1. Introduction
In today’s semiconductor industry, outsourcing has become the prevailing business model [
1]. Outsourcing and offshoring the fabrication process in particular has been a major trend for decades, due to ever-increasing manufacturing costs, leading ultimately to an increased exposure of Intellectual Property (IP) and Integrated Circuits (ICs) to external—possibly unreliable—actors. Due to this loss of control, combined with an increasing risk due to ever-growing adversarial capabilities throughout the supply chain, several threats, such as IC overproduction, counterfeiting, IP piracy and Hardware Trojan insertion, have become major sources of concern [
2].
Numerous Design-for-Trust approaches have introduced preventive mechanisms over the last years [
3]. One of the most prominent approaches against IC overproduction and IP piracy is logic locking [
4,
5]. Logic locking is based on adding key inputs into a design so that the circuit behaves as expected only in the presence of the correct secret key value. For incorrect keys, circuit’s outputs are corrupted and provide erroneous data. The correct key is programmed post-fabrication by a trusted party thereby remaining unknown to manufacturers and end-users. Therefore, logic locking helps design houses protect their IPs from untrusted entities. The first logic locking technique was proposed in 2008 [
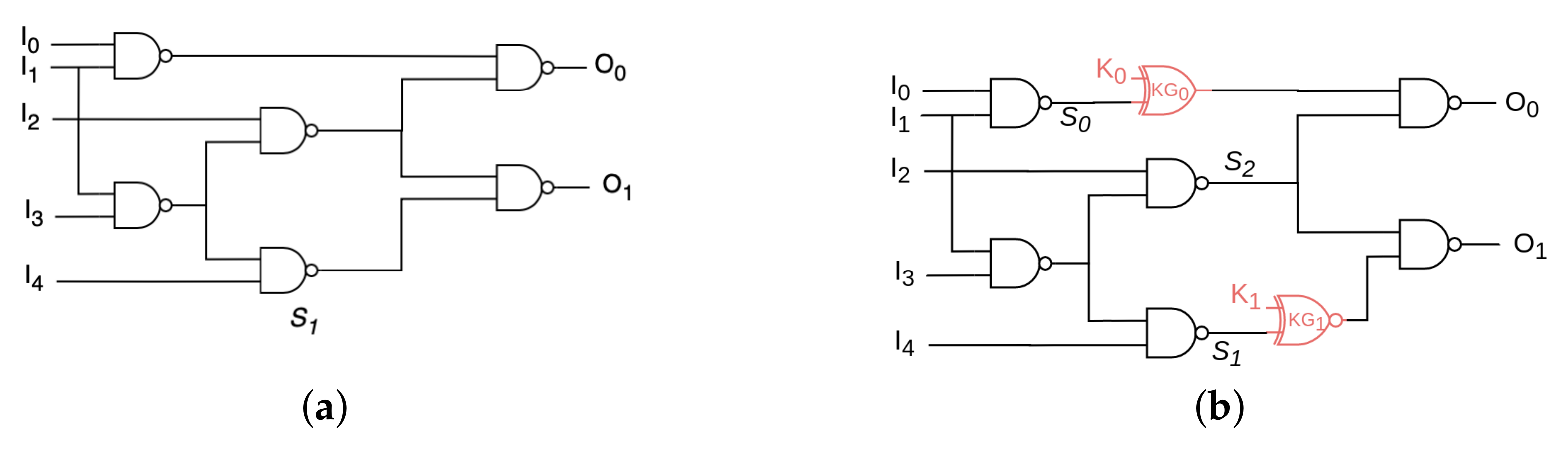
6], introducing the concept of XOR/XNOR key-gates insertion at random locations inside a design (RLL) (cf.
Figure 1). The following works proposed different types of key-gates (AND/OR gates, MUXes, LUTs, etc.) and insertion strategies [
7,
8,
9,
10,
11]. The most important insertion criterion, introduced by Fault-based Logic Locking (FLL) [
7], aims to provide sufficient errors observed at a locked circuit’ outputs, referred to as high output corruption.
However, such key-gate-based logic locking techniques have been reported to be highly susceptible to the so-called
SAT attack in 2015 [
12], which represents a milestone in the logic locking research area. This attack uses a Boolean satisfiability (SAT) solver and an unlocked circuit, referred to as the
oracle, to iteratively and efficiently prune out wrong key values. Most subsequent logic locking techniques aimed at counteracting the SAT attack, by exponentially increasing its computing time [
13,
14]. In other words, thanks to the use of a one-point function, the SAT attack could only eliminate one key value per iteration, which made it as ineffective as a brute-force attack. However, to do so, output corruption was dramatically diminished [
15], making the ICs mostly functional despite being supplied with a wrong key value. Furthermore, these Provably Secure Logic Locking (PSLL) schemes introduced an isolated block leaving structural traces allowing the identification of the block by an attacker [
16]. How to improve these PSLL schemes has been an extremely prolific field of research over the last years [
15,
17,
18,
19,
20,
21,
22,
23], aiming at reaching an acceptable trade-off between attack (both functional/SAT-based and structural-based) resilience, output corruption, and area overhead. This research has also been coupled with improvements in attacks, mimicking an extremely prolific cat and mouse game, which motivates all the more the proposal of new protection methods, while making this task even more challenging.
To address the limitations of previous schemes, we proposed SKG-Lock [
24], featuring the characteristics of causing corruption at multiple signals with different corruptibilities. In this paper, we present SKG-Lock+, which also provides high security against attacks while further improving corruption. The two main contributions of this work are as follows:
We present an improved structure of the so-called switch controller with respect to the one introduced in SKG-Lock, which further improves output corruption;
We propose a new key-gate insertion strategy , which, based on the computation of signal probabilities, allows maximizing output corruption, with a far shorter computation time than previously proposed methods.
Furthermore, we provide a thorough security analysis of SKG-Lock+ against oracle-guided attacks, proving that SKG-Lock+ achieves maximum resilience against the SAT attack regardless of different corruptibilities of the switchable key-gates, as well as its evaluation in terms of attack resilience, output corruption and overheads, along with comparisons with state-of-the-art techniques.
The rest of the paper is organized as follows.
Section 2 provides background on criteria for logic locking, SAT attack and its countermeasures, and recent works on both attacks and defenses.
Section 3 presents our proposed logic locking scheme, SKG-Lock+. Security analysis of SKG-Lock+ against state-of-the-art attacks is discussed in
Section 4. Experimental results are shown in
Section 5, in terms of computation time, output corruption, resilience against publicly available attacks and area/delay overheads. Discussions and conclusion follow in
Section 6 and
Section 7.
2. Preliminaries
2.1. Output Corruption
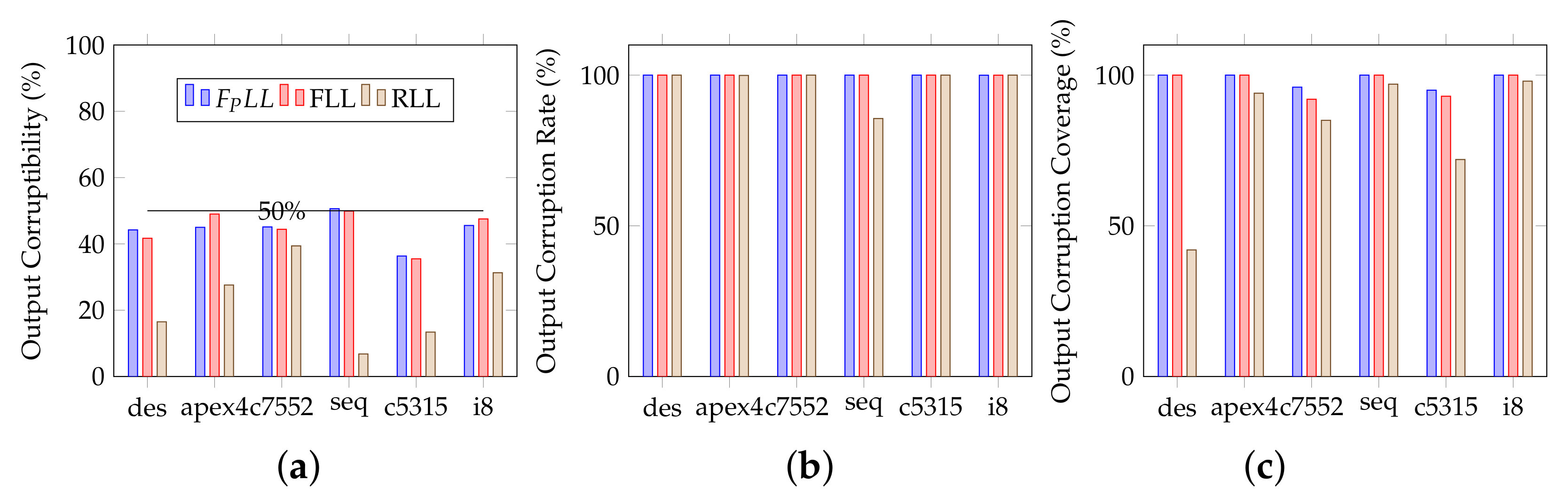
Output corruption means that a locked circuit behaves (sufficiently) erroneously upon application of any wrong key value. In order to be properly quantified, it should be further categorized into several criteria as follows.
Output corruptibility—often termed Hamming distance [
7] due to how it is computed—is estimated by the average Hamming Distance
between the outputs of a locked and an unlocked circuit. For our experimentation, we applied to a locked circuit
key values, each with
input patterns, and observed its
m-bit output
along with the output
O of the original circuit with the same input patterns, to compute the
as follows:
Output corruptibility is the original and most often used criterion to quantify output corruption. Its targeted value is 50% for maximum obscureness for an attacker. However, even a good output corruptibility may not be sufficient for preventing the usage of locked circuits. Among others, a good output corruptibility does not indeed ensure that all outputs can be impacted. In the image processing domain, for instance, a locked circuit could still be used, e.g., if the more significant bits of the output are not impacted.
Output corruption rate—also termed output error rate or error rate [
17,
25]—presents the probability of observing erroneous bit(s) at the output vector of a locked circuit. It is measured by the percentage of input patterns that lead to errors at circuit outputs when any incorrect key value is applied:
where,
Output corruption coverage presents the magnitude of corruption propagated to circuit outputs. It is characterized by the maximum number of output bits that can be corrupted, i.e., the maximum Hamming distance between the outputs on applying any wrong key and the correct key:
where,
To complement output corruptibility in a relevant way, output corruption rate (100% target) ensures that all input patterns lead to corruption and output corruption coverage (100% target) ensures that there is no output that is never corrupted.
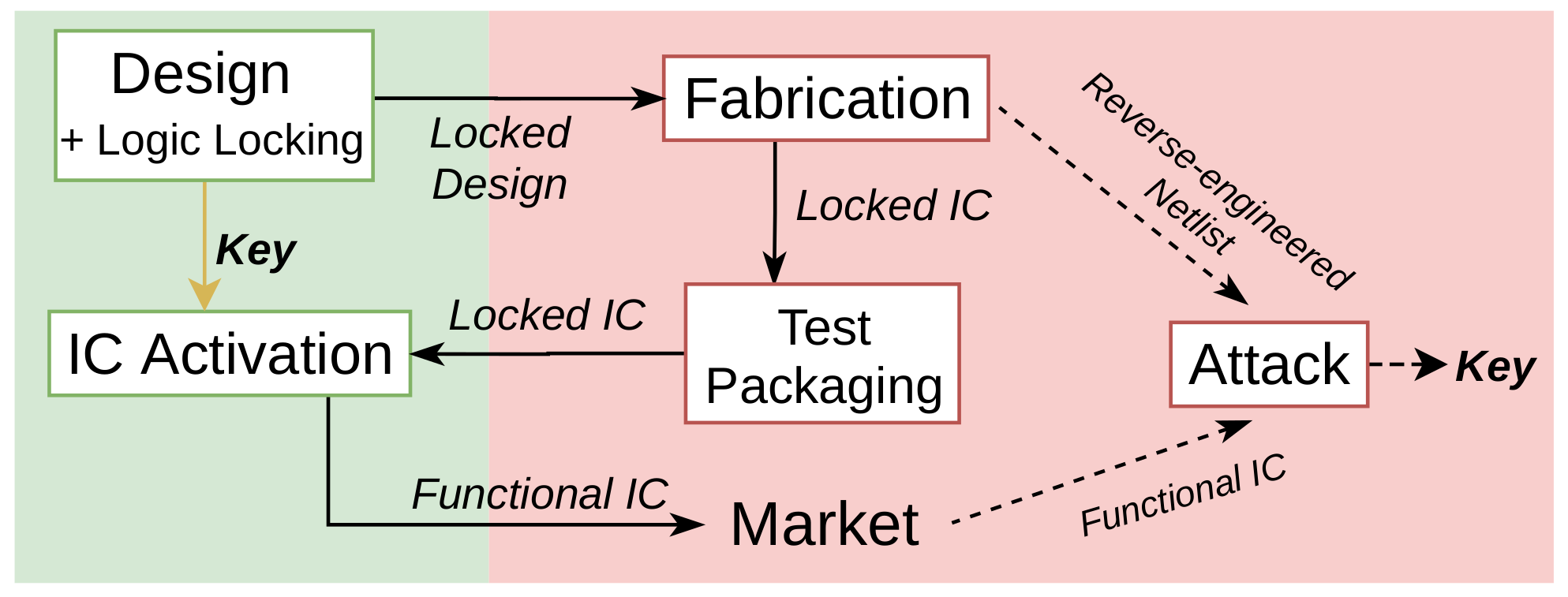
2.2. Threat Model
Logic locking aims at preventing an untrustworthy foundry from selling overproduced ICs on the black market, by rendering those inoperable, until they are properly activated. The attacker is therefore the foundry—or at least a rogue employee in the foundry—that, as a consequence, aims at unlocking the ICs/circumventing the protection (for example by finding the value of the secret key). Two types of attacks have been proposed.
Oracle-guided attacks—such as the SAT attack—whose threat model is described in
Figure 2, assume that the attacker has access to two fundamental assets:
The locked netlist, i.e., the netlist containing the logic locking structure—possibly obtained from reverse-engineering (e.g., the manufacturer can obtain it from the layout of the logic locked design);
An oracle, i.e., an unlocked IC (with accessible scan chains).
Oracle-less attacks, on the other hand, assume that the attacker does not have access to an oracle, only to the locked netlist. Structural attacks belong to this category, including removal attacks aiming to detect the protection logic to remove/disconnect it.
Note that, in this paper, we also assume that the physical security of the key—e.g., stored in a tamper-proof memory—to prevent direct access by the attacker is guaranteed. The veracity of this assumption, which may be undermined by attacks such as optical probing [
26], is out of the scope of this paper. Furthermore, one should notice that logic locking methods generate a unique global key value. Logic locking security can nevertheless be improved thanks to the individualization of the key value for each IC, by using the pre-step scheme, using process variations, provided by PUFs for example [
7].
2.3. The SAT Attack and “Post SAT” Related Works
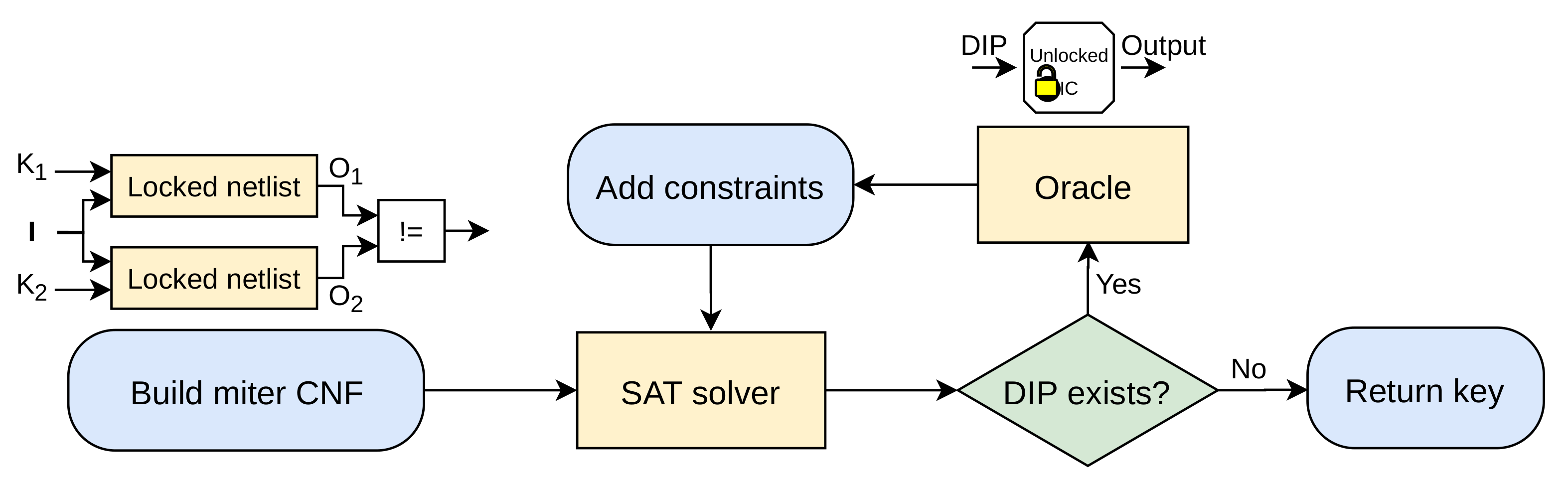
2.3.1. The SAT Attack
The SAT attack [
12] is an iterative process, as presented in
Figure 3. In each iteration, the attack finds a so-called Distinguish Input Pattern (DIP), i.e., an input pattern that results in different output values for two different key values. The DIP is then applied to the oracle to prune out the wrong key values. Note that the attack is able to prune out all key values that generate corruption for this particular input pattern—referred to as equivalent keys or keys of an equivalence class. By adding the observed disagreement between the locked netlist and the oracle as new constraints to the SAT solver, the attack reduces the key search space iteratively until no more DIP can be identified. Then, the SAT solver deduces the correct key.
This attack represents a milestone in logic locking research. Most of the methods released since 2015 attempt to be effective against this attack, alongside new attacks. Three tracks were studied to prevent the attack:
2.3.2. Provably Secure Logic Locking
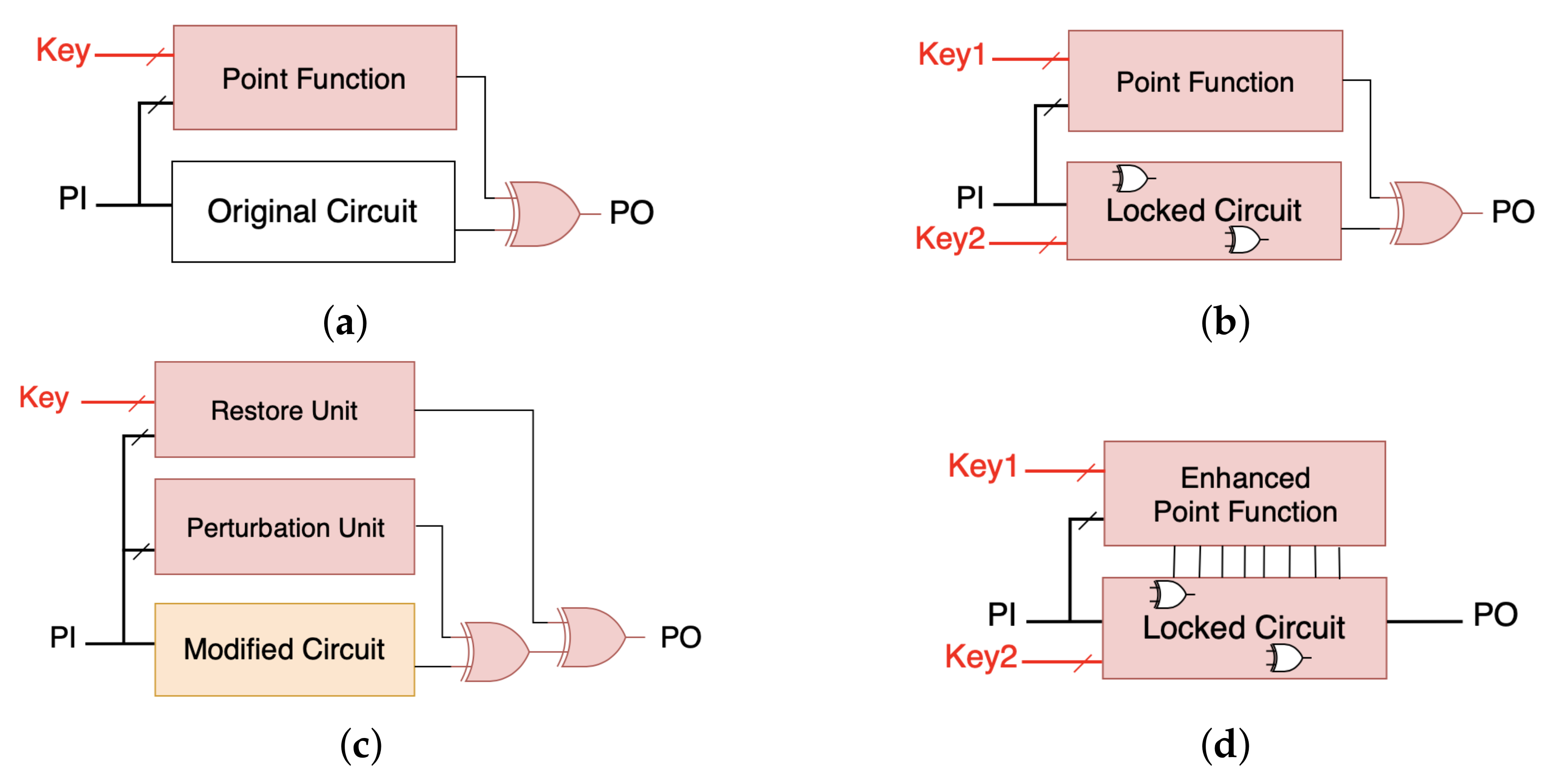
The first provable SAT countermeasures were SARLock [
13] and Anti-SAT [
14]. As already introduced, they use a point-function (i.e., a boolean function that outputs the value ‘1’ for exactly one input pattern) based structure inserted beside the circuit (cf.
Figure 4a) to maximize the number of iterations of the SAT attack to
(
n being the key size): the point-function only corrupts the circuit output for one corresponding key value per input pattern [
17]. Let us define the SAT resilience level of a logic locking technique, which is
n-secure if the number of iterations returned by the SAT attack on its locked circuits is
.
Since output corruption is dramatically low with this type of technique, a naive way to increase corruption is to insert additional key-gates beside the point-function lock [
13,
14]. In these so-called
compound schemes, the key is divided into two distinct parts (cf.
Figure 4b): the strength of the solution against the SAT attack is provided by the key bits dedicated to the SAT protection, whereas the other key bits are dedicated to the increase of the output corruption.
2.3.3. Post-SAT Attacks
Approximate attacks, notably AppSAT [
15] and Double-DIP [
38], are oracle-guided attacks that aim at finding an approximately correct key, i.e., a key value for which output corruption of the locked circuit is very low. Due to additional capabilities such as error estimation and random query reinforcement, they can avoid being trapped into solving the point-function. The Bypass attack [
39] aims to build a bypass circuit to correct the output of a circuit locked by a point-function based technique. The attack collects disagreeing input patterns of two copies of the locked circuit supplied with different wrong key values. The bypass circuit is built to correct circuit outputs for these input patterns.
Regarding compound schemes, such attacks can be used, if combined with a pre-processing step to differentiate the key bits corresponding to the key-gate insertion technique to those corresponding to the SAT protection [
40]. For example, both the SAT attack and the Bypass attack can be used on each part of the key. Fa-SAT has also been proposed [
41], which takes advantage of the fault-injection principle to aid the SAT attack tackle compound schemes. Ref. [
42] is a statistical-based attack that utilizes the variation in output corruption for different key bits to also tackle compound schemes.
Since point-function based blocks are connected to the circuit through a single signal, an attacker can aim at detecting the output of this block in order to remove it and retrieve the original design. Several oracle-less removal attacks [
43,
44] (initially dedicated to a particular protection) were proposed to exploit such vulnerabilities thanks to: (i) signal probability analysis (since the block output has exceptionally skewed probabilities), (ii) fanin analysis (since all key-inputs converge at this signal), (iii) partitioning algorithms (since the block is isolated and its size can be estimated).
2.3.4. Improved PSLL
In order to mitigate structural vulnerabilities of PSLL schemes or/and enhancing output corruption, new point-function structures have been proposed. Diversified Tree Logic (DTL) [
15] provides tunable output corruption with the modification of a few gates in the point-function based block. By replacing some of the gates in an AND tree structure with OR/AND/XOR gates, the corruptibility of the added block can indeed be increased, generating an increase in output corruption and output corruption rate. Noise-based logic locking [
21] introduces an improvement of the Anti-SAT block with non-complementary sub-blocks, which avoids a block output with probabilities skewed toward 0 or 1. By using non-complementary functions, a wide variety of structures can be implemented, less susceptible to removal attacks. CAS-Lock [
22] proposes cascaded structures for the complementary sub-blocks. Instead of an AND tree structure, the cascaded structures in this technique contain AND and OR gates. The proposed CAS-Lock block increases exponentially the complexity for an SAT attack, while providing considerable output corruption. Its output corruption is tunable by changing the location and number of AND/OR gates in the sub-blocks. G-Anti-SAT [
23] introduces a generalized approach to designing the SAT resilient logic lock. The work identifies a set of constraints for the function of each sub-block that can enable achieving maximum SAT resilience as well as non-trivial corruption. It then uses K-maps to implement such functions. A large variety of structures for sub-blocks can be realized, either complementary or non-complementary, AND tree or non-AND tree. Thus, Anti-SAT and CAS-Lock can be considered as special cases of G-Anti-SAT.
2.3.5. Corrupt-and-Correct Schemes
On the other hand, point-functions based on a Corrupt-And-Correct (CAC) scheme were also proposed, in order to mitigate structural vulnerabilities. TTLock [
45] introduced the CAC concept, in which the original circuit is transformed so that its output is flipped for one so-called protected input pattern (which is also the correct key value): a perturbation unit consisting of a comparator is added to strip the functionality of the original design, and an additional restore unit is also inserted to correct the output in the presence of a correct key value (cf.
Figure 4c). An attacker aiming at removing the added block may be able to remove the restore unit, but not the perturb unit, thus obtaining a circuit still not functioning properly. Then, the Stripped Functionality Logic Locking (SFLL) method [
17,
18,
19] generalised the concept, by e.g., allowing to choose the Hamming distance
h between the protected input patterns and the correct key (SFLL-HD) or to choose directly the
c protected input patterns (SFLL-flex). By increasing
h or
c, the output corruption can grow, however, at the cost of decreasing SAT-attack resilience and increasing the area overhead.
2.3.6. Post-PSLL/CAC Attacks
Recently, oracle-guided and oracle-less attacks have been enhanced to tackle improved PSLL and/or CAC schemes. SFLL was attacked by the removal FALL attack [
16], which manages to detect and remove its perturbation unit. CAS-lock was attacked by both an oracle-guided and an oracle-less attack in [
46]. The SPI attack [
47] is an oracle-guided and structural-based attack that exploits the properties of EDA tools to undermine CAC schemes. However, a property consisting of wisely choosing the protected input pattern(s) intrinsic to the CAC technique is also proposed by the authors to counteract the attack. The removal attack GNNUnlock+ [
48] uses a graph neural network to identify all previously proposed PSLL methods. To do so, it identifies the specific and common characteristics of signals in the different blocks and, after training, the graph neural network is able to classify which signals belong to the protection blocks.
Other types of oracle-less attacks have also been introduced. Synthesis-based attacks aim to extract the secret key by synthesizing the locked netlist upon applying constraints on key-inputs. The SCOPE attack [
49] tackles each key bit individually. For each key-input, it consists of making two circuit copies, each with logic 1 or 0 assigned to the key-input, then synthesizing and optimizing the two circuits, before comparing them using statistical analysis. The deduced key bit is the one associated with the more optimized circuit copy. Ref. [
50] prunes out incorrect keys that introduce a significant level of logic redundancy. CLIC-A [
51] is an ATPG-based attack, which exploits the use of a protected input patterns in CAC schemes.
3. Proposed Logic Locking Scheme: SKG-Lock+
In line with proposals based on improved point-function structures, which aim at increasing output corruption, we have proposed SK-Lock in [
24]. SKG-Lock+ improves on this version, as will be detailed in this section. To the best of our knowledge, these solutions are the only ones to propose an improvement of a compound scheme, making good use of the advantages of both a point-function lock and key-gate insertion (cf.
Figure 4d).
3.1. Framework
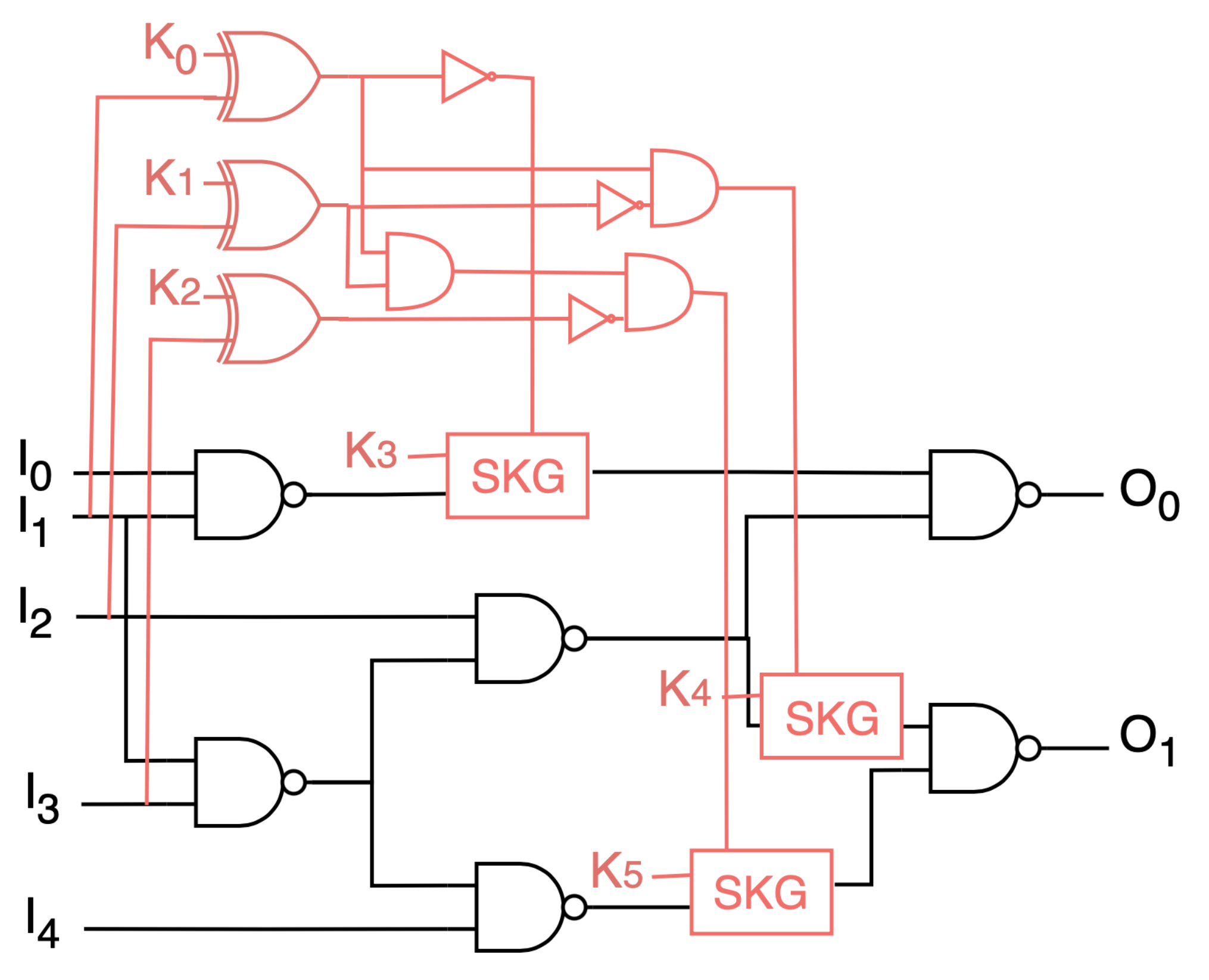
The structure of the SKG-Lock+ comprises two types of components, Switchable Key-Gates (SKGs) and a Switch Controller (SWC), as depicted in
Figure 5. Two sets of key inputs are included in SKG-Lock+, the activation key (
) and the decoy key (
):
and both come from a protected memory and are physically indistinguishable from the attacker’s point of view. In other words, they are both controllable key inputs in the locked netlist used in oracle-guided attacks.
3.2. Switchable Key-Gates
3.2.1. Structure
The structure of the SKGs is depicted in
Figure 5c. An SKG has three inputs: the signal
S from the locked circuit that is meant to be corrupted and two control signals—
and the so-called switch-signal. Compared to a traditional XOR key-gate, beside the key input, an SKG has an additional control signal. Both control signals must be asserted in order to make an SKG corrupt
S. Corruption indeed only happens when an incorrect
value is inserted and ’1’ is set on the switch-signal (in case of SKGs with positive switch; note that SKGs with negative switch can be constructed with OR and XNOR gates). As a consequence, the choice of the switch-signal allows tuning the SKGs’ ability to corrupt the circuit.
3.2.2. Insertion strategy
Since SKG-Lock+ provides security against SAT-based attacks (cf. proof in
Section 4.2), the criteria for SKG insertion strategy we chose is to maximize output corruption (One should notice that the key-gate insertion strategy is independent of the use of SKG-Lock+.
In other words, any existing insertion existing strategy can be used in the SKG-Lock+ framework.). The proposed key-gates insertion strategy based on fault analysis coming from probabilities computation consists of ranking signals in the circuit based on the co-called Output Corruption Score (OCS) to select signals for key-gate insertion.
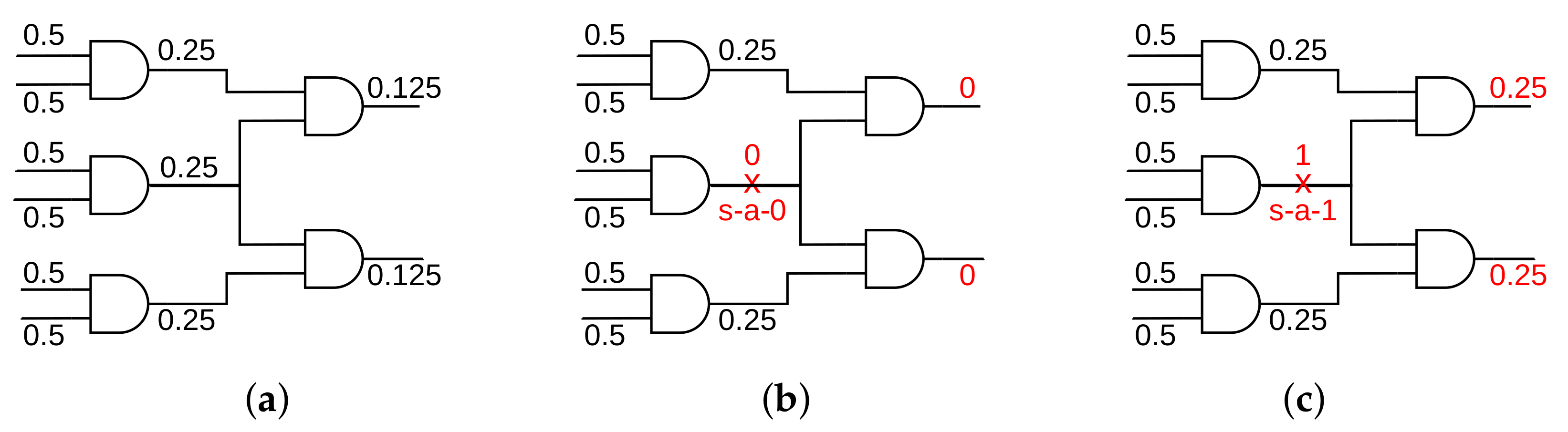
The principle of the proposed strategy is to rank every signal of the circuit according to its OCS. For each signal, this metric reflects the impact on outputs if the signal is corrupted due to an inserted key-gate. Similar to FLL, this strategy emulates the corruption by inserting stuck-at-faults (s-a-f) on signals. Applying a wrong key bit is indeed equivalent to the activation of a stuck-at-0 (s-a-0) or stuck-at-1 (s-a-1) on the corresponding corrupted signal. Then, the impact of each given fault on outputs is measured by recording the difference in the outputs’ probabilities (to be logic ‘1’ (For the rest of the chapter, we use probability of a signal to refer to its probability to be logic ‘1’.)) with and without the fault as follows (cf.
Figure 6). Calculating signals’ probabilities in a netlist consists of propagating the probability of each signal from the circuit inputs (circuit primary inputs are assigned a probability of 0.5, as well as the outputs of FFs for sequential circuits) to the circuit outputs (cf.
Figure 6a). A signal with an s-a-0 or s-a-1 changes its initial probability to 0 or 1, respectively, thereby influencing the probabilities of the signals in its fan-out (cf.
Figure 6b,c).
The calculation of the OCS for each signal consists of computing the probability of outputs. Firstly, the probability of outputs in the original circuit is measured. Then, s-a-1/0 is inserted at that signal and the probability is recomputed. By comparing the probabilities before and after the fault insertion, one obtains the total probability difference
and the number of outputs that have their probability changed
.
is the sum of absolute probability difference of each circuit output:
where
is the number of circuit outputs.
The OCS is calculated as:
Inserting key-gates at signals with high scores will impact most of the outputs for most of the input patterns, resulting in high output corruption coverage and corruption rate. One can notice that signals at circuit outputs always have an OCS of 1 since there is only one output affected and the total probability difference due to s-a-0 and s-a-1 is 1. On the other hand, internal signals with large fan-out potentially have a high OCS score and are favored by the strategy to achieve higher output corruption coverage.
Algorithm 1 describes the strategy, using key-gate insertion. The output corruption score of each signal is first calculated and signals are ranked according to their score in a descending order. After, signal selection starts from the one with the highest score. Here, an additional criterion is applied; the signals that have the same score as the previously chosen signal will not be selected for key-gate insertion. This is because signals that have the same score are structurally close to each other, such as signals connected by a buffer. Thus, selecting only one among these signals avoids series of key-gates.
The execution time of the
strategy is essentially the signal ranking step. It can be estimated as:
where
is the amount of time for calculating the output corruption score of a signal,
N is the number of signals. In comparison with FLL, which redoes the ranking each time a key-gate is inserted (cf. Equation (
9)),
only ranks signals once.
Therefore, our strategy is more scalable than FLL. Furthermore, the time of the simulation needed by FLL may be quite long. If reconvergent paths are not taken into account, the probability-based computation of
can be quite short (the version taking into account reconvergent paths takes obviously more time).
| Algorithm 1: The strategy. |
![Electronics 11 03906 i001 Electronics 11 03906 i001]() |
3.3. Switch Controller
The SWC generates the switch-signals, thereby, determining the corruptibility of each SKG. Its inputs are an key input and an equal number of circuit inputs, which can include primary inputs (PIs) and pseudo primary inputs (flip-flop outputs).
3.3.1. Original SWC
A typical design for the SWC is depicted in
Figure 5a. Its structure is a comparator, constructed with a row of XNOR gates and a cascade of AND gates. Its outputs are
n switch-signals, each of which from each signal in the AND cascade. The output at the end of the cascade
is essentially the output of a point-function between
and circuit inputs. This switch-signal has a highly skewed probability, i.e., a low activity, since it switches
the value of the connected inputs is equal to
. Therefore,
presents low corruptibility but maximal complexity for the SAT attack. The SKG connected to it is referred to as the Lowest-Corruptibility SKG (LC-SKG). Other switch-signals have a higher probability (to be logic 1); thus, SKGs driven by them have higher corruptibility, compared to LC-SKG (the corruptibility
C of each SKG is the probability of its switch-signal:
,
, etc.). Consequently, the SKG with highest corruptibility is the one driven by
. Depending on the designer’s settings, several SKGs may be driven by the same switch-signal, and/or certain switch-signals may be unused (e.g., in cases when
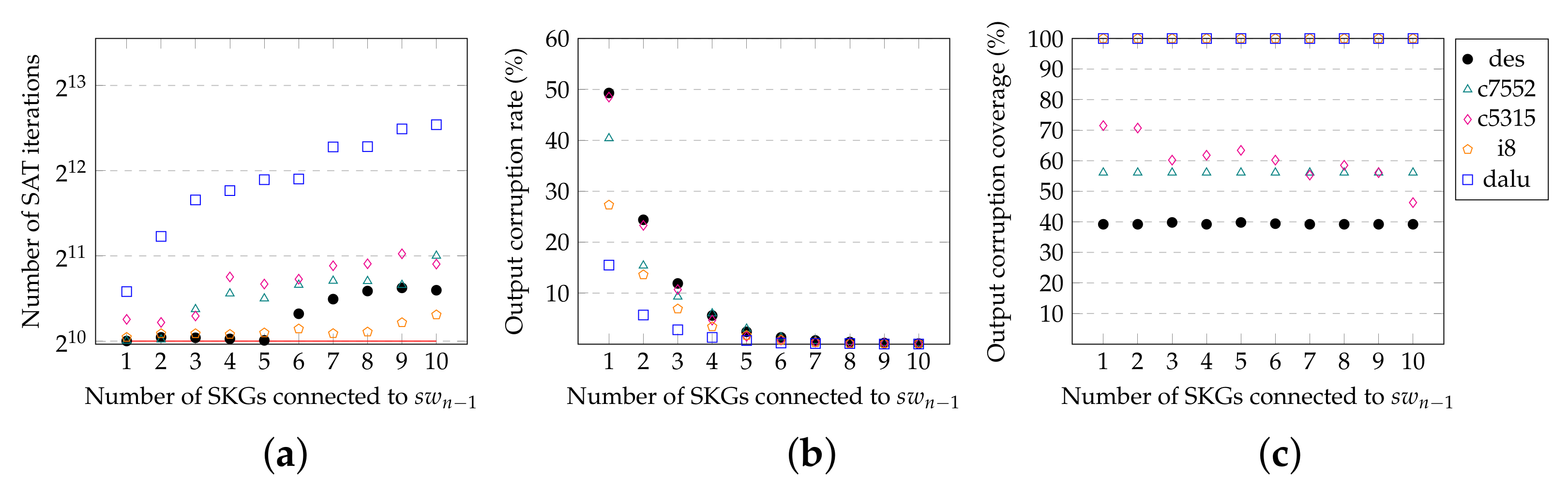
). For example, to reduce output corruption, high-probability switch-signals may be left unused, and low-probability switch-signals can be connected to more SKGs. Experimental results will detail the possible trade-off between SAT resilience and output corruption according to the choice of switch-signals mapping.
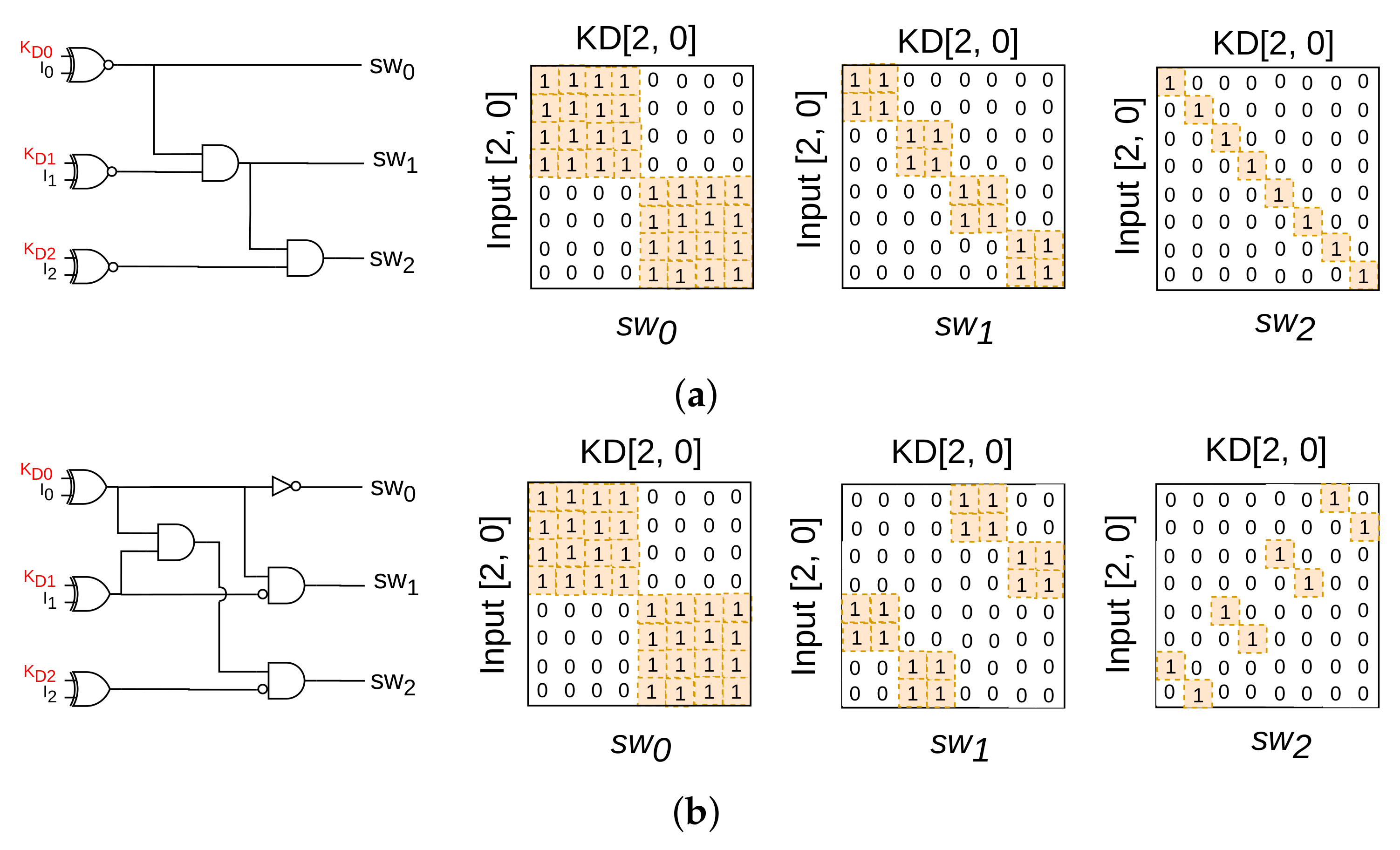
3.3.2. Improved SWC
However, with the original SWC structure presented in
Figure 5a, there is an overlap in the input patterns that activate each switch-signal, resulting in a still quite large number of input patterns for which there is no corruption. A 3-bit example of the SWC structure used in SKG-Lock is illustrated in
Figure 7a. In the corresponding switch-signals truth-tables, the rows present the primary inputs possibilities and the columns, the key values possibilities. With the original structure, due to overlap of input patterns that result in ‘1’ for each switch-signal (cf. light orange boxes in the truth tables), there can only be half of all patterns (4 out of 8) that can lead to corruption. Therefore, it is necessary to improve such an SWC structure in order to increase the number of patterns for which there can be corruption, as presented in
Figure 7b. With this improved structure, different input patterns assert different switch-signals; hence, there are 7 out of 8 patterns for which there can be corruption. In cases when all inserted KA bits are incorrect, one can expect an output corruption rate up to almost 100%.
3.4. Locking Algorithm
Algorithm 2 describes how a netlist is locked with SKG-Lock+. The designer defines:
The key sizes:
- -
The size of , hence the number of SKGs;
- -
The size of , hence the SAT-attack secure level;
A list of signals for SKG insertion (note that if the netlist already contains key-gates, the designer can easily replace them with SKGs);
A rule to map switch-signals to SKGs:
- -
Which switch-signals to use: the SAT-attack-secure level (resp. output corruption) increases with increasing number of SKGs mapped to the switch-signal with the lowest (resp. highest) switching activity;
- -
Which SKG to be mapped to which switch-signal, e.g., SKGs at strategic locations could be mapped with high-activity switch-signals to increase output corruption.
A locked netlist is then formed from the original netlist, by inserting SKGs and the SWC block, mapping circuit inputs to the SWC and switch-signals to SKGs, as depicted on a toy example in
Figure 8. Note that this insertion process is, although linear to the key size, almost instantaneous and independent of the size of the circuit. The total procedure computation time also includes the step of creating the signals list for the insertion of the SKGs, which is more time consuming than the insertion itself.
| Algorithm 2: SKG-Lock+ locking algorithm. |
![Electronics 11 03906 i002 Electronics 11 03906 i002]() |
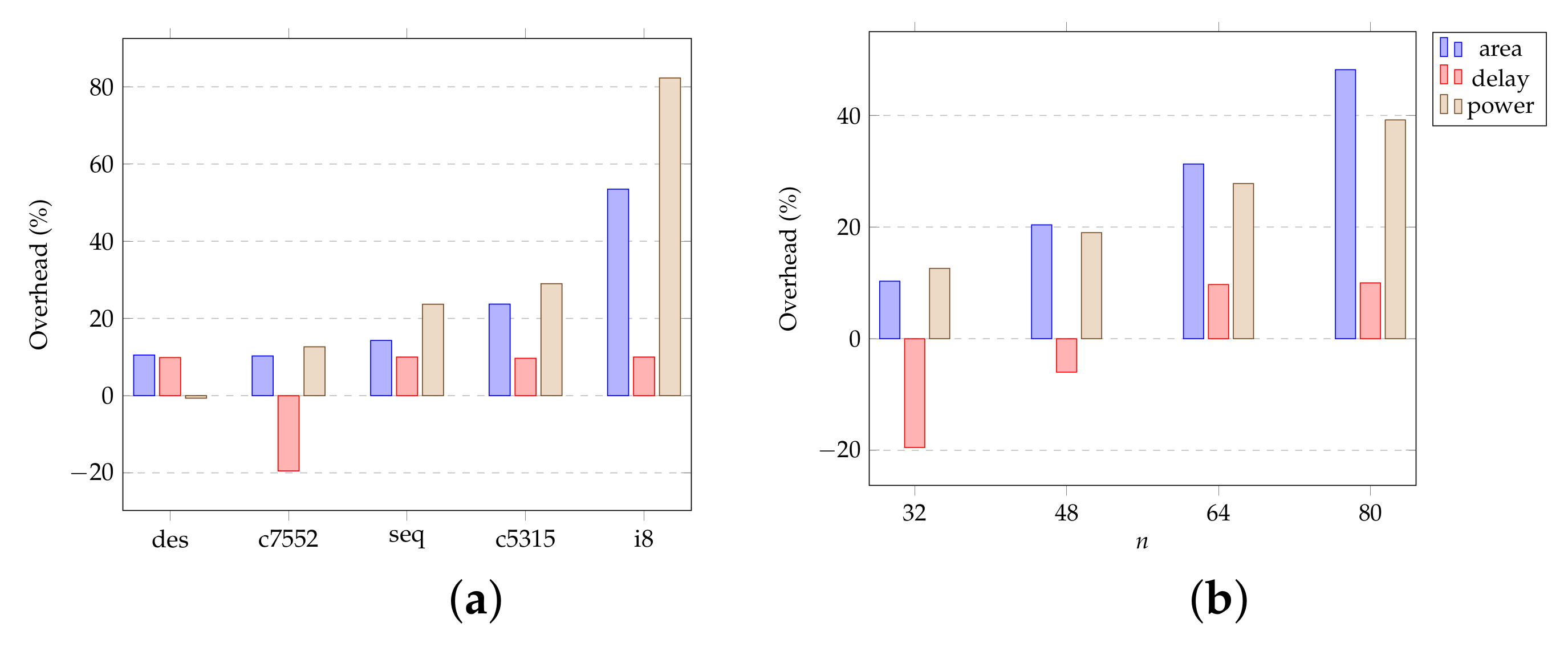
3.5. Area Overhead
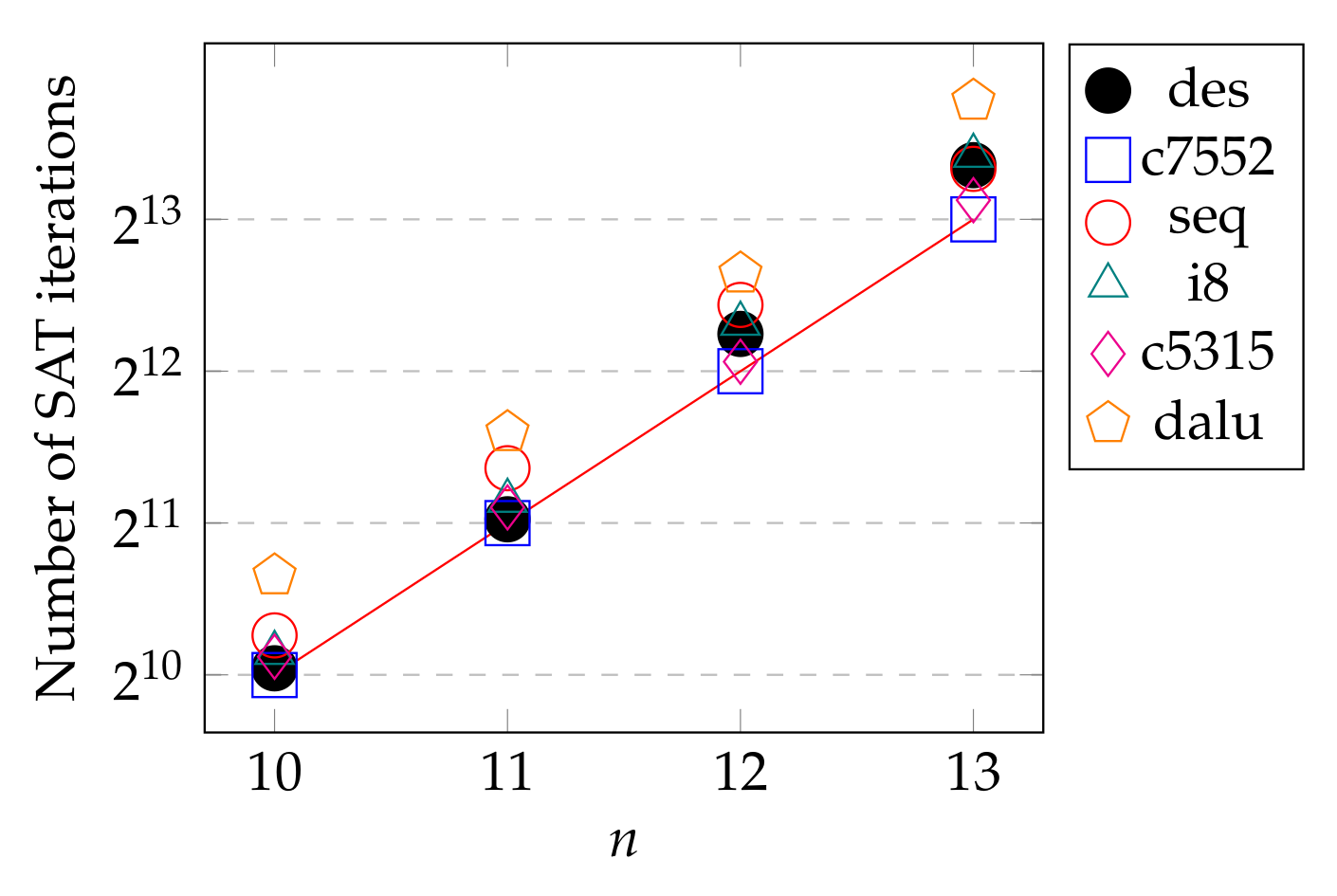
The area overhead of the SKG-Lock+ is dependant of the key size. The number of SKGs is indeed equal to the size of (each SKG generates 1 XOR/XNOR gate and 1 AND gate), and the size of the SWC is proportional to the size of . Compared to the original structure, the proposed improved SWC structure requires a little more area; for an n-bit SWC, it uses additional n-2 AND gates and its number of gates is estimated as n XOR/XNOR gates and AND gates. Additional XOR-gates are also present in case of an obfuscated SWC.
By comparison with methods of the same type, for the same SAT resilience, SKG-Lock+ has a comparable cost in area to CAS-Lock ( XOR/XNOR gates and AND/OR gates), but much less than SFLL-HD, which contains HD counters.
6. Discussion and Future Work
What about manufacturing test? Back to the threat model, with logic locking, outsourced stages (including fabricating, testing, and packaging) are completed on locked ICs, by untrustworthy offshore foundry and OSAT. The foundry fabricates silicon ICs of the locked design. The manufacturing test is performed before IC activation/on locked ICs also. This is possible since the manufacturing test, which is essentially a structural test, can be performed irrespective of circuit functionality [
57]. Furthermore, test pattern generation can be conducted without constraints on the key-bits, so the faults in the SWC of SKG-Lock+ and those on the key lines of the SKGs can be tested without any problem, the controllability of the signals in the logic cones driven by an SKG are also improved. In summary, the fault coverage is not decreased by the addition of SKG-Lock+, it can even be increased in some cases.
What about hardware Trojan horses? Considering that in the threat model considered, the foundry is the primary attacker a designer wants to protect against, it is reasonable to assume that they would also test the manufactured ICs against potential inserted hardware Trojan horses, especially those inserted especially for leaking the secret key [
58].
What about oracle-less attacks? As already explained, oracle-less attacks include removal attack and synthesis-based attacks.
Removal attacks consist of analyzing the circuit structure to detect and remove the protection. The SWC is a critical component of SKG-Lock+; if removed, all SKGs could be switched off. Structural analysis methods such as skewed-probability signal identification, circuit partitioning, and fanin analysis have been used to identify similar SAT-resistant blocks. SKG-Lock+ generates structural entanglement between the SWC and the locked circuit thanks to its multiple connections with the SKGs, in contrast to previous point-function-based techniques. Thus, a partitioning algorithm [
43] cannot be used to separate this block from the circuit. Fanin analysis [
44] is used to find the output of an obfuscated point-function block due to the convergence of all key-inputs. In SKG-Lock+, while
key-inputs are connected to the SWC,
key-inputs are connected to SKGs, which are inserted in the locked circuit. Therefore, finding the convergence points of all key-inputs leads an attacker to signals in the locked circuit rather than in the SWC. Since the SWC is based on a point function, it contains a few signals with highly skewed probabilities. XOR key-gates could be added to balance the probabilities of signals (without compromising SAT resilience).
Furthermore, one should notice that a subsequent re-synthesis step may transform the recognizable structures of both the SWC and the SKGs, and merge them with neighbor gates in the locked circuit, thereby preventing an attacker from detecting them to remove them. To corroborate this claim, we performed the following experiment. We have re-synthesized the same locked benchmark with SKG-Lock+ (on benchmarks c2670) multiple times, using different optimization parameters and delay constraints. We obtained 521 different re-synthesized netlists, for which we observed the types of the gates connected to
and
bits. These preliminary results are summarized in
Table 6. As one can see,
key bits, initially only connected to AND gates or inverters, are now also connected to OR gates mainly. Even more interesting,
key bits, initially connected to XNOR gates, are now connected mainly to inverters, AND and OR gates. These preliminary results confirm that a re-synthesis step should prevent an attacker from distinguishing the SWC and
from
bits.
More experiments are nevertheless needed, especially since re-synthesis has recently been attacked, to some extent, by SAIL [
59] (also combined with functional analysis [
60]), SnapShot [
61], and OMLA [
62], which rely on machine learning model to retrieve the—small, localized and predictable—structural changes induced by re-synthesis. These attacks are nevertheless currently only dedicated to key-gate-based logic locking methods.
SKGLock+ should also be secure against the FALL and CLIC-A attacks [
16,
51] since it does not rely on a protected input pattern, which is the feature, common to TTLock and SFLL among others, that is exploited by these attacks.
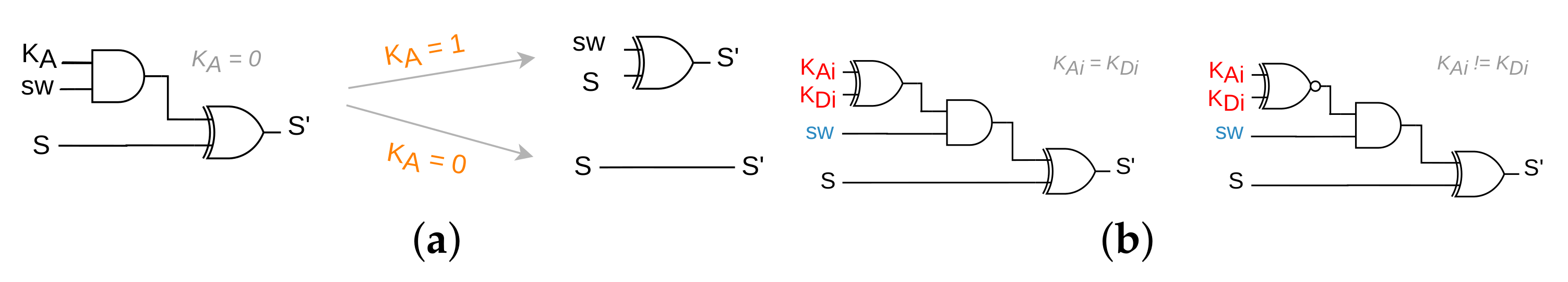
Regarding synthesis-based attacks, the SKGs structure is not secure against the SCOPE attack [
49] (cf.
Figure 14a). However, thanks to a simple countermeasure, the attack can be thwarted. As shown in
Figure 14b, thanks to an additional XOR/XNOR gate (making the SKGs to be controlled by two key-inputs, one for a
bit and the other for a
bit) assigning either value to a key-input only removes the additional XOR/XNOR gate. Therefore, it is challenging for the attack to determine which circuit copy is more optimized, hence, making it unable to recover the key bit.
In summary, SKG-Lock+ is, to some extent, secure against most oracle-less attacks. Part of our future work is to better assess SKG-Lock+ against these attacks, with also the help of the Valkyrie assessment tool [
63] to better assess potential structural vulnerabilities.
What about RTL/FSM locking? FSM/RTL locking was introduced around the same time as gate-level logic locking [
64] and has also been a very prolific subject of study to this date [
65,
66]. Among other things, it was also attacked by SAT-based attacks. A thorough comparison of SKG-Lock+ with such proposals could be of interest. Interested readers about FSM/RTL locking can refer to [
67].
7. Conclusions
In this paper, we proposed an improvement of a previously proposed logic locking technique, referred to as SKG-Lock+, for preventing locked circuit usage without requiring an unlock procedure from the designer. SKG-Lock and SKG-Lock+ based on novel switchable key-gates and a switch controller, controlled by decoy key-inputs. Futher, an improved structure of the switch-controller combined with a newly proposed key-gates insertion strategy make SKG-Lock+ superior to its preliminary version in terms of the output corruption reached.Futhermore, SKG-Lock+ is highly configurable: one can choose the exact number of key-bits dedicated to SAT protection—hence, the SAT resilience level—and those to output corruption, as well as the key-gates insertion strategy (SKG-Lock+ is easily adaptable to any strategy), and the mapping rule between its two mains components to further tune output corruption at will.
To the best of our knowledge, SKG-Lock and SKG-Lock+ are the first methods of their kind being enhanced compound structures that take advantage of the combined benefits of both a point-function and the insertion of key-gates (hence, corruption at multiple points of insertion) with intrinsic entanglement between the two.