Optimizing IoT Intrusion Detection—A Graph Neural Network Approach with Attribute-Based Graph Construction
Abstract
1. Introduction
1.1. The Rise of the IoT
1.2. Network Intrusion Detection System
1.3. Graph Neural Networks
1.4. Research Gap and Contributions
- We introduce TKSGF for IoT network intrusion detection. Our framework achieved superior performance on both binary and multi-class classification tasks using the NF-ToN IoT and NF-BoT IoT datasets, outperforming traditional machine learning methods and existing graph-based approaches.
- We develop a novel Top-K Attribute Similarity-Based Graph Construction method, rather than the existing physical-network-connection-based method. Our method ensures a more meaningful representation of node relationships and achieved better results compared to physical-link-based methods.
- We conducted comprehensive experiments to investigate the impact of graph directionality (directed vs. undirected), different K values, and various GNN architectures and configurations on IoT NIDS detection performance. These experiments provided valuable insights and reference points for future research and practical applications in the field.
2. Related Work
2.1. Machine Learning in IoT Cyber Security
2.2. Deep Learning in IoT Cyber Security
2.3. Graph Deep Learning in IoT Cyber Security
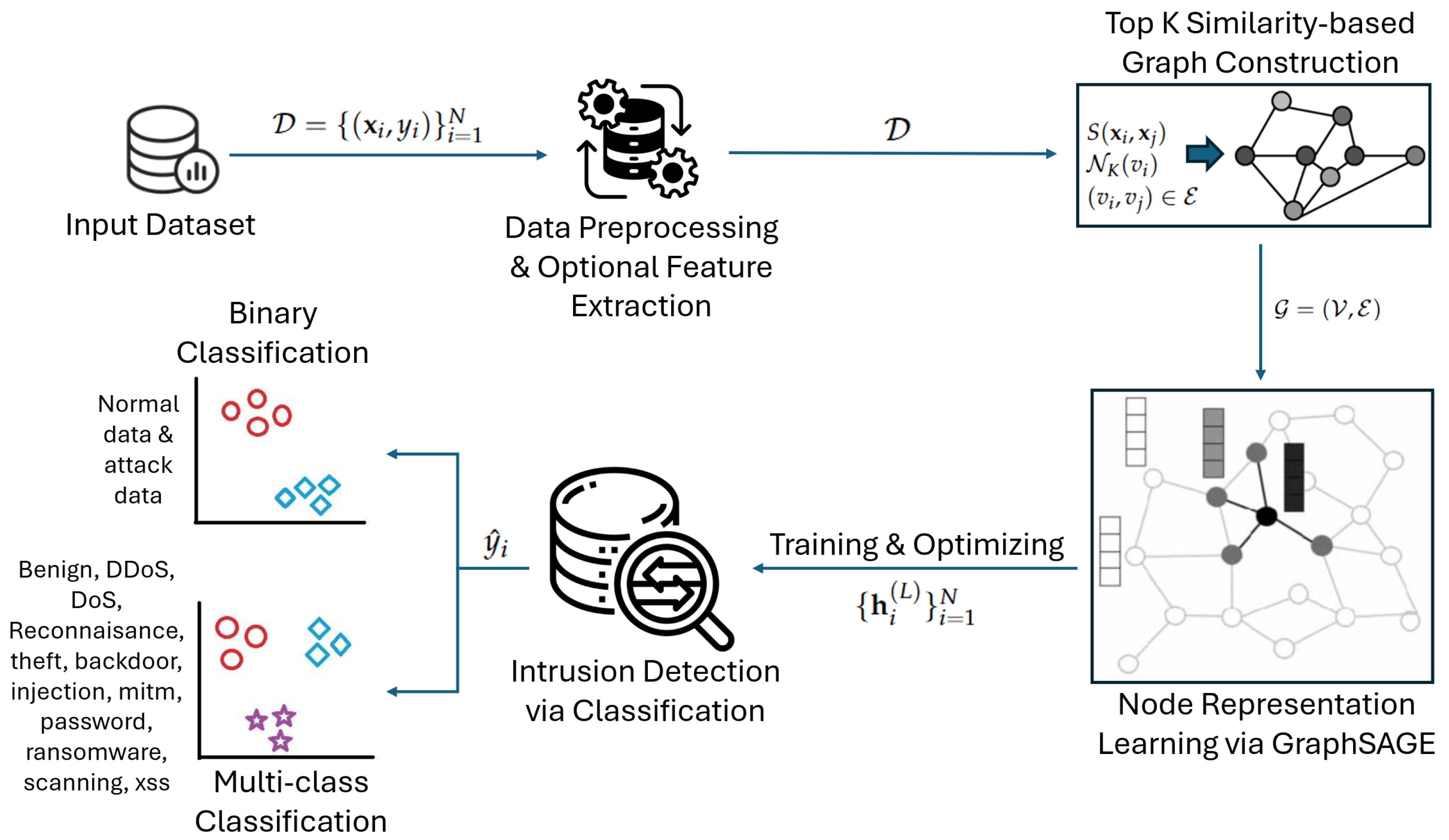
3. Methodology
3.1. Graph Theory Preliminaries
3.2. The Overall Framework
3.3. Data Preprocessing and Feature Representation
3.4. Top-K Attribute-Similarity-Based Graph Construction
3.5. Node Representation Learning with GraphSAGE
3.6. Intrusion Detection via Classification
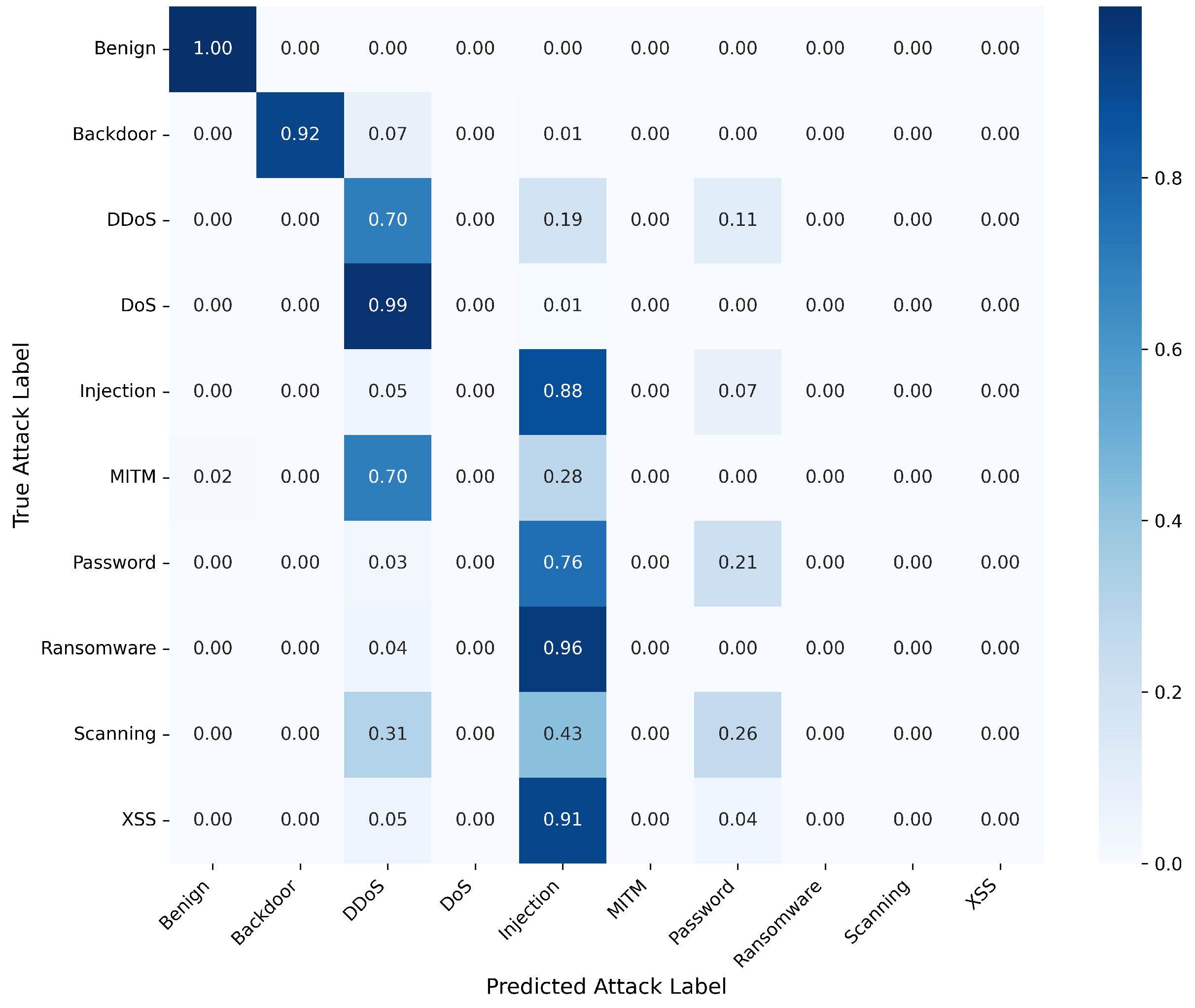
4. Results and Discussion
4.1. Datasets
- Denial of Service (DoS): Disrupts the normal functioning of a system by overwhelming it with malicious requests or operations.
- Distributed Denial of Service (DDoS): A coordinated DoS attack executed from multiple sources to flood and incapacitate a target system.
- Reconnaissance: Involves probing or scanning activities aimed at gathering information about a system’s vulnerabilities prior to launching an attack.
- Theft: Refers to unauthorized access and extraction of sensitive or personal information, often for illicit distribution or sale.
- Backdoor: Utilizes hidden entry points to gain unauthorized access to a system, bypassing standard authentication mechanisms.
- Man-in-the-Middle (MITM): An attack in which the adversary intercepts and potentially alters communications between two parties without their knowledge.
- Password Attack: Attempts to compromise user credentials in order to gain unauthorized access to protected systems or accounts.
- Ransomware: Malicious software that encrypts or locks system files, demanding payment from users in exchange for restored access. A notable example is the WannaCry ransomware worm, which propagated globally in 2017, encrypting files on affected systems and demanding payment in Bitcoin for decryption [46]. More information is available at https://attack.mitre.org/software/S0366/, accessed on 8 June 2025.
- Scanning: Involves automated probing to identify open ports, running services, or system vulnerabilities that may be exploited.
- Cross-Site Scripting (XSS): Injects malicious scripts into trusted websites or applications to exploit users and compromise system integrity.
4.2. Setup
4.3. Evaluation Metrics
4.4. Comparison with Other Works
4.5. Ablation Study
4.6. Binary Classification Results
4.7. Multi-Class Classification Results
4.8. GNN Model Structure Exploration
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Rejeb, A.; Rejeb, K.; Treiblmaier, H.; Appolloni, A.; Alghamdi, S.; Alhasawi, Y.; Iranmanesh, M. The Internet of Things (IoT) in healthcare: Taking stock and moving forward. Internet Things 2023, 22, 100721. [Google Scholar] [CrossRef]
- Sinha, B.B.; Dhanalakshmi, R. Recent advancements and challenges of Internet of Things in smart agriculture: A survey. Future Gener. Comput. Syst. 2022, 126, 169–184. [Google Scholar] [CrossRef]
- Singh, P.; Elmi, Z.; Meriga, V.K.; Pasha, J.; Dulebenets, M.A. Internet of Things for sustainable railway transportation: Past, present, and future. Clean. Logist. Supply Chain 2022, 4, 100065. [Google Scholar] [CrossRef]
- Li, Y.; Liu, Q. A comprehensive review study of cyber-attacks and cyber security; Emerging trends and recent developments. Energy Rep. 2021, 7, 8176–8186. [Google Scholar] [CrossRef]
- Manoharan, P.; Hong, W.; Yin, J.; Wang, H.; Zhang, Y.; Ye, W. Optimising Insider Threat Prediction: Exploring BiLSTM Networks and Sequential Features. In Data Science and Engineering; Springer Nature: Cham, Switzerland, 2024; pp. 1–16. [Google Scholar]
- Yin, J.; Tang, M.; Cao, J.; You, M.; Wang, H. Cybersecurity applications in software: Data-driven software vulnerability assessment and management. In Emerging Trends in Cybersecurity Applications; Springer: Cham, Switzerland, 2022; pp. 371–389. [Google Scholar]
- Guerra, J.L.; Catania, C.; Veas, E. Datasets are not enough: Challenges in labeling network traffic. Comput. Secur. 2022, 120, 102810. [Google Scholar] [CrossRef]
- Eid, A.M.; Soudan, B.; Nassif, A.B.; Injadat, M. Comparative study of ML models for IIoT intrusion detection: Impact of data preprocessing and balancing. Neural Comput. Appl. 2024, 36, 6955–6972. [Google Scholar] [CrossRef]
- Mbow, M.; Koide, H.; Sakurai, K. An intrusion detection system for imbalanced dataset based on deep learning. In Proceedings of the 2021 Ninth International Symposium on Computing and Networking (CANDAR), Matsue, Japan, 23–26 November 2021; pp. 38–47. [Google Scholar]
- Wang, Y.; Li, D.; Li, X.; Yang, M. PC-GAIN: Pseudo-label conditional generative adversarial imputation networks for incomplete data. Neural Netw. 2021, 141, 395–403. [Google Scholar] [CrossRef] [PubMed]
- Chen, Y.; Zhang, Y.; Maharjan, S. Deep learning for secure mobile edge computing. arXiv 2017, arXiv:1709.08025. [Google Scholar]
- Abdulganiyu, O.H.; Ait Tchakoucht, T.; Saheed, Y.K. A systematic literature review for network intrusion detection system (IDS). Int. J. Inf. Secur. 2023, 22, 1125–1162. [Google Scholar] [CrossRef]
- Yu, Y.; Zeng, X.; Xue, X.; Ma, J. LSTM-based intrusion detection system for VANETs: A time series classification approach to false message detection. IEEE Trans. Intell. Transp. Syst. 2022, 23, 23906–23918. [Google Scholar] [CrossRef]
- Wu, Z.; Zhang, H.; Wang, P.; Sun, Z. RTIDS: A robust transformer-based approach for intrusion detection system. IEEE Access 2022, 10, 64375–64387. [Google Scholar] [CrossRef]
- Kheddar, H. Transformers and large language models for efficient intrusion detection systems: A comprehensive survey. arXiv 2024, arXiv:2408.07583. [Google Scholar] [CrossRef]
- Aldwairi, M.; Jarrah, M.; Mahasneh, N.; Al-khateeb, B. Graph-based data management system for efficient information storage, retrieval and processing. Inf. Process. Manag. 2023, 60, 103165. [Google Scholar] [CrossRef]
- Liu, M.; Li, X.; Li, J.; Liu, Y.; Zhou, B.; Bao, J. A knowledge graph-based data representation approach for IIoT-enabled cognitive manufacturing. Adv. Eng. Inform. 2022, 51, 101515. [Google Scholar] [CrossRef]
- Bilot, T.; El Madhoun, N.; Al Agha, K.; Zouaoui, A. Graph neural networks for intrusion detection: A survey. IEEE Access 2023, 11, 49114–49139. [Google Scholar] [CrossRef]
- Juan, X.; Zhou, F.; Wang, W.; Jin, W.; Tang, J.; Wang, X. INS-GNN: Improving graph imbalance learning with self-supervision. Inf. Sci. 2023, 637, 118935. [Google Scholar] [CrossRef]
- Wu, C.; Wu, F.; Cao, Y.; Huang, Y.; Xie, X. Fedgnn: Federated graph neural network for privacy-preserving recommendation. arXiv 2021, arXiv:2102.04925. [Google Scholar]
- Xu, K.; Li, Y.; Li, Y.; Xu, L.; Li, R.; Dong, Z. Masked graph neural networks for unsupervised anomaly detection in multivariate time series. Sensors 2023, 23, 7552. [Google Scholar] [CrossRef]
- Yin, J.; Hong, W.; Wang, H.; Cao, J.; Miao, Y.; Zhang, Y. A compact vulnerability knowledge graph for risk assessment. ACM Trans. Knowl. Discov. Data 2024, 18, 1–17. [Google Scholar] [CrossRef]
- Wang, Z.; Eisen, M.; Ribeiro, A. Learning decentralized wireless resource allocations with graph neural networks. IEEE Trans. Signal Process. 2022, 70, 1850–1863. [Google Scholar] [CrossRef]
- Munikoti, S.; Agarwal, D.; Das, L.; Halappanavar, M.; Natarajan, B. Challenges and opportunities in deep reinforcement learning with graph neural networks: A comprehensive review of algorithms and applications. IEEE Trans. Neural Netw. Learn. Syst. 2023, 35, 15051–15071. [Google Scholar] [CrossRef]
- Yin, J.; Chen, G.; Hong, W.; Cao, J.; Wang, H.; Miao, Y. A heterogeneous graph-based semi-supervised learning framework for access control decision-making. World Wide Web 2024, 27, 35. [Google Scholar] [CrossRef]
- Vrahatis, A.G.; Lazaros, K.; Kotsiantis, S. Graph attention networks: A comprehensive review of methods and applications. Future Internet 2024, 16, 318. [Google Scholar] [CrossRef]
- Hajibabaee, P.; Malekzadeh, M.; Heidari, M.; Zad, S.; Uzuner, O.; Jones, J.H. An empirical study of the graphsage and word2vec algorithms for graph multiclass classification. In Proceedings of the 2021 IEEE 12th Annual Information Technology, Electronics and Mobile Communication Conference (IEMCON), Vancouver, BC, Canada, 27–30 October 2021; pp. 0515–0522. [Google Scholar]
- Guezzaz, A.; Benkirane, S.; Azrour, M.; Khurram, S. A reliable network intrusion detection approach using decision tree with enhanced data quality. Secur. Commun. Netw. 2021, 2021, 1230593. [Google Scholar] [CrossRef]
- Majidian, S.Z.; TaghipourEivazi, S.; Arasteh, B.; Ghaffari, A. Optimizing random forests to detect intrusion in the Internet of Things. Comput. Electr. Eng. 2024, 120, 109860. [Google Scholar] [CrossRef]
- Mohy-Eddine, M.; Guezzaz, A.; Benkirane, S.; Azrour, M. An efficient network intrusion detection model for IoT security using K-NN classifier and feature selection. Multimed. Tools Appl. 2023, 82, 23615–23633. [Google Scholar] [CrossRef]
- Mehmood, A.; Mukherjee, M.; Ahmed, S.H.; Song, H.; Malik, K.M. NBC-MAIDS: Naïve Bayesian classification technique in multi-agent system-enriched IDS for securing IoT against DDoS attacks. J. Supercomput. 2018, 74, 5156–5170. [Google Scholar] [CrossRef]
- Alqahtani, M.; Mathkour, H.; Ben Ismail, M.M. IoT botnet attack detection based on optimized extreme gradient boosting and feature selection. Sensors 2020, 20, 6336. [Google Scholar] [CrossRef] [PubMed]
- Douiba, M.; Benkirane, S.; Guezzaz, A.; Azrour, M. An improved anomaly detection model for IoT security using decision tree and gradient boosting. J. Supercomput. 2023, 79, 3392–3411. [Google Scholar] [CrossRef]
- Hamidouche, M.; Popko, E.; Ouni, B. Enhancing iot security via automatic network traffic analysis: The transition from machine learning to deep learning. In Proceedings of the 13th International Conference on the Internet of Things, Nagoya, Japan, 7–10 November 2023; pp. 105–112. [Google Scholar]
- Yin, J.; Tang, M.; Cao, J.; Wang, H. Apply transfer learning to cybersecurity: Predicting exploitability of vulnerabilities by description. Knowl.-Based Syst. 2020, 210, 106529. [Google Scholar] [CrossRef]
- Halbouni, A.; Gunawan, T.S.; Habaebi, M.H.; Halbouni, M.; Kartiwi, M.; Ahmad, R. CNN-LSTM: Hybrid deep neural network for network intrusion detection system. IEEE Access 2022, 10, 99837–99849. [Google Scholar] [CrossRef]
- Ullah, I.; Mahmoud, Q.H. Design and development of RNN anomaly detection model for IoT networks. IEEE Access 2022, 10, 62722–62750. [Google Scholar] [CrossRef]
- Park, C.; Lee, J.; Kim, Y.; Park, J.G.; Kim, H.; Hong, D. An enhanced AI-based network intrusion detection system using generative adversarial networks. IEEE Internet Things J. 2022, 10, 2330–2345. [Google Scholar] [CrossRef]
- Alrayes, F.S.; Zakariah, M.; Amin, S.U.; Khan, Z.I.; Helal, M. Intrusion detection in IoT systems using denoising autoencoder. IEEE Access 2024, 12, 122401–122425. [Google Scholar] [CrossRef]
- Deng, X.; Zhu, J.; Pei, X.; Zhang, L.; Ling, Z.; Xue, K. Flow topology-based graph convolutional network for intrusion detection in label-limited IoT networks. IEEE Trans. Netw. Serv. Manag. 2022, 20, 684–696. [Google Scholar] [CrossRef]
- Zhang, L.; Tan, L.; Shi, H.; Sun, H.; Zhang, W. Malicious Traffic Classification for IoT based on Graph Attention Network and Long Short-Term Memory Network. In Proceedings of the 2023 24st Asia-Pacific Network Operations and Management Symposium (APNOMS), Sejong, Republic of Korea, 6–8 September 2023; pp. 54–59. [Google Scholar]
- Hamilton, W.; Ying, Z.; Leskovec, J. Inductive representation learning on large graphs. Adv. Neural Inf. Process. Syst. 2017, 30, 1025–1035. [Google Scholar]
- Lo, W.W.; Layeghy, S.; Sarhan, M.; Gallagher, M.; Portmann, M. E-graphsage: A graph neural network based intrusion detection system for iot. In Proceedings of the NOMS 2022-2022 IEEE/IFIP Network Operations and Management Symposium, Budapest, Hungary, 25–29 April 2022; pp. 1–9. [Google Scholar]
- Xu, R.; Wu, G.; Wang, W.; Gao, X.; He, A.; Zhang, Z. Applying self-supervised learning to network intrusion detection for network flows with graph neural network. Comput. Netw. 2024, 248, 110495. [Google Scholar] [CrossRef]
- Sarhan, M.; Layeghy, S.; Moustafa, N.; Portmann, M. Netflow datasets for machine learning-based network intrusion detection systems. In Proceedings of the Big Data Technologies and Applications: 10th EAI International Conference, BDTA 2020, and 13th EAI International Conference on Wireless Internet, WiCON 2020, Virtual, 11 December 2020; Proceedings 10. Springer: Cham, Switzerland, 2021; pp. 117–135. [Google Scholar]
- Mohurle, S.; Patil, M. A brief study of wannacry threat: Ransomware attack 2017. Int. J. Adv. Res. Comput. Sci. 2017, 8, 1938–1940. [Google Scholar]
- Altaf, T.; Wang, X.; Ni, W.; Yu, G.; Liu, R.P.; Braun, R. A new concatenated multigraph neural network for IoT intrusion detection. Internet Things 2023, 22, 100818. [Google Scholar] [CrossRef]
- Manoharan, P.; Yin, J.; Wang, H.; Zhang, Y.; Ye, W. Insider threat detection using supervised machine learning algorithms. In Telecommunication Systems; Springer: Berlin/Heidelberg, Germany, 2023; pp. 1–17. [Google Scholar]
- Beaver, J.M.; Borges-Hink, R.C.; Buckner, M.A. An evaluation of machine learning methods to detect malicious SCADA communications. In Proceedings of the 2013 12th International Conference on Machine Learning and Applications, Miami, FL, USA, 4–7 December 2013; Volume 2, pp. 54–59. [Google Scholar]
- Ahmad, Z.; Shahid Khan, A.; Wai Shiang, C.; Abdullah, J.; Ahmad, F. Network intrusion detection system: A systematic study of machine learning and deep learning approaches. Trans. Emerg. Telecommun. Technol. 2021, 32, e4150. [Google Scholar] [CrossRef]
- Ngo, T.; Yin, J.; Ge, Y.F.; Zhou, C.; Cao, J. Comparative Study of Machine Learning Algorithms for IoT Cyber Threat Detection in Healthcare Information Systems. In Proceedings of the International Conference on Health Information Science, Hong Kong, China, 8–10 December 2024; Springer: Singapore, 2025; pp. 68–77. [Google Scholar]
- Elsharkawi, I.; Sharara, H.; Rafea, A. SViG: A Similarity-thresholded Approach for Vision Graph Neural Networks. IEEE Access 2025, 13, 19379–19387. [Google Scholar] [CrossRef]


| Dataset | Label | Attack | Quantities | Train | Eval | Test | Total Data |
|---|---|---|---|---|---|---|---|
| NF-BoT IoT | 0 | Benign | 13,859 | 9701 | 2079 | 2079 | 600,100 |
| 1 | DDoS | 56,844 | 39,791 | 8527 | 8526 | ||
| DoS | 56,833 | 39,783 | 8525 | 8525 | |||
| Reconnaissance | 470,655 | 329,459 | 70,598 | 70,598 | |||
| Theft | 1909 | 1336 | 286 | 287 | |||
| NF-ToN IoT | 0 | Benign | 270,279 | 162,167 | 54,056 | 54,056 | 1,379,274 |
| 1 | Backdoor | 17,247 | 10,348 | 3449 | 3450 | ||
| DDoS | 326,345 | 195,807 | 65,269 | 65,269 | |||
| DoS | 17,717 | 10,630 | 3543 | 3544 | |||
| Injection | 468,539 | 281,123 | 93,708 | 93,708 | |||
| MITM | 1295 | 777 | 259 | 259 | |||
| Password | 156,299 | 93,779 | 31,260 | 31,260 | |||
| Ransomware | 142 | 85 | 28 | 29 | |||
| Scanning | 21,467 | 12,880 | 4293 | 4294 | |||
| XSS | 99,944 | 59,966 | 19,989 | 19,989 |
| Dataset | NF-BoT-IoT | NF-BoT-IoT | NF-ToN-IoT | NF-ToN-IoT |
|---|---|---|---|---|
| Classification task | Binary | Multi-class | Binary | Multi-class |
| Proposed approach | 0.9852 | 0.8404 | 1.0000 | 0.6325 |
| Decision Tree | 0.9848 | 0.4330 | 0.9219 | 0.5460 |
| Random Forest | 0.9843 | 0.8091 | 0.9224 | 0.5596 |
| Naïve Bayes | 0.9600 | 0.7654 | 0.7264 | 0.2095 |
| E-GraphSAGE | 0.9700 | 0.8100 | 1.0000 | 0.6300 |
| Self-supervised Learning | 0.9767 | 0.8270 | N/A | N/A |
| Graph Isomorphism Network | 0.9679 | 0.8211 | 0.7417 | 0.6240 |
| Dataset | NF-BoT-IoT | NF-BoT-IoT | NF-ToN-IoT | NF-ToN-IoT | |
|---|---|---|---|---|---|
| Classification Task | Binary | Multi-Class | Binary | Multi-Class | |
| Proposed approach | Cosine + Sim08 + TopK | 0.9852 | 0.8404 | 1.0000 | 0.6325 |
| Ablation study 1 | Euclidean + Sim08 + TopK | 0.9849 | 0.8204 | 1.0000 | 0.6066 |
| Ablation study 2 | Cosine + TopK | 0.9852 | 0.8344 | 1.0000 | 0.6265 |
| Ablation study 3 | Cosine + Sim06 + TopK | 0.9849 | 0.8375 | 1.0000 | 0.6280 |
| Ablation study 4 | Cosine + Sim09 + TopK | 0.9851 | 0.8309 | 1.0000 | 0.6256 |
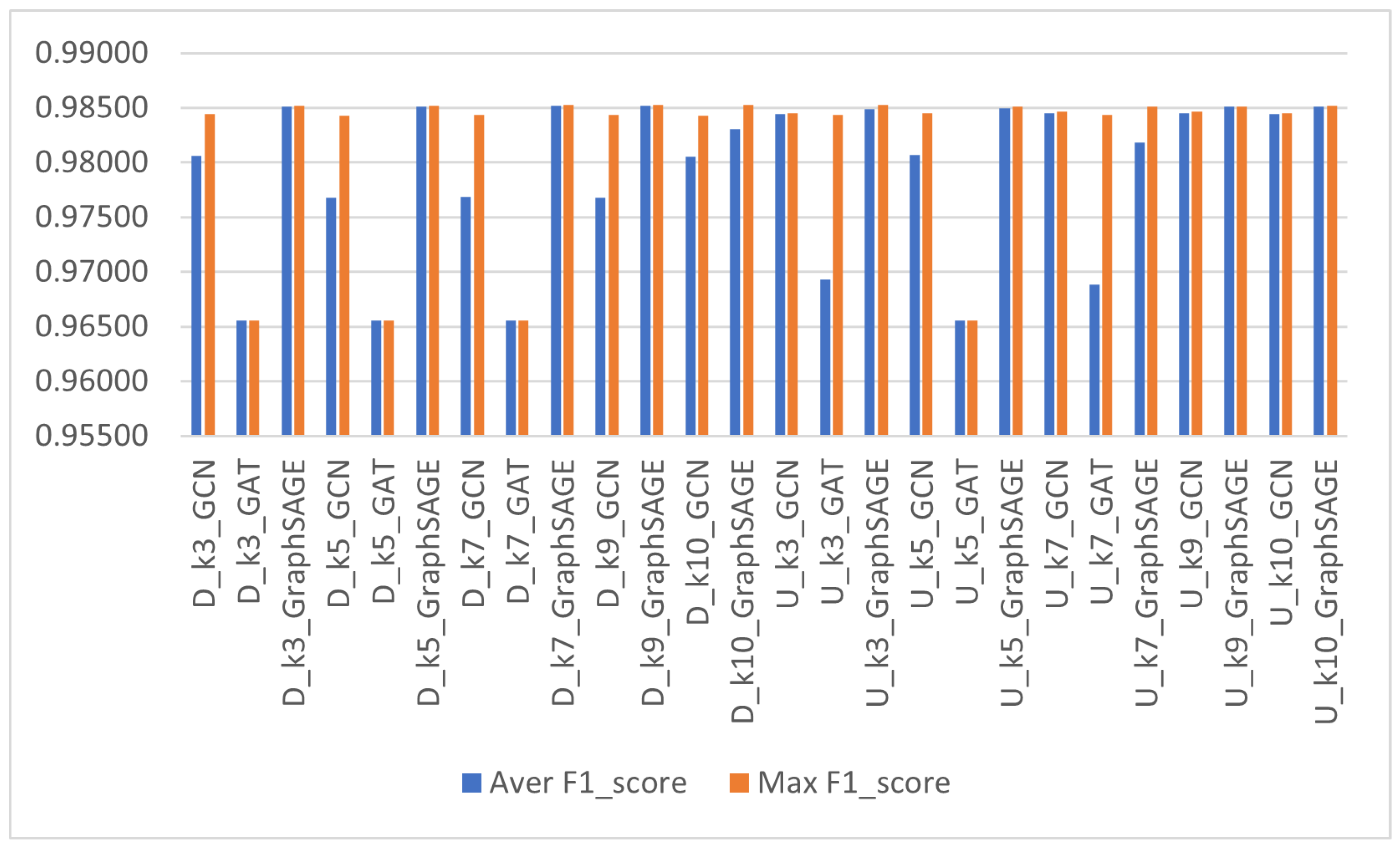
| Graph Type | k | GNN Model | Aver F1_Score | Std_Deviation | Max F1_Score | Aver Run Time (sec) | No. Runs |
|---|---|---|---|---|---|---|---|
| Directed | 3 | GCN | 0.980604 | 0.008393 | 0.984425 | 11.56 | 5 |
| GAT | 0.965590 | 0.000000 | 0.965590 | 2.00 | 5 | ||
| GraphSAGE | 0.985099 | 0.000075 | 0.985157 | 5.61 | 6 | ||
| 5 | GCN | 0.976781 | 0.010216 | 0.984286 | 7.74 | 5 | |
| GAT | 0.965590 | 0.000000 | 0.965590 | 11.86 | 5 | ||
| GraphSAGE | 0.985143 | 0.000083 | 0.985226 | 6.38 | 6 | ||
| 7 | GCN | 0.976847 | 0.010276 | 0.984354 | 11.43 | 5 | |
| GAT | 0.965590 | 0.000000 | 0.965590 | 12.29 | 5 | ||
| GraphSAGE | 0.985196 | 0.000071 | 0.985257 | 6.67 | 6 | ||
| 9 | GCN | 0.976807 | 0.010240 | 0.984320 | 10.90 | 5 | |
| GraphSAGE | 0.985222 | 0.000048 | 0.985298 | 8.58 | 6 | ||
| 10 | GCN | 0.980531 | 0.008352 | 0.984277 | 14.96 | 5 | |
| GraphSAGE | 0.983047 | 0.005238 | 0.985246 | 6.23 | 6 | ||
| Undirected | 3 | GCN | 0.984411 | 0.000064 | 0.984488 | 10.53 | 5 |
| GAT | 0.969334 | 0.008372 | 0.984310 | 1.96 | 5 | ||
| GraphSAGE | 0.984873 | 0.000281 | 0.985262 | 8.39 | 6 | ||
| 5 | GCN | 0.980686 | 0.008448 | 0.984537 | 8.33 | 5 | |
| GAT | 0.965590 | 0.000000 | 0.965590 | 1.48 | 5 | ||
| GraphSAGE | 0.984964 | 0.000154 | 0.985094 | 6.90 | 6 | ||
| 7 | GCN | 0.984507 | 0.000113 | 0.984635 | 10.62 | 5 | |
| GAT | 0.968815 | 0.007595 | 0.984310 | 1.84 | 6 | ||
| GraphSAGE | 0.981801 | 0.007942 | 0.985110 | 6.02 | 6 | ||
| 9 | GCN | 0.984504 | 0.000115 | 0.984629 | 11.15 | 5 | |
| GraphSAGE | 0.985096 | 0.000028 | 0.985127 | 8.02 | 6 | ||
| 10 | GCN | 0.984407 | 0.000062 | 0.984500 | 10.95 | 5 | |
| GraphSAGE | 0.985083 | 0.000077 | 0.985174 | 8.06 | 6 |
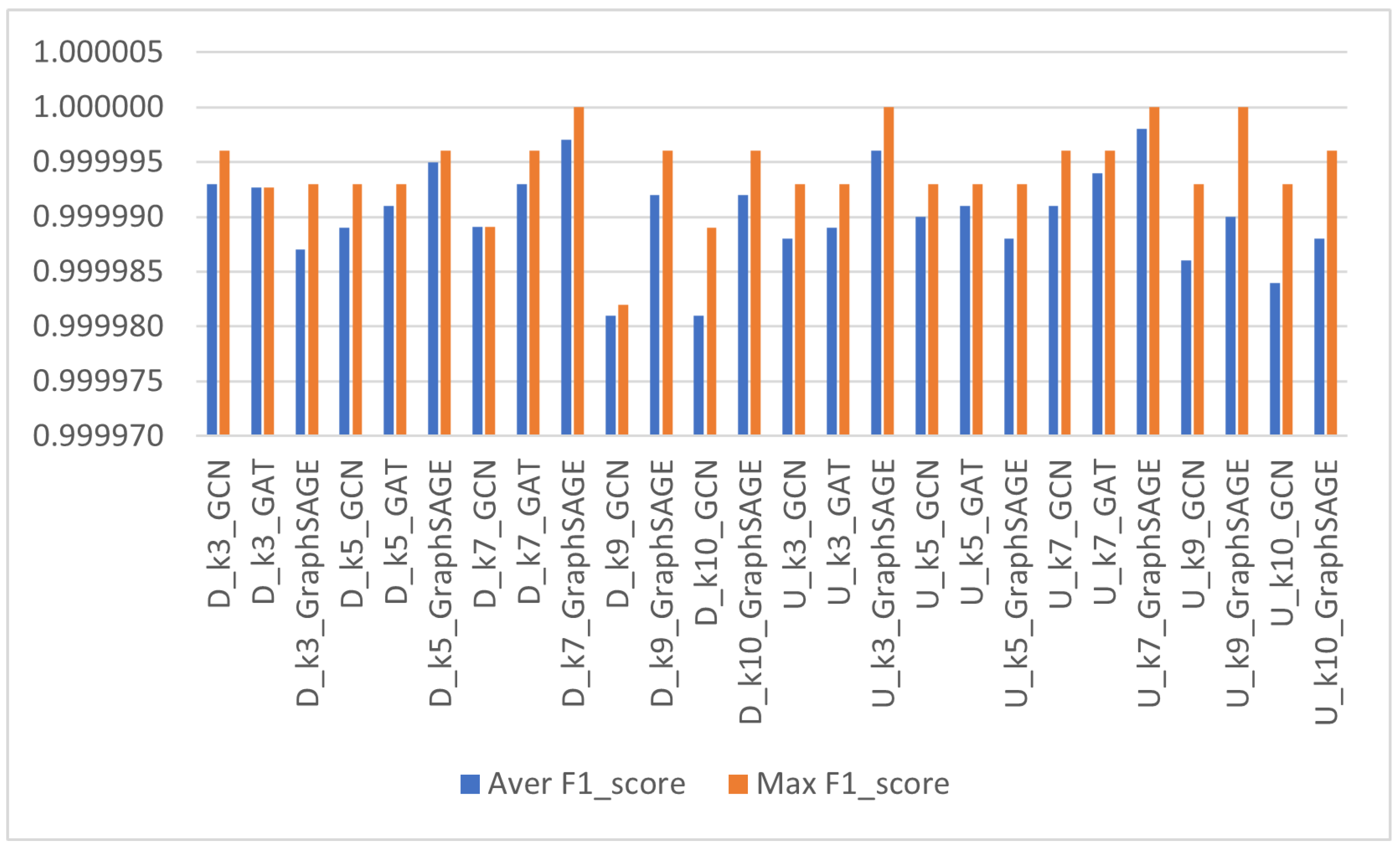
| Graph Type | k | GNN Model | Aver F1_Score | Std_Deviation | Max F1_Score | Aver Run Time (sec) | No. Runs |
|---|---|---|---|---|---|---|---|
| Directed | 3 | GCN | 0.999993 | 0.000001 | 0.999996 | 44.30 | 6 |
| GAT | 0.999993 | 0.000000 | 0.999993 | 322.21 | 5 | ||
| GraphSAGE | 0.999987 | 0.000005 | 0.999993 | 30.37 | 8 | ||
| 5 | GCN | 0.999989 | 0.000002 | 0.999993 | 55.02 | 6 | |
| GAT | 0.999991 | 0.000003 | 0.999993 | 364.50 | 5 | ||
| GraphSAGE | 0.999995 | 0.000003 | 0.999996 | 46.29 | 8 | ||
| 7 | GCN | 0.999989 | 0.000000 | 0.999989 | 75.32 | 6 | |
| GAT | 0.999993 | 0.000004 | 0.999996 | 1947.74 | 6 | ||
| GraphSAGE | 0.999997 | 0.000004 | 1.000000 | 43.75 | 6 | ||
| 9 | GCN | 0.999981 | 0.000002 | 0.999982 | 103.55 | 6 | |
| GraphSAGE | 0.999992 | 0.000004 | 0.999996 | 37.50 | 6 | ||
| 10 | GCN | 0.999981 | 0.000005 | 0.999989 | 93.41 | 5 | |
| GraphSAGE | 0.999992 | 0.000005 | 0.999996 | 35.64 | 6 | ||
| Undirected | 3 | GCN | 0.999988 | 0.000005 | 0.999993 | 36.65 | 5 |
| GAT | 0.999989 | 0.000003 | 0.999993 | 48.70 | 5 | ||
| GraphSAGE | 0.999996 | 0.000005 | 1.000000 | 42.21 | 6 | ||
| 5 | GCN | 0.999990 | 0.000003 | 0.999993 | 32.56 | 5 | |
| GAT | 0.999991 | 0.000002 | 0.999993 | 48.99 | 5 | ||
| GraphSAGE | 0.999988 | 0.000005 | 0.999993 | 42.76 | 7 | ||
| 7 | GCN | 0.999991 | 0.000004 | 0.999996 | 28.88 | 5 | |
| GAT | 0.999994 | 0.000002 | 0.999996 | 74.74 | 5 | ||
| GraphSAGE | 0.999998 | 0.000002 | 1.000000 | 30.73 | 6 | ||
| 9 | GCN | 0.999986 | 0.000004 | 0.999993 | 24.03 | 6 | |
| GraphSAGE | 0.999990 | 0.000007 | 1.000000 | 36.27 | 6 | ||
| 10 | GCN | 0.999984 | 0.000005 | 0.999993 | 24.36 | 5 | |
| GraphSAGE | 0.999988 | 0.000005 | 0.999996 | 25.58 | 6 |
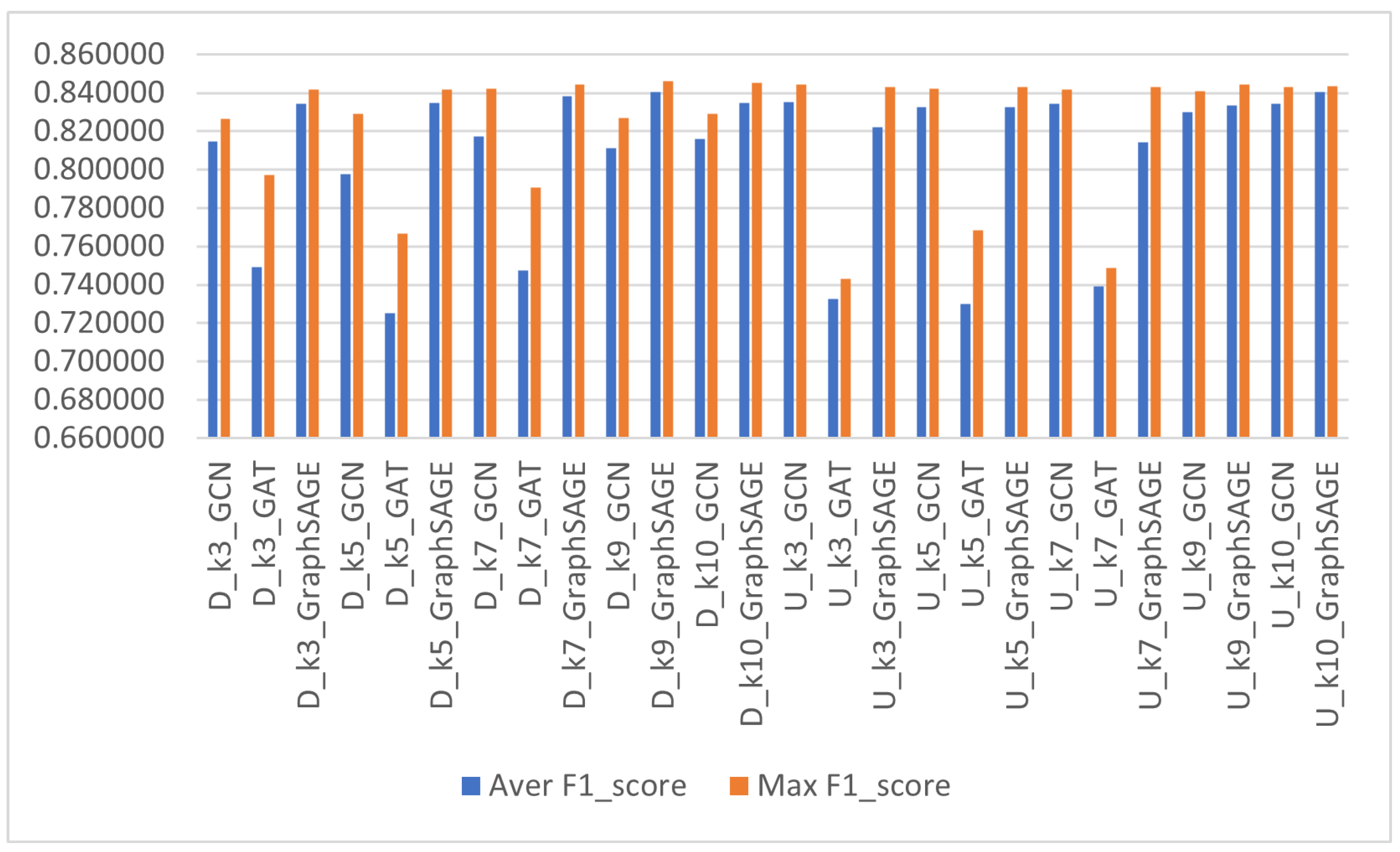
| Graph Type | k | GNN Model | Aver F1_Score | Std_Deviation | Max F1_Score | Aver Run Time (sec) | No. Runs |
|---|---|---|---|---|---|---|---|
| Directed | 3 | GCN | 0.814859 | 0.009034 | 0.826520 | 16.98 | 5 |
| GAT | 0.749033 | 0.028207 | 0.797119 | 6.15 | 5 | ||
| GraphSAGE | 0.834453 | 0.007781 | 0.841952 | 6.48 | 5 | ||
| 5 | GCN | 0.797705 | 0.056191 | 0.828939 | 16.59 | 5 | |
| GAT | 0.725212 | 0.028222 | 0.766572 | 85.13 | 5 | ||
| GraphSAGE | 0.834693 | 0.005104 | 0.841671 | 6.80 | 5 | ||
| 7 | GCN | 0.817505 | 0.016056 | 0.842142 | 19.50 | 5 | |
| GAT | 0.747354 | 0.027544 | 0.790514 | 41.76 | 5 | ||
| GraphSAGE | 0.838391 | 0.008680 | 0.844298 | 7.54 | 6 | ||
| 9 | GCN | 0.811300 | 0.011066 | 0.827032 | 20.45 | 5 | |
| GraphSAGE | 0.840263 | 0.009466 | 0.846004 | 8.12 | 6 | ||
| 10 | GCN | 0.815999 | 0.011775 | 0.828960 | 25.41 | 5 | |
| GraphSAGE | 0.834799 | 0.007305 | 0.845157 | 9.17 | 6 | ||
| Undirected | 3 | GCN | 0.835111 | 0.011149 | 0.844220 | 10.38 | 5 |
| GAT | 0.732416 | 0.005847 | 0.742869 | 1.06 | 5 | ||
| GraphSAGE | 0.822018 | 0.032488 | 0.842849 | 6.03 | 6 | ||
| 5 | GCN | 0.832770 | 0.008551 | 0.842253 | 10.24 | 5 | |
| GAT | 0.729812 | 0.027002 | 0.768543 | 3.34 | 5 | ||
| GraphSAGE | 0.832545 | 0.009027 | 0.843114 | 9.30 | 6 | ||
| 7 | GCN | 0.834307 | 0.007548 | 0.841951 | 9.27 | 5 | |
| GAT | 0.739241 | 0.009096 | 0.748806 | 2.61 | 5 | ||
| GraphSAGE | 0.814455 | 0.039932 | 0.842851 | 8.48 | 6 | ||
| Undirected | 9 | GCN | 0.830168 | 0.007789 | 0.840973 | 10.80 | 5 |
| GraphSAGE | 0.833313 | 0.010022 | 0.844539 | 9.65 | 6 | ||
| 10 | GCN | 0.834366 | 0.009582 | 0.843074 | 10.99 | 5 | |
| GraphSAGE | 0.840447 | 0.002994 | 0.843658 | 9.09 | 6 |
| Graph Type | k | GNN Model | Aver F1_Score | Std_Deviation | Max F1_Score | Aver Run Time (sec) | No. Runs |
|---|---|---|---|---|---|---|---|
| Directed | 3 | GCN | 0.612570 | 0.007504 | 0.624629 | 25.46 | 5 |
| GAT | 0.607664 | 0.004639 | 0.611103 | 530.38 | 5 | ||
| GraphSAGE | 0.626702 | 0.004311 | 0.628980 | 1029.55 | 6 | ||
| 5 | GCN | 0.616292 | 0.006024 | 0.622707 | 38.52 | 5 | |
| GAT | 0.607655 | 0.004653 | 0.611122 | 960.29 | 5 | ||
| GraphSAGE | 0.627931 | 0.001848 | 0.629155 | 1753.62 | 6 | ||
| 7 | GCN | 0.615234 | 0.007517 | 0.623258 | 33.51 | 6 | |
| GAT | 0.608106 | 0.006721 | 0.618768 | 1114.47 | 6 | ||
| GraphSAGE | 0.628322 | 0.000808 | 0.629565 | 546.65 | 6 | ||
| 9 | GCN | 0.611154 | 0.005390 | 0.620563 | 41.06 | 5 | |
| GraphSAGE | 0.627101 | 0.003331 | 0.629233 | 65.98 | 7 | ||
| 10 | GCN | 0.612157 | 0.004555 | 0.617085 | 39.49 | 5 | |
| GraphSAGE | 0.627982 | 0.001686 | 0.629250 | 69.14 | 6 | ||
| Undirected | 3 | GCN | 0.615036 | 0.006942 | 0.622537 | 25.10 | 5 |
| GAT | 0.607849 | 0.008083 | 0.620632 | 291.95 | 5 | ||
| GraphSAGE | 0.624463 | 0.004015 | 0.628668 | 325.65 | 8 | ||
| 5 | GCN | 0.614611 | 0.007201 | 0.621941 | 27.63 | 5 | |
| GAT | 0.610878 | 0.005752 | 0.618631 | 430.33 | 5 | ||
| GraphSAGE | 0.628374 | 0.000500 | 0.628892 | 703.93 | 5 | ||
| 7 | GCN | 0.619946 | 0.001882 | 0.622298 | 32.48 | 5 | |
| GAT | 0.607477 | 0.004956 | 0.611158 | 490.89 | 5 | ||
| GraphSAGE | 0.627224 | 0.002342 | 0.628887 | 1189.82 | 5 | ||
| Undirected | 9 | GCN | 0.612081 | 0.007232 | 0.620648 | 29.72 | 5 |
| GraphSAGE | 0.626142 | 0.006277 | 0.629182 | 47.16 | 7 | ||
| 10 | GCN | 0.617318 | 0.005695 | 0.622252 | 32.57 | 5 | |
| GraphSAGE | 0.627393 | 0.001871 | 0.628997 | 56.05 | 6 |
| GraphSAGE Variant | Applied Function | |||||
|---|---|---|---|---|---|---|
| 1st Layer Dropout | 1st Layer BatchNorm | Activation Function | Residual | 2nd Layer Dropout | 2nd Layer BatchNorm | |
| GraphSAGE | N/A | 1st | 2nd | N/A | 3rd | N/A |
| GraphSAGE1 | N/A | 1st | 2nd | N/A | 3rd | 4th |
| GraphSAGE2 | N/A | 1st | 3rd | 2nd | 4th | 5th |
| GraphSAGE3 | N/A | 1st | 2nd | 3rd | 4th | 5th |
| GraphSAGE4 | N/A | 2nd | 3rd | 1st | 4th | 5th |
| GraphSAGE5 | N/A | 2nd | 1st | N/A | 3rd | 4th |
| GraphSAGE6 | N/A | 2nd | 1st | 3rd | 4th | 5th |
| GraphSAGE7 | N/A | 3rd | 1st | 2nd | 4th | 5th |
| GraphSAGE8 | N/A | 3rd | 2nd | 1st | 4th | 5th |
| GraphSAGE9 | N/A | N/A | 1st | N/A | 2nd | N/A |
| GraphSAGE10 | 1st | N/A | 2nd | N/A | 3rd | N/A |
| Dataset | Classify Type | Graph Type | k | Ranking | GraphSAGE Variant | Aver F1_Score | Std_Deviation | Max F1_Score | Aver Run Time (sec) | No. Runs |
|---|---|---|---|---|---|---|---|---|---|---|
| NF-BoT-IoT | Binary | Directed | 9 | 1 | GraphSAGE | 0.985222 | 0.000048 | 0.985298 | 8.58 | 6 |
| 2 | GraphSAGE9 | 0.985031 | 0.000212 | 0.985262 | 28.56 | 5 | ||||
| 3 | GraphSAGE5 | 0.974149 | 0.010756 | 0.985196 | 56.01 | 5 | ||||
| NF-BoT-IoT | Multi | Undirected | 10 | 1 | GraphSAGE | 0.840447 | 0.002994 | 0.843658 | 9.09 | 6 |
| 2 | GraphSAGE9 | 0.835847 | 0.006773 | 0.845202 | 33.69 | 5 | ||||
| 3 | GraphSAGE1 | 0.822281 | 0.018911 | 0.843293 | 48.28 | 5 | ||||
| NF-ToN-IoT | Binary | Directed | 7 | 1 | GraphSAGE9 | 0.999999 | 0.000002 | 1.000000 | 123.69 | 5 |
| 2 | GraphSAGE | 0.999997 | 0.000004 | 1.000000 | 43.75 | 6 | ||||
| 3 | GraphSAGE7 | 0.999992 | 0.000007 | 1.000000 | 990.92 | 5 | ||||
| NF-ToN-IoT | Multi | Undirected | 5 | 1 | GraphSAGE3 | 0.632464 | 0.013479 | 0.656238 | 929.90 | 5 |
| 2 | GraphSAGE6 | 0.628516 | 0.000215 | 0.628872 | 997.19 | 5 | ||||
| 3 | GraphSAGE | 0.628374 | 0.000500 | 0.628892 | 703.93 | 5 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ngo, T.; Yin, J.; Ge, Y.-F.; Wang, H. Optimizing IoT Intrusion Detection—A Graph Neural Network Approach with Attribute-Based Graph Construction. Information 2025, 16, 499. https://doi.org/10.3390/info16060499
Ngo T, Yin J, Ge Y-F, Wang H. Optimizing IoT Intrusion Detection—A Graph Neural Network Approach with Attribute-Based Graph Construction. Information. 2025; 16(6):499. https://doi.org/10.3390/info16060499
Chicago/Turabian StyleNgo, Tien, Jiao Yin, Yong-Feng Ge, and Hua Wang. 2025. "Optimizing IoT Intrusion Detection—A Graph Neural Network Approach with Attribute-Based Graph Construction" Information 16, no. 6: 499. https://doi.org/10.3390/info16060499
APA StyleNgo, T., Yin, J., Ge, Y.-F., & Wang, H. (2025). Optimizing IoT Intrusion Detection—A Graph Neural Network Approach with Attribute-Based Graph Construction. Information, 16(6), 499. https://doi.org/10.3390/info16060499






