An Optimized Load Balancing Using Firefly Algorithm in Flying Ad-Hoc Network
Abstract
1. Introduction
- For FANETs, we propose the specific functions F1 and F2 with the optimization process by taking different parameters such as end-to-end delay (EED), packet delivery ratio (PDR), fuel emission, and throughput. The technique is used to resolve the constraints of the optimization problem with the firefly algorithm, which is used to estimate the exact match of the dynamic network topology. The primary problem is therefore converted into a distributed solvable problem, allowing senders to compute the attractiveness of flying nodes to execute congestion control.
- To reach the best solution, we present a distributed traffic congestion control algorithm that incorporates the delay constraints. We propose Rs, Rd, and Rp variables for all flying nodes to verify the incoming flow of the flying nodes and outgoing flow of the flying nodes probability to exploit network utilization and decrease transmission delay in a circulated manner. Finally, we examine the optimization method’s performance and demonstrate its convergence using a simulator.
2. Related Work
3. Proposed Network Model
3.1. Problem Formulation
- Load balancing using software-defined networking (SDN),
- User Datagram Protocol (UDP),
- Transmission Control Protocol (TCP),
- Server load balancing (SLB),
- Virtual load balancing, multi-site load balancing, and elastic load balancing, also known as global server load balancing (GSLB), and
- Geographic load balancing.
3.2. Solution of the Problem
| Algorithm 1. Proposed Firefly Algorithm |
| Step 1: Begin by initializing the objective function. |
| Step 2: Create a small population of fireflies (nodes). |
| Step 3: Calculate the light intensity and the state absorption coefficient. |
| Step 4: Repeat Steps 5–8 until the maximum generation value is reached (maximum iteration). |
| Step 5: Repeat for I = 1 to N, where N represents all of the ‘N’ fireflies. |
| Step 6: Repeat for J = 1 to I. |
| Step 7: If J’s light intensity is larger than I’s light intensity, then set: change mate selection and prey attractiveness with their distance. |
| Step 8: Reposition the firefly based on I’s attraction to J and test different solutions. |
| Compute attractiveness value of the fireflies using Equation (11) |
| (The end of the If structure) |
| (At the end of the Inner for structure.) |
| (At the end of the Outer for structure.) |
| Step 9: If the result cannot be discovered, proceed to step 4. |
| Step 10: Show the best-desired outcome. |
| Algorithm 2. Traffic Congestion Control Algorithm |
| Step 1: First of all, we need to initialize different parameters such as Rs, Rd, and Rp. |
| Step 2: If the flying node arrives at link Li: |
| Step 3: Then we have to calculate the value of ∑͞Di, which is based on Equation (7)
|
| Here, n is the error of flying nodes due to environmental issues, and χ1 is the delay errors of flying nodes at node-link Cn. |
| Step 4: Further, calculate the value of χ1. |
| Step 5: χ = χ + χ1, where χ = 0. |
| Step 6: As per the firefly algorithm, update the attractiveness as described in Equation (12). |
| Step 7: Calculate Rs based on Equation (12). |
| Step 8: Update the value of attractiveness until β remains unchanged. |
| Step 9: Stop. |
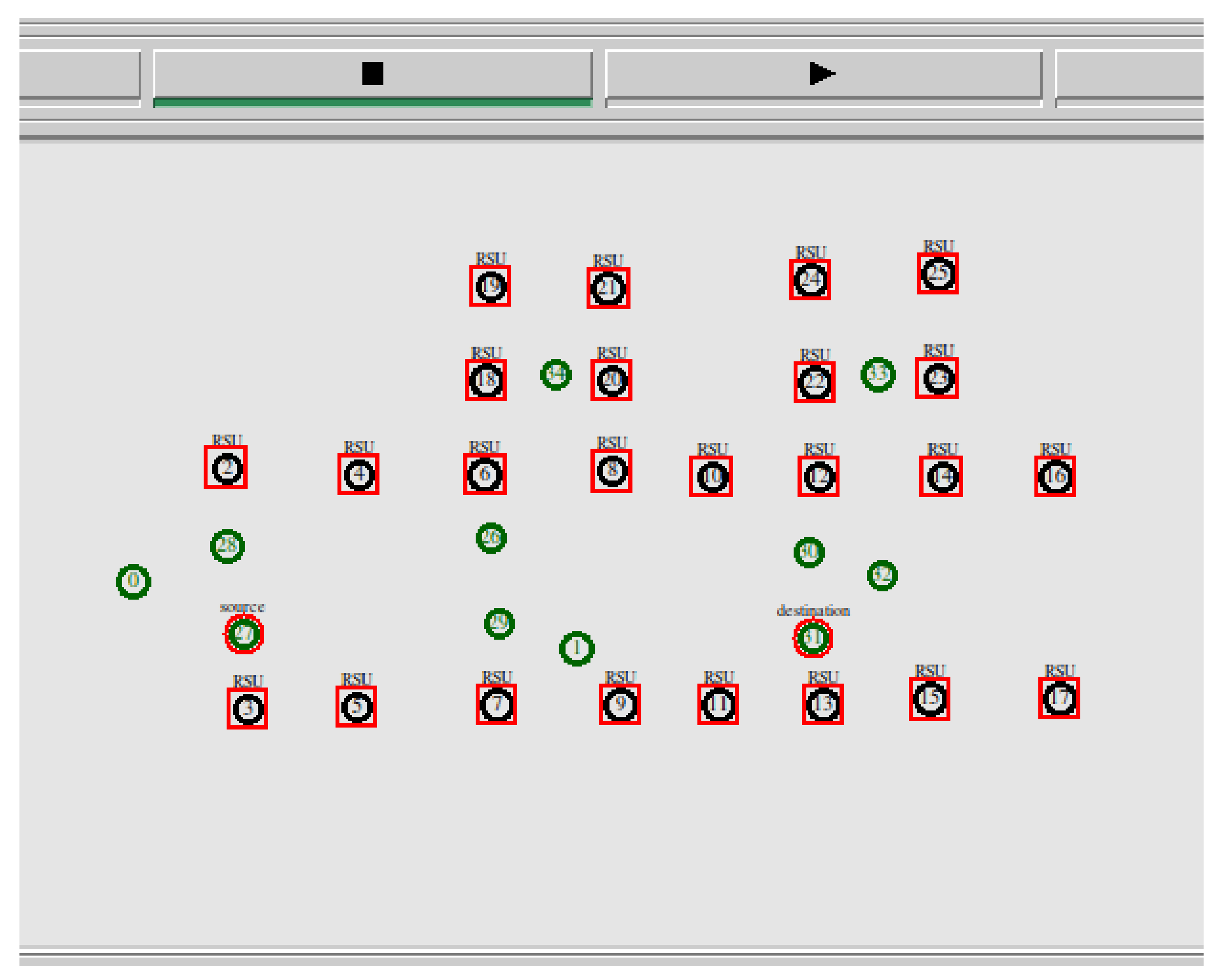
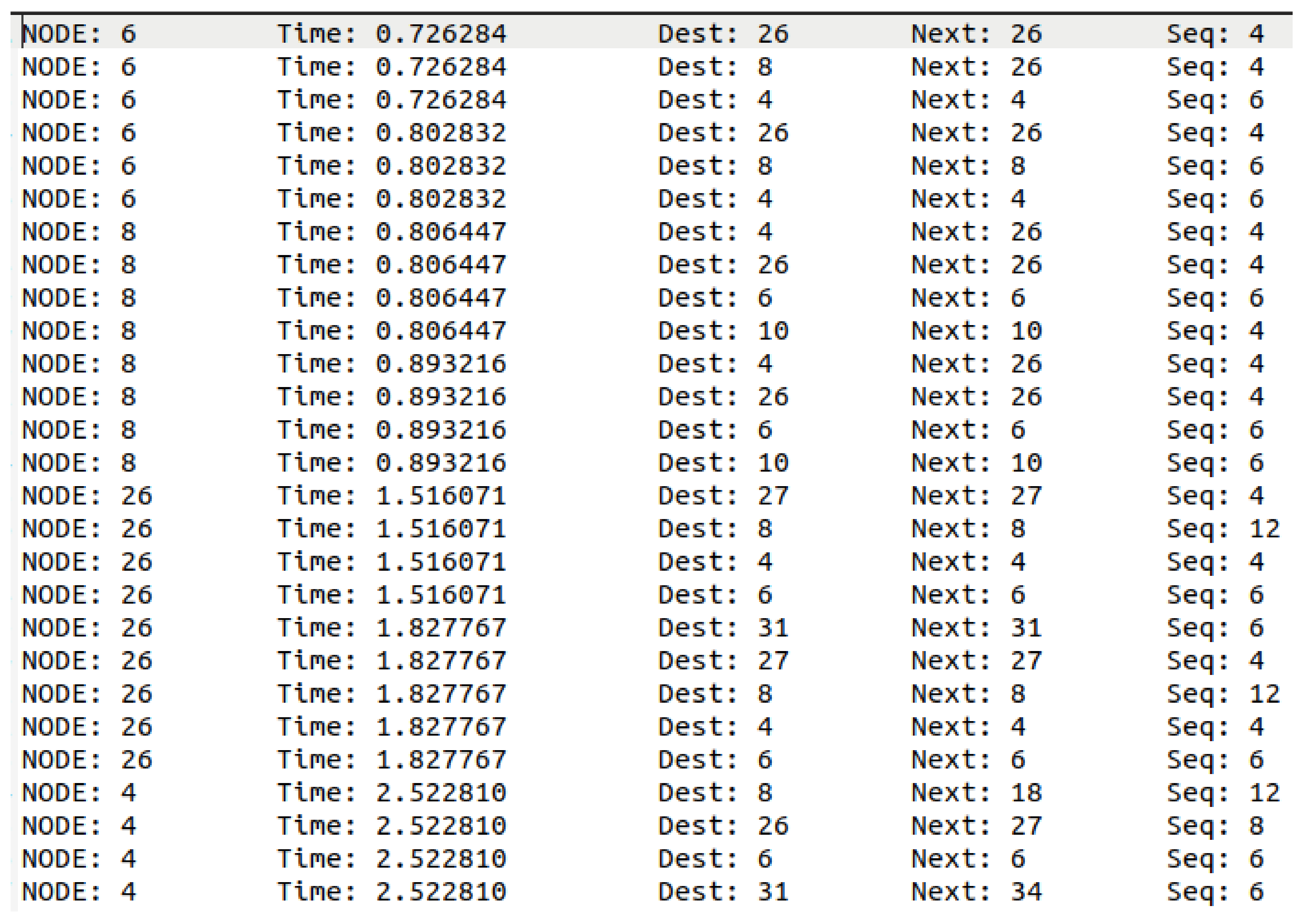
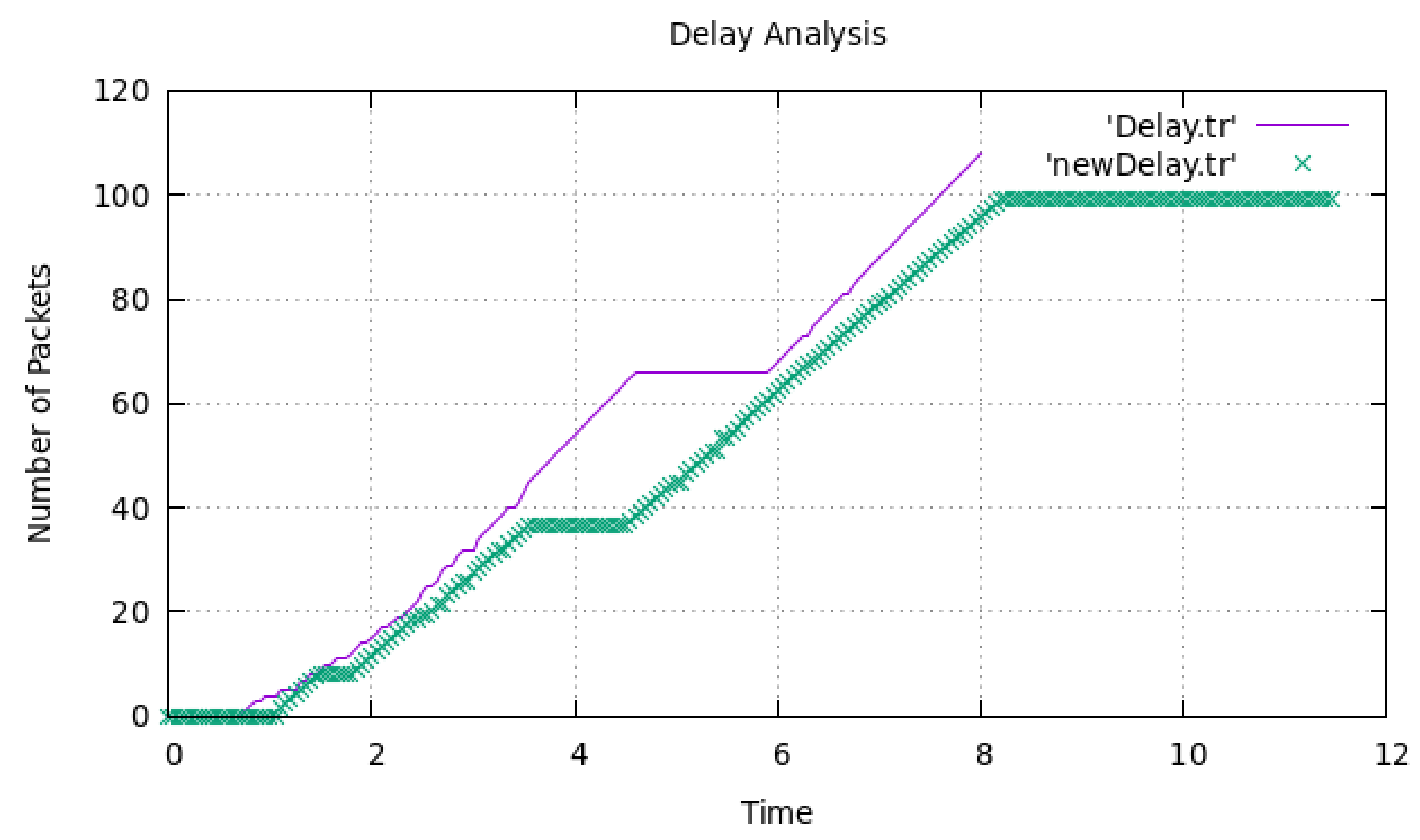
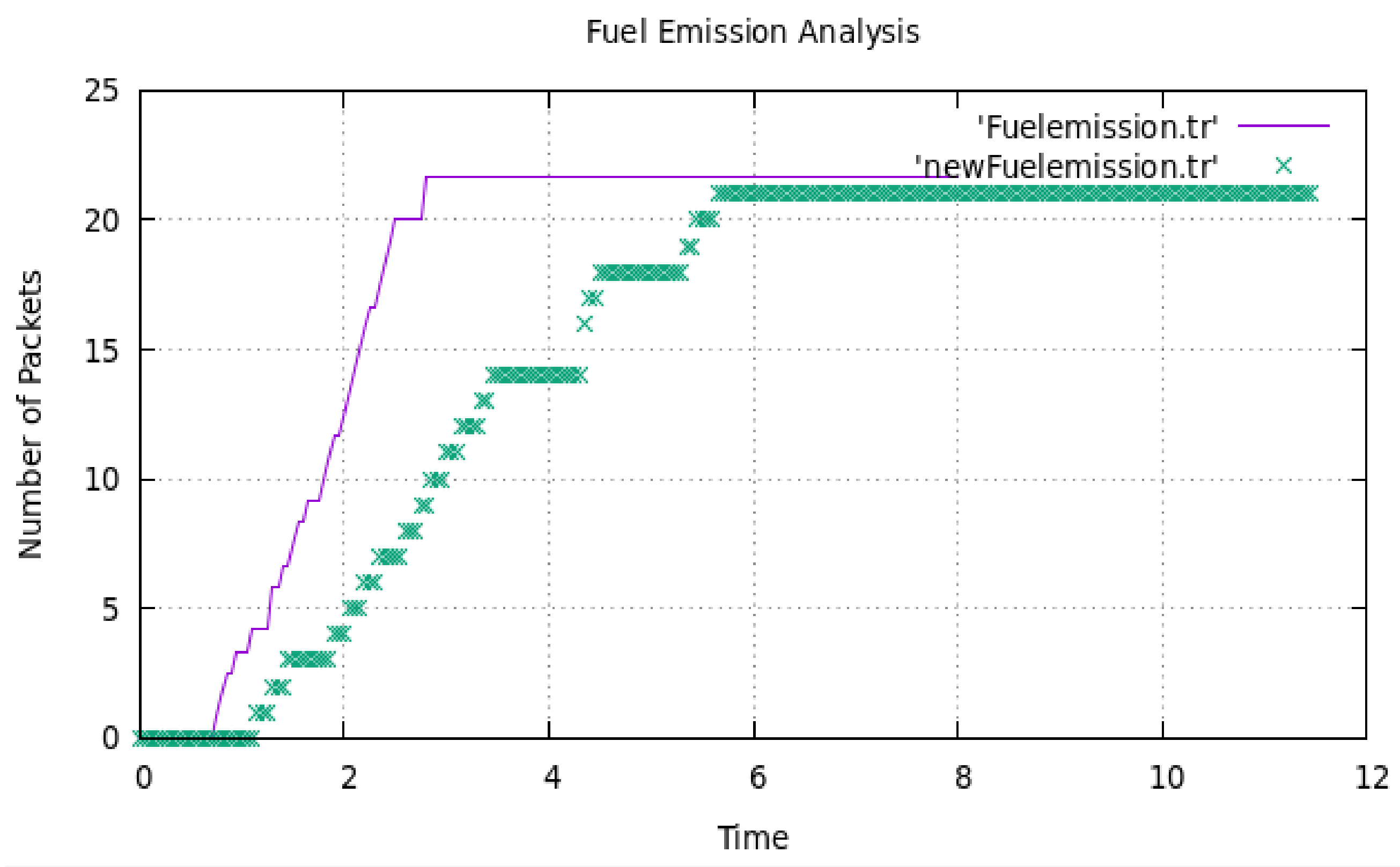
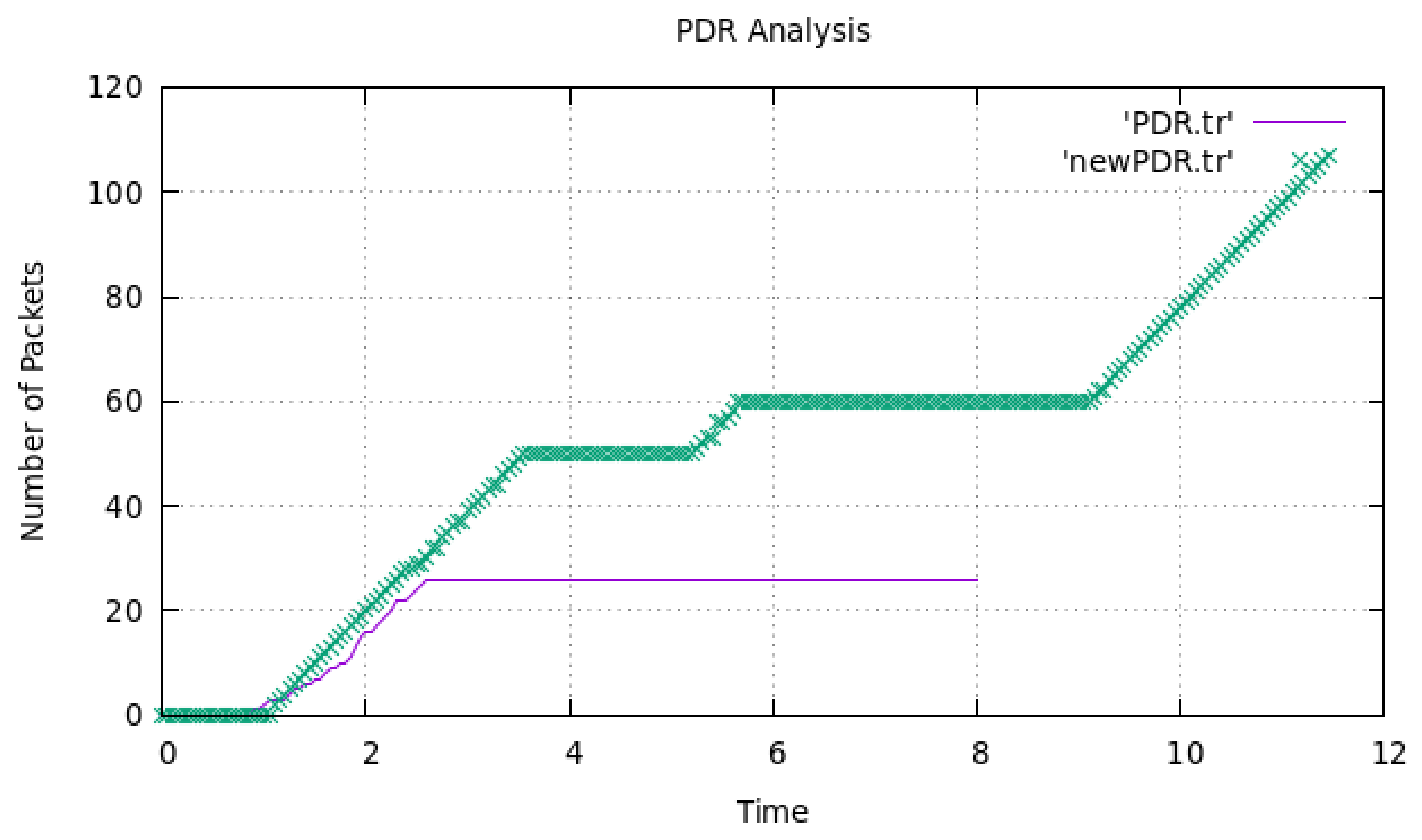
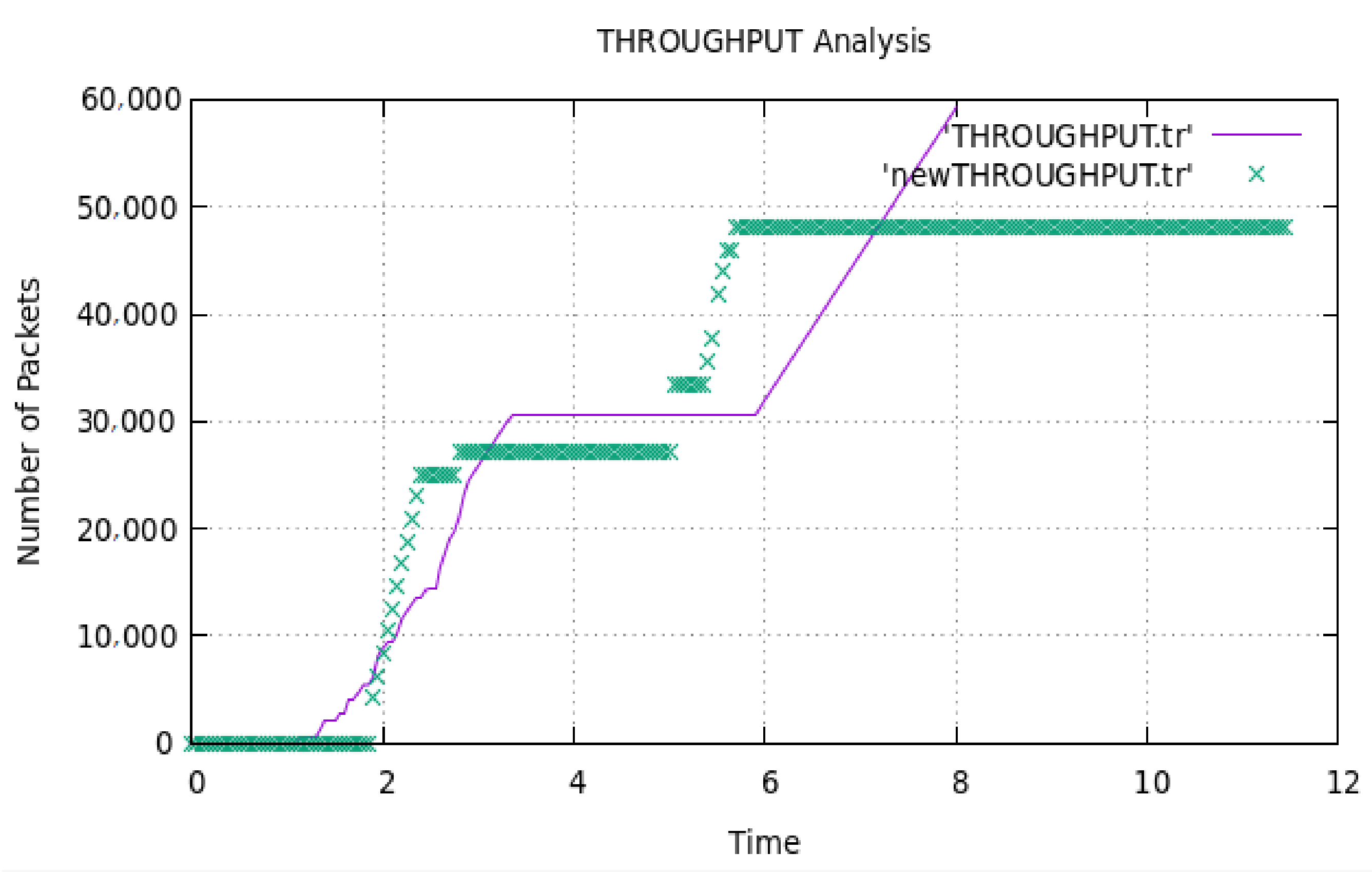
4. Results and Discussion
- geo utility.h contains geometrical utility functions such as the projection of a 3D graph to a 2D graph and the communications network between two flying nodes;
- geo pkt.h contains the new geo packet header definition;
- geo node.h and geo node.cc files define and implement the geographic node;
- geo.h and geo.cc files contain the definition and implementation of the geographic agent prototype;
- the proposed algorithms are defined and implemented in geo next node.h and geo next node.cc.
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Gupta, L.; Jain, R.; Vaszkun, G. Survey of Important Issues in UAV Communication Networks. IEEE Commun. Surv. Tutor. 2016, 18, 1123–1152. [Google Scholar] [CrossRef]
- Kang, M.-S.; Kum, D.-W.; Bae, J.-S.; Cho, Y.-Z.; Le, A.-N. Mobility Aware Hybrid Routing protocol for mobile ad hoc network. In Proceedings of the International Conference on Information Network 2012, Bali, Indonesia, 1–3 February 2012; pp. 410–414. [Google Scholar]
- Kaur, M.; Verma, S. Kavita Flying Ad-Hoc Network (FANET): Challenges and routing protocols. J. Comput. Theor. Nanosci. 2020, 17, 2575–2581. [Google Scholar] [CrossRef]
- Johnson, D.B.; Maltz, D.A. Dynamic source routing in ad hoc wireless networks. In The Kluwer International Series in Engineering and Computer Science Mobile Computing; Springer: Berlin/Heidelberg, Germany, 1996; pp. 153–181. [Google Scholar]
- Zheng, Z.; Sangaiah, A.K.; Wang, T. Adaptive Communication Protocols in Flying Ad Hoc Network. IEEE Commun. Mag. 2018, 56, 136–142. [Google Scholar] [CrossRef]
- Kaur, M.; Prashar, D. Analysis of geographic position mobility oriented routing protocol for FANETs. In Proceedings of the 2021 9th International Conference on Reliability, Infocom Technologies and Optimization (Trends and Future Directions) (ICRITO), Noida, India, 3–4 September 2021; pp. 1–4. [Google Scholar]
- Kaur, M.; Singh, A.; Verma, S.; Jhanjhi, N.Z.; Talib, M.N. FANET: Efficient routing in flying ad hoc networks (FANETs) using firefly algorithm. In Intelligent Computing and Innovation on Data Science Lecture Notes in Networks and Systems; Springer: Singapore, 2021; Volume 248, pp. 483–490. [Google Scholar] [CrossRef]
- D’Aronco, S.; Toni, L.; Mena, S.; Zhu, X.; Frossard, P. Improved utility-based congestion control for delay-constrained communication. IEEE/ACM Trans. Netw. 2016, 25, 349–362. [Google Scholar] [CrossRef]
- Mehta, R.; Lobiyal, D.K. Cross-layer optimization using two-level dual decomposition in multi-flow ad-hoc networks. Telecommun. Syst. 2017, 66, 639–655. [Google Scholar] [CrossRef]
- Khodaian, A.; Khalaj, B. Delay-constrained utility maximization in multi-hop random-access networks. IET Commun. 2010, 4, 1908–1918. [Google Scholar] [CrossRef]
- Zhang, L.; Zhuo, F.; Xu, H. A cross-layer optimization framework for congestion and power control in cognitive radio ad hoc networks under predictable contact. EURASIP J. Wirel. Commun. Netw. 2018, 2018, 57. [Google Scholar] [CrossRef]
- Li, Y.; Papachristodoulou, A.; Chiang, M.; Calderbank, A.R. Congestion control and its stability in networks with delay sensitive traffic. Comput. Netw. 2010, 55, 20–32. [Google Scholar] [CrossRef][Green Version]
- Rangisetti, A.K.; Tamma, B.R. QoS Aware load balance in software defined LTE networks. Comput. Commun. 2017, 97, 52–71. [Google Scholar] [CrossRef]
- Kafi, M.A.; Ben-Othman, J.; Ouadjaout, A.; Bagaa, M.; Badache, N. REFIACC: Reliable, efficient, fair and interference-aware congestion control protocol for wireless sensor networks. Comput. Commun. 2017, 101, 1–11. [Google Scholar] [CrossRef]
- Hajiesmaili, M.H.; Talebi, M.S.; Khonsari, A. Multiperiod network rate allocation with end-to-end delay constraints. IEEE Trans. Control. Netw. Syst. 2018, 5, 1087–1097. [Google Scholar] [CrossRef]
- Alaei, M.; Sabbagh, P.; Yazdanpanah, F. A QoS-aware congestion control mechanism for wireless multimedia sensor networks. Wirel. Netw. 2018, 25, 4173–4192. [Google Scholar] [CrossRef]
- Silva, A.P.; Obraczka, K.; Burleigh, S.; Nogueira, J.M.; Hirata, C.M. A congestion control framework for delay- and disruption tolerant networks. Ad. Hoc. Netw. 2019, 91, 101880. [Google Scholar] [CrossRef]
- León, J.P.A.; Begin, T.; Busson, A.; Llopis, L.J.D.L.C. A fair and distributed congestion control mechanism for smart grid neighborhood area networks. Ad. Hoc. Netw. 2020, 104, 102169. [Google Scholar] [CrossRef]
- Lubna, T.; Mahmud, I.; Cho, Y.-Z. D-LIA: Dynamic congestion control algorithm for MPTCP. ICT Express 2020, 6, 263–268. [Google Scholar] [CrossRef]
- Verma, L.P.; Kumar, M. An IoT based Congestion Control Algorithm. Internet Things 2020, 9, 100157. [Google Scholar] [CrossRef]
- Kaur, M.; Prashar, D.; Rashid, M.; Alshamrani, S.S.; AlGhamdi, A.S. A novel approach for securing nodes using two-ray model and shadow effects in flying ad-hoc network. Electronics 2021, 10, 3164. [Google Scholar] [CrossRef]






| Work | EED | PDR | Fuel Emission | Throughput |
|---|---|---|---|---|
| D’Aronco et al. [8] | ✓ | ✘ | ✘ | ✘ |
| Mehta et al. [9] | ✓ | ✘ | ✘ | ✓ |
| Khodaian et al. [10] | ✓ | ✓ | ✘ | ✘ |
| Li et al. [11] | ✓ | ✓ | ✘ | ✓ |
| Zhang et al. [12] | ✓ | ✘ | ✘ | ✓ |
| Rangisetti et al. [13] | ✓ | ✘ | ✘ | ✓ |
| Kafi et al. [14] | ✓ | ✓ | ✘ | ✓ |
| Hajiesmaili et al. [15] | ✓ | ✘ | ✘ | ✘ |
| Alaei et al. [16] | ✓ | ✘ | ✘ | ✓ |
| Silva et al. [17] | ✘ | ✓ | ✘ | ✘ |
| Leon et al. [18] | ✘ | ✓ | ✘ | ✓ |
| Lubna et al. [19] | ✓ | ✘ | ✘ | ✓ |
| Verma et al. [20] | ✓ | ✓ | ✘ | ✓ |
| Proposed work | ✓ | ✓ | ✓ | ✓ |
| Symbol/Notation | Description |
|---|---|
| ∑F | The notation depicts a limited set that contains all of the UAVs that are free to fly in the specified area. |
| Li | Indicates a link linking a pair of UAVs. |
| L | Denotes the set {∀l ∈ L}. |
| Uj and Ui | If the distance between Uj and Ui is below the communication radius, j ∈ Nei, where Nei is a set of Ui’s neighbors. |
| S | A session initiated by a source UAV. |
| E | A collection of all consecutive sessions. |
| L(s) | A collection of links followed by session Us. |
| S(l) = {Us ∈ ∑S ∣ Li ∈ L(s)} | A collection of all sources that use link Li. |
| ∑Di < θ | The entire delay along the path L(s) < threshold (θ). |
| Cn | Capacity of the node-link |
| Dn = P/(Cn − ∑S ∗ r) | This is expressed as a single-hop delay where P is the length of the packet and r is the rate of the source node. |
| Parameter Type | Value |
|---|---|
| Number of UAVs | 100 |
| Queue Type | Priority queue |
| Altitude of UAVs | 70 m |
| Traffic Type | CBR |
| Directional Gain | 10 dBi |
| Frequency | 2.4 GHz |
| Wireless Medium | Wireless physical medium |
| Data Rates | 54 Mbps |
| Packet Interval (s) | Exponential (1) |
| Routing Protocol | GPMOR |
| Packet Size (byte) | 1024 |
| Fuel (kg) | 80 |
| Simulation Time | 200 s |
| Pause Time | Variable |
| Antenna Type | Omni-Directional |
| Transmission Power | 0.005 W |
| Speed of UAVs | Can vary up to 60 m/s |
| Source | Neighbor | SX-Pos | SY-Pos | Distance (d) |
|---|---|---|---|---|
| 0 | 2 | −247 | 358 | 161 |
| 1 | 6 | 239 | 284 | 216 |
| 1 | 7 | 239 | 284 | 106 |
| 1 | 8 | 239 | 284 | 198 |
| 1 | 9 | 239 | 284 | 78 |
| 1 | 11 | 239 | 284 | 168 |
| 1 | 26 | 239 | 284 | 115 |
| 1 | 27 | 239 | 284 | 159 |
| 1 | 28 | 239 | 284 | 209 |
| 1 | 29 | 239 | 284 | 36 |
| 1 | 30 | 239 | 284 | 229 |
| 1 | 31 | 239 | 284 | 204 |
| 2 | 0 | −145 | 483 | 161 |
| 2 | 4 | −145 | 483 | 145 |
| 2 | 28 | −145 | 483 | 225 |
| 3 | 0 | −122 | 218 | 187 |
| 3 | 5 | −122 | 218 | 120 |
| 3 | 27 | −122 | 218 | 220 |
| 4 | 2 | 0 | 475 | 145 |
| 4 | 6 | 0 | 475 | 139 |
| 4 | 18 | 0 | 475 | 173 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kaur, M.; Prashar, D.; Rashid, M.; Khanam, Z.; Alshamrani, S.S.; AlGhamdi, A.S. An Optimized Load Balancing Using Firefly Algorithm in Flying Ad-Hoc Network. Electronics 2022, 11, 252. https://doi.org/10.3390/electronics11020252
Kaur M, Prashar D, Rashid M, Khanam Z, Alshamrani SS, AlGhamdi AS. An Optimized Load Balancing Using Firefly Algorithm in Flying Ad-Hoc Network. Electronics. 2022; 11(2):252. https://doi.org/10.3390/electronics11020252
Chicago/Turabian StyleKaur, Manjit, Deepak Prashar, Mamoon Rashid, Zeba Khanam, Sultan S. Alshamrani, and Ahmed Saeed AlGhamdi. 2022. "An Optimized Load Balancing Using Firefly Algorithm in Flying Ad-Hoc Network" Electronics 11, no. 2: 252. https://doi.org/10.3390/electronics11020252
APA StyleKaur, M., Prashar, D., Rashid, M., Khanam, Z., Alshamrani, S. S., & AlGhamdi, A. S. (2022). An Optimized Load Balancing Using Firefly Algorithm in Flying Ad-Hoc Network. Electronics, 11(2), 252. https://doi.org/10.3390/electronics11020252








