Design and Development of a Blockchain-Based System for Private Data Management
Abstract
:1. Introduction
- The design and development of a blockchain-based consent management framework for private data;
- Implementation details of the proposed model on the Amazon Web Services (AWS) cloud with a case study;
- Performance evaluation of the developed prototype using Hyperledger Caliper—a benchmark tool that measures the performance of blockchain implementation.
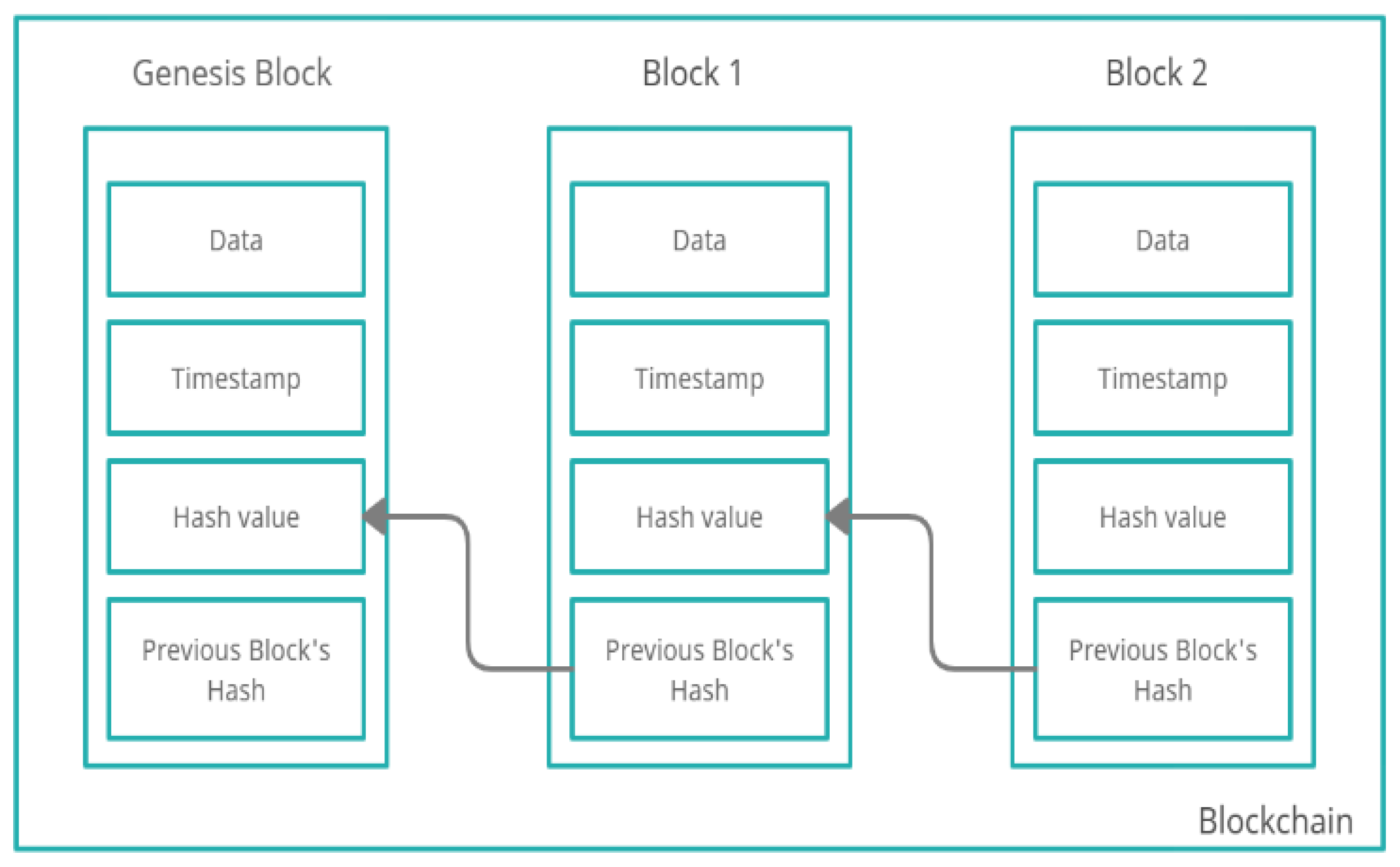
2. Background and Related Work
- Peer: Peers are similar to nodes or participants on the network but share a ledger privately among themselves. In the case of Ethereum and blockchain, all nodes are equal. However, in Hyperledger, there are a few different types of peers, such as anchor peers, committing peers, and endorsing peers. Anchor peers are identified outside of the network, and without an anchor peer, two networks cannot be connected. Committing peers are responsible for maintaining the ledger on the network. Finally, endorsing peers are helpful for validation purposes.
- Consensus: Consensus is a mechanism used to validate a block before adding it to the chain. Two types of consensus mechanisms are available in Fabric: lottery and voting. There are three phases of consensus in Fabric: endorsement, ordering, and validation.
- Chaincode: This is the smart contract (a computer program) that can be written in multiple languages, such as JavaScript, G.O., etc., and that runs on the peers on the network. Nick Szabo introduced a smart contract in 1998, and it is a self-executable program in which the terms of the buyer–seller agreement are written directly into lines of code [8]. In Hyperledger, a chain code is used to implement the business logic that governs how applications communicate with the ledger.
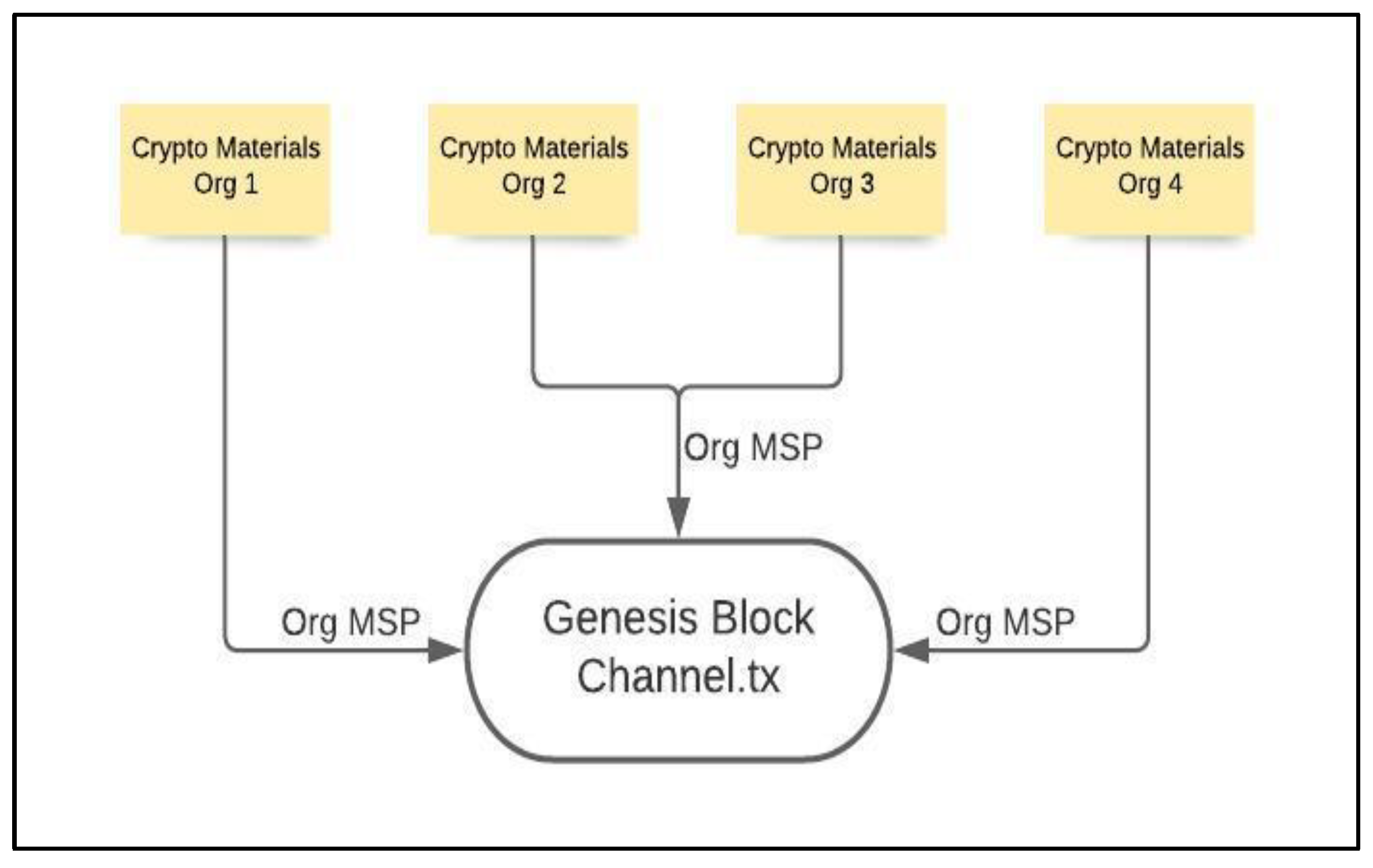
- M.S.P. (Membership Service Provider): Clients must have authenticated credentials to join a private network. M.S.P.s are a semi-abstract component that gives clients access to credentials.
2.1. Blockchain for Consent Management in Healthcare
2.2. Blockchain for Consent Management in Identity Management
2.3. Blockchain for Consent Management in Data Storage
2.4. Gaps in Existing Solutions
3. Proposed Solution
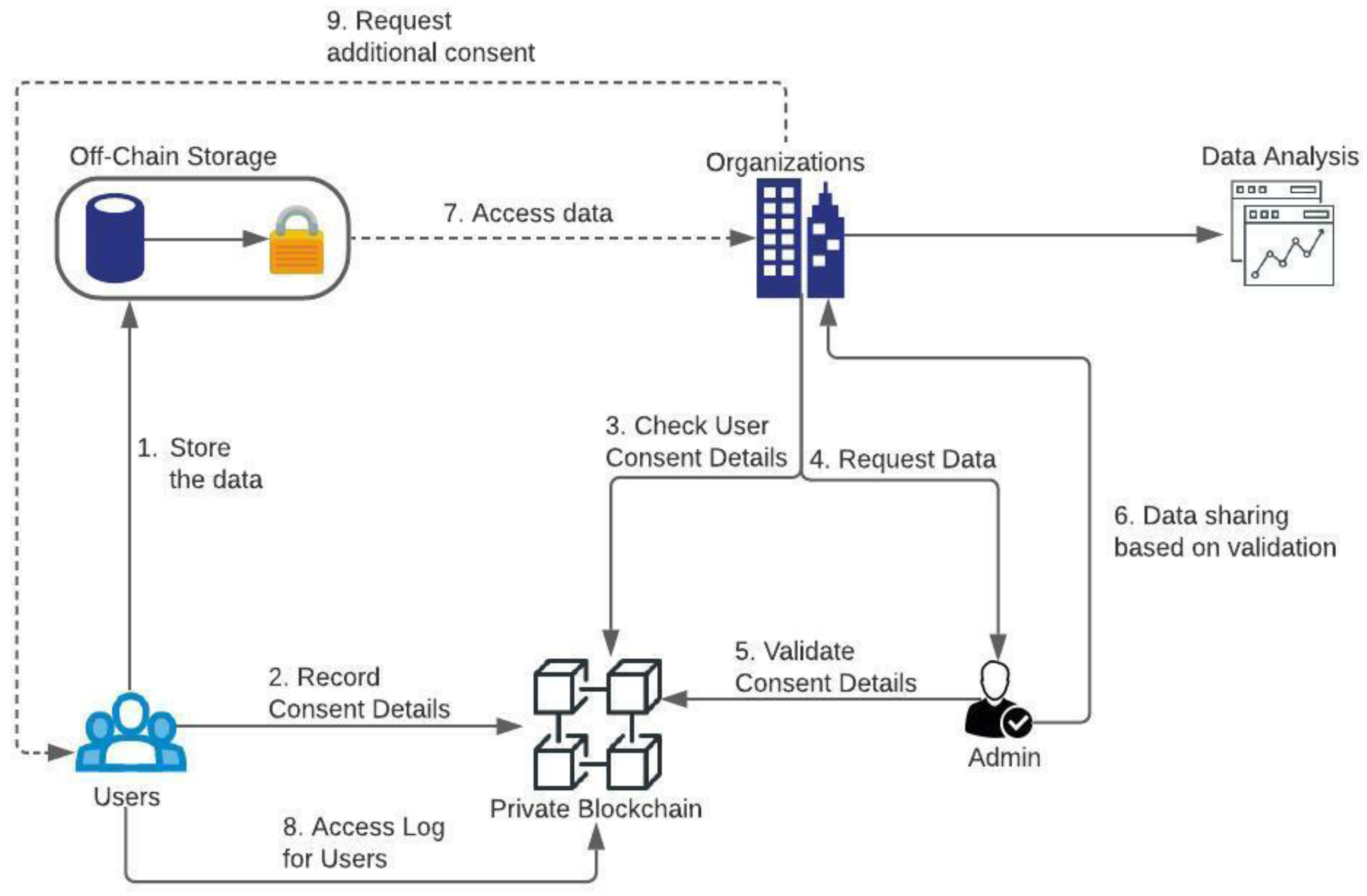
3.1. Architecture
3.1.1. Role of Admin and Integrity Relationship Assumptions
- Users trust the admin for sharing their data and information with authorized organizations;
- Users are enrolled and registered successfully by the admin so that organizations can use it for invoking the functions of chaincode;
- All privacy rules would be rigorously adhered to by research organizations, including the deletion of data when consent is revoked, avoiding unlawful data storage.
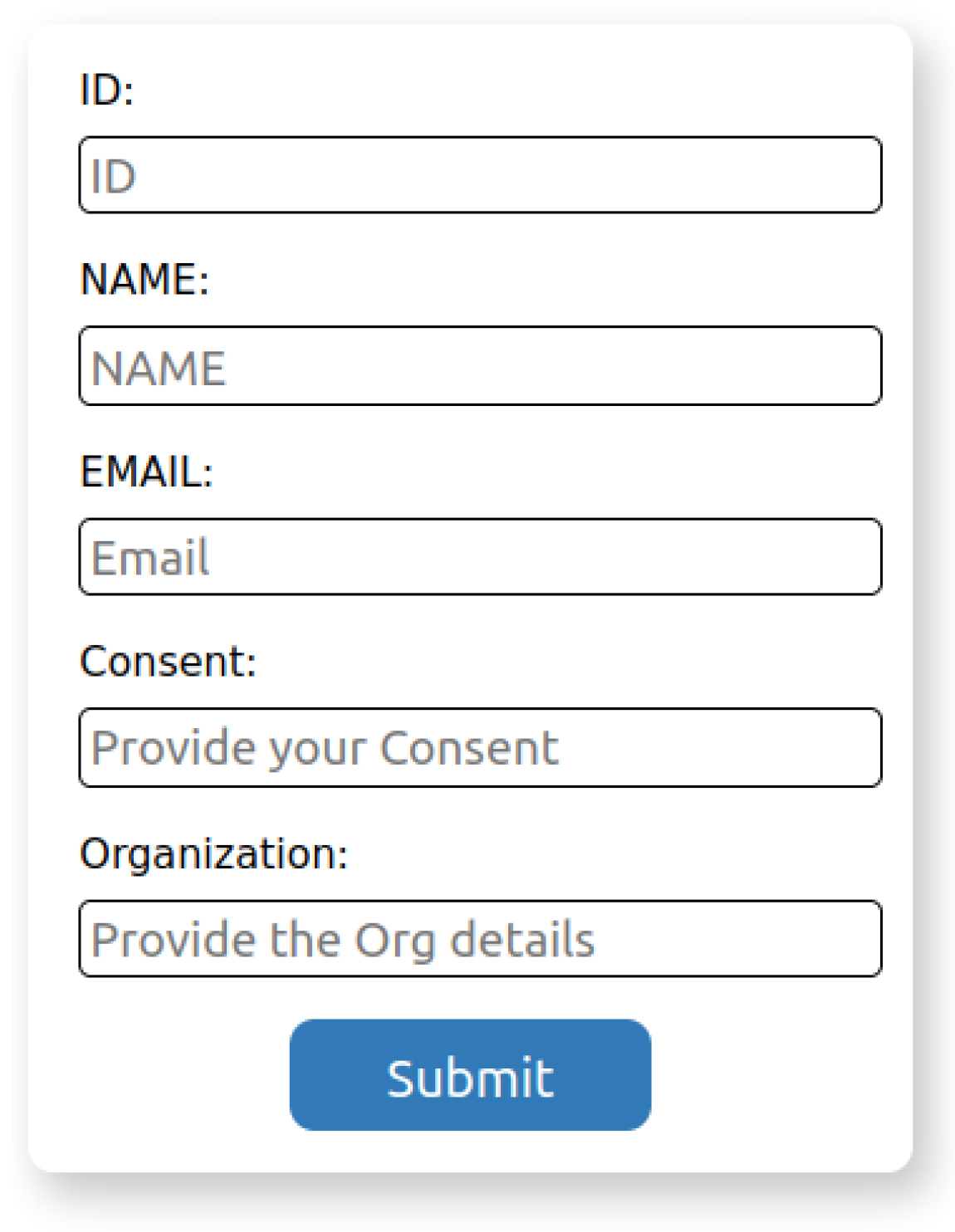
3.1.2. Off-Chain Storage
3.1.3. Blockchain Network
3.1.4. Chaincode
3.1.5. Data Sharing
3.2. Use Cases
- Healthcare: The users may be patients or volunteers that share their data with the hospitals or research organizations. The admin would be a government representative that will share the data. Hospitals/research organizations could use the data from the volunteers to perform medical analysis. To perform the analysis, consent is required from the users. The system could help them obtain consent and data from the users quickly. In general, it benefits both patients and organizations. The patients will have a list of organizations that have access to their data, and the organizations can utilize the system to achieve permission to access sensitive information.
- Internet of Things: Governments are establishing smart infrastructure in urban areas because of the development of IoT technologies. Citizens who use public infrastructure should know who has access to their data and, if possible, regulate access to the data. They can choose to share data obtained via the latest infrastructure (electricity meters) with any other entities. People could be users, and the admin could be a trusted government representative.
- Education: The users could be the students and could store their documents, such as transcripts, degrees, etc., on the database. The admin could be a person working in the educational institute. The organizations could be firms that wish to hire students and require documentation for verification, etc. In this scenario, blockchain can also be used as an identity management application.
4. Prototype Implementation
4.1. Current Implementation on the Cloud
- Understanding blockchain concepts for designing a proper framework for private data management;
- Insufficient and complicated information is present regarding Fabric SDK usage;
- Managing the development of the system’s front end, such as CORS or cross-origin resource sharing.
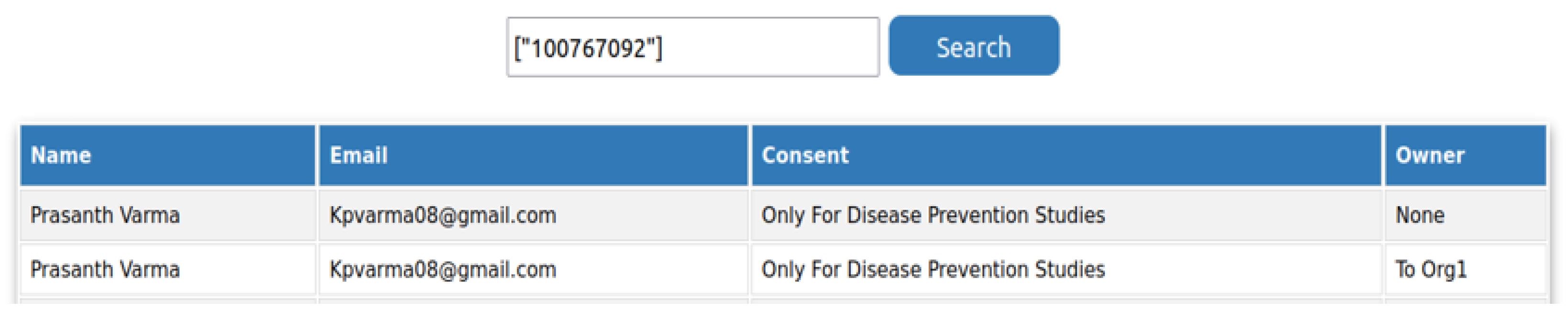
4.2. Use Case—Healthcare Research
5. Evaluation Results
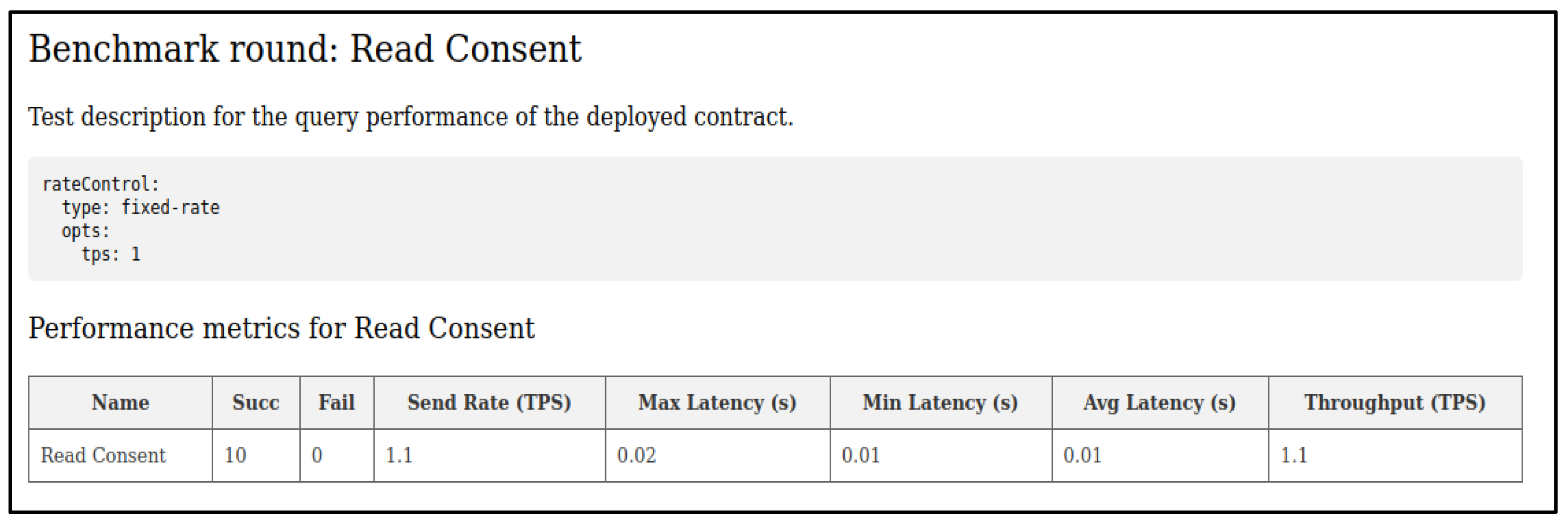
5.1. Early Local Experimental Results
Experiments
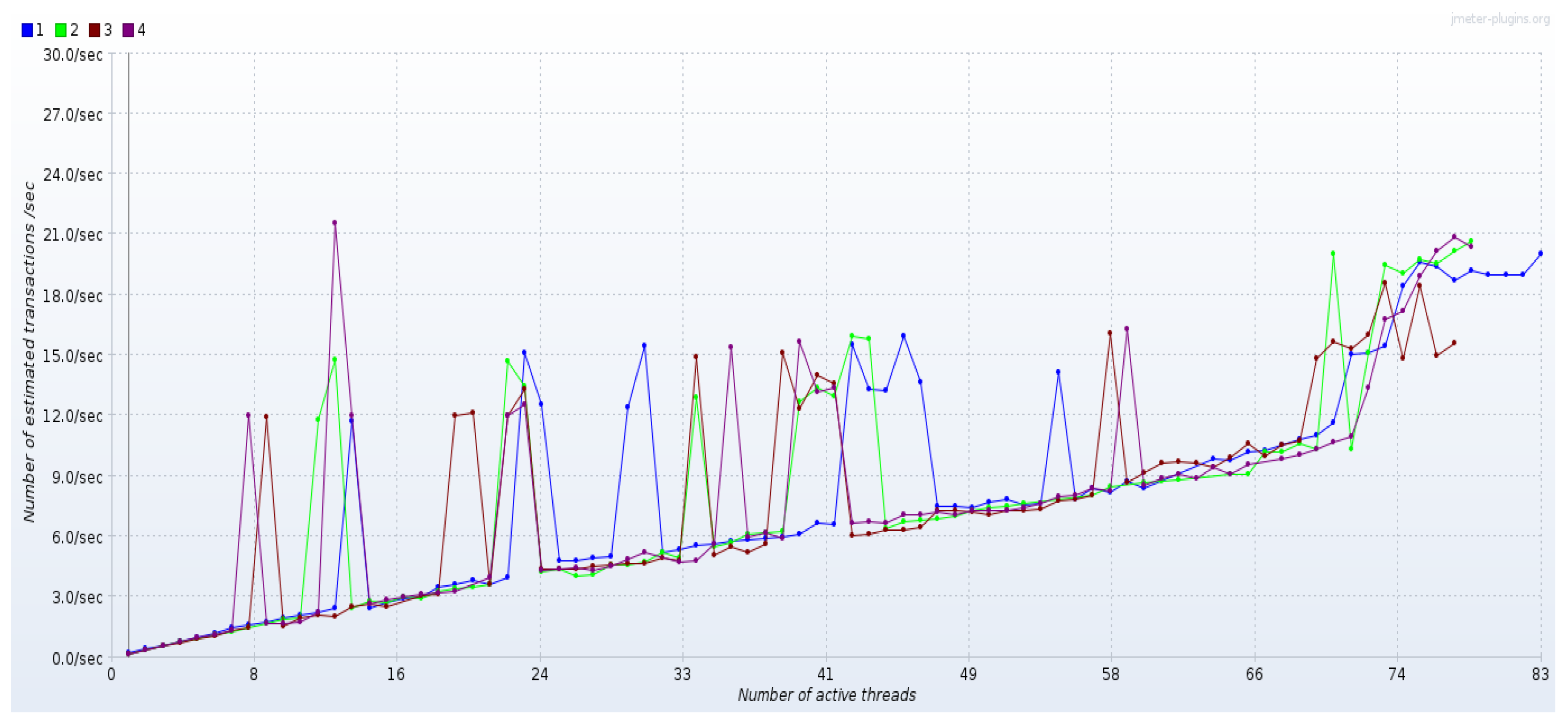
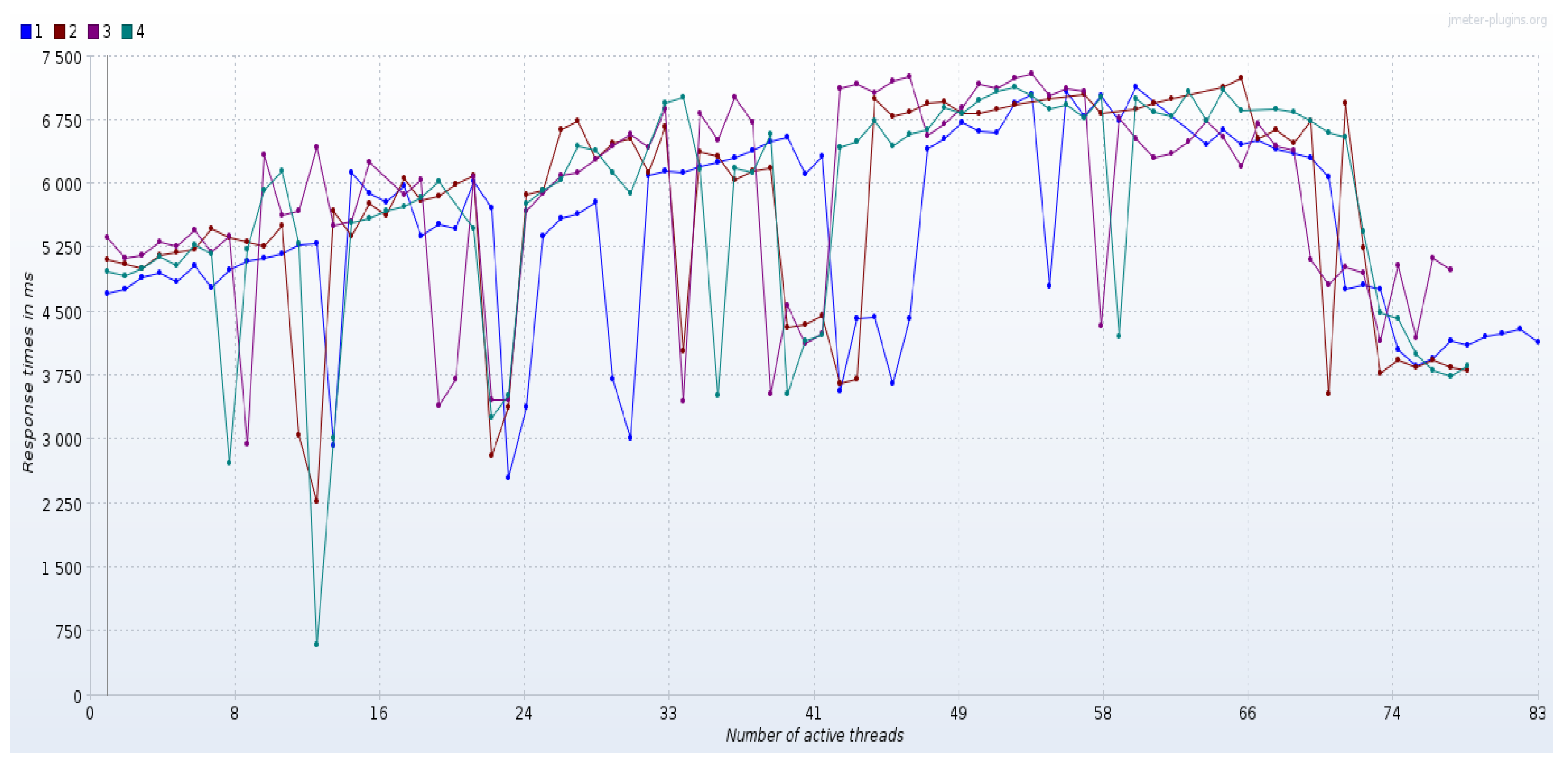
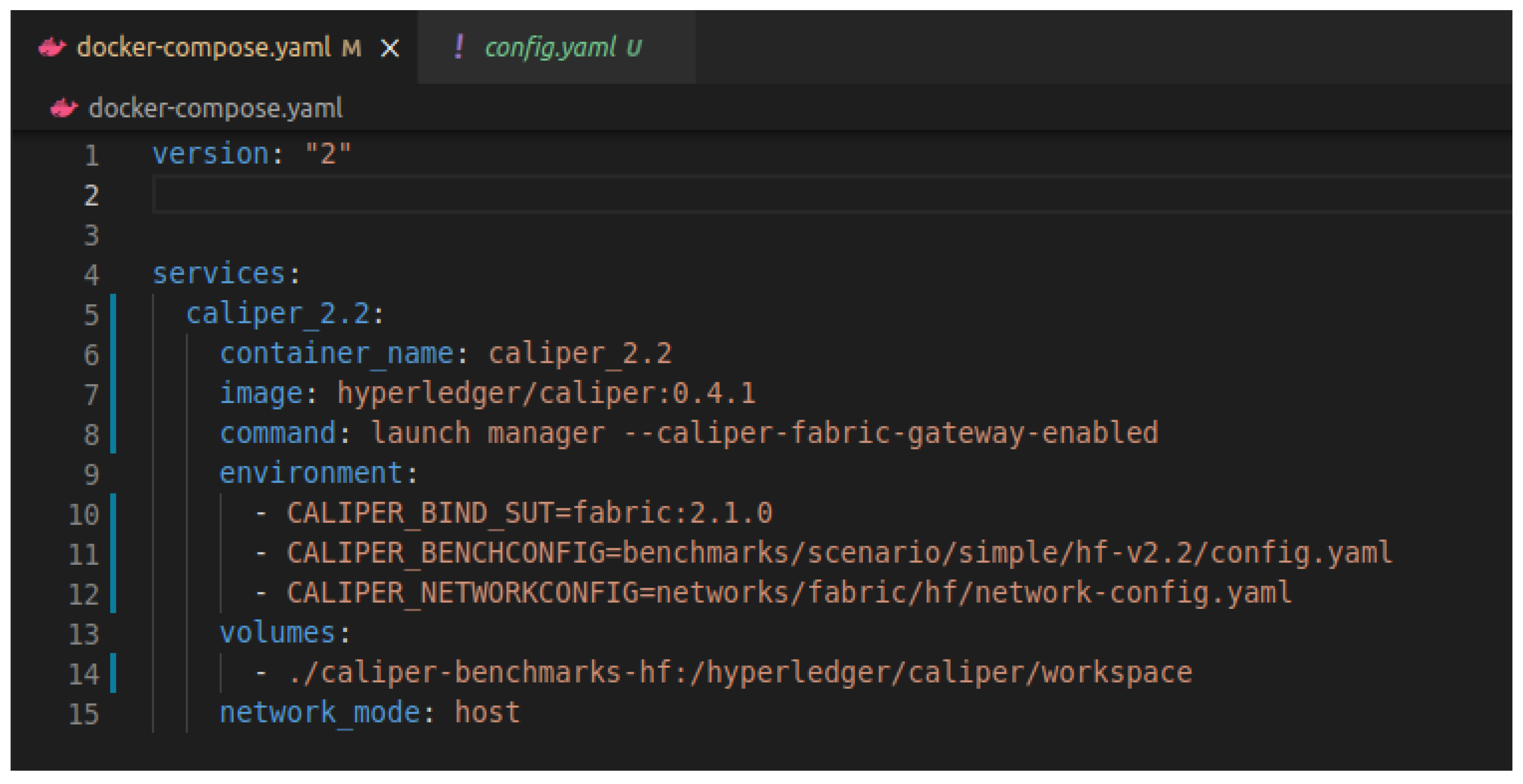
5.2. Cloud Experimental Results
- Decided on an image version. Version 0.4.1 of the Caliper image;
- Mount a container directory to your working directory;
- Set the binding and run parameters that are required, as shown in Figure 14.
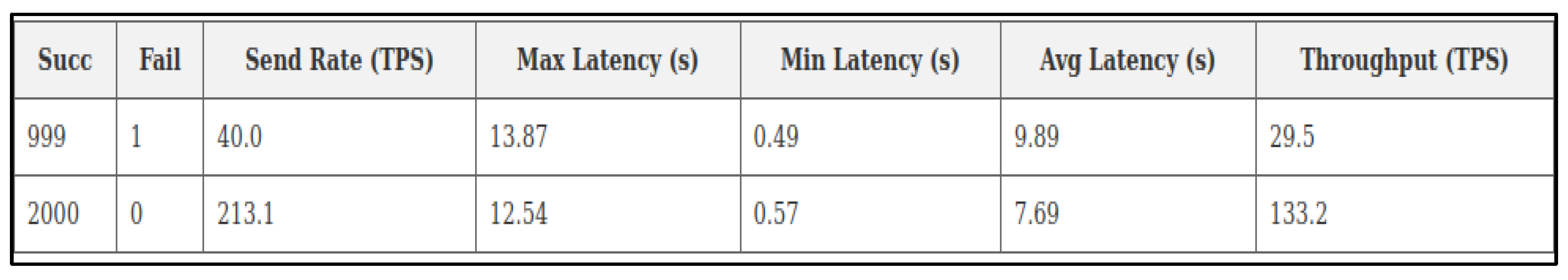
5.2.1. Experiment—1
5.2.2. Experiment—2
5.2.3. Experiment—3
6. Conclusions and Future Work
Future Work
- The system has no precautions in place to ensure the integrity of the data collected from users. It enables users to upload data to the database without validating its accuracy;
- Using an I.D., consent can be updated on the network. I.D. is generated at the time-of-service registration and functions similarly to a private key. Users will have difficulties updating their consent in the event of I.D. loss;
- The cost of the production-ready application will require a certain amount, compared to traditional systems, as it depends highly on the resources allocated, such as processing units, memory, storage, etc. This will also affect the network speed of the blockchain in reading and writing data.
Author Contributions
Funding
Conflicts of Interest
References
- Participating in Health Research Studies. Available online: https://guides.library.harvard.edu/c.php?g=389023&p=2639499 (accessed on 22 May 2021).
- Gostin, L.O.; Levit, L.A.; Nass, S.J. Beyond the HIPAA Privacy Rule: Enhancing Privacy, Improving Health Through Research; National Academies Press: Washington, DC, USA, 2009; p. 114. [Google Scholar]
- Haber, S.; Stornetta, W.S. How to timestamp a digital document. In Advances in Cryptology-CRYPTO’ 90, Proceedings of the Conference on the Theory and Application of Cryptography, Berlin/Heidelberg, Germany, 18 May 2001; Springer Nature: New York, NY, USA, 1990; pp. 437–455. [Google Scholar]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Decentralized Bus. Rev. 2008, 21260. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 22 May 2021).
- Using Blockchain to Improve Data Management in the Public Sector. Available online: https://www.mckinsey.com/business-functions/mckinsey-digital/our-insights/using-blockchain-to-improve-data-management-in-the-public-sector (accessed on 22 May 2021).
- Total Amount of Global Healthcare Data Generated in 2013 and a Projection for 2020. Available online: https://www.statista.com/statistics/1037970/global-healthcare-data-volume/ (accessed on 1 June 2021).
- Hyperledger. Available online: https://www.ibm.com/topics/hyperledger (accessed on 1 June 2021).
- Szabo, N. Formalizing and securing relationships on public networks. First Monday 1997, 2. [Google Scholar] [CrossRef]
- Azaria, A.; Ekblaw, A.; Vieira, T.; Lippman, A. Medrec: Using Blockchain for medical data access and permission management. In Proceedings of the 2016 2nd International Conference on Open and Big Data (OBD), Vienna, Austria, 22–24 August 2016. [Google Scholar]
- Liang, X.; Zhao, J.; Shetty, S.; Liu, J.; Li, D. Integrating Blockchain for data sharing and collaboration in mobile healthcare applications. In Proceedings of the 2017 IEEE 28th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), Montreal, QC, Canada, 8–13 October 2017. [Google Scholar]
- Rouhani, S.; Butterworth, L.; Simmons, A.D.; Humphery, D.G.; Deters, R. MediChain TM: A secure decentralized medical data asset management system. In Proceedings of the 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Halifax, NS, Canada, 30 July–3 August 2018. [Google Scholar]
- Swetha, M.S.; Pushpa, S.K.; Muneshwara, M.S.; Manjunath, T.N. Blockchain-enabled secure healthcare Systems. In Proceedings of the 2020 IEEE International Conference on Machine Learning and Applied Network Technologies (ICMLANT), Hyderabad, India, 20–21 December 2020. [Google Scholar]
- Al Asad, N.; Elahi, M.T.; Al Hasan, A.; Yousuf, M.A. Permission-Based Blockchain with Proof of Authority for Secured Healthcare Data Sharing. In Proceedings of the 2020 2nd International Conference on Advanced Information and Communication Technology (ICAICT), Dhaka, Bangladesh, 28–29 November 2020. [Google Scholar]
- Rajput, A.R.; Li, Q.; Ahvanooey, M.T.; Masood, I. EACMS: Emergency access control management system for personal health record based on Blockchain. IEEE Access 2019, 7, 84304–84317. [Google Scholar] [CrossRef]
- Tith, D.; Lee, J.S.; Suzuki, H.; Wijesundara, W.M.A.B.; Taira, N.; Obi, T.; Ohyama, N. Patient consent management by a purpose-based consent model for electronic health record based on blockchain technology. Healthc. Inform. Res. 2020, 26, 265–273. [Google Scholar] [CrossRef] [PubMed]
- Agbo, C.C.; Mahmoud, Q.H. Design and Implementation of a Blockchain-Based E-Health Consent Management Framework. In Proceedings of the 2020 IEEE International Conference on Systems, Man, and Cybernetics (S.M.C.), Toronto, ON, Canada, 11–14 October 2020. [Google Scholar]
- Shah, M.; Li, C.; Sheng, M.; Zhang, Y.; Xing, C. CrowdMed: A blockchain-based approach to consent management for health data sharing. In Proceedings of the International Conference on Smart Health, Shenzhen, China, 1–2 July 2019. [Google Scholar]
- Monrat, A.A.; Schelén, O.; Andersson, K. A survey of Blockchain from the perspectives of applications, challenges, and opportunities. IEEE Access 2019, 7, 117134–117151. [Google Scholar] [CrossRef]
- Chowdhury, M.J.M.; Colman, A.; Kabir, M.A.; Han, J.; Sarda, P. Blockchain as a notarization service for data sharing with personal data store. In Proceedings of the 2018 17th IEEE International Conference on Trust, Security and Privacy in Computing and Communications/12th IEEE International Conference on Big Data Science and Engineering (TrustCom/BigDataSE), New York, NY, USA, 1–3 August 2018. [Google Scholar]
- Doku, R.; Rawat, D. Pledge: A private ledger based decentralized data sharing framework. In Proceedings of the 2019 Spring Simulation Conference (SpringSim), Tucson, AZ, USA, 29 April–2 May 2019. [Google Scholar]
- Alessi, M.; Camillo, A.; Giangreco, E.; Matera, M.; Pino, S.; Storelli, D. Make users own their data: A decentralized personal data store prototype based on ethereum and ipfs. In Proceedings of the 2018 3rd International Conference on Smart and Sustainable Technologies (SpliTech), Split, Croatia, 26–29 June 2018. [Google Scholar]
- Cha, S.C.; Chen, J.F.; Su, C.; Yeh, K.H. A blockchain-connected gateway for BLE-based devices in the Internet of Things. IEEE Access 2018, 6, 24639–24649. [Google Scholar] [CrossRef]
- Rantos, K.; Drosatos, G.; Kritsas, A.; Ilioudis, C.; Papanikolaou, A.; Filippidis, A.P. A blockchain-based platform for consent management of personal data processing in the IoT ecosystem. Secur. Commun. Netw. 2019, 2019, 1431578. [Google Scholar] [CrossRef]
- Topart, L.; Genestier, P.; Picaud, Y. Blockchain brings confidence to facilitate the flow of data in the agricultural field. In Proceedings of the 2020 2nd Conference on Blockchain Research & Applications for Innovative Networks and Services (BRAINS), Paris, France, 28–30 September 2020. [Google Scholar]
- Agarwal, R.R.; Kumar, D.; Golab, L.; Keshav, S. Consentio: Managing consent to data access using permissioned blockchains. In Proceedings of the 2020 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), Toronto, ON, Canada, 2–6 May 2020. [Google Scholar]
- Aldred, N.; Baal, L.; Broda, G.; Trumble, S.; Mahmoud, Q.H. Design and Implementation of a Blockchain-based Consent Management System. arXiv 2019, arXiv:1912.09882. [Google Scholar]
- Esposito, C.; De Santis, A.; Tortora, G.; Chang, H.; Choo, K.K.R. Blockchain: A panacea for healthcare cloud-based data security and privacy? IEEE Cloud Comput. 2018, 5, 31–37. [Google Scholar] [CrossRef]
- What is Chaincode? Available online: https://fabrictestdocs.readthedocs.io/en/latest/chaincode.html (accessed on 15 June 2021).
- Hyperledger—Write First App. Available online: https://hyperledger-fabric.readthedocs.io/en/release-2.2/write_first_app.html (accessed on 10 June 2021).
- React. Available online: https://reactjs.org/ (accessed on 15 June 2021).
- FileZilla. Available online: https://filezilla-project.org/ (accessed on 15 June 2021).
- Glenn Lee. The Importance of Ramp Up and Ramp Down User Load. Available online: https://www.loadview-testing.com/blog/the-importance-of-ramp-up-and-ramp-down-user-load/#:~:text=Ramp%20up%20speed%20during%20load%20test%20is%20speed,increase%20slowly%20before%20the%20start%20of%20peak%20time (accessed on 15 June 2021).
- Amazon Web Services. Available online: https://aws.amazon.com/ (accessed on 16 June 2021).
- Hyperledger Caliper. Available online: https://hyperledger.github.io/caliper/v0.3.2/fabric-config/ (accessed on 12 June 2021).
- Hyperledger Whitepaper Metrics. Available online: https://www.hyperledger.org/wp-content/uploads/2018/10/HL_Whitepaper_Metrics_PDF_V1.01.pdf (accessed on 15 June 2021).










| Factors | Issues | Solutions with the Proposed System |
|---|---|---|
| Blockchain Storage | The main issue with the blockchain is that the sensitive data cannot be stored on the network, as it cannot be deleted if the user requests it. | To avoid this, the personal data will be stored in a separate storage location. Storing hash references of sensitive data on the network will be avoided as the hash reference of the sensitive data might also be considered personal information soon. Cloud storage will be used instead, and another advantage of not storing data on the blockchain network is the network speed. The consent data can be fetched very quickly. |
| Access log | The main issue with the current consent management systems is that the users are not aware of the organizations accessing their data. | Users will be in control and can either accept or revoke the requests from the organization. The chaincode installed on the network will allow the users to fetch the history information of their consent details. This certainly brings out the traceability and transparency in the proposed system. |
| Security | The data stored on the cloud could be leaked if the database is not regularly maintained according to the latest standards. | Having a trusted individual to oversee the maintenance of the database will help make the system secure. User revoke requests can be investigated quickly to ensure that the data is deleted from all sources in the database. Data sharing through AWS will be influential and simple in removing the access to the organizations once the user places a revoke request. The admin can also perform additional audits with the organizations to ensure the data is deleted entirely from the organization’s system. |
| Privacy | Unauthorized users. | Using a permissioned H.F. will make sure that there are no unauthorized organizations in the network. Additional attribute-based controls could be set up to provide more granular access to the users with the help of chaincode. |
| Scalability | Improving the system performance. | The system’s throughput can be increased by increasing storage and instances placed in the cloud. It is possible to do so by utilizing highly configured EC2 instances, such as t2 large, etc. Additional members can be added to the network by adding another Docker swarm instance to it. As a blockchain solution, the system is, theoretically, indefinitely scalable |
| Hyperledger Fabric | The private data management systems should be adaptive to the fast-growing blockchain technology. | The latest fabric version, which has the newer chaincode lifecycle, was utilized with a React front-end to interact with the network instead of Compose, which is now depreciated. |
| Configuration | Value |
|---|---|
| Instance Type | Ubuntu 20.04 |
| No. of Processors | 4 |
| Memory | 6.1 GB |
| Storage | 50 GB |
| Configuration | Value |
|---|---|
| Instance Type | t2.medium |
| Amazon Machine Image (AMI) | Ubuntu 18.04 |
| No. of Processors | 2 |
| Memory | 4 GB |
| Storage | 50 GB |
| Paper # | Implementation/Performance Evaluation | Comments |
|---|---|---|
| [9] | Prototype implementation details are given. | Does not provide implementation details. |
| [10] | Implementation with few performance analyses. | Does not cover the details of data sharing. |
| [11] | Implemented with Hyperledger Composer. | Does not have performance analysis. The composer is now depreciated. |
| [12] | The prototype is mentioned in this paper. | Does not provide implementation details |
| [13] | Uses multichain to implement private data management. | Performance evaluation of the system is not reported. |
| [14] | Implementation with the performance analysis is covered in this paper. | The composer is used in the system, which is now depreciated. Discussed only a few metrics of Fabric. |
| Proposed System | The implementation details and performance analysis were included. | Used the latest version of Fabric. Response time and transaction throughput for fetching the details from the network have been calculated and reported. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kakarlapudi, P.V.; Mahmoud, Q.H. Design and Development of a Blockchain-Based System for Private Data Management. Electronics 2021, 10, 3131. https://doi.org/10.3390/electronics10243131
Kakarlapudi PV, Mahmoud QH. Design and Development of a Blockchain-Based System for Private Data Management. Electronics. 2021; 10(24):3131. https://doi.org/10.3390/electronics10243131
Chicago/Turabian StyleKakarlapudi, Prasanth Varma, and Qusay H. Mahmoud. 2021. "Design and Development of a Blockchain-Based System for Private Data Management" Electronics 10, no. 24: 3131. https://doi.org/10.3390/electronics10243131
APA StyleKakarlapudi, P. V., & Mahmoud, Q. H. (2021). Design and Development of a Blockchain-Based System for Private Data Management. Electronics, 10(24), 3131. https://doi.org/10.3390/electronics10243131







