Analysis and Design of a Smart Controller for Managing Penetration of Renewable Energy Including Cybersecurity Issues
Abstract
:1. Introduction
- To develop an analytical control algorithm used in DERMS to optimally utilize the DERs for the maximum power production of PV and handling an EV aggregator using the BES system based on fuzzy logic.
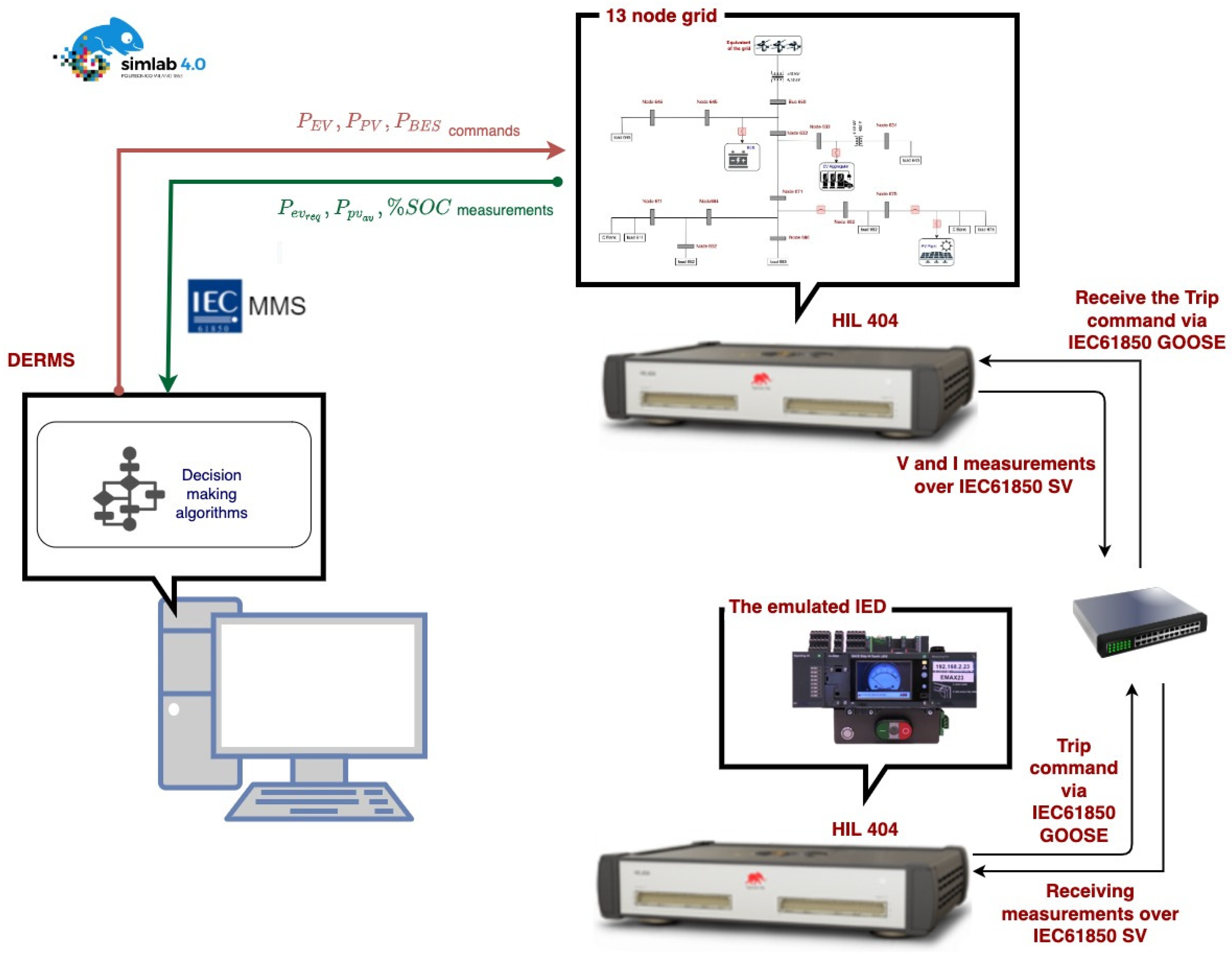
- To successfully realize DERMS to manage the DERs present in modified IEEE 13 node test feeder network using the IEC61850 communication protocol using the HIL simulation setup.
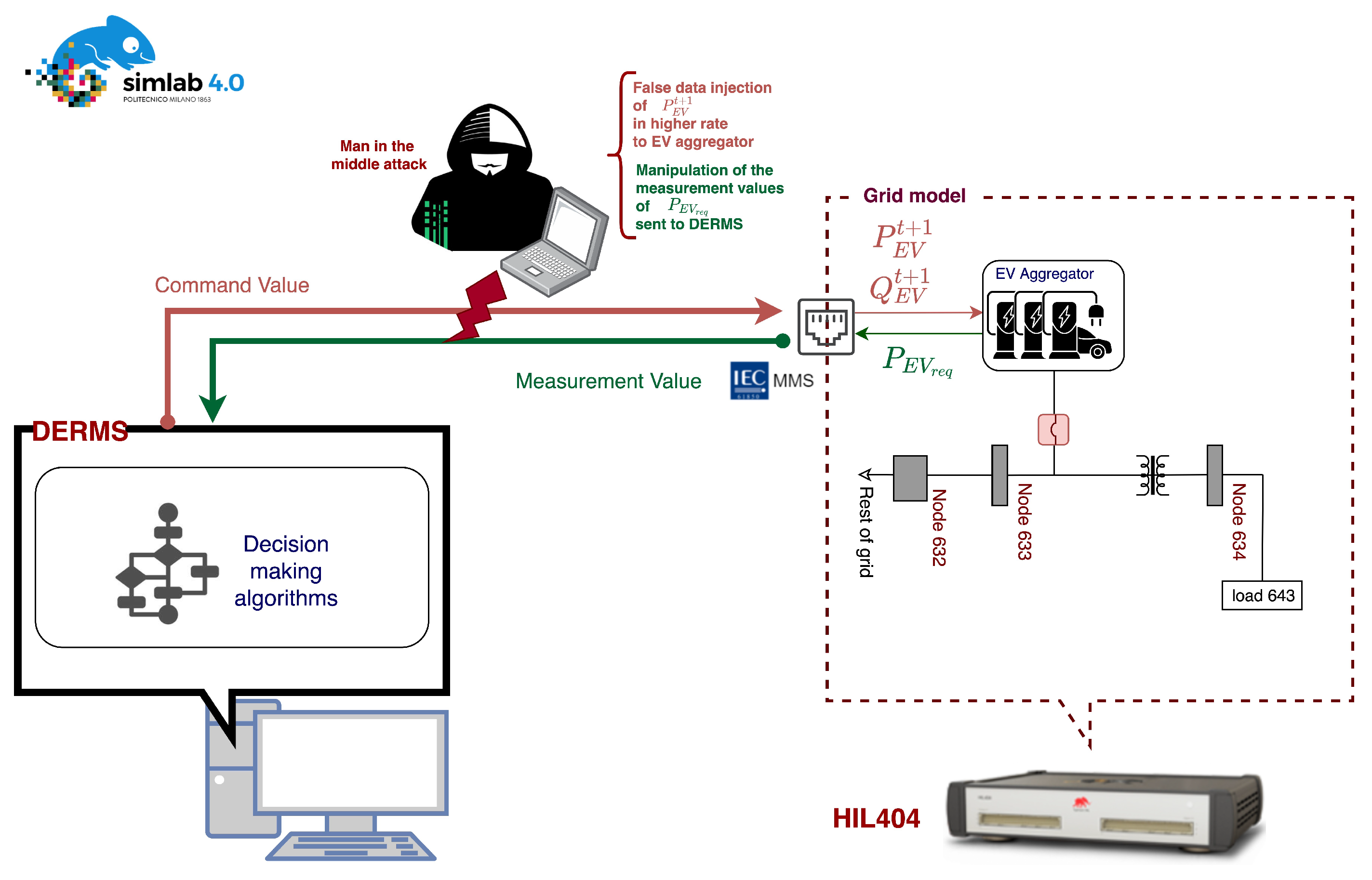
- To investigate the vulnerability threat scenarios by performing man-in-the-middle attacks exploiting EV aggregation as a vulnerable point.
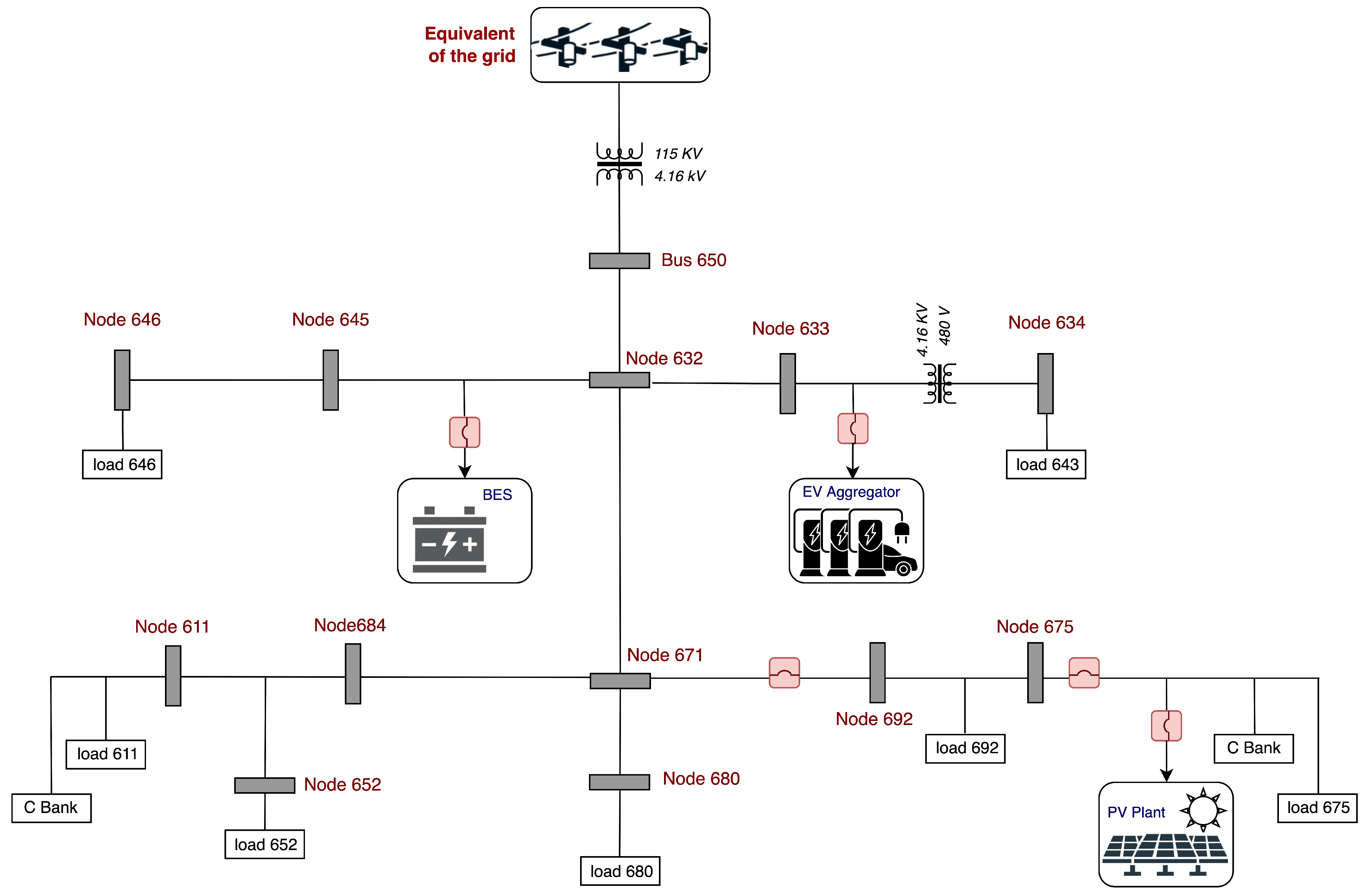
2. Modeling Electric Grid
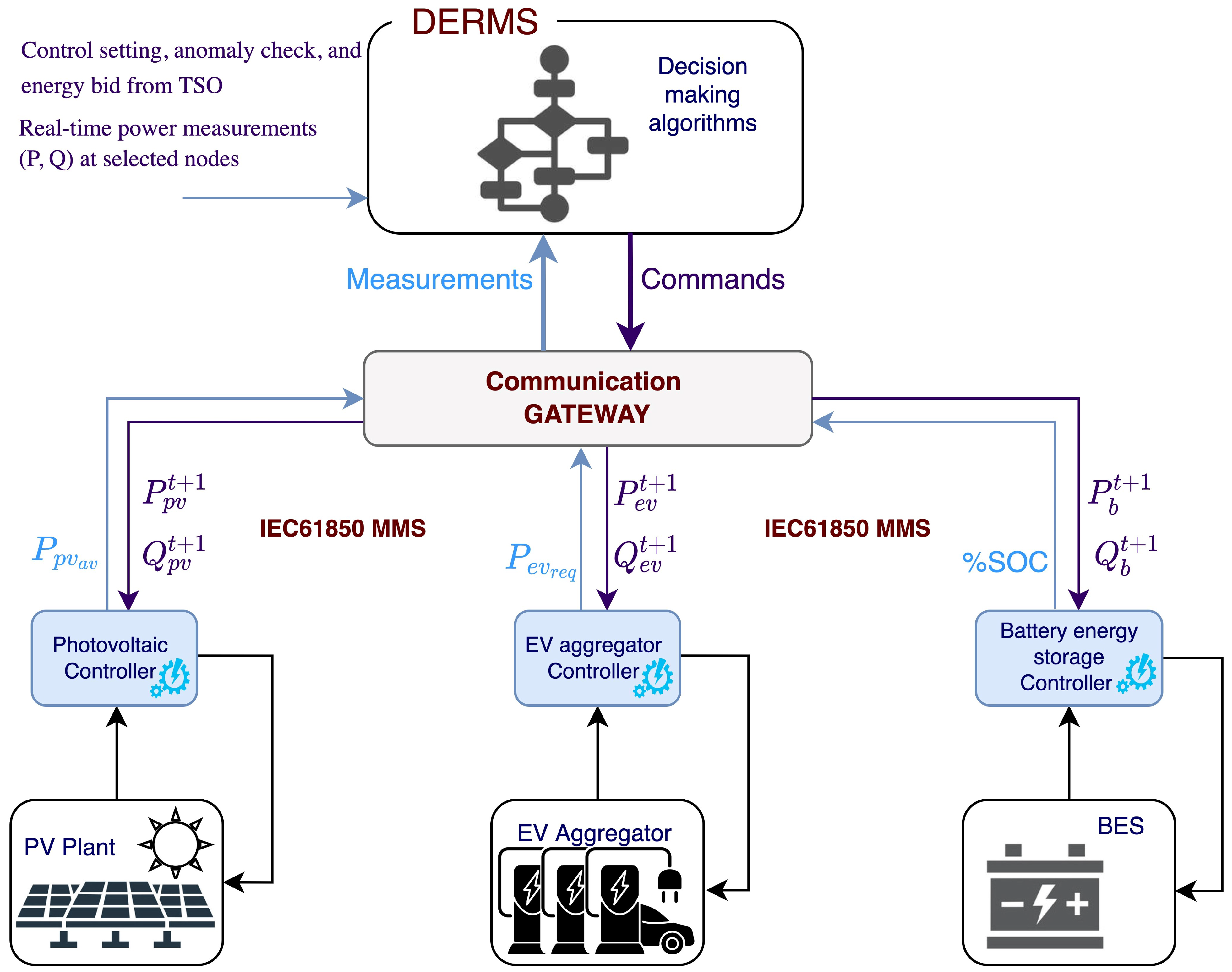
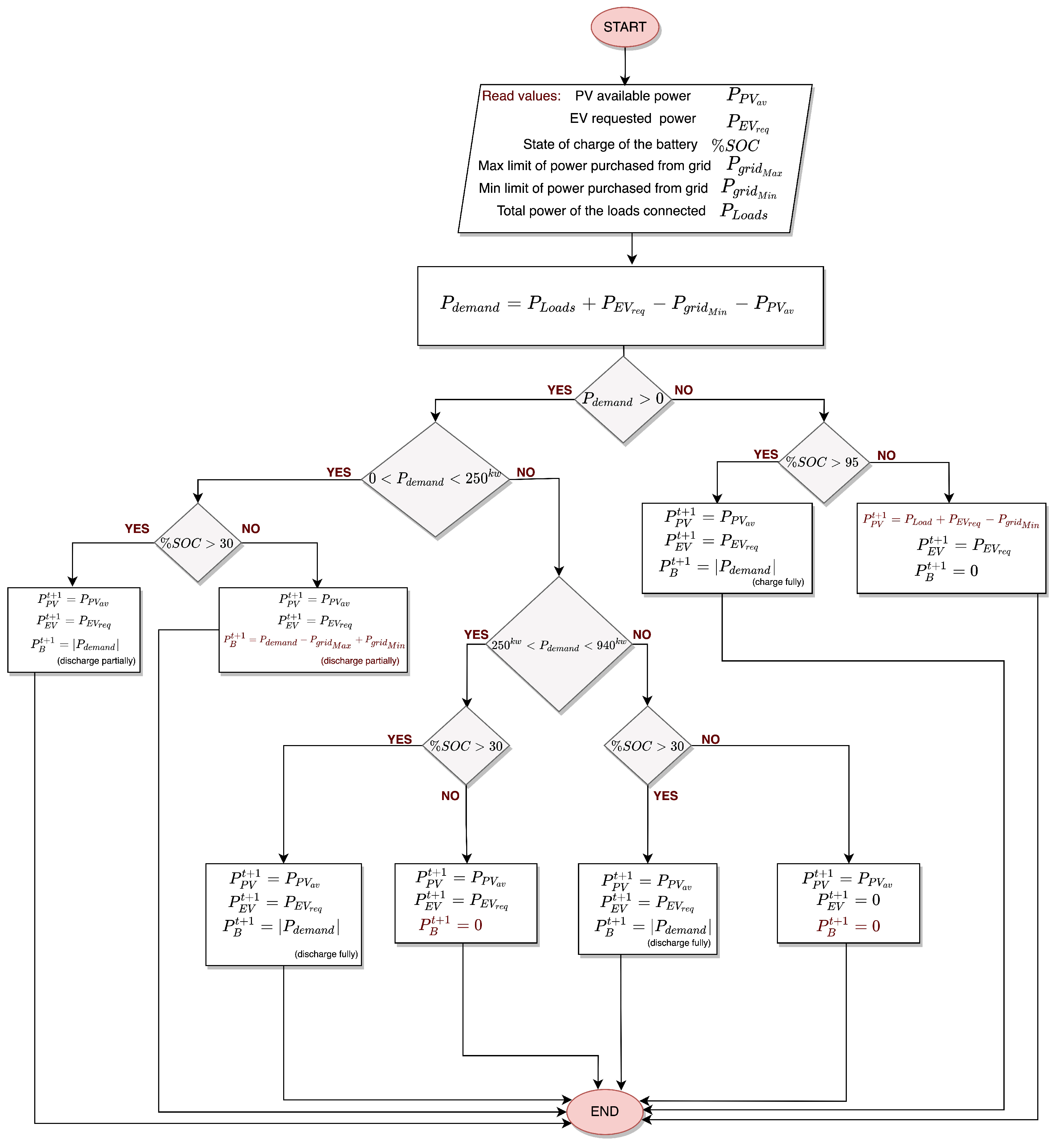
3. Distributed Energy Management System
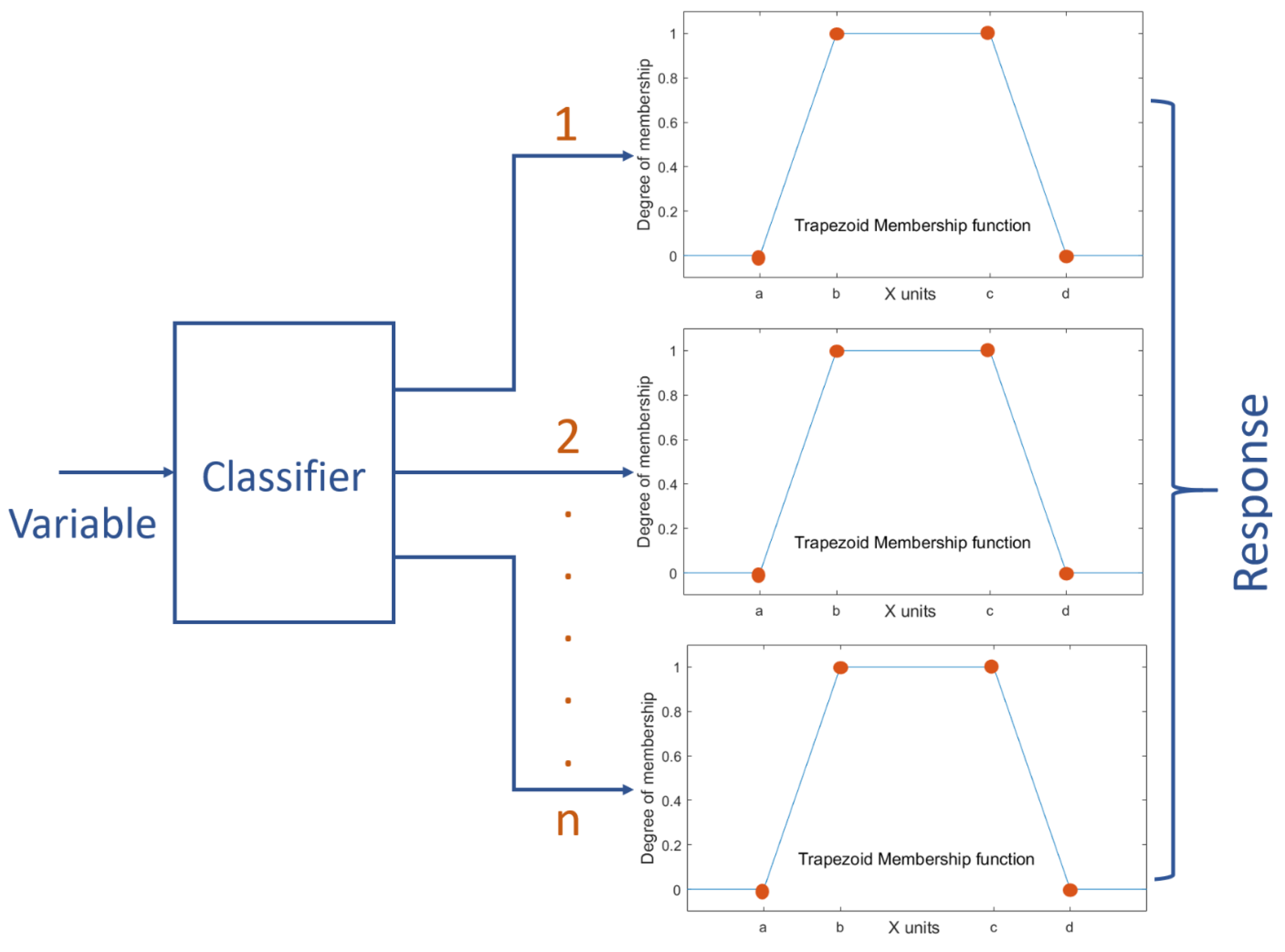
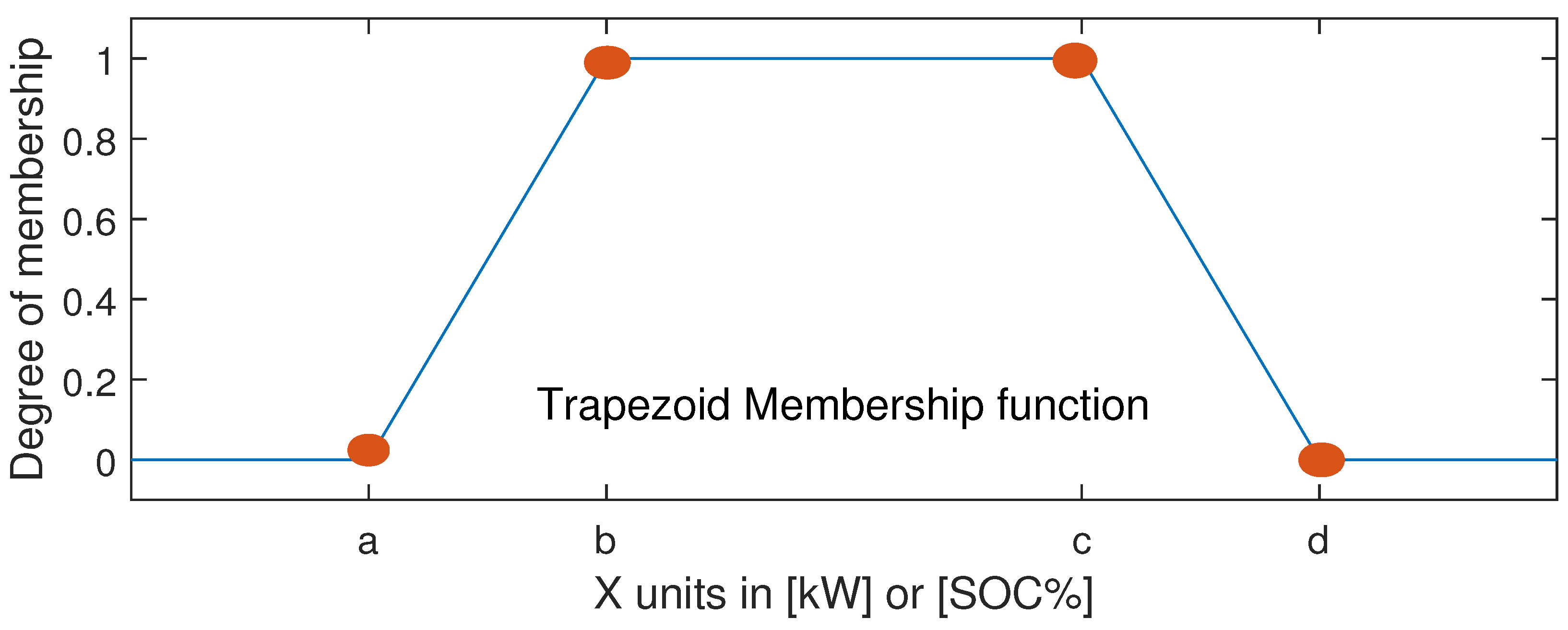
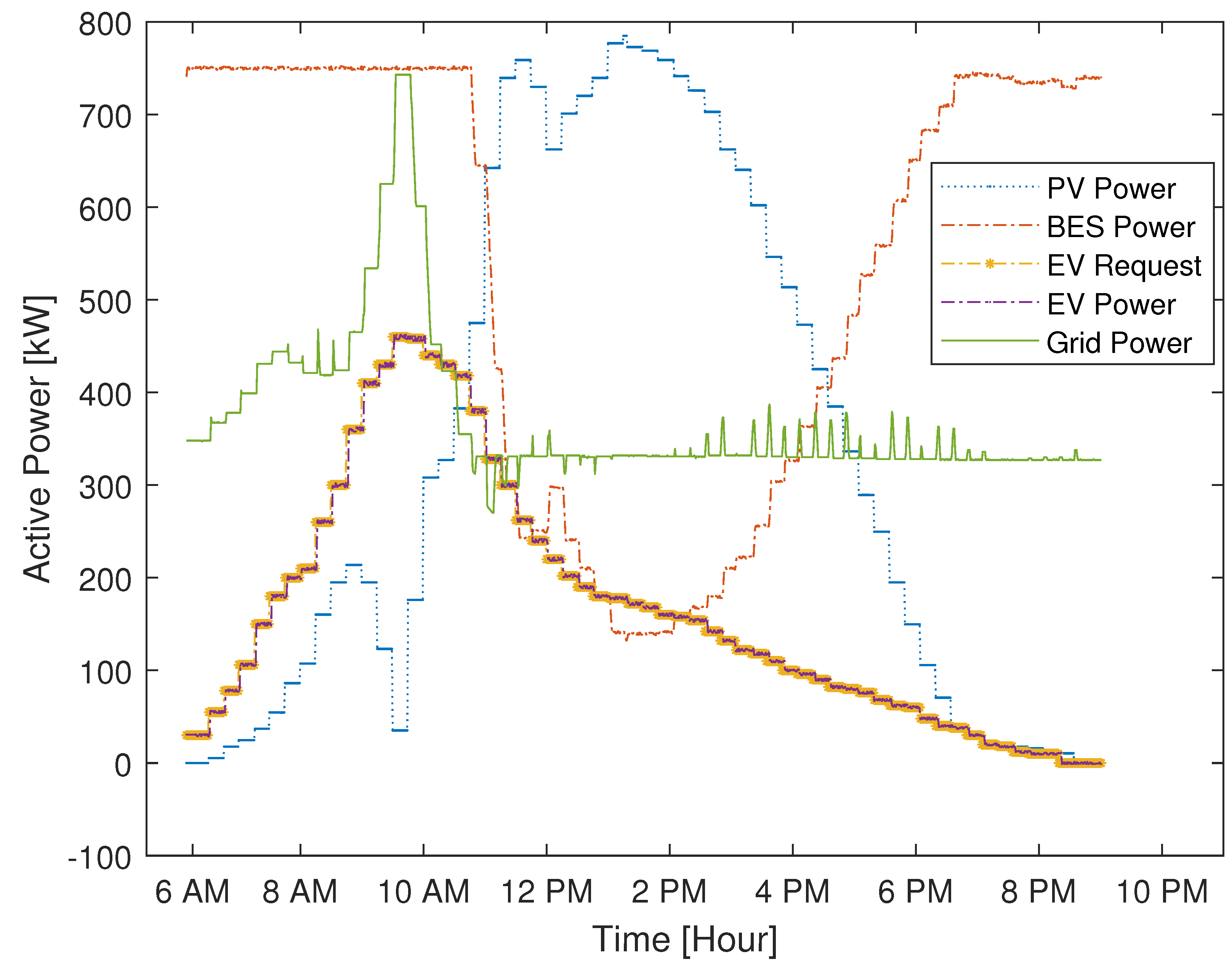
3.1. DERMS Control Algorithm
- power purchased from the upstream grid;
- PV power generated from the DER;
- total power of the connected loads;
- battery power;
- electric vehicle power;
- power that should be regulated.
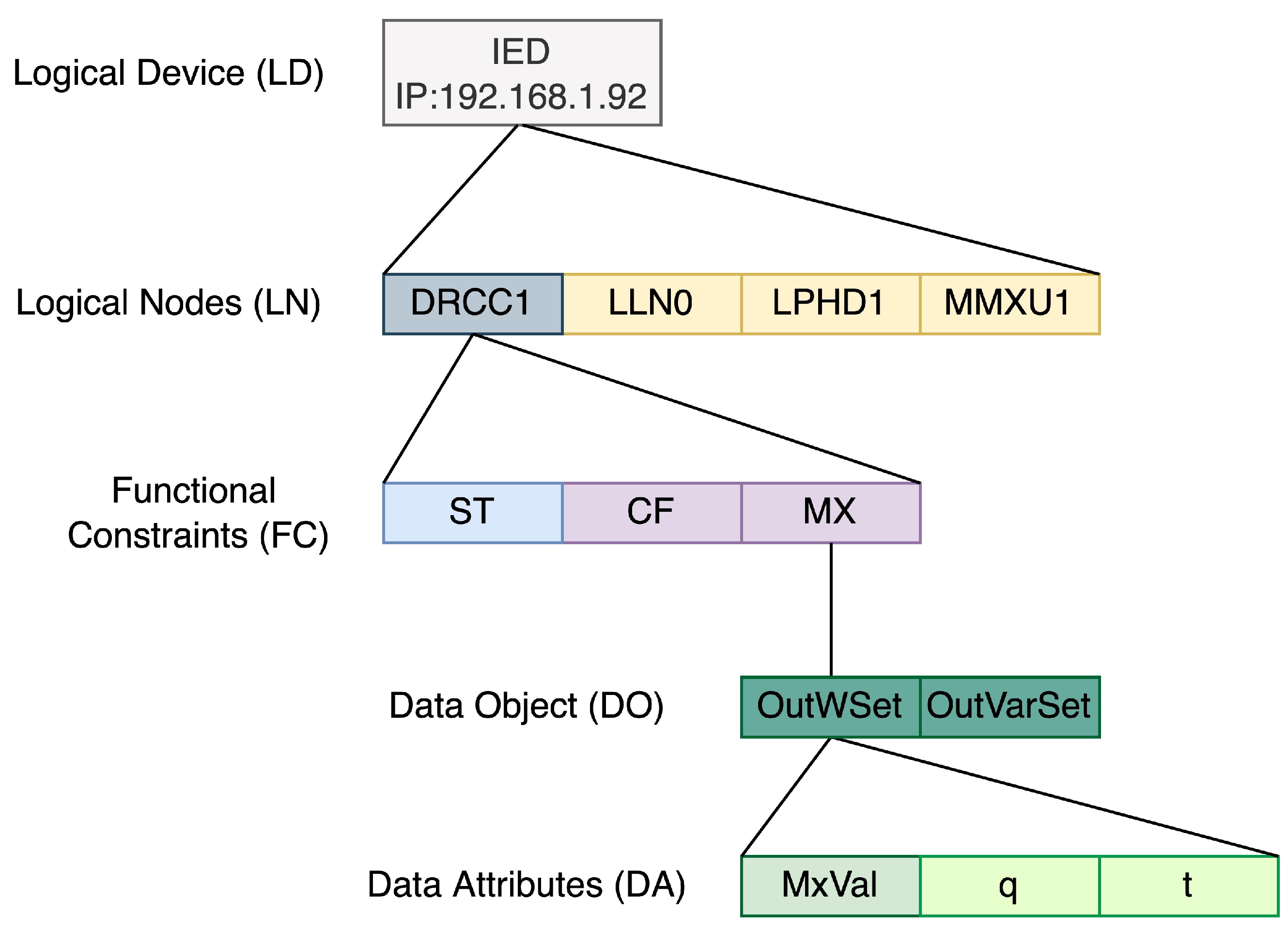
3.2. Information Model of DERs Used in Proposed DERMS
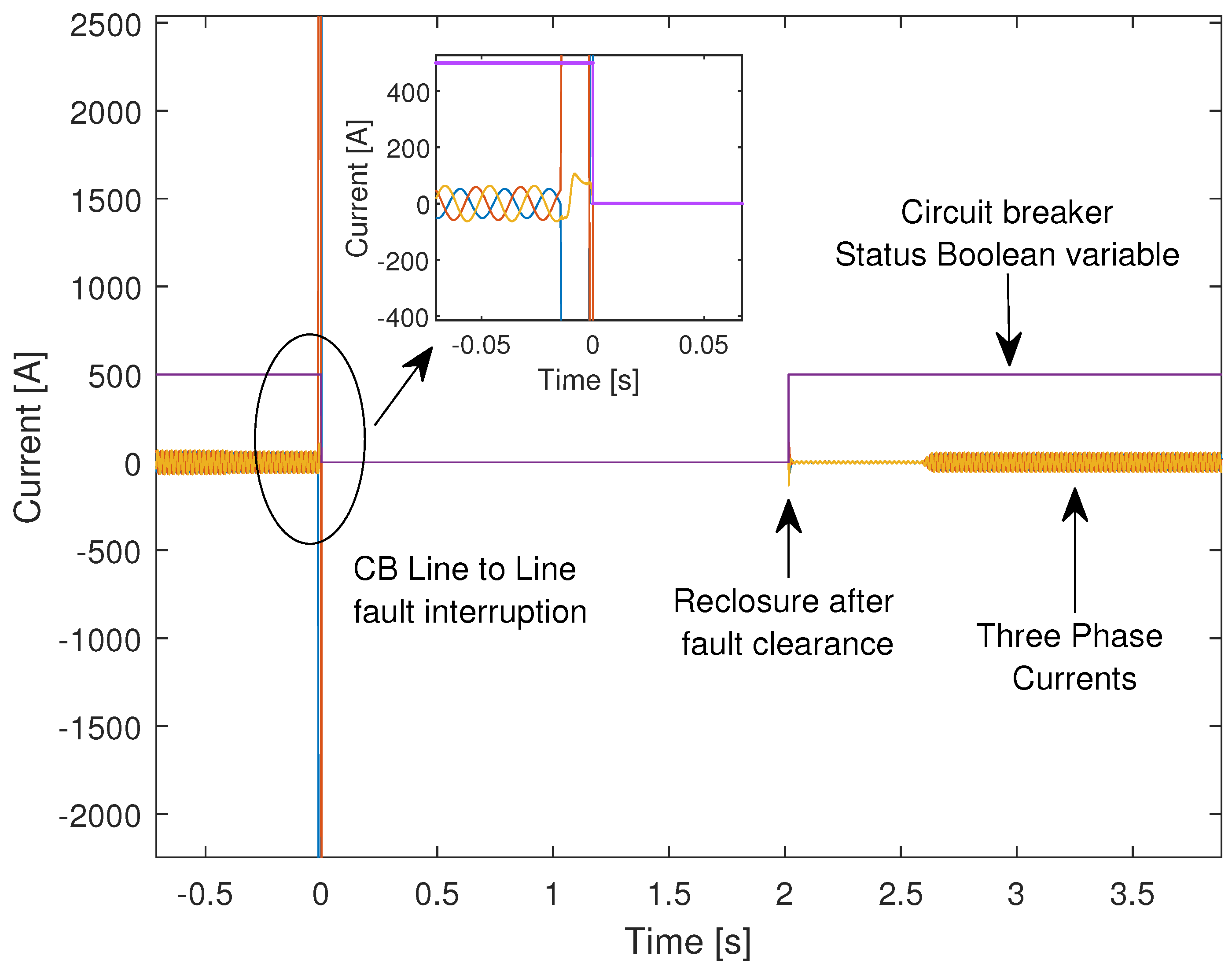
4. Real-Time HIL Simulation Setup and Attack Scenarios
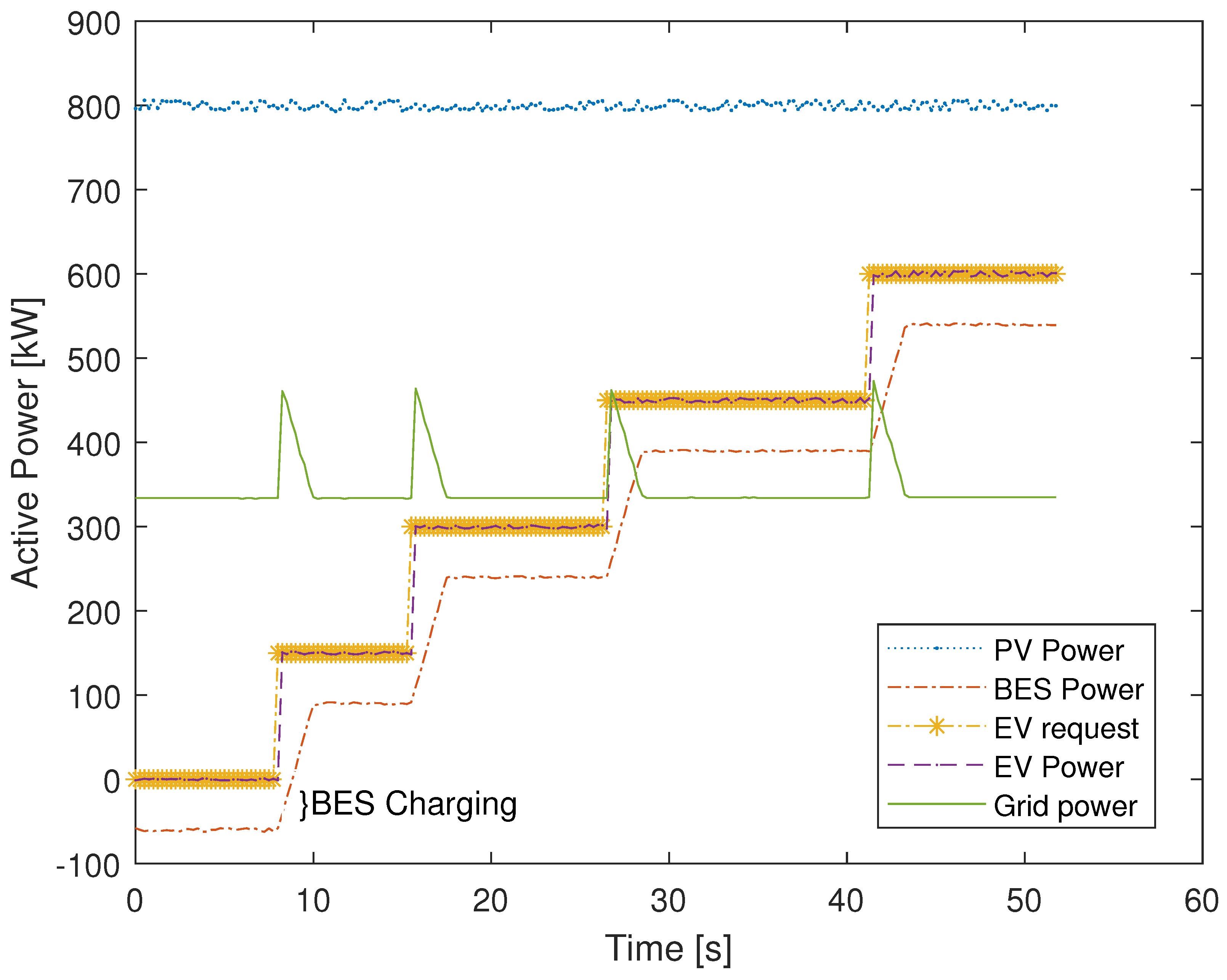
5. Results and Discussion
5.1. DERMS Operation Validation
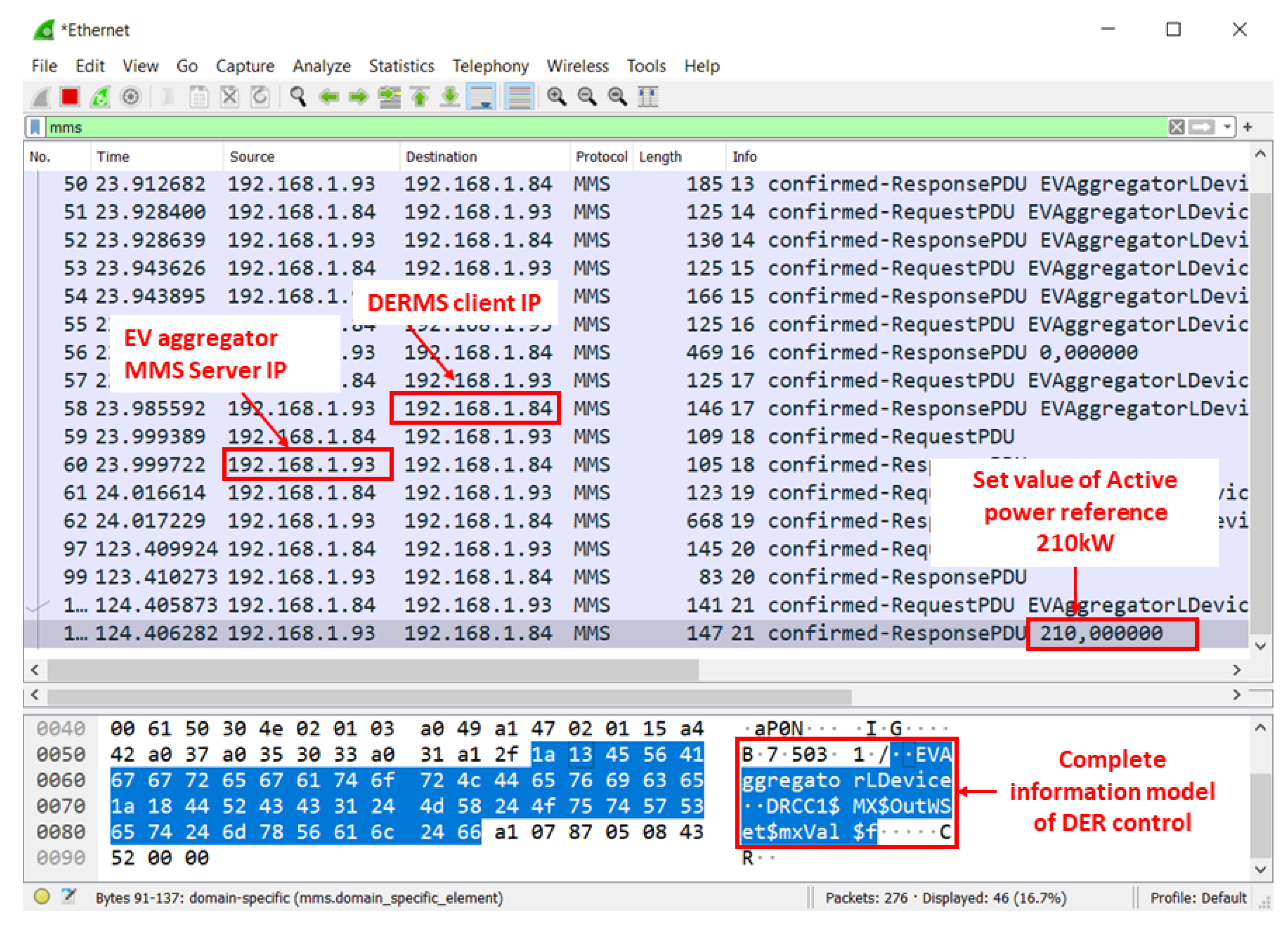
5.2. Man-in-the-Middle Attack Snooping
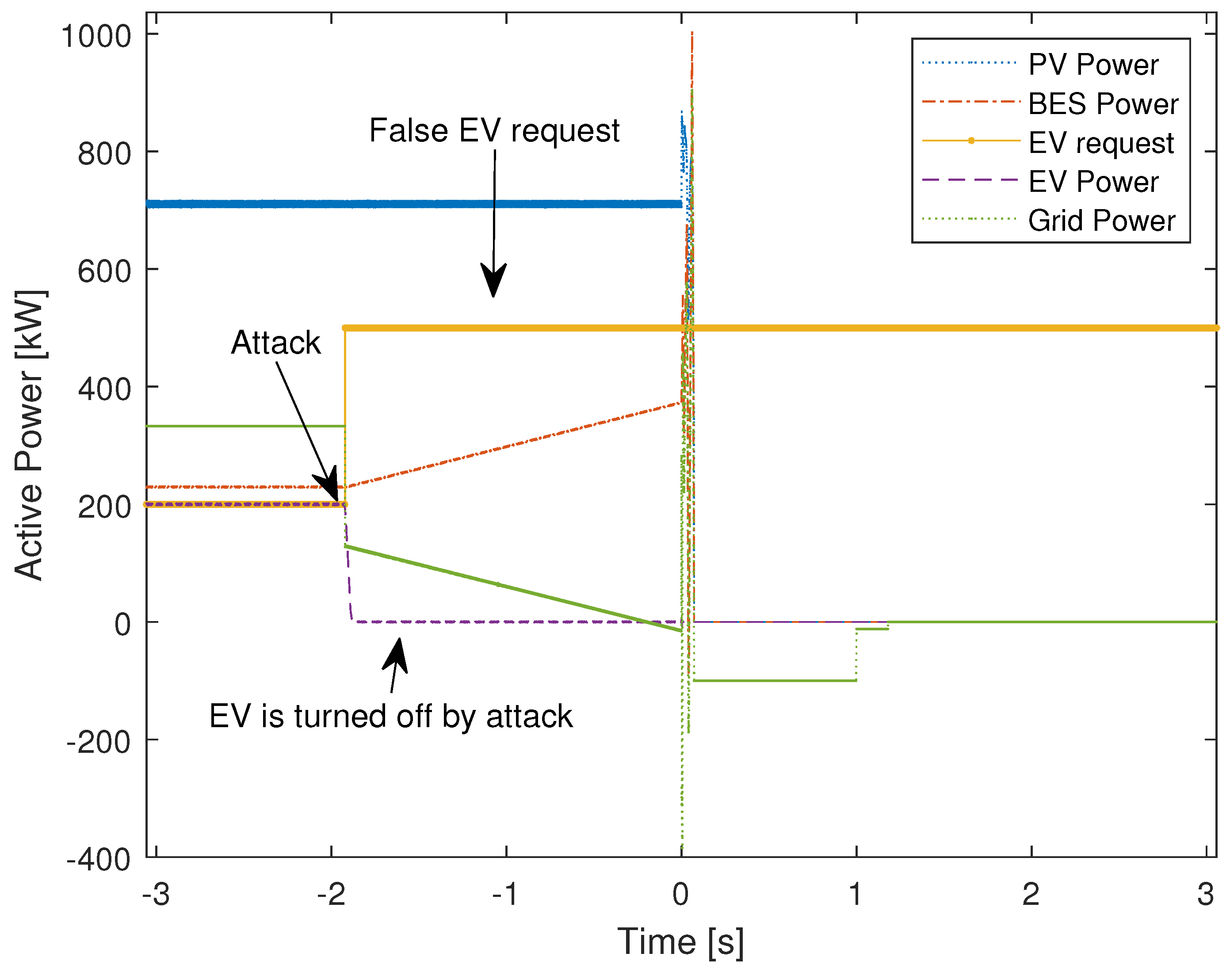
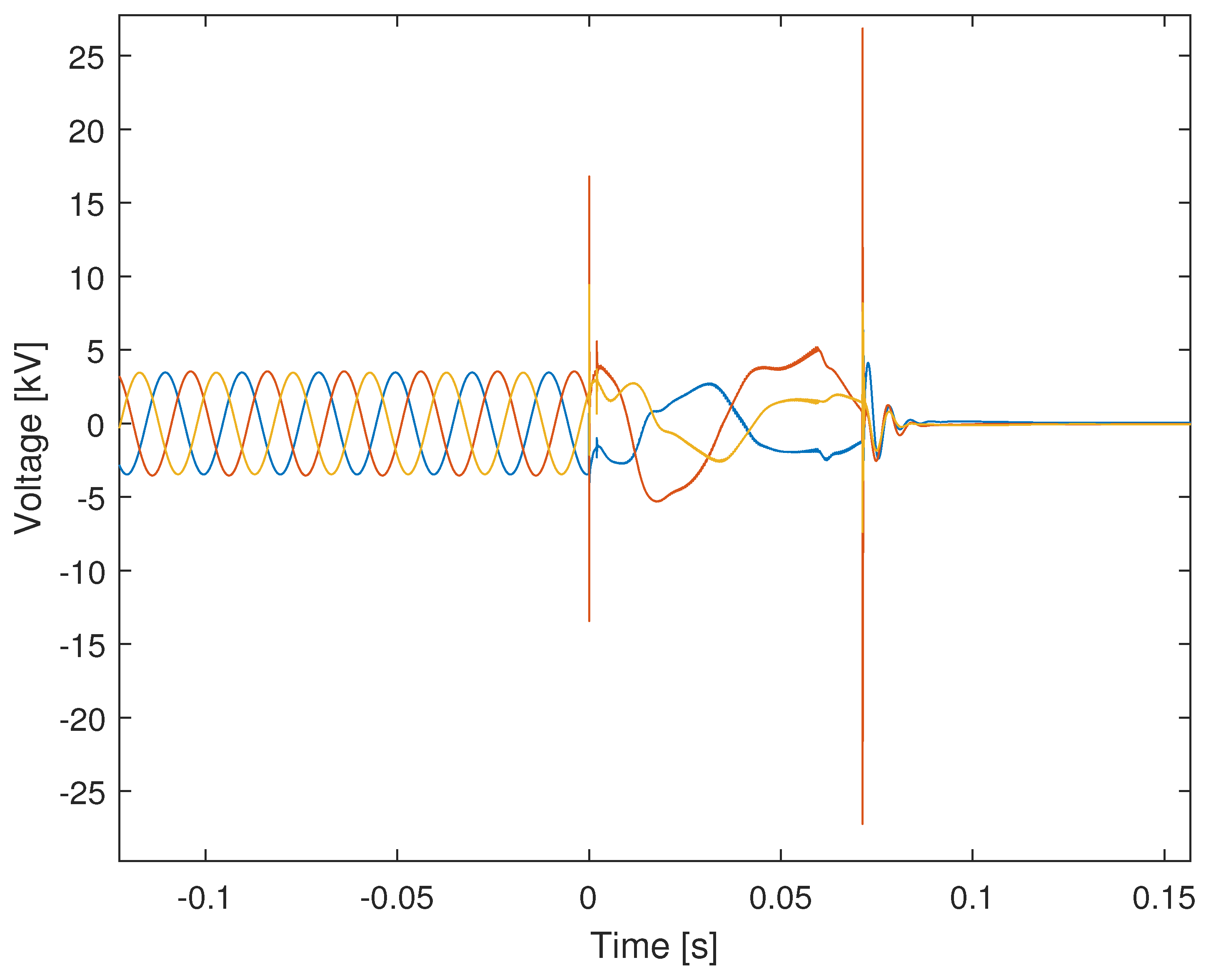
5.3. Man-in-the-Middle Attack: False Data Injection
5.4. Solution for the Caused Cybersecurity Attacks
6. Conclusions
- Implement a DERMS based on reinforcement learning and evaluate the behavior of this type of algorithm when data are altered due to cyber-attack and how they can become robust;
- Compare the reinforcement learning algorithms based on fuzzy logic;
- Detect the attacks with robust algorithms.
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| BES | Battery energy storage |
| CB | Circuit breaker |
| DER | Distributed energy resource |
| DERMS | Distributed energy resource management system |
| DSO | Distribution system operator |
| EMS | Energy management system |
| EV | Electric vehicle |
| GOOSE | Generic object oriented substation event |
| HIL | Hardware in the loop |
| IED | Intelligent electronics device |
| LD | Logical device |
| LN | Logical node |
| DA | Data attribute |
| DO | Data object |
| MMS | Manufacturing message service |
| OCPP | Open charge point protocol |
| PCC | Point of common coupling |
| PV | Photovoltaic |
| SCL | Structured control language |
| SOC | State of charge |
| TSO | Transmission system operator |
References
- Blaabjerg, F.; Yang, Y.; Yang, D.; Wang, X. Distributed power-generation systems and protection. Proc. IEEE 2017, 105, 1311–1331. [Google Scholar] [CrossRef] [Green Version]
- Yadav, A.; Srivastava, L. Optimal placement of distributed generation: An overview and key issues. In Proceedings of the 2014 International Conference on Power Signals Control and Computations (EPSCICON), Thrissur, India, 8–10 January 2014; pp. 1–6. [Google Scholar]
- Islam, M.R.; Lu, H.; Hossain, M.; Li, L. Mitigating unbalance using distributed network reconfiguration techniques in distributed power generation grids with services for electric vehicles: A review. J. Clean. Prod. 2019, 239, 117932. [Google Scholar] [CrossRef]
- Strezoski, L.; Stefani, I. Utility DERMS for Active Management of Emerging Distribution Grids with High Penetration of Renewable DERs. Electronics 2021, 10, 2027. [Google Scholar] [CrossRef]
- Riffonneau, Y.; Bacha, S.; Barruel, F.; Ploix, S. Optimal power flow management for grid connected PV systems with batteries. IEEE Trans. Sustain. Energy 2011, 2, 309–320. [Google Scholar] [CrossRef]
- Jafarian, M.; Soroudi, A.; Keane, A. Distribution System Topology Identification for DER Management Systems Using Deep Neural Networks. In Proceedings of the 2020 IEEE Power and Energy Society General Meeting (PESGM), Orlando, FL, USA, 6 August 2020; pp. 1–5. [Google Scholar] [CrossRef]
- Strezoski, L.; Padullaparti, H.; Ding, F.; Baggu, M. Integration of Utility Distributed Energy Resource Management System and Aggregators for Evolving Distribution System Operators. J. Mod. Power Syst. Clean Energy 2022, 10, 277–285. [Google Scholar] [CrossRef]
- Rahman, I.; Selak, N.; Paaso, E. Distributed Energy Resource Management System (DERMS) solution for feeder Voltage Management for Utility integrated DERs. In Proceedings of the 2021 IEEE Power & Energy Society Innovative Smart Grid Technologies Conference (ISGT), Washington DC, USA, 21–25 June 2021; pp. 1–5. [Google Scholar]
- Albertini, A.D.R.; Yabe, V.T.; Di Santoz, S.G.; Juniorx, G.M. An Overview of Distributed Energy Resources Management System Guidelines and Functional Coverage. In Proceedings of the 2022 IEEE International Conference on Power Electronics, Smart Grid, and Renewable Energy (PESGRE), Trivandrum, India, 2–5 January 2022; pp. 1–6. [Google Scholar]
- Nowak, S.; Tehrani, N.; Metcalfe, M.S.; Eberle, W.; Wang, L. Cloud-based DERMS test platform using real-time power system simulation. In Proceedings of the 2018 IEEE Power & Energy Society General Meeting (PESGM), Portland, OR, USA, 5–10 August 2018; pp. 1–5. [Google Scholar]
- Ilic, M.D.; Jaddivada, R.; Korpas, M. Interactive protocols for distributed energy resource management systems (DERMS). IET Gener. Transm. Distrib. 2020, 14, 2065–2081. [Google Scholar] [CrossRef]
- Onunkwo, I.; Wright, B.; Cordeiro, P.; Jacobs, N.; Lai, C.; Johnson, J.; Hutchins, T.; Stout, W.; Chavez, A.; Richardson, B.T.; et al. Cybersecurity Assessments on Emulated DER Communication Networks; SAND2019-2406; Sandia National Laboratories: Albuquerque, NM, USA, 2019. [CrossRef]
- Neaimeh, M.; Andersen, P.B. Mind the gap-open communication protocols for vehicle grid integration. Energy Inform. 2020, 3, 1–17. [Google Scholar] [CrossRef] [Green Version]
- Schmutzler, J.; Andersen, C.A.; Wietfeld, C. Evaluation of OCPP and IEC 61850 for smart charging electric vehicles. World Electr. Veh. J. 2013, 6, 863–874. [Google Scholar] [CrossRef] [Green Version]
- Huang, R.; Wang, Y.; Shi, W.; Yao, D.; Hu, B.; Chu, C.C.; Gadh, R. Integration of IEC 61850 into a Vehicle-to-Grid system with networked electric vehicles. In Proceedings of the 2015 IEEE Power & Energy Society Innovative Smart Grid Technologies Conference (ISGT), Bangkok, Thailand, 3–6 November 2015; pp. 1–5. [Google Scholar]
- Hänsch, K.; Naumann, A.; Wenge, C.; Wolf, M. Communication for battery energy storage systems compliant with IEC 61850. Int. J. Electr. Power Energy Syst. 2018, 103, 577–586. [Google Scholar] [CrossRef]
- Palahalli, H.; Ragaini, E.; Gruosso, G. Smart Grid Simulation Including Communication Network: A Hardware in the Loop Approach. IEEE Access 2019, 7, 90171–90179. [Google Scholar] [CrossRef]
- Mackiewicz, R. Technical overview and benefits of the IEC 61850 standard for substation automation. In Proceedings of the 2006 Power Systems Conference and Exposition, Atlanta, GA, USA, 29 October–1 November 2006; pp. 623–630. [Google Scholar]
- Hemmati, M.; Palahalli, H.; Gruosso, G.; Grillo, S. Interoperability analysis of IEC61850 protocol using an emulated IED in a HIL microgrid testbed. In Proceedings of the 2021 IEEE International Conference on Communications, Control, and Computing Technologies for Smart Grids (SmartGridComm), Aachen, Germany, 25–28 October 2021; pp. 152–157. [Google Scholar]
- Palahalli, H.; Hemmati, M.; Ragaini, E.; Gruosso, G. Hardware In The Loop Simulation of the Smart Grid with the inclusion of IEC61850 Communication Protocol. In Proceedings of the IECON 2021—47th Annual Conference of the IEEE Industrial Electronics Society, Online, 3–16 October 2021; pp. 1–6. [Google Scholar]
- Burbano, R.A.G.; Gutierrez, M.L.O.; Restrepo, J.A.; Guerrero, F.G. IED design for a small-scale microgrid using IEC 61850. IEEE Trans. Ind. Appl. 2019, 55, 7113–7121. [Google Scholar] [CrossRef]
- Rajkumar, V.S.; Tealane, M.; Ştefanov, A.; Palensky, P. Cyber attacks on protective relays in digital substations and impact analysis. In Proceedings of the 2020 8th Workshop on Modeling and Simulation of Cyber-Physical Energy Systems, Sydney, Australia, 21 April 2020; pp. 1–6. [Google Scholar]
- Schmutzler, J.; Wietfeld, C.; Andersen, C.A. Distributed energy resource management for electric vehicles using IEC 61850 and ISO/IEC 15118. In Proceedings of the 2012 IEEE Vehicle Power and Propulsion Conference, Seoul, Korea, 9–12 October 2012; pp. 1457–1462. [Google Scholar]
- Ali, I.; Hussain, S.S. Communication design for energy management automation in microgrid. IEEE Trans. Smart Grid 2016, 9, 2055–2064. [Google Scholar] [CrossRef]
- Nadeem, F.; Aftab, M.A.; Hussain, S.; Ali, I.; Tiwari, P.K.; Goswami, A.K.; Ustun, T.S. Virtual power plant management in smart grids with XMPP based IEC 61850 communication. Energies 2019, 12, 2398. [Google Scholar] [CrossRef] [Green Version]
- Biswas, P.P.; Tan, H.C.; Zhu, Q.; Li, Y.; Mashima, D.; Chen, B. A synthesized dataset for cybersecurity study of IEC 61850 based substation. In Proceedings of the 2019 IEEE International Conference on Communications, Control, and Computing Technologies for Smart Grids (SmartGridComm), Beijing, China, 21–23 October 2019; pp. 1–7. [Google Scholar]
- Kang, B.; Maynard, P.; McLaughlin, K.; Sezer, S.; Andrén, F.; Seitl, C.; Kupzog, F.; Strasser, T. Investigating Cyber-Physical attacks against IEC 61850 photovoltaic inverter installations. In Proceedings of the 2015 IEEE 20th Conference on Emerging Technologies & Factory Automation (ETFA), Luxembourg, 8–11 September 2015; pp. 1–8. [Google Scholar]
- IEEE 13 Node Test Feeder Data. Available online: https://site.ieee.org/pes-testfeeders/resources/ (accessed on 1 June 2022).
- Palahalli, H.; Ragaini, E.; Gruosso, G. Real-time smart microgrid simulation: The integration of communication layer in electrical simulation. In Proceedings of the 2021 22nd IEEE International Conference on Industrial Technology (ICIT), Valencia, Spain, 10–12 March 2021; Volume 1, pp. 631–636. [Google Scholar]
- Sparn, B.; Krishnamurthy, D.; Pratt, A.; Ruth, M.; Wu, H. Hardware-in-the-loop (HIL) simulations for smart grid impact studies. In Proceedings of the 2018 IEEE Power & Energy Society General Meeting (PESGM), Portland, OR, USA, 5–10 August 2018; pp. 1–5. [Google Scholar]
- Kim, J.; Park, K.; Ahn, B.; Chor, J.; Noh, Y.; Won, D.; Kim, T. Real-Time Hardware-in-the-Loop Distributed Energy Resources System Testbed using IEEE 2030.5 Standard. In Proceedings of the 2021 IEEE PES Innovative Smart Grid Technologies-Asia (ISGT Asia), Brisbane, Australia, 8 December 2021; pp. 1–5. [Google Scholar]
- Palahalli, H.; Huo, Y.; Gruosso, G. Real time simulation of photovoltaic system using fpga. In Proceedings of the 2018 International Symposium on Power Electronics, Electrical Drives, Automation and Motion (SPEEDAM), Amalfi, Italy, 20–22 June 2018; pp. 865–870. [Google Scholar]
- Rancilio, G.; Lucas, A.; Kotsakis, E.; Fulli, G.; Merlo, M.; Delfanti, M.; Masera, M. Modeling a large-scale battery energy storage system for power grid application analysis. Energies 2019, 12, 3312. [Google Scholar] [CrossRef] [Green Version]
- Dong, W.; Yang, Q.; Fang, X.; Ruan, W. Adaptive optimal fuzzy logic based energy management in multi-energy microgrid considering operational uncertainties. Appl. Soft Comput. 2021, 98, 106882. [Google Scholar] [CrossRef]
- Palahalli, H.; Maffezzoni, P.; Gruosso, G. Gaussian copula methodology to model photovoltaic generation uncertainty correlation in power distribution networks. Energies 2021, 14, 2349. [Google Scholar] [CrossRef]
- Islam, M.S.; Mithulananthan, N. Daily EV load profile of an EV charging station at business premises. In Proceedings of the 2016 IEEE Innovative Smart Grid Technologies-Asia (ISGT-Asia), Melbourne, Australia, 28 November–1 December 2016; pp. 787–792. [Google Scholar]


| System | Nominal Active Power (kW) | Nominal Apparent Power (kVA) |
|---|---|---|
| Battery energy system | 750 | 1500 |
| Photovoltaic system | 800 | 1200 |
| EV aggregator | 600 | 800 |
| System | Classification | a | b | c | d |
|---|---|---|---|---|---|
| 1. Available | −800 | −800 | −15 | 0 | |
| Power demand (kW) | 2. Low | 0 | 20 | 230 | 250 |
| 3. Medium | 250 | 270 | 900 | 950 | |
| 4. High | 950 | 980 | 980 | 980 | |
| 1. Low | 0 | 0 | 12 | 15 | |
| BES SOC% | 2. Medium | 15 | 20 | 85 | 90 |
| 3. High | 90 | 95 | 100 | 100 | |
| 1. Charge fully | −750 | −750 | −270 | −250 | |
| 2. Charge partially | −250 | −230 | −15 | −5 | |
| BES reference output (kW) | 3. Idle | −4 | 0 | 0 | +4 |
| 4. Discharge partially | 5 | 15 | 230 | 250 | |
| 5. Discharge fully | 250 | 270 | 750 | 750 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Palahalli, H.; Hemmati, M.; Gruosso, G. Analysis and Design of a Smart Controller for Managing Penetration of Renewable Energy Including Cybersecurity Issues. Electronics 2022, 11, 1861. https://doi.org/10.3390/electronics11121861
Palahalli H, Hemmati M, Gruosso G. Analysis and Design of a Smart Controller for Managing Penetration of Renewable Energy Including Cybersecurity Issues. Electronics. 2022; 11(12):1861. https://doi.org/10.3390/electronics11121861
Chicago/Turabian StylePalahalli, Harshavardhan, Marziyeh Hemmati, and Giambattista Gruosso. 2022. "Analysis and Design of a Smart Controller for Managing Penetration of Renewable Energy Including Cybersecurity Issues" Electronics 11, no. 12: 1861. https://doi.org/10.3390/electronics11121861
APA StylePalahalli, H., Hemmati, M., & Gruosso, G. (2022). Analysis and Design of a Smart Controller for Managing Penetration of Renewable Energy Including Cybersecurity Issues. Electronics, 11(12), 1861. https://doi.org/10.3390/electronics11121861







