Efficient Biomedical Signal Security Algorithm for Smart Internet of Medical Things (IoMTs) Applications
Abstract
1. Introduction
- (i)
- Proposing a new 2D chaotic system based on the existing modified logistic map and then demonstrating the chaotic behavior of the proposed system.
- (ii)
- Proposing a new security system to protect the confidentiality of electronic patient data (bio-signal records and patient personal information) in IoMTs.
- (iii)
- Implementing the proposed security system on a Raspberry Pi board to take advantage of its multiple benefits (low cost, multi-core for parallel computing, low power consumption, portability, etc.).
- (iv)
- Providing simulation and comparison results on a PC and a Raspberry Pi 4 Model B-embedded board to confirm the good robustness and the cost efficiency of the proposed system in IoMTs.
2. Preliminaries
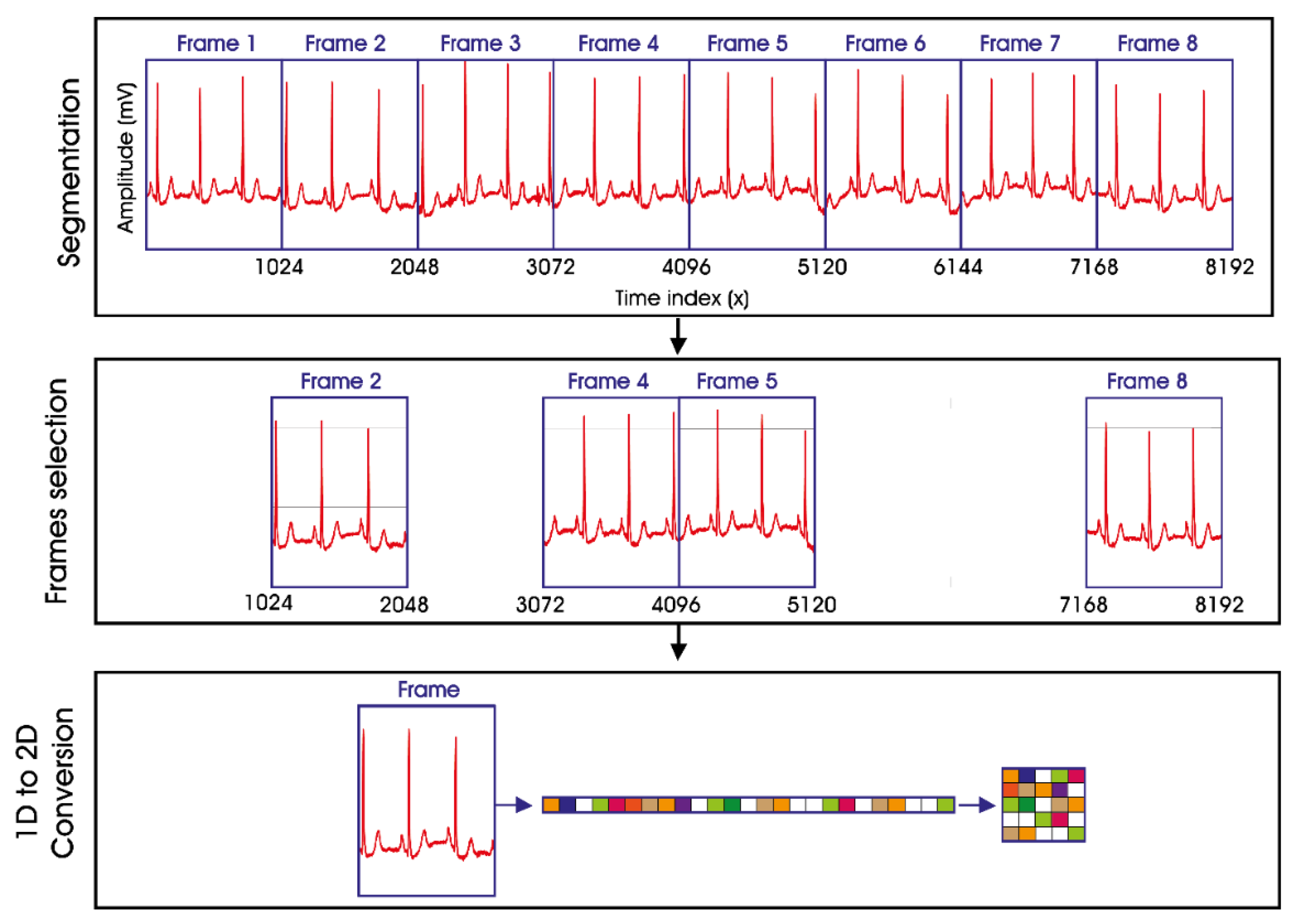
2.1. Hahn Moments
2.2. QR Code
2.3. Internet of Medical Things (IoMTs)
2.4. Modified Logistic Map
3. Proposed 2D Chaotic Sine Cosine Logistic Map
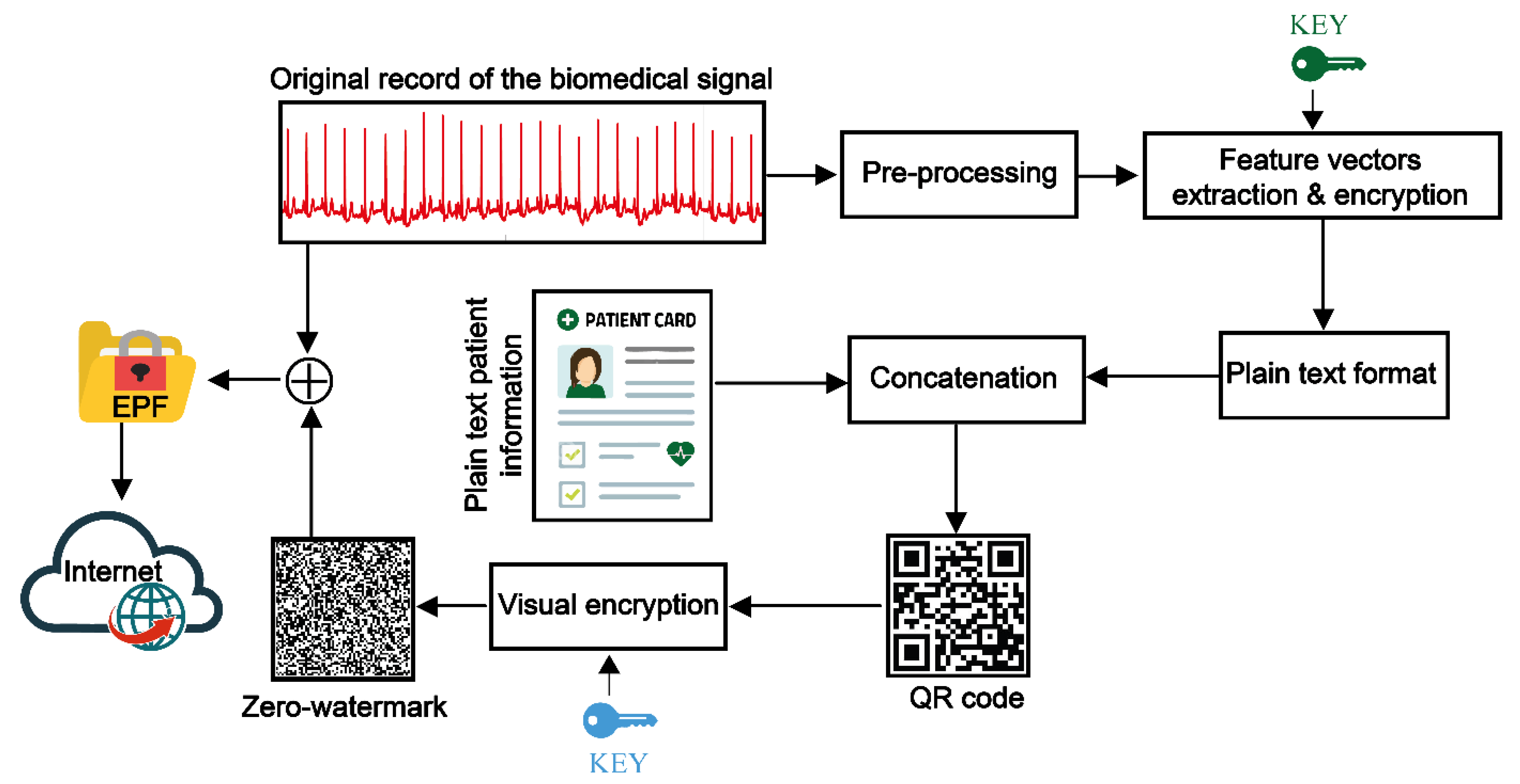
4. Proposed Security Algorithm for Patient Data in WBSN and IoMTs Applications
4.1. Pre-Processing Phase
4.2. Feature Vector Extraction and Encryption Phase
4.3. QR Code Generation
4.4. Visual Encryption of QR Code Image
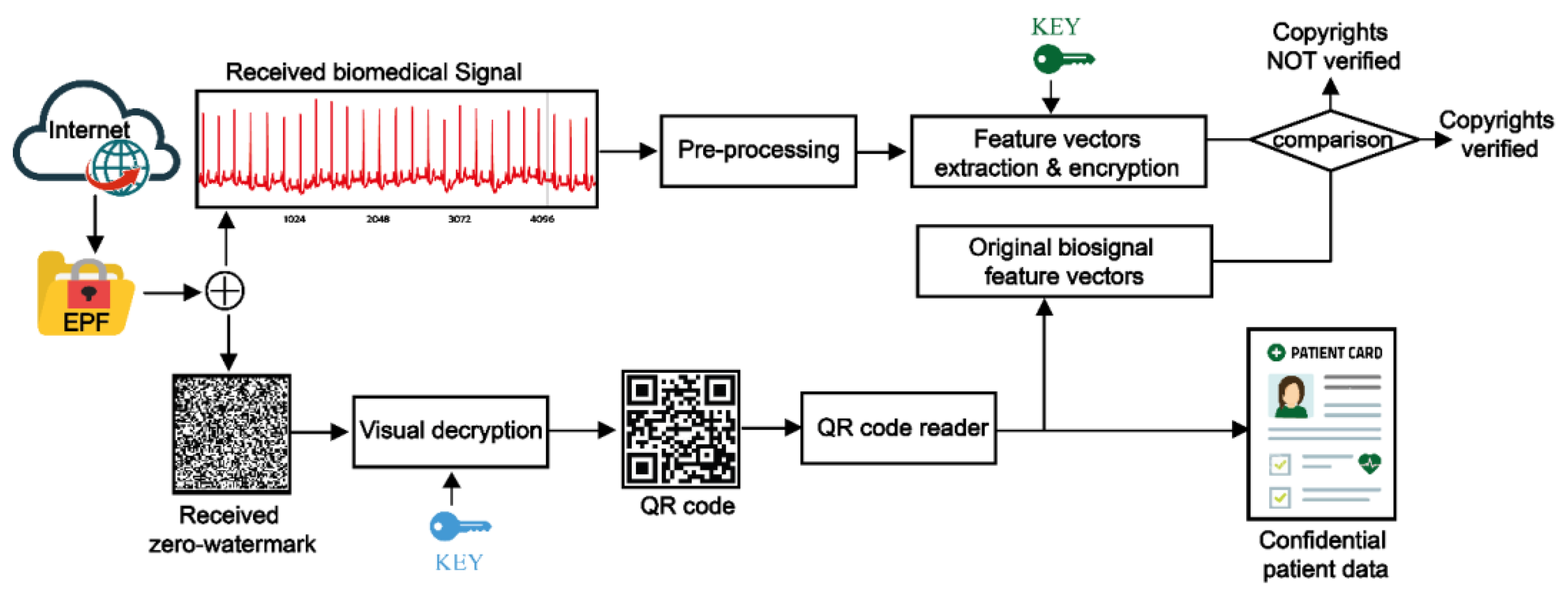
4.5. Patient Information Recovery and Copyright Verification
5. Raspberry Pi-Based Implementation of the Suggested Algorithm
5.1. Parallel Computing of the Feature Vector Extraction and Encryption
5.2. Parallel Encryption of the QR Code
- (i).
- Divide the QR code into a set of equal-sized blocks where the number of these blocks is proportional to the available CPUs.
- (ii).
- Use the method described in Section 4.4 to encrypt the QR code blocks on the available CPUs in parallel, as shown in Figure 13.
- (iii).
- Concatenate the encrypted blocks to generate the encrypted QR code.
5.3. Raspberry Pi Hardware Board
6. Simulation Results
6.1. Analysis of the Used Security Key Sensitivity and Space Size
6.2. Accuracy of the Extracted Feature Vectors
6.3. Robustness against Common Signal-Processing Effects
6.3.1. Robustness in Noisy Environments
6.3.2. Robustness against Signal Cropping
6.3.3. Robustness to Signal Compression
6.3.4. Robustness to Signal Filtering
6.4. Robustness to Geometric Attacks
6.4.1. Robustness to a Translation by Circular Shifting
6.4.2. Robustness against Signal Amplitude Scaling
6.5. Robustness Comparison with Existing Watermarking and Zero-Watermarking Schemes
6.6. Runtime Study of the Proposed Scheme on Raspberry Pi
7. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- El-Shafai, W.; El-Rabaie, S.; El-Halawany, M.M.; El-Samie, A.; Fathi, E. Encoder-independent decod-er-dependent depth-assisted error concealment algorithm for wireless 3D video communication. Multimed. Tools Appl. 2018, 77, 13145–13172. [Google Scholar] [CrossRef]
- El-Shafai, W. Pixel-level matching based multi-hypothesis error concealment modes for wireless 3D H. 264/MVC communication. 3D Res. 2015, 6, 31. [Google Scholar] [CrossRef]
- El Shafai, W.; Hrušovský, B.; El-Khamy, M.; El-Sharkawy, M. Joint space-time-view error concealment algo-rithms for 3D multi-view video. In Proceedings of the 2011 18th IEEE International Conference on Image Processing, Brussels, Belgium, 11–14 September 2011; pp. 2201–2204. [Google Scholar]
- Fatehi, F.; Jahedi, F.; Tay-Kearney, M.-L.; Kanagasingam, Y. Teleophthalmology for the elderly population: A review of the literature. Int. J. Med. Inform. 2020, 136, 104089. [Google Scholar] [CrossRef]
- Nittari, G.; Khuman, R.; Baldoni, S.; Pallotta, G.; Battineni, G.; Sirignano, A.; Amenta, F.; Ricci, G. Telemedicine Practice: Review of the Current Ethical and Legal Challenges. Telemed. e-Health 2020, 26, 1427–1437. [Google Scholar] [CrossRef]
- Zheng, Q.; Yang, M.; Yang, J.; Zhang, Q.; Zhang, X. Improvement of generalization ability of deep CNN via implicit regularization in two-stage training process. IEEE Access 2018, 6, 15844–15869. [Google Scholar] [CrossRef]
- Zhao, M.; Jha, A.; Liu, Q.; Millis, B.A.; Mahadevan-Jansen, A.; Lu, L.; Landman, B.A.; Tyska, M.J.; Huo, Y. Faster Mean-shift: GPU-accelerated clustering for cosine embedding-based cell segmentation and tracking. Med. Image Anal. 2021, 71, 102048. [Google Scholar] [CrossRef] [PubMed]
- Abdelwahab, K.M.; El-atty, A.; Saied, M.; El-Shafai, W.; El-Rabaie, S.; El-Samie, A. Efficient SVD-based audio wa-termarking technique in FRT domain. Multimed. Tools Appl. 2020, 79, 5617–5648. [Google Scholar] [CrossRef]
- Jin, B.; Cruz, L.; Gonçalves, N. Pseudo RGB-D Face Recognition. IEEE Sens. J. 2022, 22, 21780–21794. [Google Scholar] [CrossRef]
- El-Shafai, W.; El-Rabaie, S.; El-Halawany, M.; El-Samie, A. Enhancement of wireless 3d video communication using color-plus-depth error restoration algorithms and Bayesian Kalman filtering. Wirel. Pers. Commun. 2017, 97, 245–268. [Google Scholar] [CrossRef]
- Singh, S.P.; Bhatnagar, G. Perceptual hashing-based novel security framework for medical images. In Intelligent Data Security Solutions for e-Health Applications; Elsevier: Amsterdam, The Netherlands, 2020; pp. 1–20. [Google Scholar]
- El-Shafai, W. Joint adaptive pre-processing resilience and post-processing concealment schemes for 3D video transmission. 3D Res. 2015, 6, 10. [Google Scholar] [CrossRef]
- Sheikh, A.; Anderson, M.; Albala, S.; Casadei, B.; Franklin, B.D.; Richards, M.; Taylor, D.; Tibble, H.; Mossialos, E. Health information technology and digital innovation for national learning health and care systems. Lancet Digit. Health 2021, 3, e383–e396. [Google Scholar] [CrossRef] [PubMed]
- Niranjana, G.; Chatterjee, D. Security and Privacy Issues in Biomedical AI Systems and Potential Solutions. In Handbook of Artificial Intelligence in Biomedical Engineering; Apple Academic Press: Palm Bay, FL, USA, 2021; pp. 289–309. [Google Scholar]
- Subbanna, N.; Wilms, M.; Tuladhar, A.; Forkert, N.D. An analysis of the vulnerability of two common deep learning-based medical image segmentation techniques to model inversion attacks. Sensors 2021, 21, 3874. [Google Scholar] [CrossRef]
- Sharma, N.; Anand, A.; Singh, A.K. Bio-signal data sharing security through watermarking: A technical survey. Computing 2021, 103, 1883–1917. [Google Scholar] [CrossRef]
- Sharma, N.; Anand, A.; Singh, A.K.; Agrawal, A.K. Optimization based ECG watermarking in RDWT-SVD domain. Multimed. Tools Appl. 2021, 1–17. [Google Scholar] [CrossRef]
- Ali, Z.; Imran, M.; Alsulaiman, M.; Shoaib, M.; Ullah, S. Chaos-based robust method of zero-watermarking for medical signals. Future Gener. Comput. Syst. 2018, 88, 400–412. [Google Scholar] [CrossRef]
- Daoui, A.; Karmouni, H.; Sayyouri, M.; Qjidaa, H. New method for bio-signals zero-watermarking using quaternion shmaliy moments and short-time fourier transform. Multimed. Tools Appl. 2022, 81, 17369–17399. [Google Scholar] [CrossRef]
- Daoui, A.; Yamni, M.; Karmouni, H.; Sayyouri, M.; Qjidaa, H.; Ahmad, M.; Abd El-Latif, A.A. Biomedical Multimedia encryption by fractional-order Meixner polynomials map and quaternion fractional-order Meixner moments. IEEE Access 2022, 10, 102599–102617. [Google Scholar] [CrossRef]
- Lin, H.; Wang, C.; Cui, L.; Sun, Y.; Xu, C.; Yu, F. Brain-like initial-boosted hyperchaos and application in biomedical image encryption. IEEE Trans. Ind. Inform. 2022, 18, 8839–8850. [Google Scholar] [CrossRef]
- Guo, X.; Zhuang, T. Lossless watermarking for verifying the integrity of medical images with tamper localization. J. Digit. Imaging 2009, 22, 620–628. [Google Scholar] [CrossRef][Green Version]
- Daoui, A.; Yamni, M.; Karmouni, H.; Sayyouri, M.; Qjidaa, H. Biomedical Signals Reconstruction and Zero-watermarking Using Separable Fractional Order Charlier- Krawtchouk Transformation and Sine Cosine Algorithm (SCA). Signal Process. 2020, 180, 107854107854. [Google Scholar] [CrossRef]
- Mirjalili, S. SCA: A sine cosine algorithm for solving optimization problems. Knowl.-Based Syst. 2016, 96, 120–133. [Google Scholar] [CrossRef]
- Abdulbaqi, A.S.; Obaid, A.J.; Abdulameer, M.H. Smartphone-based ECG signals encryption for transmission and analyzing via IoMTs. J. Discret. Math. Sci. Cryptogr. 2021, 24, 1979–1988. [Google Scholar] [CrossRef]
- Algarni, A.D.; Soliman, N.F.; Abdallah, H.A.; Abd El-Samie, F.E. Encryption of ECG signals for telemedicine applications. Multimed. Tools Appl. 2021, 80, 10679–10703. [Google Scholar] [CrossRef]
- Qiu, H.; Qiu, M.; Lu, Z. Selective encryption on ECG data in body sensor network based on supervised machine learning. Inf. Fusion 2020, 55, 59–67. [Google Scholar] [CrossRef]
- Zhai, X.; Ait Si Ali, A.; Amira, A.; Bensaali, F. ECG encryption and identification based security solution on the Zynq SoC for connected health systems. J. Parallel Distrib. Comput. 2017, 106, 143–152. [Google Scholar] [CrossRef]
- Urquhart, L.; Sailaja, N.; McAuley, D. Realising the right to data portability for the domestic Internet of things. Pers. Ubiquitous Comput. 2018, 22, 317–332. [Google Scholar] [CrossRef]
- Zhao, X.; Kang, Z.; Liao, Q.; Zhang, Z.; Ma, M.; Zhang, Q.; Zhang, Y. Ultralight, self-powered and self-adaptive motion sensor based on triboelectric nanogenerator for perceptual layer application in Internet of things. Nano Energy 2018, 48, 312–319. [Google Scholar] [CrossRef]
- Mehmood, Y.; Ahmad, F.; Yaqoob, I.; Adnane, A.; Imran, M.; Guizani, S. Internet-of-Things-Based Smart Cities: Recent Advances and Challenges. IEEE Commun. Mag. 2017, 55, 16–24. [Google Scholar] [CrossRef]
- Qureshi, F.; Krishnan, S. Wearable Hardware Design for the Internet of Medical Things (IoMT). Sensors 2018, 18, 3812. [Google Scholar] [CrossRef] [PubMed]
- Dennis, A.K. Raspberry Pi Super Cluster; Packt Publishing Ltd.: Birmingham, UK, 2013; ISBN 978-1-78328-620-1. [Google Scholar]
- Daoui, A.; Karmouni, H.; Sayyouri, M.; Qjidaa, H. Fast and stable computation of higher-order Hahn polynomials and Hahn moment invariants for signal and image analysis. Multimed. Tools Appl. 2021, 80, 32947–32973. [Google Scholar] [CrossRef]
- Daoui, A.; Karmouni, H.; Sayyouri, M.; Qjidaa, H. Stable analysis of large-size signals and images by Racah’s discrete orthogonal moments. J. Comput. Appl. Math. 2021, 403, 113830. [Google Scholar] [CrossRef]
- QRcode.com. History of QR Code. DENSO WAVE. Available online: https://www.qrcode.com/en/history/ (accessed on 1 November 2021).
- Chen, J.-H.; Chen, W.-Y.; Chen, C.-H. Identification recovery scheme using quick response (QR) code and watermarking technique. Appl. Math. Inf. Sci. 2014, 8, 585. [Google Scholar] [CrossRef]
- Thulasidharan, P.P.; Nair, M.S. QR code based blind digital image watermarking with attack detection code. AEU Int. J. Electron. Commun. 2015, 69, 1074–1084. [Google Scholar] [CrossRef]
- Mathivanan, P.; Balaji Ganesh, A. QR code based color image cryptography for the secured transmission of ECG signal. Multimed. Tools Appl. 2019, 78, 6763–6786. [Google Scholar] [CrossRef]
- Mathivanan, P.; Ganesh, A.B.; Venkatesan, R. QR code–based ECG signal encryption/decryption algorithm. Cryptologia 2019, 43, 233–253. [Google Scholar] [CrossRef]
- Daoui, A.; Karmouni, H.; El Ogri, O.; Sayyouri, M.; Qjidaa, H. Robust image encryption and zero-watermarking scheme using SCA and modified logistic map. Expert Syst. Appl. 2022, 190, 116193. [Google Scholar] [CrossRef]
- Mohd Aman, A.H.; Hassan, W.H.; Sameen, S.; Attarbashi, Z.S.; Alizadeh, M.; Latiff, L.A. IoMT amid COVID-19 pandemic: Application, architecture, technology, and security. J. Netw. Comput. Appl. 2021, 174, 102886. [Google Scholar] [CrossRef]
- JJain, S.; Nehra, M.; Kumar, R.; Dilbaghi, N.; Hu, T.; Kumar, S.; Kaushik, A.; Li, C.-Z. Internet of medical things (IoMT)-integrated biosensors for point-of-care testing of infectious diseases. Biosens. Bioelectron. 2021, 179, 113074. [Google Scholar] [CrossRef]
- Wei, K.; Zhang, L.; Guo, Y.; Jiang, X. Health Monitoring Based on Internet of Medical Things: Architecture, Enabling Technologies, and Applications. IEEE Access 2020, 8, 27468–27478. [Google Scholar] [CrossRef]
- IEEE Std. 754-2008; IEEE Standard for Floating-Point Arithmetic. IEEE: Piscataway, NJ, USA, 2008; pp. 1–70. [CrossRef]
- Marinescu, D.C. Chapter 2—Parallel and Distributed Systems. In Cloud Computing; Marinescu, D.C., Ed.; Morgan Kaufmann: Boston, MA, USA, 2013; pp. 21–65. ISBN 978-0-12-404627-6. [Google Scholar]
- Dalcin, L.; Fang, Y.-L.L. mpi4py: Status Update After 12 Years of Development. Comput. Sci. Eng. 2021, 23, 47–54. [Google Scholar] [CrossRef]
- Banerjee, S.; Singh, G.K. Quality Guaranteed ECG Signal Compression Using Tunable-Q Wavelet Transform and Möbius Transform-Based AFD. IEEE Trans. Instrum. Meas. 2021, 70, 4008211. [Google Scholar] [CrossRef]
- De Melo Ribeiro, H.; Arnold, A.; Howard, J.P.; Shun-Shin, M.J.; Zhang, Y.; Francis, D.P.; Lim, P.B.; Whinnett, Z.; Zolgharni, M. ECG-based real-time arrhythmia monitoring using quantized deep neural networks: A feasibility study. Comput. Biol. Med. 2022, 143, 105249. [Google Scholar] [CrossRef] [PubMed]
- Pasolini, G.; Bazzi, A.; Zabini, F. A raspberry pi-based platform for signal processing education [sp education]. IEEE Signal Process. Mag. 2017, 34, 151–158. [Google Scholar] [CrossRef]
- Koshti, M.; Ganorkar, S.; Chiari, L. IoT based health monitoring system by using Raspberry Pi and ECG signal. Int. J. Innov. Res. Sci. Eng. Technol. 2016, 5, 8977–8985. [Google Scholar]
- Mhamdi, L.; Dammak, O.; Cottin, F.; Dhaou, I.B. Artificial Intelligence for Cardiac Diseases Diagnosis and Prediction Using ECG Images on Embedded Systems. Biomedicines 2022, 10, 2013. [Google Scholar] [CrossRef]
- Pardeshi, V.; Sagar, S.; Murmurwar, S.; Hage, P. Health monitoring systems using IoT and Raspberry Pi—A review. In Proceedings of the 2017 International Conference on Innovative Mechanisms for Industry Applications (ICIMIA), Bengaluru, India, 21–23 February 2017; pp. 134–137. [Google Scholar]
- Dalcín, L.; Paz, R.; Storti, M. MPI for Python. J. Parallel Distrib. Comput. 2005, 65, 1108–1115. [Google Scholar] [CrossRef]
- Buy a Raspberry Pi 4 Model B—Raspberry, Pi. Available online: https://www.raspberrypi.com/products/raspberry-pi-4-model-b/ (accessed on 14 November 2022).
- Zhang, Y.-Q.; Wang, X.-Y. A new image encryption algorithm based on non-adjacent coupled map lattices. Appl. Soft Comput. 2015, 26, 10–20. [Google Scholar] [CrossRef]
- Alvarez, G.; Li, S. Some basic cryptographic requirements for chaos-based cryptosystems. Int. J. Bifurc. Chaos 2006, 16, 2129–2151. [Google Scholar] [CrossRef]
- Goldberger, A.L.; Amaral, L.A.N.; Glass, L.; Hausdorff, J.M.; Ivanov, P.C.; Mark, R.G.; Mietus, J.E.; Moody, G.B.; Peng, C.-K.; Stanley, H.E. PhysioBank, PhysioToolkit, and PhysioNet: Components of a New Research Resource for Complex Physiologic Signals. Circulation 2000, 101, E215–E220. [Google Scholar] [CrossRef]
- Daoui, A.; Yamni, M.; Karmouni, H.; Sayyouri, M.; Qjidaa, H.; Ahmad, M.; El-Latif, A.A.A. Color Stereo Image Encryption and Local Zero-watermarking Schemes Using Octonion Hahn Moments and Modified Henon Map. J. King Saud Univ. Comput. Inf. Sci. 2022, in press. [Google Scholar] [CrossRef]
- Daoui, A.; Karmouni, H.; Sayyouri, M.; Qjidaa, H. Efficient Methods for Signal Processing Using Charlier Moments and Artificial Bee Colony Algorithm. Circuits Syst. Signal Process. 2021, 41, 166–195. [Google Scholar] [CrossRef]
- Goyal, L.M.; Mittal, M.; Kaushik, R.; Verma, A.; Kaur, I.; Roy, S.; Kim, T. Improved ECG watermarking technique using curvelet transform. Sensors 2020, 20, 2941. [Google Scholar] [CrossRef] [PubMed]
- Sanivarapu, P.V.; Rajesh, K.N.; Reddy, N.V.; Reddy, N. Patient data hiding into ECG signal using watermarking in transform domain. Phys. Eng. Sci. Med. 2020, 43, 213–226. [Google Scholar] [CrossRef]



















| Steps | Runtime in Seconds (s) |
|---|---|
| Pre-processing | 0.0710 |
| Feature vectors extraction and encryption | 1.4880 |
| Concatenation and QR code generation | 0.3800 |
| QR code encryption | 0.9820 |
| Total runtime in seconds | 2.9210 |
| Length of the Feature Vector | Conventional Serial Method | Parallel Computing Method | ETIR (%) |
|---|---|---|---|
| L = 256 | 0.1240 | 0.0325 | 73.7903 |
| L = 1024 | 0.5602 | 0.1520 | 72.8668 |
| L = 4096 | 2.1220 | 0.5810 | 72.6202 |
| L = 8100 | 2.6210 | 0.7024 | 73.2011 |
| QR Code Size | Conventional Encryption in (s) | Parallel Encryption in (s) | ETIR (%) |
|---|---|---|---|
| 0.9615 | 0.2767 | 71.2253 | |
| 1.8845 | 0.5276 | 72.0016 | |
| 2.8852 | 0.8248 | 71.4129 |
| Attacks | Proposed Scheme | Scheme [18] | Scheme [10] | Scheme [23] | Scheme [19] | Scheme [61] | Scheme [17] | Scheme [62] |
|---|---|---|---|---|---|---|---|---|
| Circular right shifting by factor k = +20 | 0.0181 | 0.0723 | 0.0953 | 0.0192 | 0.0190 | 0.0494 | 0.0236 | 0.0401 |
| Circular left shifting by factor k = −20 | 0.0179 | 0.0719 | 0.0955 | 0.0189 | 0.0191 | 0.0556 | 0.0633 | 0.0523 |
| Scaling of the amplitude by the factor | 0 | 0.1258 | 0.2369 | 0.0201 | 0.0182 | 0.1625 | 0.1409 | 0.1368 |
| Scaling of the amplitude by the factor | 0 | 0.2067 | 0.2336 | 0.0302 | 0.0201 | 0.0955 | 0.1002 | 0.0905 |
| Signal cropping in three arbitrary indices | 0 | 0.0523 | 0.0662 | 0.0255 | 0.0126 | 0.0892 | 0.0705 | 0.0806 |
| Signal compression with CR = 75% | 0.0110 | 0.0145 | 0.0136 | 0.0160 | 0.0201 | 0.0533 | 0.0602 | 0.0449 |
| Gaussian noise of strength k= 0.04 | 0.0031 | 0.0065 | 0.0082 | 0.0042 | 0.0038 | 0.0081 | 0.0056 | 0.0092 |
| Average filtering of window w = 5 | 0.0093 | 0.0102 | 0.0211 | 0.0096 | 0.0094 | 0.0105 | 0.0202 | 0.0098 |
| Gaussian noise with k = 0.06 + compression with CR = 50% + amplitude scaling by | 0.0109 | 0.0209 | 0.0311 | 0.0185 | 0.0119 | 0.0205 | 0.0198 | 0.0159 |
| Length of the Feature Vector | QR Code Size | Total Execution Time in (s) by the Sequential Method | Total Execution Time in (s) by the Parallel Method | ETIR (%) |
|---|---|---|---|---|
| L = 256 | 71.5690 | 24.1107 | 66.3258 | |
| L = 1024 | 150.0288 | 49.3229 | 67.1244 | |
| L = 4096 | 241.0704 | 82.0035 | 65.9836 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Daoui, A.; Yamni, M.; Karmouni, H.; Sayyouri, M.; Qjidaa, H.; Motahhir, S.; Jamil, O.; El-Shafai, W.; Algarni, A.D.; Soliman, N.F.; et al. Efficient Biomedical Signal Security Algorithm for Smart Internet of Medical Things (IoMTs) Applications. Electronics 2022, 11, 3867. https://doi.org/10.3390/electronics11233867
Daoui A, Yamni M, Karmouni H, Sayyouri M, Qjidaa H, Motahhir S, Jamil O, El-Shafai W, Algarni AD, Soliman NF, et al. Efficient Biomedical Signal Security Algorithm for Smart Internet of Medical Things (IoMTs) Applications. Electronics. 2022; 11(23):3867. https://doi.org/10.3390/electronics11233867
Chicago/Turabian StyleDaoui, Achraf, Mohamed Yamni, Hicham Karmouni, Mhamed Sayyouri, Hassan Qjidaa, Saad Motahhir, Ouazzani Jamil, Walid El-Shafai, Abeer D. Algarni, Naglaa F. Soliman, and et al. 2022. "Efficient Biomedical Signal Security Algorithm for Smart Internet of Medical Things (IoMTs) Applications" Electronics 11, no. 23: 3867. https://doi.org/10.3390/electronics11233867
APA StyleDaoui, A., Yamni, M., Karmouni, H., Sayyouri, M., Qjidaa, H., Motahhir, S., Jamil, O., El-Shafai, W., Algarni, A. D., Soliman, N. F., & Aly, M. H. (2022). Efficient Biomedical Signal Security Algorithm for Smart Internet of Medical Things (IoMTs) Applications. Electronics, 11(23), 3867. https://doi.org/10.3390/electronics11233867














