Global Navigation Satellite System Spoofing Attack Detection Using Receiver Independent Exchange Format Data and Long Short-Term Memory Algorithm
Abstract
1. Introduction
- Global Navigation Satellite Systems (GNSS);
- Regional Navigation Satellite Systems (RNSS);
- Satellite-Based Augmentation Systems (SBAS).
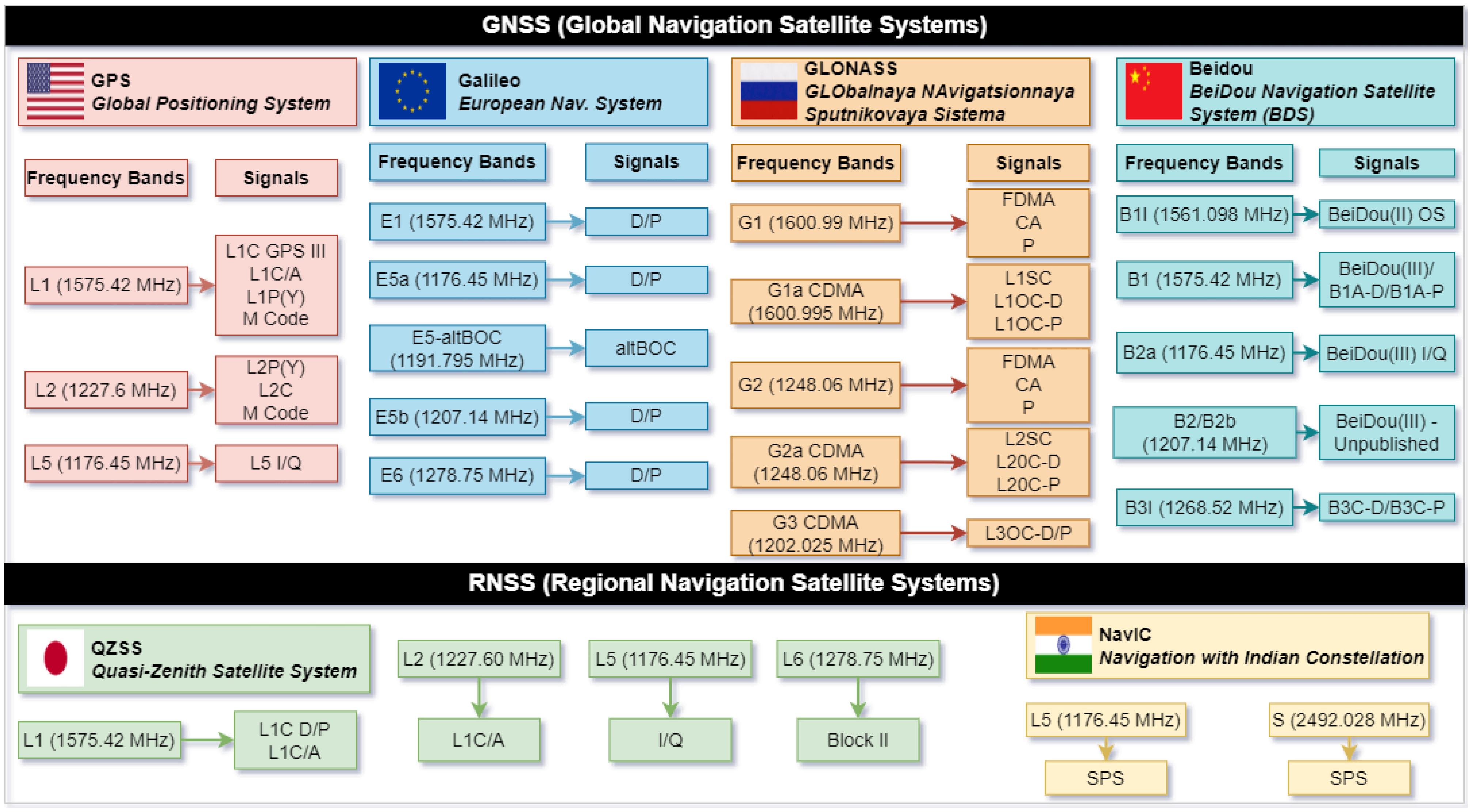
- GPS: The Global Positioning System (the current name of the Navstar system) is the system owned by the United States of America that became operational in 1995. The system comprises satellites located in the Medium Earth Orbit (MEO) and provides very accurate navigation and synchronization data [5,6].
- Galileo: This is the fully operational European navigation system that emerged at the initiative of the European Space Agency (ESA). The system has a recent history and is in continuous development. It became fully operational in 2016 and is composed of satellites placed in MEO [9].
- GLONASS: The GLObalnaya NAvigatsionnaya Sputnikovaya Sistema is the system owned by the Russian Federation that became fully operational in 1995 and is composed of satellites in MEO [10].
- NavIC/IRNSS: Navigation with Indian Constellation is the system owned by India and is composed of eight satellites with IGSO and GEO orbits [11].
- Space segment: Consists of the navigation satellites that orbit the Earth and transmit signals to users.
- Control segment: Includes monitoring and control ground stations that ensure the integrity and accuracy of the satellites.
- User segment: Includes all devices that have a built-in navigation sensor, such as smartphones, airplanes, and so on, which process the signals to determine location.
- Most civilian navigation signals are broadcast in an unencrypted format, making them vulnerable to signal manipulation. This claim is supported by several recent studies [20,21,22] in which the authors experimented with various techniques and methods for manipulating unencrypted civilian signals. Unlike military signals, which use encryption and authentication mechanisms, civilian receivers cannot distinguish between legitimate and spoofed navigation signals.
- Navigation signals come from high altitudes and reach receivers at very low power levels (typically around −130 dBm) [20]. This makes them susceptible to interference and jamming by false signals, which can be transmitted at higher power from terrestrial sources.
- Many GNSS receivers still operate on single-frequency signals (e.g., GPS L1 only), which makes them more vulnerable to spoofing [23]. Multi-frequency receivers using L1, L2, and L5 signals can improve resilience by cross-checking signals from different bands, but such protection is not yet widespread.
- The development of a real-world data acquisition and storage pipeline for collecting high-resolution GNSS observation data, including both normal and spoofed signal traces, organized according to the RINEX standard.
- The integration of LSTM learning strategies over multiple observation codes per satellite signal, enhancing anomaly detection performance and improving resilience to spoofing variations.
- Validation of the method using real spoofed signals, achieving precision between 87.00% and 97.50% and recall between 75.35% and 79.2%, depending on the satellite and observation code, thereby demonstrating the method’s practical efficacy.
2. RINEX Standard
- RINEX 2.x (1993–present): Originally developed to store GPS observations, this version was later extended to support GLONASS and Galileo. It introduced a simplified text-based structure, making it widely used for post-processing applications. Despite newer versions, RINEX 2.11 remains widely used, especially in legacy applications and receivers that do not support newer GNSS constellations.
- RINEX 3.x (2009–present): This version significantly improved multi-GNSS compatibility, allowing integration of GPS, GLONASS, Galileo, BeiDou, QZSS, SBAS, and IRNSS/NavIC data. It introduced additional observation types, including modernized GNSS signals such as GPS L5 and Galileo E5a/E5b. The latest revision, RINEX 3.05, addressed updates for new BeiDou and Galileo signals.
- RINEX 4.0 (2021–present): The latest version, RINEX 4.0, provides improved handling of high-rate data, extended support for new GNSS signals, and better integration with real-time processing workflows. This version was developed to improve efficiency in high accuracy applications such as Precise Point Positioning (PPP) and Real-Time Kinematic (RTK) positioning.
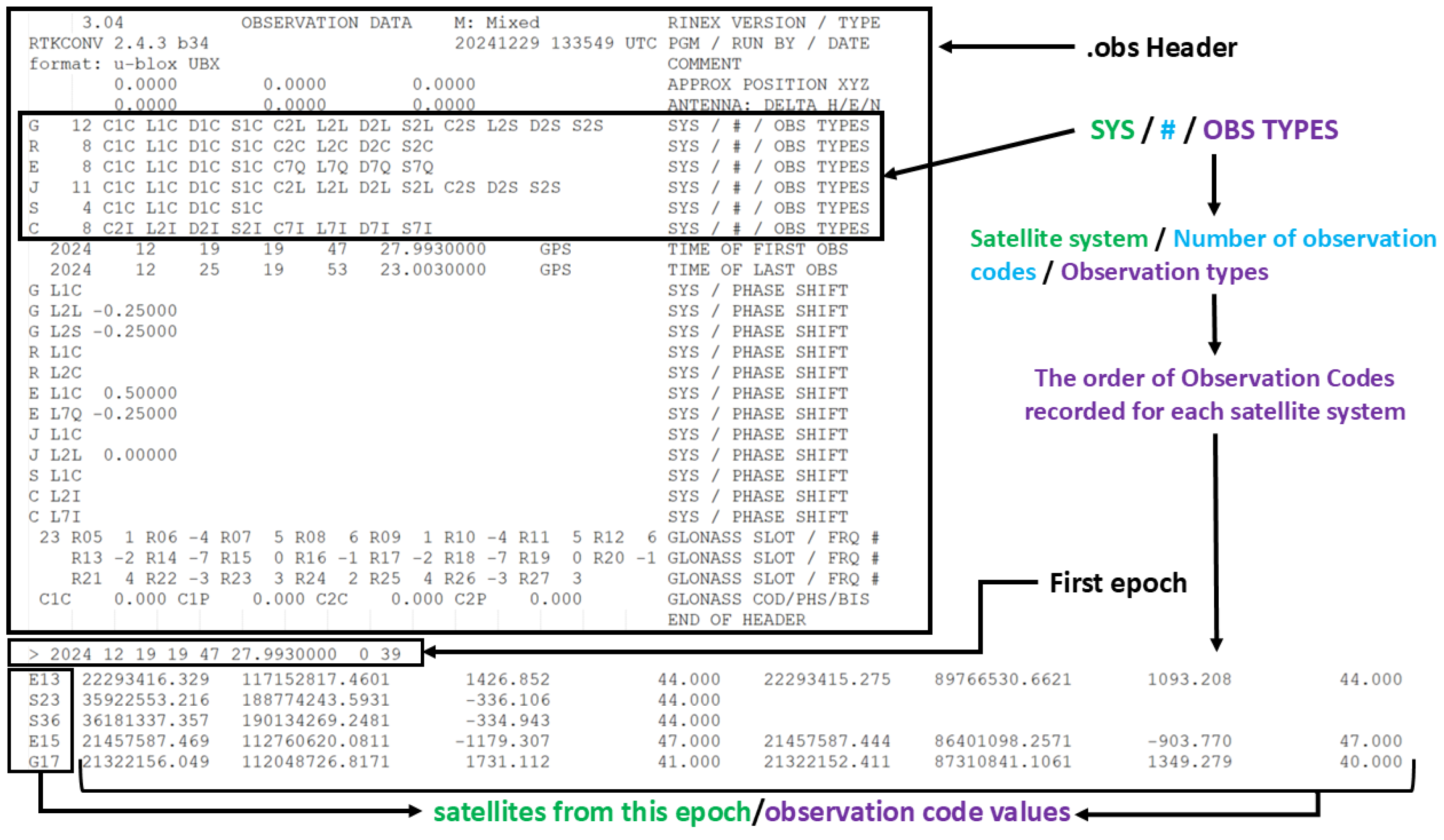
- Observation files (.obs extension): Contain raw GNSS observations, including Pseudorange, Carrier Phase, Doppler Shift, and Signal Strength.
- Navigation files (.nav extension): Store satellite ephemerides data necessary for computing positions.
- Meteorological files (.met extension): Include atmospheric data such as temperature, pressure, and humidity, which affect GNSS signal propagation.
- Pseudorange Codes (Cxx): Denoted by C and followed by the band number and channel attribute, the parameter represents the measured distance between the receiver antenna and the satellite antenna, incorporating clock offsets and from both the receiver and satellite, as well as additional biases β such as atmospheric and propagation delays [32]. The parameter is expressed in meters and its calculation will take into account the speed of light. Based on these, the parameter can be expressed by the following relation:
- Carrier Phase (Lxx): Denoted by L and followed by the band number and channel attribute, refers to the measurement of the accumulated phase of the carrier signal transmitted by a satellite, as received by a GNSS receiver.
- Doppler Shift (Dxx): Denoted by D and followed by the band number and channel attribute, refers to the measurement of the frequency shift in the received satellite signal and transmitted satellite signal caused by the relative motion between the satellite and the receiver [33].
- Signal Strength (Sxx): Denoted by S and followed by the band number and channel attribute, refers to a measure of the power or quality of the received satellite signal at the receiver’s antenna [34]. In RINEX observation files, it is typically represented as Carrier-to-Noise Density Ratio (C/N0) values, which indicate the ratio of the received signal power to the background noise level.
3. Literature Overview
4. Training and Testing Scenarios
4.1. Training Scenario and System Configurations
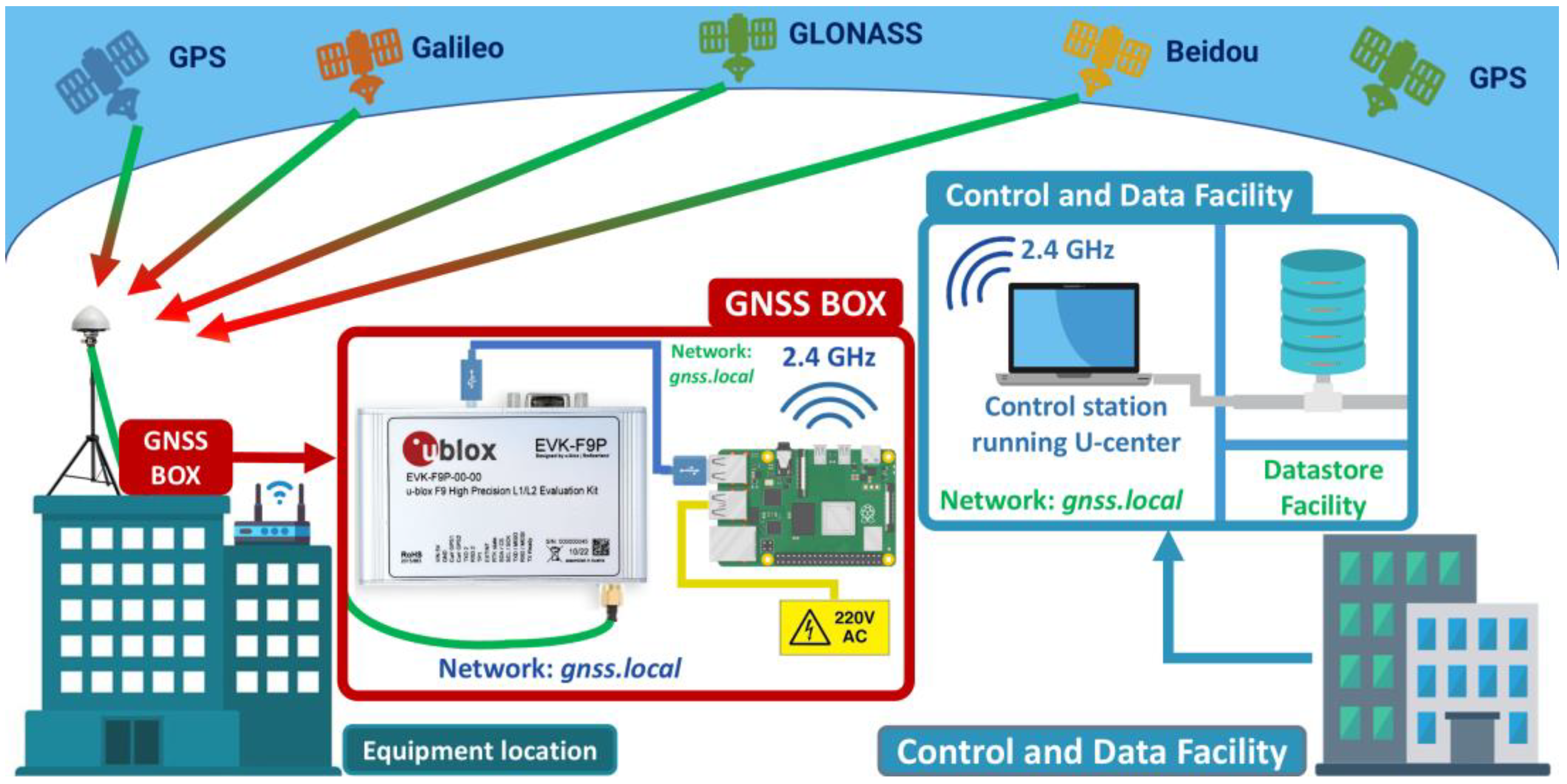
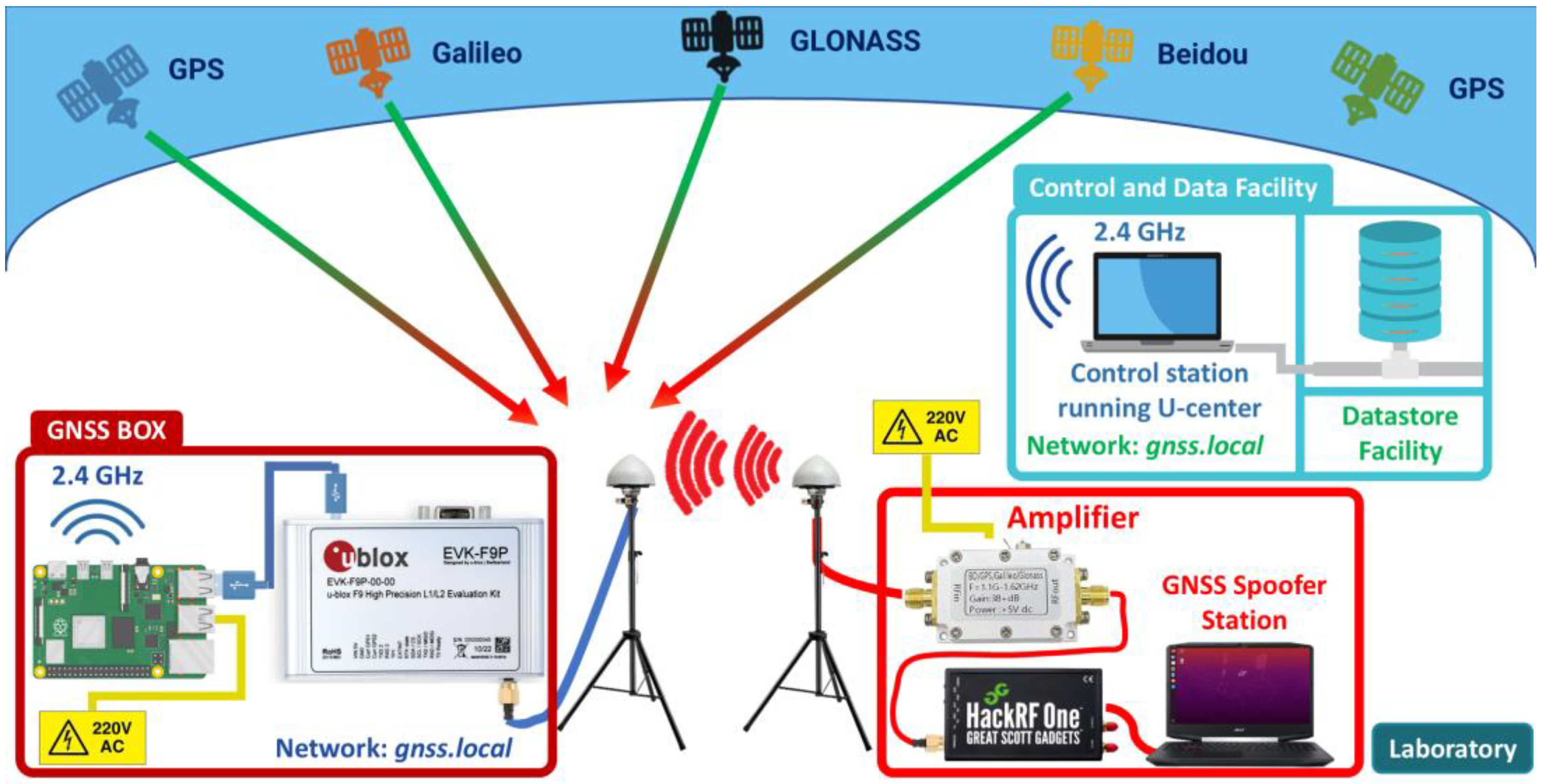
4.1.1. Training Scenario Topology
4.1.2. System Configurations for Training Scenario
- Libraries and dependencies installation: The libraries required to interact with the EVK-F9P sensor are gpsd, gpsd-clients, python3-gps, and ser2net. The gpsd daemon is used to manage the data received from the GNSS sensor and the gpsd-clients, python3-gps libraries are needed to interpret the navigation messages. The ser2net utility is required to establish TCP/UDP connections to the port assigned to the GNSS sensor by the Raspberry Pi operating system.sudo apt-get install gpsd gpsd-clients python3-gps ser2net
- Configuring GNSS sensor remote data transfer:
- GNSS sensor assigned port query: To perform remote data transfer, it is necessary to query the port assigned by the operating system. The port allocated to the GNSS sensor by the operating system will be a teletype (tty) port, usually ttyACM0 port.sudo ls/dev/tty*
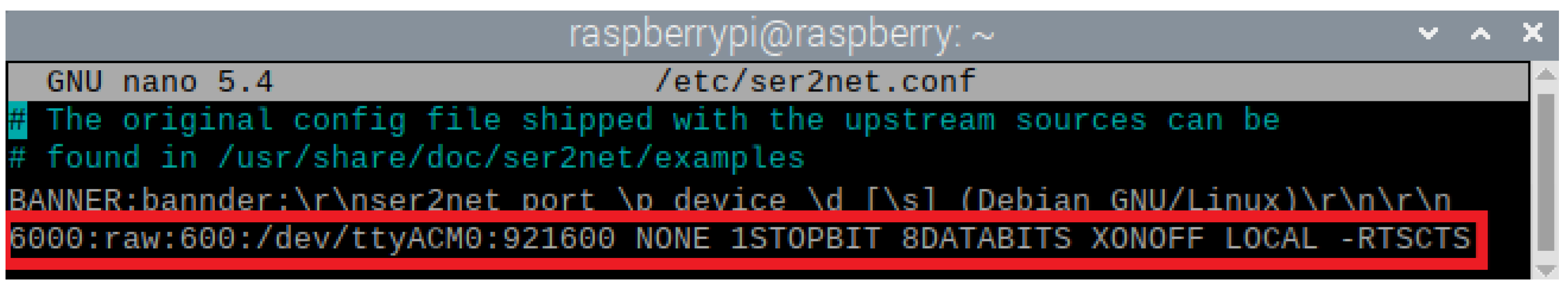
- Ser2net configuration: The tty port must be set in the ser2net config file, through which a TCP connection on port 6000 at a 921,600 bitrate will be established. Figure 4 shows the ser2net configuration file, as well as the command used to configure the TCP connection to the teletype port ACM0.
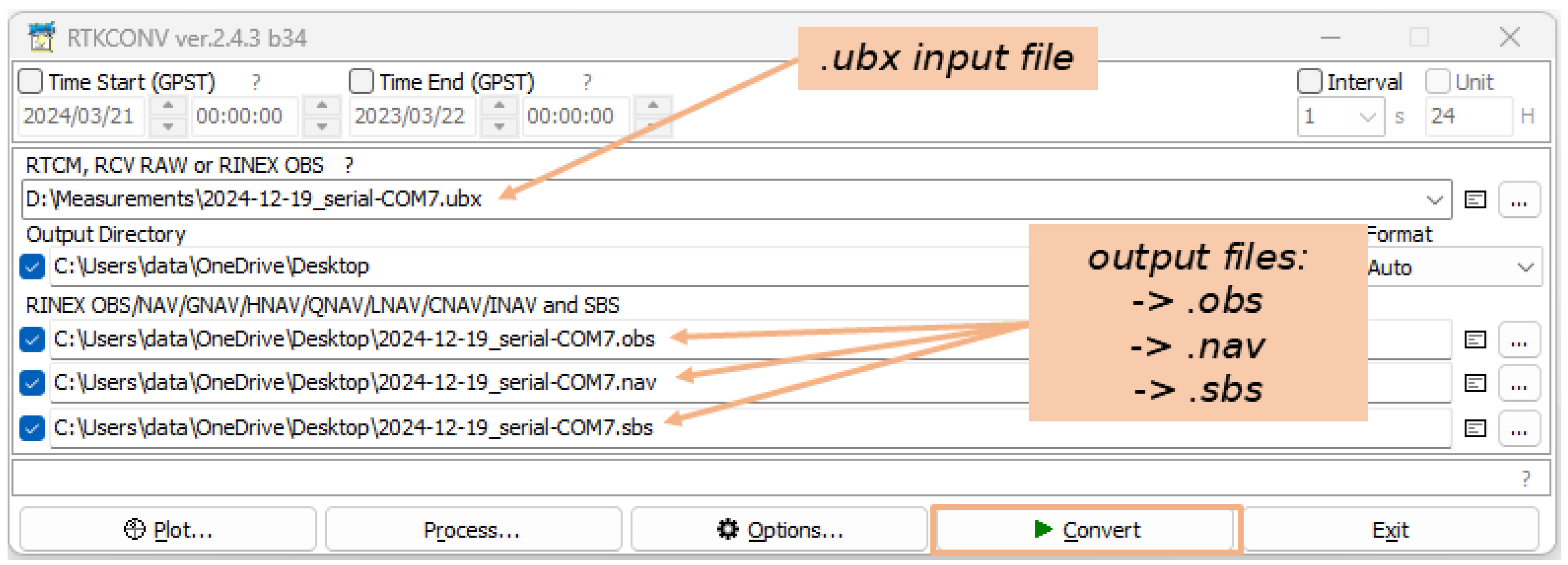
4.1.3. Training Data Processing
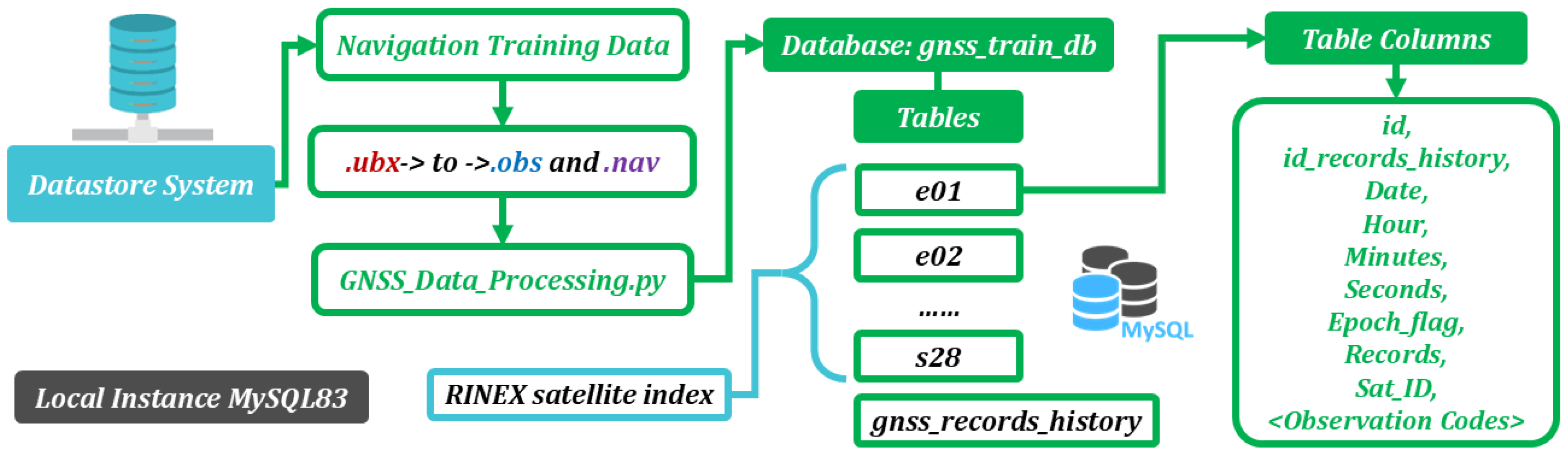
| Algorithm 1. GNSS Data Processing |
| 1: DATABASE Open Connection |
| 2: OPEN .obs file |
| 3: READ .obs file Header to get <Observation Codes> |
| 4: for line in file.lines |
| 5: if line.startwith(‘>’) |
| 6: EXTRACT Epoch_info = [Date, Hour, Minutes, Seconds, Epoch_flag, Records] |
| 7: else |
| 8: EXTRACT Sat_ID, <Observation Codes Values> |
| 9: if Sat_ID.table.exists == False |
| 10: CREATE Sat_ID.table with columns [Epoch_info, <Observation Codes>] |
| 11: STORE [Epoch_info, <Observation Codes Values>] in Sat_ID.table |
| 12: end for |
| 13: DATABASE Close Connection |
4.2. Testing Scenario and System Configurations
4.2.1. Testing Scenario Topology
4.2.2. System Configurations for Testing Scenario
- HackRF One installation: The device is an SDR solution that allows transmission and reception of radio signals over a wide frequency range (1–6 GHz). To use HackRF One for GNSS spoofing, it requires proper driver installation and firmware updates.sudo apt-get install hackrf
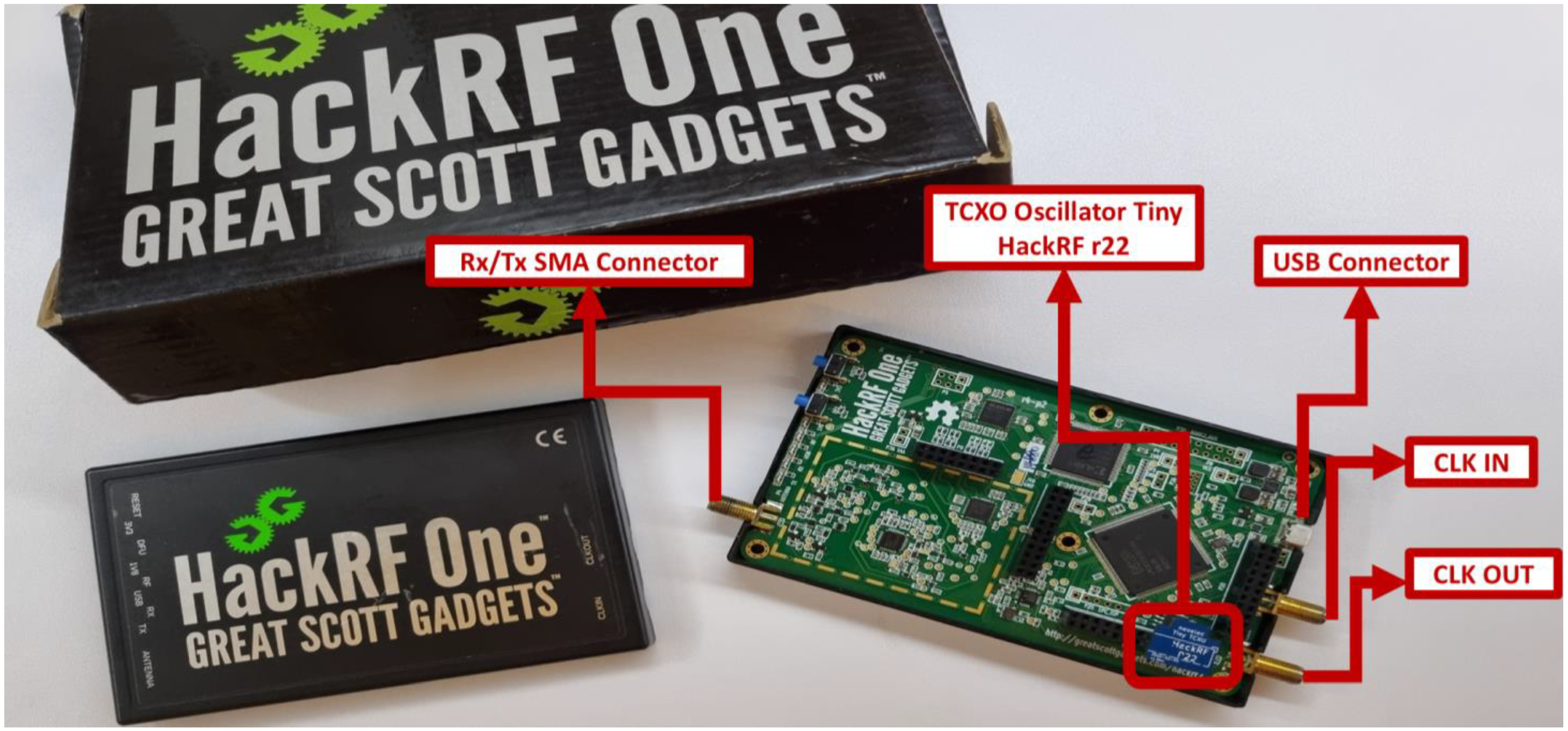
- TCXO installation: It is recommended that the GNSS signal transmission using HackRF be performed with the aid of a frequency stabilizer to ensure signal accuracy. This can be achieved by using a Temperature Compensated Crystal Oscillator (TCXO), which minimizes frequency drift caused by temperature variations and ensures a more precise and stable signal [49]. The oscillator used is a Nooeiec model and was inserted into the port P22 on the board, as shown in Figure 10. Once the oscillator is inserted, we need to check that the TCXO is recognized by the device. If the following command output is [0] = 0 × 51, then the oscillator is not recognized and if the output is [0] − 0 × 01, then the oscillator is successfully recognized.hackrf_debug-–si5351c-n 0-r
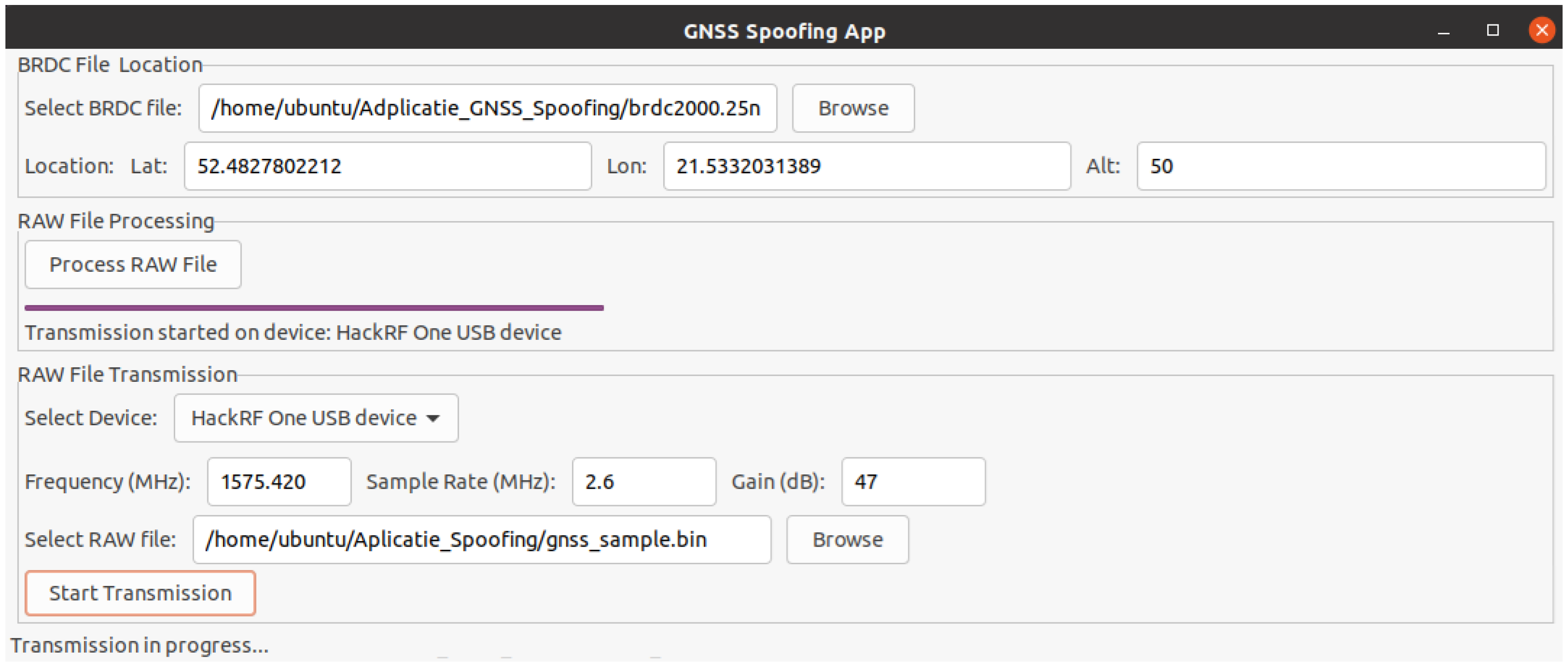
- GNSS Spoofing Application development: The application that will perform the generation of the false navigation signal sample was developed using the Python programming language and open-source libraries. Next, the application will perform the following operations:
- Signal sample generation: Acquiring a navigation signal sample can be accomplished by several methods. The first method is to record the navigation signals and output them at a later date. The second method is to generate the signal using its specific data and technical parameters. In our scenario, the second method was used in the development of the application due to the fact that it allows greater control over the navigation data. In the following, for signal sample generation, we used the structure and technical specifications of GPS signals in the L1 band, as this is one of the main bands used in navigation. Generating a navigation signal sample for a specific system involves the use of its ephemeride files. These files contain precise orbital and clock data of the satellites, allowing accurate reconstruction of satellite positions and navigation data [50]. For the GPS constellation, ephemeride files can be obtained online from the Crustal Dynamics Data Information System (CDDIS). In our scenario, we have used the ephemerides file corresponding to 21 January 2025, i.e., the file brdc2000.25n. Next, the process of generating signal samples using the chosen ephemerides file is realized using a series of libraries developed by Takuji Ebinuma and his collaborators from the gps-sdr-sim project, available on the GitHub platform. These libraries are getopt.c, getopt.h, gpssim.c, gpssim.h, gpssim.o, which we have integrated in our application. These libraries will help to extract the satellites from the ephemerides file corresponding to a given location (latitude, longitude, and altitude) and to generate the raw navigation data file.
- Signal sample transmission: After generating the raw navigation data file, its transmission will be realized using the hackrf_transfer.c module from the installed hackrf library. This module allows us to set the transmission frequency, sample rate, gain, and many other options at which the signal sample will be transmitted. Figure 11 shows the interface of the application built using Python version 3.13 that will realize the signal sample generation and transmission.
4.2.3. Testing Data Processing
5. Results and Discussion
5.1. LSTM Architecture and Training Results
5.1.1. LSTM Training Architecture
| Algorithm 2. LSTM Training from DB |
| 1: DATABASE Open Connection (gnss_train_db) |
| 2: GET list of tables (satellites), excluding gnss_records_history table |
| 3: for table in tables.gnss_train_db |
| 4: LOAD data.table into Pandas DataFrame |
| 5: GET timestamp = [Date, Hour, Minutes, Seconds] |
| 6: CONVERT into a DateTime column |
| 7: GET set of <Observation Codes> for each satellite signal |
| 8: for each set of <Observation Codes> |
| 9: LOAD Observation_Code.values |
| 10: CLEAN Observation_Code.values for NaNs |
| 11: NORMALIZE StandardScaler(<Observation_Code.values>) |
| 12: SPLIT data into 80% training and 20% validation |
| 13: BUILD LSTM model |
| 14: Input: n_features = 4 |
| 15: Encoder: LSTM(64) -> Dropout(0.2) -> LSTM(32) |
| 16: Bottleneck: RepeatVector(16) |
| 17: Decoder: LSTM(32) -> Dropout(0.2) -> LSTM(64) |
| 18: Output: TimeDistributed(Dense(4)) |
| 19: Compile: Adam Optimizer and MSE Loss Function |
| 20: TRAIN LSTM model |
| 21: Fit Model: Early Stopping—Monitoring Validation Loss |
| 22: SAVE trained model (Keras format) |
| 23: end for |
| 24: end for |
| 25: DATABASE Close Connection |
5.1.2. LSTM Training Data
5.1.3. LSTM Training Performances
5.2. LSTM Architecture and Testing Results
5.2.1. LSTM Testing Architecture
| Algorithm 3. LSTM Training from DB |
| 1: DATABASE Open Connection (gnss_test_db) |
| 2: GET list of tables (satellites), excluding gnss_records_history table |
| 3: for table in tables.gnss_test_db |
| 4: LOAD data.table into Pandas DataFrame |
| 5: GET timestamp = [Date, Hour, Minutes, Seconds] |
| 6: CONVERT into a DateTime column |
| 7: GET set of <Observation Codes> |
| 8: for each set of <Observation Codes> |
| 9: LOAD Observation_Code.values |
| 10: CLEAN Observation_Code.values for NaNs |
| 11: NORMALIZE StandardScaler(Observation_Code.values) |
| 12: LOAD Satellite_Signal_Model = Satellite_Signal_LSTM_Model.keras |
| 13: RECONSTRUCT Observation_Code = Satellite_Signal_Model.predict |
| 14: RECONSTRUCT ERROR: absolute mean of differences (original/reconstruct) |
| 15: THRESHOLD: thr |
| 16: ANOMALY DETECTION: detect values exceeding threshold |
| 17: VALIDATE ANOMALIES values in timestamp for each observation codes |
| 18: PLOT RESULTS |
| 19: end for |
| 20: end for |
| 21: DATABASE Close Connection |
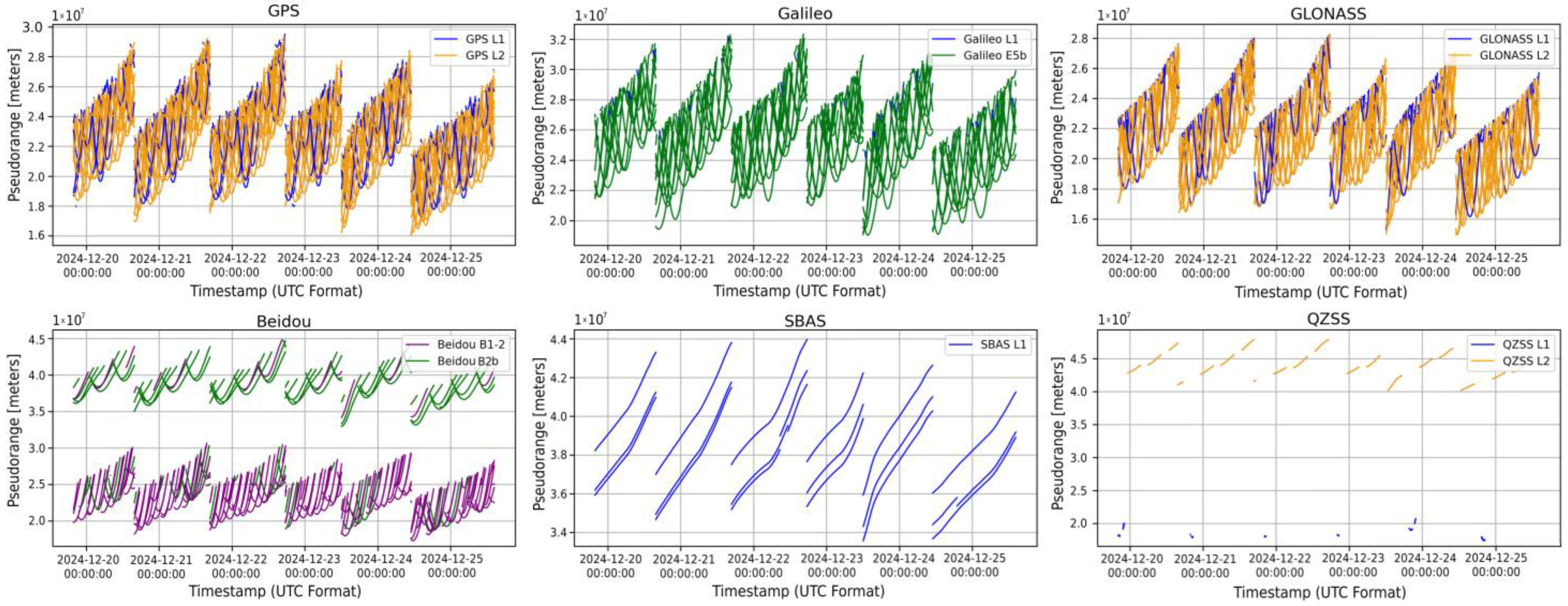
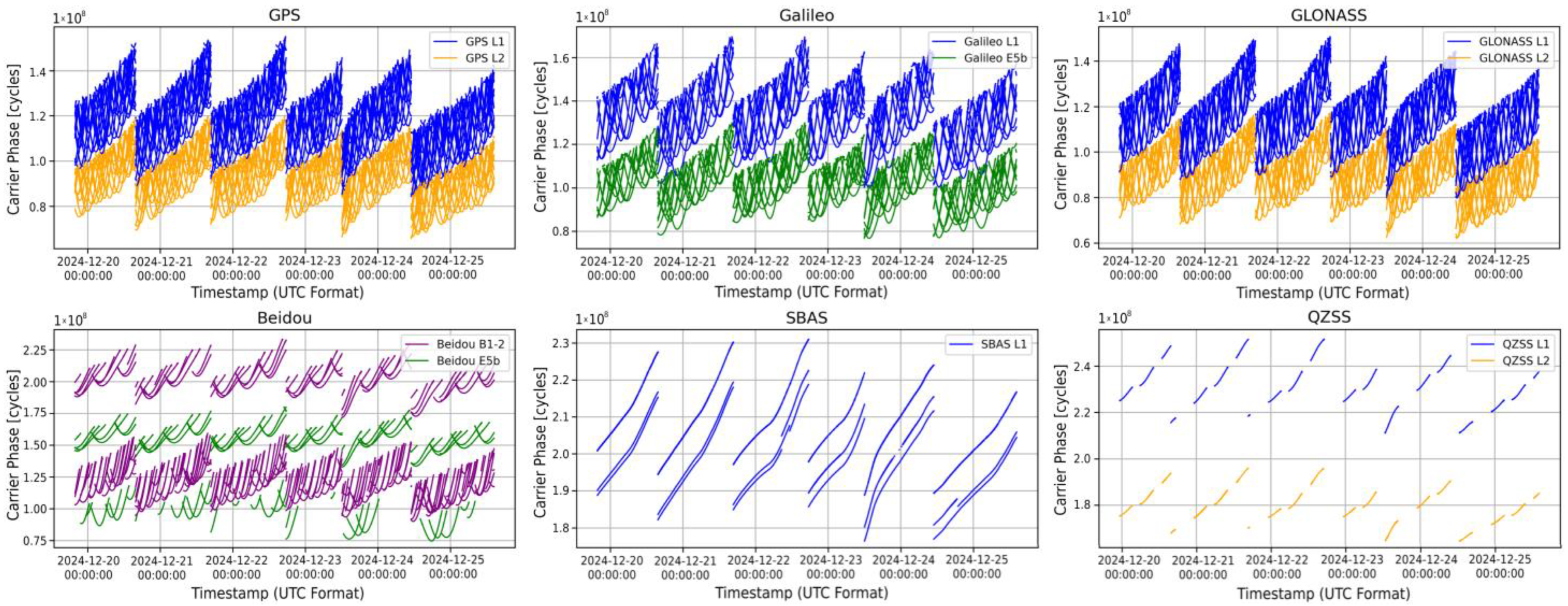
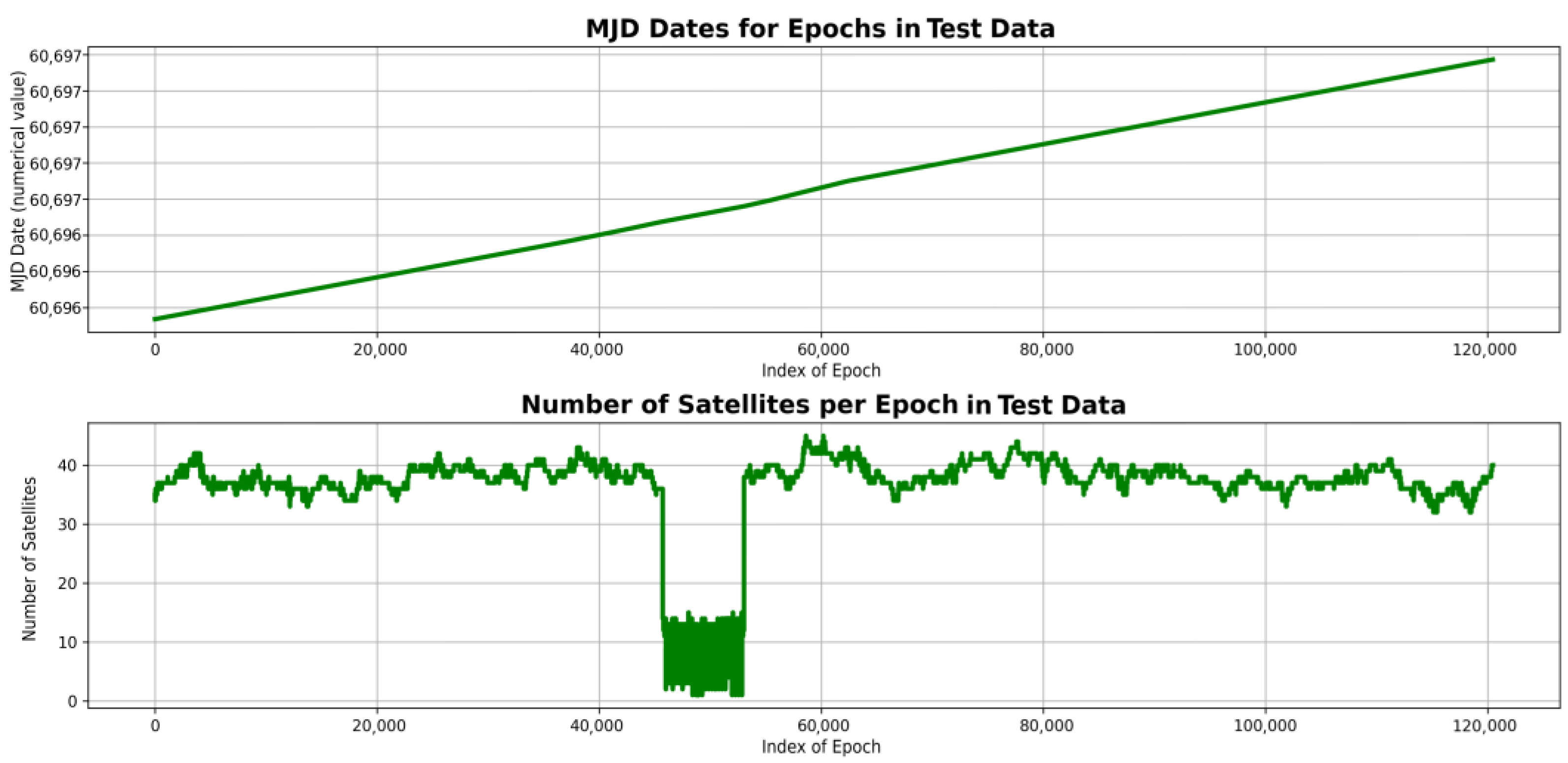
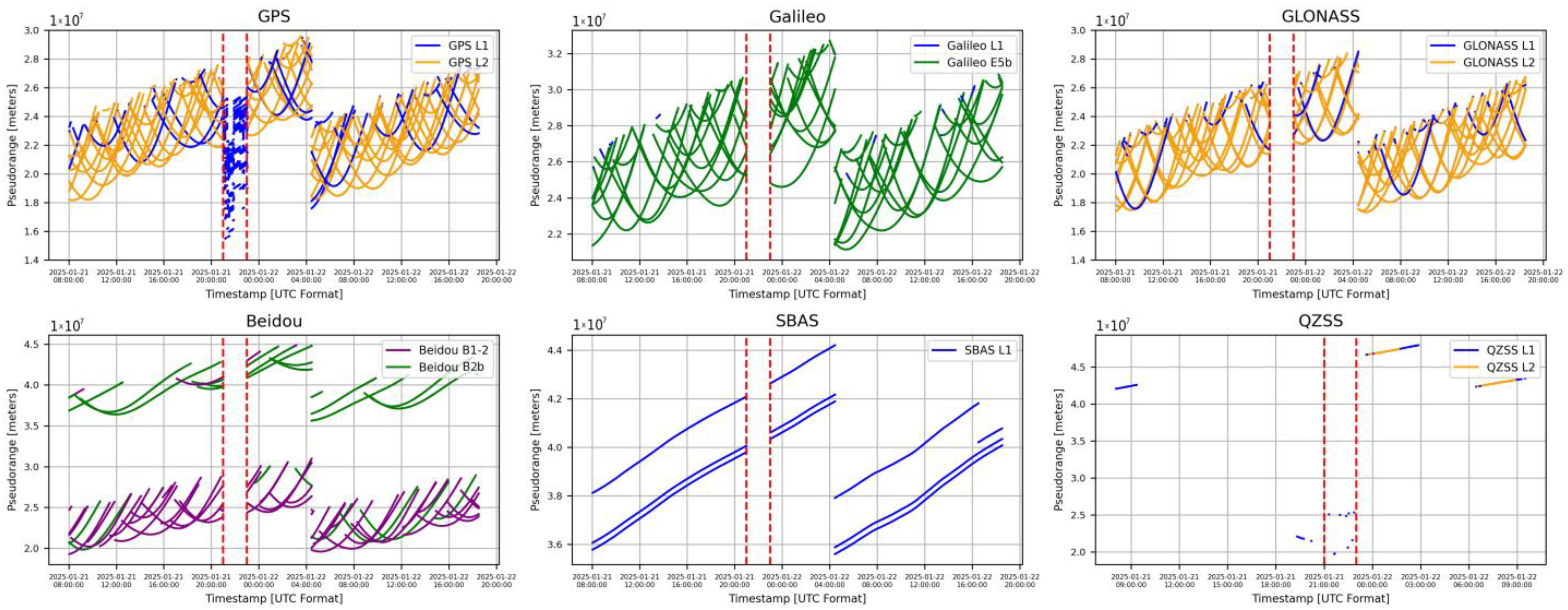
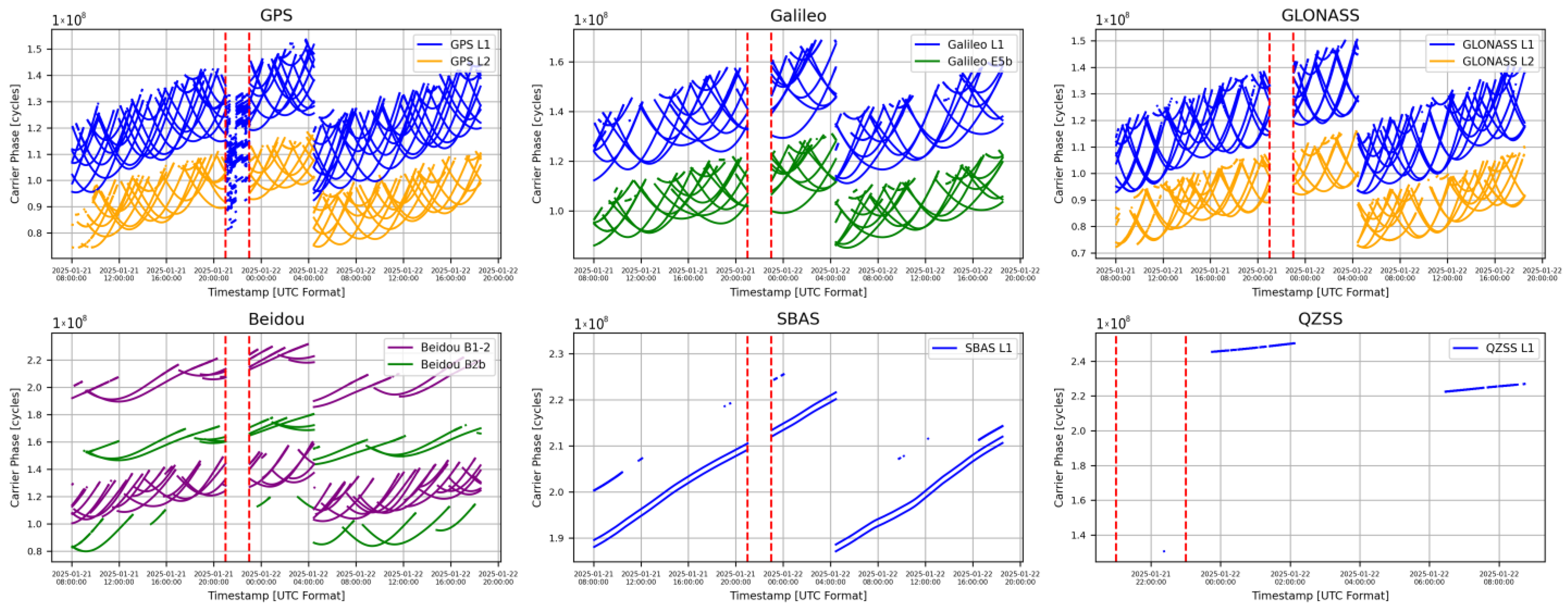
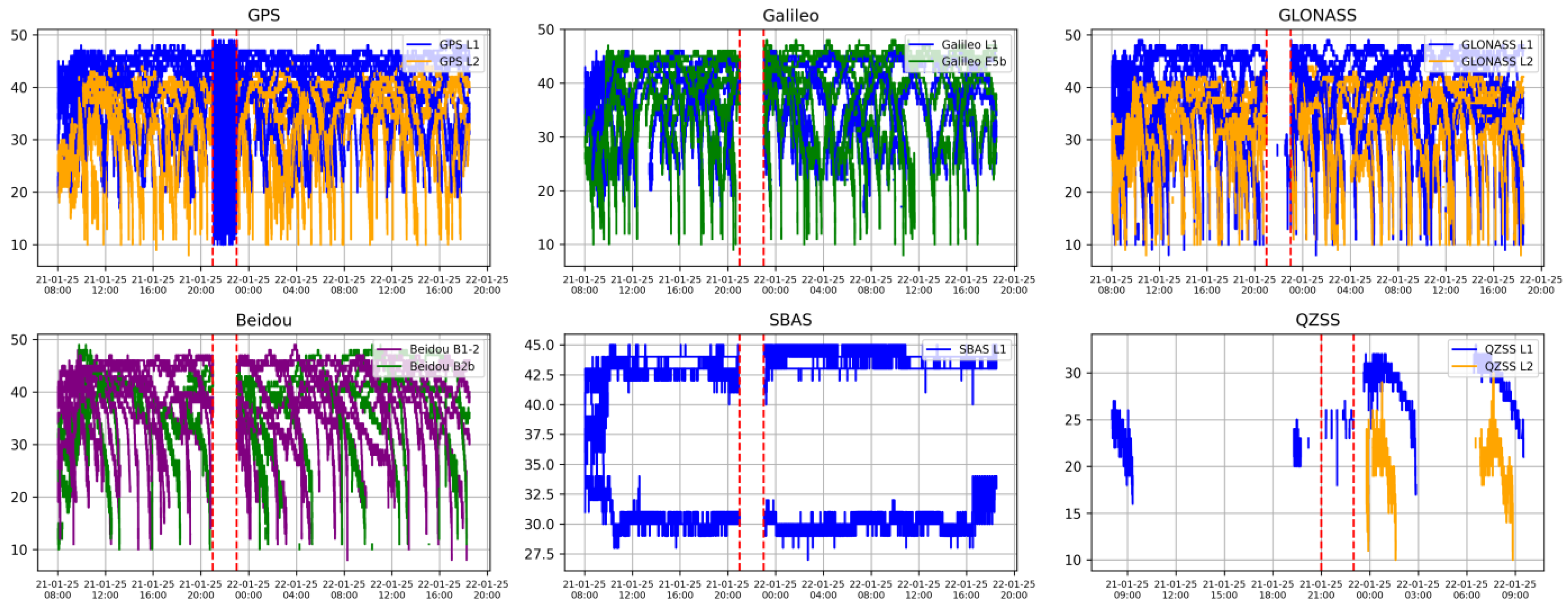
5.2.2. LSTM Testing Data
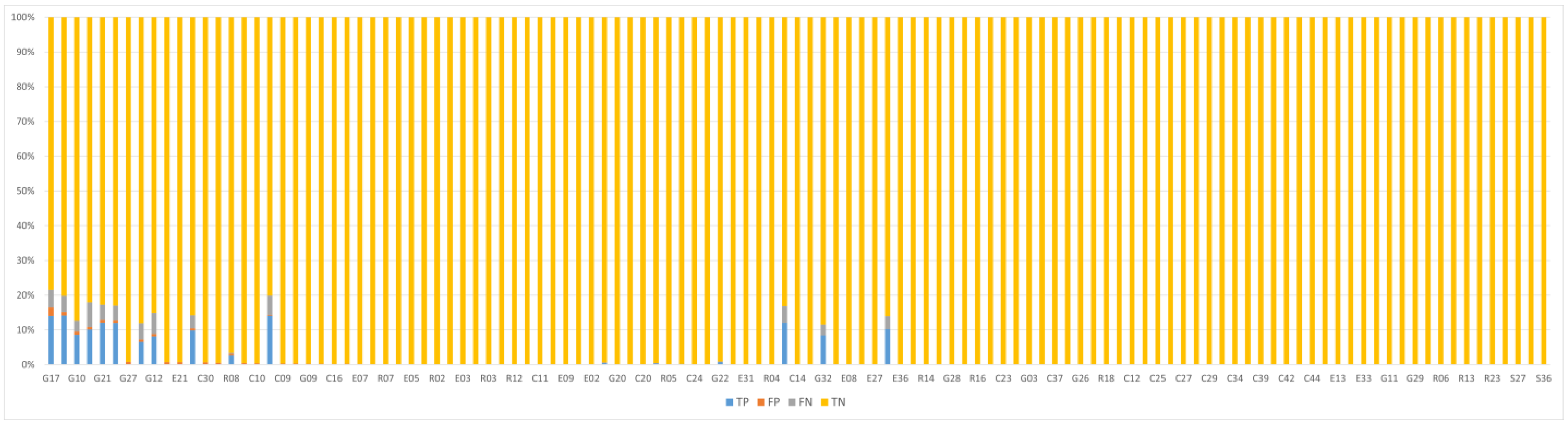
5.2.3. LSTM Testing Performances
- True Positive (TP): The number of data points correctly identified as anomalies, i.e., points that truly belong to the attack interval and are correctly detected by the model.
- True Negative (TN): The number of data points correctly identified as normal, i.e., points that are outside the attack interval and are not falsely marked as anomalous.
- False Positive (FP): The number of data points incorrectly identified as anomalies, i.e., normal points that were mistakenly flagged as anomalous.
- False Negative (FN): The number of data points incorrectly identified as normal, i.e., points within the attack interval that the model failed to detect as anomalies.
- Precision: The proportion of predicted anomalies that are actually true anomalies:
- Recall (or True Positive Rate): Measures the model’s ability to correctly detect actual anomalies. It represents the proportion of true anomalies that were successfully identified:
- F1-score: Represents the harmonic mean between precision and recall. It balances the trade-off between false positives and false negatives:
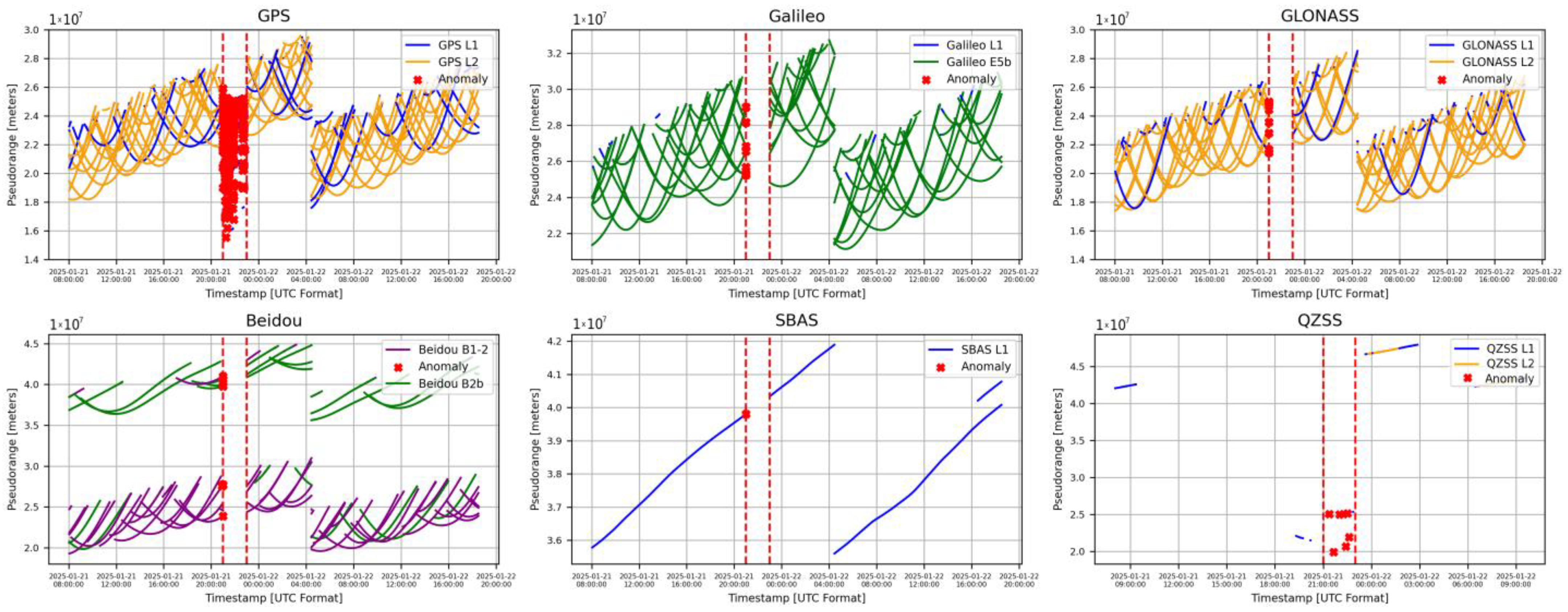
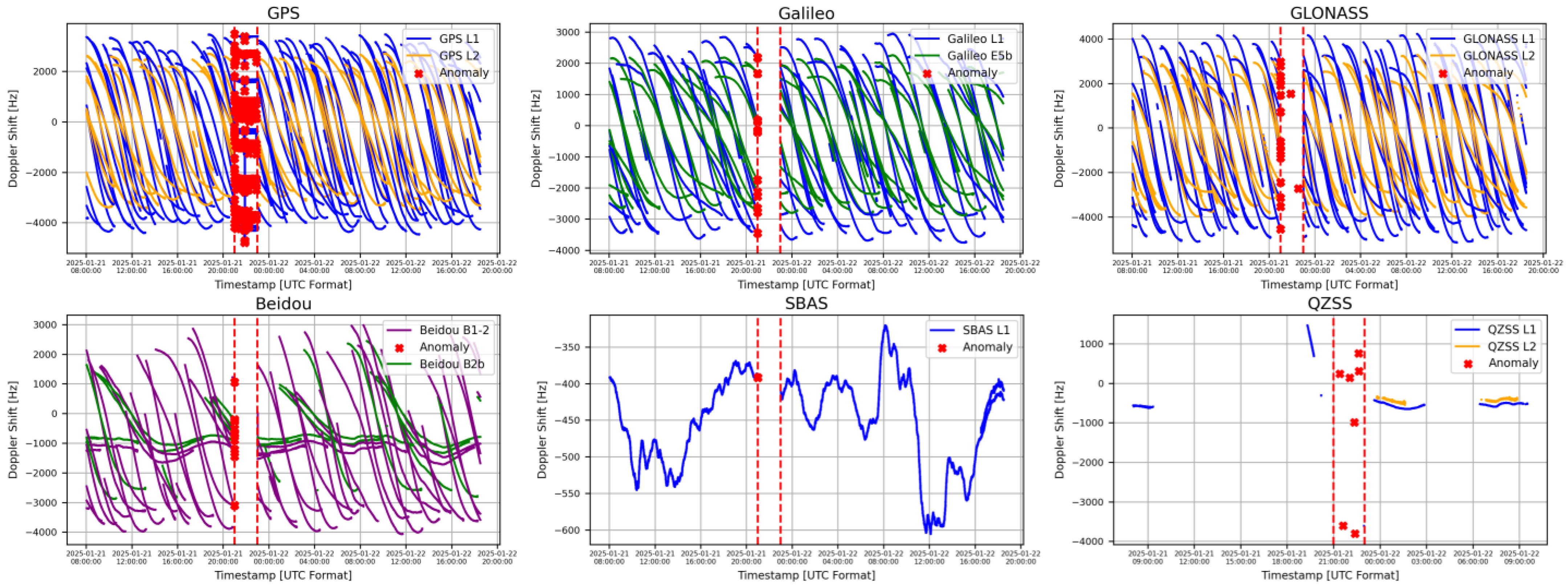
5.2.4. LSTM Attack Detection
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Yasyukevich, Y.V.; Zhang, B.; Devanaboyina, V.R. Advances in GNSS Positioning and GNSS Remote Sensing. Sensors 2024, 24, 1200. [Google Scholar] [CrossRef]
- Teunissen, P.J.G.; Montenbruck, O. Springer Handbook of Global Navigation Satellite Systems; Springer: Cham, Switzerland, 2017. [Google Scholar]
- Gao, J. A Brief Discussion on Understanding GNSS and Navigation Engineering. Acad. J. Sci. Technol. 2024, 11, 248–249. [Google Scholar]
- Zalewski, P.; Bąk, A.; Bergmann, M. Evolution of Maritime GNSS and RNSS Performance Standards. Remote Sens. 2022, 14, 5291. [Google Scholar] [CrossRef]
- John, W.B. The Navstar Global Positioning System. In Position, Navigation, and Timing Technologies in the 21st Century: Integrated Satellite Navigation, Sensor Systems, and Civil Applications; IEEE: New York, NY, USA, 2021; pp. 65–85. [Google Scholar]
- Pinninti, K.; Veligatla, S.B.; Gireddy, A.K.R. Extraction of Satellite Data and Generation of C/A Codes for GPS Signals on FPGA. In Proceedings of the 2024 International Conference on Integrated Circuits and Communication Systems (ICICACS), Raichur, India, 23–24 February 2024; pp. 1–4. [Google Scholar]
- Xia, F.; Wang, C.; Chen, D.; Wu, J.; Ye, S.; Sun, W. Estimation of antenna phase center offsets for BeiDou IGSO and MEO satellites. GPS Solut. 2020, 24, 90. [Google Scholar]
- Lu, J.; Guo, X.; Su, C. Global capabilities of BeiDou Navigation Satellite System. Satell. Navig. 2020, 1, 27. [Google Scholar] [CrossRef]
- Andrei, C.-O.; Johansson, J.; Koivula, H.; Poutanen, M. Signal performance analysis of the latest quartet of Galileo satellites during the first operational year. In Proceedings of the 2020 International Conference on Localization and GNSS (ICL-GNSS), Tampere, Finland, 2–4 June 2020; pp. 1–6. [Google Scholar]
- Jiao, F.; Yu, X.; Hu, Y. Performance of GNSS space service for geostationary autonomous operations. J. Navig. 2024, 77, 257–275. [Google Scholar] [CrossRef]
- Pan, L.; Pei, G.; Yu, W.; Zhang, Z. Assessment of IRNSS-Only Data Processing: Availability, Single-Frequency SPP and Short-Baseline RTK. Remote Sens. 2022, 14, 2462. [Google Scholar]
- Karasawa, K.; Takizawa, Y.; Sasaki, Y.; Hirota, Y.; Ashida, K.; Karakama, T.; Kaneko, T. Satellite Positioning System with Active Antenna for QZSS. In Proceedings of the 2021 IEEE 10th Global Conference on Consumer Electronics (GCCE), Kyoto, Japan, 12–15 October 2021; pp. 65–68. [Google Scholar]
- Gu, H.; Rao, Y.; Zou, D.; Shi, H.; Guo, Y. Analysis of Multipath Characteristics of Quasi-Zenith Satellite System L5 Frequency Point. Remote Sens. 2025, 17, 889. [Google Scholar]
- Lim, C.; Park, B.; Yun, Y. L1 SFMC SBAS Message for Service Expansion of Multi-Constellation GNSS Support. IEEE Access 2023, 11, 81690–81710. [Google Scholar] [CrossRef]
- GPS Space Segment. Available online: https://www.gps.gov/systems/gps/space/ (accessed on 19 February 2025).
- Galileo Space Segment. Available online: https://www.gsc-europa.eu/galileo/system/ (accessed on 19 February 2025).
- GLONASS Space Segment. Available online: https://glonass-iac.ru/en/about_glonass/ (accessed on 19 February 2025).
- Beidou Space Segment. Available online: https://gssc.esa.int/navipedia/index.php/BeiDou_Space_Segment (accessed on 19 February 2025).
- Maciejewska, A.; Maciuk, K. Research using GNSS (Global Navigation Satellite System) products—A comprehensive literature review. J. Appl. Geod. 2025. [Google Scholar] [CrossRef]
- Meng, L.; Yang, L.; Yang, W.; Zhang, L. A Survey of GNSS Spoofing and Anti-Spoofing Technology. Remote Sens. 2022, 14, 4826. [Google Scholar] [CrossRef]
- Zhong, M.; Li, H.; Lu, M. Analysis and Validation of Distributed GNSS Spoofing Threat. Eng. Proc. 2025, 88, 42. [Google Scholar]
- Dasgupta, S.; Ahmed, A.; Rahman, M.; Bandi, T.N. Unveiling the Stealthy Threat: Analyzing Slow Drift GPS Spoofing Attacks for Autonomous Vehicles in Urban Environments and Enabling the Resilience. arXiv 2024, arXiv:2401.01394. [Google Scholar]
- Ma, X.; Han, C.; Jin, R.; Wang, D.; Bai, P.; Zhen, W. Study on GNSS Spoofing Interference Detection Method in Urban Multipath Environment Based on CNN and Clustering Model. In Proceedings of the 2023 Cross Strait Radio Science and Wireless Technology Conference (CSRSWTC), Guilin, China, 10–13 November 2023; Available online: https://ieeexplore.ieee.org/document/10427220 (accessed on 12 February 2025).
- Motallebighomi, M.; Sathaye, H.; Singh, M.; Ranganathan, A. Cryptography is not enough: Relay attacks on authenticated GNSS signals. arXiv 2022, arXiv:2204.11641. [Google Scholar]
- The Hindu Businessline. Report: “GPS Jamming Near Conflict Zones Affect Cargo Ships Transiting Mediterranean and the Black Sea” by Teraja Simhan. Available online: https://www.thehindubusinessline.com/news/world/gps-jamming-near-conflict-zones-affect-cargo-ships-transiting-mediterranean-and-the-black-sea/article68038995.ece (accessed on 12 February 2025).
- AIN. Report: “GPS Spoofing Incidents Increase in Middle East” by Kerry Lynch. Available online: https://www.ainonline.com/aviation-news/air-transport/2023-11-08/gps-spoofing-incidents-increase-middle-east (accessed on 12 February 2025).
- The Wall Street Journal. Report: “Electronic Warfare Spooks Airlines, Pilots and Air-Safety Officials”. Available online: https://ops.group/dashboard/wp-content/uploads/2024/09/GPS-Spoofing-Final-Report-OPSGROUP-WG-OG24.pdf (accessed on 12 February 2025).
- GPS WORLD. Report: “GNSS Spoofing Threatens Airline Safety, Alarming Pilots and Aviation Officials” by Jesse Khalil. Available online: https://www.gpsworld.com/gnss-spoofing-threatens-airline-safety-alarming-pilots-and-aviation-officials/ (accessed on 12 February 2025).
- Gao, Y.; Li, G. A Slowly Varying Spoofing Algorithm Avoiding Tightly-Coupled GNSS/IMU With Multiple Anti-Spoofing Techniques. IEEE Trans. Veh. Technol. 2022, 71, 8864–8876. [Google Scholar] [CrossRef]
- Kawamoto, S.; Takamatsu, N.; Abe, S. RINGO: A RINEX pre-processing software for multi-GNSS data. Earth Planets Space 2023, 75, 54. [Google Scholar] [CrossRef]
- Han, J.; Lee, S.J.; Yun, H.S.; Kim, K.B.; Bae, S. WPyRINEX: A new multi-purpose Python package for GNSS RINEX data. Peer J. Comput. Sci. 2024, 10, e1800. [Google Scholar]
- Medina, E.T.; Lohan, E.S. GNSS Spoofing Modeling and Consistency-Check-Based Spoofing Mitigation with Android Raw Data. Electronics 2025, 14, 898. [Google Scholar]
- Kabir, M.H.; Hasan, M.A.; Shin, W. A Precise Positioning Method with Integration of GNSS and Doppler Shift Based Positioning using LEO Satellite. In Proceedings of the 2023 14th International Conference on Information and Communication Technology Convergence (ICTC), Jeju Island, Republic of Korea, 11–14 October 2023; pp. 315–317. [Google Scholar]
- Ghizzo, E.; Pena, A.G.; Lesouple, J.; Milner, C.; Macabiau, C. Assessing GNSS Carrier-to-Noise-Density Ratio Estimation in The Presence of Meaconer Interference. In Proceedings of the ICASSP 2024—2024 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Seoul, Republic of Korea, 14–19 April 2024; pp. 8971–8975. [Google Scholar]
- Weikong, Q.; Zhang, Y.; Liu, X. A GNSS anti-spoofing technology based on Doppler shift in vehicle networking. In Proceedings of the 2016 International Wireless Communications and Mobile Computing Conference, Paphos, Cyprus, 5–9 September 2016; IEEE: New York, NY, USA, 2016; pp. 725–729. [Google Scholar]
- Yang, B.; Tian, M.; Ji, Y.; Cheng, J.; Xie, Z.; Shao, S. Research on GNSS Spoofing Mitigation Technology Based on Spoofing Correlation Peak Cancellation. IEEE Commun. Lett. 2022, 26, 3024–3028. [Google Scholar] [CrossRef]
- Jin, R.; Yan, J.; Cui, X.; Yang, H.; Zhen, W.; Gu, M.; Ji, G. A Spoofing Detection and Direction-Finding Approach for Global Navigation Satellite System Signals Using Off-the-Shelf Anti-Jamming Antennas. Remote Sens. 2025, 17, 864. [Google Scholar] [CrossRef]
- Galan, A.; O’Driscoll, C.; Fernandez-Hernandez, I.; Pollin, S. Sensitivity Analysis of Galileo OSNMA Cross-Authentication Sequences. Eng. Proc. 2025, 88, 12. [Google Scholar]
- Hammarberg, T.; García, J.M.V.; Alanko, J.N.; Bhuiyan, M.Z.H. An Experimental Performance Assessment of Galileo OSNMA. Sensors 2024, 24, 404. [Google Scholar] [CrossRef]
- Semanjski, S.; Semanjski, I.; De Wilde, W.; Muls, A. Use of Supervised Machine Learning for GNSS Signal Spoofing Detection with Validation on Real-World Meaconing and Spoofing Data—Part I. Sensors 2020, 20, 1171. [Google Scholar] [CrossRef] [PubMed]
- Pervysheva, Y.; Käppi, J.; Syrjärinne, J.; Nurmi, J.; Lohan, E.S. Multi-Receiver Ensemble Machine-Learning Techniques for GNSS Spoofing Detection with Generalisability Approach. In Proceedings of the 2024 32nd Telecommunications Forum (TELFOR), Belgrade, Serbia, 26–27 November 2024; pp. 1–4. [Google Scholar]
- Iqbal, A.; Aman, M.N.; Sikdar, B. A Deep Learning Based Induced GNSS Spoof Detection Framework. IEEE Trans. Mach. Learn. Commun. Netw. 2024, 2, 457–478. [Google Scholar]
- Park, H.; Jang, H. Enhancing Time Series Anomaly Detection: A Knowledge Distillation Approach with Image Transformation. Sensors 2024, 24, 8169. [Google Scholar] [CrossRef]
- Lee, G.; Yoon, Y.; Lee, K. Anomaly Detection Using an Ensemble of Multi-Point LSTMs. Entropy 2023, 25, 1480. [Google Scholar] [CrossRef]
- Lin, Y.; Xie, Z.; Chen, T.; Cheng, X.; Wen, H. Image privacy protection scheme based on high-quality reconstruction DCT compression and nonlinear dynamics. Expert Syst. Appl. 2024, 257, 124891. [Google Scholar] [CrossRef]
- Wang, F.; Jiang, Y.; Zhang, R.; Wei, A.; Xie, J.; Pang, X. A Survey of Deep Anomaly Detection in Multivariate Time Series: Taxonomy, Applications, and Directions. Sensors 2025, 25, 190. [Google Scholar] [CrossRef]
- Xu, J.; Li, K.; Li, D. An Automated Few-Shot Learning for Time-Series Forecasting in Smart Grid Under Data Scarcity. IEEE Trans. Artif. Intell. 2024, 5, 2482–2492. [Google Scholar] [CrossRef]
- Xu, J.; Li, K.; Li, D. Multioutput Framework for Time-Series Forecasting in Smart Grid Meets Data Scarcity. IEEE Trans. Ind. Inform. 2024, 20, 11202–11212. [Google Scholar]
- Tropea, M.; Arieta, A.; De Rango, F.; Pupo, F. A Proposal of a Troposphere Model in a GNSS Simulator for VANET Applications. Sensors 2021, 21, 2491. [Google Scholar] [CrossRef] [PubMed]
- Carlin, L.; Hauschild, A.; Montenbruck, O. Precise point positioning with GPS and Galileo broadcast ephemerides. GPS Solut. 2021, 25, 77. [Google Scholar]
- Maltsev, A.S.; Burtsev, S.Y.; Pecheritsa, D.S. Evaluation of Root Mean Square of Global Navigation Satellite Systems Receiver Carrier Phase Measurement Error. In Proceedings of the 2024 IEEE 3rd International Conference on Problems of Informatics, Electronics and Radio Engineering (PIERE), Novosibirsk, Russia, 15–17 November 2024; pp. 50–55. [Google Scholar]
- Sun, M.-T.; Feng, W.-C.; Lai, T.-H.; Yamada, K.; Okada, H.; Fujimura, K. GPS-based message broadcast for adaptive inter-vehicle communications, Vehicular Technology Conference Fall 2000. In Proceedings of the IEEE VTS Fall VTC2000. 52nd Vehicular Technology Conference (Cat. No.00CH37152), Boston, MA, USA, 24–28 September 2000; Volume 6, pp. 2685–2692. [Google Scholar]
- Liu, S.; Li, S.; Zheng, J.; Fu, Q.; Yuan, Y. C/N0 Estimator Based on the Adaptive Strong Tracking Kalman Filter for GNSS Vector Receivers. Sensors 2020, 20, 739. [Google Scholar] [CrossRef] [PubMed]


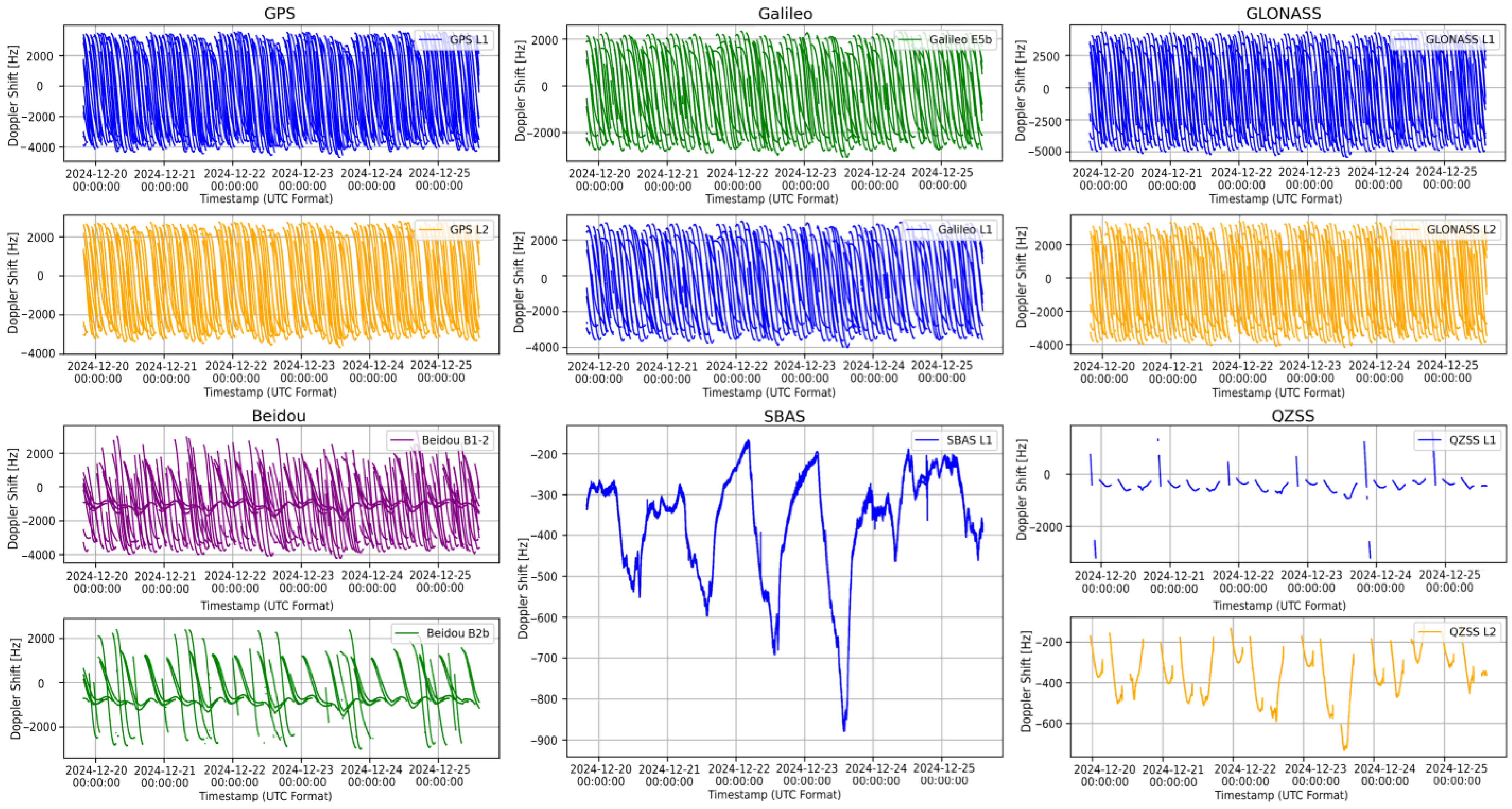
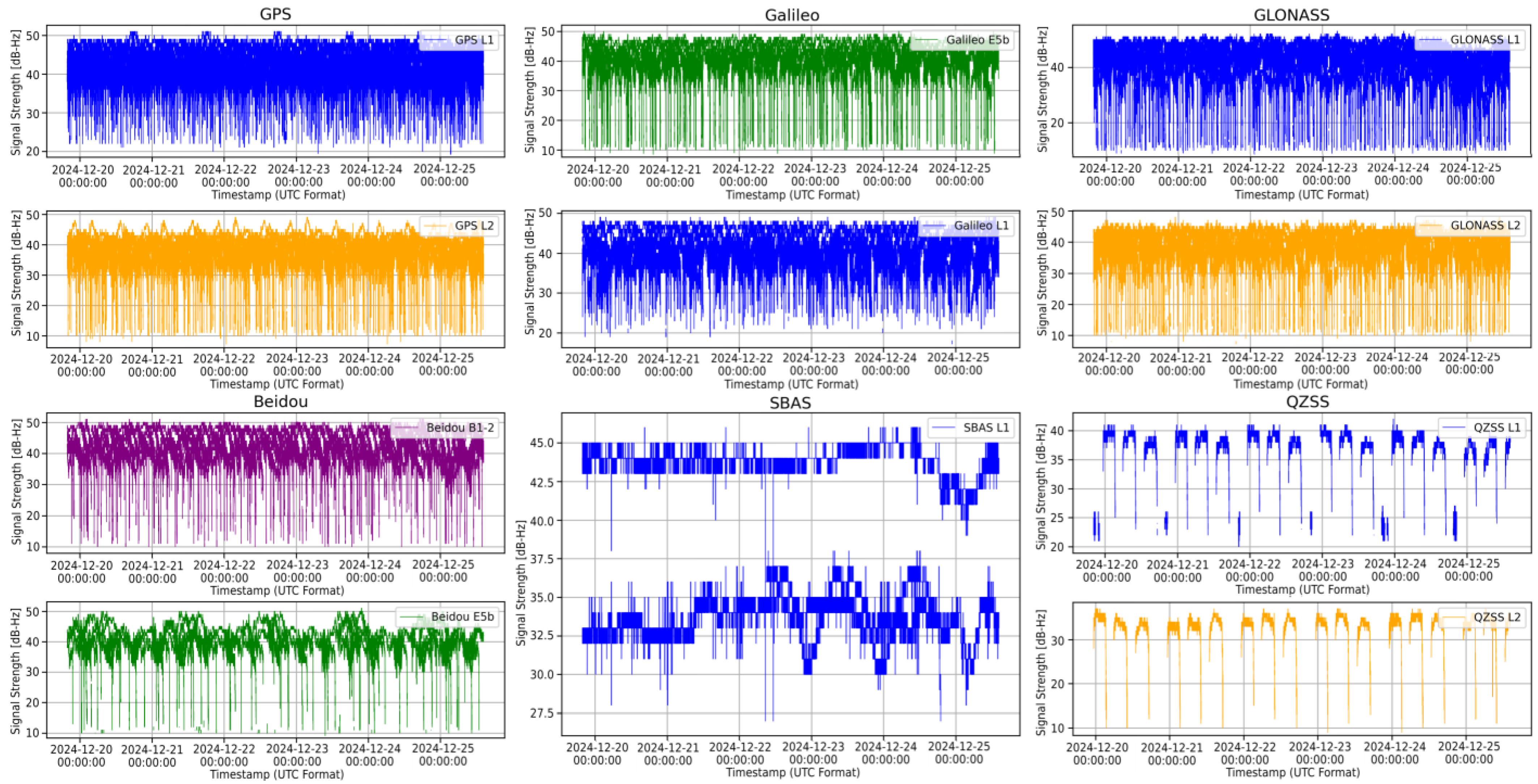
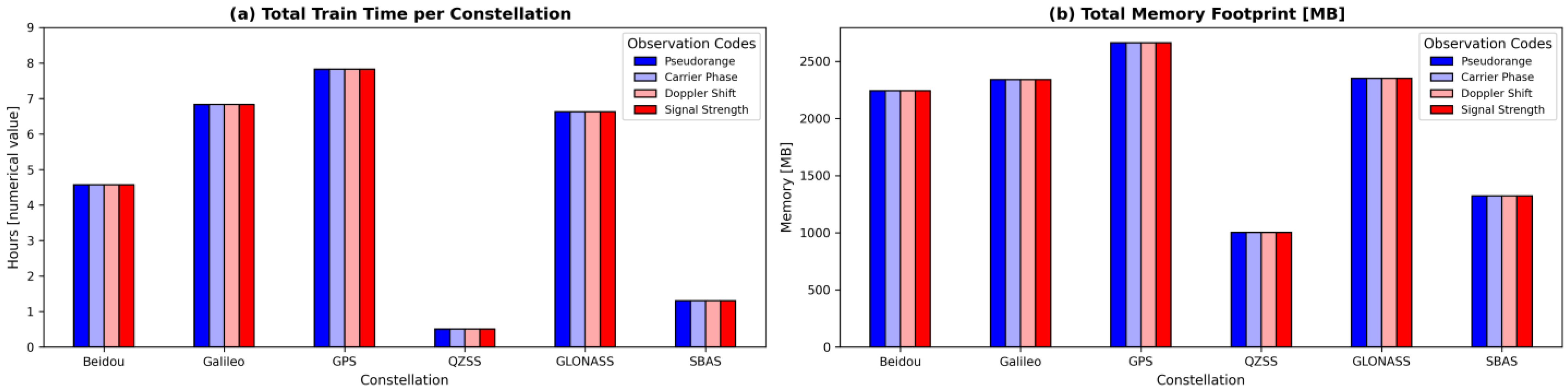
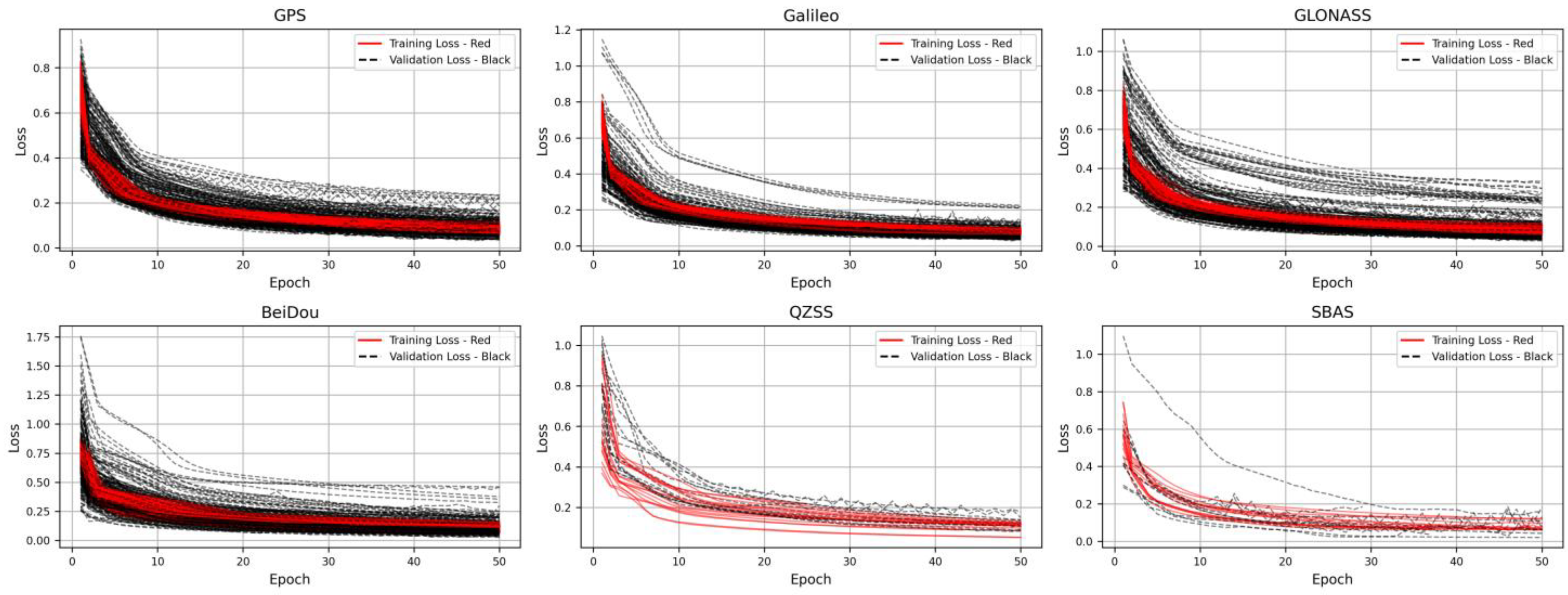




| No. | Model Configuration | Dropout | Learn. Rate | Layers | Latent_DIM | Loss Function | MAE | RMSE |
|---|---|---|---|---|---|---|---|---|
| #1 | Complete model | 0.2 | 1.00 × 10−4 | 4 | 16 | MAE | 0.117 | 0.186 |
| #2 | No dropout | x | 1.00 × 10−4 | 4 | 16 | MAE | 0.162 | 0.25 |
| #3 | Simplified | 0.2 | 1.00 × 10−4 | 2 | 16 | MAE | 0.169 | 0.256 |
| #4 | Latent_DIM = 8 | 0.2 | 1.00 × 10−4 | 4 | 8 | MAE | 0.138 | 0.215 |
| #5 | Latent_DIM = 64 | 0.2 | 1.00 × 10−4 | 4 | 64 | MAE | 0.132 | 0.199 |
| #6 | Dropout = 0.4 | 0.4 | 1.00 × 10−4 | 4 | 16 | MAE | 0.141 | 0.22 |
| Description | Values |
|---|---|
| Measurement period | 2024-12-19T19:47:00–2024-12-25T19:53:00 |
| Total number of observed satellites | 127 satellites (Beidou-36, Galileo-25, GPS-32, GLONASS-24, QZSS-6, SBAS-4) |
| Total number of recorded epochs | 500,000 |
| Total number of recorded observations | 19,966,505 |
| Measurement location | Romania |
| Description | Values |
|---|---|
| Measurement period | 2025-01-21T08:02:42–2025-01-22T18:30:48 |
| Attack period | 2025-01-21T21:00:00–2025-01-21T23:00:00 |
| Total number of observed satellites | 123 satellites (Beidou-34, Galileo-23, GPS-32, GLONASS-24, QZSS-6, SBAS-4) |
| Total number of spoofed satellites | 25 satellites (Beidou-0, Galileo-0, GPS-19, GLONASS-0, QZSS-4, SBAS-2) |
| Total number of recorded epochs | 120,000 |
| Total number of spoofed epochs | 7321 |
| Total number of recorded observations | 4,405,510 |
| Total number of spoofed observations | 91,835 |
| Measurement location | Romania |
| Scaling Coefficient | Precision (%) | Recall (%) | F1-Score (%) |
|---|---|---|---|
| k = 2.0 | 82.3 | 95.1 | 89.3 |
| k = 2.5 | 88.6 | 91.4 | 90.0 |
| k = 3.0 | 91.8 | 89.7 | 90.7 |
| k = 3.5 | 94.1 | 81.5 | 87.3 |
| k = 4.0 | 94.5 | 73.2 | 83.1 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Romaniuc, A.-G.; Vasile, V.-C.; Borda, M.-E. Global Navigation Satellite System Spoofing Attack Detection Using Receiver Independent Exchange Format Data and Long Short-Term Memory Algorithm. Information 2025, 16, 502. https://doi.org/10.3390/info16060502
Romaniuc A-G, Vasile V-C, Borda M-E. Global Navigation Satellite System Spoofing Attack Detection Using Receiver Independent Exchange Format Data and Long Short-Term Memory Algorithm. Information. 2025; 16(6):502. https://doi.org/10.3390/info16060502
Chicago/Turabian StyleRomaniuc, Alexandru-Gabriel, Vlad-Cosmin Vasile, and Monica-Elena Borda. 2025. "Global Navigation Satellite System Spoofing Attack Detection Using Receiver Independent Exchange Format Data and Long Short-Term Memory Algorithm" Information 16, no. 6: 502. https://doi.org/10.3390/info16060502
APA StyleRomaniuc, A.-G., Vasile, V.-C., & Borda, M.-E. (2025). Global Navigation Satellite System Spoofing Attack Detection Using Receiver Independent Exchange Format Data and Long Short-Term Memory Algorithm. Information, 16(6), 502. https://doi.org/10.3390/info16060502








