Abstract
SDN (Software-Defined Networking) renders network management more centralized and flexible. However, its control plane is vulnerable to attacks. By introducing dynamic heterogeneous redundancy, the amimic control plane is built to effectively solve the problems of single control points of failure, unknown backdoor vulnerabilities and static configuration. Heterogeneity is an important indicator for evaluating the security of a system. Generally speaking, the greater the heterogeneity, the higher the security. Currently, there is little research evaluating the security of the mimic control plane in SDN by quantifying the heterogeneity. To this end, this paper proposes two methods for measuring the heterogeneity, based on the biological population diversity assessment method. Firstly, the heterogeneity quantification method, i.e., method 1, is based on system complexity and difference. On this basis, another heterogeneous quantification method, i.e., method 2, is established using high order symbiosis of the vulnerabilities. The experimental results show that, compared to the known methods, the heterogeneous quantification method 1 considers more comprehensive factors and is closer to reality. The heterogeneity quantification method 2 is more instructive to quantify the security of the mimic control plane.
1. Introduction
The core ideas of SDN (Software-Defined Networking) [] are logical centralization, the separation of the control plane and the data forwarding plane. This centralized and flexible design concept helps to flat network management and make network operation and maintenance more flexible and efficient. With the widespread application of SDN, attackers gradually increase their attack methods on the control plane, resulting in poor scalability [], a single point of failure [] and other shortcomings brought by centralized management. Therefore, the security development and design of the SDN control plane has gradually attracted widespread attention in both academia and industry.
In the field of SDN controller security research, there are two main ideas: one is to carry out incremental security development, based on the characteristics of controllers; the other is to enhance the security of the control plane by introducing multi-controller technology. Research on the use of multi-controller technology to enhance the security of the control plane can be divided into three categories: fault tolerance [], moving target defense [], and mimic defense [].
By adopting diversified technologies to enhance the uncertainty and polymorphism of the system, moving target defense can reduce the exposure time of system vulnerability as much as possible and increase the difficulty of attack, thus ensuring the security of SDN [,,]. Fault tolerance takes advantage of multi-controller technology to resist failures of some controllers, thereby improving the reliability of SDN systems [,,]. Based on diversity technologies, mimic defense utilizes the dynamic, heterogeneous, redundant and negative feedback characteristics of the “Dynamic heterogeneous redundancy (DHR)” architecture to give the system endogenous security attributes. Compared to moving target defense and fault tolerance, mimic defense significantly improves the security of the system [,,].
In order to solve the security problems of the SDN control plane, mimic defense is introduced into the SDN control plane. A set of heterogeneous executors are constructed by applications, controllers, and operating systems; namely, the mimic control plane. The endogenous security attributes of the control plane are formed by the dynamic scheduling of these executors, multi-executor arbitration, and feedback of abnormal executor information. Existing studies on the security of the mimic control plane have focused on the architecture, scheduling space, timing, and algorithms based on negative feedback. Hu proposes the basic evaluation model of the MNOS (Mimic Network Operating System) and summarizes the bottleneck of mimic defense in the field of SDN. Aiming at how to evaluate security, the MNOS offers a security assessment method []. Based on the diversity of the executors, Qi et al. proposes a multi-controller security architecture, Mcad-SA [,], to prevent a flow rule modification attack in SDN. A dynamic scheduling algorithm is also proposed to evaluate the security of the mimic SDN controllers, based on security policies []. Regarding the reliability and availability of the SDN controller as the optimization goal, a heuristic genetic algorithm suitable for multiple controllers is proposed in []. In order to solve the reliability and scalability problems presented by mimic defense, the DSL scheduling algorithm is put forward in []. Compared with the random scheduling algorithm, this algorithm improves the reliability of multiple controllers. In the perspective of SDN service deployment, Li [] introduced mimic defense technology to increase the degree of heterogeneity, and on this basis, improved the scheduling algorithm and decision mechanism. However, there is little research on the heterogeneous quantification of the SDN control plane as it is difficult to evaluate the heterogeneous quantification of multi-controller failures, and the mimic architecture has problems that are difficult to evaluate in terms of security gain quantification. However, heterogeneity is one of the foundations of mimic defense. The greater the heterogeneity between the executors, the higher the security. The rationality of the quantitative evaluation of heterogeneity is closely related to the rationality of the mimic system security. Therefore, it is of great significance to study the quantitative evaluation of heterogeneity suitable for the mimic control plane in SDN.
Heterogeneity means diversity. There are currently many system diversity assessment methods, and these ideas are essentially similar: quantifying system similarity and complexity. In traditional quantification methods, Euclidean distance, Mahalanobis distance, and cosine quantification are used in low-dimensional systems. The attribute dimension of the executors for the mimic control plane in SDN is relatively high. In high-dimensional application scenarios, the effect of traditional methods is relatively poor []. Mitra et al. [] uses the method of maximum information compression index to calculate the similarity between feature values, and the definition of the relationship between its attribute values will lead to inaccurate quantification of similarity. Pincus [] proposes to use approximate entropy to determine system complexity, but the relative consistency is low, and it is impossible to quantify the difference between executors in mimic control plane. A fuzzy probability model is proposed in [], formalizing the description of hypotheses and problems and drawing conclusions for diversity validity by deduction. There are some SDN systems that can increase its heterogeneity using virtualization. CoVisor [] introduced SDN control planes that can manage a single physical network and Yang [] studied a case for SDN-based network virtualization. Liao [] proposes a distributed and efficient network hypervisor for SDN virtualization. Although, to a certain extent, the conclusions support the idea that mimic defense technology can ensure the reliability of the system by diversity of executors in a certain way, it does not give a specific quantitative evaluation method.
In the present field of mimic defense technology, some studies have attempted to use heterogeneity to quantitatively evaluate the security of mimic systems. Liu et al. [] determined the final scheduling scheme according to the similarity index, and weighed the dynamics and reliability; however, the quantification of the similarity index requires an exponential function for fitting. Zhang et al. [] takes known symbiotic vulnerabilities as the evaluation parameter, and constructs a Heterogeneity based on the Common Vulnerability (HBCV) method of mimic construction for Web servers. Compared with Shannon entropy and quadratic entropy, this method can distinguish the heterogeneity of heterogeneous systems more finely. However, there are several shortcomings: (1) Heterogeneity is assessed by known vulnerabilities, without considering the impact of potential vulnerabilities brought by code reuse on the system; (2) The quantification of heterogeneity is based on the dissimilarity of each pair of executors in the executor set. As measured by the heterogeneity of the mimic system, the heterogeneity of each pair of executors in the mimic system cannot completely determine its security, and the use of the heterogeneity model to evaluate the security of mimic system is limited.
Based on the existing heterogeneity research in the field of mimic defense technology, combined with the characteristics of the SDN control plane, this work proposes a method to quantify the heterogeneity of the mimic control plane in SDN. The main contributions and innovations are as follows:
- Based on Shannon entropy and quadratic entropy, the heterogeneous quantitative model 1 for the mimic control plane in SDN is modeled, by incorporating parameters such as symbiotic vulnerabilities and code reuse rate. Compared with the HBCV quantitative analysis method [], model 1 can better describe the code reuse rate and its impact on heterogeneity;
- The high-order symbiosis of vulnerabilities are defined, combining the high-order symbiosis of vulnerabilities and the security of the mimic system to construct a heterogeneous quantitative model 2. Compared with the quantitative analysis method of HBCV, this model can better describe the impact of higher-order vulnerabilities on the heterogeneity in scenarios with more than three executors;
- The simulation of the quantified model 2, which uses the vulnerability database data and the controller vulnerabilities in [], confirms the impact of various parameters (e.g., code reuse rate and common vulnerability ratio) on heterogeneity measurement and verifies that the proposed method is more accurate and effective compared with the scenario based on [], by taking the vulnerability distribution of the SDN control plane application scenarios into account.
The organizational structure of the paper is as follows. Section 2 describes the mimic structure of the SDN control plane and construct a mimic model of SDN. In Section 3, the heterogeneity of the quantitative method for the mimic control plane is proposed, based on the biodiversity assessment model. Section 4 verifies the effectiveness and advancement of the method proposed in this paper through simulation and experiment. Finally, our work is summarized, and future work is discussed in Section 5.
2. Mimic Model in SDN
2.1. Mimic Architecture
Cyberspace mimic defense (CMD) is a defense technology used against unknown attacks, proposed by Jiangxing Wu, an academic of the Chinese Academy of Engineering []. The theory of CMD introduces dynamics, heterogeneity and redundancy mechanisms into cyberspace to defend against cyberspace attacks. The basic architecture of DHR is shown in Figure 1, which primarily includes: an input agent, a heterogeneous executor pool, a heterogeneous component, a mimic scheduler, an online executor set and a mimic arbiter. Among them, the input agent is responsible for the distribution of the input data to the system. The distribution principle is duplication; that is, to replicate the input data into n copies and distribute them to n heterogeneous executors with different structures and functionally equivalents. Each executor is independent of each other and manipulates the input data in parallel. In addition, the respective results are summarized to the mimic arbiter, which is a voting module that employs a certain voting algorithm to generate voting results. The results indicate the status of every executor, whether the output data of the heterogeneous executors are consistent. In addition, the mimic arbiter feeds back the status to the scheduler. If the status shows that the behavior of some online executors is different to the others, these online executors must be replaced by offline executors from the heterogeneous executor pool. The selection of online executors to be replaced and offline executors to be online is performed by a specific scheduling algorithm, according to the current situation. In addition, the executors to be replaced should be cleaned and the recovery operations should be performed. Each executor in the heterogeneous executor pool is composed of elements that belong to different component sets. The different distribution of these elements in each executor results in a heterogeneous executor pool with different structures and functionally equivalent executors. The heterogeneity, dynamics, and redundancy of DHR provide the system with uncertainty in time and space, making it difficult for attackers to exploit the vulnerabilities of the system, which in turn gives the system endogenous defense characteristics and natural immunity.
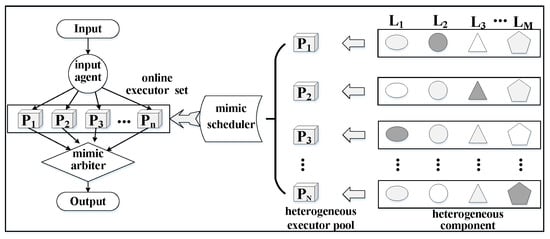
Figure 1.
The Schematic diagram of DHR structure.
2.2. Mimic Architecture in SDN
In order to solve the SDN control plane security problem, the DHR structure is introduced into the SDN control plane, which is called the mimic control plane. The architecture is shown in Figure 2. Mimic proxy is introduced to build the DHR architecture. The functions of mimic proxy include message distribution and balancing, executor resource scheduling, and redundant message voting. The heterogeneous executor pool includes all of the control plane resources, and each executor is an entity with control plane functions, including APIs, controllers, and operating systems. The heterogeneity of each executor is primarily reflected in the diversity of the above components.
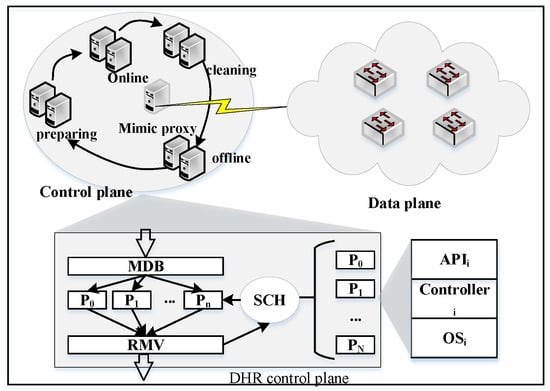
Figure 2.
The DHR architecture of control plane in SDN.
The message dispatching and balancing module (MDB) is the entry point for the data plane to send messages to the control plane, copying and distributing request messages to the equivalent heterogeneous executors. The heterogeneous and redundant controlling pool (HRCP) is the function service provider of the control and management plane, and each executor has a corresponding initial state. The redundant message voter (RMV) is responsible for the data message and executor status information exchange between the control plane and the data plane. On the one hand, the RMV judges the output results of the heterogeneous executors with equivalent functions and sends data to the data plane according to the voting algorithm; on the other hand, the RMV feeds back the inconsistent state of the output data of the executors to the scheduler (SCH). The SCH detects the running status of the executor and receives the feedback information from the RMV, and performs operations such as offline cleaning, executor synchronization, and online scheduling.
2.3. Mimic Model in SDN and Heterogeneity Analysis
As shown in Figure 2, we model the mimic control plane in SDN and analyze the working mechanism of the mimic architecture.
Definition 1 (Equivalent executor).
Equivalent executor (executor for short) refers to an entity that can independently provide control plane function services, denoted as Pi.
∃i, j ∈ {1, 2, …}, if Pi and Pj are exactly the same, that is, each executor not only has the same function but also the same structure, then Pi = Pj. On the contrary, if they have different structures, it is recorded as Pi ≠ Pj. The set of mimic control plane executors is denoted as P = {Pi|Pi is an executor, and i = 1, 2, …, n}.
When a set of heterogeneous executors encounter legal or illegal service requests from the data plane, the heterogeneity among the executors can improve the reliability and security of the mimic control plane. This section focuses on the impact of the heterogeneity of executor sets on the reliability and security of the entire control plane.
Definition 2 (Vulnerability set).
The set of all vulnerabilities in the executor Pi, denoted as VULi = {VULij|VULij is a vulnerability in the component j on the executor Pi, and j = 1, 2, …, m}.
If the VULi of Pi is the same as the VULq of Pq, then VULi = VULq; if the vulnerabilities in VULi and VULq are completely different, then VULi ≠ VULq. Otherwise, there is one or more groups that can be exploited in the same pattern, namely VULi ˄ VULq ≠ ⏀, which is recorded as VULi ⋍ VULq.
Definition 3 (Structure function of executor).
The output of the executor Pi is determined by the input excitation and the executor’s structure. The executor structure function is set as f (*).
Definition 4 (Attack process).
The attack process refers to the process in which the attacker exploits the vulnerability VULij to attack the executor Pi and generates the abnormal output of f (*), that is, f(VULij→Pi) = AOij.
In order to describe the attack situation of the mimic control plane, only the output results obtained by attacking the executor Pi by the attacker using the vulnerability VULi in the executor Pi vulnerability set VULij when the executor is attacked, including abnormal output and data for tampering, downtime, etc., the attack effect is recorded as AOij. If the attack is unsuccessful, the attack effect is recorded as Ø. If the attacker uses the vulnerability VULij to attack the executors Pi and Pq, where i ≠ q, the attack effect obtained is exactly the same, it is recorded as AOij = AOqj; if the attack effect obtained is different, it is recorded as AOij ≠ AOqj.
Definition 5 (Voting).
For an attacker that uses the vulnerability VULij to attack the executor set P, the voting process of RMV on the attack effect is recorded as farb(AO1j,AO2j, …, AOnj), and the voting result is recorded as RES, where j = 1, 2, …, m, farb(*) characterizes voting algorithms, such as majority-rule voting, maximum likelihood voting, voting by consensus, large number voting based on historical information, weighted voting, mask voting, etc. This article discusses voting algorithms based on consensus.
- In a homogeneous redundant system (redundant backup system), if all the executors in the executor set are exactly the same, then all the vulnerability sets are the same, that is, VUL1 = VUL2 = … = VULn, attacks can be launched successfully when exploiting arbitrary vulnerability of the executor, and achieve the same attack effect, that is, f(VUL1j→P1) = f(VUL2j→P2) = … = f(VULnj→Pn), AO1j = AO2j = … = AOnj, j = 1, 2, …, m, RMV vote on the output of the executor, the voting result is expressed as follows:
RES = farb(AO1j,AO2j, …, AOnj) = AOij, i = 1, 2, …, n.
Property 1.
When an attacker launches an attack on a homogeneous redundant system, the attack target is any vulnerability in the vulnerability set, which will cause the consensus voting RMV to fail, and then result in the failure or error of the entire system.
- 2.
- Assuming an ideal heterogeneous redundant system, all the executors in the executor set P are completely orthogonal, expressed as P1﬩P2﬩ … ﬩Pn. The so-called orthogonal means that there is no common vulnerability among the executors, that is {VULi˄VULj = ⏀| ∃i, j∈1, 2, …, N, and i≠j}. Therefore, an attacker can use the vulnerability to successfully attack the executor Pi, but cannot use the vulnerability to successfully attack the executor other than Pi. This case can be expressed as follows:
f(VULij→Pi) = AOij, f(VULij→Pl) = NULL, (l∈1, 2, …, N and l≠i)
RMV votes based on the attack effect, and the voting result RES can be shown as:
RES = farb(AO1j, AO2j, …, AOnj) = NULL, i = 1, 2, …, n
Property 2.
When an attacker launches an attack on an ideal heterogeneous redundant system, the attack target will not cause consensus voting failure. RMV can successfully block the attack against a single executor and ensure the normal operation of the system.
- 3.
- The ideal heterogeneous redundant system does not exist in the real environment, and the non-ideal redundant system has the symbiotic vulnerability VULcov. Assuming that VULcov exists in {P1, P2, …, Pm, and m < n}, the attacker uses the vulnerability VULip to executor set P to attack, then all executors can be attacked successfully, and the attacker obtains the same attack effect. We have
f(VULcov→P1) = f(VULcov→P2) = … = f(VULcov→Pm) = AOcov;
f(VULcov→Pm+1) = f(VULcov→Pm+2) = … = f(VULcov→Pn) = NULL.
When , according to the consensus voting algorithm, the RMV voting result is RES = farb(AO1j, AO2j, …, AOnj) = AOcov, and the attack is successful.
When , according to the consensus voting algorithm, the RMV voting result is RES = farb(AO1j, AO2j, …, AOnj) = NULL, and the attack is not successful.
In addition, in a real environment, when the attack vulnerability is a non-symbiotic vulnerability, the attack effect is the same as that of an ideal heterogeneous executor of Property 2 and cannot be successful.
Property 3.
The attacker launches an attack on a real heterogeneous redundant system. When the attack target is a symbiotic vulnerability, if the number of executors of the symbiotic vulnerability is greater than the number of other executors in the heterogeneous system, the consensus voting will fail, leading to RMV Failure and causing failure or error of the entire system; when the target of the attack is symbiotic vulnerabilities and the number of executors with symbiotic vulnerabilities is less than the number of other executors, or when the target is non-symbiotic vulnerabilities, it will not cause consensus voting failure, RMV can successfully block attacks against a single or multiple executor with symbiotic vulnerabilities and ensure the normal operation of the system.
When constructing a mimic control plane in SDN, there is no guarantee that the controller and operating system must not have symbiotic vulnerabilities, that is, the ideal heterogeneous redundant system does not exist. Therefore, only property 3 conforms to the real application scenario of the mimic control plane. The greater the heterogeneity among the executors in the system, the less likely the existence of symbiotic vulnerabilities, and the lower the probability of successfully attacking the system, that is, the higher the security of the system. Therefore, the heterogeneity can be used as one of the indicators for evaluating the safety of mimic defense systems.
The mimic control plane selects functionally equivalent heterogeneous components at the application layer, controller layer, and operating system layer to form functionally equivalent heterogeneous executors. In principle, the same executors will not be selected in engineering practice.
3. Quantitative Analysis of Heterogeneity of Mimic Control Plane
In the preceding section, we have analyzed the reasons why heterogeneity can improve the security of the mimic control, and the heterogeneity can be regarded as an indicator to quantify its security. In this section, the definition of heterogeneity is given, and two quantitative methods of heterogeneity are proposed on the basis of analyzing the existing quantitative methods.
3.1. Definition of Heterogeneity
The literature [] describes heterogeneity as complexity and difference based on biodiversity and proves and deduces this definition. Intuitively, as shown in Figure 3, there are four typical scenarios for the heterogeneity of the population. Scenario A has a single type without complexity and difference, and Scenario B has many types, but the difference is small; the difference is substantial in Scenario C, but the complexity is small; Scenario D has both complexity and difference.
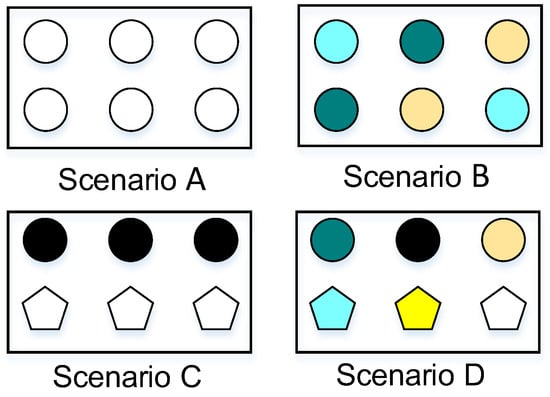
Figure 3.
Schematic diagram of heterogeneity.
Through the analysis of the mechanism of the mimic control plane in the previous section, it can be seen that the heterogeneity increases the difficulty of attacking in the mimic system and improves the security of the mimic system. However, the current mimic control plane and all of the mimic defense systems lack standardized and unified conventions and definitions for heterogeneity. Here, we learn from the research methods of biological population diversity to study the heterogeneity of the heterogeneous executors of the mimic system. On the one hand, the mimic control plane executor set is heterogeneous and redundant, and the type of executor is not unique. Therefore, when defining the heterogeneity of the mimic control plane, the complexity of the executor type must be reflected; on the other hand, the complexity of the types of executors cannot explain whether there are same vulnerabilities among the executors, it is therefore necessary to further reflect the difference in the threat of known and unknown vulnerabilities between two heterogeneous executors.
In addition, when there are no less than five executors online for operation, the difference between two executors cannot fully reflect the impact of heterogeneity on the security of the mimic system []. The high-order symbiosis of vulnerabilities can be used to define this feature. Therefore, to measure the heterogeneity of a mimic system, two indicators are needed. Heterogeneity 1 can be expressed, based on the literature [], using complexity and difference. Heterogeneity 1 of the mimic control plane is denoted as HET1, the complexity of the mimic control plane is denoted as C, and the difference of the mimic control plane is denoted as FD. Its heterogeneity, complexity, and difference have the following relationship HET1 = C × FD. As Heterogeneity 1 cannot reflect the harm of the multi-executor symbiotic vulnerabilities to the system, Heterogeneity 2 (HET2) can be used to measure the heterogeneity of the system through the high-order symbiosis (HOS) of the system vulnerabilities.
3.2. Formal Description of Executor
As the main carrier of the entire control plane, the executor set of the mimic control plane is composed of multiple heterogeneous executors. Each executor is composed of many components. The following is a further formal description of the executor set.
Definition 6 (Component set).
A set of components that implement a certain type of function of the SDN control plane system is denoted as Lk = {Lkj | j = 1, 2, …, m}. This set must cover all functional components of this type of all executors in the mimic control plane.
All of the elements in the component set must meet the requirements of functional equivalence. Components of a single executor may include an operating system and a controller. It is also possible to further subdivide the components into subfunctions of operating systems and controllers. If the controller is regarded as a type of functional equivalent, this type of component set can be defined as {ONOS, NOX, OpenDaylight, Beacon, Floodlight, Ryu, …}; if the operating system is regarded as a functional equivalent, this type of component set can be defined as {{Centos x}, {Debian x}, {Ubuntu x}, {Red Hat x}, {Windows x}, {MAC OS x}, …}, where x represents the system version.
Definition 7 (Feature matrix of executors).
The feature matrix of the executors is a matrix form that describes the mimic SDN control plane by the types and numbers of executors and components, which can be denoted as
Among them, ci1, ci2, …, cin represents the same type of components with equivalent functions, and group c1j, c2j, …, cmj represents a collection of different types of components that form a single executor. Here, each eigenvalue has no mathematical meaning, and only represents whether each component of each executor is the same. Assume that the mimic control plane consists of three heterogeneous executors. The components of Executor 1 are {OpenDaylight, ubuntu 12}T, the components of Executor 2 include {Ryu, Red Hat 7}T, and the components of Executor 3 include {Floodlight, ubuntu 12}T. Then the feature matrix is
The feature matrix has the following two properties:
Property 4.
The eigenvalues of the feature matrix C of the mimic control plane executor set are only for characterization. Therefore, arithmetic operations or matrix operations cannot be performed.
Property 5.
The feature matrix of the mimic control plane can be interchanged in any column, but row interchange is not allowed.
Definition 8 (Abundance eigenvector).
The feature vector formed by the proportion of each component of the component set in the heterogeneous executor, denoted as, we call the abundance eigenvector of the component set Lk, which represents all the same component abundances as [], the eigenvalues of the abundance eigenvectors have the following relationship
Suppose the feature matrix of the executor set is
The abundance feature vectors of its components are , , , respectively. The abundance feature vector represents the diversity of the components in the executor concentration and is the basis for evaluating the complexity of the system.
3.3. Complexity Description
In the literature [], Shannon entropy is a biological measure to evaluate species diversity. Shannon entropy can be used to evaluate the stability of biological populations. In this paper, we quantify the complexity of the executor set in the same way that biodiversity can be quantified through Shannon entropy. Here, regardless of the attacker’s factor, the complexity of the component set Lk can be expressed as
The complexity of the executor set can be expressed by the feature vector .
In the mimic control plane, s represents the number of component types, and pki is the proportion of component i in component set Lk. For the mimic control plane, in extreme cases, when there is only one component, the Shannon entropy is 0. When each component uniquely exists in each executor in the executor set, the Shannon entropy reaches the maximum value lnS. Therefore, the complexity is the highest for a certain type of component of the mimic control plane when the number of types of components is equal to the number of executors.
3.4. Difference Description
In order to evaluate the security of the mimic control plane in SDN, we describe the differences between the executors in the executor set. In terms of the description of the differences between the executors, the quantification method of quadratic entropy can be used for measurement []. The premise of quantifying the quadratic entropy is to calculate the square distance between each member of the population. Current research introduces quadratic entropy into the evaluation of system diversity. For the mimic control plane, the difference of the component set Lk can be expressed as:
Among them, represents the difference between components, which must meet the constraints: and . This parameter plays a key role in evaluating the difference; therefore, needs to be defined according to the application scenario of mimic SDN.
Starting from the original intention of evaluating the mimic control plane, the defined heterogeneity must be able to quantify the difficulty of resisting attackers to exploit vulnerabilities, and must be able to reflect the difference in vulnerabilities among components. The vulnerabilities mentioned here include known and potentially unknown vulnerabilities.
Among them, is the ratio of known vulnerabilities to all vulnerabilities (), which is called the vulnerability discovery coefficient, represents the characteristic value of known symbiotic vulnerabilities, and represents the feature value of unknown symbiotic vulnerabilities. The symbiotic vulnerabilities have been discussed in the literature []. For a single component, the programmer will leave a vulnerability on an average of 1000 to 1500 lines of code []. Parts of the symbiotic vulnerabilities may be caused by code reuse, usually characterized by code reuse rate.
In the initial stage, changes with the degree of recognition of the system, starting from 0 and increasing with time; with the recognition of components, it gradually increases, and finally approaches to 1. This change trend is similar to exponential distribution; therefore, exponential function can be used to characterize this parameter.
represents the degree of people’s awareness of the component over time, and this function changes slowly over time
The known symbiotic vulnerability feature value , can be evaluated according to the degree of vulnerability based on NVD database and CVSS standard []. CVSS establishes a standard for measuring the severity of vulnerabilities based on a series of dimensions. The scoring range of vulnerabilities is 0–10. The higher the score, the greater the damage of the vulnerability.
Among them, t represents the vulnerability of a single component, uses the CVSS score of each symbiotic vulnerability of component i and j for quantification, and are quantized, respectively, by the CVSS score of vulnerabilities of the component i and j. The component differences are characterized by according to the CVSS score of each known vulnerability. If components i and j have the same vulnerabilities, = 1; otherwise, the components i and j are completely heterogeneous, = 0.
Executor difference is used to characterize the difference between executors by quantifying the characterization of unknown vulnerabilities and symbiotic vulnerabilities. When there is only one component set of a certain type of executor, = 0, and takes the minimum value; with the increase in , the difference of executor set increases gradually. When there is only one type of multiple types of components in the executor, the quadratic entropy degenerates to the Simpson index, and takes the maximum value (1-1/S).
3.5. Quantification of Heterogeneity 1
Considering the complexity and difference, the Heterogeneity 1 (HET1) of the executor set of the mimic control plane can be calculated by the heterogeneity of the component set Lk of the M-type executor set, the formula is as follows:
Property 6.
If the executors of an executor set satisfy , the heterogeneity of the executor set reaches the minimum value HET1min = 0; if are satisfied, any two components of the same kind of the executor set are set. If is satisfied, the heterogeneity of the executor set reaches the maximum value, the formula is as follows:
In this paper, the quantification of Heterogeneity 1 is based on quadratic entropy, which is similar to the application scenario of reference []; therefore, the proof of this formula will not be repeated here.
Heterogeneous redundant executors are selected based on the complexity and difference among the candidate executors and their components, so that the heterogeneity of the executors is maximized. Ideally, the relationship among the heterogeneity of the mimic control plane and the types of components (i.e., S) and the number of executors (i.e., M) is shown in Figure 4.
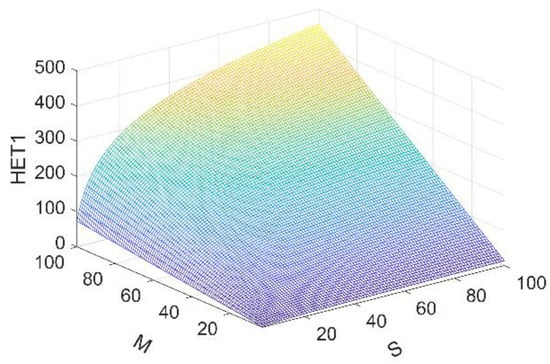
Figure 4.
HET1max of the mimic control plane.
3.6. Quantification of Heterogeneity 2
The quantification of Heterogeneity 1 takes into account the complexity and differentiation between two executors, and to a certain extent, reflects the degree of heterogeneity of the mimic system []. However, considering the DHR characteristics of the mimic SDN, the difference between two executors cannot directly reflect the security situation of the system when more than two executors in the mimic control plane have symbiotic vulnerabilities. Therefore, here we define another quantitative indicator of system heterogeneity based on the high-order symbiosis of vulnerabilities: HET2.
Definition 9 (High-order Symbiosis of Vulnerabilities).
When there are vulnerabilities in different executors in the executor set that can result in the same attack effect, and the number of executors that meet this situation is m, it is said that such vulnerabilities have m’th-order symbiosis. When m ≥ 3, it is collectively referred to as high-order symbiosis of vulnerabilities.
On one hand, high-order symbiosis vulnerabilities depend on the common vulnerabilities of different components. On the other hand, they also depend on whether different executors contain the same components. If no less than three executors contain the same components, their corresponding vulnerabilities are transformed into high-order symbiotic vulnerabilities.
For example, as shown in Figure 5, it is assumed that there are three equivalent heterogeneous executors: P1, P2, P3. Each executor contains several functions, and each function may or may not have vulnerabilities, represented by the shaded rectangle and pure rectangle, respectively. The functions with vulnerabilities are different for each executor. The vulnerabilities in each executor are shown in Figure 5. The executor can be compared to a chromosome, and resources with vulnerabilities and those without vulnerabilities can be compared to two kinds of gene fragments. Assuming that P1, P2, and P3 all have four vulnerabilities, the gene fragments corresponding to the vulnerabilities are different. There are two high-order symbiotic vulnerabilities in Scenario 1, and there is no high-order symbiotic vulnerability in Scenario 2. In both cases, if the number of executors in the executor set is greater than five, theoretically, Scenario 1 has a risk of being attacked, while Scenario 2 has no risk of being attacked. However, if measured according to the above-mentioned quantitative indicators of the complexity and difference of the executor, the heterogeneity of the two scenarios is equal.
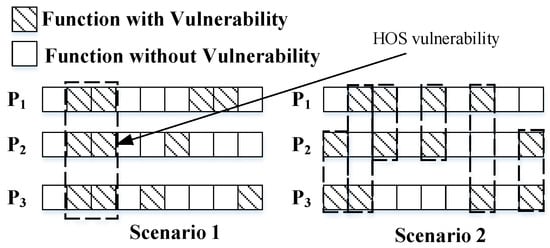
Figure 5.
Schematic diagram of high-order symbiosis of vulnerabilities.
The reason for this is that the quantification process of isomerism 1 only considers the performance of the heterogeneous executors in the isomer concentration. According to the voting properties of the mimic control plane, when the number of online executors is (2f + 1), it will cause the vote to fail if more than m (m ≥ f) executors have the same output result due to symbiotic vulnerabilities. The attack will be successful. Therefore, it is necessary to consider the impact of high-order symbiotic vulnerabilities on heterogeneity. For m executors, the mathematical expression of the m’th order symbiotic of the vulnerability, the heterogeneity quantification 2, is as follows:
Among them, t represents the vulnerability of a single component; represents the total CVSS score for symbiotic vulnerabilities of component k in m executors; represents the total CVSS score for the vulnerabilities of component k in executor i. In the extreme case, if component k in m executors are exactly the same, then ; otherwise, the m’th-order symbiotic vulnerability is 0, . We can obtain the symbiosis evaluation expression of m high-order symbiotic vulnerabilities of n executors with component k:
We select m executors from n executors to form the executor groups. In formula (9), j stands for the number of the executor groups. represents the total number of executor groups, and , m ≥ 2.
The m’th-order symbiosis of vulnerabilities in all the components of the executors, HOS, can be expressed as:
Among them, represents the proportion of the component i in the total number of vulnerabilities of this type of component in all executors.
According to formulas (8)–(10):
When the overall vulnerabilities of various components of the executors are fixed, the more high-order symbiotic vulnerabilities, the bigger the HOS. The more vulnerabilities the attacker can exploit, the lower the system security.
Therefore, the ratio of non-symbiotic vulnerabilities to total vulnerabilities can be used to characterize HET2, which can be obtained by formulas (8)–(11):
In addition, the larger the HET2 and the smaller the HOS, the less likely the system will be successfully attacked. Assuming that the probability of the system being successfully attacked is Pe and the system security is A, then A∝1/Pe. Therefore, HET2 has following properties:
Property 7.
When the overall vulnerability of the mimic control plane is certain, HET2 is negatively related to the probability of the system being successfully attacked, and positively related to the security of the system, denoted as HET2∝1/Pe, HET2∝A.
When the number of online executors is (2f + 1), the m’th-order (m ≥ f) symbiosis of vulnerabilities becomes a key factor in the security of the mimic control plane. When the number of online executors on the mimic control plane changes, the security of the system needs to be re-evaluated according to the quantitative index HET2 of the heterogeneity of the online executors.
4. Simulation and Experimental Evaluation Analysis
MATLAB R2016a is taken as the simulation platform for evaluating heterogeneity indicators HET1 and HET2. We evaluate the influence of the executor feature (for example, number of executors, vulnerability distribution, high-order symbiosis of vulnerabilities, etc.) on two quantitative indicators. In addition, an example of a mimic control plane is built in the virtual machine VMWare environment to evaluate heterogeneity. The vulnerability information of the operating system and controller is collected and obtained from literature [] and literature [].
4.1. Evaluation of HET1
According to the analysis above, there are many factors that affect HET1, including the type and number of executor components, symbiotic vulnerability ratio, code reuse rate, and vulnerability discovery coefficient. It should be noted that every factor has a default value, respectively, in order to simplify the analysis. The following is a brief analysis of the factors affecting heterogeneity in the simulation:
- The type and number of executor components are the functional entities of the mimic control plane, as described in this work. In the simulation, the component type and the number of executors is set to the same value in order to facilitate analysis. Considering the cost of resources and performance, less than 10 mimic control plane scenarios are evaluated in default.
- The symbiotic vulnerability ratio refers to the ratio of symbiotic vulnerabilities of different executors to all online executors’ vulnerabilities, which reflects the distribution of symbiotic vulnerabilities of executors. In the simulation, the symbiotic vulnerability ratio between each executor is set to the same value in default, which is set to 0.1.
- The code reuse rate refers to the code reuse ratio of different executors, which reflects the distribution of the symbiotic vulnerabilities of the executors. The evaluation method of the code reuse rate for specific control plane can be referred to in the literature []. In the simulation, the symbiotic vulnerability ratio between each executor is set to the same value, which is set to 0.2 in default.
- The vulnerability discovery coefficient (α) reflects the ratio between the known vulnerabilities of the executor and all the vulnerabilities that may exist, including unknown vulnerabilities. It is calculated according to Formula (4). As time goes on, the coefficient gradually becomes larger until approaches to 1. In the current simulation, the value is set to 0.6 in default.
As shown in Figure 6a, in order to compare with the HBCV algorithm in [], the existing common vulnerabilities are not considered. It can be seen from the figure that the reference literature evaluates the ideal heterogeneous executor, and its heterogeneity reaches the maximum. HET1 is less than the heterogeneity of HBCV. The reason for this is that the evaluation criteria of this article consider the possibility of unknown vulnerabilities caused by code reuse. That is, when there are no symbiotic vulnerabilities in heterogeneous executors, unknown vulnerabilities may be introduced due to code reuse. HET1, in this article, can better reflect the true heterogeneity.
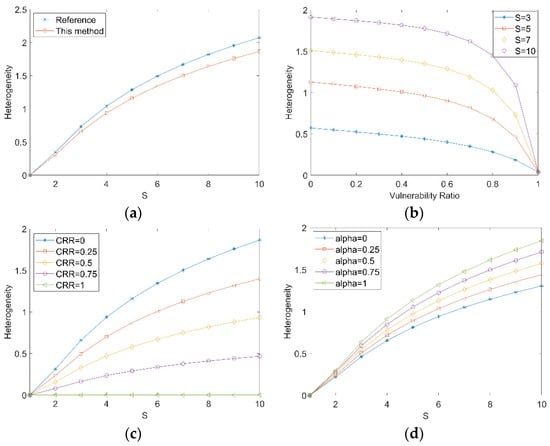
Figure 6.
HET1 of the mimic control plane. (a) Comparison of HET1 and HBCV; (b)The impact of symbiotic vulnerability ratio; (c) The impact of the number of executors; (d) The impact of the vulnerability discovery coefficient.
As shown in Figure 6b, when the symbiotic vulnerability ratio is 0, the heterogeneity is the largest; when the symbiotic vulnerability ratio is 1, the heterogeneity is the smallest in the current cognitive situation.
As shown in Figure 6c, the greater the degree of the code reuse rate (CRR), the lower the heterogeneity. When the code reuse rate is 1, it is equivalent to a homogeneous system, and the heterogeneity is 0; when the code reuse is 0, the heterogeneity is higher than other situations.
As shown in Figure 6d, with the increase in heterogeneous executors, the heterogeneity of the mimic control plane gradually increases. When the heterogeneity is equal to 1, there is no symbiotic vulnerability. In this situation, the heterogeneity is maximized. In the case of equal executors, with the recognition of code reuse, heterogeneity is reduced. This is because code reuse may lead to symbiotic vulnerabilities, which reduce the heterogeneity of the system.
The above experimental results show that when the system is ideally heterogeneous, the method outlined in the literature [] can be used for evaluation. However, in reality, the type and number of executor components of the mimic control plane, symbiotic vulnerability ratio, component code reuse rate, and vulnerability discovery coefficient all have a direct impact on the heterogeneity of the mimic control plane; thus, HET1 is more intuitive and reasonable.
4.2. Evaluation of HET2
When evaluating Heterogeneity 2 (HET2), in order to simplify the analysis, the symbiotic vulnerability ratio can be unified. We set the symbiotic vulnerability ratio of each executor to the same value and evaluate the impact of the different symbiotic vulnerability ratios on the HOS of different high-order symbiotic vulnerabilities.
As shown in Figure 7, as the vulnerability ratio increases, the HOS gradually increases. The higher the order of symbiosis, the lower the HOS. When the vulnerability ratio is 0 and 1, HOS is 0 and 1, respectively. Moreover, as shown in Figure 7, as the vulnerability ratio increases, HET2 gradually decreases. The higher the symbiosis order, the larger HET2. When the vulnerability ratio is 0 and 1, HET2 are 1 and 0, respectively. The simulation results show that if the SDN control executor has more symbiotic vulnerabilities, higher HOS and larger HET2 can be achieved. The above simulation results also conform to common sense.
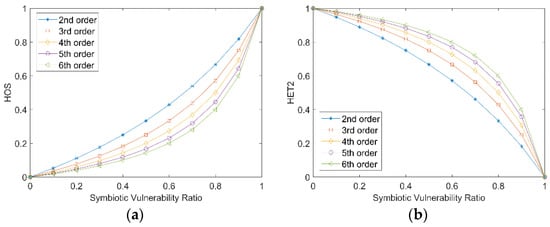
Figure 7.
The impact of symbiotic vulnerability ratio. (a) The impact on HOS (b) The impact on HET2.
4.3. Mimic Control Plane Instance and Quantitative Analysis of Heterogeneity
In this experiment, five different mimic control plane executor sets are selected, each of which includes three executors. Different operating systems and SDN controllers are selected for the executors of the mimic control plane. The vulnerability information of the operating system comes from the NVD database [], and the method for obtaining the vulnerability information of the controller comes from the literature []. As its CVSS score is not given, the default unified setting is 5; that is, the level of all vulnerabilities is medium.
All components in executor sets 1, 2 and 3 are not the same. The controller of executors in Executor Set 4 is exactly the same, and the executors of executor set 5 are completely homogeneous. The experimental results are shown in Table 1.

Table 1.
Comparison of heterogeneous quantification results of mimic control plane.
- (1)
- In Executor Set 1, HBCV has the same heterogeneity as HET1, primarily because the operating system used by the components in the executor set is non-homologous; therefore, the code reuse rate is 0. In the absence of a code reuse rate, the HET1 evaluation index in this article is the same as HBCV.
- (2)
- Comparing Executor Set 2 with Executor Set 1, the second executor was replaced by Redhat7 from OpenBSD. Redhat7 and Ubuntu12 are Linux homologous systems and have code reuse. Therefore, the heterogeneity of HET1 is lower than HBCV. At the same time, due to the introduction of Redhat7, the symbiotic vulnerabilities have increased, HET2 becomes larger, and the security of Executor Set 2 is lower than that of Executor Set 1.
- (3)
- Comparing Executor Set 3 with Executor Set 2, the controller of the first executor is changed from Ryu to ONOS. Compared with Ryu, the vulnerabilities of ONOS have increased. Both HBCV and HET1 have decreased, while HET2 has increased. The main reason for this is that the symbiotic vulnerabilities in Executor Set 3 have increased. Higher HET2 indicates more security, and Executor Set 3 is more secure than Executor Set 2. Combined with property 7, this group’s comparison shows that the reduction in HBCV and HET1 does not necessarily make the system more secure, and the system security needs to be evaluated in conjunction with HET2.
- (4)
- Comparing Executor Sets 4 and 2, the controller is a unified Ryu controller, its HBCV/HET1/HET2 is greatly reduced, and the system security is greatly reduced.
- (5)
- Executor Set 5 is a completely homogeneous system, HBCV/HET1/HET2 are all 0, Heterogeneity 2 has the maximum value of 1, and the system has the lowest security.
It can be seen from the example of the mimic control plane constructed above that, on the one hand, the HET1 is different from HBCV. When the same software or operating system exists, the HET1 is lower than the HBCV. On the other hand, HBCV and HET1 cannot fully reflect the security of the mimic control plane, but HET2 can more accurately reflect the security of the system. Therefore, using HET1 and HET2 to comprehensively evaluate the heterogeneity of the mimic control plane can more accurately evaluate its security.
5. Conclusions and Future Work
The mimic control plane significantly increases the security of the SDN control plane, but how to effectively evaluate the security of the mimic control plane is a key issue that needs to be resolved and it is useful to consider designing a mimic control plane. Based on previous studies, this paper draws on biodiversity, based on Shannon entropy and quadratic entropy; introduces the vulnerability attributes of the SDN control plane into quadratic entropy; and incorporates it into the quantitative model of HET1 as a parameter for evaluating differences. In addition, based on the high-order symbiosis of vulnerabilities, a quantitative model of HET2 is constructed to effectively evaluate the security of the mimic control plane. The experimental results show that, compared with the heterogeneity quantification method HBCV, based on known vulnerabilities, the two quantification models proposed in this paper are more targeted for the heterogeneity quantification of the mimic control plane, and can better reflect system security.
This article conducts a quantitative analysis of the proposed heterogeneity metrics and high-order symbiosis of vulnerabilities in theory but does not include how to design an actual system, and also does not involve the scheduling algorithm and the impact of voting strategies on scheduling. Therefore, future work will contain two aspects: (1) Designing a mimic control plane by normalizing the executors to ensure the consistency of their input and output, according to the principles of the proposed methods; (2) Evaluating the security of the system in combination with the scheduling algorithm and voting strategy based on the attack attributes.
Author Contributions
Conceptualization, methodology, original draft, W.Z.; funding acquisition, calculation, Z.Z.; Verification, review and editing, K.S. and S.W.; All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported in part by the National Core Electronic Devices, High-end Generic Chips and Basic Software Major Projects under Grant 2017ZX01030301, and in part by the National Natural Science Foundation of China for Innovative Research Groups under Grant 61521003.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- McKeown, N.; Anderson, T.; Balakrishnan, H.; Parulkar, G.; Peterson, L.; Rexford, J.; Shenker, S.; Turner, J. OpenFlow: Enabling innovation in campus networks. ACM SIGCOMM Comput. Commun. Rev. 2008, 38, 69–74. [Google Scholar] [CrossRef]
- Zuo, Q.; Chen, M.; Ding, K.; Xu, B. On generality of the data plane and scalability of the control plane in software-defined networking. China Commun. 2014, 11, 55–64. [Google Scholar] [CrossRef]
- Deb, R.; Roy, S. A comprehensive survey of vulnerability and information security in SDN. Comput. Networks 2022, 206, 108802. [Google Scholar] [CrossRef]
- Hsieh, H.-C.; Chiang, M.-L.; Chang, T.-Y. Improving the fault-tolerance of software-defined networks with dynamic overlay agreement. Clust. Comput. 2021, 24, 2597–2614. [Google Scholar] [CrossRef]
- Yang, Y.; Cheng, L. An SDN-based MTD model. Concurr. Comput. Pract. Exp. 2019, 31, e4897. [Google Scholar] [CrossRef]
- Hu, H.; Wang, Z.; Cheng, G.; Wu, J. MNOS: A mimic network operating system for software defined networks. IET Inf. Secur. 2017, 11, 345–355. [Google Scholar] [CrossRef]
- Aydeger, A.; Saputro, N.; Akkaya, K. A moving target defense and network forensics framework for ISP networks using SDN and NFV. Futur. Gener. Comput. Syst. 2018, 94, 496–509. [Google Scholar] [CrossRef]
- Cho, J.-H.; Sharma, D.P.; Alavizadeh, H.; Yoon, S.; Ben-Asher, N.; Moore, T.J.; Kim, D.S.; Lim, H.; Nelson, F.F. Toward Proactive, Adaptive Defense: A Survey on Moving Target Defense. IEEE Commun. Surv. Tutorials 2020, 22, 709–745. [Google Scholar] [CrossRef]
- Zheng, J.; Namin, A.S. A Survey on the Moving Target Defense Strategies: An Architectural Perspective. J. Comput. Sci. Technol. 2019, 34, 207–233. [Google Scholar] [CrossRef]
- Chiang, M.-L.; Hsieh, H.-C.; Wang, C.-W. Improving the Fault-Tolerance Under Software-Defined Network Based on New Sight of Agreement Protocol. IEEE Access 2018, 6, 40898–40908. [Google Scholar] [CrossRef]
- Sakic, E.; Deric, N.; Kellerer, W. MORPH: An Adaptive Framework for Efficient and Byzantine Fault-Tolerant SDN Control Plane. IEEE J. Sel. Areas Commun. 2018, 36, 2158–2174. [Google Scholar] [CrossRef]
- Yuan, B.; Jin, H.; Zou, D.; Yang, L.T.; Yu, S. A Practical Byzantine-Based Approach for Faulty Switch Tolerance in Software-Defined Networks. IEEE Trans. Netw. Serv. Manag. 2018, 15, 825–839. [Google Scholar] [CrossRef]
- Hu, H.; Wu, J.; Wang, Z.; Cheng, G. Mimic defense: A designed-in cybersecurity defense framework. IET Inf. Secur. 2018, 12, 226–237. [Google Scholar] [CrossRef]
- Wang, Z.P.; Hu, H.C.; Cheng, G.Z. A DNS Architecture Based on Mimic Security Defense. Acta Electron. Sin. 2017, 45, 2705–2714. [Google Scholar]
- Zhang, Z.; Ma, B.L.; Wu, J.X. Testing and Analysis of Web Server Mimic Defense Principle Verification System. J. Inf. Secur. 2017, 2, 13–28. [Google Scholar]
- Qi, C.; Wu, J.; Hu, H.; Cheng, G.; Liu, W.; Ai, J.; Yang, C. An intensive security architecture with multi-controller for SDN. In Proceedings of the IEEE INFOCOM 2016—IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), San Francisco, CA, USA, 10–14 April 2016; pp. 401–402. [Google Scholar]
- Qi, C.; Wu, J.; Cheng, G.; Ai, J.; Zhao, S. An aware-scheduling security architecture with priority-equal multi-controller for SDN. China Commun. 2017, 14, 144–154. [Google Scholar] [CrossRef]
- Qi, C.; Wu, J.; Hu, H.; Cheng, G. Dynamic-scheduling mechanism of controllers based on security policy in software-defined network. Electron. Lett. 2016, 52, 1918–1920. [Google Scholar] [CrossRef]
- Li, J.F.; Lan, J.L.; Hu, Y.X.; Wu, J.X. Quantitative approach of multi-controller’s consensus in SDN. J. Commun. 2016, 37, 86–93. [Google Scholar]
- Li, J.; Wu, J.; Hu, Y.; Li, K. DSL: Dynamic and Self-Learning Schedule Method of Multiple Controllers in SDN. ETRI J. 2017, 39, 364–372. [Google Scholar] [CrossRef]
- Li, C.H.; Ren, Y.F.; Tang, Z.Y.; Wang, W. Mimic defense method for service deployment in SDN. J. Commun. 2018, 39, 121–130. [Google Scholar]
- Shao, C.S.; Lou, W.; Yan, L.M. Optimization of Algorithm of Similarity Measurement in High-Dimensional Data. Comput. Technol. Dev. 2011, 21, 1–4. [Google Scholar]
- Mitra, P.; Murthy, C.; Pal, S. Unsupervised feature selection using feature similarity. IEEE Trans. Pattern Anal. Mach. Intell. 2002, 24, 301–312. [Google Scholar] [CrossRef]
- Pincus, S.M. Approximate entropy as a measure of system complexity. Proc. Natl. Acad. Sci. USA 1991, 88, 2297–2301. [Google Scholar] [CrossRef]
- Salako, K.; Strigini, L. When Does "Diversity" in Development Reduce Common Failures? Insights from Probabilistic Modeling. IEEE Trans. Dependable Secur. Comput. 2013, 11, 193–206. [Google Scholar] [CrossRef]
- Xin, J.; Gossels, J.; Rexford, J.; Walker, D. CoVisor: A Compositional Hypervisor for Software-Defined Networks. USENIX Assoc. 2015, 87–101. [Google Scholar]
- Yang, G.; Shin, C.; Yoo, Y.; Yoo, C.C. A Case for SDN-based Network Virtualization. In Proceedings of the 2021 29th International Symposium on Modeling, Analysis, and Simulation of Computer and Telecommunication Systems (MASCOTS), Houston, TX, USA, 3–5 November 2021. [Google Scholar]
- Liao, L.X.; Wang, J.; Chao, H.C.; Qin, B. Distributed and Efficient Network Hypervisor for SDN Virtualization. J. Internet Technol. 2021, 22, 625–636. [Google Scholar]
- Liu, Q.R.; Lin, S.J.; Gu, Z.Y. Heterogeneous redundancies scheduling algorithm for mimic security defense. J. Commun. 2018, 39, 188–198. [Google Scholar]
- Zhang, J.X.; Pang, J.M.; Zhang, Z. Quantification Method for Heterogeneity on Web Server with Mimic Construction. J. Softw. 2020, 31, 564–577. [Google Scholar]
- Shahzad, M.; Shafiq, M.Z.; Liu, A.X. Large Scale Characterization of Software Vulnerability Life Cycles. IEEE Trans. Dependable Secur. Comput. 2019, 17, 730–744. [Google Scholar] [CrossRef]
- Wu, J.X. Research on cyber mimic defense. J. Cyber Secur. 2016, 1, 1–10. [Google Scholar]
- Twu, P.; Mostofi, Y.; Egerstedt, M. A measure of heterogeneity in multi-agent systems. In Proceedings of the 2014 American Control Conference, Portland, OR, USA, 4–6 June 2014; pp. 3972–3977. [Google Scholar] [CrossRef]
- Hill, M.O. Diversity and Evenness: A Unifying Notation and Its Consequences. Ecology 1973, 54, 427–432. [Google Scholar] [CrossRef]
- Rao, C.R. Diversity and dissimilarity coefficients: A unified approach. Theor. Popul. Biol. 1982, 21, 24–43. [Google Scholar] [CrossRef]
- Wei, S.; Zhang, H.; Zhang, W.; Yu, H. Conditional Probability Voting Algorithm Based on Heterogeneity of Mimic Defense Sys-tem. IEEE Access 2020, 8, 188760–188770. [Google Scholar] [CrossRef]
- Mell, P.; Scarfone, K.; Romanosky, S. Common Vulnerability Scoring System. IEEE Secur. Priv. 2006, 4, 85–89. [Google Scholar] [CrossRef]
- Garcia, M.; Bessani, A.; Gashi, I.; Neves, N.; Obelheiro, R. Analysis of operating system diversity for intrusion tolerance. Software: Pract. Exp. 2013, 44, 735–770. [Google Scholar] [CrossRef]
- Lee, S.; Kim, J.; Woo, S.; Yoon, C.; Scott-Hayward, S.; Yegneswaran, V.; Porras, P.; Shin, S. A comprehensive security assessment framework for software-defined networks. Comput. Secur. 2020, 91, 101720. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).