1. Introduction
Smartphone and other mobile device usage has increased greatly in the past years: data from Eurostat shows that over the past five years, the number of individuals in the EU aged 16 to 74 that are using a mobile phone to access the internet has increased from
in 2011 to
in 2016 [
1]. Similarly, in emerging economies such as Malaysia, Chile, Brazil and Turkey, smartphone ownership rates have increased by more than
in two years (with an increase of
in Turkey) [
2]. Together with mobile devices, Wi-Fi networks have become more prevalent, often being offered by either commercial or public entities as a service to their customers. Connecting to the internet using one of these Wi-Fi networks entails some form of trust: the connections themselves—and, in case these connections happen unencrypted, their data—can be monitored by the provider of the network. Moreover, the provided networks often lack any form of security, with previous studies showing that
of 1404 encountered smartphones were set up to automatically make a connection to at least one insecure network [
3]. This allows not only the network provider, but also others within range of the network to eavesdrop on communications. Having access to this information can allow for third parties to generate a highly accurate profile of mobile device users, which entails inherent privacy risks [
4].
The problem of security is worsened by the fact that not all apps are using secure methods of connecting to the internet. Indeed, if apps fail to implement proper end-to-end encryption, eavesdroppers are able to see the data sent by these apps on an insecure Wi-Fi network. In 2012, Georgiev et al. showed that even when apps are using secure (SSL) connections, they often fail to validate certificates correctly, opening the door to active man-in-the-middle attacks [
5]. This means that providers of Wi-Fi networks would be able to intercept data, even if encryption is used. The researchers uncovered faulty certificate checking in libraries for cloud computing (e.g., EC2), web services (e.g., Apache Axis), merchant sof tware development kits (e.g., PayPal), and ad libraries (e.g., AdMob).
Data from Eurostat further shows that
of internet users had been limited or kept from performing an internet activity (e.g., buying goods or providing personal information to online communities) due to security concerns during the 12 months prior to a 2015 survey. However, only
of these users had limited their internet use because of security concerns when accessing the internet on a mobile device via a wireless connection from places other than home [
1].
In the past, researchers have studied the amount of privacy and security awareness of Wi-Fi users, with one of the more notable studies being performed by Klasnja et al. in 2009 [
6], where laptop users were surveyed about their network usage and corresponding privacy concerns. These studies show that user expectations of privacy often do not correspond to the reality, and that a person’s stance towards privacy often does not correspond to their actual behavior [
7].
Our study expands on this earlier work but updates the methodology to deal with the changing technology landscape. On one hand, it aims to assess whether mobile device users are aware of the network connections that are being made over Wi-Fi by installed applications (possibly in the background). On the other hand, it tries to find out how comfortable these users are with the fact that this application data is sent over the Wi-Fi network they are connected to, allowing it to be monitored by either the network operator, an eavesdropper (in the case of unsecured networks and connections), or both. We only consider the use of Wi-Fi networks to access the internet by mobile device users, and not the Wi-Fi connections that are used by network providers to access their backbones.
With this, we aim to assess whether the changed security and technology landscape has led to a change in security perceptions and practices between 2009 and 2017. We aim to get an idea of whether the principles of visibility (“The interface should allow the user to easily review any active actors and authority relationships that would affect security-relevant decisions”) and trusted path (“The interface must provide an unspoofable and faithful communication channel between the user and any entity trusted to manipulate authorities on the user’s behalf”), as defined by Yee [
8], are satisfied for current mobile device users.
2. Related Work
This study is mainly influenced by work from Klasnja et al. [
6], in which participants’ network usage is monitored. Part of the study consisted of showing participants a list of web sites to which specific bits of personal information were sent unencrypted, asking the participants about their awareness on the transmitted information, and how they felt about it. Klasnja et al. observed that four out of the eleven participants were aware that other people could possibly access their information being transmitted over Wi-Fi, but that this understanding did not raise concerns. Our study works in a similar way to this work but updates its methodology to deal with the changing technology landscape where mobile devices are rapidly surpassing notebooks in usage [
9]. The revised methodology uses smartphones and tablets as the main devices, and envisions to gather more quantitative rather than qualitative data with a participant pool of
. Our approach also considers only the connection metadata (such as the originating app and the connection endpoint), rather than the actual transmitted data.
After the study by Klasnja et al., Consolvo et al. introduced the “Wi-Fi Privacy Ticker” [
10]. This tool informs users about sensitive data being sent out over their wireless interface, while indicating whether the connection is secure. The results of their study show that the ticker helped participants to increase their awareness, and that it helped participants form more accurate mental models of the circumstances in which data gets transmitted, eventually contributing to changes in user behavior while on Wi-Fi. In our work, we try to (i) assess the level of awareness (without actively raising awareness) and (ii) determine if this awareness has a positive impact on security habits.
A study from 2010 by Swanson et al. [
11] reported on the perception of privacy and security when using wireless networks for a group of 11 randomly selected persons. They show that users make security choices based on (often mistaken) analogies to the physical world, similar to what happens in naïve, or “folk” physics, and that this leads to users who are confident in their knowledge about security while making unsafe decisions. They call this phenomenon “naïve risk mitigation”, providing examples of participants trusting a connection because they trust the company they are interacting with, or participants believing a malicious actor would not have the time to sort through all the data that could be gathered. Their survey also included an educative component, as it explained the associated risks of such actions to the participants. This study shows the need for concrete examples of network scenarios when surveying device users about security of their data. We apply this in our own work by having the survey questions represent concrete scenarios of applications sending data over wireless networks, with both the applications and the networks corresponding to those used by the participants.
Even when people think of themselves as privacy conscious, their actual behavior often does not match their intentions. Norberg et al. describe “The Privacy Paradox” as the relationship between individuals’ intentions to disclose personal information and their actual personal information disclosure behavior [
7]. They find that individuals will actually disclose a significantly larger amount of personal information than their stated intentions indicate.
Like privacy stance, there does not seem to be a direct relationship between a person’s technical background and the actions they take to control their privacy or increase their online security. In a 2015 study, Kang et al. use diagramming to determine users’ mental models about the internet, and conclude that individuals’ technical backgrounds do not influence their privacy or security behavior [
12]. Our study tries to assess whether these findings also apply to users of Wi-Fi networks, by looking for correlations between technical level and privacy intentions of the participants, and the security of networks to which they connect.
In 2012, Chin et al. analyzed the confidence smartphone users had in smartphone security and privacy [
13]. The study finds that participants are less likely to perform certain privacy sensitive activities on their smartphones than on their laptops, finding, e.g., a difference of 7% vs. 60% of participants not willing to entering their social security number. With the study being performed in 2012, participants cited reasons such as “new phone technology” for not trusting their mobile devices with privacy sensitive information. However, some participants also noted not trusting the Wi-Fi network, or mentioned “potential hackers hanging out in cafes”. These results seem inconsistent with a Eurostat survey from 2015, where only
of participants had limited their internet use because of security concerns when using the internet with a mobile device via a wireless connection from places other than home (compared to
in total) [
1]. This could indicate that the technology landscape has changed considerably since 2012, with smartphones becoming a more integral part of people’s lives.
A more recent study from Clark et al. shows that users of internet services are often unaware about which of their data is transmitted to the cloud and stored there, using GMail’s attachment storage as an example [
14]. They show that task-oriented users rarely stop to think about the security implications of their actions. Their results suggest that the same might apply to wireless network users, quickly connecting to a free Wi-Fi hotspot in order to perform a task at hand (e.g., to get to a website containing information needed at that moment).
With these studies indicating a possible discrepancy between users’ privacy attitudes and behaviors between five years ago and now, our goal is to assess to what extent the shift from personal computers and laptops to smartphones has impacted these privacy properties. Moreover, we want to find out whether the Privacy Paradox also applies to mobile device users in 2017. Our main contribution can hence be summarized as the answer to the question: with a security landscape that changed significantly since 2009, did privacy perceptions and practices change with it?
5. Results
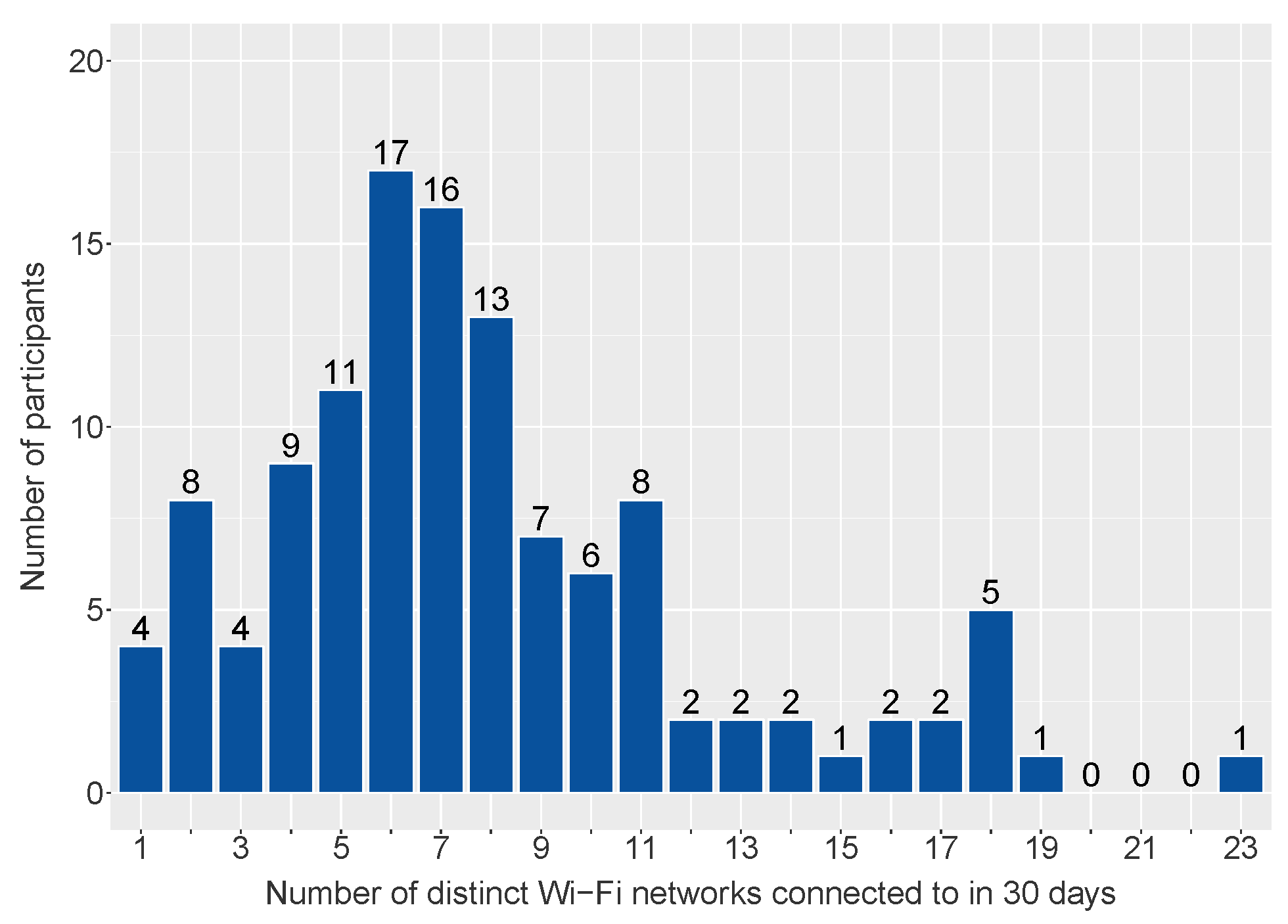
During the 30-day connection monitoring study, users connected to an average of 8.02 Wi-Fi networks, with the vast majority of users (61%) connecting to anywhere between 4–8 networks (see
Figure 1). This shows a larger than 100% increase compared to the study performed on notebooks instead of smartphones by Klasnja et al. in 2009, where the average user connected to four networks during a period of four weeks. In addition, 310 of the 866 networks that devices connected to (35.8%) did not have any security (in the form of WEP, WPA, WPA2 or WPA2-enterprise) enabled. All of the participants connected to at least one secured network, which shows an improvement in security compared to Klasnja’s study in 2009, where four out of 11 participants only connected to unsecured networks. Even so, as mentioned in
Section 3.1, a network having security enabled does not necessarily mean the network is secure. Indeed, WEP and WPA have been proven to have major security weaknesses. A Pearson correlation test did not show any statistically significant correlation between the expertise of the participants and the number of unsecured networks they connected to during the experiment. Furthermore, our results show there is no statistically significant correlation between participants’ privacy stances (measured by the number of positive answers to the questions defined in [
19]) and the number of unsecured networks they connected to during the experiment. A general overview of the collected data is available in
Table 2.
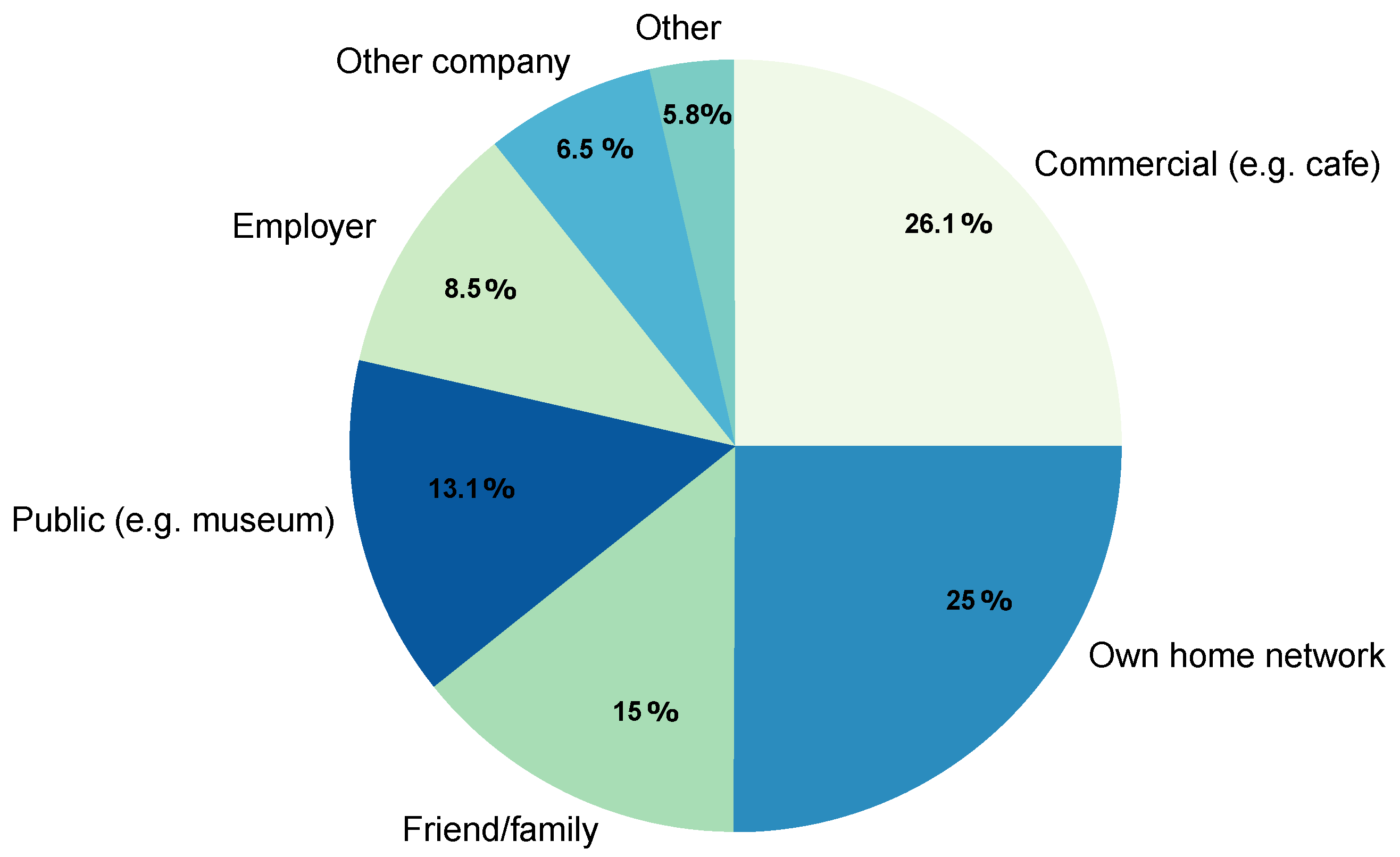
After accounting for the fact that the number of ISP hotspots was artificially limited in the questionnaire (by removing these 51 networks from the list of 311 networks participants were surveyed for), the two most prevalent types of networks that were part of the questionnaire were commercially offered Wi-Fi networks (belonging to e.g., a cafe or a supermarket) and own home routers, together accounting for just over
of all encountered networks (see
Figure 2).
Participants indicated on multiple occasions that they were unsure about the identity of networks they connected to, indicating this either as part of the general survey feedback (“My responses on [network X] are not reliable, as I don’t know this network”) or at the moment they are connecting to the network (by giving a one-line summary along the lines of “No idea”, “Unknown network” or “Don’t know this”).
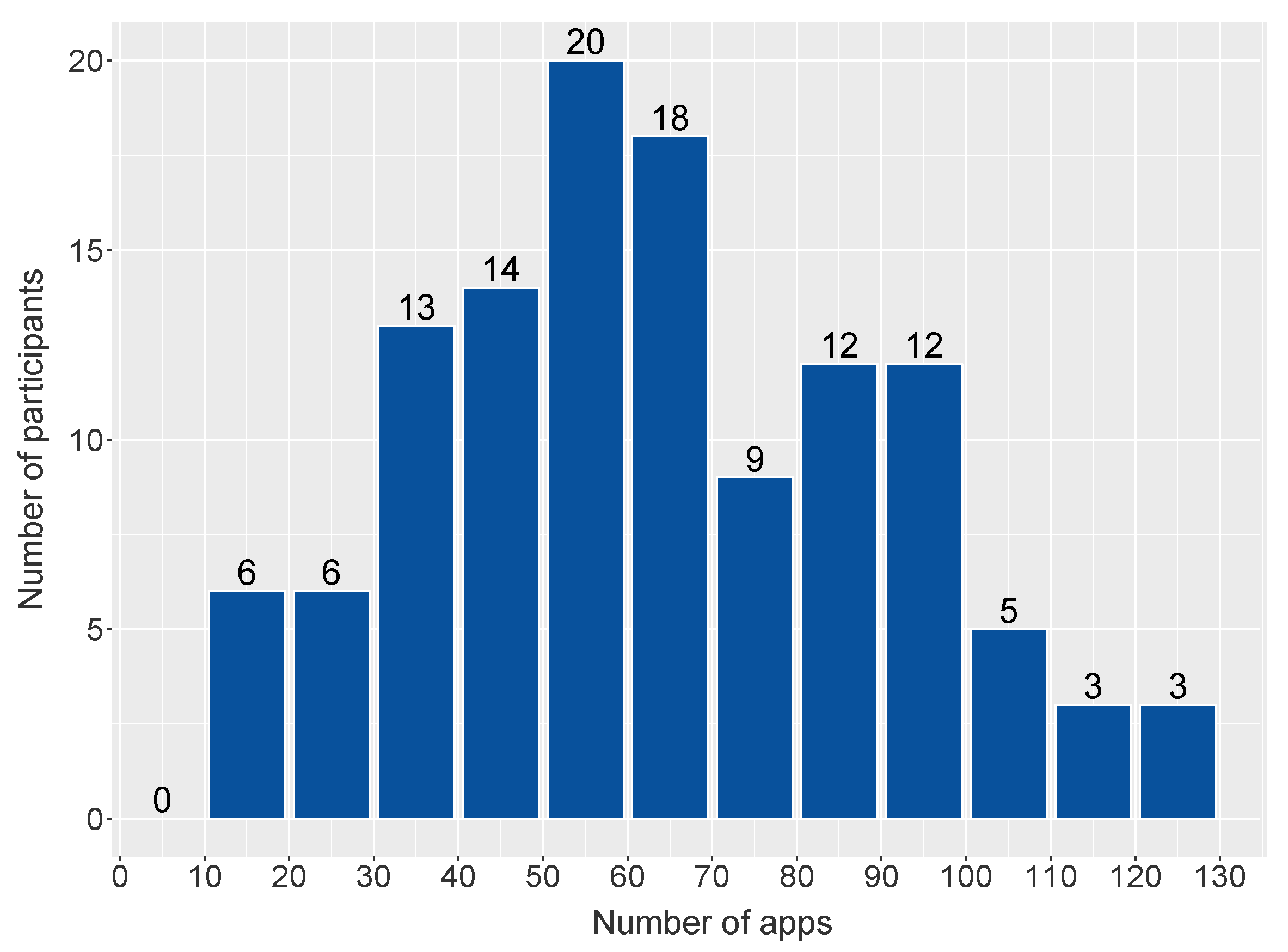
The participants’ devices had an average of 65.44 apps making a connection to an external server during the experiment, with most devices (
) having between 30 and 70 apps connecting over this period (see
Figure 3).
Participants were often surprised about connections being made by apps, indicating that they were unaware about 345 of 928 (
) connections that were surfaced as part of the exit survey. Excluding messaging apps (where participants indicated awareness for
of the connections being made), this number grows to 264 out of 629 apps (or
). This also showed in the general feedback given at the end of the study, where two participants talked about a mismatch in privacy expectations and actual behavior. One participant explicitly noted
“It surprises me that Skype transmitted data, as I did not configure the app yet”, while another user’s privacy expectations did not align with what the app was actually doing, as indicated by their feedback
“When surfing anonymously, the ‘incognito’ mode of Google Chrome that I use regularly was seemingly not taken into account”. Another participant explicitly indicated that the survey caused them to take action, providing as feedback:
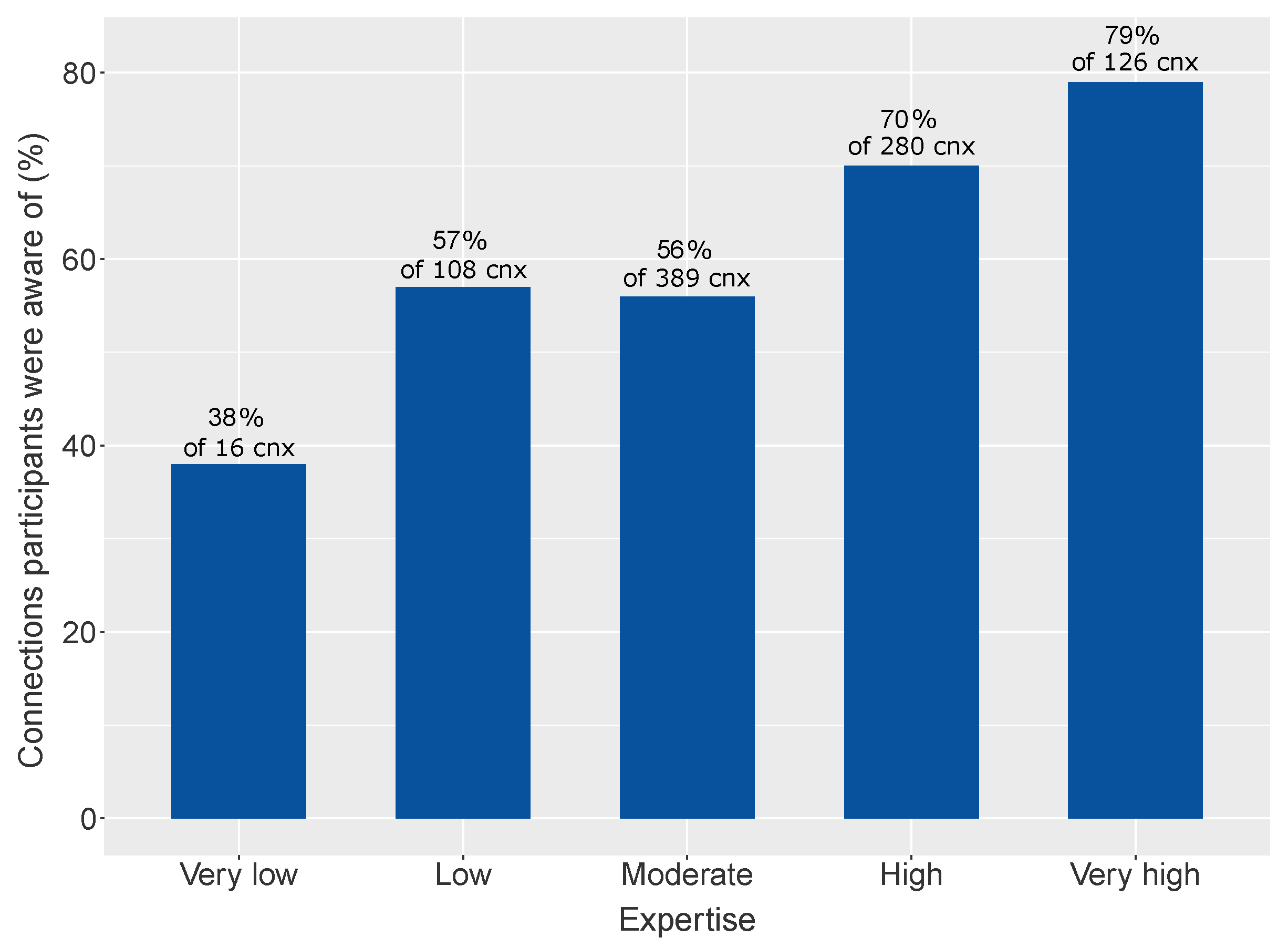
“Interesting survey. I’ll certainly remove FileExpert from my device now.”. In this regard, we found a medium correlation between the declared expertise of participants and how aware they were about the connections being made (Pearson’s
).
Figure 4 shows the distribution of the awareness count depending on the expertise of the participants.
Of the 321 insecure connection pairs (
pairs containing both an insecure Wi-Fi network and an unencrypted connection made by the app), participants responded for 292 cases (
) that they would not want a person in the neighborhood of the Wi-Fi network being able to see the data sent over the connection, stating they either
disagree or
strongly disagree with the statement “A random person in the neighborhood of <network name> (e.g., someone standing on the street close to the building) is permitted to see all information (see previous question) of app <appname>”. This could indicate that participants were not aware about the security risks inherent to connecting to open networks, or that they were unaware about the app making an insecure connection (remember that connections made to advertisement networks were not used for any survey questions, as explained in
Section 3.1) on this network.
Even when asked about the extent to which the network owner would be permitted to see data transmitted by the apps that actually transmitted data over the network, 655 out of 928 connection pairs (71%) were deemed by participants to contain data that would be too sensitive for the network owner, indicated by answering that they “disagree” or “strongly disagree” to the statement “The owner of <network name> is permitted to see all information (see previous question) of app <appname>”. This number even increases to 88% if we only consider the 191 hotspot networks provided by ISPs, which we hypothesize could be the case because participants may be considering these hotspots as belonging to an unknown person’s home network. The data analysis showed a small correlation between the expertise of participants in computer networks and their concern about the network owner seeing the transmitted data (Person’s , ).
We also analyzed the effect of the type of data (username, password and data such as instant messages, emails or weather information) on the privacy concern level of participants in our study. To measure participant’s privacy concern, we use a 5-point Likert scale for the security concern rating, where 1 corresponds to “Not at all concerned”, and 5 corresponds to “Extremely concerned”. The Shapiro–Wilk and Barlett’s tests show that the data violates the normality and homogeneity of variance requirements to perform an ANOVA test. Thus, in this case, we use the Friedman non-parametric test for the comparison among the groups (considering that one participant contributes to the sample with multiple records, we use a within subjects design). The Friedman test reveals a significant effect of the type of data on the privacy concern of the participants when using a mobile app (, ). A post hoc test using Mann–Whitney tests with Bonferroni correction shows significant differences between privacy concerns for the username and data, and username and password. Participants rated the privacy concern for the username the lowest (, ), followed by the password (, ), and gave the data the highest privacy concern rating (, ).
Given the wide variety of applications that made a connection from the smartphones of the participants, we performed the same analysis considering only applications in the
Communication category (i.e., messaging apps). As explained in
Section 3.2, we selected at least one application of this type (if one was available) when generating the survey questions. The results of the analysis follow the same trend as those observed for the full dataset: the Friedman test reveals a significant effect of the type of data on the privacy concern of the participants (
,
). A post hoc test using Mann–Whitney tests with Bonferroni correction again shows significant differences between privacy concerns for the username and data, and username and password, with similar differences (username:
,
, password:
,
, data:
,
).
6. Discussion
Our results show some interesting trends, both in terms of data gathered about participants’ mobile device Wi-Fi usage, as in terms of their privacy and security awareness and concerns. This section provides some general remarks and further insights derived from the results.
First, this research was purposefully limited to connections on Wi-Fi networks because of the many inherent risks involved: these networks are often operated by small businesses, and security can be lacking. However, as mobile data is getting cheaper, more smartphone users are using their cellular network to connect to the internet. This is also indicated by the study’s participants, with comments such as
“I’m connecting to (public) wifi predominantly when I’m abroad, as I have a good data-subscription domestically and I trust my mobile provider more than I trust public networks.” and
“This research was about public wifi. I still use this, but not as much as I used to when I had a tablet that only had wifi. Now that I have a data subscription I use [Wi-Fi networks] a lot less. The security of mobile data connections seems more relevant to me now”. Even so, our results show that mobile device users in 2017 are still relying on Wi-Fi for a significant amount of their internet access, with the majority connecting to 4–8 different Wi-Fi networks in 30 days. Adding to this is that a large part of Wi-Fi usage can be attributed to ISP hotspot networks, together accounting for over
of all connection pairs that were logged by the monitoring app (Because connections are only logged periodically, they provide only a representative subset of all connections made by the device. See
Section 3.1 for more information on why this is still relevant.).
It is important to note that over one third (35.80%) of Wi-Fi networks participants connected to were insecure, allowing eavesdroppers to monitor metadata about network connections and—when the connections themselves are unencrypted – their actual data. Moreover, it facilitates malicious actors into mounting so-called “Evil Twin” attacks, where an existing (unsecured) network in the victim’s preferred network list is spoofed by an attacker, causing the victim’s device to automatically connect to the malicious network [
20]. Combined with the fact that 12.92% of logged connections (excluding servers of advertisement agencies) were insecure, this presents a real security risk. When considering all networks (even those filtered out for the survey), the biggest offenders seem to be commercial entities (35.75% of open networks) and hotspots provided by the ISP of the home network (23.46% of open networks). This indicates that, even in 2017, Wi-Fi network security should still be considered an important topic in research and in the industry.
As is clear from
Section 4, the participant pool is skewed towards highly educated people with a high expertise in computer networks (even though this expertise is self-reported, it was cross-checked with their ability to explain network security; see
Section 4 for more information.). This leads to the expectation of participants being more aware about the apps operating on their devices than the general public, and to their expertise in computer networks having a positive impact on their security habits. Our analysis does indeed show that participants reporting a high expertise in computer networks are slightly more aware about connections being made, confirming expectations. Nonetheless, even participants reporting a “high” or “very high” expertise in computer networks were still unaware about
of connections made by apps on their device.
More surprising is that this expertise in computer networks does not seem to translate to better security practices: having this expertise did not prevent participants from connecting to as many unsecured Wi-Fi networks as less technically experienced participants. This confirms prior results from Friedman et al. [
21], who found that high-technology participants did not necessarily have better security habits than those with a less technological backgound. With the study by Friedman et al. dating from 2002 and using only personal computers as the users’ device for connecting to the internet, our results indicate that their conclusions are still valid 15 years later on mobile devices.
Similarly, the privacy stance of participants (measured by usage of privacy-enhancing tools used and actions taken in the past, depicted in
Figure 5) did not have any significant influence on the number of unsecured Wi-Fi networks they connected to. This indicates that, while users are prepared to install or use privacy-enhancing tools in a one time set-it-and-forget-it manner, they often lack the time or inclination to be continually aware about the security risks of using public Wi-Fi networks. This is in line with results from Dourish et al. [
22] and Klasnja et al. [
6] (studies from 2004 and 2009, respectively), where it is discussed that task-oriented users do not generally think about these issues when they are going about their work. Instead, they choose to delegate responsibility for security to tools, other individuals or institutions.
This mismatch in privacy stance and security behavior directly translates to participants’ perceptions about transmitted data: when confronted with specific scenarios about unencrypted connections that occurred on insecure networks (presented as a hypothetical scenario), of participants indicated being worried about the corresponding data being available to eavesdroppers. Furthermore, participants are most concerned about the privacy of actual app data, even more so than they are about the privacy about the app’s password. This result seems to confirm the Privacy Paradox, as participants are transmitting a significantly larger amount of data over insecure channels than they intend to.
It would be interesting to see whether the types of apps that are used in more insecure scenarios handle less privacy-sensitive data than those used in high-security scenarios. We did not explicitly label apps in our dataset as having access to “privacy-sensitive” data, as doing so would be inherently subjective, depending on for example the cultural background of the researchers. While the privacy sensitivity of the data itself was not the focus of this research, we consider it an interesting area for future work to use the permission accesses granted to apps as a proxy for the data they are able to access. This would allow for investigating possible correlations between the amount of sensitive data an app handles, and the security of the app’s connections.
Asking the participants about their privacy-sensitiveness to the different types of information that could be transmitted by an app beforehand pushed them to think about what this data could comprise before answering questions about network owners or eavesdroppers having access to this data. Together with the previous results, this demonstrates that using very specific, personalized scenarios (instead of more general ones) might prove to work better to inform mobile device users about security and privacy issues.