On Wide-Area IoT Networks, Lightweight Security and Their Applications—A Practical Review
Abstract
1. Introduction
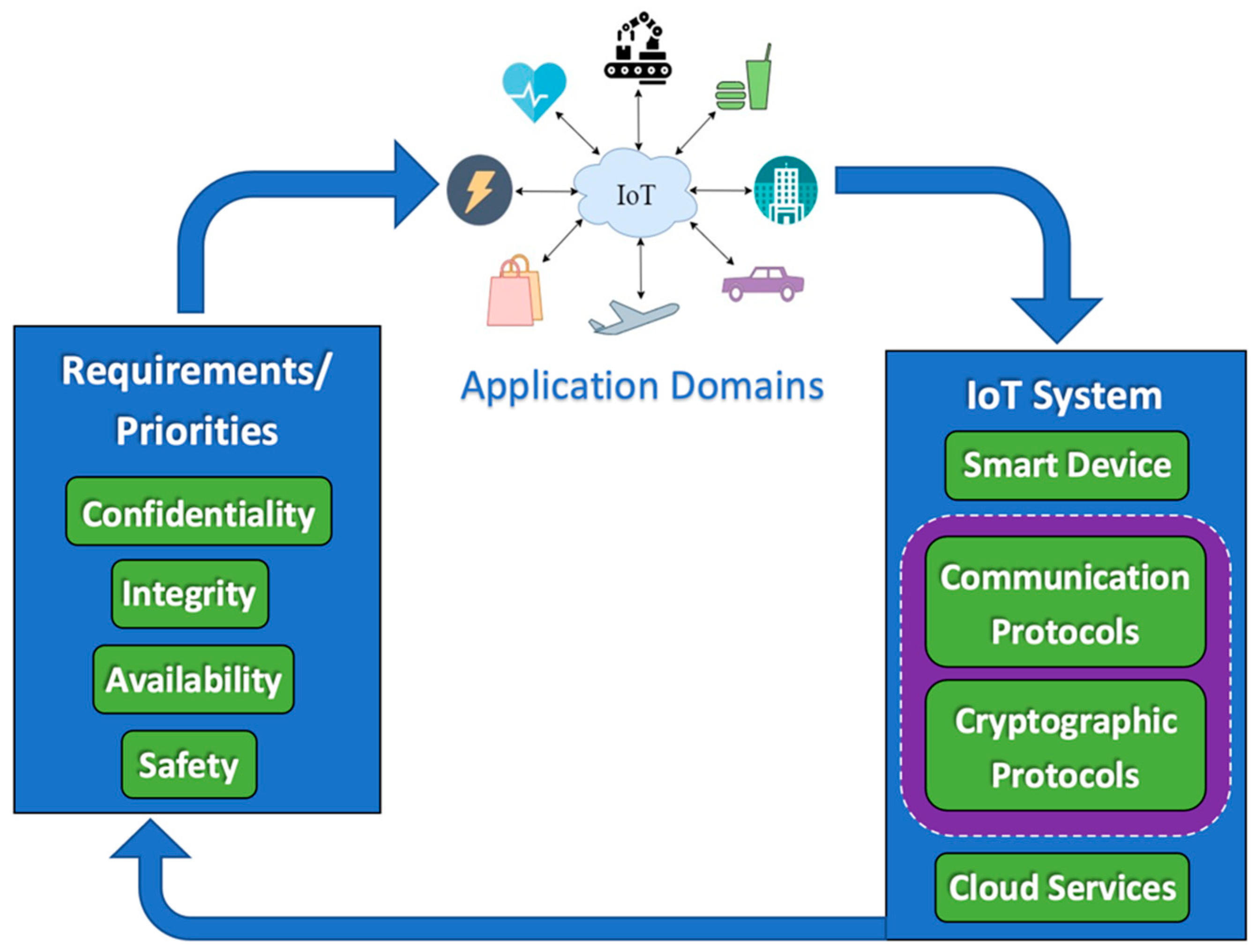
1.1. IoT System Implementation Challenges
1.2. Current Work Contributions
- The IoT device, its communication protocols, and security features;
- The application domain and how each application adopts the security features.
- Apply the CIA triad to explain standard communication protocols as well as lightweight cryptography, in different application domains. The goal is to explain a few protocols in detail while focusing on low-energy and long-range communication technologies.
- Provide a tutorial on IoT lightweight security that is accessible to even non-technical readers. This will illustrate the trade-offs of different protocols for different applications, and provide a good foundation for IoT communications.
- Explain and classify lightweight security approaches for AES and ECC algorithms. They are compared to older security techniques, in terms of primitives such as key sizes, number of encryption cycles, and hardware architectures.
- Bridge the gap between hardware and application developers, telecommunication providers, and customers, on the topic of IoT security’s operational priorities and how to apply lightweight security protocols. The main goal is to promote innovation towards the widespread implementation of open IoT systems.
2. Literature Review on IoT and Lightweight Security Protocols
2.1. Building Blocks
2.2. Standardized Protocols for IoT
- Data link layer protocols such as IEEE 802.15.4 and long-range WAN (LoRaWAN).
- Network layer protocols such as 6LoWPAN, which allows devices to connect to IPv6 routers with compressed IP headers.
- Application layer protocols: they compare CoAP, which runs over UDP, and message queuing telemetry transport (MQTT), which runs over TCP.
- Domain name service (DNS) protocols translate between a domain name and an IP address since smart devices can join and leave the network at any time. Multicast domain name service (mDNS) supports multiple devices in the same DNS query, DNS service discovery (DNS-SD) discovers devices that provide a certain service, and UBonjour combines mDNS and DNS-SD.
- IEEE802.15.4 at the physical/data link layer, which does not specify a key management protocol.
- IPv6LowPAN, which they reference as an adaptation layer that allows IPv6 packets to be carried over IEEE 802.15.4 frames.
- IPv6 Routing Protocol for Low Power and Lossy Networks (RPL) is the routing protocol at the network layer, along with its two security modes: preinstalled keys, or authenticated mode, where nodes such as routers obtain keys from a certification authority (CA).
- CoAP at the application layer and DTLS, which has different authentication modes, such as pre-shared keys, raw public keys, and certificate mode. When COAP is used with DTLS, it is recommended to use raw public keys, which means that the public keys are pre-programmed in the devices at the time of manufacturing. All devices in the same network know the other devices’ public keys.
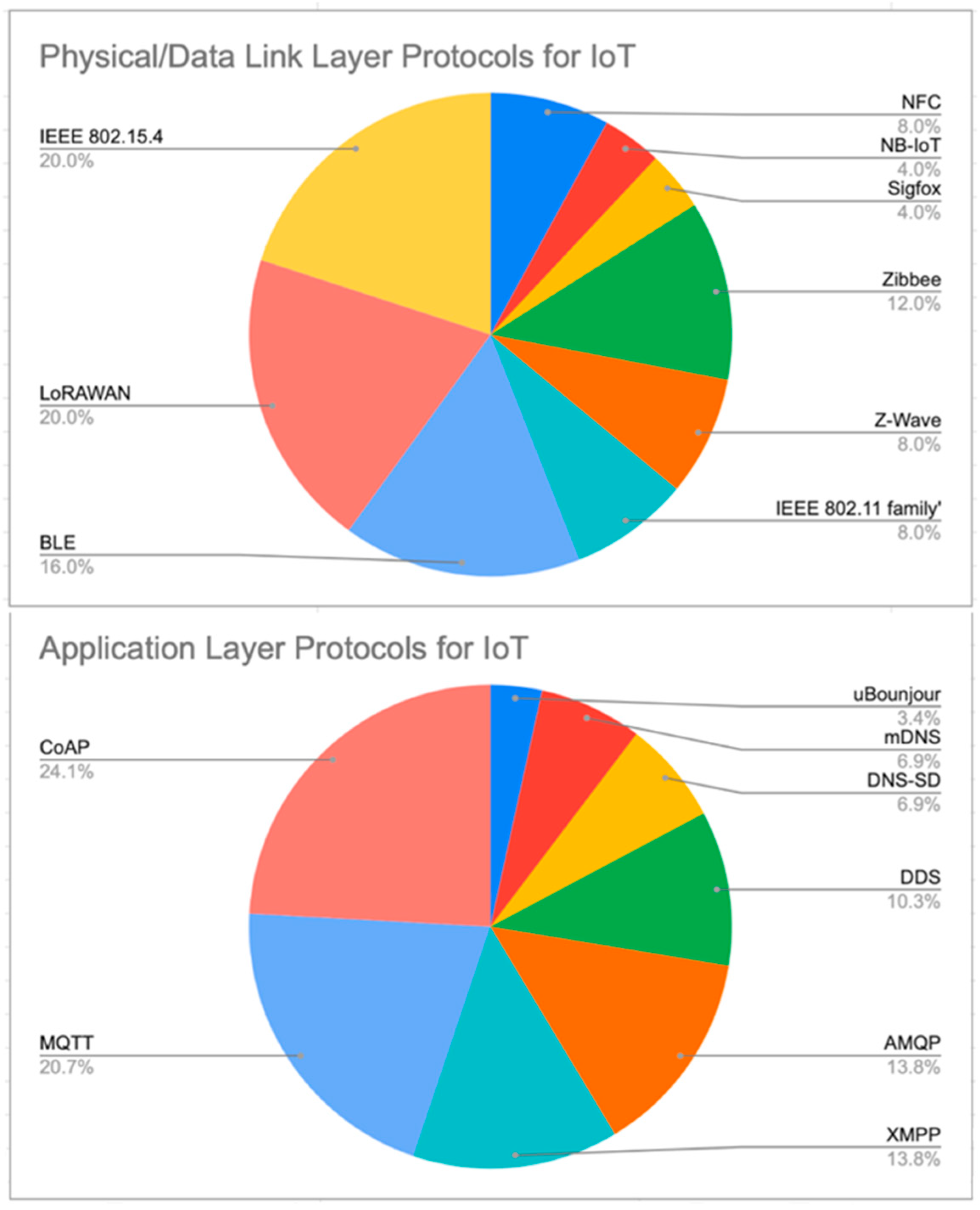
- For the physical and data link protocols that are described in Table 1, it can be concluded that IEEE 802.15.4 and LoRaWAN are the most adopted protocols. For instance, IEEE 802.15.4 has been described in five of the eight papers, i.e., around 24% of the papers. IEEE 802.15.4 is a good example of short-range IoT and LoRaWAN for long-range applications. Moreover, the IEEE 802.15.4 security architecture provides a foundation for other protocols, such as Zigbee, BLE, and LoRaWAN.
- At the network layer, the consensus is 6LoWPAN as the main protocol used in the adaptation layer. The routing protocol RPL is mentioned in a few studies, but not as often as 6LoWPAN.
- At the application layer, there is a close tie between CoAP and MQTT. Although it is shown in Figure 4 that the percentage of CoAP is slightly higher, several studies, such as [27], which described a more specific application domain, mentioned that MQTT is definitely one of the most popular application layer protocols for IoT.
2.3. Lightweight Solutions for IoT
- Smart devices such as sensors and actuators.
- Edge computing networks are composed of smartphones, Wi-Fi routers, or LoRa gateways. They support device mobility and process data closer to the smart device.
- Fog computing networks have more powerful routers, industrial switches, and servers.
- Cloud computing components such as the Amazon Web Services (AWS) cloud platform, where data are stored, visualized, and analyzed.
2.4. Challenges and Requirements in Implementing IoT
- -
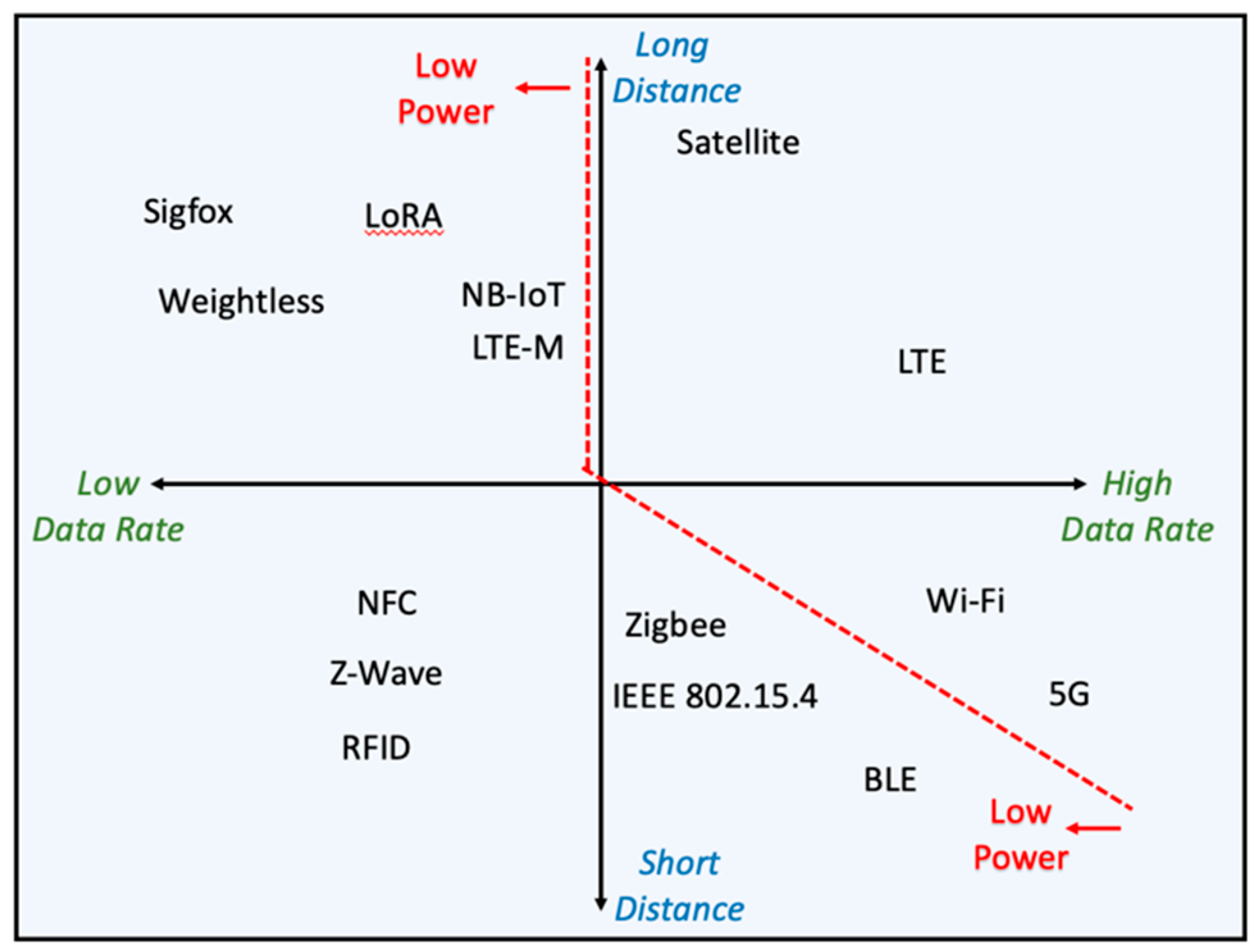
- Next, this paper reviews the physical and data link layer technologies and how they provide security given the type of application. The type of application field determines the IoT system’s security requirements in terms of what is more important to be provided: confidentiality, integrity, availability, and/or safety. After reviewing the first category of papers (Section 2.2), trends are identified regarding which communication protocols are being adopted for IoT systems. Among them, LoRAWAN, NB-IoT, and Sigfox are the physical and data link layer protocols that will be explained in detail in Section 3 from the point of view of the CIA triad and IoT applications. They have been cited in the first category of papers and are adopted in the industry.
- -
- Regarding the second category of papers, which showed a variety of new lightweight encryption protocols, Section 4 focuses on AES encryption and recent research studies that aim to make AES more suitable for IoT devices. AES is a popular algorithm for regular computer systems, and because it is such a well-established standard, it is practical to review how AES encryption is being adapted for IoT systems. Another encryption algorithm that has been mentioned in several category 2 and 3 papers is ECC, which is a public-key encryption algorithm typically used for key distribution that has great potential for industry; however, ECC is computationally intensive. Thus, Section 4 in this paper also discusses approaches to make ECC more lightweight for IoT systems.
3. Long-Range, Low-Power IoT Communication Protocols and Their Security
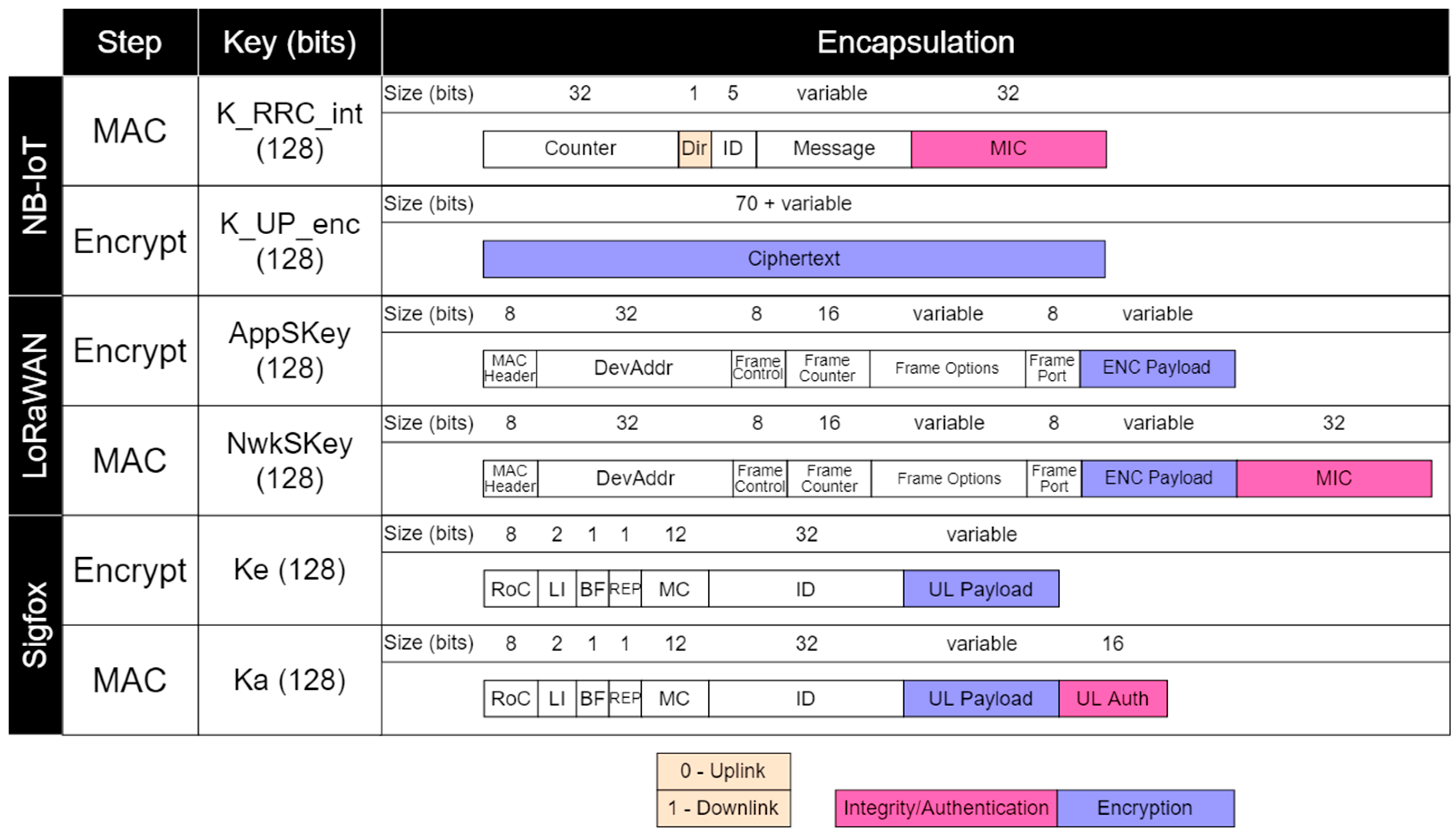
- security level zero means no security;
- security levels one to three provide only integrity and authentication by generating different sizes of message integrity code (MIC);
- security level four provides only confidentiality and security;
- security levels five to seven provide integrity, authentication, and confidentiality.
- Encrypt-and-MAC (E&M), where the encrypted data and the MAC are generated independently.
- Encrypt-then-MAC (EtM), where the encryption is done first, and then the MAC is calculated using the encrypted data as one of the inputs.
- MAC-then-Encrypt (MtE), where the MAC is produced first, and then it is encrypted together with the rest of the data.
3.1. LoRaWAN
- Within the LoRa physical layer specification, LoRaWAN uses different ISM bands depending on the geographic region. In North America, LoRa uses 72 uplink channels and eight downlink channels in the 902–928 MHz ISM band [25]. The channels are modulated using Chirp-Spread Spectrum (CSS) with multiple Spreading Factors (SF). SFs are chosen depending on the application since different SFs provide different transmission rates, which can vary from 300 bps to 50 kbps [49]. Higher SFs are associated with lower data rates. The advantage of a spread spectrum is that multiple nodes can transmit at the same time within the same physical channel. LoRaWAN nodes can initiate transmission at any time using a random-access mode similar to unslotted ALOHA networks [50].
- LoRa network topology has in the uplink the gateways or base stations (BS), which relay data packets from motes to a network server at the core IP network [51]. The server performs security functions, such as authentication, checking the packets’ integrity, and removing duplicate packets. For the downlink, i.e., from the application server to the mote, the network server usually stores data from the user application to send to end devices.
- The downlink and uplink transmissions depend on the type of LoRaWAN motes [47]:
- Class A devices are battery-powered devices that “wake up” to send data. All transmissions are initiated by the device in the uplink. These devices conserve energy; however, they experience the longest downlink latency because they can only receive downlink data after an uplink transmission.
- Class B devices are battery-powered actuators that have scheduled receive windows. They listen for commands to perform an action. Because of the receive windows, these devices have low downlink latency while still being energy-efficient.
- Class C devices in Class C are actuators that are not restricted by battery life and require the fastest response time. The receive window is always open, except when there is an uplink transmission.
3.2. NB-IoT
- Stand-alone mode operates on a separate Global System for Mobile (GSM) communications channel, with a bandwidth of 200 kHz.
- Guard-band mode operates on the side bands of the LTE channel, with 180 kHz bandwidth, and it uses one physical resource block (PRB) of the LTE band.
- In-band mode operates in the LTE band and it also uses one PRB, at 180 kHz bandwidth. From a cellular provider’s point of view, the latter mode is considered the best option, because it maximizes the provider’s channel assignments [61].
- Power Saving Mode (PSM) allows the UE to enter a sleep mode, from which it can wake itself up at any time to transmit data.
- Extended Discontinuous Reception (eDRX), in which the UE enters sleep mode from which it wakes up periodically. These wake-up periods are synchronized with the network, which sends control messages to the device to tell it to return to idle mode, receive data, or request to transmit data.
3.3. C-UNB/Sigfox
3.4. Summary of LPWA Networks
4. Emerging Lightweight Security Approaches
- Lightweight block cipher, which includes smaller block and key sizes, simpler rounds, and key schedules.
- Lightweight hash function, with enhancements such as smaller inputs and smaller outputs.
- High-performance system and whether it has a custom CPU or crypto-arrays to perform encryption tasks in parallel.
- Low-resource device in terms of software or hardware implementations.
4.1. Symmetric Encryption—Lightweight AES Approaches
4.1.1. Lightweight AES for FPGA
4.1.2. Low-Power AES Data Encryption Architecture (LPADA)
- Low-power S-Box: an ultra-low-power Content Addressable Memory (CAM) stores the S-Box as a look-up table in memory, the contents of which are generated before a data substitution begins. To improve the speed and reduce power in the SubBytes transformation, two approaches are adopted together in LPADA. The first is that the
- CAM uses parallel searching techniques to reduce delays in the SubBytes operation. Second, a low-power CAM architecture is used to discharge entries in the look-up table that do not match the search data. Power management techniques also ensure that the S-Box portion of the memory remains powered at all times to avoid losing its contents.
- Power-gating technique: to reduce power consumption, this technique means that the power supply to certain logic circuits in the FPGA, which are built using transistors, is turned off. This power-gating technique is done in LPADA using P-type metal oxide semiconductor transistors (PMOS), which can switch off power to all components of the AES circuit when in sleep mode. The exception for this is the S-Box, for which power is maintained.
- Dynamic power management (DPM) method: consists of three operation modes that control supply voltages and clock frequencies based on the device’s state. These modes include active, idle, and sleep modes. The active mode consists of all components receiving power and a clock when the device is performing an action request, such as an encryption operation. In idle mode, which is controlled by a five-minute timer, all components receive power while their clock rates are gated to reduce dynamic power consumption. This means that the clock rates are reduced to a lower value or set to zero. If an action request is not made within the five-minute timer interval, the device will enter sleep mode when power to all circuits is switched off, except for the S-Box.
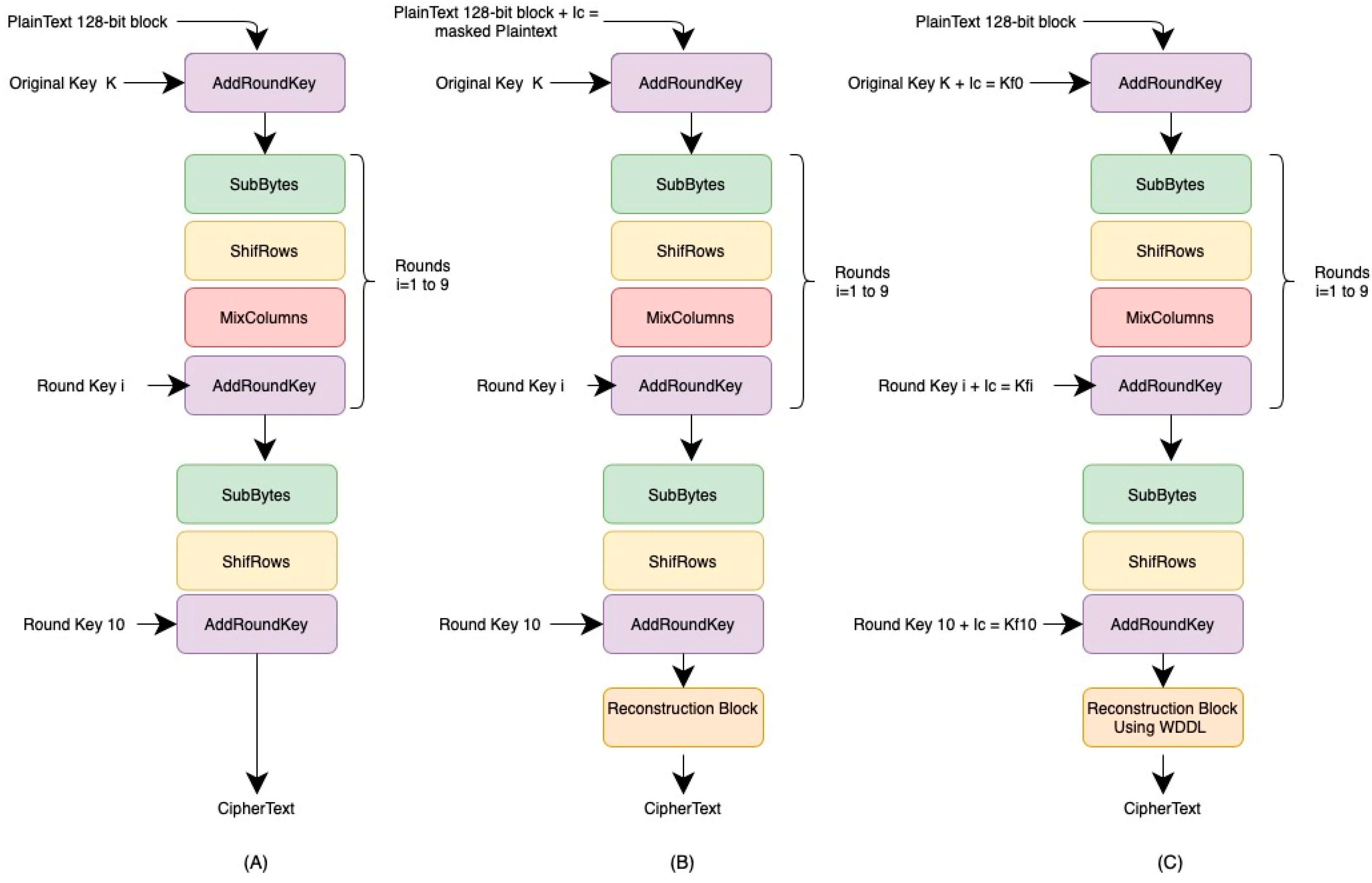
4.1.3. Lightweight AES (LAES)
4.1.4. Authenticated Lightweight Encryption (ALE)
4.1.5. Lightweight Masked AES Implementation
4.1.6. Sixty-Four-Bit AES Key Schedule
- The RotWord transformation is applied to the last column of the previous round key. It performs one circular upwards shift of all bytes within the column.
- The SubBytes transformation is applied using the S-Box.
- The sum of the resulting four bytes, the first column of the previous round key, and the round constant generates the first column of the new round key.
- The round constants are different random numbers generated at each round (r0, r1, …, r7), where each ri is one byte.
- The master key is XORed with the round constants (r0, r1, …, r7) to create a newKey.
- Each byte of the newKey is XORed with each other to generate 32 bytes (k0 to k31). For the bytes that are in a position that is a multiple of eight (e.g., 8, 16, or 24), a special transformation occurs using the SubBytes transformation with the four-bit S-Box from the PRESENT algorithm. Then, a modified MixColums is implemented, followed by another SubBytes transformation with the same four-bit S-Box. These temporary values are also XORed with the bytes of the newKey.
- At the end of each round of key generation, there is also a round constant reverse array (r7, r6, …, r0), which is used in an XOR operation. This reverse array is XORed with the newKey values to generate the new round key.
4.1.7. ISA Extension for AES and SM4
- Selects a byte for the source register rs2;
- Performs one S-Box look-up (SubBytes);
- Performs part of the MixColumns operation;
- Rotates this resulting byte (ShiftRows);
- Performs logic XOR of the result with rs1 which has the round key.
4.1.8. Quark-AES
4.2. Asymmetric Encryption—Lightweight ECC Approaches
4.2.1. Elliptic Curve Diffie–Hellman
4.2.2. Elliptic Curve Digital Signature
4.2.3. ECC Applications in IoT
- ECC Watermark: This is a modified version of the ECC algorithm, where the ECDH key exchange protocol is combined with a new authentication method. ECC Watermark replaces ECDSA with a fragile zero watermarking technique [84]. The watermark is generated during the encryption phase by the sender, who generates a hash of the packet’s source IP address, protocol field, and destination IP address using the sender’s private key. The generated watermark is appended to the packet’s payload. This method utilizes a private-key hash function rather than elliptic curve multiplication operations for signature generation, thus avoiding the complexity of the multiplicative inverse operation. This can be considered a lightweight hash with a smaller output, which is the watermark that is appended to the packet.
- ECIOT: Elliptic Curve Internet of Things (ECIOT) [85] utilizes the ECDH key exchange protocol so that the sender and receiver can establish a session key K. The ECIOT protocol then performs an XOR operation using as inputs K and the data. In summary, ECIOT encrypts and decrypts data with the simple XOR operation, after ECDH generates the shared key K. This can be considered a simpler round of encryption, where one logical operation constitutes one round of the encryption process.
- Lightweight Elliptic Curve Accelerator: The work proposed in [86] is the hardware architecture of an accelerator that performs the scalar multiplication that generates the public key of ECDH. The private key a multiplies the base point G to generate the public key Ha = aG. This means that the base point G is added a number of times. The design goal of the proposed hardware accelerator is to reduce the hardware footprint, or area of the FPGA, to implement this scalar multiplication efficiently.
4.3. Digital Fingerprinting
5. Conclusions and Future Work
- Implement encryption-only functions at the device. For the smart device and the link between the device and the gateway, it simplifies the computation at the device if it supports only the encryption operation. This is practical because, in many IoT systems, the device sends data in the uplink. In this way, even if the device needs to receive encrypted data, a server or base station can use the decryption operation, as in the over-the-air-authentication in LoRa when the Join Server sends a Join Accept message encrypted using the AES-128 ECB decrypt operation. When the device receives the data, it applies the corresponding encryption operation to recover the plaintext. This can be a good approach to reducing the IoT device’s complexity.
- Evaluate link layer security based on how private or how public your network is. Some studies, such as [21], argue that in most cases the link between the smart device and the gateway at the edge network is a “safe haven”, because it is in a protected physical site or a private network. Therefore, security is extremely important in the public domain network, or the commodity internet, that connects the gateway to the application server in the cloud. While this applies to some manufacturing and energy utility networks, not all IoT systems have a protected wireless network to operate on. Many IoT applications, such as Sigfox and Zigbee, support different levels of security. For instance, Sigfox supports clear mode or encryption mode, while Zigbee has multiple levels of security. Therefore, this last-mile link needs to be carefully evaluated to choose an appropriate security level to be implemented in this network.
- Hybrid block-stream lightweight ciphers are a promising solution for IoT. Table 3 presents lightweight block ciphers based on surveys that we reviewed. The most recent algorithm mentioned is from 2013 with SIMON and SPECK, which were created by the National Security Agency (NSA). PRESENT and CLEFIA are two standards that have been mentioned in several papers since they are included in the ISO/IEC 29192 lightweight cryptography standard. In current communication technologies for IoT, such as LoRa, C-UNB/Sigfox, and NB-IoT, we saw the dominance of AES-128 in CTR mode, which was created in the late 1990s. As described in this paper, there have been several efforts to implement lightweight versions of AES as hardware platforms, such as in FPGA, either to reduce gate area implementation, adopt smaller keys, or take fewer rounds to reduce its complexity. However, to the best of our knowledge, there is not much evidence of the widespread implementation of the lightweight encryption algorithms listed in Table 3. One possible reason is that stream ciphers are better suited to resource-constrained devices, as they encrypt bit by bit instead of in blocks of bits. In hardware, series operations can be implemented with fewer hardware resources (i.e., fewer registers or flip-flops) than parallel operations, although series operations are slower than parallel ones, as explained in Section 4.1.8. Hence, stream ciphers tend to have series-like implementations, whereas block ciphers resemble more parallel operations, with blocks of bits processed all at the same time. Although our survey did not cover stream ciphers, Trivium, Grain, and MICKEY are mentioned as popular stream ciphers. One of the new algorithms covered here, the Authenticated Lightweight Encryption (ALE), uses a hybrid approach by mixing AES and a stream cipher called LEX. In a way, AES-CTR was also considered to resemble a stream cipher [44]. Thus, this leads us to continue our research to further investigate hybrid lightweight ciphers, which combine block and stream cipher properties.
- Leverage more robust devices at the edge to implement public-key encryption. Although many survey papers, such as [2,18,24], mention several schemes that use or adapt ECC as a key delivery and authentication method, Lara-Nino et al. [86] proposed a new hardware architecture to implement the scalar multiplication to generate the session keys; it is still unclear if ECC keys can be generated and all the calculations performed at the smart devices. One study made it very clear how ECC-based lightweight cryptography [94] can be used in practical IoT systems. It included experiments in a testbed where ECC was used at the edge, in the gateways, such as Wi-Fi access points or a Sigfox base station. Such devices connect the IoT devices to the public internet. Located at the edge network, they support the smart device’s mobility and can process the smart device’s data (such as filtering sensor data). The proposed scheme uses ECDH as the public/private-key algorithm and to generate the session key for the AES symmetric encryption. Thus, a strong end-to-end encryption exists between the gateway and the application server. The authors explain that the smart device uses a “low key” to encrypt data to the gateway at the edge to provide a minimum level of security. This resembles the proposal by Khan et al. [21], who advocated for applying security at the more powerful nodes that reside at the edge or fog network of the IoT system, which they call ”end-through-node-to-end encryption”.
- Customize or augment the application layer security of standard communication protocols. The only communication technology reviewed in this paper that provided end-to-end encryption was LoRaWAN. Even using LoRa, it is recommended to implement one’s own application-level encryption to provide the required level of end-to-end confidentiality for one’s application. The next application example explains this idea well, in which we use Zigbee but implement our own application layer security scheme in a hybrid FPGA/microcontroller module to protect the data.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Lueth, K.L. Why It Is Called Internet of Things: Definition, History, Disambiguation. Available online: https://iot-analytics.com/internet-of-things-definition/ (accessed on 7 January 2022).
- Ferrag, M.A.; Maglaras, L.A.; Janicke, H.; Jiang, J.; Shu, L. Authentication Protocols for Internet of Things: A Comprehensive Survey. Secur. Commun. Netw. 2017, 2017, 6562953. [Google Scholar] [CrossRef]
- Brooks, R. The CIA Triangle and Its Real-World Application. Available online: https://blog.netwrix.com/2019/03/26/the-cia-triad-and-its-real-world-application (accessed on 7 January 2022).
- Chaudhary, R.; Aujla, G.S.; Garg, S.; Kumar, N.; Rodrigues, J.J.P.C. SDN-Enabled Multi-Attribute-Based Secure Communication for Smart Grid in IIoT Environment. IEEE Trans. Ind. Inform. 2018, 14, 2629–2640. [Google Scholar] [CrossRef]
- Nielsen, J.J.; Madueño, G.C.; Pratas, N.K.; Sørensen, R.B.; Stefanovic, C.; Popovski, P. What Can Wireless Cellular Technologies Do about the Upcoming Smart Metering Traffic? IEEE Commun. Mag. 2015, 53, 41–47. [Google Scholar] [CrossRef]
- Meneghello, F.; Calore, M.; Zucchetto, D.; Polese, M.; Zanella, A. IoT: Internet of Threats? A Survey of Practical Security Vulnerabilities in Real IoT Devices. IEEE Internet Things J. 2019, 6, 8182–8201. [Google Scholar] [CrossRef]
- Wlazlo, P.; Sahu, A.; Huang, H.; Mao, Z.; Goulart, A.; Davis, K.; Zonouz, S. Man-in-the-Middle Attacks and Defence in a Power System Cyber-Physical Testbed. IET Cyber-Phys. Syst. Theory Appl. 2021, 6, 164–177. [Google Scholar] [CrossRef]
- Williams, R.; McMahon, E.; Samtani, S.; Patton, M.; Chen, H. Identifying vulnerabilities of consumer Internet of Things (IoT) devices: A scalable approach. In Proceedings of the 2017 IEEE International Conference on Intelligence and Security Informatics (ISI), Beijing, China, 22–24 July 2017; pp. 179–181. [Google Scholar]
- Rachit, S.B.; Ragiri, P.R. Security trends in Internet of Things: A survey. SN Appl. Sci. 2021, 3, 121. [Google Scholar] [CrossRef]
- Hinshaw, D.; Pop, V. The Hapless Shakedown Crew That Hacked Trump’s Inauguration. Wall Str. J. 25 October 2019. Available online: https://www.wsj.com/articles/the-hapless-shake-down-crew-that-hacked-trumps-inauguration-11572014333 (accessed on 7 January 2022).
- Schneier, B. Applied Cryptography—Protocols, Algorithms, and Source Code in C; John Wiley & Sons: Hoboken, NJ, USA, 1996. [Google Scholar]
- Gurunath, R.; Agarwal, M.; Nandi, A.; Samanta, D. An Overview: Security Issue in IoT Network. In Proceedings of the 2018 2nd International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC) I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC), Palladam, India, 30–31 August 2018; pp. 104–107. [Google Scholar] [CrossRef]
- Miorandi, D.; Sicari, S.; De Pellegrini, F.; Chlamtac, I. Internet of things: Vision, applications and research challenges. Ad Hoc Netw. 2012, 10, 1497–1516. [Google Scholar] [CrossRef]
- Liyanage, M.; Braeken, A.; Kumar, P.; Ylianttila, M. IoT Security: Advances in Authentication; Wiley: Chennai, India, 2020. [Google Scholar]
- Florea, I.; Rughinis, R.; Ruse, L.; Dragomir, D. Survey of Standardized Protocols for the Internet of Things. In Proceedings of the 21st International Conference on Control Systems and Computer Science, CSCS 2017, Bucharest, Romania, 29–31 May 2017; IEEE: New York, NY, USA, 2017; pp. 190–196. [Google Scholar] [CrossRef]
- Dragomir, D.; Gheorghe, L.; Costea, S.; Radovici, A. A Survey on Secure Communication Protocols for IoT Systems. In Proceedings of the 2016 International Workshop on Secure Internet of Things, SIoT 2016, Heraklion, Greece, 26–30 September 2016; IEEE Computer Society: New York, NY, USA, 2016; pp. 47–62. [Google Scholar] [CrossRef]
- Deshmukh, S.; Sonavane, S.S. Security protocols for Internet of Things: A survey. In Proceedings of the 2017 International Conference on Nextgen Electronic Technologies: Silicon to Software (ICNETS2), Chennai, India, 23–25 March 2017; pp. 71–74. [Google Scholar] [CrossRef]
- Malik, M.; Dutta, M.; Granjal, J. A Survey of Key Bootstrapping Protocols Based on Public Key Cryptography in the Internet of Things. IEEE Access 2019, 7, 27443–27464. [Google Scholar] [CrossRef]
- Dizdarevic, J.; Carpio, F.; Jukan, A.; Masip-Bruin, X. A Survey of Communication Protocols for Internet of Things and Related Challenges of Fog and Cloud Computing Integration. ACM Comput. Surv. 2019, 51, 1–29. [Google Scholar] [CrossRef]
- Glaroudis, D.P.; Iossifides, A.C.; Chatzimisios, P. Survey, comparison and research challenges of IoT application protocols for smart farming. Comput. Netw. 2020, 168, 107037. [Google Scholar] [CrossRef]
- Khan, M.N.; Rao, A.; Camtepe, S. Lightweight Cryptographic Protocols for IoT-Constrained Devices: A Survey. IEEE Internet Things J. 2021, 8, 4132–4156. [Google Scholar] [CrossRef]
- Agrawal, M.; Zhou, J.; Chang, D. A Survey on Lightweight Authenticated Encryption and Challenges for Securing Industrial IoT. In Security and Privacy Trends in the Industrial Internet of Things; Alcaraz, C., Ed.; Springer: Berlin/Heidelberg, Germany, 2019; pp. 71–94. [Google Scholar] [CrossRef]
- Singh, S.; Sharma, P.K.; Moon, S.Y.; Park, J.H. Advanced lightweight encryption algorithms for IoT devices: Survey, challenges and solutions. J. Ambient. Intell. Humaniz. Comput. 2017, 1–18. [Google Scholar] [CrossRef]
- Lara-Nino, C.A.; Diaz-Perez, A.; Morales-Sandoval, M. Elliptic Curve Lightweight Cryptography: A Survey. IEEE Access 2018, 6, 72514–72550. [Google Scholar] [CrossRef]
- Gunathilake, N.A.; Buchanan, W.J.; Asif, R. Next Generation Lightweight Cryptography for Smart IoT Devices: Implementation, Challenges and Applications. In Proceedings of the 2019 IEEE 5th World Forum on Internet of Things (WF-IoT), Limerick, Ireland, 15–18 April 2019; pp. 707–710. [Google Scholar]
- Nabeel, N.; Habaebi, M.H.; Mustapha, N.A.C.; Islam, M.R. IoT Light Weight (LWT) Crypto Functions. Int. J. Interact. Mob. Technol. 2019, 13, 117–129. [Google Scholar] [CrossRef]
- Patil, A.; Banerjee, S.; Borkar, G. A Survey on Securing Smart Gadgets Using Lightweight Cryptography. In Proceedings of the International Conference on Wireless Communication; Vasudevan, H., Gajic, Z., Deshmukh, A.A., Eds.; Springer: Singapore, 2020; pp. 503–515. [Google Scholar]
- Cazorla, M.; Marquet, K.; Minier, M. Survey and benchmark of lightweight block ciphers for wireless sensor networks. In Proceedings of the 2013 International Conference on Security and Cryptography (SECRYPT), Reykjavik, Iceland, 29–31 July 2013; pp. 1–6. [Google Scholar]
- Nguyen, K.T.; Laurent, M.; Oualha, N. Survey on secure communication protocols for the Internet of Things. Ad Hoc Netw. 2015, 32, 17–31. [Google Scholar] [CrossRef]
- Noor, M.B.M.; Hassan, W.H. Current research on Internet of Things (IoT) security: A survey. Comput. Netw. 2019, 148, 283–294. [Google Scholar] [CrossRef]
- Frustaci, M.; Pace, P.; Aloi, G.; Fortino, G. Evaluating Critical Security Issues of the IoT World: Present and Future Challenges. IEEE Internet Things J. 2018, 5, 2483–2495. [Google Scholar] [CrossRef]
- Hou, J.; Qu, L.; Shi, W. A survey on internet of things security from data perspectives. Comput. Netw. 2019, 148, 295–306. [Google Scholar] [CrossRef]
- Patel, C.; Doshi, N. Security Challenges in IoT Cyber World. In Security in Smart Cities: Models, Applications, and Challenges; Lecture Notes in Intelligent Transportation and Infrastructure; Springer: Cham, Switzerland, 2019. [Google Scholar] [CrossRef]
- Deep, S.; Zheng, X.; Jolfaei, A.; Yu, D.; Ostovari, P.; Bashir, A.K. A survey of security and privacy issues in the Internet of Things from the layered context. IEEE Trans. Emerg. Telecommun. Technol. 2020, e3935. [Google Scholar] [CrossRef]
- Hamad, S.A.; Sheng, Q.Z.; Zhang, W.E.; Nepal, S. Realizing an Internet of Secure Things: A Survey on Issues and Enabling Technologies. IEEE Commun. Surv. Tutor. 2020, 22, 1372–1391. [Google Scholar] [CrossRef]
- Serror, M.; Hack, S.; Henze, M.; Schuba, M.; Wehrle, K. Challenges and Opportunities in Securing the Industrial Internet of Things. IEEE Trans. Ind. Inform. 2021, 17, 2985–2996. [Google Scholar] [CrossRef]
- Dehghantanha, A.; Choo, K. Handbook of Big Data and IoT Security; Springer International Publishing: Berlin/Heidelberg, Germany, 2019. [Google Scholar]
- Xu, L.D.; He, W.; Li, S. Internet of Things in Industries: A Survey. IEEE Trans. Ind. Inform. 2014, 10, 2233–2243. [Google Scholar] [CrossRef]
- Lephamer, H. Transmission Systems Design Handbook; Artech House: Norwood, MA, USA, 2002. [Google Scholar]
- Truong, H.; Dustdar, S. Principles for Engineering IoT Cloud Systems. IEEE Cloud Comput. 2015, 2, 68–7610. [Google Scholar] [CrossRef]
- McGrew, D.A.; Viega, J. The Galois/Counter Mode of Operation (GCM), NIST Computer Security Resource Center (CSRC). Available online: https://csrc.nist.rip/groups/ST/toolkit/BCM/documents/proposedmodes/gcm/gcm-spec.pdf (accessed on 7 January 2022).
- Bogdanov, A.; Knudsen, L.R.; Leander, G.; Paar, C.; Poschmann, A.; Robshaw, M.J.B.; Seurin, Y.; Vikkelsoe, C. PRESENT: An Ultra-Lightweight Block Cipher. In Cryptographic Hardware and Embedded Systems—CHES 2007; Paillier, P., Verbauwhede, I., Eds.; Springer: Berlin/Heidelberg, Germany, 2007; pp. 450–466. [Google Scholar]
- NIST. Advanced Encryption Standard (AES) (FIPS PUB 197). Available online: https://nvlpubs.nist.gov/nistpubs/FIPS/NIST.FIPS.197.pdf (accessed on 1 November 2001).
- Blazhevski, D.; Stojcevska, B.; Pachovski, V. Modes of Operation of the AES Algorithm. In Proceedings of the 10th Conference for Informatics and Information Technology (CIIT 2013), Bitola, Macedonia, 18–21 April 2013; pp. 212–216. [Google Scholar]
- Dworkin, M. Recommendation for Block Cipher Modes of Operation: Methods and Techniques; NIST Special Publication 800-38A: Gaithersburg, MD, USA, 2001. [Google Scholar]
- Song, J.; Poovendran, R.; Lee, J.; Iwata, T. The AES-CMAC Algorithm; RFC 4493; RFC Editor: Nagoya, Japan, 2006. [Google Scholar]
- What Is LoRaWAN®: LoRa Alliance®. Available online: https://lora-alliance.org/resource-hub/what-lorawanr (accessed on 7 January 2022).
- Vejlgaard, B.; Lauridsen, M.; Nguyen, H.; Kovacs, I.Z.; Mogensen, P.; Sorensen, M. Coverage and Capacity Analysis of Sigfox, LoRa, GPRS, and NB-IoT. In Proceedings of the IEEE 85th Vehicular Technology Conference (VTC Spring), Sydney, Australia, 4–7 June 2017; pp. 1–5. [Google Scholar]
- Chaudhari, B.S.; Zennaro, M. LPWAN Technologies for IoT and M2M Applications; Elsevier Science Technology: Amsterdam, The Netherlands, 2020. [Google Scholar]
- Bertsekas, D.P.; Gallager, R.G. Data Networks; Prentice Hall: Englewood Cliffs, NJ, USA, 1992. [Google Scholar]
- Wixted, A.J.; Kinnaird, P.; Larijani, H.; Tait, A.; Ahmadinia, A.; Strachan, N. Evaluation of LoRa and LoRaWAN for wireless sensor networks. In Proceedings of the IEEE SENSORS, Orlando, FL, USA, 30 October–2 November 2016; pp. 1–3. [Google Scholar]
- Seller, O. LoRAWAN Security. J. ICT 2021, 9, 47–60. [Google Scholar] [CrossRef]
- Cole, T. LoRaWAN: IoT Keeps Track of Reindeer in Finland. Available online: https://www.smart-industry.net/lorawan-iot-keeps-track-of-reindeer-in-finland/ (accessed on 7 January 2022).
- Bellini, B.; Amaud, A. A 5 μA wireless platform for cattle heat detection. In Proceedings of the IEEE 8th Latin American Symposium on Circuits Systems (LASCAS), Bariloche, Argentina, 20–23 February 2017; pp. 1–4. [Google Scholar]
- De Carvalho Silva, J.; Rodrigues, J.J.P.C.; Alberti, A.M.; Solic, P.; Aquino, A.L.L. LoRaWAN—A low power WAN protocol for Internet of Things: A review and opportunities. In Proceedings of the 2nd International Multidisciplinary Conference on Computer and Energy Science (SpliTech), Split, Croatia, 12–14 July 2017; pp. 1–6. [Google Scholar]
- Semtech. LORA Developer Portal. Available online: https://lora-developers.semtech.com/library/tech-papers-and-guides/lora-and-lorawan/ (accessed on 7 January 2022).
- Bandyopadhyay, N.; Gaurav, P.; Kundu, M.; Misra, B.; Hoare, B. IoT-based Health and Farm Monitoring System via LoRa-based Wireless Sensor Network. In Proceedings of the 4th International Conference on Electronics, Materials Engineering Nano-Technology (IEMENTech), Kolkata, India, 2–4 October 2020; pp. 1–7. [Google Scholar] [CrossRef]
- Semtech Deploys LoRa-Based Network for South Korean Expressways. Available online: https://www.semtech.com/company/press/semtech-deploys-lora-based-network-for-south-korean-expressways (accessed on 7 January 2022).
- 3GPP TR 45.820; Cellular System Support for Ultra-Low Complexity and Low Throughput Internet of Things (CIoT). Technical Specification Group GSM/EDGE Radio Access Network. Release 13. Zayas, Almudena Diaz, and Pedro Merino: Paris, France, 2015.
- Shin, E.; Jo, G. Structure of NB-IoT NodeB system. In Proceedings of the International Conference on Information and Communication Technology Convergence (ICTC), Jeju Island, Korea, 18–20 October 2017; pp. 1269–1271. [Google Scholar]
- Migabo, E.; Djouani, K.; Kurien, A. A Modelling Approach for the Narrowband IoT (NB-IoT) Physical (PHY) Layer Performance. In Proceedings of the IECON 2018—44th Annual Conference of the IEEE Industrial Electronics Society, Washington, DC, USA, 21–23 October 2018; pp. 5207–5214. [Google Scholar]
- Wang, Y.E.; Lin, X.; Adhikary, A.; Grovlen, A.; Sui, Y.; Blankenship, Y.; Bergman, J.; Razaghi, H.S. A Primer on 3GPP Narrowband Internet of Things. IEEE Commun. Mag. 2017, 55, 117–123. [Google Scholar] [CrossRef]
- Mangalvedhe, N.; Ratasuk, R.; Ghosh, A. NB-IoT deployment study for low power wide area cellular IoT. In Proceedings of the IEEE 27th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), Bologna, Italy, 9–12 September 2016; pp. 1–6. [Google Scholar]
- Cruz, R.; Coelho, A.; Campos, R.; Ricardo, M. A Theoretical Model for Planning NB-IoT Networks. In Proceedings of the 2019 International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Barcelona, Spain, 21–23 October 2019; pp. 1–4. [Google Scholar]
- Foni, S.; Pecorella, T.; Fantacci, R.; Carlini, C.; Obino, P.; Di Benedetto, M. Evaluation methodologies for the NB-IoT system: Issues and ongoing efforts. In Proceedings of the AEIT International Annual Conference, Cagliari, Italy, 20–22 September 2017; pp. 1–6. [Google Scholar]
- Sultania, A.K.; Zand, P.; Blondia, C.; Famaey, J. Energy Modeling and Evaluation of NB-IoT with PSM and eDRX. In Proceedings of the IEEE Globecom Workshop, Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–7. [Google Scholar]
- Fattah, H. 5G LTE Narrowband Internet of Things (NB-IoT); CRC Press: Boca Raton, FL, USA; Taylor Francis Group: Abingdon, UK, 2018. [Google Scholar]
- Hussain Pirzada, S.J.; Murtaza, A.; Hasan, M.N.; Xu, T.; Jianwei, L. The Implementation of AES-CMAC Authenticated Encryption Algorithm on FPGA. In Proceedings of the IEEE 2nd International Conference on Computer and Communication Engineering Technology (CCET), Beijing, China, 16–18 August 2019; pp. 193–197. [Google Scholar]
- Campillo, O.S. Security Issues in Internet of Things. Master’s Dissertation, Universitat Politecnica de Catalunya BarcelonaTech, Barcelona, Spain. Available online: https://upcommons.upc.edu/bitstream/handle/2117/109290/Security Issues in Internet of Things.pdf (accessed on 7 January 2022).
- Cavo, L.; Fuhrmann, S.; Liu, L. Implementation of an Area Efficient Crypto Processor for a NB-IoT SoC Platform. In Proceedings of the 2018 IEEE Nordic Circuits and Systems Conference (NORCAS): NORCHIP and International Symposium of System-on-Chip (SoC), Tallinn, Estonia, 30–31 October 2018; pp. 1–5. [Google Scholar]
- Frankel, S.; Krishnan, S. IP Security (IPsec) and Internet Key Exchange (IKE) Document Roadmap. 2011, pp. 1–63. Available online: https://www.hjp.at/doc/rfc/rfc6071.html (accessed on 7 January 2022).
- Goulart, A.E.; Sahu, A. Cellular IoT for Mobile Autonomous Reporting in the Smart Grid. Int. J. Interdiscip. Telecommun. Netw. 2016, 8, 50–65. [Google Scholar] [CrossRef][Green Version]
- EP-SPECS Rev. 1.5, F. Sigfox Connected Objects: Radio Specifications. Available online: https://build.sigfox.com/sigfox-device-radio-specifications (accessed on 7 January 2022).
- Sahu, A.; Goulart, A. Implementation of a C-UNB Module for NS-3 and Validation for DLMS-COSEM Application Layer Protocol. In Proceedings of the 2019 IEEE ComSoc International Communications Quality and Reliability Workshop (CQR), Naples, FL, USA, 16–18 April 2019; pp. 1–6. [Google Scholar]
- Basson, J.A.; Broekman, A.; Jacobsz, S.W. TD-DAQ: A low-cost data acquisition system monitoring the unsaturated pore pressure regime in tailings dams. HardwareX 2021, 10, e00221. [Google Scholar] [CrossRef]
- James, M.; Kumar, D. An Implementation of Modified Lightweight Advanced Encryption Standard in FPGA. Procedia Technol. 2016, 25, 582–589. [Google Scholar] [CrossRef]
- Tsai, K.; Leu, F.; You, I.; Chang, S.; Hu, S.; Park, H. Low-Power AES Data Encryption Architecture for a LoRaWAN. IEEE Access 2019, 7, 1463–146357. [Google Scholar] [CrossRef]
- Acla, H.B.; Gerardo, B.D. Performance Evaluation of Lightweight Advanced Encryption Standard Hardware Implementation. Int. J. Recent Technol. Eng. 2019, 8, 1810–1815. [Google Scholar]
- Bogdanov, A.; Mendel, F.; Regazzoni, F.; Rijmen, V.; Tischhauser, E. ALE: AES-Based Lightweight Authenticated Encryption. In Proceedings of the 20th International Workshop on Fast Software Encryption (FSE 2013), Singapore, 11–13 March 2013. [Google Scholar]
- Yu, W.; Köse, S. A Lightweight Masked AES Implementation for Securing IoT against CPA Attacks. IEEE Trans. Circuits Syst. I Regul. Pap. 2017, 64, 2934–2944. [Google Scholar] [CrossRef]
- Kurt Pehlivanoglu, M.; Sakalli, M.; Duru, N.; Sakalli, F. The New Approach of AES Key Schedule for Lightweight Block Ciphers. IOSR J. Comput. Eng. 2017, 19, 21–26. [Google Scholar] [CrossRef]
- Saarinen, M.J.O. A Lightweight ISA Extension for AES and SM4. arXiv 2020, arXiv:2002.07041. [Google Scholar]
- Yu, J.; Aagaard, M. Benchmarking and Optimizing AES for Lightweight Cryptography on ASICs. In Proceedings of the Lightweight Cryptography Workshop 2019, Gaithersburg, MD, USA, 4–6 November 2019. [Google Scholar]
- Sarwar, K.; Yongchareon, S.; Yu, J. Lightweight ECC with Fragile Zero-Watermarking for Internet of Things Security. In Proceedings of the 17th IEEE International Conference on Trust, Security and Privacy in Computing and Communications/12th IEEE International Conference on Big Data Science and Engineering (TrustCom/BigDataSE), New York, NY, USA, 1–3 August 2018; pp. 867–872. [Google Scholar] [CrossRef]
- Shah, D.P.; Shah, P.G. Revisiting of elliptical curve cryptography for securing Internet of Things (IOT). In Proceedings of the 2018 Advances in Science and Engineering Technology International Conferences (ASET), Abu Dhabi, United Arab Emirates, 6 February–5 April 2018; pp. 1–3. [Google Scholar] [CrossRef]
- Lara-Nino, C.A.; Diaz-Perez, A.; Morales-Sandoval, M. Lightweight elliptic curve cryptography accelerator for internet of things applications. Ad Hoc Netw. 2020, 103, 102159. [Google Scholar] [CrossRef]
- Hinden, R.; Deering, S. IPv6 Addressing Architecture; RFC 3513; RFC Editor: Marina del Rey, CA, USA, 2003. [Google Scholar]
- Biryukov, A. The Design of a Stream Cipher LEX. Selected Areas in Cryptography; Biham, E., Youssef, A.M., Eds.; Springer: Berlin/Heidelberg, Germany, 2007; pp. 67–75. [Google Scholar]
- Jakimoski, G.; Khajuria, S. ASC-1: An Authenticated Encryption Stream Cipher. Selected Areas in Cryptography; Miri, A., Vaudenay, S., Eds.; Springer: Berlin/Heidelberg, Germany, 2012; pp. 356–372. [Google Scholar]
- Tiri, K.; Verbauwhede, I. Synthesis of Secure FPGA Implementations. IACR Cryptol. Eprint Arch. 2004. Available online: https://eprint.iacr.org/2004/068 (accessed on 7 January 2022).
- Shaikh, J.R.; Nenova, M.; Iliev, G.; Valkova-Jarvis, Z. Analysis of standard elliptic curves for the implementation of elliptic curve cryptography in resource-constrained E-commerce applications. In Proceedings of the IEEE International Conference on Microwaves, Antennas, Communications and Electronic Systems (COMCAS), Tel Aviv, Israel, 13–15 November 2017; pp. 1–4. [Google Scholar]
- Hankerson, D.R.; Menezes, A.J.; Vanstone, S. Guide to Elliptic Curve Cryptography; Springer: Berlin/Heidelberg, Germany, 2010. [Google Scholar]
- He, D.; Zeadally, S. Authentication protocol for an ambient assisted living system. IEEE Commun. Mag. 2015, 53, 71–77. [Google Scholar] [CrossRef]
- Gyamfi, E.; Ansere, J.A.; Xu, L. ECC Based Lightweight Cybersecurity Solution for IoT Networks Utilizing Multi-Access Mobile Edge Computing. In Proceedings of the Fourth International Conference on Fog and Mobile Edge Computing (FMEC), Rome, Italy, 10–13 June 2019; pp. 149–154. [Google Scholar]
- Kodali, R.K.; Naikoti, A. ECDH based security model for IoT using ESP8266. In Proceedings of the International Conference on Control, Instrumentation, Communication and Computational Technologies (ICCICCT), Kumaracoil, India, 16–17 December 2016; pp. 629–633. [Google Scholar]
- Toradmalle, D.; Singh, R.; Shastri, H.; Naik, N.; Panchidi, V. Prominence of ECDSA over RSA Digital Signature Algorithm. In Proceedings of the Second International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud), Palladam, India, 30–31 August 2018; pp. 253–257. [Google Scholar]
- Eisenbarth, T.; Kumar, S.; Paar, C.; Poschmann, A.; Uhsadel, L. A Survey of Lightweight-Cryptography Implementations. IEEE Des. Test Comput. 2007, 24, 522–533. [Google Scholar] [CrossRef]
- Kim, Y.; Kim, G. A Performance Analysis of Lightweight Cryptography Algorithm for Data Privacy in IoT Devices. In Proceedings of the International Conference on Information and Communication Technology Convergence (ICTC), Jeju Island, Korea, 17–19 October 2018; pp. 936–938. [Google Scholar]
- Chanal, P.M.; Kakkasageri, M.S. Hybrid Algorithm for Data Confidentiality in Internet of Things. In Proceedings of the 10th International Conference on Computing, Communication and Networking Technologies (ICCCNT), Kharagpur, India, 6–8 July 2019; pp. 1–5. [Google Scholar]
- Dua, A.; Dutta, A. A Study of Applications Based on Elliptic Curve Cryptography. In Proceedings of the 3rd International Conference on Trends in Electronics and Informatics (ICOEI), Tirunelveli, India, 23–25 April 2019; pp. 249–254. [Google Scholar]
- Hemmes, J.; Dressler, J. Work-In-Progress: IoT Device Signature Validation. In Proceedings of the IEEE 10th Annual Information Technology, Electronics and Mobile Communication Conference (IEMCON), Vancouver, BC, Canada, 17–19 October 2019; pp. 43–48. [Google Scholar]
- Gu, T.; Mohapatra, P. BF-IoT: Securing the IoT Networks via Fingerprinting-Based Device Authentication. In Proceedings of the 2018 IEEE 15th International Conference on Mobile Ad Hoc and Sensor Systems (MASS), Chengdu, China, 9–12 October 2018; pp. 254–262. [Google Scholar]




| Reference | Year | Topic |
|---|---|---|
| Liyanage et al. [14] | 2020 | Discusses the evolution of IoT, the taxonomy, and proposed architectures, probes the various efforts for the standardization of IoT, and illustrates some IoT applications. |
| Florea et al. [15] | 2017 | Discusses application layer protocols (CoAP, MQTT), service discovery protocols (mDNS, DNS-SD, uBonjour), infrastructure protocols (IEEE 802.15.4, 6LoWPAN, LoRaWAN), and smart home systems with wireless sensors and robot assistants that use IEEE 802.15.4, 6LoWPAN, CoAP. |
| Dragomir et al. [16] | 2016 | Standardized IoT communication protocols are explained in detail, with analysis of their security in terms of integrity, confidentiality, authentication, and protection against replay attacks. |
| Deshmukh et al. [17] | 2017 | Communication protocols at each OSI (Open Systems Interconnection) layer. Briefly describes a few communication protocols used for IoT and whether they support security at the respective layer. |
| Ferrag et al. [2] | 2017 | Review of forty authentication protocols in four environments, M2M, IoV, IoE, and IoS, that are evaluated under thirty-five attacks. Countermeasures and formal security verification techniques are also addressed. |
| Malik et al. [18] | 2019 | Secure key generation and distribution (or key bootstrapping) in the context of IoT applications and constrained devices. With a focus on low-power and short-distance technologies, it reviews how public-key algorithms and authentication protocols are being adapted for IoT. |
| Dizdarevic et al. [19] | 2019 | Application layer protocols for IoT in the context of specific challenges in fog and cloud computing integration. |
| Glaroudis et al. [20] | 2020 | Discusses IoT application protocols—MQTT, CoAP, XMPP, AMQP, DDS protocol, including HTTP-based applications, and the WebSocket protocol—within the context of IoT systems in agriculture, which must be reliable. |
| Reference | Year | Topic |
|---|---|---|
| Khan et al. [21] | 2021 | Discusses the idea of proxy re-encryption, where nodes at the edge networks can apply more robust security algorithms. Introduces end-through-nodes-to-end security. Compares several lightweight solutions. |
| Agrawal et al. [22] | 2019 | Reviews seventeen lightweight authenticated encryption (LAE) algorithms dating back to 2010. The algorithms are compared in terms of hardware implementation and software speed. |
| Singh et al. [23] | 2017 | Compares lightweight block ciphers and hash functions in terms of the number of rounds, key size, and block size. Introduces primitives that evaluate whether an encryption algorithm is lightweight. |
| Lara-Nino et al. [24] | 2018 | Explains the foundations of ECC in detail. Reviews ECC solutions that are suited for IoT devices. Defines criteria to identify if an ECC algorithm is lightweight or not. |
| Gunathilake et al. [25] | 2019 | Reviews practical and theoretical lightweight cryptography (LWC). Several block ciphers are compared against AES. Moreover, they review papers about the security of LoRaWAN. |
| Nabeel et al. [26] | 2019 | Advantages and drawbacks of lightweight hash function families. A comparison of permutations and transformation functions used in different lightweight hash families. |
| Patil et al. [27] | 2020 | Discusses baby monitoring camera security. Algorithms such as AES, PRESENT, and an ECC-based algorithm are presented as lightweight solutions for these systems. |
| Cazorla et al. [28] | 2013 | Very useful overview of seventeen lightweight block ciphers, potential attacks against them, and a comparison of their memory requirements and performance (cycles/byte). |
| Reference | Year | Topic |
|---|---|---|
| Nguyena et al. [29] | 2015 | Challenges and requirements in building a secure IoT system. A taxonomy of different security protocols proposed for wireless sensor networks and IoT with respect to key bootstrapping mechanisms. |
| Noor and Hassan [30] | 2019 | State of IoT security research, relevant tools, and modeling tools and simulators. The challenges in applying security mechanisms in IoT. |
| Rachit et al. [9] | 2021 | Compares protocols and standards used in IoT. Overview of the latest security research trends for IoT security. |
| Frustaci et al. [31] | 2018 | How to design IoT security. A taxonomic analysis from the perspective of IoT system model: perception, transportation, and application layers. |
| Hou et al. [32] | 2019 | A three-dimensional approach to IoT security, i.e., one-stop, multi-stop, and end application dimensions. |
| Patel and Doshi [33] | 2019 | IoT applications in different fields. IoT architecture layers, security requirements, and threats related to each layer. |
| Deep et al. [34] | 2020 | The security and privacy issues in IoT systems at each layer in the protocol stack, with challenges, existing security solutions, and key distribution. |
| Hamad et al. [35] | 2020 | Cloud-based IoT security and applications. Security requirements in terms of access control, integrity, and authentication. |
| Serror et al. [36] | 2021 | Assessment of the security challenges for industrial IoT, including vulnerabilities, risks, threats. Mapping of existing solutions and challenges. |
| Dehghantanh et al. [37] | 2019 | Overview of cybersecurity and digital forensic challenges related to big data and IoT. A cyber defense triage process for IoT infrastructure. |
| Xu et al. [38] | 2014 | IoT from the perspective of industrial applications. The technologies used in industries: identification, service management, and access. |
| Miorandi et al. [13] | 2012 | One of the earliest IoT surveys. Overview of IoT, where it can be used (application fields or services), and the technologies that enable these services. |
| Block Cipher | Year | Block Size (Bits) | Key Size (Bits) | Rounds | Cazorla [28] | Agrawal [22] | Singh [23] | Khan [21] | Gunathilake [25] | ISO Std |
|---|---|---|---|---|---|---|---|---|---|---|
| SPECK | 2013 | 64 | 96 | 26 | ✓ | ✓ | ✓ | |||
| SIMON | 2013 | 64 | 96 | 26 | ✓ | ✓ | ✓ | |||
| TWINE | 2013 | 64 | 80/128 | 36 | ✓ | ✓ | ✓ | ✓ | ||
| KLEIN | 2012 | 64 | 64/80/96 | 12/16/20 | ✓ | |||||
| LED | 2011 | 64 | 64/128 | 32/48 | ✓ | ✓ | ✓ | |||
| LBlock | 2011 | 64 | 80 | 32 | ✓ | ✓ | ||||
| Piccolo | 2011 | 64 | 80/128 | 25/31 | ✓ | ✓ | ||||
| KATAN and KTANTAN | 2009 | 32/48/64 | 80 | 254 | ✓ | |||||
| PRESENT | 2007 | 64 | 80/128 | 31 | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| CLEFIA | 2007 | 128 | 128 | 18 | ✓ | ✓ | ✓ | |||
| DESL and DESXL | 2007 | 64 | 184 | 16 | ✓ | ✓ | ||||
| HIGHT | 2006 | 64 | 128 | 32 | ✓ | ✓ | ✓ | ✓ | ||
| mCrypton | 2006 | 64 | 64/96/128 | 12 | ✓ | |||||
| IDEA | 2006 | 64 | 128 | 85 | ✓ | |||||
| NOEKEON | 2000 | 128 | 128 | 16 | ✓ | |||||
| SKIPJACK | 1999 | 64 | 80 | 32 | ✓ | |||||
| AES | 1998 | 128 | 128/192/256 | 10/12/14 | ✓ | ✓ | ✓ | ✓ | ✓ | |
| TEA and XTEA | 1997 | 64 | 128 | 64 | ✓ | ✓ | ✓ | |||
| RC5 | 1995 | 64 | 128 | 1–255 | ✓ | ✓ |
| Application | Message Frequency | Message Size |
|---|---|---|
| Waste management | 1 per hour | 50 bytes |
| Bike renting | 4 per hour | 50 bytes |
| Gas meter | 4 per hour | 100 bytes |
| Parking | 1 per hour | 100 bytes |
| Water meter | 1 per day | 200 bytes |
| Electricity meter | 1 every 4 h | 300 bytes |
| Pollution monitoring | 1 per hour | 1000 bytes |
| Communications | LoRaWAN | NB-IoT | C-UNB/Sigfox |
| Uplink Rate | 0.3–50 kbps | 159 kbps (Rel14) | 0.6 kbps |
| Spectrum | ISM band | licensed | ISM band |
| Channel Bandwidth | 125, 250, 500 kHz | 180, 200 kHz | 192 kHz |
| One Micro-Channel | 125 kHz | 15 or 3.75 kHz | 0.6 kHz |
| Number of Uplink Channels | 72 | 12, 48 | 320 |
| Uplink Access | random (ClassA) | scheduled | random |
| Uplink Packet Size | 51 bytes | 128 bytes | 12 bytes |
| Security | LoRaWAN | NB-IoT | C-UNB/Sigfox |
| Strategy | Encrypt-then-MAC | MAC-then-Encrypt | Encrypt-then-MAC |
| Confidentiality | AES-CTR | AES-CTR, SNOW, ZUC | AES-CTR |
| Authentication | AES-CMAC | AES-CMAC, SNOW, ZUC | AES-CMAC |
| Integrity—MIC Size | 32 bits | 32 bits | 16 bits |
| Replay Protection | 32-bit counter | 32-bit counter | 12-bit counter |
| Block Cipher Primitives | High Performance | Implementation | ||||||
|---|---|---|---|---|---|---|---|---|
| Small Block | Small Key | Simple Round | Key Schedule | Custom CPU | Crypto Array | Software | Hardware | |
| LightAES for FPGA [76] | ✓ | ✓ | ✓ | |||||
| LPADA [77] | ✓ | ✓ | ||||||
| LAES [78] | ✓ | ✓ | ||||||
| ALE [79] | ✓ | ✓ | ✓ | ✓ | ||||
| Masked AES [80] | ✓ | ✓ | ||||||
| AES-64 [81] | ✓ | ✓ | ✓ | ✓ | ||||
| ISA [82] | ✓ | ✓ | ✓ | |||||
| Quark [83] | ✓ | ✓ | ||||||
| ECC WaterMark [84] | ✓ | ✓ | ||||||
| ECIOT [85] | ✓ | ✓ | ✓ | |||||
| ECC Accel. [86] | ✓ | |||||||
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Goulart, A.; Chennamaneni, A.; Torre, D.; Hur, B.; Al-Aboosi, F.Y. On Wide-Area IoT Networks, Lightweight Security and Their Applications—A Practical Review. Electronics 2022, 11, 1762. https://doi.org/10.3390/electronics11111762
Goulart A, Chennamaneni A, Torre D, Hur B, Al-Aboosi FY. On Wide-Area IoT Networks, Lightweight Security and Their Applications—A Practical Review. Electronics. 2022; 11(11):1762. https://doi.org/10.3390/electronics11111762
Chicago/Turabian StyleGoulart, Ana, Anitha Chennamaneni, Damiano Torre, Byul Hur, and Fadhil Y. Al-Aboosi. 2022. "On Wide-Area IoT Networks, Lightweight Security and Their Applications—A Practical Review" Electronics 11, no. 11: 1762. https://doi.org/10.3390/electronics11111762
APA StyleGoulart, A., Chennamaneni, A., Torre, D., Hur, B., & Al-Aboosi, F. Y. (2022). On Wide-Area IoT Networks, Lightweight Security and Their Applications—A Practical Review. Electronics, 11(11), 1762. https://doi.org/10.3390/electronics11111762






