FPGA Implementation of Mutual Authentication Protocol for Medication Security System
Abstract
:1. Introduction
2. Background Review
2.1. Medication Errors
2.2. WSN Security and Privacy Issues
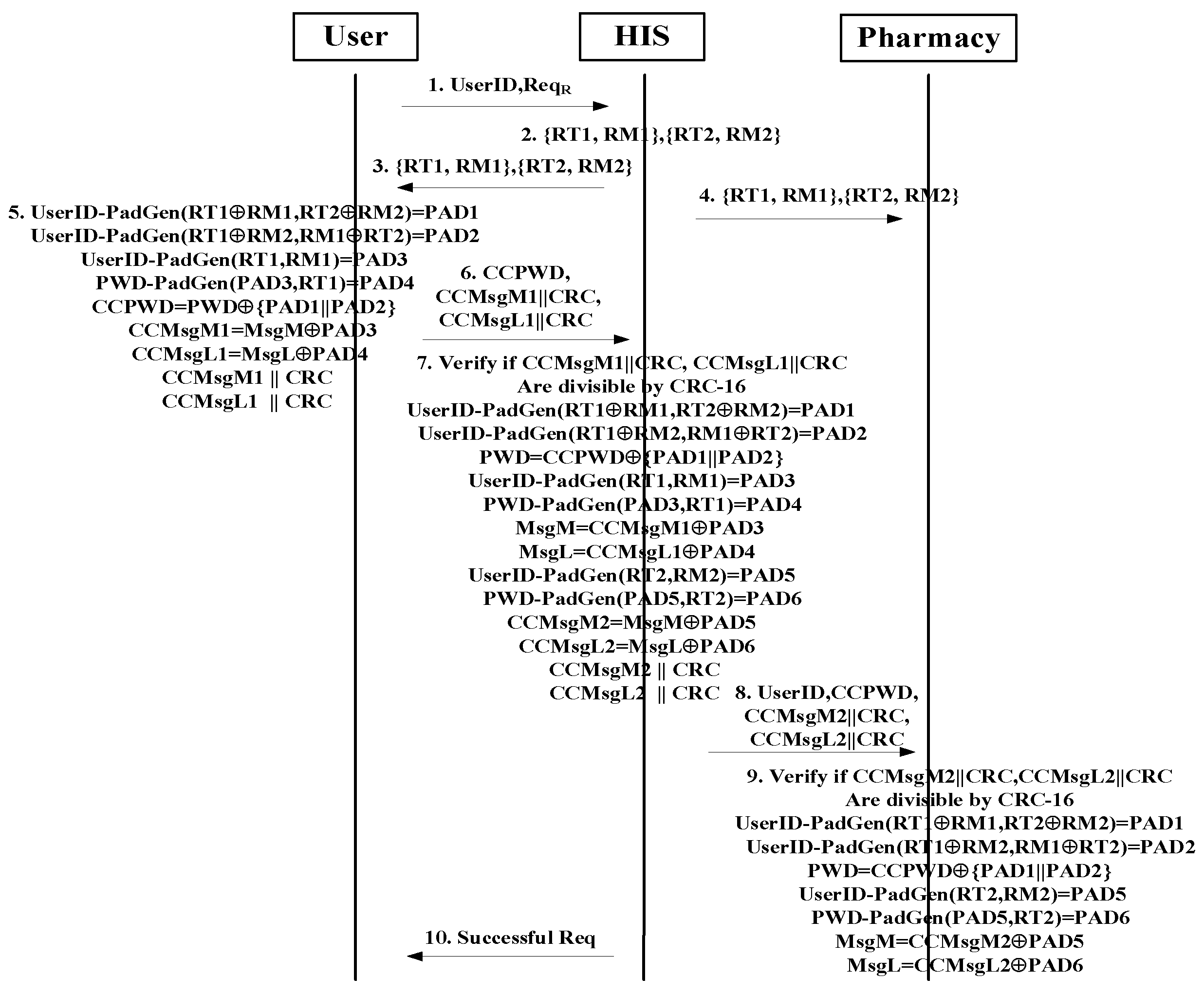
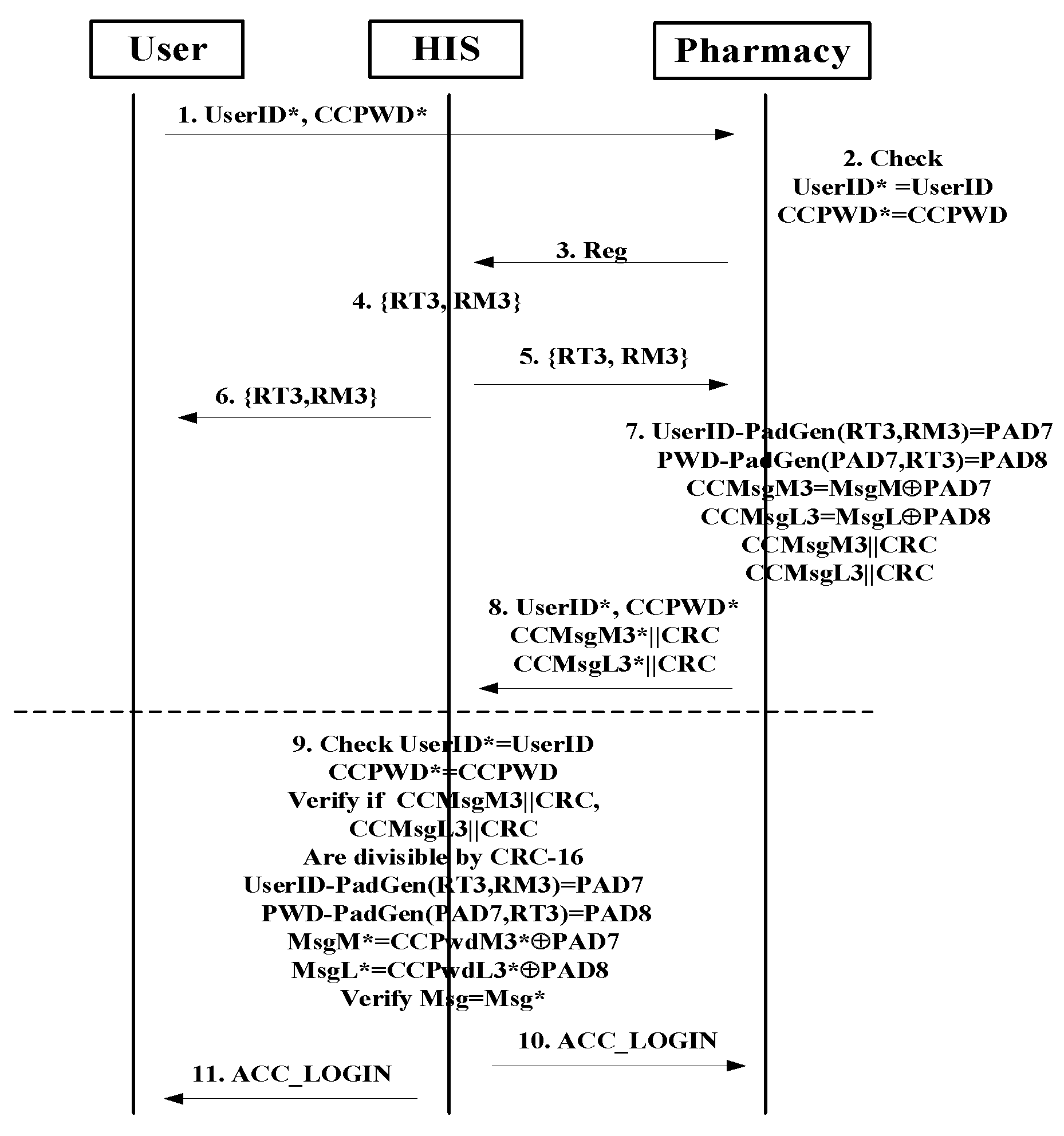
3. Medication Safety WSN Authentication Scheme
3.1. Mutual Authentication Algorithm
‖mdt3 mdt3+16 mdm3 mdm3+16‖mdt4 mdt4+16 mdm4 mdm4+16 (Base 2),
= dv1 dv2 dv3 dv4 (Base 16).
‖adt3 adt3+16 adm3 adm3+16‖adt4 adt4+16 adm4 adm4+16 (Base 2),
= kv1 kv2 kv3 kv4 (Base 16),
= PAD.
3.2. Definition of the Proposed Medication Safety WSN Protocol
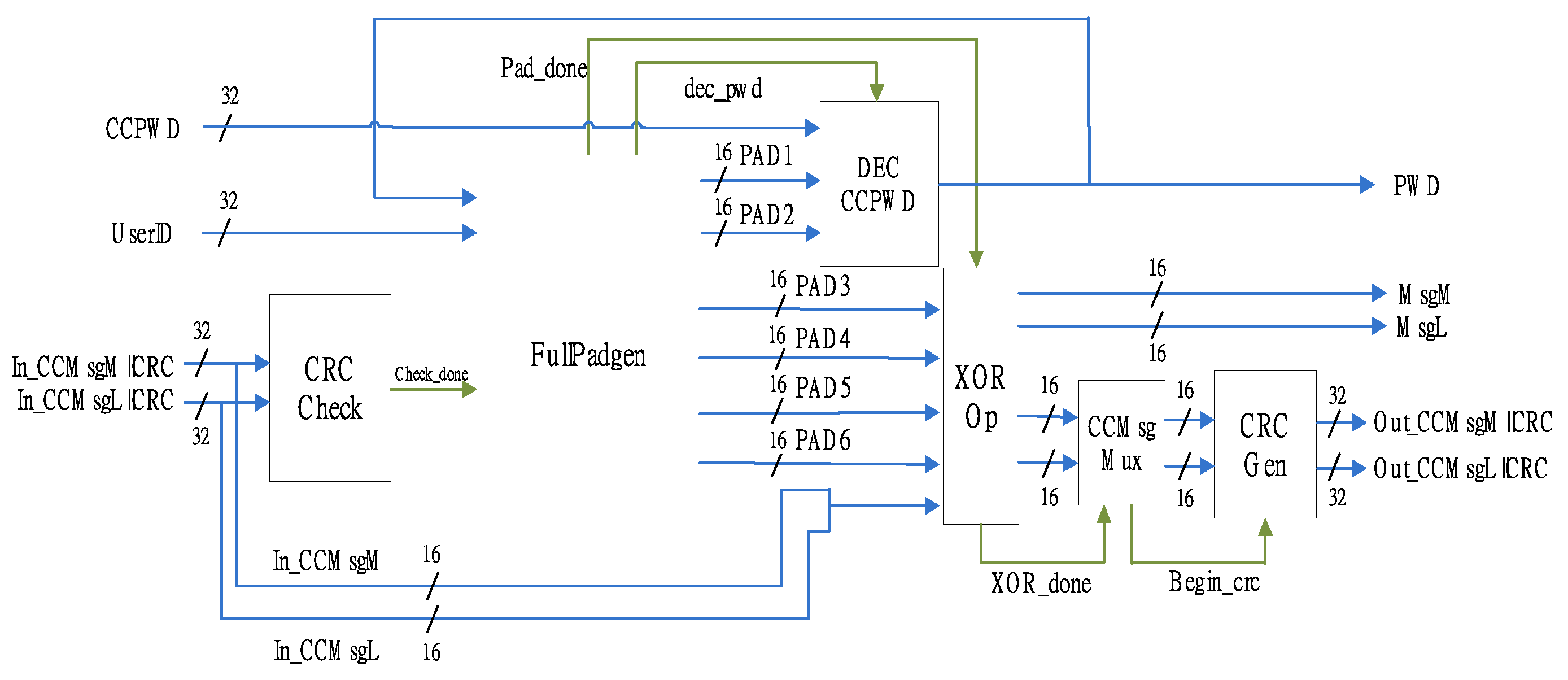
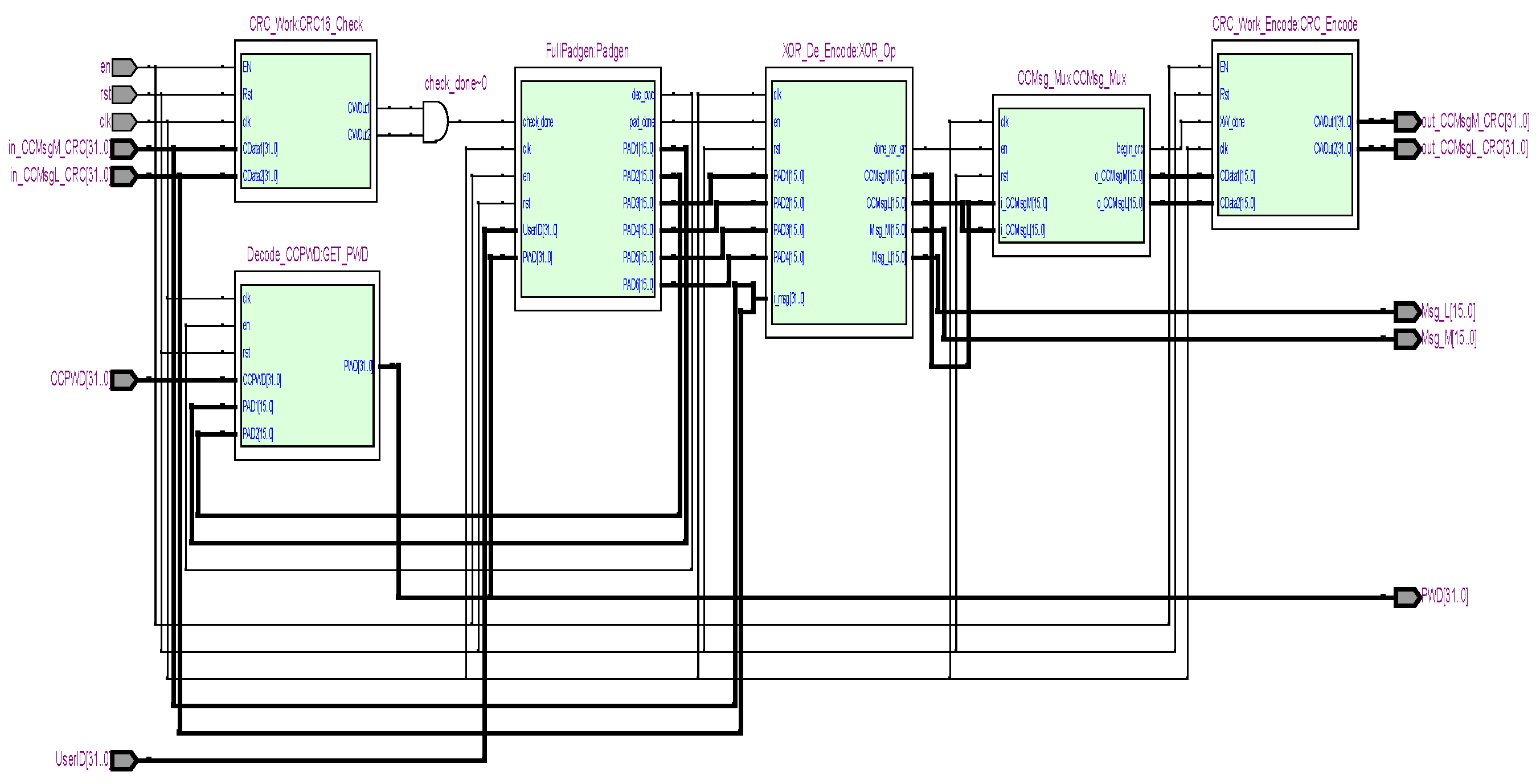
4. Design and Implementation Results
4.1. XOR Method Medication Safety System Architecture
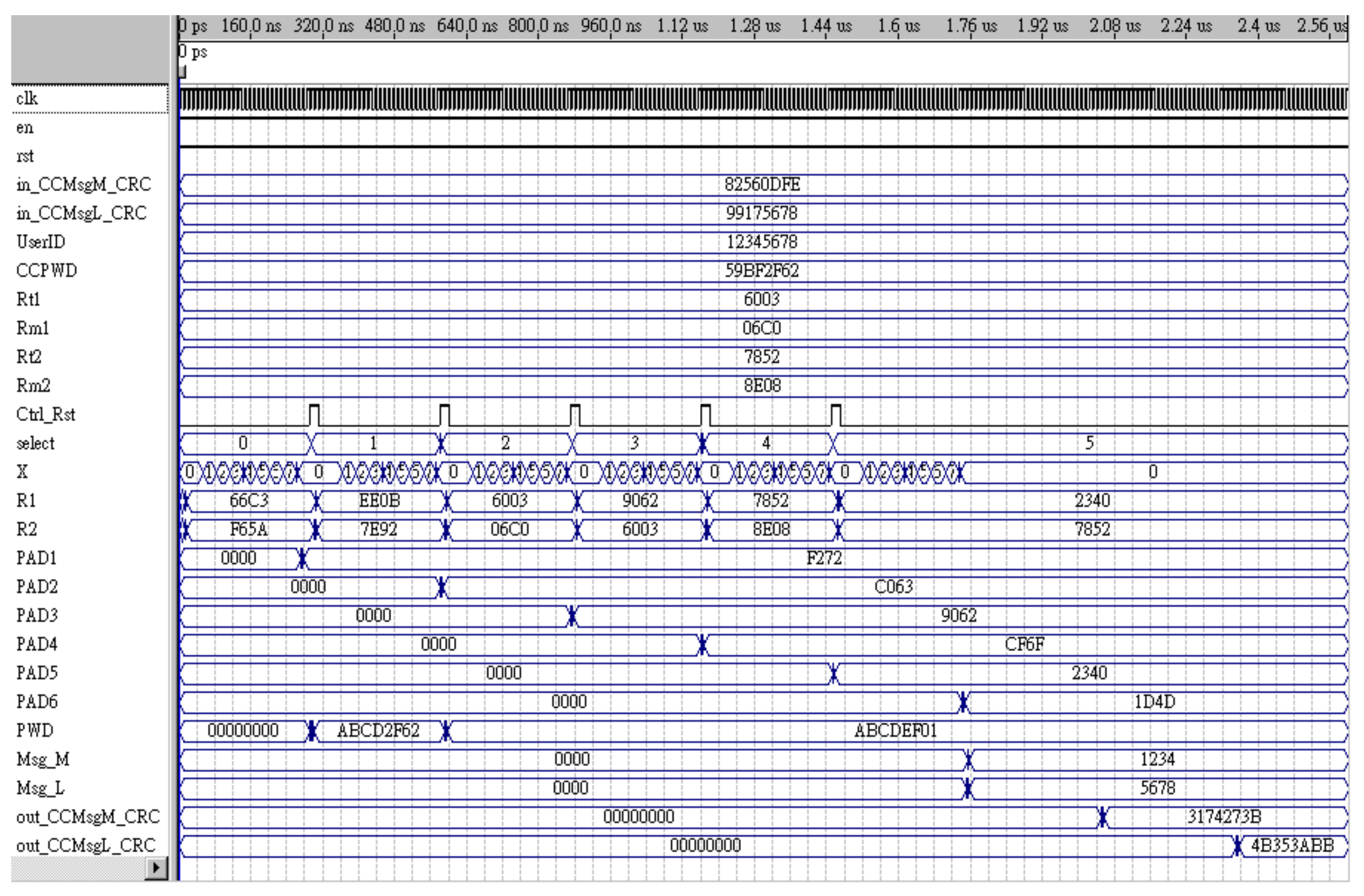
4.2. Verilog Simulation Results
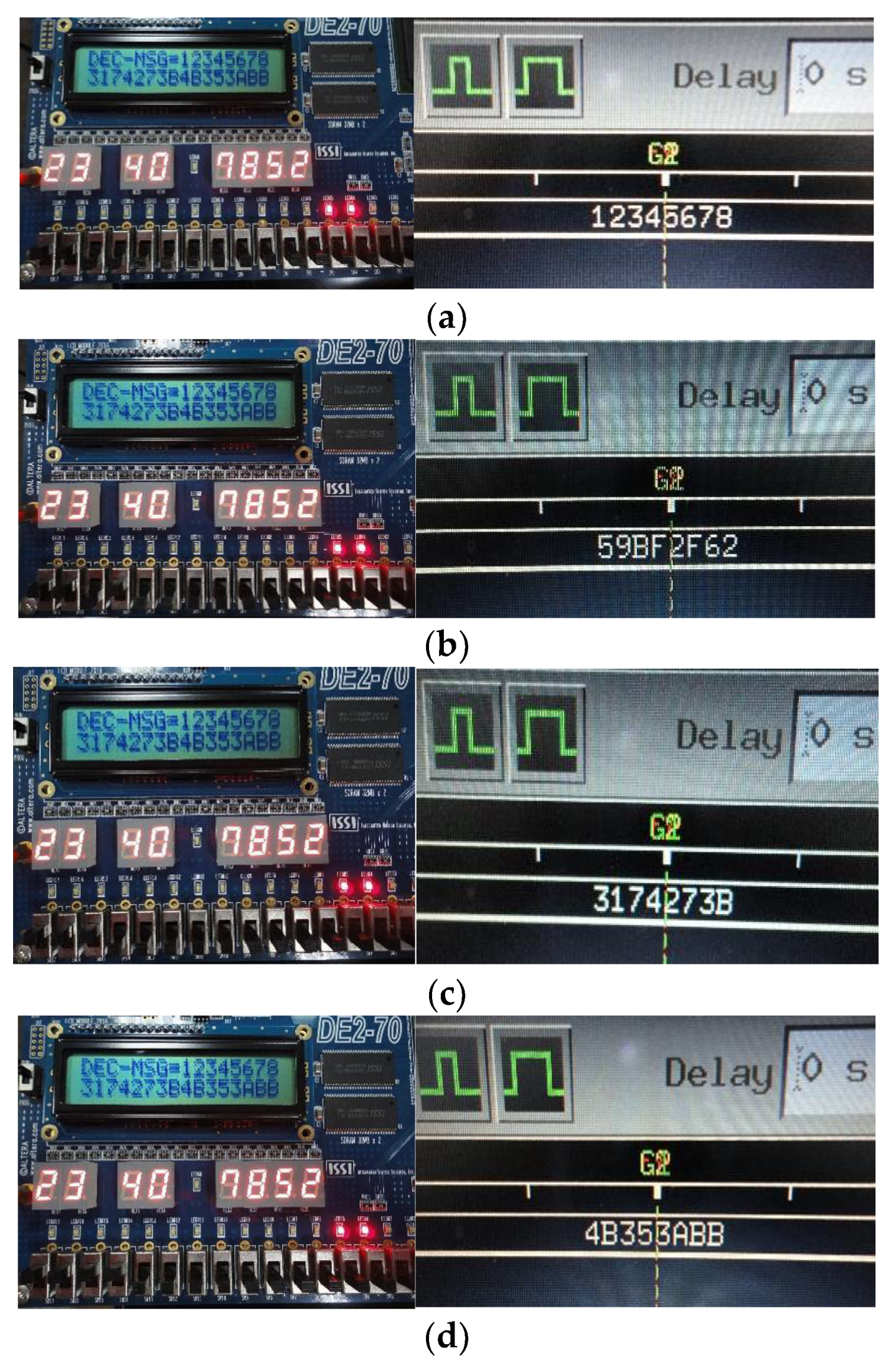
4.3. FPGA Hardware Verification of the XOR-Padgen Algorithm
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Ghayvat, H.; Mukhopadhyay, S.; Gui, X.; Suryadevara, N. WSN-and IoT-based smart homes and their extension to smart buildings. Sensors 2015, 15, 10350–10379. [Google Scholar] [CrossRef] [Green Version]
- Dadhirao, C.; Sangam, R. Localization Techniques Using Machine Learning Algorithms. In Architectural Wireless Networks Solutions and Security Issues. Lecture Notes in Networks and Systems; Das, S.K., Samanta, S., Dey, N., Patel, B.S., Hassanien, A.E., Eds.; Springer: Singapore, 2021; Volume 196. [Google Scholar] [CrossRef]
- DAR. Proceedings of the Distributed Sensor Nets Workshop, Pittsburgh, PA, USA, 7–8 December 1978; Department of Computer Science, Carnegie Mellon University: Pittsburgh, PA, USA, 1978. [Google Scholar]
- Granjal, J.; Monteiro, E.; Silva, J.S. Security in the Integration of Low-Power Wireless Sensor Networks with the Internet: A Survey. Ad Hoc Netw. 2015, 24, 264–287. [Google Scholar] [CrossRef]
- Ragnoli, M.; Barile, G.; Leoni, A.; Ferri, G.; Stornelli, V. An Autonomous Low-Power LoRa-Based Flood-Monitoring System. J. Low Power Electron. Appl. 2020, 10, 15. [Google Scholar] [CrossRef]
- Onasanya, A.; Lakkis, S.; Elshakankiri, M. Implementing IoT/WSN based smart Saskatchewan Healthcare System. Wirel. Netw. 2019, 25, 3999–4020. [Google Scholar] [CrossRef]
- Parrilla, L.; Castillo, E.; Lopez-Ramos, J.A.; Alvarez-Bermejo, J.A.; Garcia, A.; Morales, D.P. Unified Compact ECC-AES Co-Processor with Group-Key Support for IoT Devices in Wireless Sensor Networks. Sensors 2018, 18, 251. [Google Scholar] [CrossRef] [Green Version]
- Wazid, M.; Das, A.K.; Hussain, R.; Succi, G.; Rodrigues, J.J.P.C. Authentication in cloud-driven IoT-based big data environment: Survey and outlook. J. Syst. Archit. 2019, 97, 185–196. [Google Scholar] [CrossRef]
- Kirimtat, A.; Krejcar, O.; Kertesz, A.; Tasgetiren, M.F. Future Trends and Current State of Smart City Concepts: A Survey. IEEE Access 2020, 8, 86448–86467. [Google Scholar] [CrossRef]
- Aronson, J.K. Medication errors: What they are, how they happen, and how to avoid them. QJM Int. J. Med. 2009, 102, 513–521. [Google Scholar] [CrossRef]
- Kavanagh, C. Medication governance: Preventing errors and promoting patient safety. Br. J. Nurs. 2017, 26, 159–165. [Google Scholar] [CrossRef]
- Aghili, S.F.; Mala, H.; Shojafar, M.; Peris-Lopez, P. LACO: Lightweight Three-Factor Authentication, Access Control and Ownership Transfer Scheme for E-Health Systems in IoT. Future Gener. Comput. Syst. 2019, 96, 410–424. [Google Scholar] [CrossRef]
- O’Dorisio, D. Securing Wireless Networks for HIPAA Compliance. 2003. Available online: http://www.sans.org/rr/whitepapers/awareness/1335.php (accessed on 28 October 2021).
- Chang, C.-H. Controversy over information privacy arising from the Taiwan National Health Insurance Database examining the Taiwan Taipei High Administrative Court Judgment No. 102-Su-36 (TSAI v. NHIA). Pace Int’l L. Rev. 2016, 28, 29. [Google Scholar]
- Kumar, P.; Lee, H.J. Security issues in healthcare applications using wireless medical sensor networks: A survey. Sensors 2012, 12, 55–91. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Tehseen, M.; Javed, H.; Shah, I.H.; Ahmed, S. A Lightweight Key Negotiation and Authentication Scheme for Large Scale WSNs. In Recent Trends and Advances in Wireless and IoT-Enabled Networks; Springer: Cham, Switzerland, 2019; pp. 225–235. [Google Scholar]
- Nabavi, S.R.; Mousavi, S.M. A review of distributed dynamic key management schemes in wireless sensor networks. JCP 2018, 13, 77–89. [Google Scholar] [CrossRef]
- Haseeb, K.; Almogren, A.; Islam, N.; Ud Din, I.; Jan, Z. An Energy-Efficient and Secure Routing Protocol for Intrusion Avoidance in IoT-Based WSN. Energies 2019, 12, 4174. [Google Scholar] [CrossRef] [Green Version]
- Wang, D.; He, D.; Wang, P.; Chu, C.H. Anonymous Two-Factor Authentication in Distributed Systems: Certain Goals Are Beyond Attainment. IEEE Trans. Dependable Secur. Comput. 2015, 12, 428–442. [Google Scholar] [CrossRef]
- Dishongh, T.J.; McGrath, M. Wireless Sensor Networks for Healthcare Applications; Artech House: Norwood, MA, USA, 2009. [Google Scholar]
- Huang, Y.J.; Lin, W.C.; Li, H.L. Efficient Implementation of RFID Mutual Authentication Protocol. IEEE Trans. Ind. Electron. 2012, 59, 4784–4791. [Google Scholar] [CrossRef]

| Symbol | Description |
|---|---|
| UserID | User identification |
| PWD | User password |
| RN | Random number |
| Rtx, Rmx | Random number |
| Padgen () | Coding function |
| In_CCPWx | Input cover coding password |
| In_CCMsgx | Input cover coding message |
| Out_CCPWx | Output cover coding password |
| Out _CCMsgx | Output cover coding message |
| Req | Request |
| PADx | Encryption pad |
| CRC | Cyclic redundancy code |
| ⊕ | XOR |
| ‖ | Concatenation |
| NPWD | New password |
| Family | Quartus II 8.0 Cyclone II |
|---|---|
| Device | EP2C70F896C6 |
| Logic elements | 1536/68,416 |
| Registers | 705 |
| PLLs | 0/4 |
| M4Ks | 0/250 |
| Total memory bits (Total RAM block bits) | 0/1,152,000 |
| Logic array blocks (Block interconnects) | 2063/197,592 |
| I/O pins | 259/622 |
| Clock pins | 1/8 |
| Maximum fan-out | 705 |
| Total fan-out | 8410 |
| Average fan-out | 2.91 |
| Embedded multipliers | 0/300 |
| FPGA clock source (MHz) | 50 |
| Fmax (MHz) | 174.40 |
| Clock period (ns) | 6.281 |
| Longest Path Delay (ns) | 5.512 |
| Worst Case Setup time (tsu) (ns) | 7.214 |
| Worst Case Hold time (th) (ns) | 0.496 |
| Total Power (mW) | 246.07 |
| Dynamic Power (mW) | 20.79 |
| Static Power (mW) | 155.13 |
| I/O Power (mW) | 70.15 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lin, W.-C.; Huang, P.-K.; Pan, C.-L.; Huang, Y.-J. FPGA Implementation of Mutual Authentication Protocol for Medication Security System. J. Low Power Electron. Appl. 2021, 11, 48. https://doi.org/10.3390/jlpea11040048
Lin W-C, Huang P-K, Pan C-L, Huang Y-J. FPGA Implementation of Mutual Authentication Protocol for Medication Security System. Journal of Low Power Electronics and Applications. 2021; 11(4):48. https://doi.org/10.3390/jlpea11040048
Chicago/Turabian StyleLin, Wei-Chen, Po-Kai Huang, Chung-Long Pan, and Yu-Jung Huang. 2021. "FPGA Implementation of Mutual Authentication Protocol for Medication Security System" Journal of Low Power Electronics and Applications 11, no. 4: 48. https://doi.org/10.3390/jlpea11040048
APA StyleLin, W.-C., Huang, P.-K., Pan, C.-L., & Huang, Y.-J. (2021). FPGA Implementation of Mutual Authentication Protocol for Medication Security System. Journal of Low Power Electronics and Applications, 11(4), 48. https://doi.org/10.3390/jlpea11040048






