Secure Data Transmission Using GS3 in an Armed Surveillance System
Abstract
1. Introduction
2. Foundations
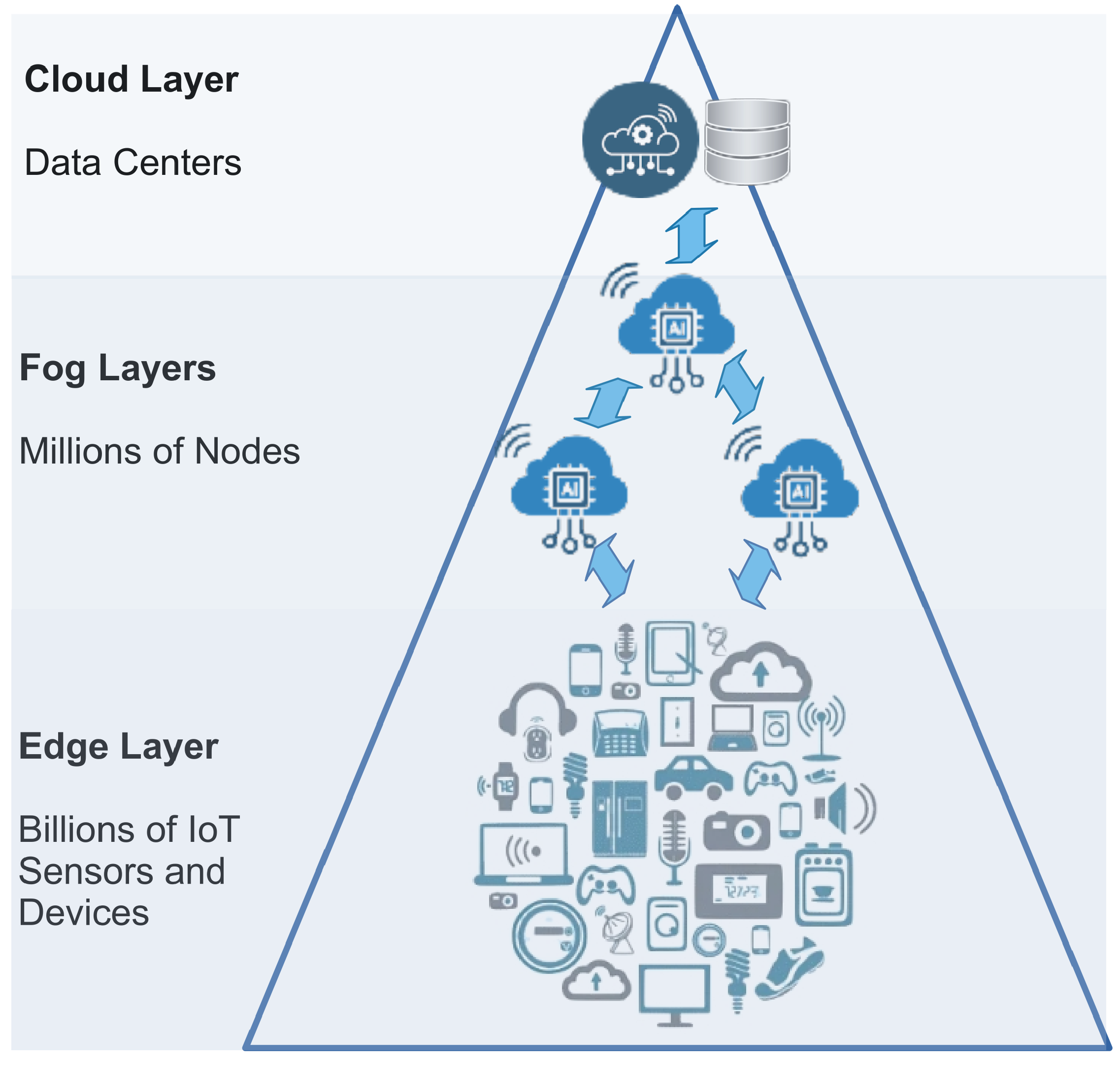
2.1. Computing Paradigms
- Edge layer: This layer is composed of billions of IoT devices, which capture and preprocess data. Moreover, it is possible to design ad hoc and dynamic wireless sensor networks (WSNs) [19]. A common characteristic in this layer is a restriction on computational resources.
- Fog layers: These intermediate layers, located between end devices and the cloud, help to resolve problems such as network latency or real-time analytics [20].
- Cloud computing: A paradigm based on powerful computing devices that provide security and enable the analysis and processing of vast IoT data. However, some applications require real-time processing and responses that this layer cannot provide.
2.2. Reviewed Lightweight Cipher Algorithms
2.2.1. Stream Cipher Algorithms
- Feedback Shift Register (FSR) Sequences: A linear FSR is a shift register whose input bit is a linear function of its previous state. The XOR function is commonly used. Linear FSRs are defined by primitive polynomials. Nonetheless, their linearity is a security weakness. Algorithms such as Trivium [22], A5/1 [23], or Geffe [24] aim for greater security strength by connecting several linear FSRs to achieve a non-LFSR.
- Cellular Automata: A cellular automaton (CA) is a grid of cells, each of which has a finite number of states and a neighbourhood to interact with. In each iteration, a cell calculates its new state, which depends on its state and its neighbors’ states. Class 3 (chaos) patterns, as defined by Wolfram [25], evolve through chaotic behaviour. Therefore, Class 3 is interesting from a cryptography point of view. A simple one-dimensional CA would be defined with for the surrounding (adjacent) cells, so there are possible patterns for a neighbourhood. Therefore, some of the possible rules show chaotic behaviour. Rule-30 is a case that is defined by (1). is the state of cell i at time t. Pentavium [26] is an improved CA with a 5-neighbourhood design to enhance the cryptographic properties of Trivium.
- Chaotic Systems (CS): CS are deterministic nonlinear systems that manifest complex behaviour. Moreover, tiny differences in the initial conditions provoke different behaviours. The motion of a magnetic pendulum is a simple system that exhibits chaotic behaviour. The logistic map (LM) is a one-dimensional chaotic system. The discrete mathematical model of the LM system is defined by (2). The chaotic behaviour appears when . Therefore, the initial conditions of the chaotic system must avoid values where the system exhibits periodic-like behaviour.Related research on chaotic systems has been published. Dridi et al. [27] propose an encryption/decryption procedure operating in cipher block chaining (CBC) mode. The system is produced by a pseudo-random key stream generated by a PRGN based on a chaotic system. Alshammari et al. [28] modified the well-known Advanced Encryption Standard (AES) with a new S-box generated by the Lorenz chaotic map [29]. Zhu et al. [30] propose a cipher schema based on a combined chaotic system between a logistic map and tent map to improve the statistical properties of the generated sequences.
- Numerical Pseudo-Random Number Generators: Stream ciphers are based on different techniques. The Rivest cipher (RC4) or ARC4 cipher [31] has two subproccesses called the key-scheduling algorithm (KSA) and pseudo-random generation algorithm (PRGA). It is a simple and fast cipher. Several improvements to RC4 have been published. The modified ARC4 (MARC) is one of them [32]. It enhances the security of RC4 by modifying its key-scheduling algorithm (KSA) and improves the performance by modifying the PGRA process. The Salsa20 [33] algorithm was proposed by Daniel J. Bernstein and presented in the eSTREAM project in 2005. It only uses Add–XOR–Rotate operations to generate 512-bit keystreams in each cycle, iterating 20 times the quarter round (QR). The Chacha20 [34] cipher improves upon Salsa20. Chacha20 modifies each word twice in each QR function, while Salsa20 modifies only once per QR.
2.2.2. Block Cipher Algorithms
- Substitution–Permutation Network (SPN): An SPN takes blocks of plaintext and keys and then executes rounds of substitution (S-boxes) and permutation layers to achieve a ciphertext. The Advanced Encryption Standard (AES) algorithm divides messages into 16-byte blocks with keys of 128, 192, or 256 bits in size. This cipher is an important encryption algorithm due to its high level of security and reduced execution time. Another cipher based on SPN is PRESENT. It was developed with devices with reduced computational resources [35] in mind.
- Feistel Network (FN): DES [36] is the reference cipher operating in FN balanced mode, with blocks with a 64-bit size and keys of 56 bits during 16 rounds. Its strength resides in a confusion step with 8 S-boxes. However, to break the key, only operations would be necessary. Simon [37] is also based on a balanced FN with n-bit words and a -bit block size. It can operate with different combinations of block sizes ([32–128] bits), key sizes ([64–256] bits), and rounds ([32–72]) to allow more flexibility, bearing in mind constrained devices, where simplicity in design is important.
- Add–Rotate–XOR (ARX) operations: Speck [37] is a software-orientated cipher and it is based on ARX operations. It can work with different combinations of block sizes ([32–128] bits), key sizes ([64–256] bits), and numbers of rounds ([32–72]).
2.3. Weapon Detection Systems
- A recent review [38] affirms that the Faster R-CNN [39] and You Only Look Once (YOLO) [40] models are architectures that are commonly used. The performance is improved if a dataset with real and synthetic images is used during the training phase. The lighting conditions in images, difficulties in identifying small weapons, lightweight models to use in real-time applications, and unsupervised learning are presented as challenges.
- Another study [41] achieves the objectives of detecting different types of weapons and determining whether the armed human pose is standard or dangerous with high accuracy. In the first phase, the models YOLOv8s, YOLOv8l, and YOLOv8x are implemented. Second, the weighted boxes fusion (WBF) method is used to combine the results obtained from the three YOLOv8 models and to improve the detection accuracy to 30%.
- EfficientDet [42], as an object detection model, is used in [16]. Moreover, the cloud computing paradigm is avoided due to issues such as network latency, data privacy, and slow decision making. Therefore, all processing is performed in the edge layer. A Raspberry Pi 3 is used as an edge device. Positive detections are sent to the server using the Message Queuing Telemetry Transport (MQTT) [43] protocol. This model achieves an inference time of 1.48 s per frame.
- With the objective of improving detection under low light conditions, one study proposes the YOLOv7-DarkVision model [15]. This research applies the techniques of gamma correction, contrast and brightness, Gaussian blur, and normalisation to dark frames. Then, the YOLOv7 model [44] is deployed for the inference phase.
- YOLOv8-AD (You Only Look Once v8—Attack Detection) [45] is a modified version of YOLOv8 [46] that aims to improve the detection of armed soldiers taking attack actions. YOLOV8-AD is based on a dynamic deformable attention mechanism, multi-branch modules with dynamic snake convolution and atrous convolution, a lightweight dynamic detection head with multi-dimensional attention, and a network based on the Inner Minimum Points Distance Intersection over Union (Inner-MPDIoU) loss function. Experiments were executed on powerful hardware (Nvidia Titan 12GB GPU, Intel Core i7 CPU). The results revealed high precision and strong detection capabilities.
- Another study [47] proposes using YOLOv4 as an object detection model through real-time surveillance cameras. To address the problems of occlusion, hidden handguns, and people close to each other, three heuristics and seven machine learning models are compared. The random forest classifier ML model achieves the best performance.
- The objectives of [48] were to reduce the number of false positives and maintain a low inference time. This was addressed by incorporating a secondary cascaded classifier and a temporal window approach. To enhance the detection of weapons with a small aspect ratio, a scale matching technique was executed. Moreover, a comparative analysis was performed on the YOLOv5, YOLOv7, and YOLOv8 versions for real-time weapon detection. The experiments were executed on a powerful Nvidia A100 with 40 GB of memory.
| Paper (Year) | Key Contributions | Limitations/Areas for Improvement |
|---|---|---|
| Systematic review on weapon detection in surveillance footage through deep learning (2024) [38] |
|
|
| Multi-Weapon Detection Using Ensemble Learning (2023) [41] |
|
|
| Weapons Detection System Based on Edge Computing and Computer Vision (2023) [16] |
|
|
| Robust Weapon Detection in Dark Environments Using YOLOv7-DarkVision (2024) [15] |
|
|
| A Fine-Grained Detection Network Model for Soldier Targets Adopting Attack Action (2024) [45] |
|
|
| Improving Armed People Detection on Video Surveillance Through Heuristics and Machine Learning Models (2024) [47] |
|
|
| Effective Strategies for Enhancing Real-Time Weapons Detection in Industry (2024) [48] |
|
|
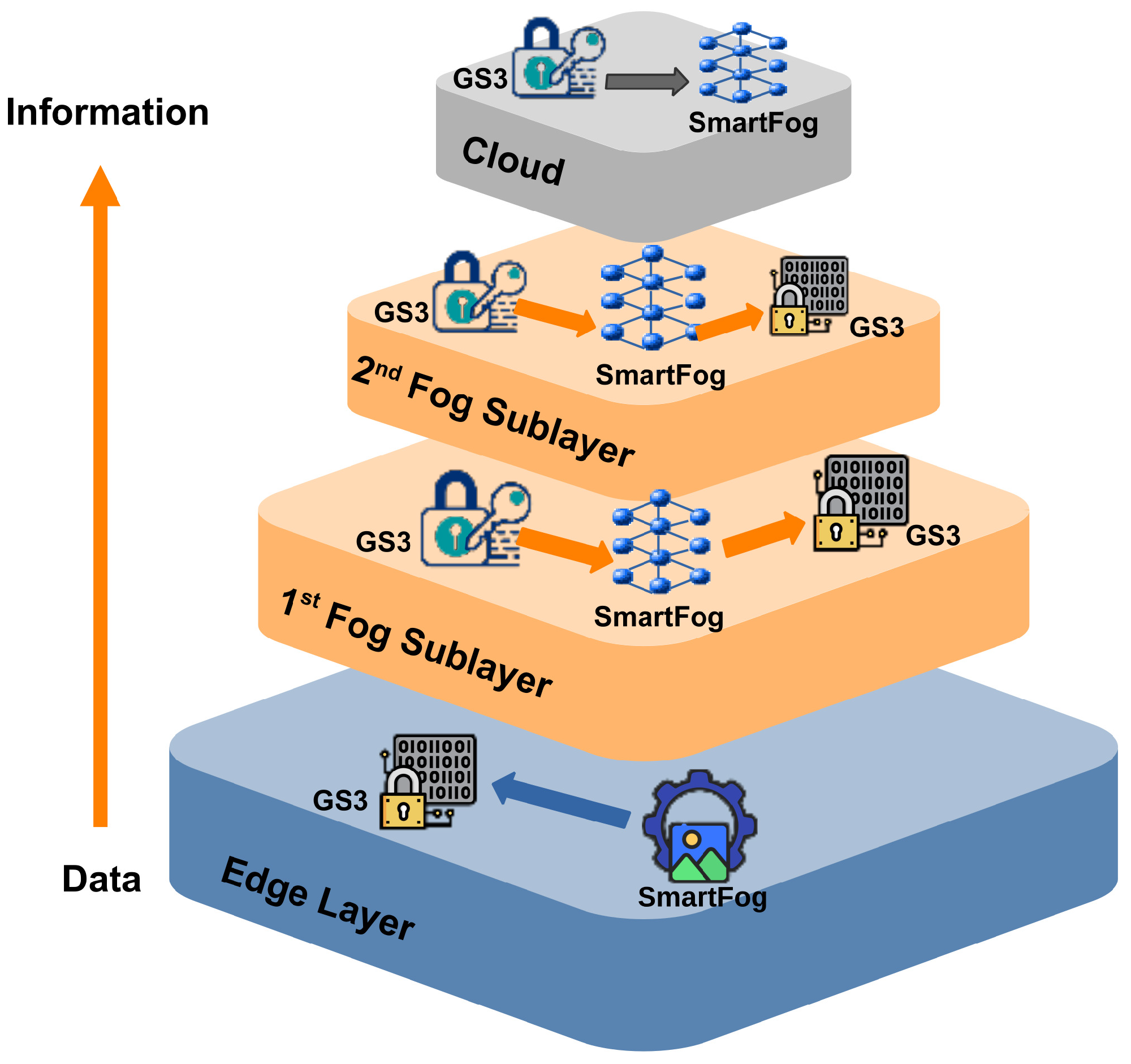
3. Methodology
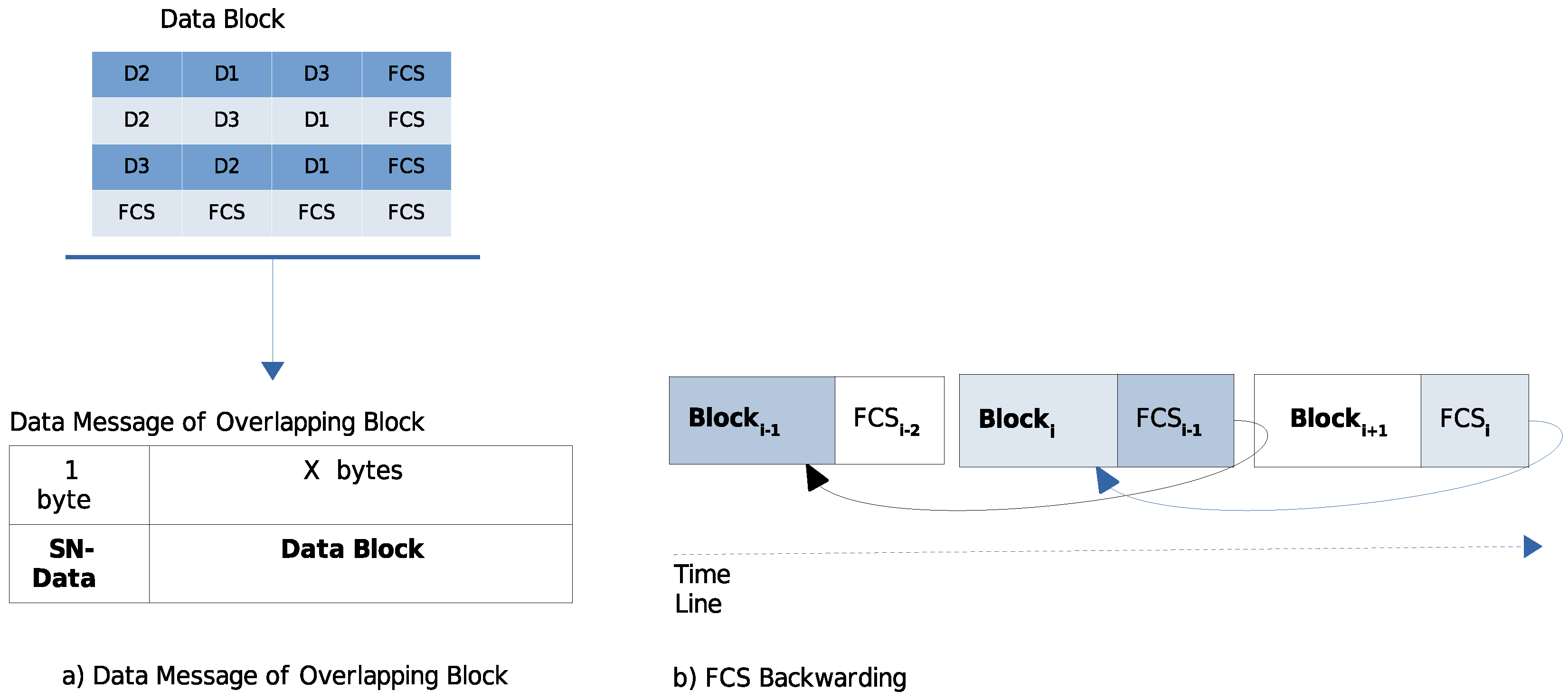
3.1. Data Block Structure
3.2. Functional Description
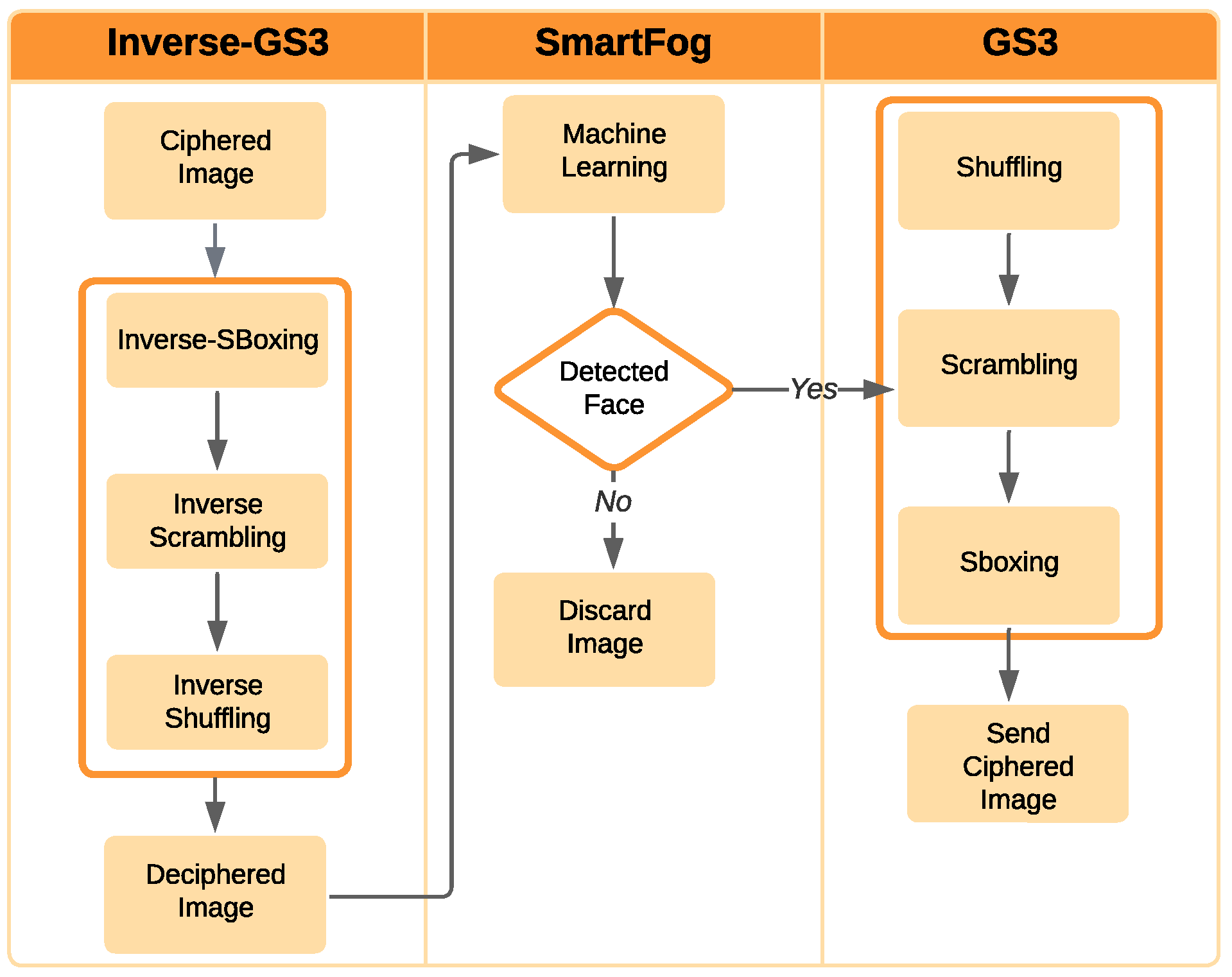
3.2.1. Edge Layer
- Capturing an image from a camera;
- Executing the background subtraction (BS) and foreground mask (FM) to decide if there are any changes in the current scene.

- Shuffle subprocess: Firstly, the CRC-16 value for each row and column is calculated. Secondly, a lightweight pseudo-random subprocess to swap the initial positions of the RGB channels of the pixel is applied. This task reaches Shannon’s property [51] of diffusion.
- Scramble subprocess: This lightweight method generates a pseudo-random 288-bit string to modify the initial pixel values with an XOR operation. Thus, Shannon’s cryptography principle of confusion [51] is accomplished.
3.2.2. First Fog Sublayer
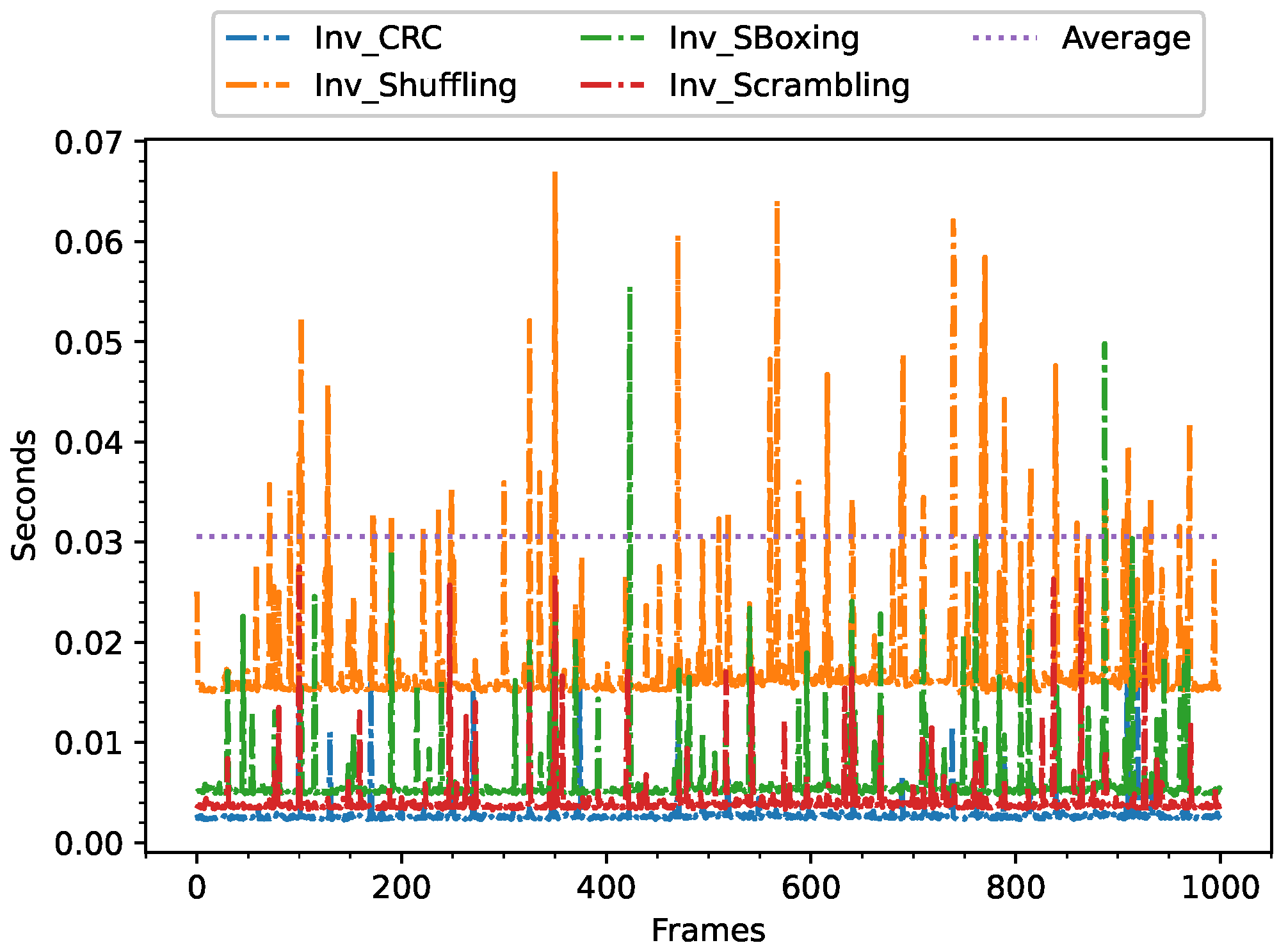
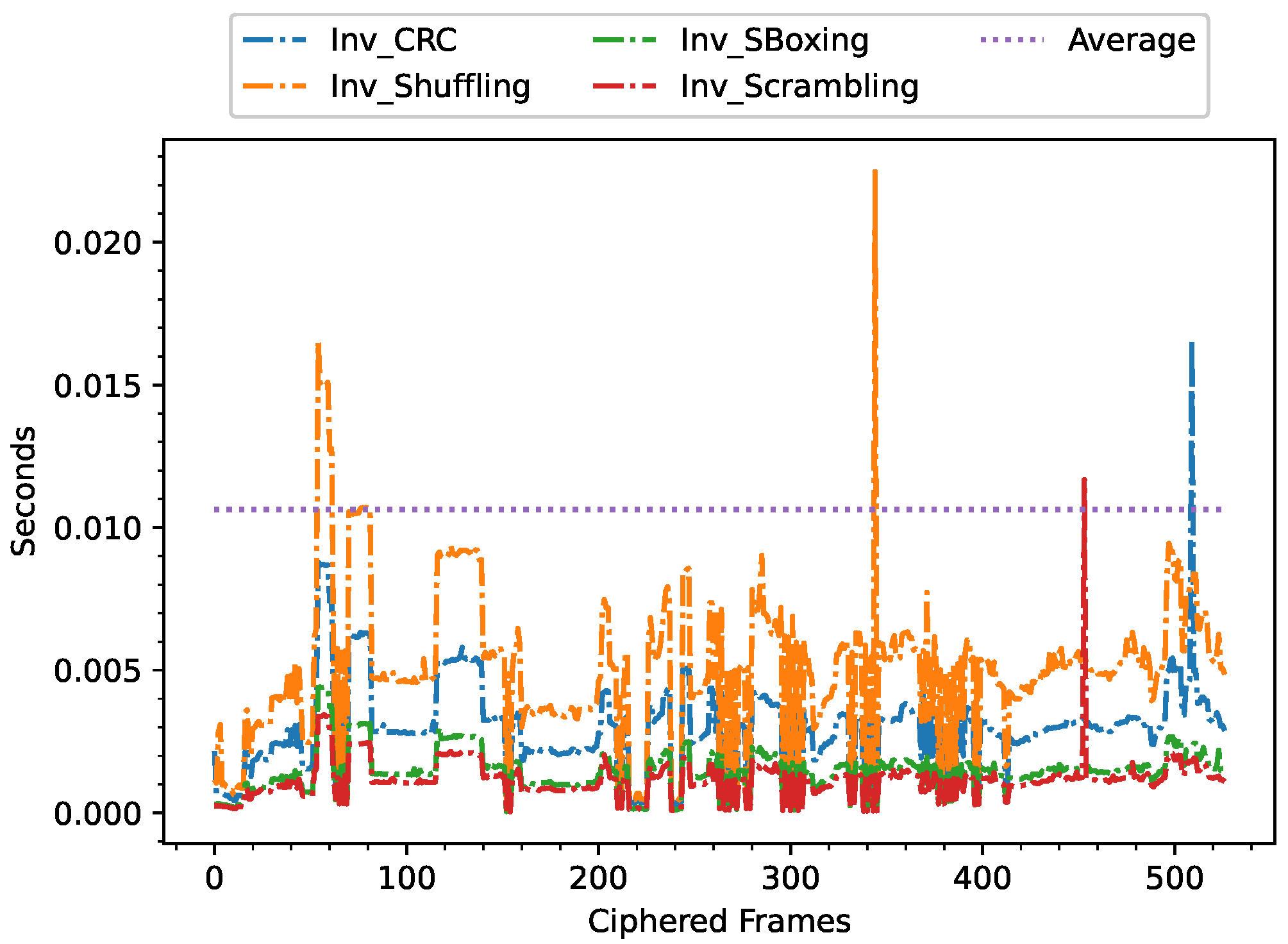
- Inverse S-boxing subprocess;
- Inverse Scrambling subprocess;
- Inverse Shuffling subprocess.
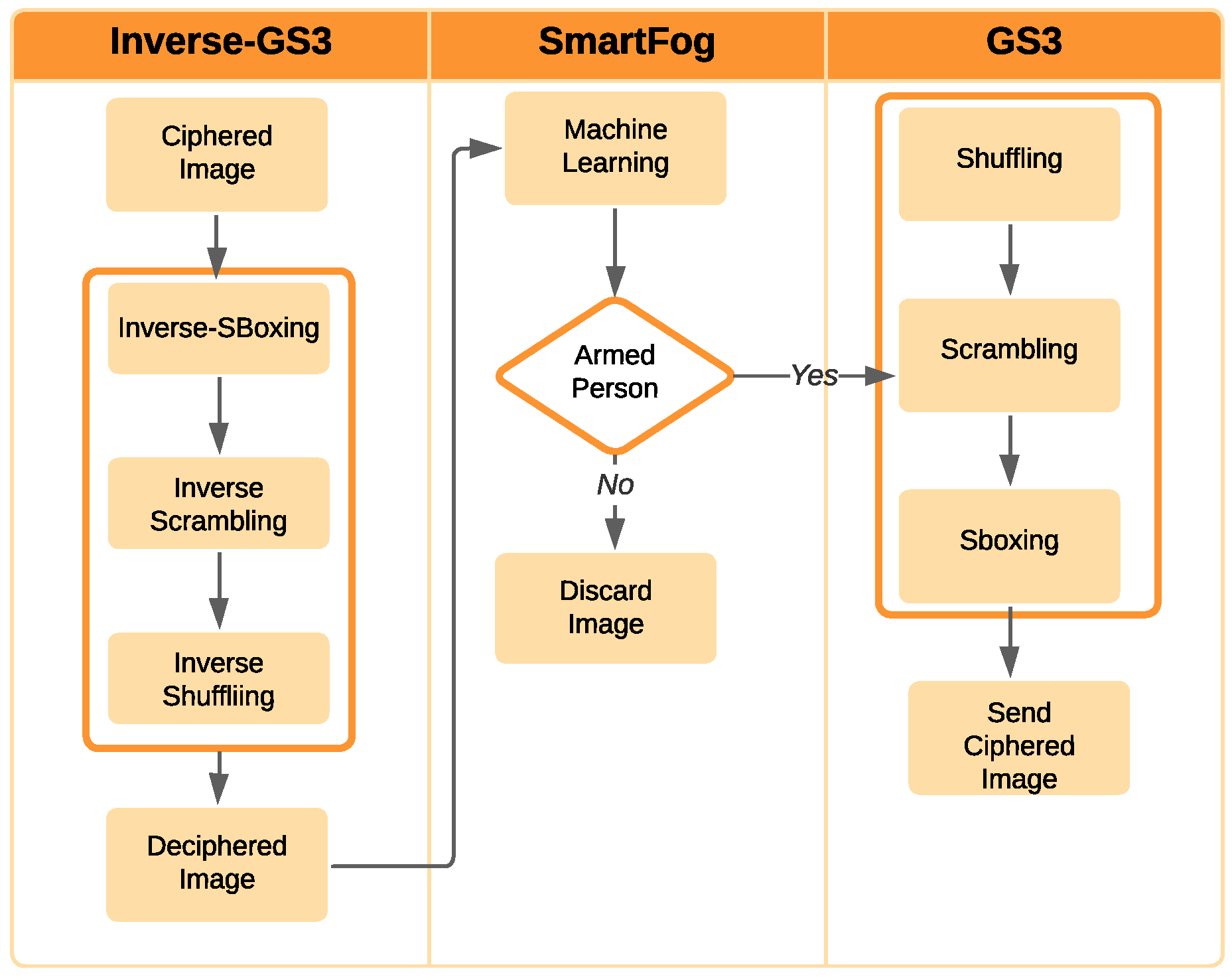
3.2.3. Second Fog Sublayer
3.2.4. Cloud Layer
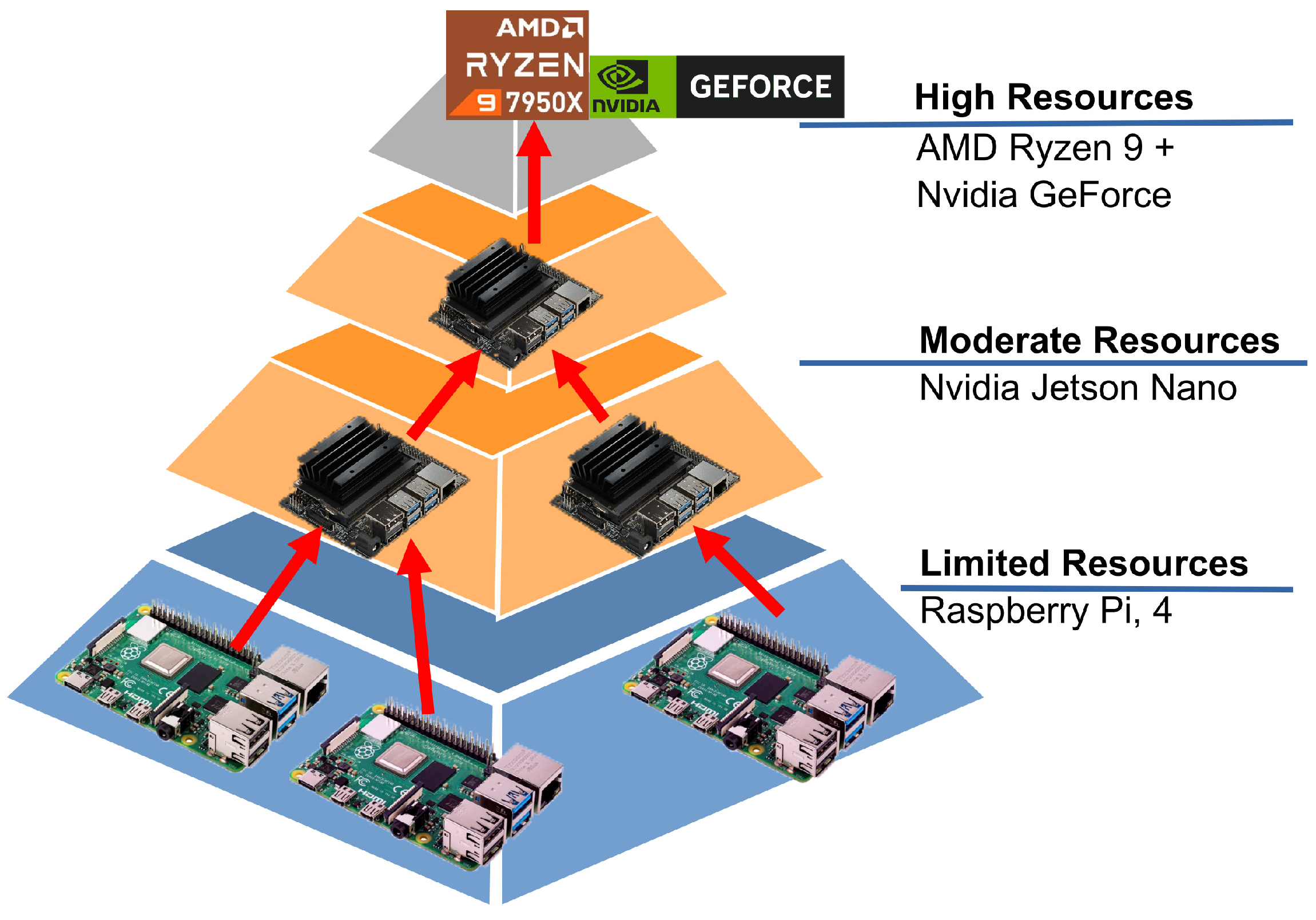
3.3. Deployment Diagram
- Edge layer: This layer is composed of grid sensor platforms with limited computational resources—for example, Raspberry Pi platforms with a camera for capturing images.
- First or second fog sublayer: Network-enabled platforms with moderate computational resources—for example, Nvidia Jetson Nano devices equipped with a graphics processing unit (GPU) to execute machine learning processes.
- Cloud layer: This layer is composed of devices with high-end resources for the CPU, GPU, and memory—for example, an AMD Ryzen server with a GeForce Nvidia GPU.
4. Implementation
- Edge layer
- -
- Hardware: Raspberry Pi 4 Model B Rev 1.4. ARMv7l @ 1.8 GHz, 2 GB RAM.
- -
- Software: Raspbian GPU/Linux 10 (buster) operating system. C++ programming language.
- First and second fog sublayers
- -
- Hardware: Nvidia Jetson Nano with ARMv8 Processor, 4 Cores @ 1.4 GHz, 2–4 GB RAM, and Nvidia Maxwell GPU.
- -
- Software: Nvidia Jetson Nano, Jetpack 4.6. C++ and Python are programming languages.
- Cloud layer
- -
- Hardware: AMD Ryzen 9 computer, with an Nvidia GeForce RTX 2070 GPU.
- -
- Software: Debian 12 as the operating system. C++ and Python programming languages.
5. Experimentation
- Evaluation of the reviewed lightweight cipher algorithms;
- Execution time;
- CPU percentage consumption;
- GPU percentage consumption;
- Memory percentage consumption;
- Power consumption.
- Background (B): No person appears in this video. The edge node tries to detect variations in the background scene. Therefore, the percentage of data sent to the first fog sublayer will be negligible or zero.
- Person (P): Scenes are composed of one person walking or standing. This person does not carry any weapon. However, it is expected to have some data traffic between the edge and the first fog sublayer. Therefore, secure data communications are sent.
- People (Pn): This scenario is similar to the prior case. However, there are several people involved who are walking or standing. All data communications to the first fog sublayer are protected. Nevertheless, no traffic is expected to the second fog sublayer because no weapon is detected.
- Armed person (AP): This video contains a person holding a weapon. With all communications secured, this scenario will send data through the first and second fog sublayers.
- Armed people (APn): This video contains scenes with several people holding guns in the same frame. Moreover, a person can hold different weapons at the same time. It is expected that a higher number of secured communications will occur between fog sublayers.
5.1. Evaluation of the Reviewed Lightweight Cipher Algorithms
5.1.1. Security Metrics
- Execution time: This parameter is commonly used to compare the consumption of resources in different algorithms. However, it is crucial in resource-constrained IoT devices.
- Entropy test: This value measures the randomness of the ciphered data. Therefore, the entropy value is at the maximum if all values of the data have the same or a similar probability [51]. Entropy is defined by Equation (3):The S variable is random and it produces output values within , and is the probability of occurrence of the output.
- test: This metric is used to confirm the results of the entropy test. The higher the uniformity of the ciphered data is, the harder it is for an intruder to obtain helpful knowledge about the data. The test is defined by Equation (4). Considering 8 bits per pixel, , is the observed probability and is the expected probability of the grey level , respectively.
- Key Space: The total number of distinct keys that can be generated to encrypt the data. The recommendation [59] for a minimal-length key for symmetric algorithms is 112 bits.
5.1.2. Scores of the Security Metrics
- These measures were taken on a Raspberry Pi model B, ARM @ 1.8 GHz and 2 GB RAM devices, using Python as the programming language.
- The image used for the test was the well-known Lake [60] image in its greyscale version, with a size of bytes and an 8-bit resolution.
- Execution time score: We set a maximum value of two seconds. The achieved score is calculated with (5):
- Entropy score: Considering an 8-bit resolution, the ideal value of entropy is 8. This value is provided by (6):
- score: Considering a significance level of , the value is obtained by (7). According to the 255-degrees-of-freedom table and , the critical value of is . Therefore, this test is passed if .
- Key space: The key space score is calculated with (8). The maximum number of keys in this case is 544.
- Sum score: The end score is the sum of each achieved mark, which is defined in (9):
| Category | Cipher | Time (s) | Score | Entropy | Score | Score | Key Space | Score | ||
|---|---|---|---|---|---|---|---|---|---|---|
| Stream Ciphers | LFSR | A5/1 [23] | 48.8 | −23.4 | 7.99 | 0.99 | 248 | 0.15 | 64 | 0.11 |
| Geffe [24] | 700 | −349 | 7.99 | 0.99 | 238 | 0.18 | 64 | 0.11 | ||
| Celular Automata | Pentavium [26] | 443 | −220 | 7.99 | 0.99 | 260 | 0.11 | 160 | 0.29 | |
| Trivium [61] | 15.2 | −6.6 | 7.99 | 0.99 | 291 | 0.007 | 160 | 0.29 | ||
| Numerical | RC4 [31] | 1.04 | 0.48 | 7.98 | 0.99 | 198 | 0.32 | 256 | 0.47 | |
| RC4-Marc [32] | 0.75 | 0.62 | 7.99 | 0.99 | 264 | 0.09 | 256 | 0.47 | ||
| Salsa20 [33] | 47.2 | −22.6 | 7.99 | 0.99 | 252 | 0.13 | 512 | 0.94 | ||
| Chacha20 [34] | 1.95 | 0.027 | 7.99 | 0.99 | 648 | −1.2 | 512 | 0.94 | ||
| Block Ciphers | SPN | AES [18] | 1.7 | 0.11 | 7.99 | 0.99 | 256 | 0.12 | 256 | 0.47 |
| Present [35] | 18.3 | −8.15 | 7.99 | 0.99 | 299 | −0.01 | 256 | 0.47 | ||
| FN | DES [36] | 24.3 | −11.1 | 7.99 | 0.99 | 259 | 0.11 | 256 | 0.47 | |
| Simon [37] | 0.85 | 0.57 | 7.99 | 0.99 | 270 | 0.07 | 256 | 0.47 | ||
| ARX | Speck [37] | 0.57 | 0.71 | 7.99 | 0.99 | 256 | 0.12 | 256 | 0.47 | |
| Proposal | GS3 [11] | 1.21 | 0.39 | 7.99 | 0.99 | 242 | 0.17 | 544 | 1.00 | |
5.1.3. Analysis of Security Strengths
Simulated Attack Model
- Tampering packet: A malicious node alters some data packets and then forwards them.
- Replay attack: An intruder resends old data packets. Therefore, the freshness of the data is affected.
- Packet forgery: A malicious node sends fake data packets, so the traffic network is increased and the energy consumption rises consequently.
- Selective forwarding: A malicious node sends data packets selectively, and others can be partially deleted. Therefore, this may cause a loss of data.
Analysis of the Key Space
Differential Cryptoanalysis
- Select a byte randomly from the plaintext and modify the four most significant bits (MSb) of it. When altering only 1 bit, the values of the NPCR and UACI were 99.607 and 33.511, respectively.
- The same data block was scrambled with small changes in the seeds or keys. When altering only the most significant bit of the parameter b in Equation (2), the values of the NPCR and UACI were 99.61 and 33.67, respectively.
Randomness Tests
- Ent test suite [63]: This test was run with a binary file of about bits. The results were as follows: entropy, 1.00 bits per bit; arithmetic mean value of data bits, 0.50, where 0.5 means random; Monte Carlo value for Pi, 3.138799615; and serial correlation coefficient, 0.000069.
- 800-22-rev1 test suite [64]: This was run with 100 sequences of 100,000 bits. Only 2 out of the 15 tests that compose the suite fail to assess the randomness, specifically the dft and overlapping-template-matching tests.
5.2. Edge Layer
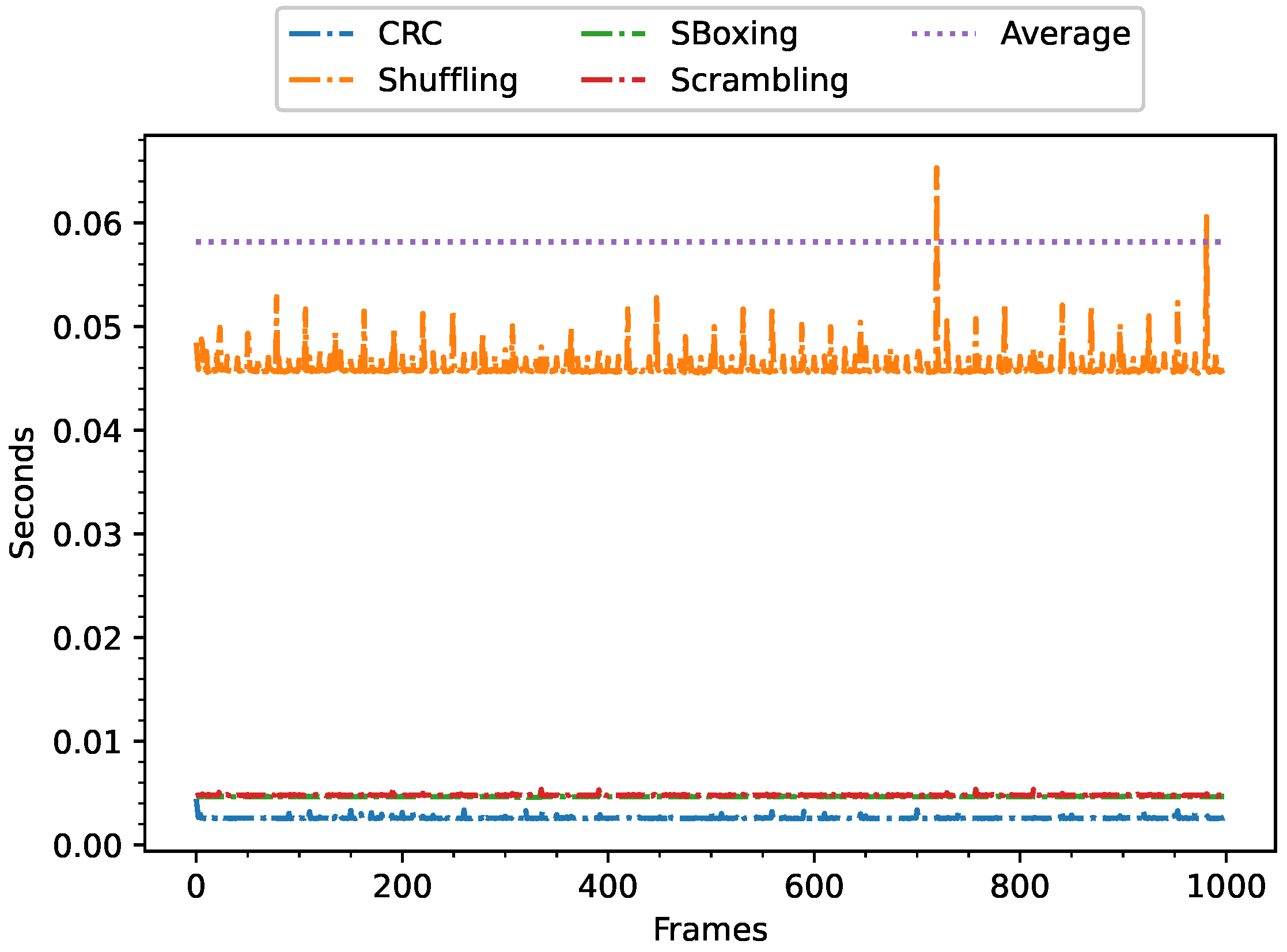
5.2.1. Cipher Execution Time of GS3 Method in the Edge Layer
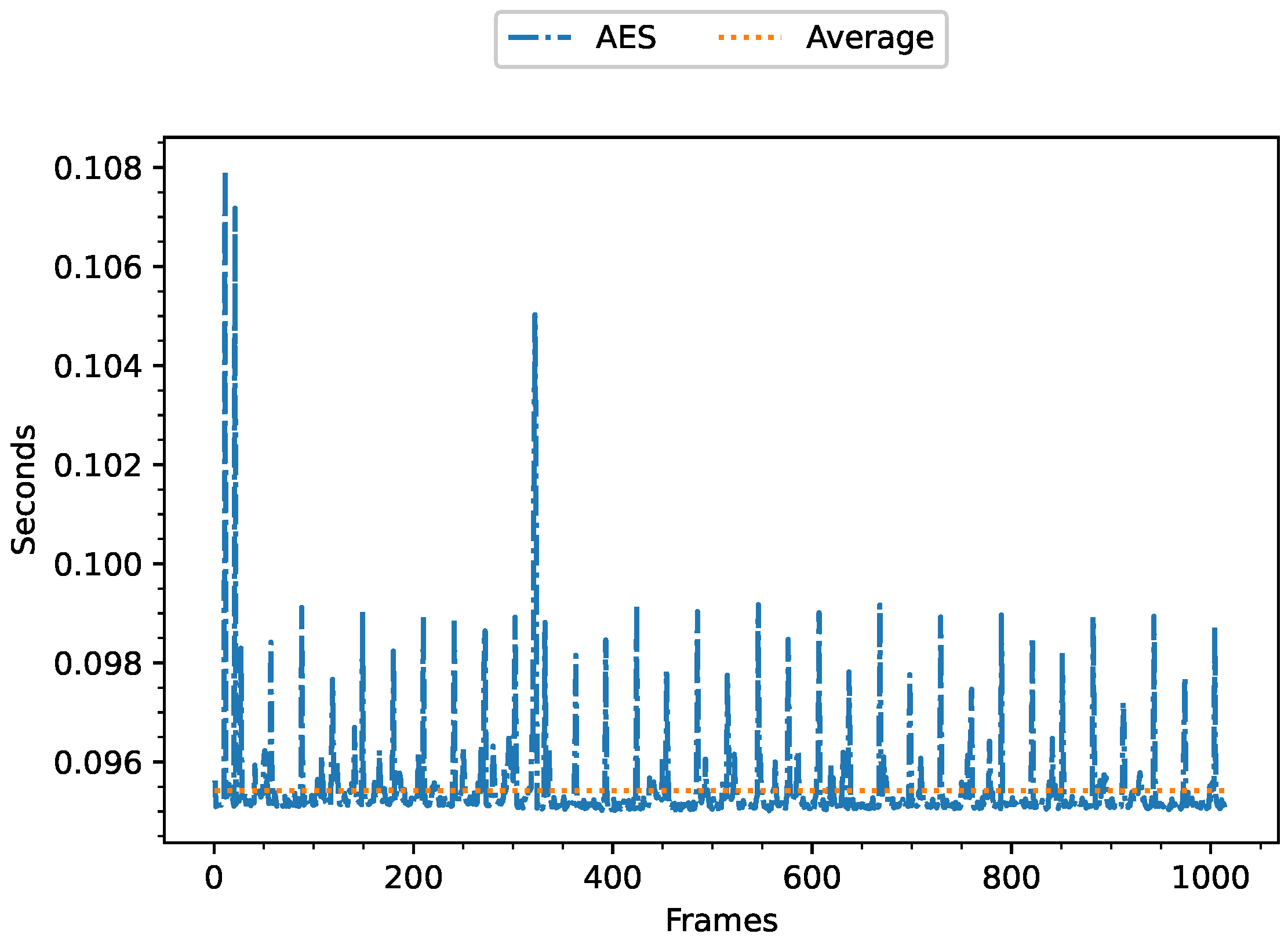
5.2.2. Cipher Execution Time of AES Algorithm in the Edge Layer
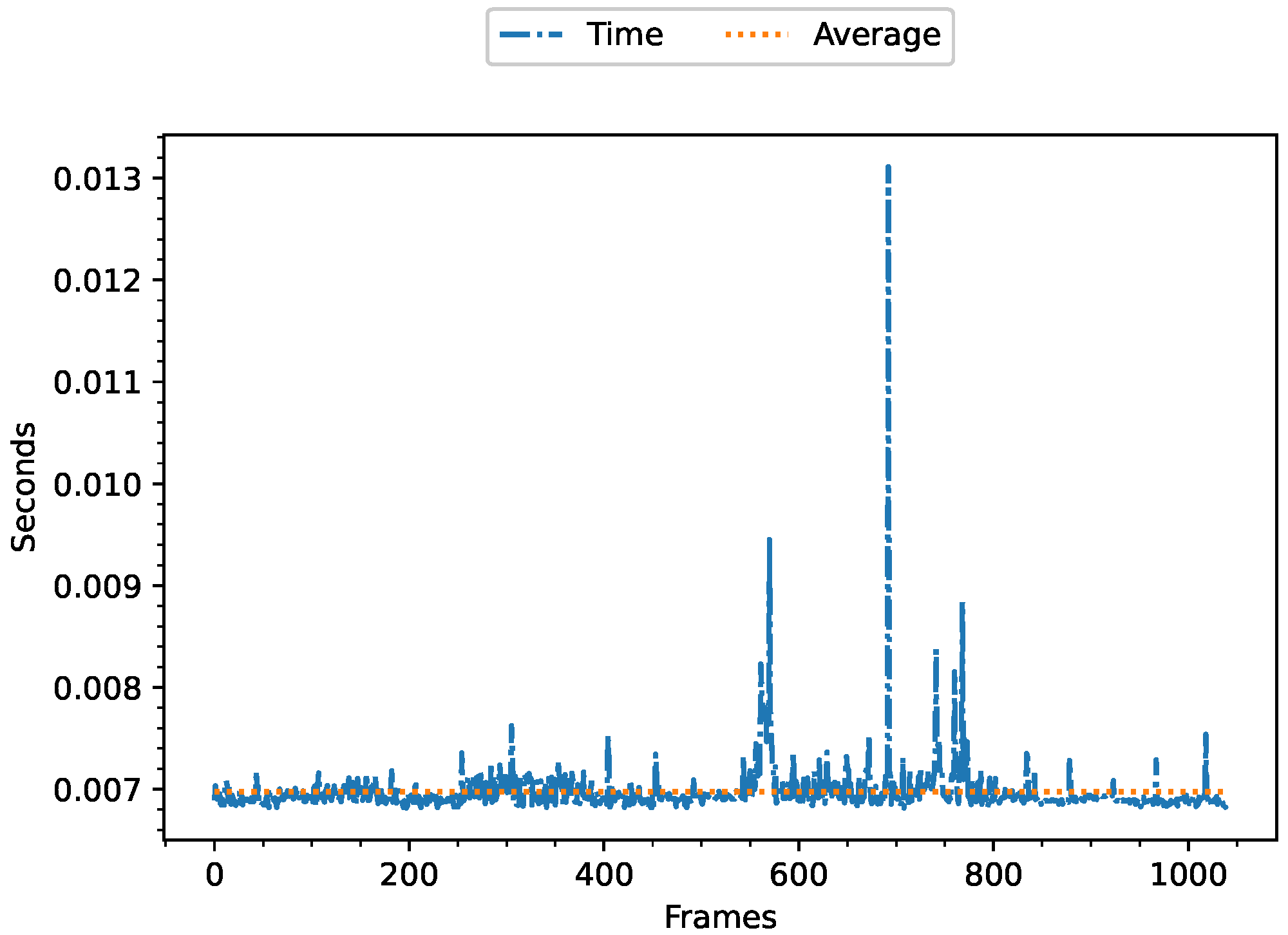
5.2.3. Execution Time of SmartFog Method in the Edge Layer
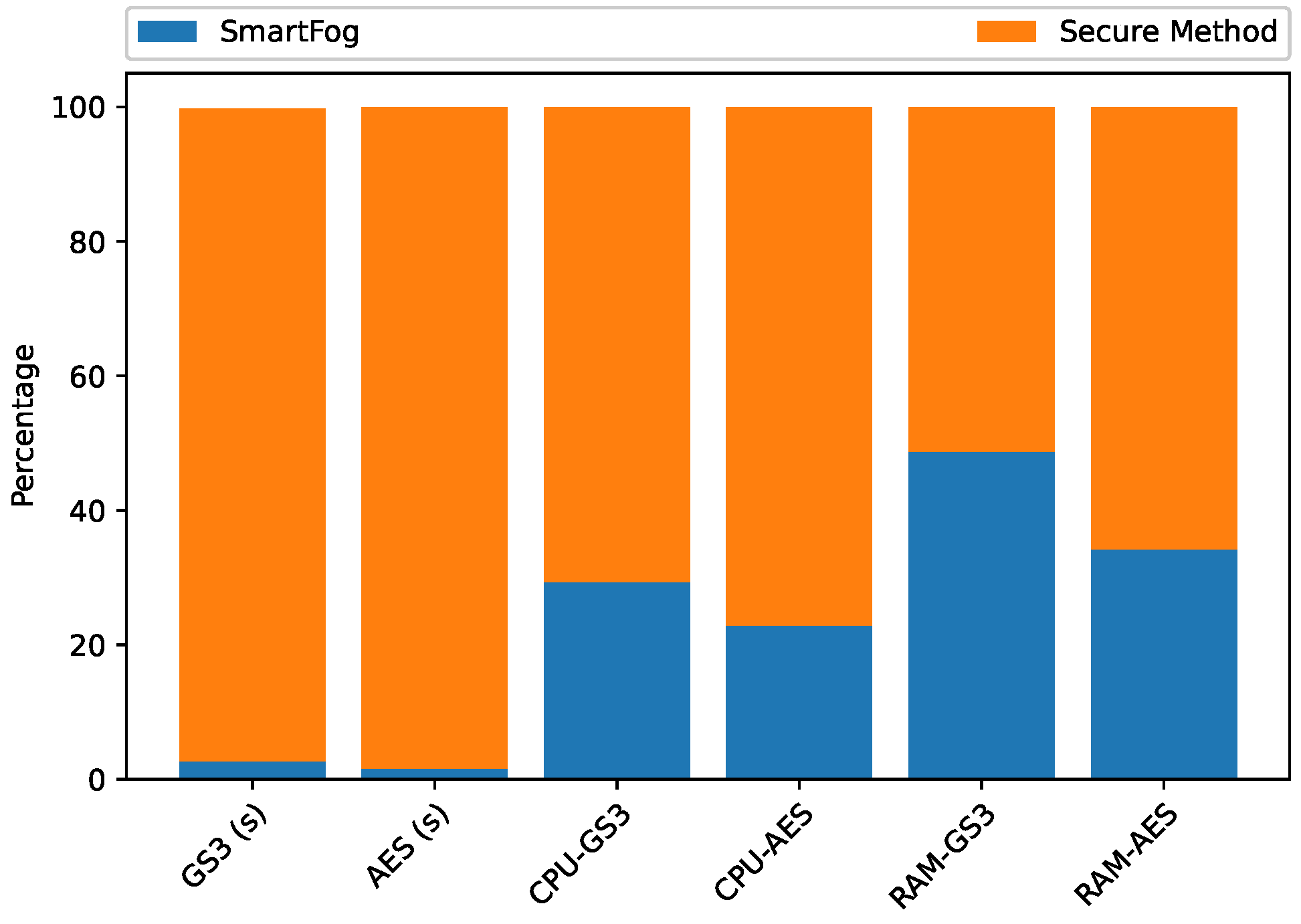
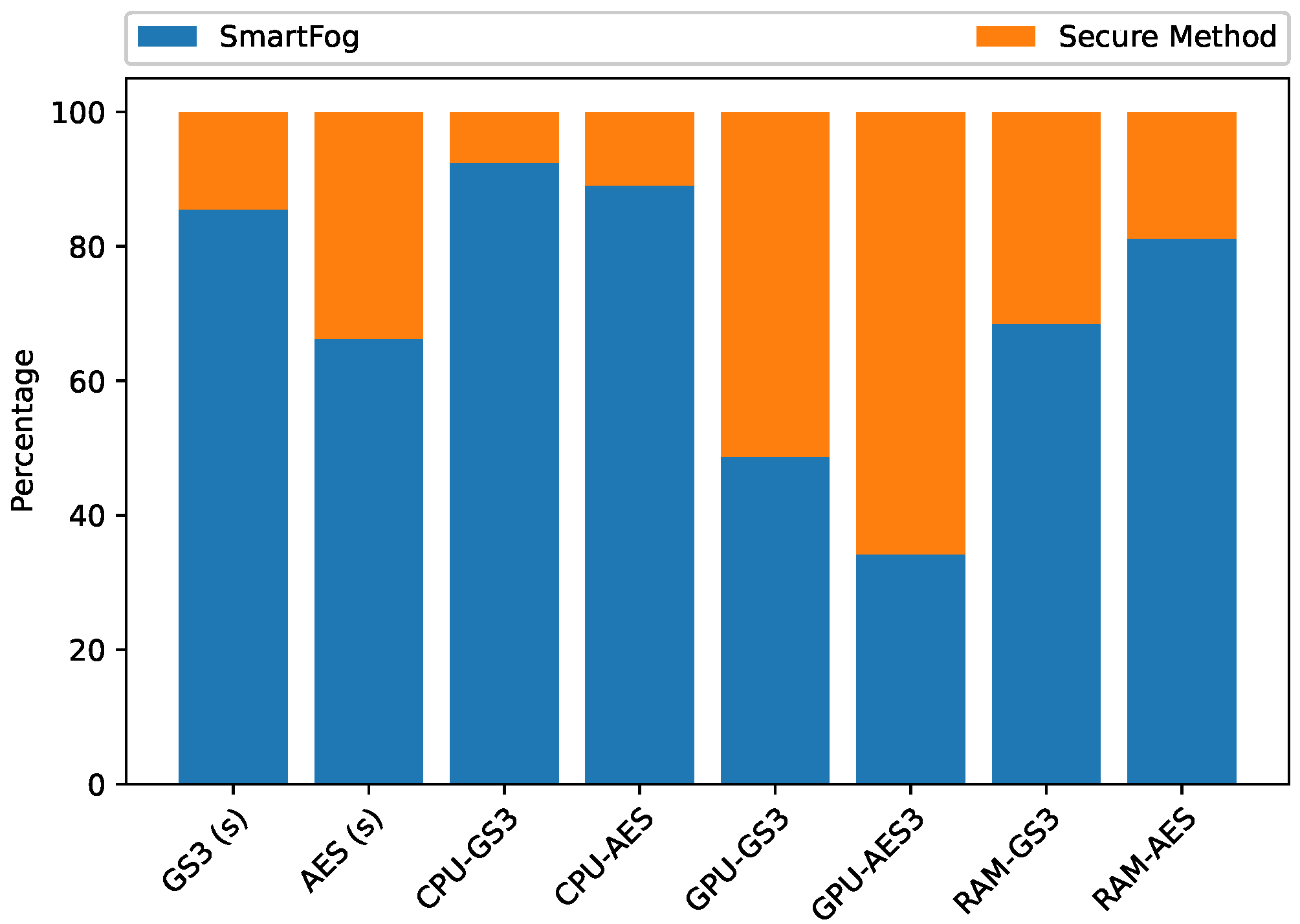
5.2.4. Quantitative Results of Execution Time, CPU, and Memory Consumption in the Edge Layer
5.3. First Fog Sublayer
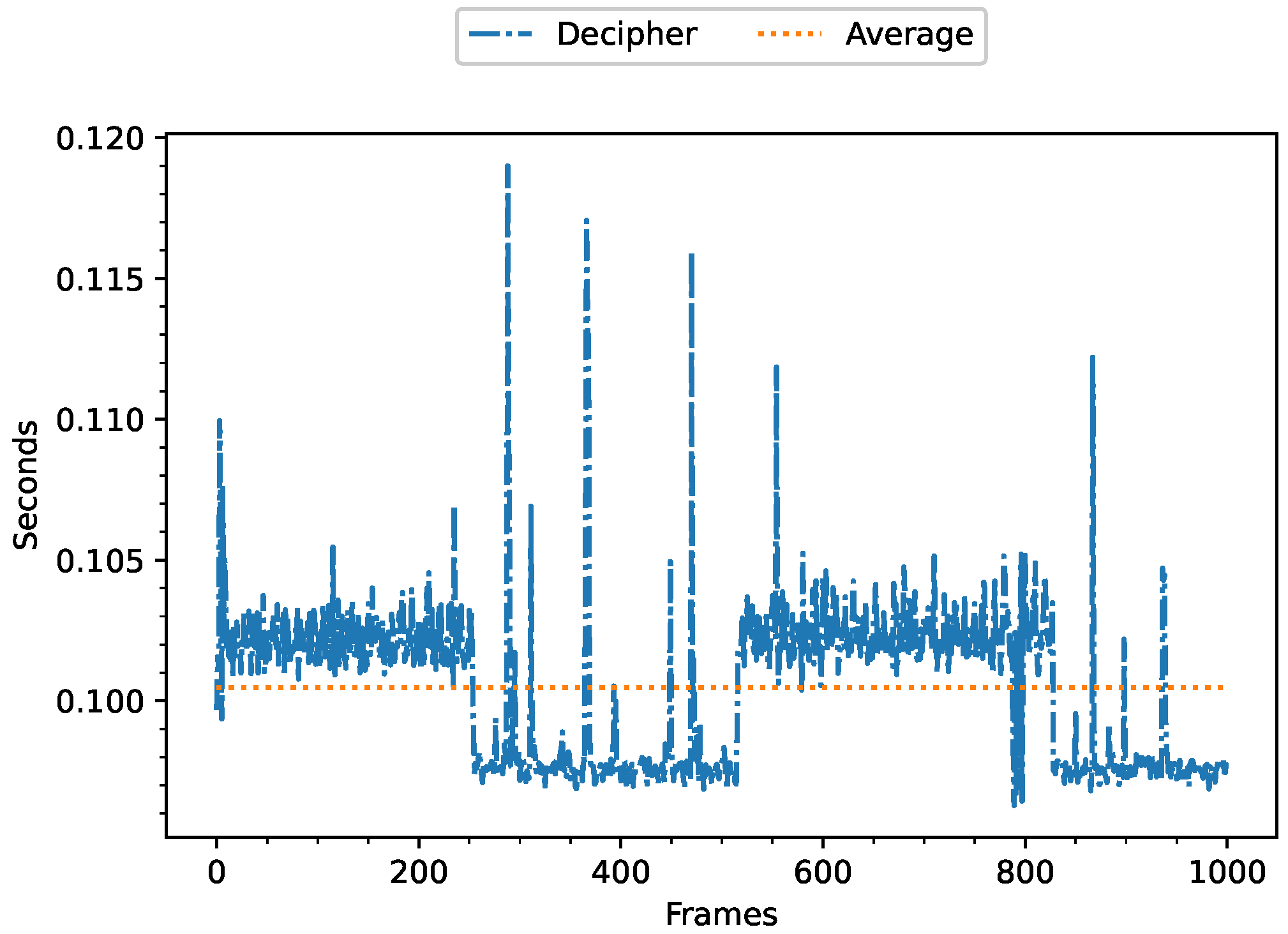
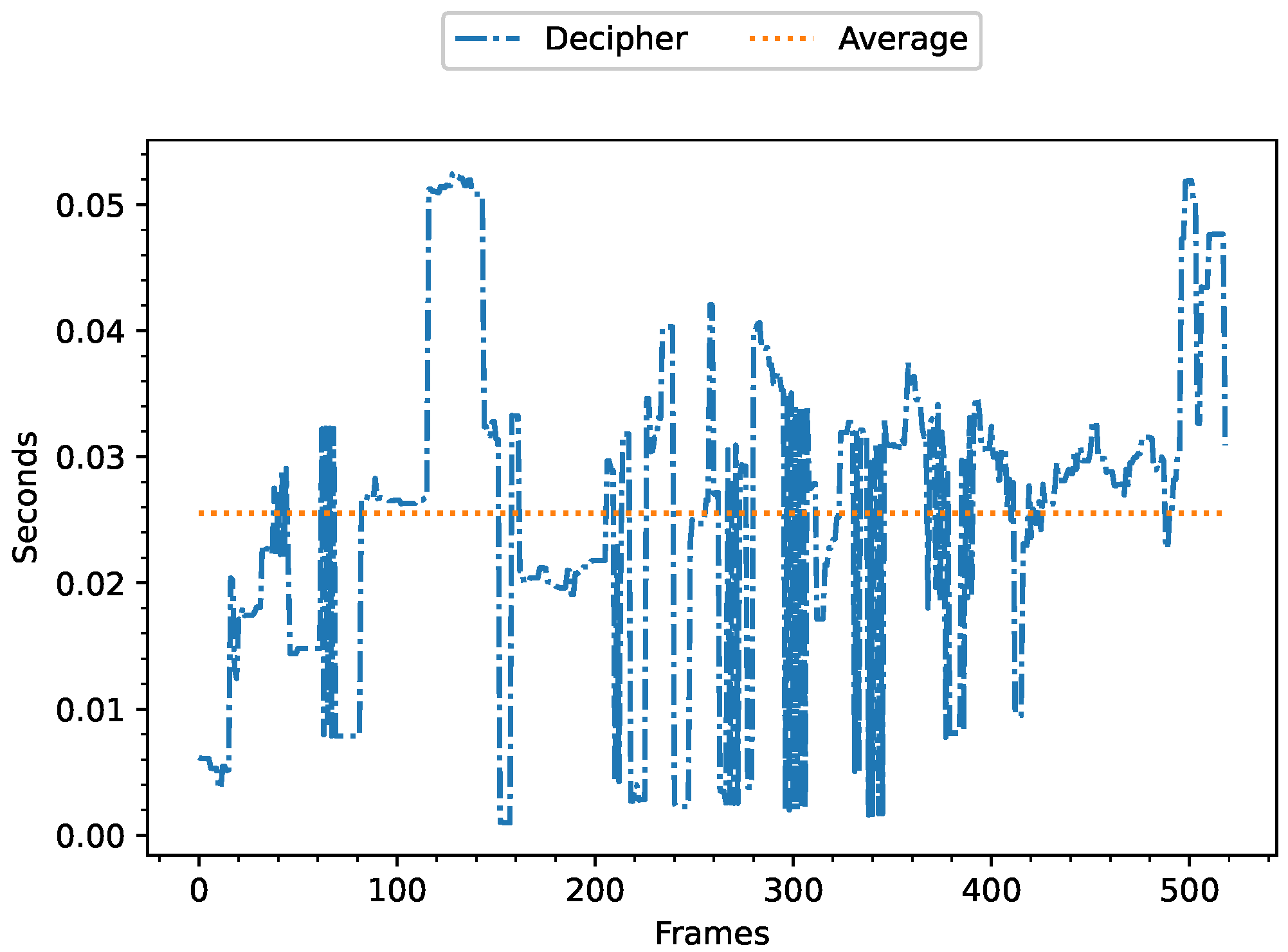
5.3.1. Decipher Execution Time of GS3 Method in the First Fog Sublayer
5.3.2. Cipher Execution Time of GS3 Method in the First Fog Sublayer
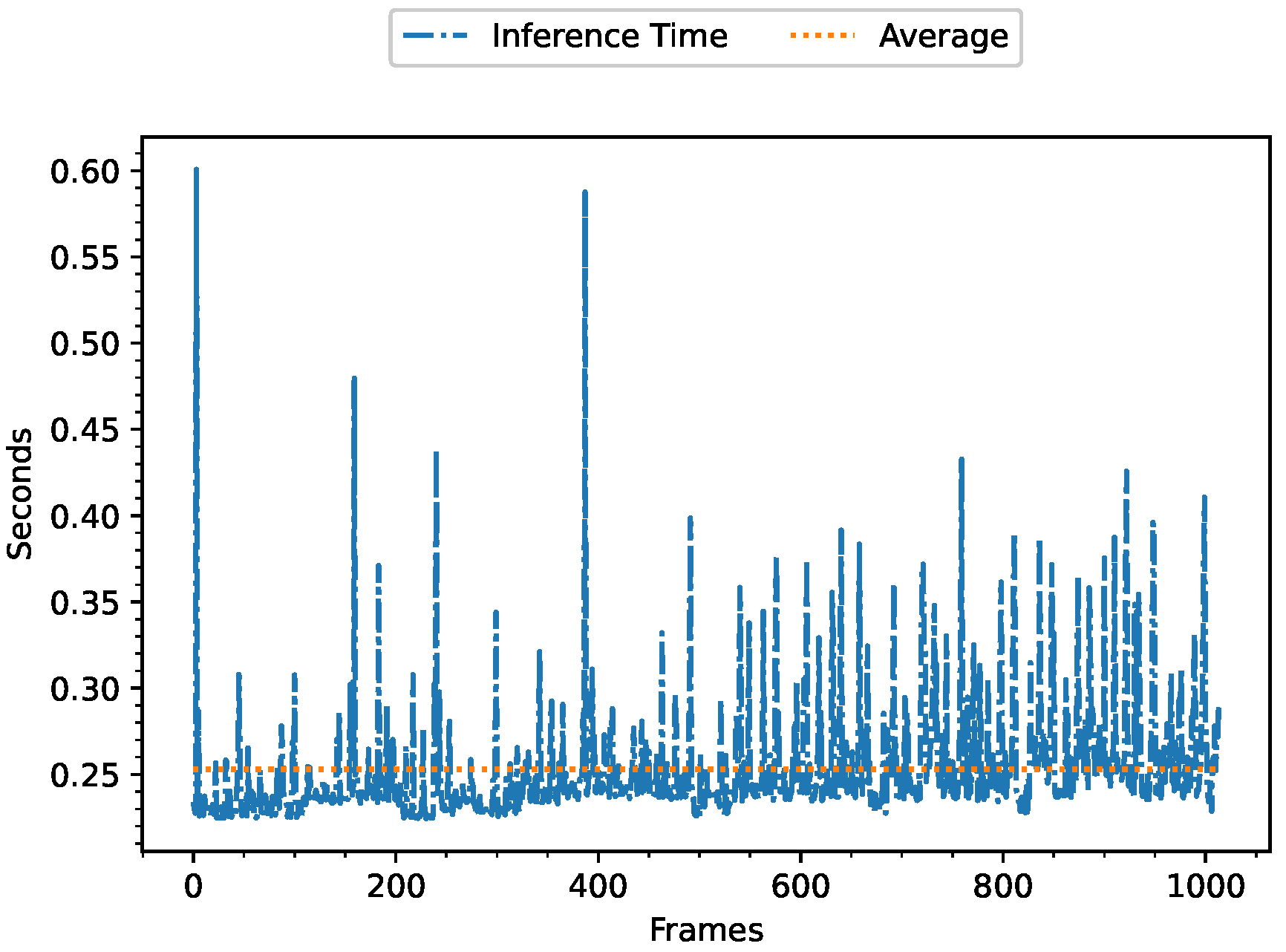
5.3.3. Inference Time in the First Fog Sublayer
5.3.4. Decipher Execution Time of AES Algorithm in the First Fog Sublayer
5.3.5. Cipher Execution Time of AES Algorithm in the First Fog Sublayer
5.3.6. Quantitative Results of Execution Time, CPU, GPU, and Memory Consumption in the First Fog Sublayer
5.4. Second Fog Sublayer
5.4.1. Decipher Execution Time of GS3 Proposal in the Second Fog Sublayer
5.4.2. Cipher Execution Time of GS3 Proposal in the Second Fog Sublayer
5.4.3. Inference Time in the Second Fog Sublayer
5.4.4. Decipher Execution Time of AES Algorithm in the Second Fog Sublayer
5.4.5. Cipher Execution Time of AES Algorithm in the Second Fog Sublayer
5.4.6. Quantitative Results of Execution Time, CPU, GPU, and Memory Consumption in the Second Fog Sublayer
5.5. Power Consumption
- The Agilent 3631A power supply [66].
- A Raspberry Pi [67] as an edge device; it is powered by a regulated Agilent 3631A power source.
- The Agilent 34405A multimeter to measure the current; it is connected in series with the circuit.
- The Agilent 34405A multimeter is connected to a computer via a USB port to transfer current samples using the Virtual Instrument Software Architecture (VISA) protocol [68] developed by IVI Foundation [69]. A Python script is run on the computer that receives the measures. These are interpreted by the PyVISA library [70]. After this, the Pandas Python library [71] allows the reading and analysis of the current measures. Then, data are represented using the Matplotlib Python library [72].
5.6. Visual Results
- Figure 28a,b present ciphered frames with the GS3 proposal and AES algorithm, respectively.
- After the deciphering process, the received frame in the first fog sublayer is processed and analysed by our weapon detection system. As a result, bounding boxes identifying armed persons are computed. Figure 29a exhibits this processing.
- After deciphering the received frame in the second fog sublayer, bounding boxes for the detection of faces are generated. Figure 29b shows the detected faces. These faces will be recognised in the cloud layer.
6. Discussion
7. Conclusions
8. Future Works
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Taylor, B.G.; Mitchell, K.J.; Turner, H.A.; Sheridan-Johnson, J.; Mumford, E.A. Prevalence of Gun Carrying and Gun Violence Victimization and Perpetration Among a Nationally Representative Sample of U.S. Youth and Young Adults. AJPM Focus 2025, 4, 100294. [Google Scholar] [CrossRef] [PubMed]
- Rezey, M.L.; Olson, D.E.; Stemen, D. Urban Victims of Nonlethal Gun Violence: A Chicago-Centered Analysis Using the National Crime Victimization Survey. Crime Delinq. 2025, 71, 2389–2416. [Google Scholar] [CrossRef]
- Global Terrorism Index. Available online: https://www.visionofhumanity.org/maps/global-terrorism-index/ (accessed on 1 November 2024).
- Alenizi, A.S.; Al-Karawi, K.A. Internet of Things (IoT) Adoption: Challenges and Barriers. In Proceedings of the Seventh International Congress on Information and Communication Technology; Yang, X.S., Sherratt, S., Dey, N., Joshi, A., Eds.; Springer: Singapore, 2023; pp. 217–229. [Google Scholar]
- Rejeb, A.; Rejeb, K.; Treiblmaier, H.; Appolloni, A.; Alghamdi, S.; Alhasawi, Y.; Iranmanesh, M. The Internet of Things (IoT) in healthcare: Taking stock and moving forward. Internet Things 2023, 22, 100721. [Google Scholar] [CrossRef]
- Dhanaraju, M.; Chenniappan, P.; Ramalingam, K.; Pazhanivelan, S.; Kaliaperumal, R. Smart Farming: Internet of Things (IoT)-Based Sustainable Agriculture. Agriculture 2022, 12, 1745. [Google Scholar] [CrossRef]
- Firouzi, F.; Farahani, B.; Marinsek, A. The convergence and interplay of edge, fog, and cloud in the AI-driven Internet of Things (IoT). Inf. Syst. 2022, 107, 101840. [Google Scholar] [CrossRef]
- Kong, L.; Tan, J.; Huang, J.; Chen, G.; Wang, S.; Jin, X.; Zeng, P.; Khan, M.; Das, S.K. Edge-computing-driven Internet of Things: A Survey. ACM Comput. Surv. 2023, 55, 174. [Google Scholar] [CrossRef]
- Bukhari, S.M.S.; Zafar, M.H.; Abou Houran, M.; Moosavi, S.K.R.; Mansoor, M.; Muaaz, M.; Sanfilippo, F. Secure and privacy-preserving intrusion detection in wireless sensor networks: Federated learning with SCNN-Bi-LSTM for enhanced reliability. AD HOC Netw. 2024, 155, 103407. [Google Scholar] [CrossRef]
- Alcaraz Velasco, F.; Palomares, J.M.; Olivares, J. Lightweight method of shuffling overlapped data-blocks for data integrity and security in WSNs. Comput. Netw. 2021, 199, 108470. [Google Scholar] [CrossRef]
- Alcaraz-Velasco, F.; Palomares, J.M.; Olivares, J. GS3: A Lightweight Method of Generating Data Blocks With Shuffling, Scrambling, and Substituting Data for Constrained IoT Devices. IEEE Internet Things J. 2024, 11, 25782–25801. [Google Scholar] [CrossRef]
- Piccialli, F.; Di Somma, V.; Giampaolo, F.; Cuomo, S.; Fortino, G. A survey on deep learning in medicine: Why, how and when? Inf. Fusion 2021, 66, 111–137. [Google Scholar] [CrossRef]
- Cui, Y.; Chen, R.; Chu, W.; Chen, L.; Tian, D.; Li, Y.; Cao, D. Deep Learning for Image and Point Cloud Fusion in Autonomous Driving: A Review. IEEE Trans. Intell. Transp. Syst. 2022, 23, 722–739. [Google Scholar] [CrossRef]
- Li, J.; Xu, W.; Deng, L.; Xiao, Y.; Han, Z.; Zheng, H. Deep learning for visual recognition and detection of aquatic animals: A review. Rev. Aquac. 2023, 15, 409–433. [Google Scholar] [CrossRef]
- 5Yadav, P.; Gupta, N.; Sharma, P.K. Robust weapon detection in dark environments using Yolov7-DarkVisionImage. Digit. Signal Process. 2024, 145, 104342. [Google Scholar] [CrossRef]
- Burnayev, Z.R.; Toibazarov, D.O.; Atanov, S.K.; Canbolat, H.; Seitbattalov, Z.Y.; Kassenov, D.D. Weapons Detection System Based on Edge Computing and Computer Vision. Int. J. Adv. Comput. Sci. Appl. 2023, 14, 812–820. [Google Scholar] [CrossRef]
- Martinez, H.; Rodriguez-Lozano, F.J.; León-García, F.; Palomares, J.M.; Olivares, J. Distributed Fog computing system for weapon detection and face recognition. J. Netw. Comput. Appl. 2024, 232, 104026. [Google Scholar] [CrossRef]
- Nechvatal, J.; Barker, E.; Bassham, L.; Burr, W.; Dworkin, M.; Foti, J.; oback, E. Report on the Development of the Advanced Encryption Standard (AES). J. Res. Natl. Inst. Stand. Technol. 2001, 106, 511–577. [Google Scholar] [CrossRef]
- Jamshed, M.A.; Ali, K.; Abbasi, Q.H.; Imran, M.A.; Ur-Rehman, M. Challenges, Applications, and Future of Wireless Sensors in Internet of Things: A Review. IEEE Sens. J. 2022, 22, 5482–5494. [Google Scholar] [CrossRef]
- Singh, S.K.; Kumar Dhurandher, S. Architecture of Fog Computing, Issues and Challenges: A Review. In Proceedings of the 2020 IEEE 17th India Council International Conference (INDICON), New Delhi, India, 10–13 December 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Shamshad, S.; Riaz, F.; Riaz, R.; Rizvi, S.S.; Abdulla, S. An Enhanced Architecture to Resolve Public-Key Cryptographic Issues in the Internet of Things IoT, Employing Quantum Computing Supremacy. Sensors 2022, 22, 8151. [Google Scholar] [CrossRef]
- De Cannière, C.; Preneel, B. New Stream Cipher Designs: The eSTREAM Finalists. (Trivium); Springer: Berlin/Heidelberg, Germany, 2008; pp. 244–266. [Google Scholar]
- Gundaram, P.K.; Tentu, A.N.; Allu, S.N. State Transition Analysis of GSM Encryption Algorithm A5/1. J. Commun. Softw. Syst. 2022, 18, 36–41. [Google Scholar] [CrossRef]
- Bajaj, N. Linear Feedback Shift Register: 1.0.6. Available online: https://pypi.org/project/pylfsr/ (accessed on 17 April 2023).
- Wolfram, S. Random sequence generation by cellular automata. Adv. Appl. Math. 1986, 7, 123–169. [Google Scholar] [CrossRef]
- John, A.; Nandu, B.C.; Ajesh, A.; Jose, J. PENTAVIUM: Potent Trivium-Like Stream Cipher Using Higher Radii Cellular Automata. In Cellular Automata; Gwizdałła, T.M., Manzoni, L., Sirakoulis, G.C., Bandini, S., Podlaski, K., Eds.; Springer International Publishing: Cham, Switzerland, 2021; pp. 90–100. [Google Scholar]
- Dridi, F.; El Assad, S.; El Hadj Youssef, W.; Machhout, M.; Lozi, R. Design, Implementation, and Analysis of a Block Cipher Based on a Secure Chaotic Generator. Appl. Sci. 2022, 12, 9952. [Google Scholar] [CrossRef]
- Alshammari, B.M.; Guesmi, R.; Guesmi, T.; Alsaif, H.; Alzamil, A. Implementing a Symmetric Lightweight Cryptosystem in Highly Constrained IoT Devices by Using a Chaotic S-Box. Symmetry 2021, 13, 129. [Google Scholar] [CrossRef]
- Lorenz, E.N. Deterministic Nonperiodic Flow. J. Atmos. Sci. 1963, 20, 130–141. [Google Scholar] [CrossRef]
- Zhu, S.; Deng, X.; Zhang, W.; Zhu, C. A New One-Dimensional Compound Chaotic System and Its Application in High-Speed Image Encryption. Appl. Sci. 2021, 11, 11206. [Google Scholar] [CrossRef]
- Schneier, B.; Sutherland, P. Applied Cryptography: Protocols, Algorithms, and Source Code in C, 2nd ed.; John Wiley & Sons, Inc.: Hoboken, NJ, USA, 1995. [Google Scholar]
- Zheng, J. MARC: Modified ARC4. In Foundations and Practice of Security; Garcia-Alfaro, J., Cuppens, F., Cuppens-Boulahia, N., Miri, A., Tawbi, N., Eds.; Springer: Berlin/Heidelberg, Germany, 2013; pp. 33–44. [Google Scholar]
- The eSTREAM Project, Salsa20. Available online: https://www.ecrypt.eu.org/stream/salsa20pf.html (accessed on 1 April 2024).
- ChaCha20 and Poly1305 for IETF Protocols. RFC 7539. Available online: https://www.rfc-editor.org/info/rfc7539 (accessed on 5 February 2024).
- Bogdanov, A.; Knudsen, L.R.; Leander, G.; Paar, C.; Poschmann, A.; Robshaw, M.J.B.; Seurin, Y.; Vikkelsoe, C. PRESENT: An Ultra-Lightweight Block Cipher. In Cryptographic Hardware and Embedded Systems—CHES; Paillier, P., Verbauwhede, I., Eds.; Springer: Berlin/Heidelberg, Germany, 2007; pp. 450–466. [Google Scholar]
- Data Encryption Standard DES. Available online: https://csrc.nist.gov/CSRC/media/Publications/fips/46/archive/1977-01-15/documents/NBS.FIPS.46.pdf (accessed on 1 April 2024).
- Beaulieu, R.; Shors, D.; Smith, J.; Treatman-Clark, S.; Weeks, B.; Wingers, L.; The SIMON and SPECK Families of Lightweight Block Ciphers. Cryptology ePrint Archive, Paper 2013/404. Available online: https://eprint.iacr.org/2013/404 (accessed on 5 January 2024).
- Santos, T.; Oliveira, H.; Cunha, A. Systematic review on weapon detection in surveillance footage through deep learning. Comput. Sci. Rev. 2024, 51, 100612. [Google Scholar] [CrossRef]
- Girshick, R. Fast R-CNN. In Proceedings of the 2015 IEEE International Conference on Computer Vision (ICCV), Santiago, Chile, 11–18 December 2015; pp. 1440–1448. [Google Scholar] [CrossRef]
- YOLO. Available online: https://docs.ultralytics.com/models/ (accessed on 2 January 2025).
- Abdullah, M.; Al-Noori, A.H.Y.; Suad, J.; Tariq, E. A multi-weapon detection using ensembled learning. J. Intell. Syst. 2024, 33, 20230060. [Google Scholar] [CrossRef]
- EfficientDet. Available online: https://github.com/xuannianz/EfficientDet?tab=readme-ov-file (accessed on 12 November 2024).
- Message Queuing Telemetry Transport. Available online: https://mqtt.org// (accessed on 12 April 2025).
- Wang, C.Y.; Bochkovskiy, A.; Liao, H.Y.M. YOLOv7: Trainable Bag-of-Freebies Sets New State-of-the-Art for Real-Time Object Detectors. In Proceedings of the 2023 IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR), Vancouver, BC, Canada, 17–24 June 2023; pp. 7464–7475. [Google Scholar] [CrossRef]
- You, Y.; Wang, J.; Yu, Z.; Sun, Y.; Peng, Y.; Zhang, S.; Bian, S.; Wang, E.; Wu, W. A Fine-Grained Detection Network Model for Soldier Targets Adopting Attack Action. IEEE Access 2024, 12, 107445–107458. [Google Scholar] [CrossRef]
- Ultralytics YOLOv8. Available online: https://docs.ultralytics.com/es/models/yolov8/ (accessed on 1 March 2024).
- Amado-Garfias, A.J.; Conant-Pablos, S.E.; Ortiz-Bayliss, J.C.; Terashima-Marin, H. Improving Armed People Detection on Video Surveillance Through Heuristics and Machine Learning Models. IEEE Access 2024, 12, 111818–111831. [Google Scholar] [CrossRef]
- Torregrosa-Dominguez, A.; Alvarez-Garcia, J.A.; Salazar-Gonzalez, J.L.; Soria-Morillo, L.M. Effective Strategies for Enhancing Real-Time Weapons Detection in Industry. Appl. Sci. 2024, 14, 8198. [Google Scholar] [CrossRef]
- Sanjuan, E.B.; Cardiel, I.A.; Cerrada, J.A.; Cerrada, C. Message Queuing Telemetry Transport (MQTT) Security: A Cryptographic Smart Card Approach. IEEE Access 2020, 8, 115051–115062. [Google Scholar] [CrossRef]
- Bouakkaz, F.; Omar, M.; Laib, S.; Guermouz, L.; Tari, A.; Bouabdallah, A. Lightweight Sharing Scheme for Data Integrity Protection in WSN. Wirel. Pers. Commun. 2016, 89, 211–226. [Google Scholar] [CrossRef]
- Shannon, C.E. Communication theory of secrecy systems. Bell Syst. Tech. J. 1949, 28, 656–715. [Google Scholar] [CrossRef]
- Farah, T.; Rhouma, R.; Belghith, S. A novel method for designing S-box based on chaotic map and Teaching–Learning-Based Optimization. Nonlinear Dyn. 2017, 88, 1059–1074. [Google Scholar] [CrossRef]
- Artuğer, F.; Özkaynak, F. A method for generation of substitution box based on random selection. Egypt. Inform. J. 2022, 23, 127–135. [Google Scholar] [CrossRef]
- Islam, F.u.; Liu, G. Designing S-Box Based on 4D-4Wing Hyperchaotic System. 3D Res. 2017, 8, 9. [Google Scholar] [CrossRef]
- YOLOv5s. Available online: https://github.com/ultralytics/yolov5?tab=readme-ov-file (accessed on 15 January 2025).
- Wu, C.; Cai, C.; Xiao, F.; Wang, J.; Guo, Y.; Ma, L. YOLO-LSM: A Lightweight UAV Target Detection Algorithm Based on Shallow and Multiscale Information Learning. Information 2025, 16, 393. [Google Scholar] [CrossRef]
- Face-Recognition Lybrary. Available online: https://pypi.org/project/face-recognition/ (accessed on 15 January 2025).
- Free Videos Shared by the Pexels Community. Available online: https://www.pexels.com/videos/ (accessed on 1 February 2024).
- Federal Office for Information Security (BSI). Cryptographic Mechanisms: Recommendations and Key Lengths, Version: 2023-1; Technical report; German Federal Office for Information Security: Bonn, Germany, 2023. [Google Scholar]
- Data Base Images. Available online: https://ccia.ugr.es/cvg/dbimagenes/ (accessed on 2 March 2025).
- Yudha, U. Source Code of Trivium. Available online: https://github.com/uisyudha/Trivium (accessed on 4 January 2024).
- Wu, Y.; Noonan, J.P.; Agaian, S.S. NPCR and UACI Randomness Tests for Image Encryption. Cyber J. J. Sel. Areas Telecommun. 2011, 1, 31–38. [Google Scholar]
- Walker, J. A Pseudorandom Number Sequence Test Program. Available online: https://www.fourmilab.ch/random/ (accessed on 4 March 2024).
- Bassham, L.E.; Rukhin, A.L.; Soto, J.; Nechvatal, J.R.; Smid, M.E.; Barker, E.B.; Leigh, S.D.; Levenson, M.; Vangel, M.; Banks, D.L.; et al. SP 800-22 Rev. 1a. A Statistical Test Suite for Random and Pseudorandom Number Generators for Cryptographic Applications; Technical report; National Institute of Standards and Technology (NIST): Gaithersburg, MD, USA, 2010. [Google Scholar]
- Castillo-Secilla, J.M.; Aranda, P.C.; Outeiriño, F.J.B.; Olivares, J. Experimental Procedure for the Characterization and Optimization of the Power Consumption and Reliability in ZigBee Mesh Networks. In 2010 Third International Conference on Advances in Mesh Networks; IEEE Computer Society: Wahsington, DC, USA, 2010; pp. 13–16. [Google Scholar]
- Agilent 3631A Power Suppley. Available online: https://www.keysight.com/es/en/product/E3631A/80w-triple-output-power-supply-6v-5a–25v-1a.html (accessed on 1 March 2024).
- Vujović, V.; Maksimović, M. Raspberry Pi as a Wireless Sensor node: Performances and constraints. In Proceedings of the 37th International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), Opatija, Croatia, 26–30 May 2014; pp. 1013–1018. [Google Scholar]
- VISA Protocol. Available online: https://www.ivifoundation.org/specifications/default.html#visa-specifications (accessed on 1 January 2024).
- IVI Foundation. Available online: https://www.ivifoundation.org/ (accessed on 1 January 2024).
- PyVISA Library. Available online: https://pyvisa.readthedocs.io/en/latest/introduction/index.html (accessed on 1 January 2024).
- Pandas Library. Available online: https://pandas.pydata.org (accessed on 1 January 2024).
- Matplotlib Library. Available online: https://matplotlib.org/ (accessed on 1 January 2024).
- Leon-Garcia, F.; Palomares, J.M.; Olivares, J. D2R-TED: Data—Domain Reduction Model for Threshold-Based Event Detection in Sensor Networks. Sensors 2018, 18, 3806. [Google Scholar] [CrossRef]
- Mekdad, Y.; Aris, A.; Babun, L.; Fergougui, A.E.; Conti, M.; Lazzeretti, R.; Uluagac, A.S. A survey on security and privacy issues of UAVs. Comput. Netw. 2023, 224, 109626. [Google Scholar] [CrossRef]










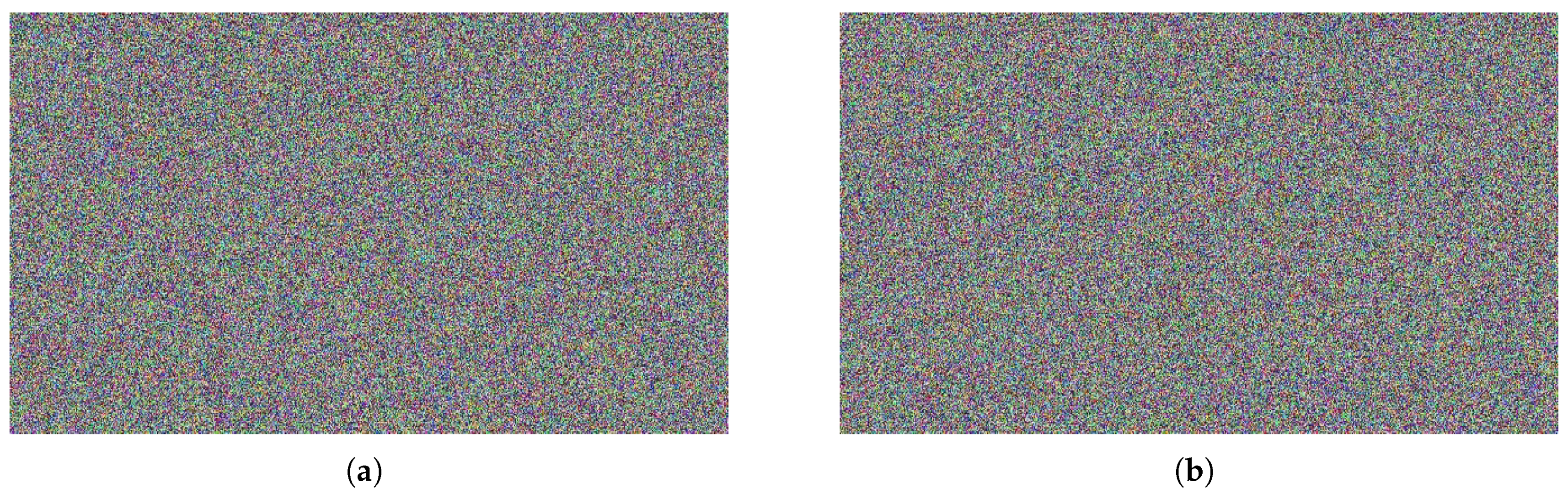

| Type of Attack | Attacks | Detected |
|---|---|---|
| Tamper | 355 | 100% |
| Replaying | 435 | 100% |
| Forwarding | 420 | 100% |
| Forgery | 390 | 100% |
| Method | Operation | |||
|---|---|---|---|---|
| GS3 | Cipher | 0.058 | – | – |
| AES | Cipher | 0.095 | – | – |
| SmartFog | BS | 0.0056 | 10.24 | 2.54 |
| SmartFog + AES | Combined | 0.102 | 44.65 | 7.42 |
| SmartFog + GS3 | Combined | 0.063 | 34.85 | 5.21 |
| Method | Operation | ||||
|---|---|---|---|---|---|
| GS3 | Decipher | 0.030 | – | – | – |
| Cipher | 0.013 | – | – | – | |
| AES | Decipher | 0.100 | – | – | – |
| Cipher | 0.029 | – | – | – | |
| SmartFog | Inference | 0.253 | 82.83 | 62.10 | 76.19 |
| SmartFog + AES | Combined | 0.382 | 93.01 | 60.37 | 93.85 |
| SmartFog + GS3 | Combined | 0.296 | 89.59 | 55.84 | 92.06 |
| Method | Operation | ||||
|---|---|---|---|---|---|
| GS3 | Decipher | 0.011 | – | – | – |
| Cipher | 0.001 | – | – | – | |
| AES | Decipher | 0.025 | – | – | – |
| Cipher | 0.002 | – | – | – | |
| SmartFog | Inference | 0.196 | 64.8 | 21.31 | 92.44 |
| SmartFog + AES | Combined | 0.229 | 70.95 | 9.73 | 92.78 |
| SmartFog + GS3 | Combined | 0.213 | 68.14 | 9.11 | 91.96 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alcaraz-Velasco, F.; Palomares, J.M.; León-García, F.; Olivares, J. Secure Data Transmission Using GS3 in an Armed Surveillance System. Information 2025, 16, 527. https://doi.org/10.3390/info16070527
Alcaraz-Velasco F, Palomares JM, León-García F, Olivares J. Secure Data Transmission Using GS3 in an Armed Surveillance System. Information. 2025; 16(7):527. https://doi.org/10.3390/info16070527
Chicago/Turabian StyleAlcaraz-Velasco, Francisco, José M. Palomares, Fernando León-García, and Joaquín Olivares. 2025. "Secure Data Transmission Using GS3 in an Armed Surveillance System" Information 16, no. 7: 527. https://doi.org/10.3390/info16070527
APA StyleAlcaraz-Velasco, F., Palomares, J. M., León-García, F., & Olivares, J. (2025). Secure Data Transmission Using GS3 in an Armed Surveillance System. Information, 16(7), 527. https://doi.org/10.3390/info16070527








