Pokémon GO Forensics: An Android Application Analysis
Abstract
:1. Introduction
- (i)
- Identifies the most recent time frame in which the application was run in the foreground of a mobile device by examining the session information contained within the upsight.xml file.
- (ii)
- Identifies the relative geolocation of the user at the end of the most recent time frame in which the application was run in the foreground of a mobile device by examining the information stored in the upsight.db file.
- (iii)
- Identifies additional methods that can indicate user activity prior to and during the most recent time in which the application was run in the foreground of a mobile device by examining the timestamps of files contained in the bundles directory, the timestamp contained in the lastPushTokenRegistrationTime value and the entries contained in the pokémon trainer’s “journal”.
- (iv)
- Determines the use of a Pokémon GO Plus accessory with the application by the presence of the pgp.xml file. This artifact contains the MAC address of the device connected to the mobile device and can be used to link a specific Plus accessory to the mobile device.
- (v)
- Determines the effects of the Pokémon GO Plus accessory on the artifacts that are generated by the application.
- (vi)
- Determines that no geolocation information can be found within the metadata of the images created with the in-game camera feature.
- (vii)
- Provides additional discussion pertaining to the geolocation information that can be found in the cell ID values within the Crittercism logs of applications used prior to 31 July 2016.
- (viii)
- Develops an application-specific analysis tool capable of extracting these artifacts from a backup of the Android application and presenting them to an investigator in an easily readable format. This analysis tool exceeds the capabilities of the Cellebrite’s UFED (Universal Forensic Extraction Device) Physical Analyzer in processing Pokémon GO application data.
2. Literature Review
2.1. Pokémon GO: Game Play
2.2. Forensically Relevant Artifacts
2.3. Limitations of Prior Research
3. Forensic Analysis of Pokémon GO
3.1. Data Acquisition Method
3.2. Preliminary Data Analysis
3.3. Targeted Data Analysis
3.4. Upsight Session Information
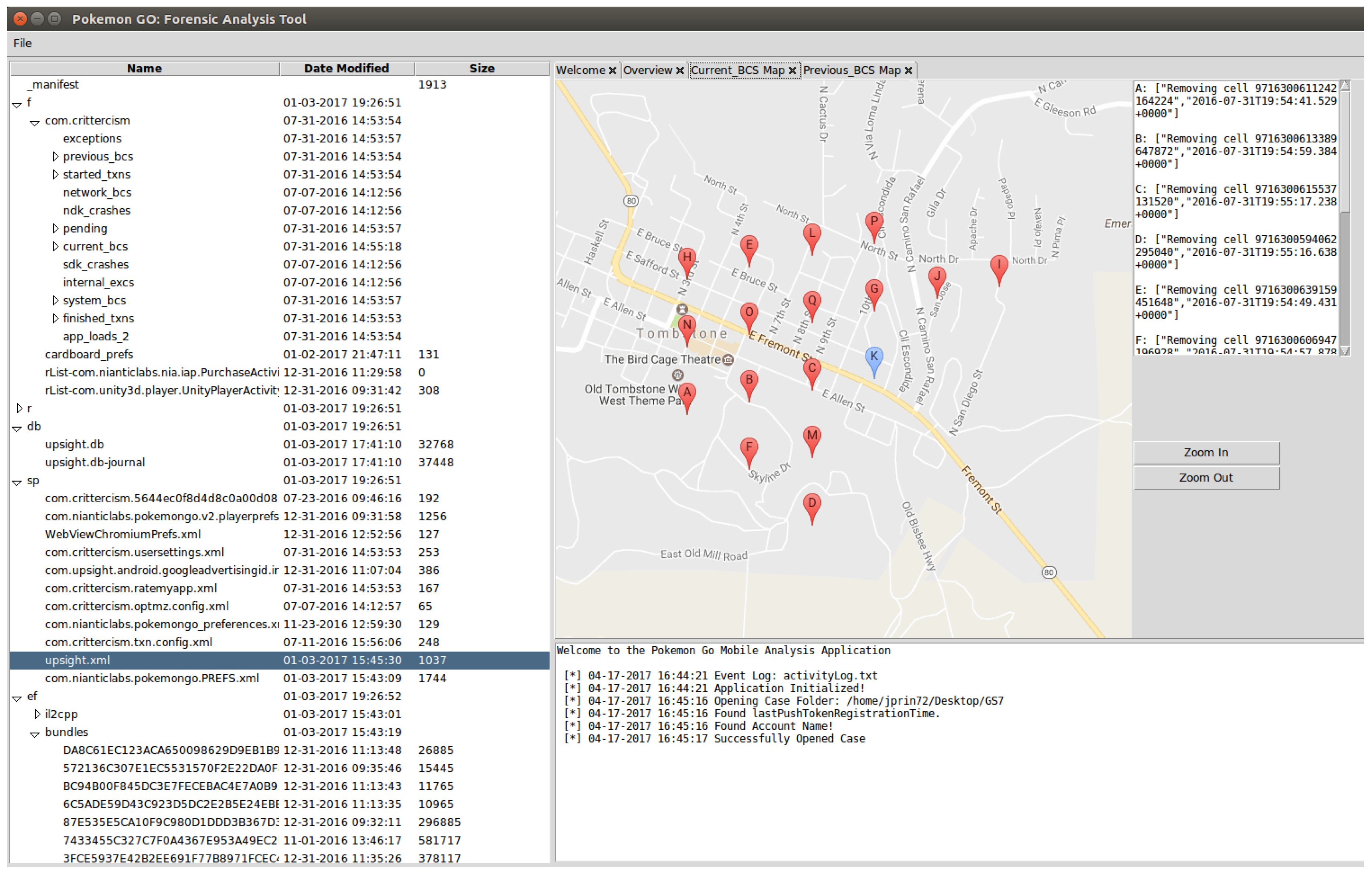
3.4.1. Geolocation Information
3.4.2. Game Play Prior to Current Session
3.4.3. Pokémon GO Plus
<?xml version=‘1.0’ encoding=‘utf-8’ standalone=‘yes’ ?> <map> <string name="BT_KEY_98:B6:E9:0F:53:0C">HSYcDgN5pyxJFGwX7x0mbw== </string> </map>
3.5. Legacy Artifacts: Crittercism Logs
3.6. Image Metadata
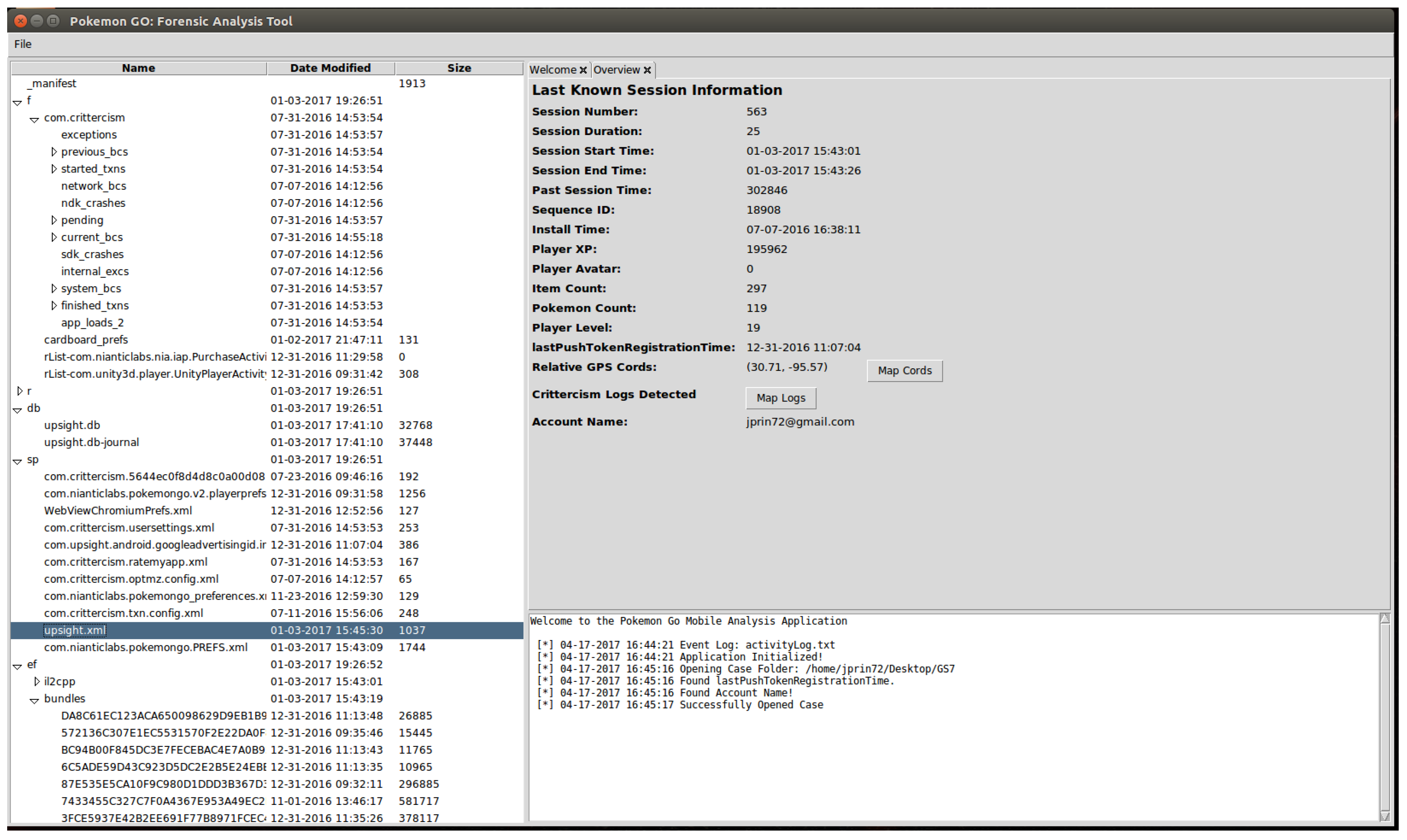
4. Pokémon GO: Forensic Analysis Tool
- Capture Pokémon GO backup: This obtains an ADB backup of only the Pokémon GO application from a target mobile device.
- Capture full backup: This obtains an ADB backup of the entire target mobile device.
- Create new analysis from backup: This creates a new case folder in the current working directory named after the selected Android backup file. The Android backup is then extracted to this directory, and the relevant forensic information is parsed from the application.
- Open case folder: This opens a case folder containing an extracted Android backup file and parses the relevant forensic information from the application.
5. Conclusions
Appendix A. Collection of Phone Dumps
| Data Dump Name | Activity | Notes |
|---|---|---|
| Dump 1 | Start: 24 February 2017 0:41 a.m. Application required update and restart. | Updated to version 0.57.2 Updated to version 0.57.2 |
| Dump 2 | Start: 24 February 2017 1:36 p.m. Location: Apartment Activity: • Captured Pidgey @ 1:38 p.m. • Level 3 • Captured Pikachu @ 1:42 p.m. Terminated Application: 24 February 2017 1:42 p.m. | This dump is designed to act as a baseline image for the application. |
| Dump 3 | Start: 24 February 2017 2:32 p.m. Location: Catholic Student Center Activity: • Captured Hoppip @ 2:35 p.m. • Level 4 • Visited 4 pokéstops around St. Thomas Terminated Application: 24 February 2017 2:40 p.m. | Compared to the previous dump, the starting and ending location for Dump 3 has changed substantially. A few pokémon were captured, and several pokéstops were visited to help determine the creation of new items within the bundles directory. |
| Dump 4 | Start: 24 February 2017 2:45 p.m. Location: Catholic Student Center Activity: • Captured Sentret @ 2:47 p.m. • Captured Spinarak @ 2:48 p.m. • Captured Murkrow @ 2:55 p.m. • Level 5 • Captured Natu @ 3:03 p.m. • Captured Totodile @ 3:08 p.m. • Captured Wooper @ 3:09 p.m. • Captured Caterpie @ 3:11 p.m. Backgrounded App: Phone call @ 3:14 p.m. Resumed App: 3:30 p.m. • Level 6 Backgrounded App: Locked screen @ 3:33 p.m. in front of Library Resumed App: 3:38 p.m. in triangle garden with Swing Statue • Captured Jiggly Puff @ 3:41 • Picture with app camera at intramural fields @ 3:47 p.m. • Picture with app camera at Bowers Stadium @ 3:51 • Captured Spearow @ 3:52 p.m. Terminated Application: 24 February 2017 3:57 p.m. Location: Don Sanders Stadium | This dump covers a large amount of ground, and backgrounds the application multiple times to help determine how the Upsight platform handles the creation of session information. The starting location for this dump also varies significantly from the location in which the application was terminated. Ending Statistics: Pokémon in Possession: 56 Pokémon Eggs: 7 Items: 189 Caught Pokémon: 18 Seen Pokémon: 31 |
| Dump 5 | Start: 24 February 2017 4:23 p.m. Location: Catholic Student Center Activity: • Transferred 31 pokémon • Visit pokéstop Terminated Application: 24 February 2017 4:29 | This dump takes place at the Catholic Student Center. The only actions that occurred was the transfer of 31 pokémon, and a pokéstop visit. This is to help determine how the pokémon count and item count variables are updated. |
| Dump 6 | Start: 24 February 2017 4:33 p.m. Location: Catholic Student Center Activity: • Captured Kakunna @ 4:35 p.m. • Captured Staryu @ 4:36 p.m. Backgrounded App: 24 February 2017 4:38 p.m. Acquired Backup of App (Still running in background): 24 February 2017 4:41 p.m. Application restarted. • Visit pokéstop Terminated Application: 24 February 2017 4:42 p.m. | This dump also takes place at the Catholic Student Center. A few pokémon were captured, and then the application was backgrounded and a backup was taken. This caused the application to restart. Ending Statistics: Pokémon in Possession: 30 Pokémon Eggs: 8 Items: 203 Caught Pokémon: 20 Seen Pokémon: 33 |
| Dump 7 | Start: 24 February 2017 4:47 p.m. Location: Catholic Student Center then drove to Walmart Activity: • Captured Marill @ 4:55 p.m. • Level 7 • Captured Horsea @ 4:57 p.m. Backgrounded App: 24 February 2017 4:57 p.m. at Walmart Terminated Application: 24 February 2017 5:19 at Apartment | This dump was started at the Catholic Student Center. The application was utilized while driving to Walmart. The application was then backgrounded at Walmart. The application was then terminated at the Apartment. This was designed to help determine how the Upsight platform logs geolocation information, and generates session information. |
| Dump 8 | Start: 25 February 2017 3:40 p.m. Terminated Application: 25 February 2017 3:40 p.m. | During this dump, the application was started and then quickly exited after it finished loading. This is to help determine how the Upsight platform creates session information. |
| Dump 9 | Start: 19 March 2017 4:14 p.m. Connected Pokémon Go Plus device Terminated Application: 19 March 2017 4:15 p.m. | This dump was created to act as a baseline for testing the Pokémon GO Plus device. |
| Dump 10 | Start: 19 March 2017 4:43 p.m. Location: Apartment Connected Pokémon GO Plus device Backgrounded App: 4:45 p.m. (locked phone) Went driving around campus. Visited numerous pokéstops and caught several pokémon with Pokémon GO Plus Reconnected Pokémon GO Plus: 4:50 p.m. Terminated Application: 19 March 2017 5:13 p.m. after successful catch. Location: One-way street by Library | This dump focuses on determining the effect that using the Pokémon Go Plus device has on the session information generated by the Upsight platform. The starting and ending locations for the data acquisition very significantly. The application briefly opened before being terminated, as a result of the screen being locked while still running the application. |
| Dump 11 | Start: 19 March 2017 7:09 p.m. Location: Apartment Connected Pokémon GO Plus Backgrounded App: 19 March 2017 7:12 p.m. Caught numerous Pokémon at apartment with Pokémon GO Plus. Terminated Application: 19 March 2017 9:30 p.m. | This dump is focused on determining the effect that using the Pokémon Go Plus device has on the timestamps of files within the bundles directory. There was no change in the starting and ending location of this dump. |
| Dump 12 | Start: 13 April 2017 3:20 p.m. Location: Apartment Connected Pokémon Go Plus device. Backgrounded App: 13 April 2017 3:21 p.m. Activity: • Captured Pokémon @ 3:35 p.m. • Captured Pokémon @ 3:37 p.m. • Captured Pokémon @ 3:42 p.m. Terminated Application: 13 April 2017 3:53 p.m. | This dump was focused on determining the effect that using the Pokémon GO Plus device has on the Upsight session information. All captured pokémon were recorded |
Appendix B. Pokémon Go Targeted Data Analysis
| Item | Dump 1 | Dump 2 | Dump 3 | Dump 4 |
|---|---|---|---|---|
| Session Number | 3 | 4 | 5 | 8 |
| Current Session Duration | 0 | 283 | 491 | 1118 |
| Session Start Timestamp | 24 February 2017, 10:41:40 a.m. | 24 February 2017, 1:36:58 p.m. | 24 February 2017, 2:32:14 | 24 February 2017, 3:38:19 p.m. |
| Last Know Session Time | 24 February 2017, 10:41:40 a.m. | 24 February 2017, 1:41:41 p.m. | 24 February 2017, 2:40:25 p.m. | 24 February 2017, 3:56:57 p.m. |
| Sequence ID | 46 | 69 | 95 | 265 |
| Install Timestamp | 17 January 2017, 1:34:00 p.m. | 17 January 2017, 1:34:00 p.m. | 17 January 2017, 1:34:00 p.m. | 17 January 2017, 1:34:00 p.m. |
| Security ID | 9249052116809215539 | 9249052116809215539 | 9249052116809215539 | 9249052116809215539 |
| Player XP | 2920 | 5270 | 7190 | 18545 |
| Player Avatar | 0 | 0 | 0 | 0 |
| Item Count | 54 | 59 | 64 | 90 |
| Pokémon Count | 0 | 3 | 7 | 12 |
| Player Level | 2 | 3 | 4 | 6 |
| Past Session Time | 1364 | 1364 | 1647 | 4056 |
| Upsight Database Coordinates | 30.72, −95.56 | 30.72, −95.55 | 30.71, −95.54 | |
| lastPushTokenRegistrationTime | 24 February 2017, 10:41:40 a.m. | 24 February 2017, 10:41:40 a.m. | 24 February 2017, 10:41:40 a.m. | 24 February 2017, 10:41:40 a.m. |
| Item | Dump5 | Dump6 | Dump7 | Dump8 |
|---|---|---|---|---|
| Session Number | 9 | 10 | 12 | 13 |
| Current Session Duration | 310 | 289 | 609 | 20 |
| Session Start Timestamp | 24 February 2017, 4:23:56 p.m. | 24 February 2017, 4:33:26 p.m. | 24 February 2017, 4:47:29 p.m. | 25 February 2017, 3:40:21 p.m. |
| Last Know Session Time | 24 February 2017, 4:29:06 p.m. | 24 February 2017, 4:38:15 p.m. | 24 February 2017, 4:57:39 p.m. | 25 February 2017, 3:40:41 p.m. |
| Sequence ID | 309 | 335 | 377 | 385 |
| Install Timestamp | 17 January 2017, 1:34:00 p.m. | 17 January 2017, 1:34:00 p.m. | 17 January 2017, 1:34:00 p.m. | 17 January 2017, 1:34:00 p.m. |
| Security ID | 9249052116809215539 | 9249052116809215539 | 9249052116809215539 | 9249052116809215539 |
| Player XP | 18595 | 20345 | 22045 | 22045 |
| Player Avatar | 0 | 0 | 0 | 0 |
| Item Count | 189 | 193 | 206 | 232 |
| Pokémon Count | 56 | 25 | 31 | 36 |
| Player Level | 6 | 6 | 7 | 7 |
| Past Session Time | 5174 | 5484 | 5827 | 6436 |
| Upsight Database Coordinates | 30.72, −95.55 | 30.72, −95.55 | 30.71, −95.57 | 30.72, −95.56 |
| lastPushTokenRegistrationTime | 24 February 2017, 10:41:40 a.m. | 24 February 2017, 10:41:40 a.m. | 24 February 2017, 10:41:40 a.m. | 24 February 2017, 10:41:40 a.m. |
| Item | Dump9 | Dump10 | Dump11 | Dump12 |
|---|---|---|---|---|
| Session Number | 18 | 21 | 22 | 28 |
| Current Session Duration | 95 | 2 | 143 | 68 |
| Session Start Timestamp | 19 March 2017, 4:14:00 p.m. | 19 March 2017, 5:12:04 p.m. | 19 March 2017, 7:09:51 p.m. | 13 April 2017, 3:20:14 p.m. |
| Last Know Session Time | 19 March 2017, 5:12:06 p.m. | 19 March 2017, 5:12:06 p.m. | 19 March 2017, 7:12:15 p.m. | 13 April 2017, 3:21:22 p.m. |
| Sequence ID | 435 | 454 | 471 | 530 |
| Install Timestamp | 17 January 2017, 1:34:00 p.m. | 17 January 2017, 1:34:00 p.m. | 17 January 2017, 1:34:00 p.m. | 17 January 2017, 1:34:00 p.m. |
| Security ID | 9249052116809215539 | 9249052116809215539 | 9249052116809215539 | 9249052116809215539 |
| Player XP | 23375 | 30800 | 32080 | 38335 |
| Player Avatar | 0 | 0 | 0 | 0 |
| Item Count | 225 | 224 | 260 | 249 |
| Pokémon Count | 41 | 42 | 63 | 72 |
| Player Level | 7 | 8 | 8 | 9 |
| Past Session Time | 6749 | 6996 | 6998 | 7542 |
| Upsight Database Coordinates | 30.72, −95.56 | 30.72, −95.55 | 30.72, −95.56 | 30.72, −95.56 |
| lastPushTokenRegistrationTime | 16 March 2017, 11:04:15 a.m. | 16 March 2017, 11:04:15 a.m. | 16 March 2017, 11:04:15 a.m. | 7 April 2017, 3:51:21 p.m. |
Appendix C. Pokémon GO: Forensic Analysis Tool
References
- PokémonGO. Available online: http://pokemongo.nianticlabs.com/en/ (accessed on 9 April 2017).
- Schwartz, J. Pokémon GO Compared to Other Popular Apps. Available online: https://www.similarweb.com/blog/pokemon-go-compared (accessed on 9 April 2017).
- Schwartz, J. Pokémon GO: The Data Behind America’s Latest Obsession. Available online: https://www.similarweb.com/blog/pokemon-go (accessed on 9 April 2017).
- 2017 U.S. Cross-Platform Future in Focus. Available online: http://www.comscore.com/Insights/Presentations-and-Whitepapers/2017/2017-US-Cross-Platform-Future-in-Focus (accessed on 9 April 2017).
- Thier, D. Firm: ‘Pokémon GO’ Has Made $1 Billion Since Launch. Available online: https://www.forbes.com/sites/davidthier/2017/01/31/firm-pokemon-go-has-made-1-billion-since-launch/#433f79ba20e3 (accessed on 9 April 2017).
- Weinberger, M. The Fad May Be Over, but Pokémon GO Still Has 65 Million Monthly Active Players. Available online: http://www.businessinsider.com/pokemon-go-65-million-monthly-active-players-2017-4 (accessed on 9 April 2017).
- Althoff, T.; White, R.W.; Horvitz, E. Influence of Pokémon GO on physical activity: Study and Implications. J. Med. Internet Res. 2016, 18. [Google Scholar] [CrossRef] [PubMed]
- Smith, D. Hundreds of People Mobbed Central Park to Catch a Vaporeon in Pokémon GO. Available online: http://www.businessinsider.com/pokemon-go-mob-runs-after-vaporeon-video-2016-7 (accessed on 9 April 2017).
- Gilbert, B. This 40-Second Video Will Convince You That Pokémon GO Is an Insane Phenomenon. Available online: http://www.businessinsider.com/pokemon-go-mob-runs-after-squirtle-video-2016-7 (accessed on 9 April 2017).
- Bowerman, M. Woman Discovers Body While Playing ‘Pokémon Go’. Available online: https://www.usatoday.com/story/tech/nation-now/2016/07/11/woman-playing-pokemon-go-discovers-dead-body-river-playing-game/86939056/ (accessed on 9 April 2017).
- Daye, A. Pokémon Go Helps Marines to Catch Suspect. Available online: http://www.cnn.com/2016/07/13/us/pokmon-go-helps-marines-to-catch-suspect/ (accessed on 9 April 2017).
- Miller, R. Teens Used Pokémon Go App to Lure Robbery Victims, Police Say. Available online: https://www.usatoday.com/story/tech/2016/07/10/four-suspects-arrested-string-pokemon-go-related-armed-robberies/86922474/ (accessed on 9 April 2017).
- Military Base Issues ‘Pokémon GO’ Warning. Available online: http://www.foxnews.com/tech/2016/07/19/military-base-issues-pokemon-go-warning.html (accessed on 9 April 2017).
- Roberts, A. ‘Pokémon Go’ Is a Major Distraction for Drivers According to a New Study. Available online: http://uproxx.com/gaming/pokemon-go-too-distracting-new-study/ (accessed on 9 April 2017).
- Lahman, S. Pokémon Go Player Crashes His Car into a Tree. Available online: https://www.usatoday.com/story/news/nation/2016/07/14/pokmon-go-player-crashes-his-car-into-tree/87074762/ (accessed on 9 April 2017).
- Birch, N. This Distracted ‘Pokémon Go’ Player Crashed into a Police Car on Camera. Available online: http://uproxx.com/gammasquad/pokemon-go-police-car/ (accessed on 9 April 2017).
- Pokémon Go Player Crashes Car into School While Playing Game. Available online: https://www.theguardian.com/australia-news/2016/jul/29/pokemon-go-player-crashes-car-into-school-while-playing-game (accessed on 9 April 2017).
- Inada, M. ‘Pokémon Go’—Related Car Crash Kills Woman in Japan. Available online: https://www.wsj.com/articles/woman-killed-in-pokemon-go-related-car-crash-in-japan-1472107854 (accessed on 9 April 2017).
- Maus, S.; Hofken, H.; Schuba, M. Forensic analysis of geodata in Android smartphones. In Proceedings of the International Conference on Cybercrime, Security and Digital Forensics, Glasgow, UK, 27–28 June 2011. [Google Scholar]
- Hilbert, D. On the continuous representation of a line on a surface part. Math. Ann. 1891, 38, 459–460. [Google Scholar] [CrossRef]
- Call Me Ash Ketchum: Open Source Forensics with Pokemon Go. Available online: https://www.security-sleuth.com/sleuth-blog/2016/8/13/call-me-ash-ketchum-open-source-forensics-with-pokemon-go (accessed on 9 April 2017).
- Head, N. Pokémon Go: An Introductory Forensic Study. Available online: https://www.intaforensics.com/2016/08/05/pokemon-go-an-introductory-forensic-study/ (accessed on 9 April 2017).
- Lawson, V. A Forensic Examination of Pokémon Go. Master’s Thesis, Utica College, New York, NY, USA, 2016. [Google Scholar]
- Murphy, C. A Sneak Peek at Pokemon Go Application Forensics. Available online: https://digital-forensics.sans.org/blog/2016/08/09/a-sneak-peek-at-pokemon-go-application-forensics (accessed on 9 April 2017).
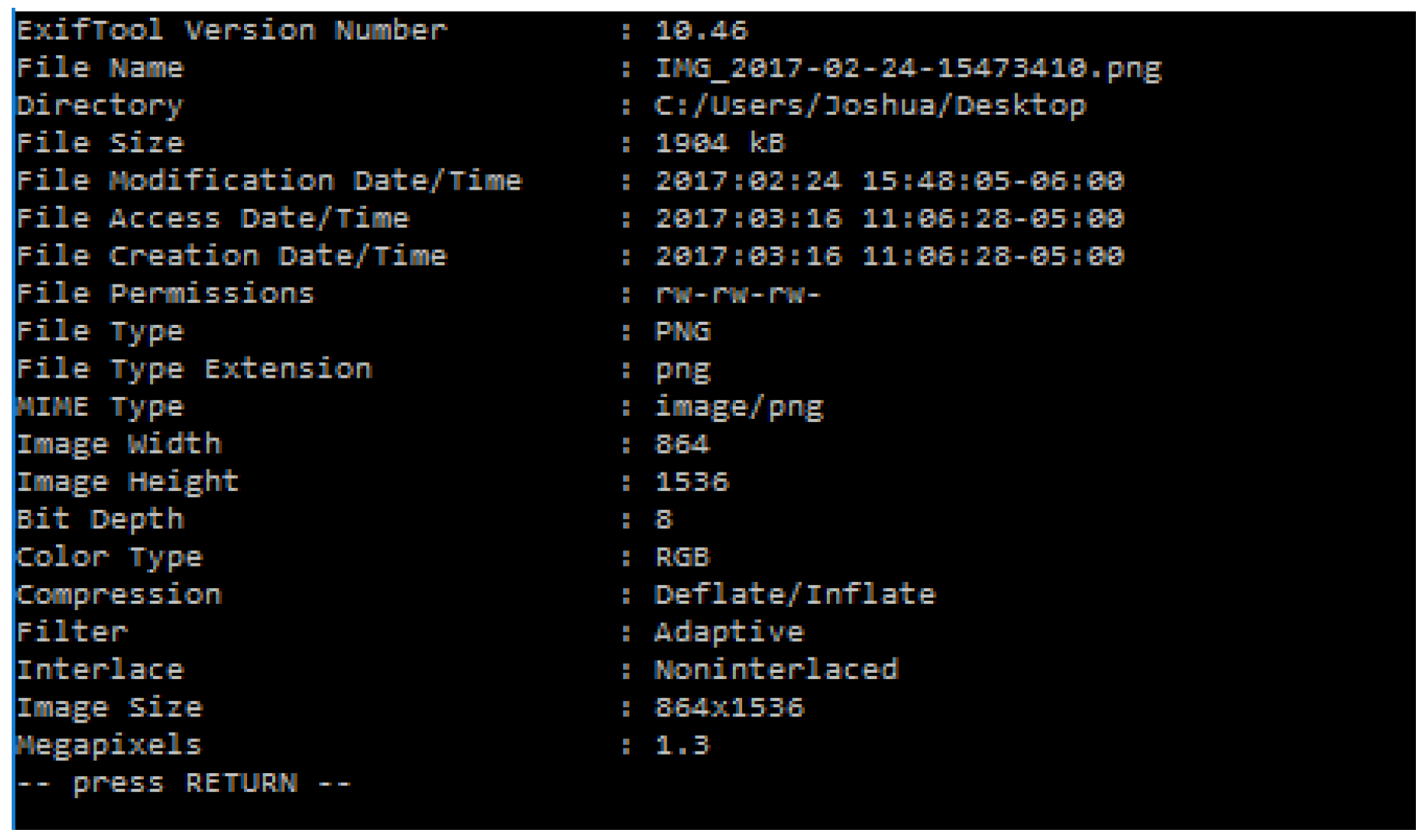
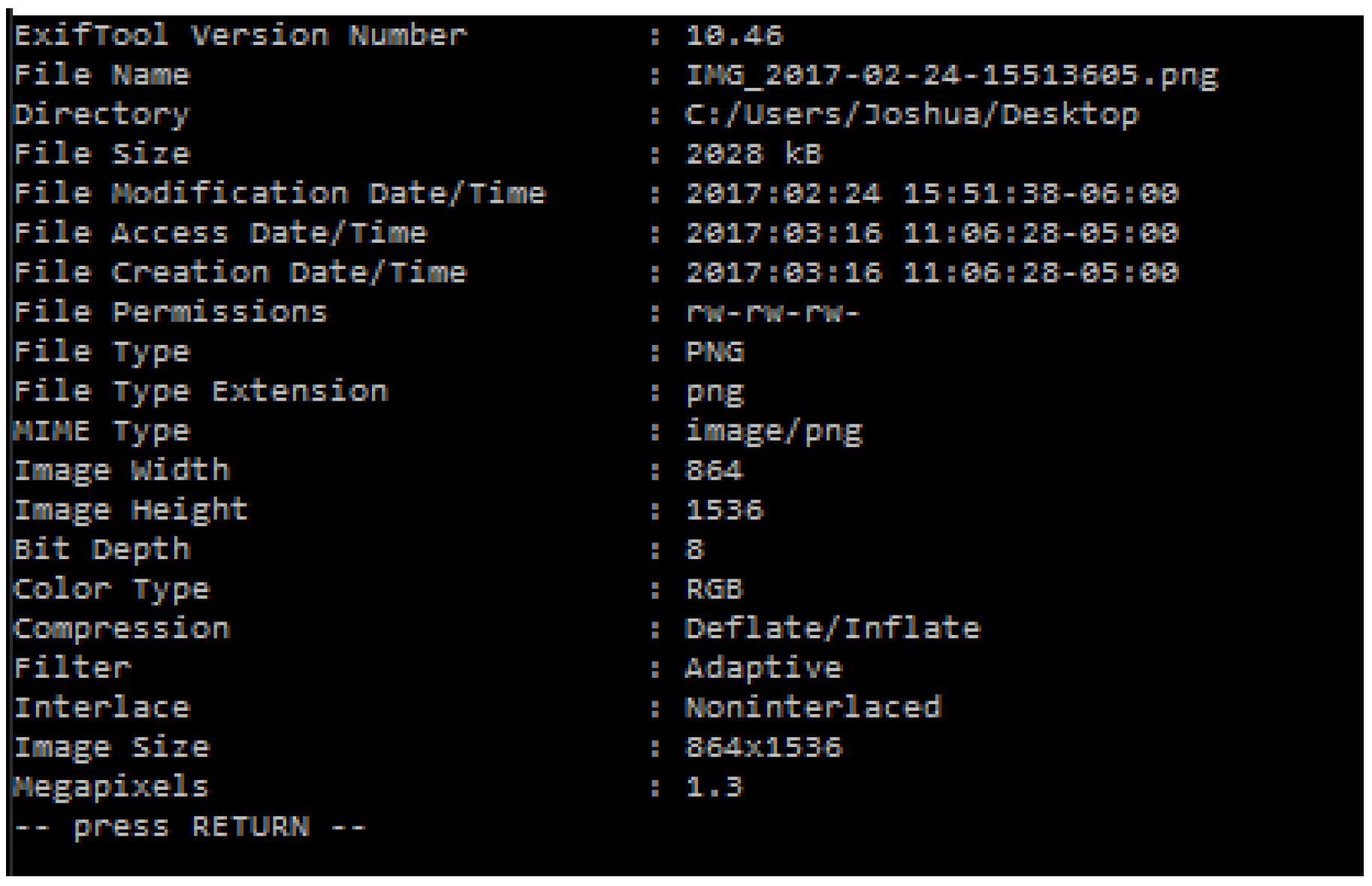
| Item | Description |
|---|---|
| Session Number | Number of the current session. |
| Current Session Duration | Duration of the current session in seconds. |
| Session Start Timestamp | Date and time that the current session started represented as a UNIX timestamp. |
| Last Known Session Timestamp | Date and time that the current session ended represented as a UNIX timestamp. |
| Sequence ID | A continually incrementing number that appears to be proportional to the players activity. |
| Install Time Stamp | Date and time at which the application was installed represented as a UNIX timestamp. |
| SID | Security Identifier. This value never changes. |
| Player XP | Player’s experience level at the end of the current session. |
| Item Count | Number of items the user has in their possession at the START of the current session. |
| Pokémon Count | Number of pokémon a user has in their possession at the START of the current session. |
| Player Level | Level of the player at the end of the current session. |
| Past Session Time | Total active game play since the game was installed in seconds. |
| Upsight.model.location (upsight.db) | GPS coordinates of the last location of game play. Stored within a SQLite database. |
| lastPushTokenRegistrationToken | Value within com.upsight.Android.googleadvertisingid.internal. registration.xml that may indicate user activity around a certain point in time. |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sablatura, J.; Karabiyik, U. Pokémon GO Forensics: An Android Application Analysis. Information 2017, 8, 71. https://doi.org/10.3390/info8030071
Sablatura J, Karabiyik U. Pokémon GO Forensics: An Android Application Analysis. Information. 2017; 8(3):71. https://doi.org/10.3390/info8030071
Chicago/Turabian StyleSablatura, Joshua, and Umit Karabiyik. 2017. "Pokémon GO Forensics: An Android Application Analysis" Information 8, no. 3: 71. https://doi.org/10.3390/info8030071
APA StyleSablatura, J., & Karabiyik, U. (2017). Pokémon GO Forensics: An Android Application Analysis. Information, 8(3), 71. https://doi.org/10.3390/info8030071






