FGAC: A Fine-Grained Access Control Framework for Supply Chain Data Sharing
Abstract
1. Introduction
- We extend the RBAC (role-based access control) model with attribute keywords and propose a fine-grained access control (FGAC) framework.
- We implement the FGAC framework with smart contract Chaincodes in blockchain Hyperledger Fabric and apply it to the data sharing of the supply chain system in Shanghai Port.
- Using a model-checking tool as the system verification technique, we demonstrate and analyze the feasibility and safety of FGAC framework.
2. Related Work
2.1. Blockchain and Blockchain-Empowered Data Sharing
2.2. Access Control Mechanisms
2.3. Summary
3. Fine-Grained Access Control Framework
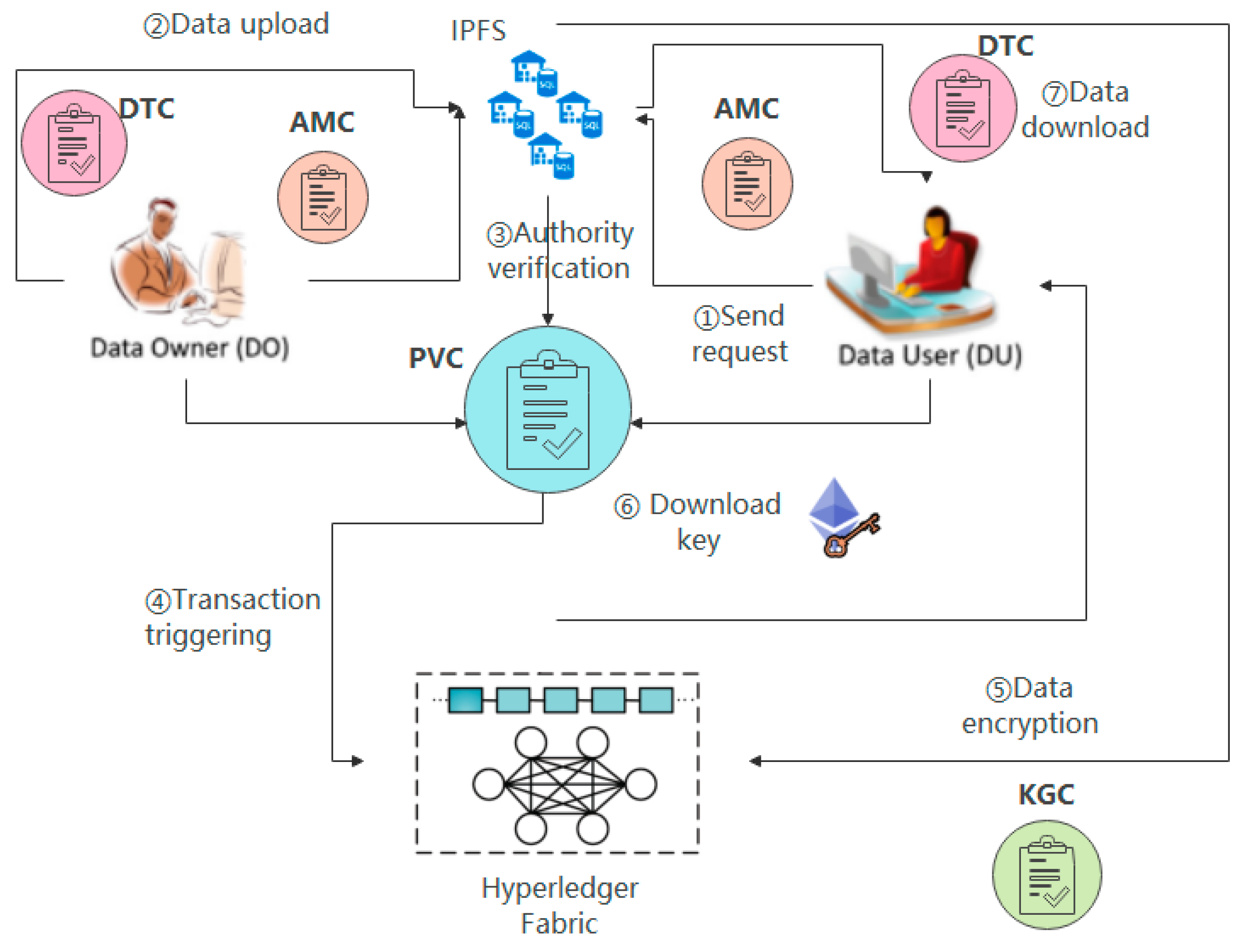
3.1. Access Control Model and Workflow
- Send Request: The DU sends a transaction to the data transmission contract to call the access request function in the contract. The transaction contains the target data and the name of the DU device. By calling the access request function in the contract, the DU role attribute is obtained from the database and triggered. The request access event in this function sends the transaction to the DO.
- Data Upload: The DO sends a transaction request to the data transmission contract through the client to call the data upload function in the contract. The transaction includes the DO device name, the shared data information, and the role attribute keywords.
- Authority Verification: When both the DO and DU are given their role information, and the attribute keywords are set, the transaction is sent to the attribute validation contract, and the validation function in the contract is called to validate the role attributes and data keywords of the DO and DU. Then, the function queries the attribute parameters in the contract according to the passed parameters, obtains the DO and DU parameters such as domain name, attribute, and blockchain account address, and triggers the matching request event in the function to verify whether both parties meet the permissions.
- Trigger Transaction: When the data sharing parties satisfy the access control strategy, and the verification is successful, the transaction is packaged and executed. The request processing function in the property matching contract will call the DO and DU attribute information and send the result to the data transmission contract, triggering data sharing.
- Data Encryption: The key generation contract is called to encrypt the identity information of the DO and DU and the requested shared data. When the verification result is successful, the contract distributes the key to the DU for decryption.
- Data and Key Download: The DU obtains the key through the key generation contract after satisfying the access control strategy, triggers the transaction to view the shared data stored in IPFS, and matches the plaintext and ciphertext to decrypt the required shared data, to obtain plaintext data.
3.2. Event Definition
3.2.1. Transaction Sending and Processing
3.2.2. Event Notification and Execution
3.2.3. Call of Functions
3.2.4. Attribute Information
3.2.5. Strategy Match
3.3. Access Control of Data Sharing Process Using Smart Contract Chaincodes
3.3.1. Attribute Management Contract (AMC)
3.3.2. Data Transmission Contract (DTC)
3.3.3. Property Verification Contract (PVC)
3.3.4. Key Generation Contract (KGC)
4. Application Scenario
- The data owner (DO) has access rights to all raw data;
- Authoritative organizations can obtain some data related to specific projects with high accuracy and timeliness (i.e., they cannot be changed without authorization);
- Data statistic agencies can access supply chain and management data but cannot change them;
- Other relevant departments and data technology companies can only access and obtain shipping-related data, but data accuracy and timeliness are not guaranteed (e.g., there may be a competitive relationship);
- Screening opponents and other companies in the same industry cannot obtain any type of data;
- Other company departments on the chain can share data according to priority, and sensitive data can also be shared depending on the situation and level;
- Neither private nor innovative data can be shared.
5. Experimental Analysis and Verification
5.1. Comparative Analysis
5.2. Verification Results and Analysis
- The built model has no deadlock;Expression: A[] not deadlock
- The data users in the above access control framework can normally access the status of read data;Expression: E<>DU1. read data
- The data users in the above access control framework can normally access the status of obtaining permission;Expression: E<>DU1.get_permission
6. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Ghorbel, A.; Ghorbel, M.; Jmaiel, M. Accountable Privacy Preserving Attribute-Based Access Control for Cloud Services Enforced Using Blockchain. Int. J. Inf. Secur. 2021, 21, 489–508. [Google Scholar] [CrossRef]
- Saini, A.; Zhu, Q.; Singh, N.; Xiang, Y.; Gao, L.; Zhang, Y. A Smart-Contract-Based Access Control Framework for Cloud Smart Healthcare System. IEEE Internet Things J. 2021, 8, 5914–5925. [Google Scholar] [CrossRef]
- Zhu, Y.; Ahn, G.-J.; Hu, H.; Ma, D.; Wang, S. Role-Based Cryptosystem: A New Cryptographic RBAC System Based on Role-Key Hierarchy. IEEE Trans. Inf. Forensic Secur. 2013, 8, 2138–2153. [Google Scholar] [CrossRef]
- Hu, V.C.; Ferraiolo, D.; Kuhn, R.; Schnitzer, A.; Sandlin, K.; Miller, R.; Scarfone, K. Guide to Attribute Based Access Control (ABAC) Definition and Considerations; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2014; p. NIST SP 800-162. [Google Scholar]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Decentralized Bus. Rev. 2008, 4, 2. [Google Scholar]
- Matsumoto, S.; Reischuk, R.M. IKP: Turning a PKI Around with Decentralized Automated Incentives. In Proceedings of the 2017 IEEE Symposium on Security and Privacy (SP), San Jose, CA, USA, 25 May 2017; IEEE: Manhattan, NY, USA, 2017; pp. 410–426. [Google Scholar]
- Das, D.; Banerjee, S.; Biswas, U. A Secure Vehicle Theft Detection Framework Using Blockchain and Smart Contract. Peer-to-Peer Netw. Appl. 2021, 14, 672–686. [Google Scholar] [CrossRef]
- Wood, D.G. Ethereum: A Secure Decentralised Generalised Transaction Ledger. Ethereum Proj. Yellow Pap. 2014, 151, 1–32. [Google Scholar]
- Ouaddah, A.; Elkalam, A.A.; Ouahman, A.A. Towards a Novel Privacy-Preserving Access Control Model Based on Blockchain Technology in IoT. In Europe and MENA Cooperation Advances in Information and Communication Technologies; Rocha, Á., Serrhini, M., Felgueiras, C., Eds.; Advances in Intelligent Systems and Computing; Springer International Publishing: Cham, Switzerland, 2017; Volume 520, pp. 523–533. ISBN 978-3-319-46567-8. [Google Scholar]
- Zhang, Y.; Kasahara, S.; Shen, Y.; Jiang, X.; Wan, J. Smart Contract-Based Access Control for the Internet of Things. IEEE Internet Things J. 2019, 6, 1594–1605. [Google Scholar] [CrossRef]
- Miao, S.; Zhang, X.; Liu, Z. Fine-Grained Access Control Mechanism of Energy Internet. Wuhan Univ. J. Nat. Sci. 2022, 27, 231–239. [Google Scholar] [CrossRef]
- Zikratov, I.; Kuzmin, A.; Akimenko, V.; Niculichev, V.; Yalansky, L. Ensuring Data Integrity Using Blockchain Technology. In Proceedings of the 2017 20th Conference of Open Innovations Association (FRUCT), St-Petersburg, Russia, 3–8 April 2017; IEEE: Manhattan, NY, USA, 2017; pp. 534–539. [Google Scholar]
- Shah, M.; Li, C.; Sheng, M.; Zhang, Y.; Xing, C. CrowdMed: A Blockchain-Based Approach to Consent Management for Health Data Sharing. In Smart Health; Chen, H., Zeng, D., Yan, X., Xing, C., Eds.; Lecture Notes in Computer Science; Springer International Publishing: Cham, Switzerland, 2019; Volume 11924, pp. 345–356. ISBN 978-3-030-34481-8. [Google Scholar]
- Shamshad, S.; Minahil; Mahmood, K.; Kumari, S.; Chen, C.-M. A Secure Blockchain-Based e-Health Records Storage and Sharing Scheme. J. Inf. Secur. Appl. 2020, 55, 102590. [Google Scholar] [CrossRef]
- Spanaki, K.; Karafili, E.; Despoudi, S. AI Applications of Data Sharing in Agriculture 4.0: A Framework for Role-Based Data Access Control. Int. J. Inf. Manag. 2021, 59, 102350. [Google Scholar] [CrossRef]
- Xia, Q.; Sifah, E.B.; Asamoah, K.O.; Gao, J.; Du, X.; Guizani, M. MeDShare: Trust-Less Medical Data Sharing Among Cloud Service Providers via Blockchain. IEEE Access 2017, 5, 14757–14767. [Google Scholar] [CrossRef]
- Shen, B.; Guo, J.; Yang, Y. MedChain: Efficient Healthcare Data Sharing via Blockchain. Appl. Sci. 2019, 9, 1207. [Google Scholar] [CrossRef]
- Zheng, B.K.; Zhu, L.-H.; Shen, M.; Gao, F.; Zhang, C.; Li, Y.-D.; Yang, J. Scalable and Privacy-Preserving Data Sharing Based on Blockchain. J. Comput. Sci. Technol. 2018, 33, 557–567. [Google Scholar] [CrossRef]
- Qin, X.; Huang, Y.; Yang, Z.; Li, X. A Blockchain-Based Access Control Scheme with Multiple Attribute Authorities for Secure Cloud Data Sharing. J. Syst. Archit. 2021, 112, 101854. [Google Scholar] [CrossRef]
- Chi, J.; Li, Y.; Huang, J.; Liu, J.; Jin, Y.; Chen, C.; Qiu, T. A Secure and Efficient Data Sharing Scheme Based on Blockchain in Industrial Internet of Things. J. Netw. Comput. Appl. 2020, 167, 102710. [Google Scholar] [CrossRef]
- Qi, S.; Lu, Y.; Zheng, Y.; Li, Y.; Chen, X. Cpds: Enabling Compressed and Private Data Sharing for Industrial Internet of Things Over Blockchain. IEEE Trans. Ind. Inf. 2021, 17, 2376–2387. [Google Scholar] [CrossRef]
- Li, T.; Ren, W.; Xiang, Y.; Zheng, X.; Zhu, T.; Choo, K.-K.R.; Srivastava, G. FAPS: A Fair, Autonomous and Privacy-Preserving Scheme for Big Data Exchange Based on Oblivious Transfer, Ether Cheque and Smart Contracts. Inf. Sci. 2021, 544, 469–484. [Google Scholar] [CrossRef]
- Ma, X.; Wang, C.; Chen, X. Trusted Data Sharing with Flexible Access Control Based on Blockchain. Comput. Stand. Interfaces 2021, 78, 103543. [Google Scholar] [CrossRef]
- Xu, R.; Chen, Y.; Blasch, E.; Chen, G. BlendCAC: A BLockchain-Enabled Decentralized Capability-Based Access Control for IoTs. In Proceedings of the 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Halifax, NS, Canada, 30 July–3 August 2018; IEEE: Manhattan, NY, USA; pp. 1027–1034. [Google Scholar]
- Cruz, J.P.; Kaji, Y.; Yanai, N. RBAC-SC: Role-Based Access Control Using Smart Contract. IEEE Access 2018, 6, 12240–12251. [Google Scholar] [CrossRef]
- Kamboj, P.; Khare, S.; Pal, S. User Authentication Using Blockchain Based Smart Contract in Role-Based Access Control. Peer-to-Peer Netw. Appl. 2021, 14, 2961–2976. [Google Scholar] [CrossRef]
- Yavari, A.; Panah, A.S.; Georgakopoulos, D.; Jayaraman, P.P.; van Schyndel, R. Scalable Role-Based Data Disclosure Control for the Internet of Things. In Proceedings of the 2017 IEEE 37th International Conference on Distributed Computing Systems (ICDCS), Atlanta, GA, USA, 5–8 June 2017; IEEE: Manhattan, NY, USA, 2017; pp. 2226–2233. [Google Scholar]
- Wang, X.; Jiang, X.; Li, Y. Model for Data Access Control and Sharing Based on Blockchain. J. Softw. 2019, 30, 1661–1669. [Google Scholar] [CrossRef]
- Li, J.; Chen, N.; Zhang, Y. Extended File Hierarchy Access Control Scheme with Attribute-Based Encryption in Cloud Computing. IEEE Trans. Emerg. Top. Comput. 2021, 9, 983–993. [Google Scholar] [CrossRef]
- Su, M.; Li, F.; Shi, G.; Li, L. An Action Based Access Control Model for Multi-Level Security. Int. J. Secur. Its Appl. 2012, 6, 359–366. [Google Scholar]
- Kumar, S.; Bharti, A.K.; Amin, R. Decentralized Secure Storage of Medical Records Using Blockchain and IPFS: A Comparative Analysis with Future Directions. Secur. Priv. 2021, 4, e162. [Google Scholar] [CrossRef]
- Qin, X.; Huang, Y.; Yang, Z.; Li, X. LBAC: A Lightweight Blockchain-Based Access Control Scheme for the Internet of Things. Inf. Sci. 2021, 554, 222–235. [Google Scholar] [CrossRef]
- Chai, B.; Yan, B.; Yu, J.; Wang, G. BHE-AC: A Blockchain-Based High-Efficiency Access Control Framework for Internet of Things. Pers. Ubiquitous Comput. 2021, 26, 971–982. [Google Scholar] [CrossRef]
- Behrmann, G.; David, A.; Larsen, K.G. A Tutorial on Uppaal. In Formal Methods for the Design of Real-Time Systems; Bernardo, M., Corradini, F., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2004; Volume 3185, pp. 200–236. ISBN 978-3-540-23068-7. [Google Scholar]





| Scheme | Distributed | Flexibility | Dynamics | Fine-Grained |
|---|---|---|---|---|
| RBAC [6] | √ 1 | √ | √ | × 2 |
| ABAC [7] | √ | √ | √ | × |
| CapBAC [8] | √ | √ | × | × |
| FGAC | √ | √ | √ | √ |
| Scheme | Characteristics |
|---|---|
| LBAC [32] | It proposes lightweight access control and uses smart contracts to ensure the correctness of outsourced decryption without additional verification on the user side but does not define role attributes. |
| BHEAC [33] | The blockchain-based token request mechanism allows users to request resources in batches and map the obtained tokens to multiple resources; it avoids repeated requests by users but has a broad division of permissions. |
| AI applications [15] | Only access control policies and data sharing protocols (DSAs) were designed to explain research strategies and research decisions, and no experiments and validation were performed. |
| FGAC of this work | It enhances role-based access control by providing different attribute keywords for different types of users. It is implemented in the form of smart contract Chaincodes and evaluated through quantitative verification. |
| Name | Property | Equivalent Property |
|---|---|---|
| Possibly | E<>η | |
| Invariant | A[]η | Not E<>notηη |
| Potentially always | E[]η | |
| Eventually | A<>η | Not E[]notηη |
| Leads to | η→Ψ | A[](ηimply A<>Ψ) |
| Property Formula | Validation Results | Verification Time | Peak Memory Usage |
|---|---|---|---|
| A[] not deadlock | Pass | 0.001 s | 9.306 KB |
| E<>DU1.read_data | Pass | 0.001 s | 9.236 KB |
| E<>DU1.get_permission | Pass | 0.001 s | 9.330 KB |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liu, Y.; Li, X.; Ma, Y. FGAC: A Fine-Grained Access Control Framework for Supply Chain Data Sharing. Systems 2022, 10, 208. https://doi.org/10.3390/systems10060208
Liu Y, Li X, Ma Y. FGAC: A Fine-Grained Access Control Framework for Supply Chain Data Sharing. Systems. 2022; 10(6):208. https://doi.org/10.3390/systems10060208
Chicago/Turabian StyleLiu, Yang, Xiangyu Li, and Yan Ma. 2022. "FGAC: A Fine-Grained Access Control Framework for Supply Chain Data Sharing" Systems 10, no. 6: 208. https://doi.org/10.3390/systems10060208
APA StyleLiu, Y., Li, X., & Ma, Y. (2022). FGAC: A Fine-Grained Access Control Framework for Supply Chain Data Sharing. Systems, 10(6), 208. https://doi.org/10.3390/systems10060208






