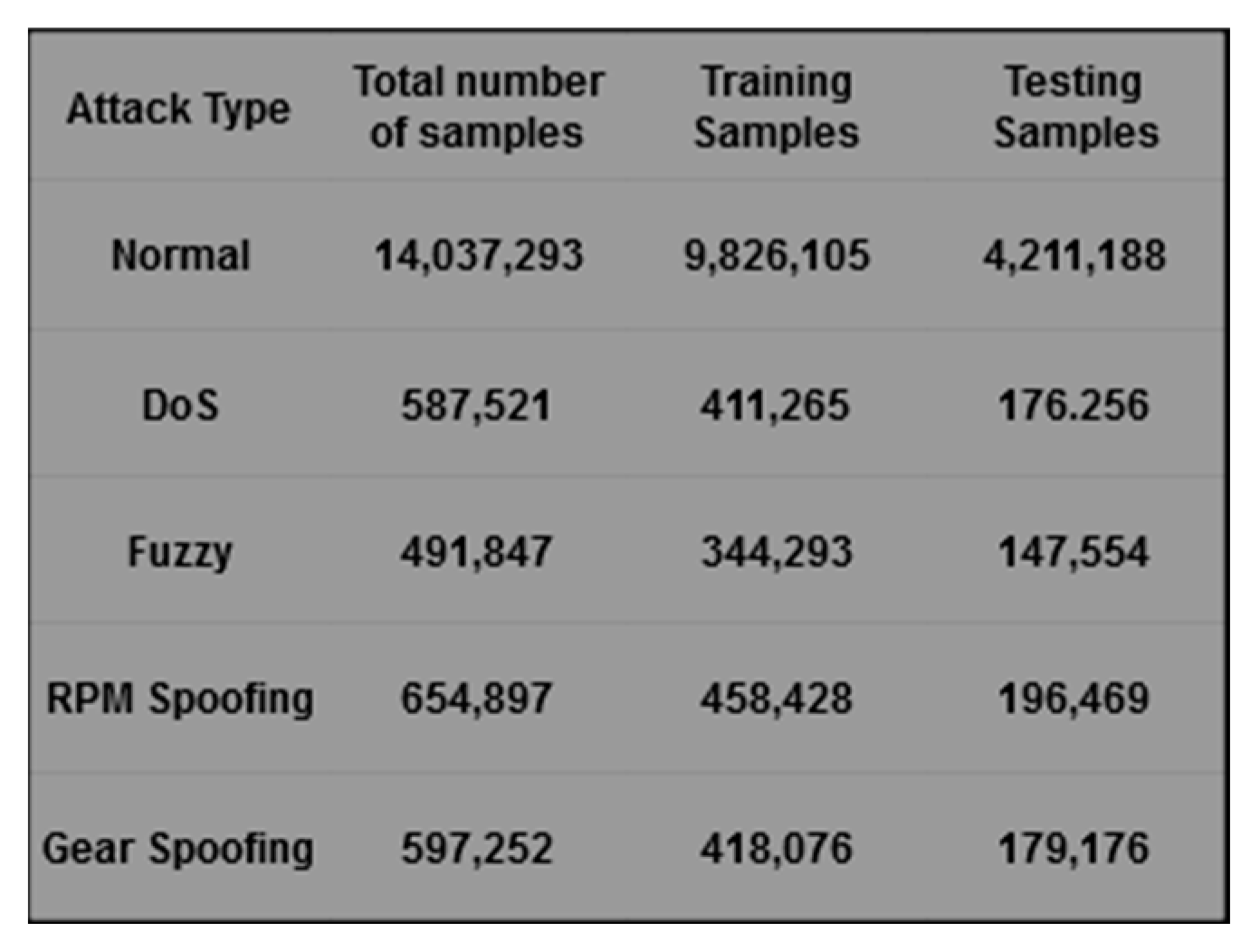
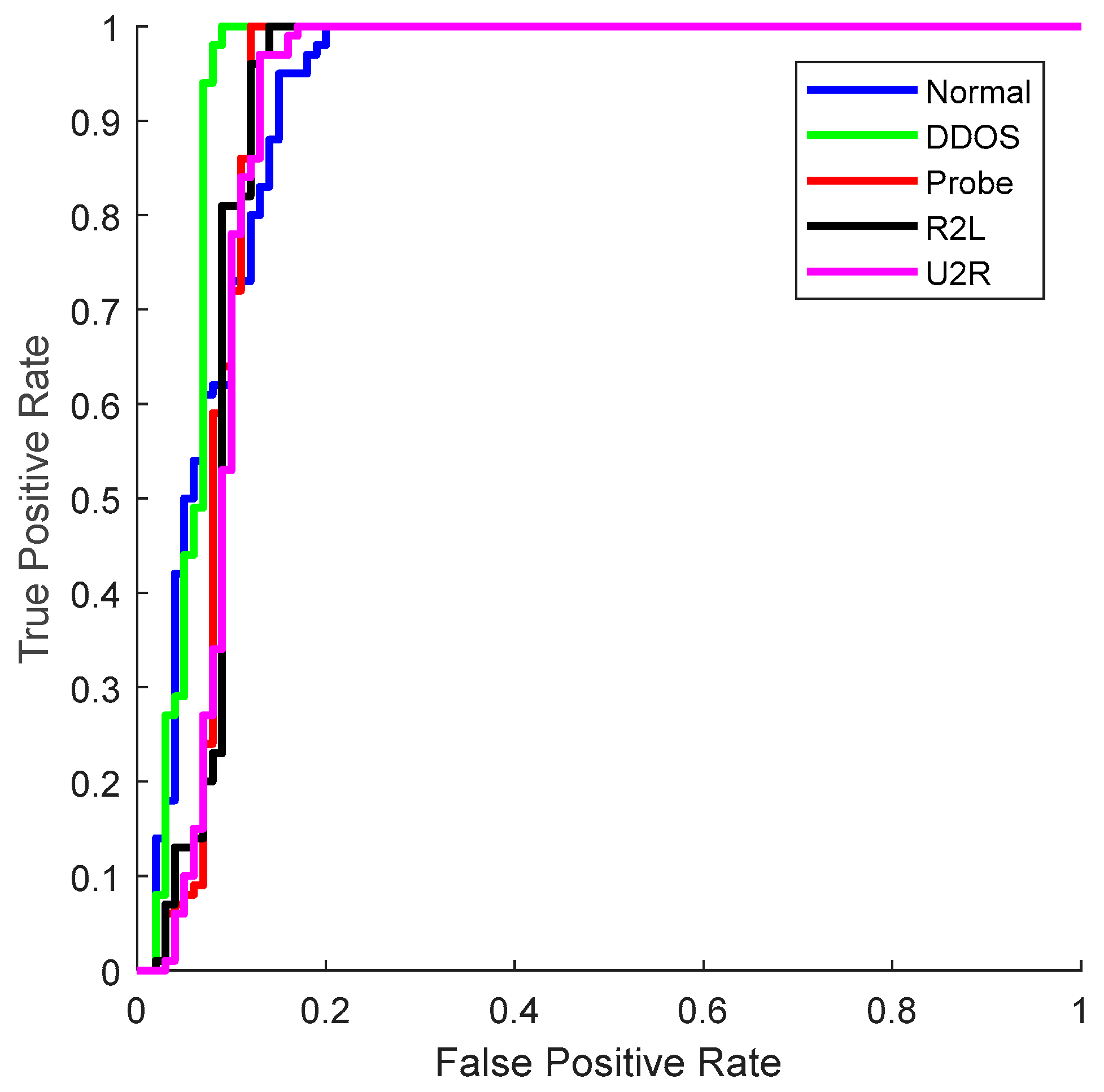
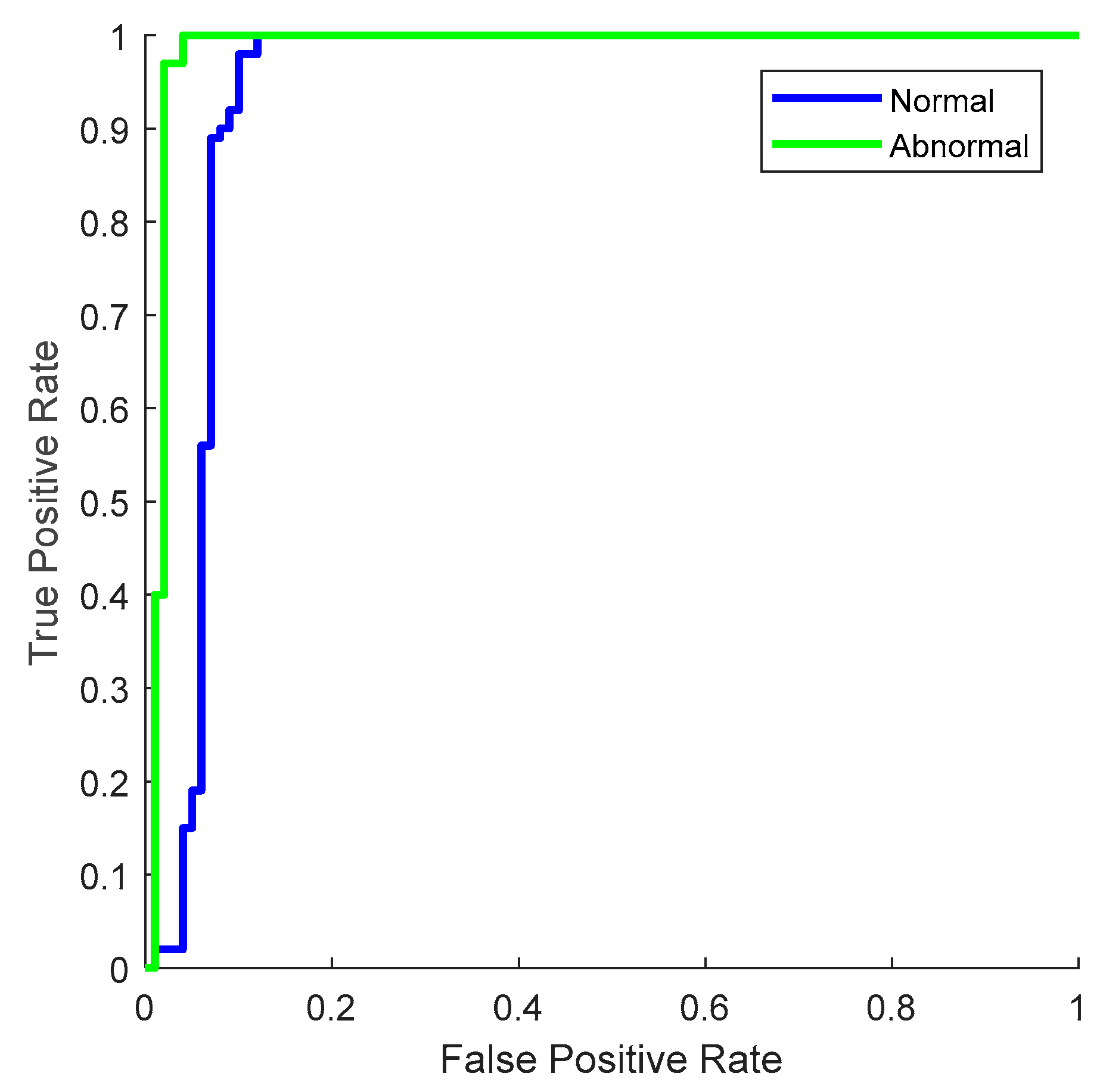
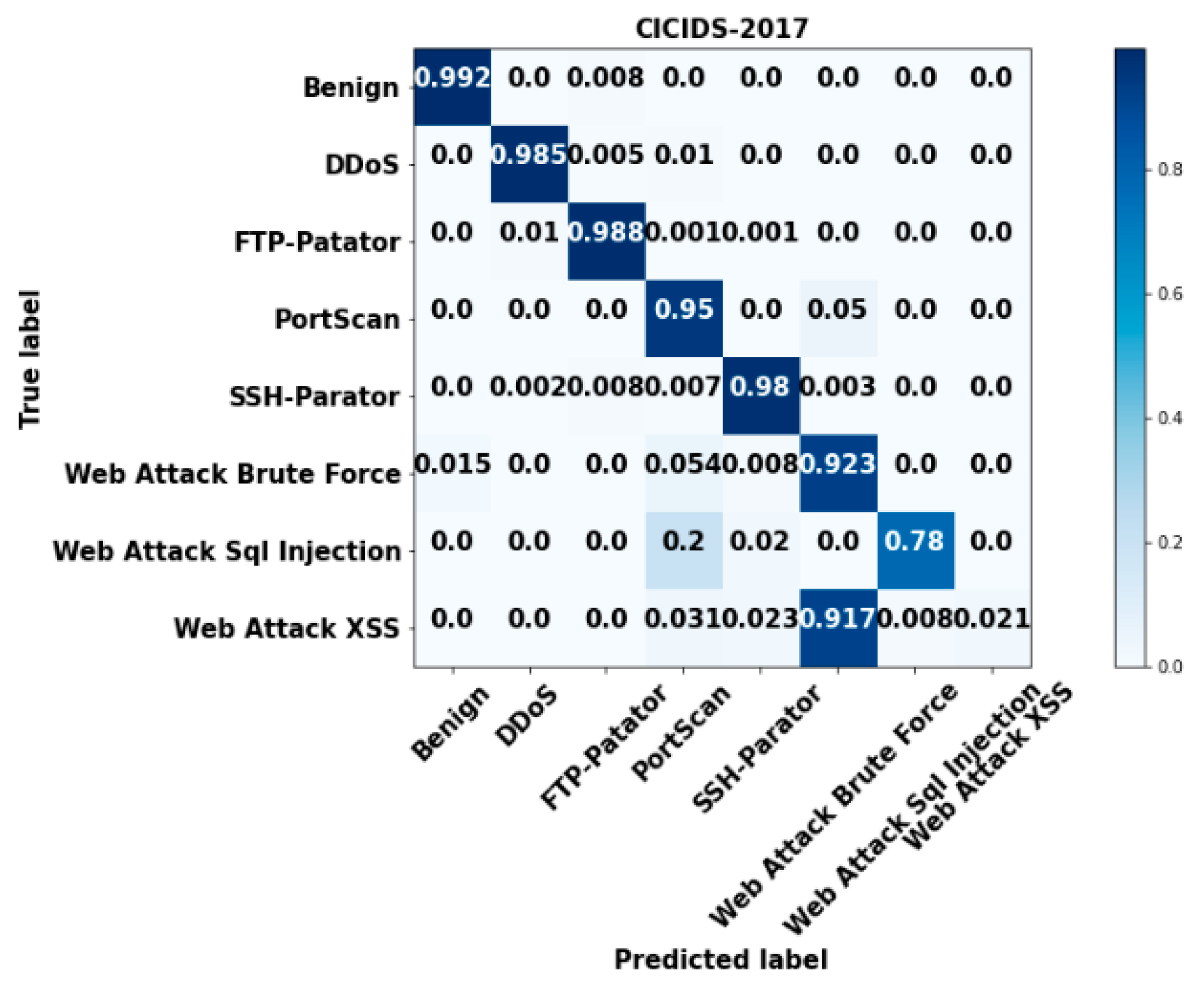
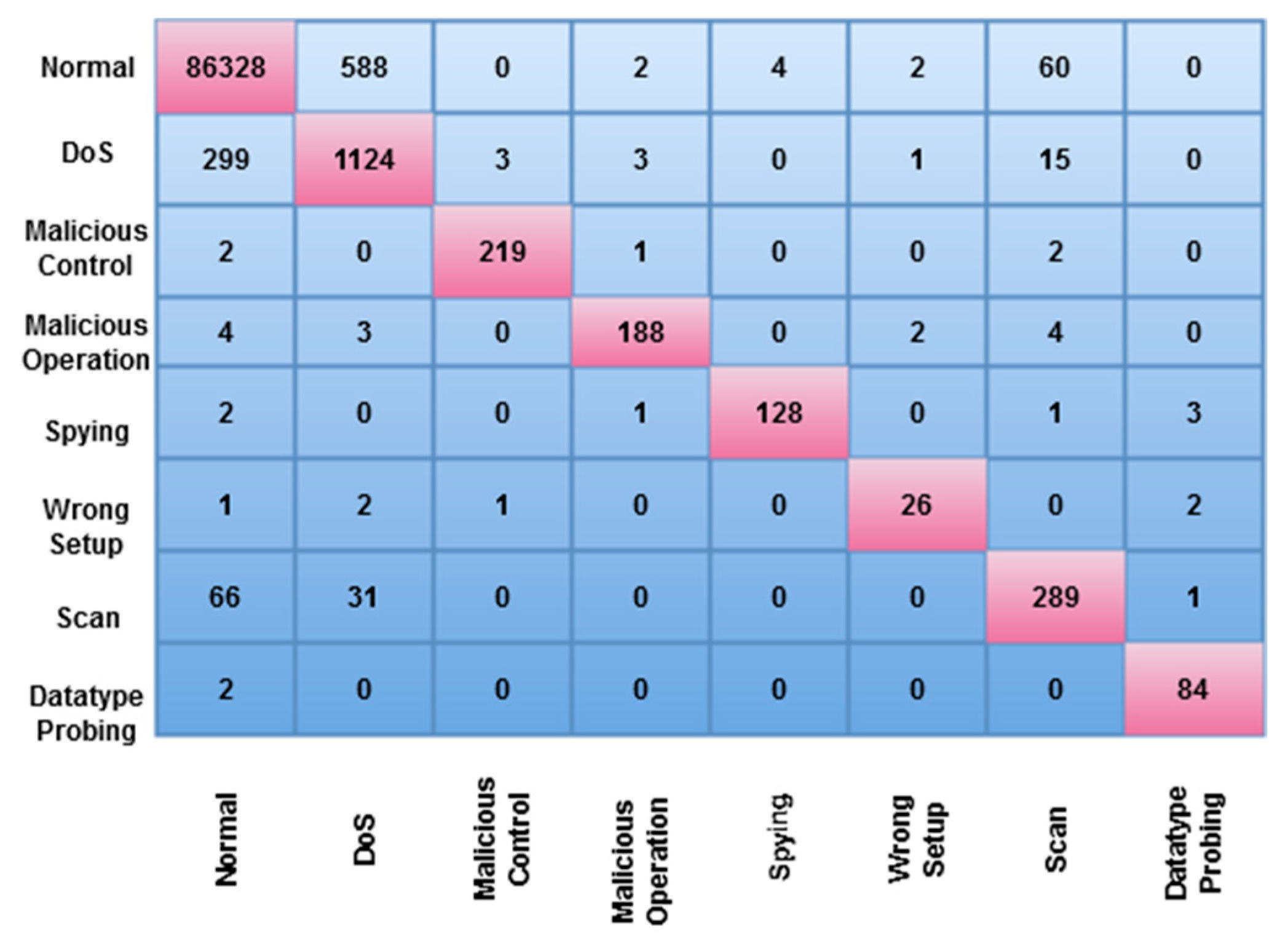
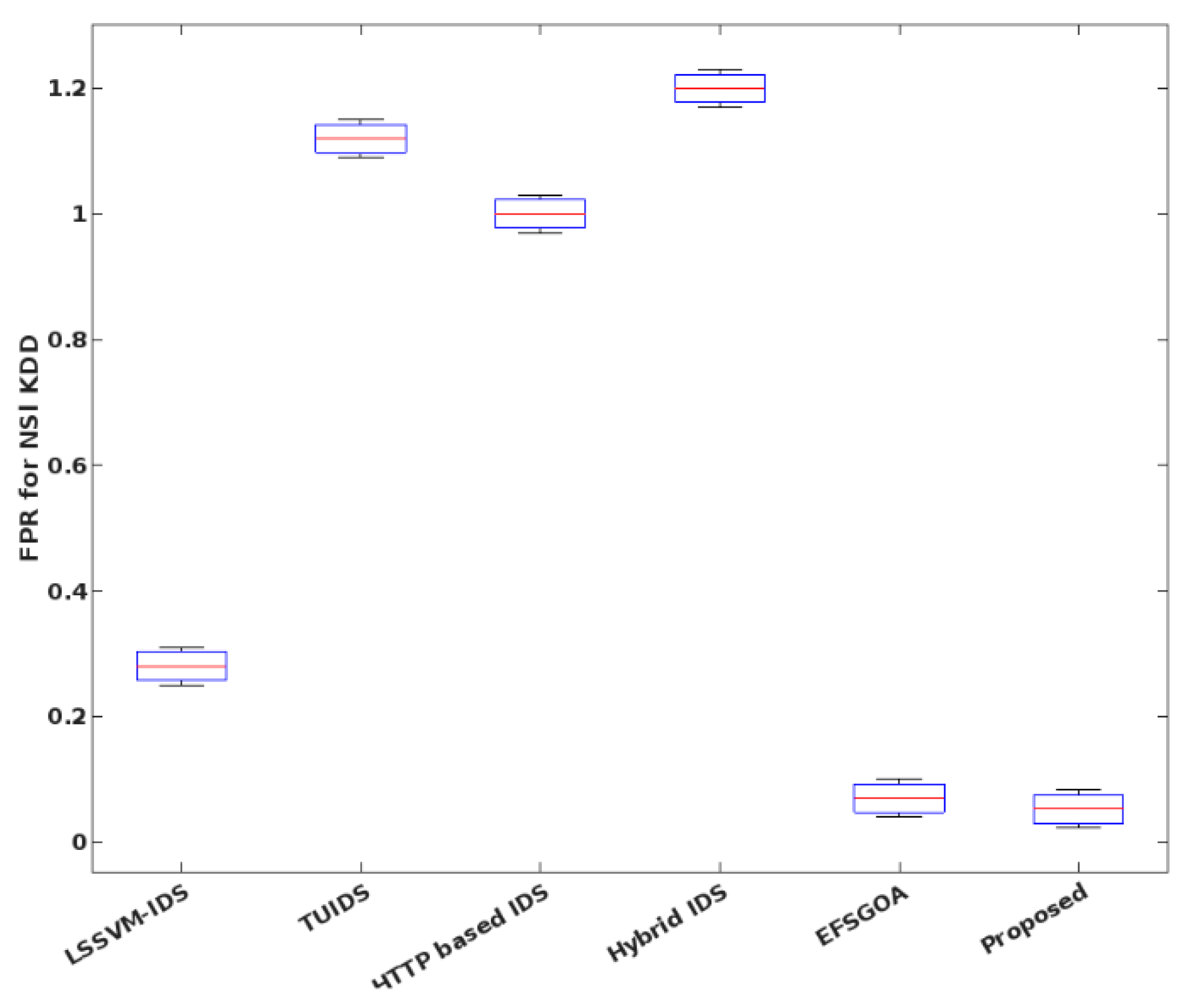
4. Results
5. Discussion
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Jakaria, A.; Rahman, M.A.; Gokhale, A. Resiliency-aware deployment of SDN in smart grid SCADA: A formal synthesis model. IEEE Trans. Netw. Serv. Manag. 2021, 18, 1430–1444. [Google Scholar] [CrossRef]
- Khadidos, A.O.; Khadidos, A.O.; Manoharan, H.; Alyoubi, K.H.; Alshareef, A.M.; Selvarajan, S. Integrating Industrial Appliances for Security Enhancement in Data Point Using SCADA Networks with Learning Algorithm. Int. Trans. Electr. Energy Syst. 2022, 17, 5235. [Google Scholar] [CrossRef]
- Baker, T.; Asim, M.; MacDermott, Á.; Iqbal, F.; Kamoun, F.; Shah, B. A secure fog-based platform for SCADA-based IoT critical infrastructure. Softw. Pract. Exp. 2020, 50, 503–518. [Google Scholar] [CrossRef]
- Sajid, A.; Abbas, H.; Saleem, K. Cloud-assisted IoT-based SCADA systems security: A review of the state of the art and future challenges. IEEE Access 2016, 4, 1375–1384. [Google Scholar] [CrossRef]
- Katyara, S.; Shah, M.A.; Chowdhary, B.S.; Akhtar, F.; Lashari, G.A. Monitoring, control and energy management of smart grid system via WSN technology through SCADA applications. Wirel. Pers. Commun. 2019, 106, 1951–1968. [Google Scholar] [CrossRef]
- Altaha, M.; Hong, S. Anomaly Detection for SCADA System Security Based on Unsupervised Learning and Function Codes Analysis in the DNP3 Protocol. Electronics 2022, 11, 2184. [Google Scholar] [CrossRef]
- Ivanković, I.; Peharda, D.; Novosel, D.; Žubrinić-Kostović, K.; Kekelj, A. Smart grid substation equipment maintenance management functionality based on control center SCADA data. J. Energy: Energ. 2018, 67, 30–35. [Google Scholar] [CrossRef]
- Shitharth, S.; Prasad, K.M.; Sangeetha, K.; Kshirsagar, P.R.; Babu, T.S.; Alhelou, H.H. An Enriched RPCO-BCNN Mechanisms for Attack Detection and Classification in SCADA Systems. IEEE Access 2021, 9, 156297–156312. [Google Scholar] [CrossRef]
- Ramesh, A.; Satvik, D.; Nagasundari, S.; Honnavalli, P.B. Simulation of SCADA System for Advanced Metering Infrastructure in Smart Grid. In Proceedings of the International Conference on Smart Electronics and Communication (ICOSEC), Trichy, India, 10–12 September 2020; pp. 1071–1077. [Google Scholar]
- Tsitaitse, T.J.; Cai, Y.; Ditta, A. Secure self-healing group key distribution scheme with constant storage for SCADA systems in smart grid. Wirel. Pers. Commun. 2018, 101, 1749–1763. [Google Scholar] [CrossRef]
- Chan, A.C.-F.; Zhou, J. Toward Safe Integration of Legacy SCADA Systems in the Smart Grid. In Proceedings of the International Conference on Applied Cryptography and Network Security, Kyoto, Japan, 19–22 June 2022; pp. 338–357. [Google Scholar]
- Gozuoglu, A.; Ozgonenel, O. Training Set Design for Smart Grids and Scada Co-Simulations. In Proceedings of the 7th International Istanbul Smart Grids and Cities Congress and Fair (ICSG), Istanbul, Turkiye, 25–26 April 2019; pp. 124–128. [Google Scholar]
- Kermani, M.; Adelmanesh, B.; Shirdare, E.; Sima, C.A.; Carnì, D.L.; Martirano, L. Intelligent energy management based on SCADA system in a real Microgrid for smart building applications. Renew. Energy 2021, 171, 1115–1127. [Google Scholar] [CrossRef]
- Wertani, H.; Salem, J.B.; Lakhoua, M. Analysis and supervision of a smart grid system with a systemic tool. Electr. J. 2020, 33, 106784. [Google Scholar] [CrossRef]
- Gusrialdi, A.; Qu, Z. Smart grid security: Attacks and defenses. In Smart Grid Control; Springer: Berlin/Heidelberg, Germany, 2019; pp. 199–223. [Google Scholar]
- Kim, Y.; Hakak, S.; Ghorbani, A. Smart grid security: Attacks and defence techniques. IET Smart Grid 2022, 1–21. [Google Scholar] [CrossRef]
- Sangeetha, K.; Shitharth, S.; Mohammed, G.B. Enhanced SCADA IDS Security by Using MSOM Hybrid Unsupervised Algorithm. Int. J. Web Based Learn. Teach. Technol. 2022, 17, 1–9. [Google Scholar] [CrossRef]
- Kao, C.-Y.; Chueh, H.-E. A Vendor-Managed Inventory Mechanism Based on SCADA of Internet of Things Framework. Electronics 2022, 11, 881. [Google Scholar] [CrossRef]
- Ghosh, U.; Chatterjee, P.; Shetty, S. Securing SDN-enabled smart power grids: SDN-enabled smart grid security. In Research Anthology on Smart Grid and Microgrid Development; IGI Global: Hershey, PA, USA, 2022; pp. 1028–1046. [Google Scholar]
- Shitharth, S.; Satheesh, N.; Kumar, B.P.; Sangeetha, K. IDS Detection Based on Optimization Based on WI-CS and GNN Algorithm in SCADA Network. In Architectural Wireless Networks Solutions and Security Issues, Lecture Notes in Network and Systems; Springer: Singapore, 2021; Volume 196, pp. 247–266. [Google Scholar] [CrossRef]
- Nafees, M.N.; Saxena, N.; Cardenas, A.; Grijalva, S.; Burnap, P. Smart Grid Cyber-Physical Situational Awareness of Complex Operational Technology Attacks: A Review. ACM Comput. Surv. 2022, 74, 5570. [Google Scholar] [CrossRef]
- Reda, H.T.; Anwar, A.; Mahmood, A. Comprehensive survey and taxonomies of false data injection attacks in smart grids: Attack models, targets, and impacts. Renew. Sustain. Energy Rev. 2022, 163, 112423. [Google Scholar] [CrossRef]
- Ding, J.; Qammar, A.; Zhang, Z.; Karim, A.; Ning, H. Cyber Threats to Smart Grids: Review, Taxonomy, Potential Solutions, and Future Directions. Energies 2022, 15, 6799. [Google Scholar] [CrossRef]
- Khoei, T.T.; Slimane, H.O.; Kaabouch, N. A Comprehensive Survey on the Cyber-Security of Smart Grids: Cyber-Attacks, Detection, Countermeasure Techniques, and Future Directions. arXiv 2022, arXiv:2207.07738. [Google Scholar]
- Mahi-Al-rashid, A.; Hossain, F.; Anwar, A.; Azam, S. False Data Injection Attack Detection in Smart Grid Using Energy Consumption Forecasting. Energies 2022, 15, 4877. [Google Scholar] [CrossRef]
- Martinelli, F.; Mercaldo, F.; Santone, A. A Method for Intrusion Detection in Smart Grid. Procedia Comput. Sci. 2022, 207, 327–334. [Google Scholar] [CrossRef]
- Khadidos, A.O.; Manoharan, H.; Selvarajan, S.; Khadidos, A.O.; Alyoubi, K.H.; Yafoz, A. A Classy Multifacet Clustering and Fused Optimization Based Classification Methodologies for SCADA Security. Energies 2022, 15, 3624. [Google Scholar] [CrossRef]
- Rajawat, A.S.; Rawat, R.; Barhanpurkar, K. Security Improvement Technique for Distributed Control System (DCS) and Supervisory Control-Data Acquisition (SCADA) Using Blockchain at Dark Web Platform. Cyber Secur. Digit. Forensics 2022, 56, 317–333. [Google Scholar]
- Minh, Q.N.; Nguyen, V.-H.; Quy, V.K.; Ngoc, L.A.; Chehri, A.; Jeon, G. Edge Computing for IoT-Enabled Smart Grid: The Future of Energy. Energies 2022, 15, 6140. [Google Scholar] [CrossRef]
- Hussain, S.Z.R.; Osman, A.; Moin, M.A.; Memon, J.A. IoT Enabled Real-time Energy Monitoring and Control System. In Proceedings of the 9th International Conference on Smart Grid (icSmartGrid), Setubal, Portugal, 29 June–1 July 2021; pp. 97–102. [Google Scholar]
- Khalid, L.F.; Ameen, S.Y. Secure Iot integration in daily lives: A review. J. Inf. Technol. Inform. 2021, 1, 6–12. [Google Scholar]
- Justindhas, Y.; Jeyanthi, P. Attack detection and prevention in IoT-SCADA networks using NK-classifier. Soft Comput. 2022, 26, 6811–6823. [Google Scholar] [CrossRef]
- Lu, K.-C.; Liu, I.-H.; Liao, J.-W.; Wu, S.-C.; Liu, Z.-C.; Li, J.-S. Evaluation and Build to honeypot System about SCADA Security for Large-Scale IoT Devices. J. Robot. Netw. Artif. Life 2019, 6, 157–161. [Google Scholar] [CrossRef]
- Huda, S.; Yearwood, J.; Hassan, M.M.; Almogren, A. Securing the operations in SCADA-IoT platform based industrial control system using ensemble of deep belief networks. Appl. Soft Comput. 2018, 71, 66–77. [Google Scholar] [CrossRef]
- Hossain, M.T.; Badsha, S.; Shen, H. Porch: A novel consensus mechanism for blockchain-enabled future scada systems in smart grids and industry 4.0. In Proceedings of the 2020 IEEE International IOT, Electronics and Mechatronics Conference (IEMTRONICS), Vancouver, Canada, 9–12 September 2020; pp. 145–477. [Google Scholar]
- Rivera, A.O.G.; Tosh, D.K.; Ghosh, U. Resilient sensor authentication in SCADA by integrating physical unclonable function and blockchain. Clust. Comput. 2022, 25, 1869–1883. [Google Scholar] [CrossRef]
- Singh, V.K.; Ebrahem, H.; Govindarasu, M. Security evaluation of two intrusion detection systems in smart grid scada environment. In Proceedings of the 2018 North American Power Symposium (NAPS), Fargo, ND, USA, 9–11 September 2018; pp. 1–6. [Google Scholar]
- Hasan, M.M.; Mouftah, H.T. Optimization of trust node assignment for securing routes in smart grid SCADA networks. IEEE Syst. J. 2018, 13, 1505–1513. [Google Scholar] [CrossRef]
- Islam, S.N.; Baig, Z.; Zeadally, S. Physical layer security for the smart grid: Vulnerabilities, threats, and countermeasures. IEEE Trans. Ind. Inform. 2019, 15, 6522–6530. [Google Scholar] [CrossRef]
- Masri, A.; Al-Jabi, M. Toward fault tolerant modelling for SCADA based electricity distribution networks, machine learning approach. PeerJ Comput. Sci. 2021, 7, e554. [Google Scholar] [CrossRef] [PubMed]
- Abir, S.A.A.; Anwar, A.; Choi, J.; Kayes, A. Iot-enabled smart energy grid: Applications and challenges. IEEE Access 2021, 9, 50961–50981. [Google Scholar] [CrossRef]
- Risco, A.B.; Salinas, R.I.G.; Guerrero, A.O.; Esparta, D.L.B. IoT-based SCADA System for Smart Grid Stability Monitoring using Machine Learning Algorithms. In Proceedings of the IEEE XXVIII International Conference on Electronics, Electrical Engineering and Computing (INTERCON), Online, 5–7 August 2021; pp. 1–4. [Google Scholar]
- Radoglou-Grammatikis, P.I.; Sarigiannidis, P.G. Securing the smart grid: A comprehensive compilation of intrusion detection and prevention systems. IEEE Access 2019, 7, 46595–46620. [Google Scholar] [CrossRef]
- Singh, V.K.; Govindarasu, M. Cyber Kill Chain-Based Hybrid Intrusion Detection System for Smart Grid. In Wide Area Power Systems Stability, Protection, and Security; Springer: Berlin/Heidelberg, Germany, 2021; pp. 571–599. [Google Scholar]
- Holik, F.; Flå, L.H.; Jaatun, M.G.; Yayilgan, S.Y.; Foros, J. Threat modeling of a smart grid secondary substation. Electronics 2022, 11, 850. [Google Scholar] [CrossRef]
- Devyatkin, D.A. Estimation of Vegetation Indices With Random Kernel Forests. IEEE Access 2023, 11, 29500–29509. [Google Scholar] [CrossRef]
- Yang, L.; Moubayed, A.; Shami, A. MTH-IDS: A multitiered hybrid intrusion detection system for Internet of vehicles. IEEE Internet Things J. 2021, 9, 616–632. [Google Scholar] [CrossRef]









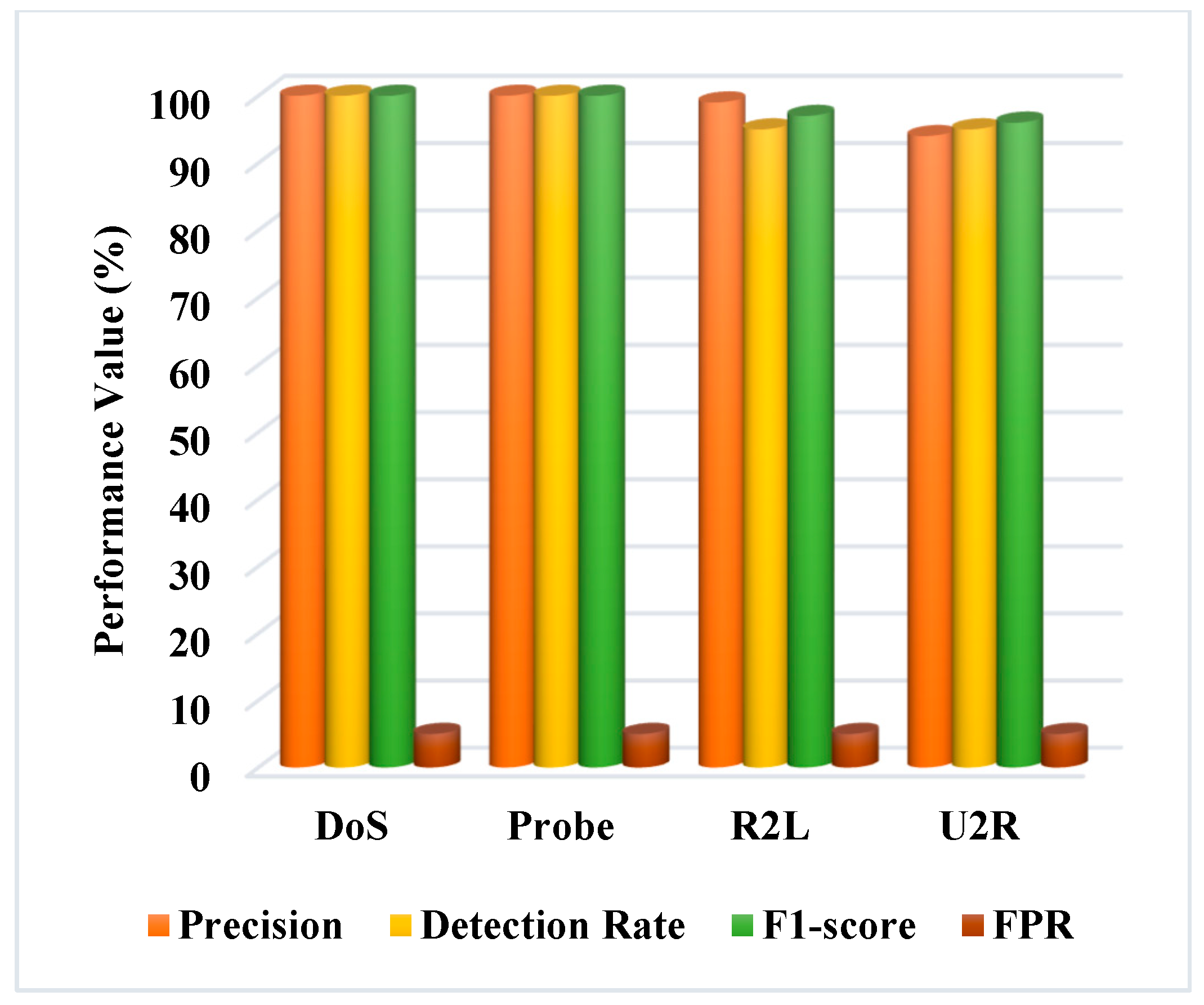

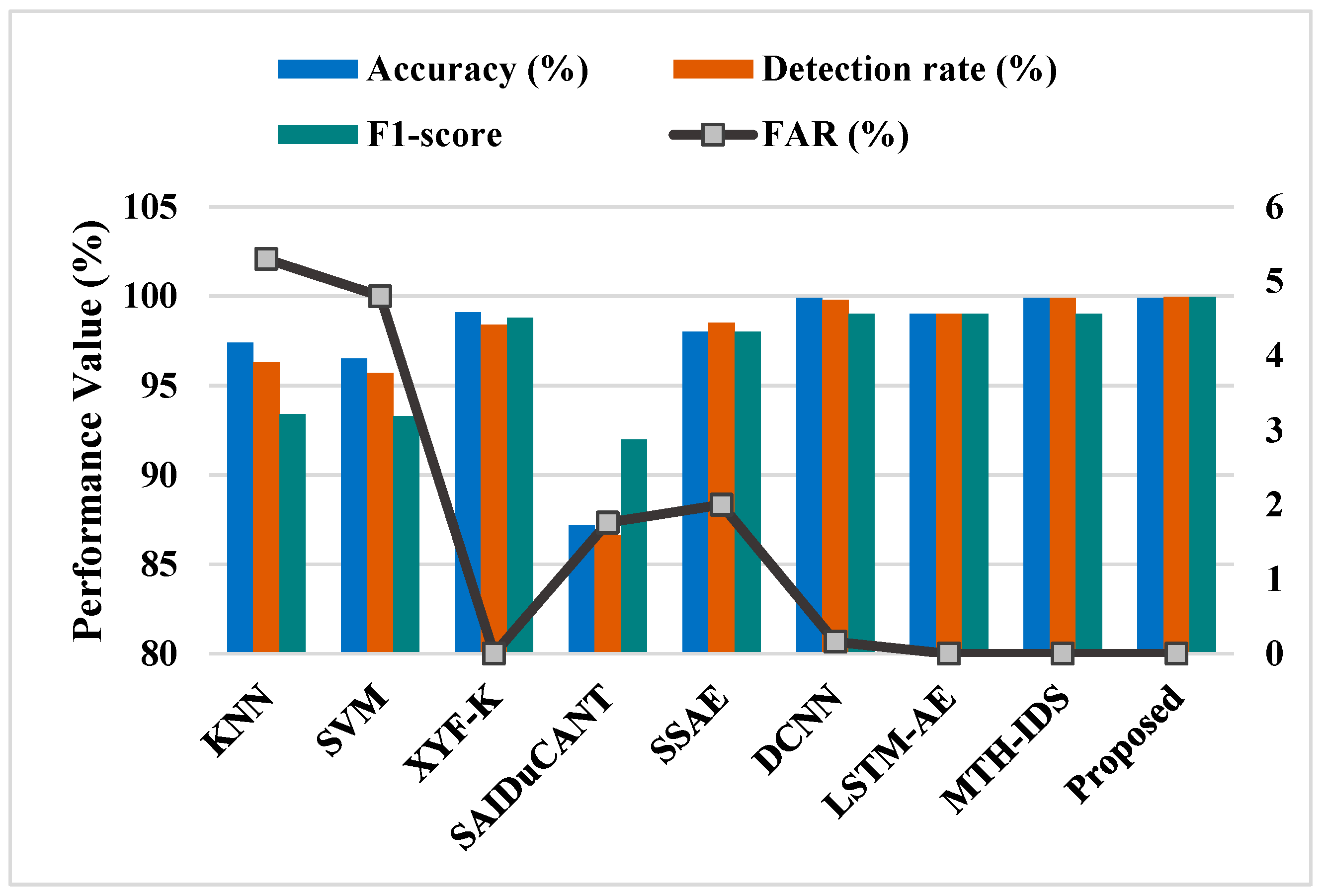
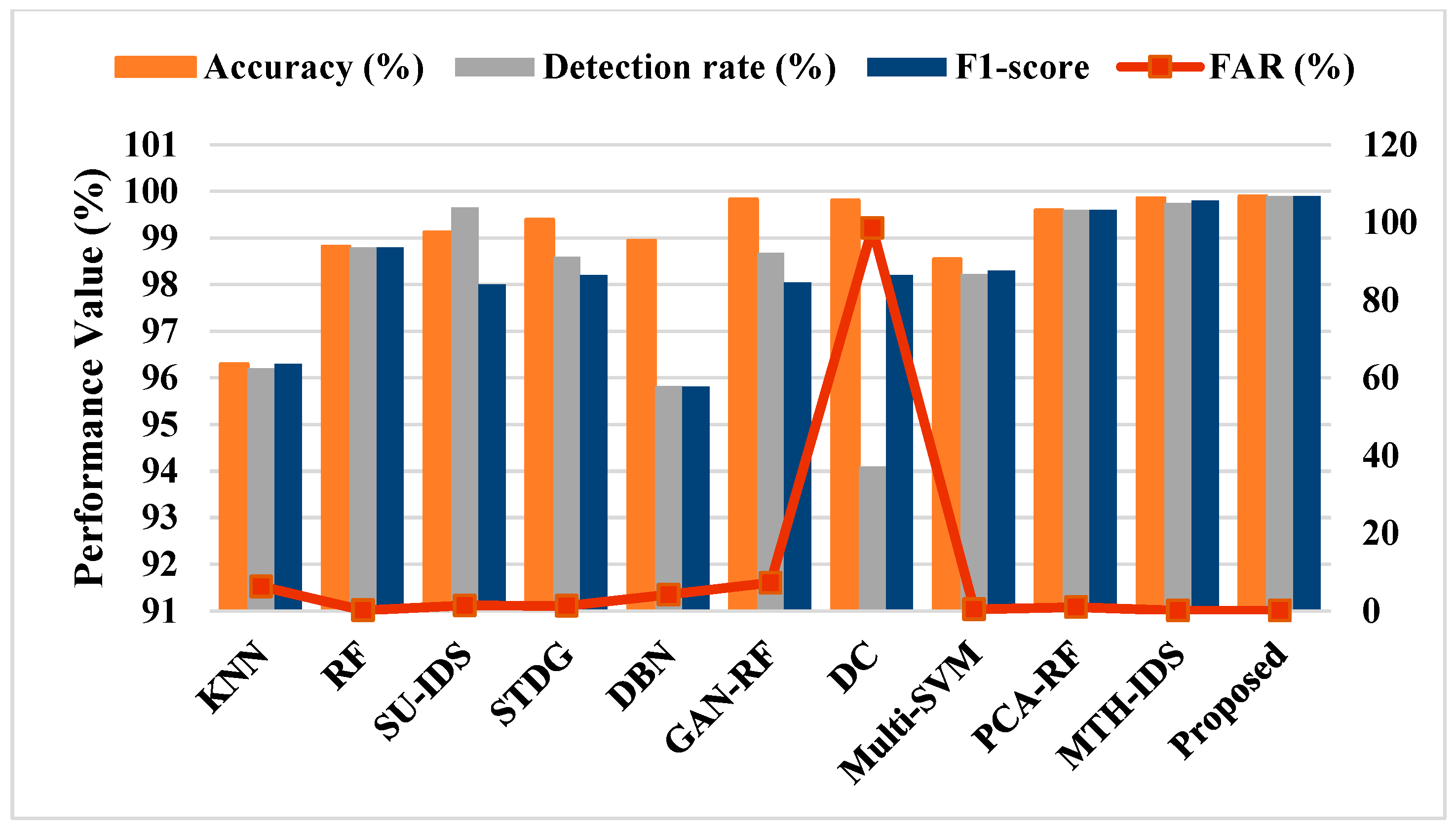
| Parameters | Descriptions |
|---|---|
| Transformed input parameter | |
| Specified range of input variables | |
| Initial range of input parameters (minimum and maximum values of the dataset) | |
| Infected individual | |
| Exposed individual | |
| Susceptible | |
| Recovered | |
| Dead | |
| Vaccinated | |
| Hospitalized | |
| Quarantined | |
| Agents can infect people | |
| Contact rate of infection | |
| Contact rate of pathogen | |
| Contact rate of deceased | |
| Contact rate of recovered | |
| Natural death rate | |
| Disease-induced death rate | |
| Recruitment rate | |
| Rate response to vaccination | |
| Z | Recovery rate |
| S | Rate of burial of deceased individual |
| V | Rate of vaccination of individual |
| Rate of quarantine | |
| K | Number of trees |
| Number of leaves | |
| M | Matrix |
| P | Regularization parameter |
| Loss function |
| Datasets | Name |
|---|---|
| Dataset 1 | NSL-KDD |
| Dataset 2 | CAN intrusion |
| Dataset 3 | CIC-IDS 2017 |
| Dataset 4 | BoT-IoT |
| Dataset 5 | DS2OS |
| Dataset 6 | UNSW-NB 15 |
| Dataset 7 | CIRA-CIC-DoHBrw-2020 |
| Methods | Precision | Recall | F1-Measure | Detection rate | FAR |
|---|---|---|---|---|---|
| LR | 78.1 | 80.1 | 79.1 | 80 | 11.50 |
| XGB | 84.5 | 83.4 | 83.9 | 83 | 9.13 |
| DT | 87.3 | 88.5 | 87.9 | 88 | 7.8 |
| HCNN | 96.3 | 97.12 | 97.6 | 97 | 2.5 |
| Proposed | 99.2 | 98.9 | 99.1 | 99.2 | 1.5 |
| Methods | Accuracy |
|---|---|
| DBN | 95 |
| DNN | 90.25 |
| DL | 95 |
| LSTM | 96.2 |
| IDS-DL | 96 |
| CNN IDS | 96 |
| HCRNN | 97.75 |
| Proposed | 99.3 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Rabie, O.B.J.; Balachandran, P.K.; Khojah, M.; Selvarajan, S. A Proficient ZESO-DRKFC Model for Smart Grid SCADA Security. Electronics 2022, 11, 4144. https://doi.org/10.3390/electronics11244144
Rabie OBJ, Balachandran PK, Khojah M, Selvarajan S. A Proficient ZESO-DRKFC Model for Smart Grid SCADA Security. Electronics. 2022; 11(24):4144. https://doi.org/10.3390/electronics11244144
Chicago/Turabian StyleRabie, Osama Bassam J., Praveen Kumar Balachandran, Mohammed Khojah, and Shitharth Selvarajan. 2022. "A Proficient ZESO-DRKFC Model for Smart Grid SCADA Security" Electronics 11, no. 24: 4144. https://doi.org/10.3390/electronics11244144
APA StyleRabie, O. B. J., Balachandran, P. K., Khojah, M., & Selvarajan, S. (2022). A Proficient ZESO-DRKFC Model for Smart Grid SCADA Security. Electronics, 11(24), 4144. https://doi.org/10.3390/electronics11244144









