Approaches towards Blockchain Innovation: A Survey and Future Directions
Abstract
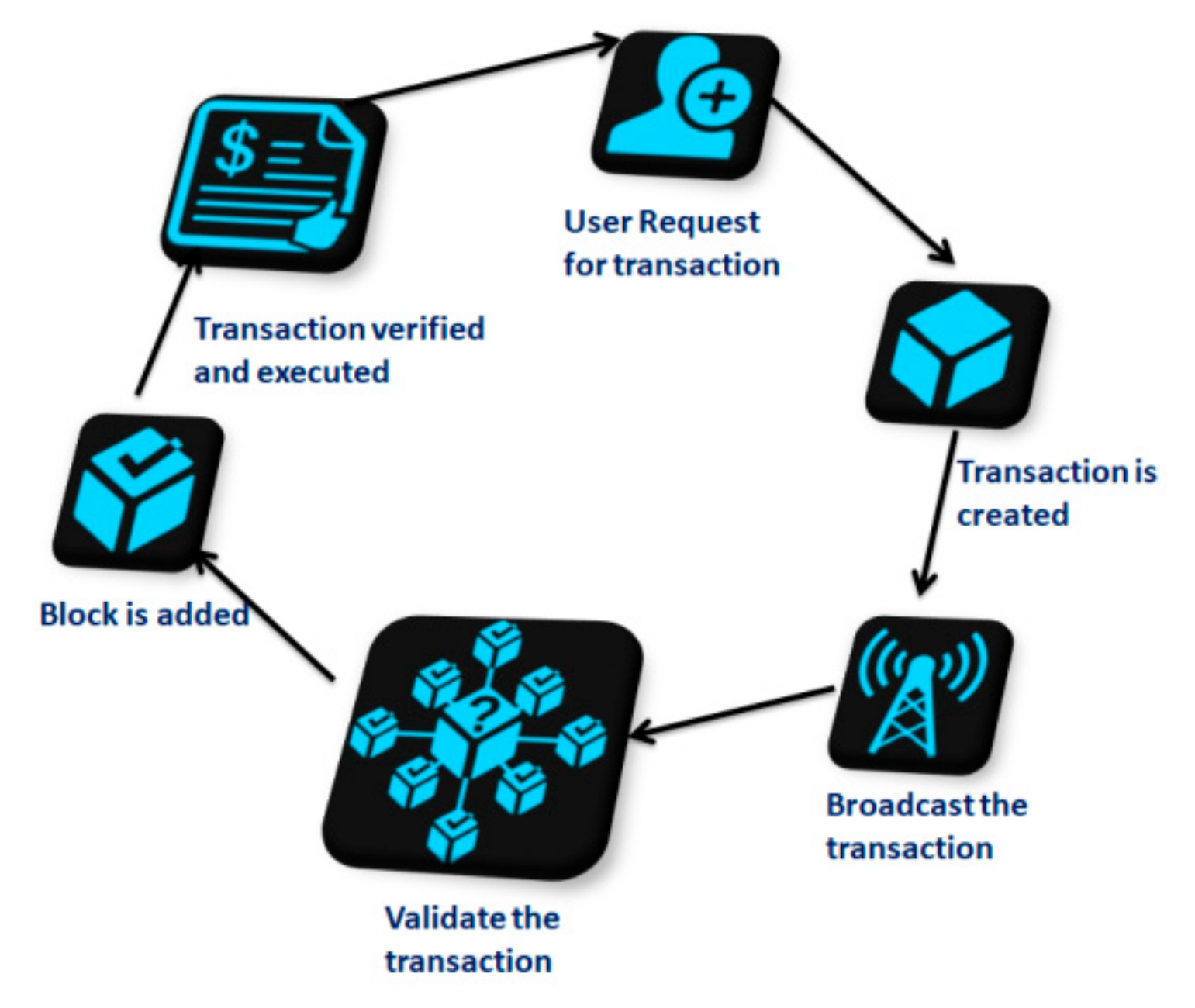
:1. Introduction
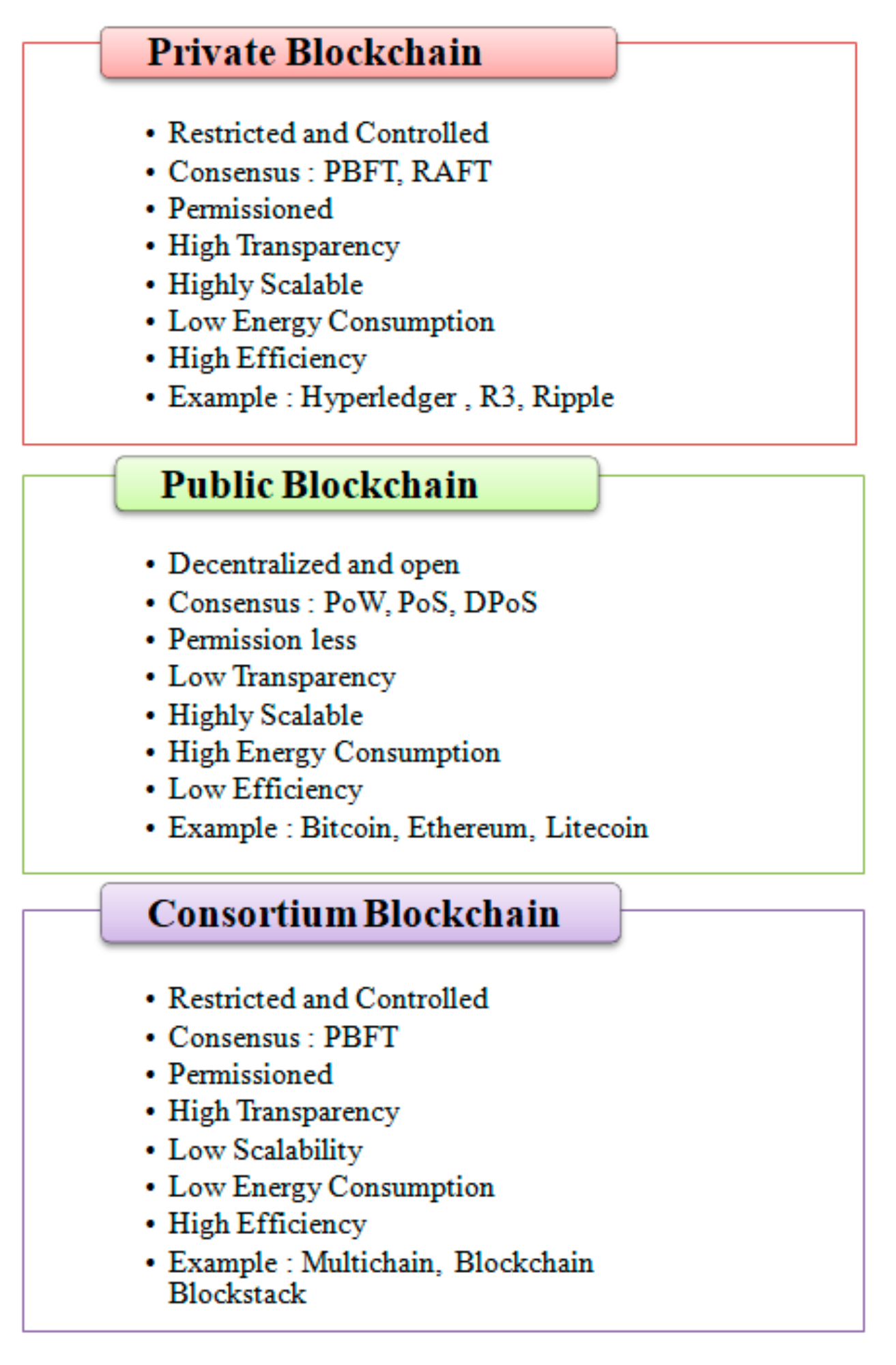
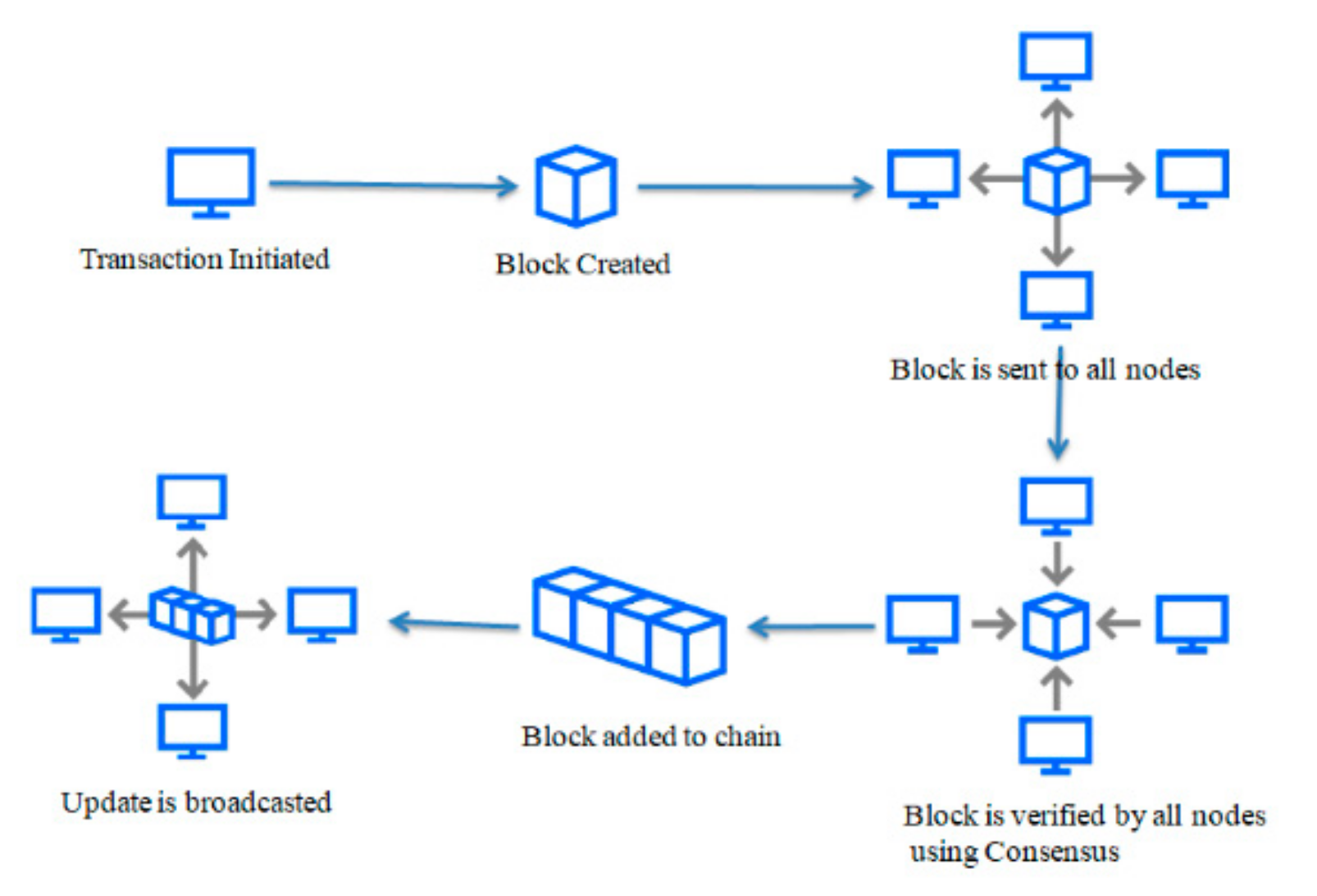
2. Background Study
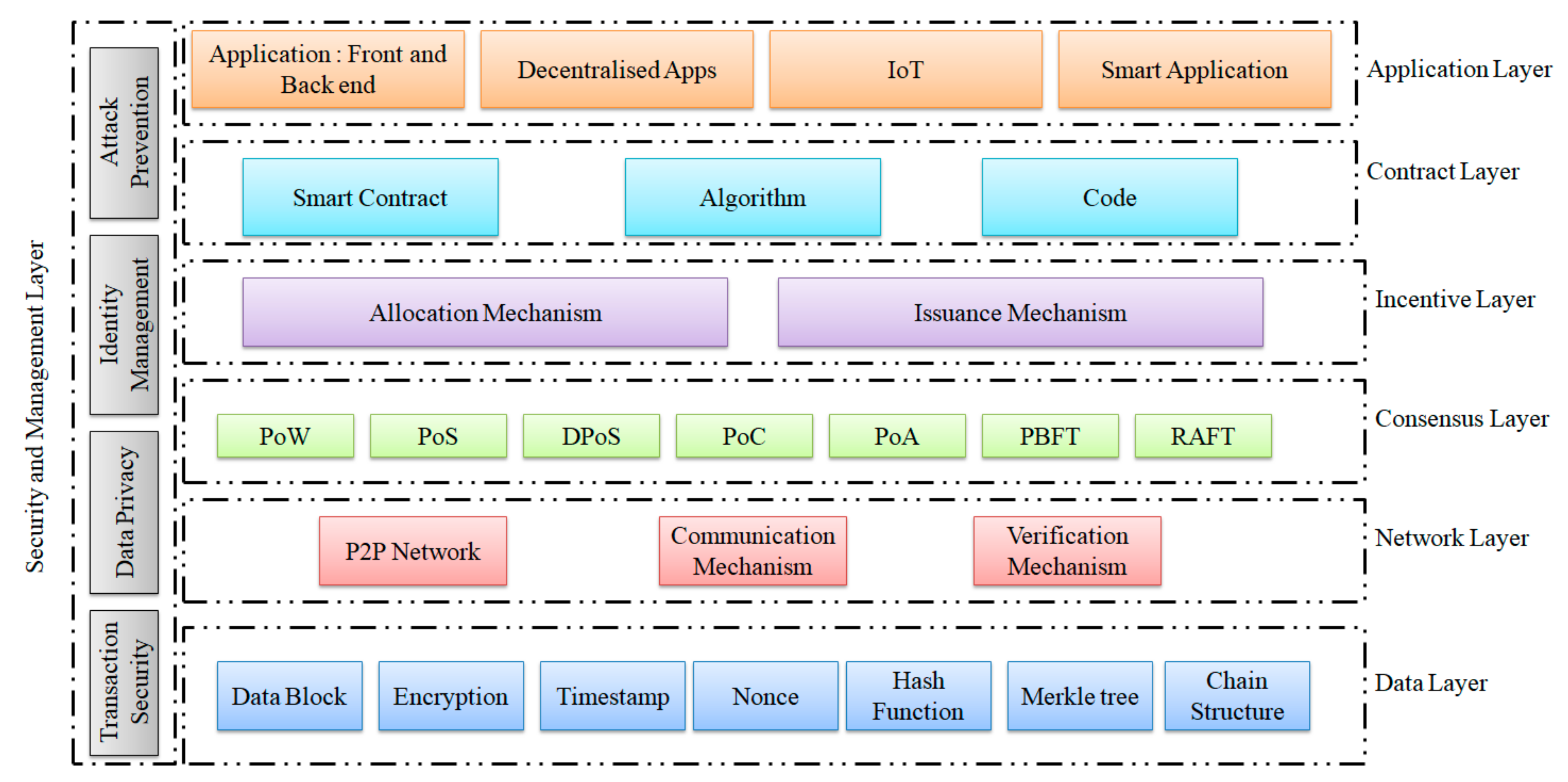
3. Blockchain Architecture
3.1. Data Layer
3.2. Network Layer
3.3. Consensus Layer
3.4. Incentive Layer
3.5. Contract Layer
3.6. Application Layer
4. Blockchain Applications
4.1. Smart HealthCare
4.2. Smart Transportation
4.3. Smart Grids
4.4. Financial Systems
5. Security Attacks in Blockchain
5.1. Blockchain Network Attacks
5.2. User Wallet Attacks
5.3. Smart Contract Attacks
5.4. Transaction Verification Mechanism Attacks
5.5. Mining Pool Attacks
6. Challenges
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Puthal, D.; Mohanty, S.; Kougianos, E.; Das, G. When Do We Need the Blockchain? IEEE Consum. Electron. Mag. 2021, 10, 53–56. [Google Scholar] [CrossRef]
- Aleksieva, V.; Valchanov, H.; Huliyan, A. Smart Contracts based on Private and Public Blockchains for the Purpose of Insurance Services. In Proceedings of the 2020 International Conference Automatics and Informatics (ICAI), Varna, Bulgaria, 1–3 October 2020; pp. 1–4. [Google Scholar] [CrossRef]
- Baucas, M.J.; Gadsden, S.A.; Spachos, P. IoT-based Smart Home Device Monitor Using Private Blockchain Technology and Localization. IEEE Netw. Lett. 2021. [Google Scholar] [CrossRef]
- Jiang, S.; Cao, J.; Wu, H.; Yang, Y. Fairness-based Packing of Industrial IoT Data in Permissioned Blockchains. IEEE Trans. Ind. Inform. 2020. [Google Scholar] [CrossRef]
- Kim, D.; Doh, I.; Chae, K. Improved Raft Algorithm exploiting Federated Learning for Private Blockchain performance enhancement. In Proceedings of the 2021 International Conference on Information Networking (ICOIN), Jeju Island, Korea, 13–16 January 2021; pp. 828–832. [Google Scholar] [CrossRef]
- Guo, X.; Guo, Q.; Liu, M.; Wang, Y.; Ma, Y.; Yang, B. A Certificateless Consortium Blockchain for IoTs. In Proceedings of the 2020 IEEE 40th International Conference on Distributed Computing Systems (ICDCS), Singapore, 29 November–1 December 2020; pp. 496–506. [Google Scholar] [CrossRef]
- Meng, T.; Wolter, K.; Zhao, Y.; Xu, C. On Consortium Blockchain Consistency: A Queueing Network Model Approach. IEEE Trans. Parallel Distrib. Syst. 2021, 32, 1369–1382. [Google Scholar] [CrossRef]
- Kwak, S.; Lee, J. Implementation of Blockchain based P2P Energy Trading Platform. In Proceedings of the 2021 International Conference on Information Networking (ICOIN), Jeju Island, Korea, 13–16 January 2021; pp. 5–7. [Google Scholar] [CrossRef]
- Toshniwal, B.; Kataoka, K. Comparative Performance Analysis of Underlying Network Topologies for Blockchain. In Proceedings of the 2021 International Conference on Information Networking (ICOIN), Jeju Island, Korea, 13–16 January 2021; pp. 367–372. [Google Scholar] [CrossRef]
- Nguyen, D.C.; Pathirana, P.N.; Ding, M.; Seneviratne, A. BEdgeHealth: A Decentralized Architecture for Edge-based IoMT Networks Using Blockchain. IEEE Internet Things J. 2021. [Google Scholar] [CrossRef]
- Abdella, J.; Tari, Z.; Anwar, A.; Mahmood, A.; Han, F. An Architecture and Performance Evaluation of Blockchain-based Peer-to-Peer Energy Trading. IEEE Trans. Smart Grid 2021. [Google Scholar] [CrossRef]
- Xiao, Y.; Zhang, P.; Liu, Y. Secure and Efficient Multi-Signature Schemes for Fabric: An Enterprise Blockchain Platform. IEEE Trans. Inf. Forensics Secur. 2021, 16, 1782–1794. [Google Scholar] [CrossRef]
- Zhang, L.; Ge, Y. Identity Authentication Based on Domestic Commercial Cryptography with Blockchain in the Heterogeneous Alliance Network. In Proceedings of the 2021 IEEE International Conference on Consumer Electronics and Computer Engineering (ICCECE), Guangzhou, China, 15–17 January 2021; pp. 191–195. [Google Scholar] [CrossRef]
- Ahmad, A.; Saad, M.; Kim, J.; Nyang, D.; Mohaisen, D. Performance Evaluation of Consensus Protocols in Blockchain-based Audit Systems. In Proceedings of the 2021 International Conference on Information Networking (ICOIN), Jeju Island, Korea, 13–16 January 2021; pp. 654–656. [Google Scholar] [CrossRef]
- Nair, P.R.; Dorai, D.R. Evaluation of Performance and Security of Proof of Work and Proof of Stake using Blockchain. In Proceedings of the 2021 Third International Conference on Intelligent Communication Technologies and Virtual Mobile Networks (ICICV), Tirunelveli, India, 4–6 February 2021; pp. 279–283. [Google Scholar] [CrossRef]
- Machacek, T.; Biswal, M.; Misra, S. Proof of X: Experimental Insights on Blockchain Consensus Algorithms in Energy Markets. In Proceedings of the 2021 IEEE Power & Energy Society Innovative Smart Grid Technologies Conference (ISGT), Washington, DC, USA, 15–19 September 2021; pp. 1–5. [Google Scholar] [CrossRef]
- Yang, J.; Paudel, A.; Gooi, H.B. Compensation for Power Loss by a Proof-of-Stake Consortium Blockchain Microgrid. IEEE Trans. Ind. Inform. 2021, 17, 3253–3262. [Google Scholar] [CrossRef]
- Cong, X.; Zi, L. DTNB: A blockchain transaction framework with discrete token negotiation for the delay tolerant network. IEEE Trans. Netw. Sci. Eng. 2021. [Google Scholar] [CrossRef]
- Zhang, J. A Hybrid Model for Central Bank Digital Currency Based on Blockchain. IEEE Access 2021. [Google Scholar] [CrossRef]
- Qu, Y.; Pokhrel, S.R.; Garg, S.; Gao, L.; Xiang, Y. A Blockchained Federated Learning Framework for Cognitive Computing in Industry 4.0 Networks. IEEE Trans. Ind. Inform. 2021, 17, 2964–2973. [Google Scholar] [CrossRef]
- Jiang, S.; Cao, J.; McCann, J.A.; Yang, Y.; Liu, Y.; Wang, X.; Deng, Y. Privacy-Preserving and Efficient Multi-Keyword Search over Encrypted Data on Blockchain. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; pp. 405–410. [Google Scholar] [CrossRef]
- Cagigas, D.; Clifton, J.; Diaz-Fuentes, D.; Fernández-Gutiérrez, M. Blockchain for Public Services: A Systematic Literature Review. IEEE Access 2021, 9, 13904–13921. [Google Scholar] [CrossRef]
- Omar, I.A.; Jayaraman, R.; Debe, M.S.; Salah, K.; Yaqoob, I.; Omar, M. Automating Procurement Contracts in the Healthcare Supply Chain Using Blockchain Smart Contracts. IEEE Access 2021, 9, 37397–37409. [Google Scholar] [CrossRef]
- Iqbal, N.; Jamil, F.; Ahmad, S.; Kim, D. A Novel Blockchain-Based Integrity and Reliable Veterinary Clinic Information Management System Using Predictive Analytics for Provisioning of Quality Health Services. IEEE Access 2021, 9, 8069–8098. [Google Scholar] [CrossRef]
- Egala, B.S.; Pradhan, A.K.; Badarla, V.R.; Mohanty, S.P. Fortified-Chain: A Blockchain Based Framework for Security and Privacy Assured Internet of Medical Things with Effective Access Control. IEEE Internet Things J. 2021. [Google Scholar] [CrossRef]
- Abdellatif, A. MEdge-Chain: Leveraging Edge Computing and Blockchain for Efficient Medical Data Exchange. IEEE Internet Things J. 2021. [Google Scholar] [CrossRef]
- De Brito Gonçalves, J.P.; De Resende, H.C.; Municio, E.; Villaça, R.; Marquez-Barja, J.M. Securing E-Health Networks by applying Network Slicing and Blockchain Techniques. In Proceedings of the 2021 IEEE 18th Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 9–12 January 2021; pp. 1–2. [Google Scholar] [CrossRef]
- Aich, S. Protecting Personal Healthcare Record Using Blockchain & Federated Learning Technologies. In Proceedings of the 2021 23rd International Conference on Advanced Communication Technology (ICACT), PyeongChang, Korea, 7–10 February 2021; pp. 109–112. [Google Scholar] [CrossRef]
- Jiang, S.; Cao, J.; Wu, H.; Yang, Y.; Ma, M.; He, J. BlocHIE: A BLOCkchain-Based Platform for Healthcare Information Exchange. In Proceedings of the 2018 IEEE International Conference on Smart Computing (SMARTCOMP), Taormina, Italy, 18–20 June 2018; pp. 49–56. [Google Scholar] [CrossRef]
- Li, C.; Fu, Y.; Yu, F.R.; Luan, T.H.; Zhang, Y. Vehicle Position Correction: A Vehicular Blockchain Networks-Based GPS Error Sharing Framework. IEEE Trans. Intell. Transp. Syst. 2021, 22, 898–912. [Google Scholar] [CrossRef]
- Zhang, C.; Zhu, L.; Xu, C.; Sharif, K. PRVB: Achieving Privacy-Preserving and Reliable Vehicular Crowdsensing via Blockchain Oracle. IEEE Trans. Veh. Technol. 2021, 70, 831–843. [Google Scholar] [CrossRef]
- Sadiq, A.; Javed, M.U.; Khalid, R.; Almogren, A.; Shafiq, M.; Javaid, N. Blockchain Based Data and Energy Trading in Internet of Electric Vehicles. IEEE Access 2021, 9, 7000–7020. [Google Scholar] [CrossRef]
- Maaroufi, S.; Pierre, S. BCOOL: A Novel Blockchain Congestion Control Architecture Using Dynamic Service Function Chaining and Machine Learning for Next Generation Vehicular Networks. IEEE Access 2021. [Google Scholar] [CrossRef]
- Yang, Q.; Wang, H. Privacy-Preserving Transactive Energy Management for IoT-aided Smart Homes via Blockchain. IEEE Internet Things J. 2021. [Google Scholar] [CrossRef]
- Xu, S.; Guo, C.; Hu, R.Q.; Qian, Y. BlockChain Inspired Secure Computation Offloading in a Vehicular Cloud Network. IEEE Internet Things J. 2021. [Google Scholar] [CrossRef]
- J, G.; Ding, X.; Wu, W. A Blockchain-Enabled Ecosystem for Distributed Electricity Trading in Smart City. IEEE Internet Things J. 2021, 8, 2040–2050. [Google Scholar] [CrossRef]
- Samy, S.; Azab, M.; Rizk, M. Towards a Secured Blockchain-based Smart Grid. In Proceedings of the 2021 IEEE 11th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 27–30 January 2021; pp. 1066–1069. [Google Scholar] [CrossRef]
- Tariq, M.; Ali, M.; Naeem, F.; Poor, H.V. Vulnerability Assessment of 6G-Enabled Smart Grid Cyber–Physical Systems. Internet Things J. IEEE 2021, 8, 5468–5475. [Google Scholar] [CrossRef]
- Niloy, F.A.; Nayeem, M.A.; Rahman, M.; Dowla, M. Blockchain-Based Peer-to-Peer Sustainable Energy Trading in Microgrid using Smart Contracts. In Proceedings of the 2021 2nd International Conference on Robotics, Electrical and Signal Processing Techniques (ICREST), Dhaka, Bangladesh, 5–7 January 2021; pp. 61–66. [Google Scholar] [CrossRef]
- Tao, M.; Wang, Z.; Qu, S. Research on Multi-Microgrids Scheduling Strategy Considering Dynamic Electricity Price Based on Blockchain. IEEE Access 2021. [Google Scholar] [CrossRef]
- Ayaz, F.; Sheng, F.; Tian, D.; Guan, Y.L. A Proof-of-Quality-Factor (PoQF)-Based Blockchain and Edge Computing for Vehicular Message Dissemination. IEEE Internet Things J. 2021, 8, 2468–2482. [Google Scholar] [CrossRef]
- Lin, I.-C.; Liao, T.-C. A Survey of Blockchain Security Issues and Challenges. Int. J. Netw. Secur. 2017, 19, 653–659. [Google Scholar]
- Liu, Z.; Yin, X. LSTM-CGAN: Towards Generating Low-Rate DDoS Adversarial Samples for Blockchain-Based Wireless Network Detection Models. IEEE Access 2021, 9, 22616–22625. [Google Scholar] [CrossRef]
- Apostolaki, M.; Zohar, A.; Vanbever, L. Hijacking bitcoin: Routing attacks on cryptocurrencies. In Proceedings of the 38th IEEE Symposium on Security and Privacy (Oakland), San Jose, CA, USA, 22–26 May 2017; pp. 375–392. [Google Scholar]
- Douceur, J.R. The sybil attack. In The First International Workshop on Peer-to-Peer Systems, ser. IPTPS ’01; Springer: London, UK, 2002; pp. 251–260. [Google Scholar]
- Saad, M.; Spaulding, J.; Njilla, L.; Kamhoua, C.; Shetty, S.; Nyang, D.; Mohaisen, A. Exploring the Attack Surface of Blockchain: A Systematic Overview. IEEE Commun. Surv. Tutor. 2020, 22, 3. [Google Scholar] [CrossRef]
- Nicolas, K.; Wang, Y.; Giakos, G.C.; Wei, B.; Shen, H. Blockchain System Defensive Overview for Double-Spend and Selfish Mining Attacks: A Systematic Approach. IEEE Access 2021, 9, 3838–3857. [Google Scholar] [CrossRef]
- Bastiaan, M. Preventing the 51%-Attack: A Stochastic Analysis of Two Phase Proof of Work in Bitcoin. 2015. Available online: http://referaat.cs.utwente.nl/conference/22/paper/7473/preventingthe-51-attack-a-stochasticanalysis-oftwo-phase-proof-of-work-in-bitcoin.pdf (accessed on 19 March 2021).
- Wang, S.; Cheng, Y.; Yin, B.; Cao, X.; Zhang, S.; Cai, L.X. A Selfish Attack on Chainweb Blockchain. In Proceedings of the GLOBECOM 2020—2020 IEEE Global Communications Conference, Taipei, Taiwan, 7–11 December 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Leelavimolsilp, T.; Tran-Thanh, L.; Stein, S. On the preliminary investigation of selfish mining strategy with multiple selfish miners. arXiv 2018, arXiv:1802.02218. [Google Scholar]
- Marcus, Y.; Heilman, E.; Goldberg, S. Low-resource eclipse attacks on ethereum’s peer-to-peer network. IACR Cryptol. ePrint Arch. 2018, 2018, 236. [Google Scholar]
- Fleder, M.; Kester, M.S.; Pillai, S. Bitcoin transaction graph analysis. arXiv 2015, arXiv:1502.01657. [Google Scholar]
- Vyas, C.A.; Lunagaria, M. Security concerns and issues for bitcoin. In Proceedings of the National Conference cum Workshop on Bioinformatics and Computational Biology NCWBCB, Majitar, India, 10–12 May 2014. [Google Scholar]
- Ghiasi, M.; Dehghani, M.; Niknam, T.; Kavousi-Fard, A.; Siano, P.; Alhelou, H. Cyber-Attack Detection and Cyber-Security Enhancement in Smart DC-Microgrid Based on Blockchain Technology and Hilbert Huang Transform. IEEE Access 2021, 9, 29429–29440. [Google Scholar] [CrossRef]
- Finney, H. The Finney Attack (the bitcoin Talk Forum). 2013. Available online: https://bitcointalk.org/index.php (accessed on 19 March 2021).
- Eyal, I.; Gencer, A.E.; Sirer, E.G.; van Renesse, R. Bitcoin-ng: A scalable blockchain protocol. In Proceedings of the 13th USENIX Symposium on Networked Systems Design and Implementation (NSDI), Santa Clara, CA, USA, 16–18 March 2016; pp. 45–59. [Google Scholar]
- Singh, S.; Hosen, A.; Yoon, B. Blockchain Security Attacks, Challenges, and Solutions for the Future Distributed IoT Network. IEEE Access 2021, 9, 13938–13959. [Google Scholar] [CrossRef]
- Qi, X.; Zhang, Z.; Jin, C.; Zhou, A. A Reliable Storage Partition for Permissioned Blockchain. IEEE Trans. Knowl. Data Eng. 2021, 33, 14–27. [Google Scholar] [CrossRef]
- Qiu, C.; Ren, X.; Cao, Y.; Mai, T. Deep Reinforcement Learning Empowered Adaptivity for Future Blockchain Networks. IEEE Open J. Comput. Soc. 2021, 2, 99–105. [Google Scholar] [CrossRef]
- Sun, W.; Li, S.; Zhang, Y. Edge caching in blockchain empowered 6G. China Commun. 2021, 18, 1–17. [Google Scholar] [CrossRef]
- Wu, H.; Cao, J.; Jiang, S.; Yang, R.; Yang, Y.; Hey, J. TSAR: A Fully-Distributed Trustless Data ShARing Platform. In Proceedings of the 2018 IEEE International Conference on Smart Computing (SMARTCOMP), Taormina, Italy, 18–20 June 2018; pp. 350–355. [Google Scholar] [CrossRef]
- Chen, N.; Cho, D.S.-Y. A Blockchain based Autonomous Decentralized Online Social Network. In Proceedings of the 2021 IEEE International Conference on Consumer Electronics and Computer Engineering (ICCECE), Guangzhou, China, 15–17 January 2021; pp. 186–190. [Google Scholar] [CrossRef]
- Jiang, S.; Cao, J.; Wu, H.; Yang, Y. Data Management in Supply Chain Using Blockchain: Challenges and a Case Study. In Proceedings of the 2019 28th International Conference on Computer Communication and Networks (ICCCN), Valencia, Spain, 29 July–1 August 2019; pp. 1–8. [Google Scholar] [CrossRef]
- Ricci, L.; Maesa, D.D.F.; Favenza, A.; Ferro, E. Blockchains for COVID-19 Contact Tracing and Vaccine Support: A Systematic Review. IEEE Access 2021, 9, 37936–37950. [Google Scholar] [CrossRef]
- Sun, S.; Du, R.; Chen, S.; Li, W. Blockchain-Based IoT Access Control System: Towards Security, Lightweight, and Cross-Domain. IEEE Access 2021, 9, 36868–36878. [Google Scholar] [CrossRef]
- Mohanta, B.K.; Jena, D.; Ramasubbareddy, S.; Daneshmand, M.; Gandomi, A. Addressing Security and Privacy Issues of IoT Using Blockchain Technology. IEEE Internet Things J. 2021, 8, 881–888. [Google Scholar] [CrossRef]
- Li, Y.; Ruan, Q. Petri Net Modeling and Analysis of the Drug Traceability System Based on Blockchain. In Proceedings of the 2021 IEEE International Conference on Consumer Electronics and Computer Engineering (ICCECE), Guangzhou, China, 15–17 January 2021; pp. 591–595. [Google Scholar] [CrossRef]
- Ali, O.; Jaradat, A.; Kulakli, A.; Abuhalimeh, A. A Comparative Study: Blockchain Technology Utilization Benefits, Challenges and Functionalities. IEEE Access 2021, 9, 12730–12749. [Google Scholar] [CrossRef]
- Mazumder, M.M.H.U.; Islam, T.; Alam, M.R.; Al Haque, M.E.; Islam, M.S.; Alam, M.M. A Novel Framework for Blockchain Based Driving License Management and Driver’s Reputation System for Bangladesh. In Proceedings of the 2021 2nd International Conference on Robotics, Electrical and Signal Processing Techniques (ICREST), Dhaka, Bangladesh, 5–7 January 2021; pp. 263–268. [Google Scholar] [CrossRef]
- Hewa, T.M.; Hu, Y.; Liyanage, M.; Kanhare, S.; Ylianttila, M. Survey on Blockchain based Smart Contracts: Technical Aspects and Future Research. IEEE Access 2021. [Google Scholar] [CrossRef]
- Sadawi, A.; Hassan, M.S.; Ndiaye, M. A Survey on the Integration of Blockchain with IoT to Enhance Performance and Eliminate Challenges. IEEE Access 2021, 9. [Google Scholar] [CrossRef]
- Rottenstreich, O. Sketches for Blockchains. In Proceedings of the 2021 International Conference on COMmunication Systems & NETworkS (COMSNETS), Bangalore, India, 5–9 January 2021; pp. 254–262. [Google Scholar] [CrossRef]

| Consensus Protocol | Description | Language Used | Advantage | Disadvantage |
|---|---|---|---|---|
| Proof-of-Work (POW) [15,16] | Miners contend with one another to address a numerical puzzle to add a block in the chain and a get reward | Solidity C++ Golang | Double spending is avoided Everyone mines | More computational power 51% attack Longer processing time |
| Proof-of-Stake (POS) [15,17] | Miners are replaced with validators Validators are chosen based on a combination of random selection and wealth (stake value) If a validator acts maliciously then its stake gets slashed | Native | More secure Energy efficient | “The nothing at stake” problem Only a few selected “validators” |
| Delegated Proof-of-Stake (DPoS) [18,19] | An election system is maintained to choose the node which verifies the block | Native | Protects from double spending attacks Energy efficient | “The nothing at stake” problem Partially centralized |
| Proof-of-Burn (PoB) [14] | Coin burning strategy | C++ Golang Solidity Serpent | Minimal energy consumption Less energy consumption. | Requires lot of resources Need more testing |
| Proof-of-Authority (PoA) [16] | Combination of PoW and PoS | Native | High performance and fault tolerance Avoids 51% attack | Not fully decentralized Scalability issue |
| Proof-of-Elapsed Time (PoET) [14] | Follows a lottery system A random waiting time is generated and the node with the shortest waiting time will win the block | Python | Less power consumption Cost efficient Enhanced transparency | Hardware security Same node may be elected as leader |
| Proof-of-Capacity (PoC) [14] | Hard disk space is used to choose the miners Here you will pay for hard drive space | - | Energy efficient No need to upgrade hard drives | High energy consumption Node with more disk space chosen as miner |
| Practical Byzantine Fault Tolerance (PBFT) [19,14] | Consensus is obtained even if the network contain malicious nodes Here malicious node should not exceed one-third of the total number of nodes | Golang Java | Does not compute mathematical calculations Does not require multiple confirmations | Communication overhead |
| RAFT [5] | Voting based method Elect leader in randomized way and perform verification process to achieve consistency | Scala Java Go C++ | Easy to implement Process speed is high | Low security Tolerant in handling network partition |
| Framework | Description | Language | Testing | Blockchain |
|---|---|---|---|---|
| Hardhat | Open source | JavaScript | Waffle | Hardhat runtime environment/local, testnets, mainnet |
| Truffle | Open source with paid upgrades | JavaScript | Has testing | Ganache/local, testnets, mainnet |
| Brownie | Open source | Python | Has testing | Ganache/local, testnets, mainnet |
| Embark | Open source | JavaScript | Has testing | Ganache/local, testnets, mainnet |
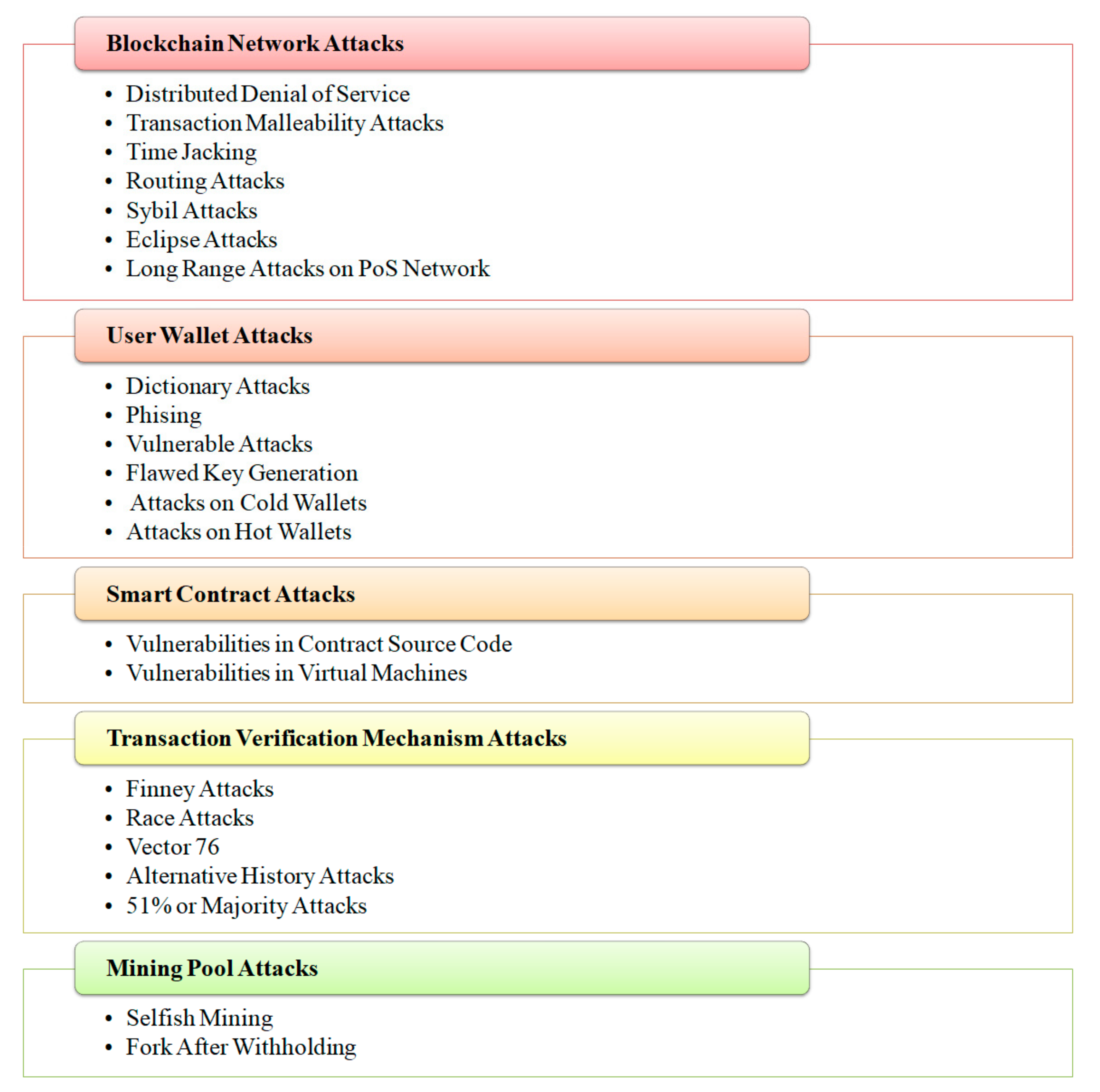
| Attacks | Types | Description | Impact | Solution |
|---|---|---|---|---|
| Blockchain Network Attacks [44,51,45] | Distributed Denial of Service | Disconnect mining pool | Theft Malicious mining | fee-based and age-based designs increase block size |
| Transaction Malleability Attacks | Tricks a victim to pay twice | Throughput Leads to DoS, DDoS attacks | Segregated Witness (SegWit) process | |
| Time Jacking | Vulnerability in timestamps | Chain Splitting Revenue Loss Delay Malicious mining | Restricting acceptance time range Use node system time Synchronized clocking | |
| Routing Attacks | Tampering | Partition attack Delay attack | Peer Monitoring | |
| Sybil Attacks | Hacker will take control of multiple nodes | Throughput Leads to DoS, DDoS attacks Double spending | Behaviour Monitoring Incentive Mechanism | |
| Eclipse Attacks | Hack large number of IP addresses | Partitioning | Disabling incoming connections Peer Monitoring Choose specific outgoing connections | |
| Long Range Attacks on PoS Network | Based on PoS | Attempt to mint more blocks Stake bleeding Posterior corruption | - | |
| User Wallet Attacks [52,53] | Dictionary Attacks | Find weakness in cryptographic algorithm | Find wallet credentials | - |
| Phising | Hack logs | - | ||
| Vulnerable Attacks | Vulnerability in cryptographic signature | Theft | - | |
| Flawed Key Generation | Vulnerability in key generation | Poor randomness of input to generate key Still possible in ECDSA algorithm | - | |
| Attacks on Cold Wallets | Exploits bugs in the network. Obtain private key as well as PIN | Theft Revenue Loss | Backups | |
| Attacks on Hot Wallets | Internet-connected apps are used to store keys | Steal fund | Wallet Insurance | |
| Smart Contract Attacks [54] | Vulnerabilities in Contract Source Code | Bugs in source code | Delay Theft Revenue Loss | - |
| Vulnerabilities in Virtual Machines | Vulnerability in EVM with DAO attacks | Immutable defects Bugs in access control Short address attack | - | |
| Transaction Verification Mechanism Attacks [55,48] | Finney Attacks | Create identical transactions | Revenue Loss | Increase Block Reward |
| 51% or Majority Attacks | Get 51% control of network hash rate | Chain Splitting Revenue Loss Malicious mining Double spend Prevent transaction from being confirmed | Two phased proof of work | |
| Mining Pool Attacks [50,56,49] | Selfish Mining | Peer to peer system | Revenue Loss Malicious mining | Time-stamped blocks |
| Fork After Withholding | Malicious miners hide the winning blocks | Malicious mining | Enforce PoW submission |
| Research Direction | Uses | Issue | Challenge |
|---|---|---|---|
| Security and privacy [65,66] | Decentralized network | Users remain pseudonymous than being anonymous | Ensure anonymity |
| Storage [67,58] | Cloud storage Decentralized storage system Proof of retrievability | Immense storage capacity Lack of trust Lack of privacy and security | Ensure privacy and security |
| Energy Efficiency [68] | Consensus schemes Proof of Trust | Computationally expensive (PoW) Lacks scalability(PBFT) | Ensure energy efficient consensus scheme |
| Scalability [69] | Consensus schemes | POW: enhances scalability but suffers from high latency, low throughput and double spending attack PBFT: achieves consensus in the presence of malicious replicas, but suffers from scalability problems | Ensure scalability and performance |
| Incentive Mechanism [70] | Incentive scheme | Double spending attacks Participation of malicious nodes | Punishment scheme for malicious nodes |
| Interoperability [71] | Consensus algorithm | Dissimilar consensus mechanism | Design interoperable protocols |
| Regulation [62,72] | Decentralization | Regularity issue Unstructured data formats No proper storage standards | Ensure regulation rule for data integrity |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Guru, D.; Perumal, S.; Varadarajan, V. Approaches towards Blockchain Innovation: A Survey and Future Directions. Electronics 2021, 10, 1219. https://doi.org/10.3390/electronics10101219
Guru D, Perumal S, Varadarajan V. Approaches towards Blockchain Innovation: A Survey and Future Directions. Electronics. 2021; 10(10):1219. https://doi.org/10.3390/electronics10101219
Chicago/Turabian StyleGuru, Divya, Supraja Perumal, and Vijayakumar Varadarajan. 2021. "Approaches towards Blockchain Innovation: A Survey and Future Directions" Electronics 10, no. 10: 1219. https://doi.org/10.3390/electronics10101219
APA StyleGuru, D., Perumal, S., & Varadarajan, V. (2021). Approaches towards Blockchain Innovation: A Survey and Future Directions. Electronics, 10(10), 1219. https://doi.org/10.3390/electronics10101219







