Improving Physically Unclonable Functions’ Performance Using Second-Order Compensated Measurement
Abstract
1. Introduction
2. Related Work
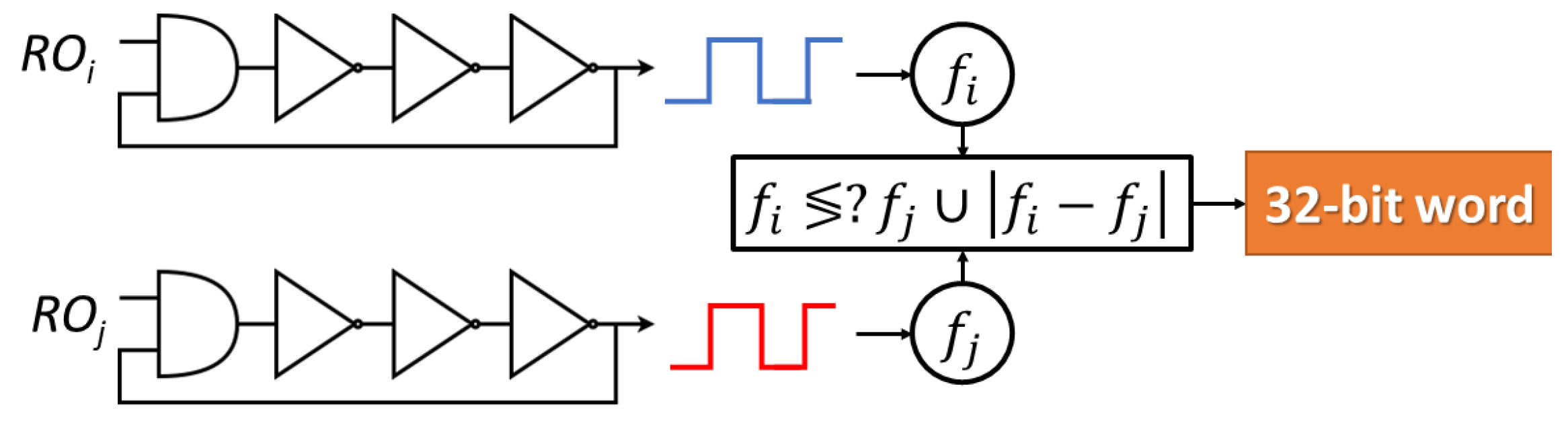
3. Second-Order Compensated Measurement
3.1. Description of the Proposal
3.2. Target Application
4. Implementation and Methodology
4.1. Experimental Setup
4.2. PUF Response Generation
5. Properties and Characteristic Parameters
5.1. Reproducibility, Uniqueness and Identifiability
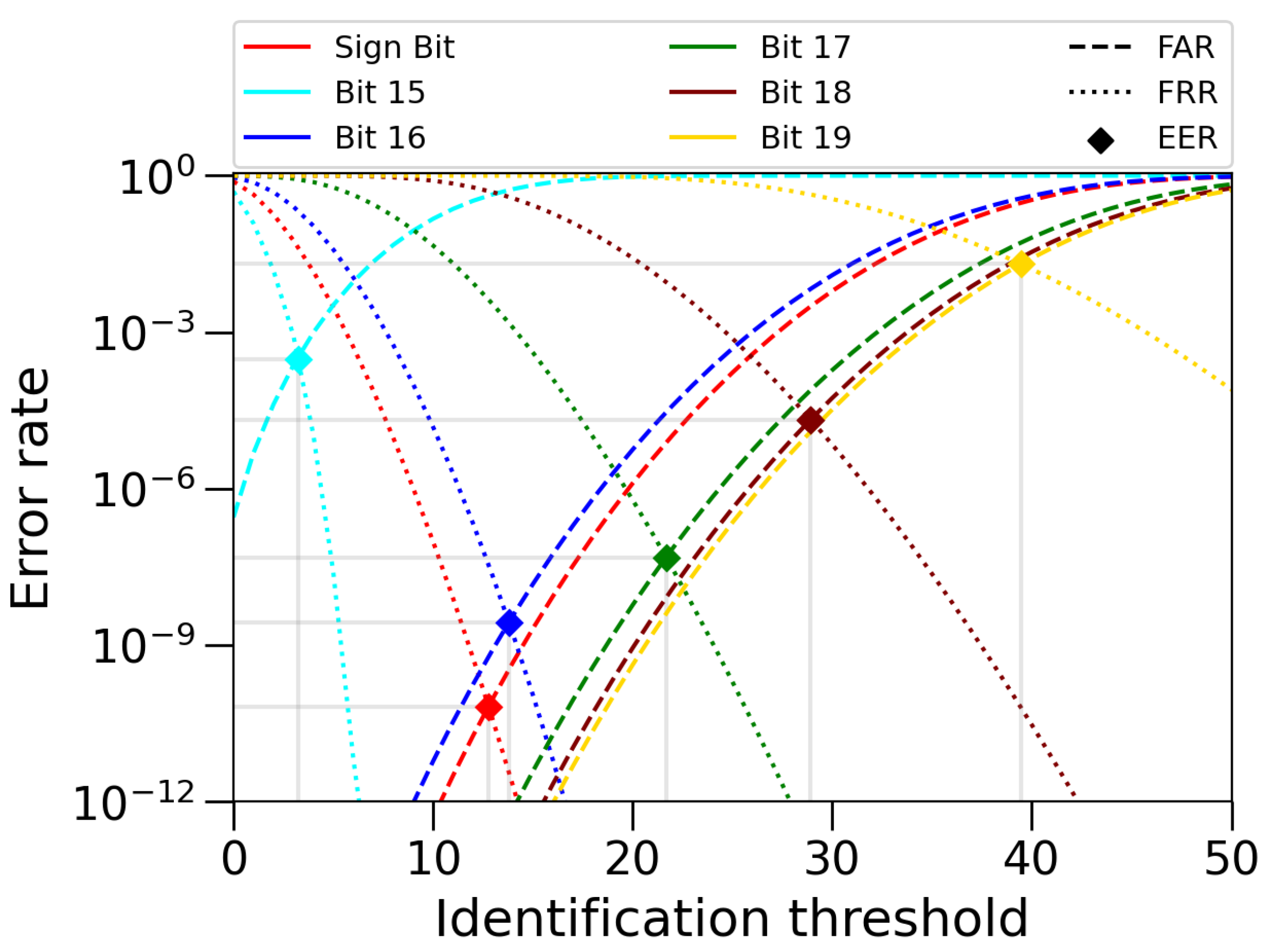
5.2. Identification Threshold: FAR and FRR
6. Results
6.1. PUF Analysis Using Single Bits
6.2. PUF Analysis Using the Sign Bit Together with Other Quality Bits
6.3. Entropy Analysis
6.4. Voltage and Temperature Variations
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| EER | Equal error rate. |
| FAR | False acceptance rate. |
| FPGA | Field-programmable gate array. |
| FRR | False rejection rate. |
| HD | Hamming distance. |
| IoT | Internet of Things. |
| PUF | Physically Unclonable Function. |
| RO | Ring oscillator. |
| ROC | Receiver operating characteristic. |
References
- Chen, Z.; Lee, W.; Hong, Q.; Gu, C.; Guan, Z.; Ding, L.; Zhang, J. A Lightweight and Machine-Learning-Resistant PUF Using Obfuscation-Feedback-Shift-Register. IEEE Trans. Circuits Syst. II Express Briefs 2022, 69, 4543–4547. [Google Scholar] [CrossRef]
- Mahalat, M.H.; Subba, S.; Mondal, A.; Sikdar, B.K.; Chakraborty, R.S.; Sen, B. CAPUF: Design of a configurable circular arbiter PUF with enhanced security and hardware efficiency. Integration 2023, 95, 102113. [Google Scholar] [CrossRef]
- Shifman, Y.; Shor, J. Preselection Methods to Achieve Very Low BER in SRAM-Based PUFs—A Tutorial. IEEE Trans. Circuits Syst. II Express Briefs 2022, 69, 2551–2556. [Google Scholar] [CrossRef]
- Lu, L.; Kim, T.T.-H. A High Reliable SRAM-Based PUF With Enhanced Challenge-Response Space. IEEE Trans. Circuits Syst. II Express Briefs 2022, 69, 589–593. [Google Scholar] [CrossRef]
- Anandakumar, N.N.; Hashmi, M.S.; Tehranipoor, M. FPGA-based Physical Unclonable Functions: A comprehensive overview of theory and architectures. Integration 2021, 81, 175–194. [Google Scholar] [CrossRef]
- Boke, A.K.; Nakhate, S.; Rajawat, A. FPGA implementation of PUF based key generator for secure communication in IoT. Integration 2023, 89, 241–247. [Google Scholar] [CrossRef]
- Cultice, T.; Thapliyal, H. PUF-Based Post-Quantum CAN-FD Framework for Vehicular Security. Information 2022, 13, 382. [Google Scholar] [CrossRef]
- Amsaad, F.; Niamat, M.; Dawoud, A.; Kose, S. Reliable Delay Based Algorithm to Boost PUF Security Against Modeling Attacks. Information 2018, 9, 224. [Google Scholar] [CrossRef]
- Maiti, A.; Schaumont, P. Improving the quality of a Physical Unclonable Function using configurable Ring Oscillators. In Proceedings of the 2009 International Conference on Field Programmable Logic and Applications, Prague, Czech Republic, 31 August–2 September 2009; pp. 703–707. [Google Scholar]
- Morozov, S.; Maiti, A.; Schaumont, P. An Analysis of Delay Based PUF Implementations on FPGA. In Reconfigurable Computing: Architectures, Tools and Applications: Proceedings of the 6th International Symposium, ARC 2010, Bangkok, Thailand, 17–19 March 2010; Sirisuk, P., Ed.; Proceedings 6; Springer: Berlin/Heidelberg, Germany, 2010; pp. 382–387. [Google Scholar]
- Maes, R. Physically Unclonable Functions: Concept and Constructions; Springer: Berlin/Heidelberg, Germany, 2012; pp. 11–48. [Google Scholar]
- Kodýtek, F.; Lórencz, R.; Buček, J. Improved ring oscillator PUF on FPGA and its properties. Microprocess. Microsyst. 2016, 47, 55–63. [Google Scholar] [CrossRef]
- Cherkaoui, A.; Bossuet, L.; Marchand, C. Design, Evaluation, and Optimization of Physical Unclonable Functions Based on Transient Effect Ring Oscillators. IEEE Trans. Inf. Forensics Secur. 2016, 11, 1291–1305. [Google Scholar] [CrossRef]
- Immler, V.; Hennig, M.; Kürzinger, L.; Sigl, G. Practical aspects of quantization and tamper-sensitivity for physically obfuscated keys. In Proceedings of the Third Workshop on Cryptography and Security in Computing Systems, Prague, Czech Republic, 20 January 2016. [Google Scholar]
- Tuyls, P.; Schrijen, G.J.; Škorić, B.; van Geloven, J.; Verhaegh, N.; Wolters, R. Read-Proof Hardware from Protective Coatings. In Cryptographic Hardware and Embedded Systems-CHES 2006: Proceedings of the 8th International Workshop, Yokohama, Japan, 10–13 October 2006; Goos, G., Ed.; Proceedings 8; Springer: Berlin/Heidelberg, Germany, 2006. [Google Scholar]
- Buchovecká, S.; Lórencz, R.; Kodýtek, F.; Buček, J. True random number generator based on ring oscillator PUF circuit. Euromicro Conf. Digit. Syst. Des. (DSD) 2017, 53, 33–41. [Google Scholar] [CrossRef]
- Mandry, H.; Herkle, A.; Müelich, S.; Becker, J.; Fischer, R.F.H.; Ortmanns, M. Normalization and Multi-Valued Symbol Extraction From RO-PUFs for Enhanced Uniform Probability Distributions. IEEE Trans. Circuits Syst. II Express Briefs 2020, 67, 3372–3376. [Google Scholar] [CrossRef]
- Baturone, I.; Román, R.; Corbacho, Á. A Unified Multibit PUF and TRNG Based on Ring Oscillators for Secure IoT Devices. IEEE Internet Things J. 2023, 10, 6182–6192. [Google Scholar] [CrossRef]
- Maes, R.; Herrewege, A.V.; Verbauwhede, I. PUFKY: A Fully Functional PUF-Based Cryptographic Key Generator. In Cryptographic Hardware and Embedded Systems—CHES 2012: Proceedings of the 14th International Workshop, Leuven, Belgium, 9–12 September 2012; Prouff, E., Ed.; Proceedings 14; Springer: Berlin/Heidelberg, Germany, 2012. [Google Scholar]
- Fernández-Aragón, J.; Diez-Senorans, G.; Garcia-Bosque, M.; Celma, S. Design and characterisation of a Physically Unclonable Function on FPGA using second-order compensated measurement. In Proceedings of the 2022 IFIP/IEEE 30th International Conference on Very Large Scale Integration (VLSI-SoC), Patras, Greece, 3–5 October 2022; pp. 1–2. [Google Scholar]
- Fernández-Aragón, J.; Diez-Senorans, G.; Garcia-Bosque, M.; Celma, S. Oscilador de anillo PUF en FPGA: Diseño y caracterización mediante el uso de la medición compensada de segundo orden. Jorn. Jóvenes Investig. I3A 2022, 10. [Google Scholar] [CrossRef]
- Suh, G.E.; Devadas, S. Physical Unclonable Functions for Device Authentication and Secret Key Generation. In Proceedings of the Design Automation Conference—DAC, San Diego, CA, USA, 4–8 June 2007; pp. 37–39. [Google Scholar]
- Díez-Senorans, G.; Garcia-Bosque, M.; Sánchez-Azqueta, C.; Celma, S. Digitization Algorithms in Ring Oscillator Physically Unclonable Functions as a Main Factor Achieving Hardware Security. IEEE Access 2021, 9, 147343–147356. [Google Scholar] [CrossRef]
- Garcia-Bosque, M.; Díez-Señorans, G.; Sánchez-Azqueta, C.; Celma, S. Introduction to Physically Unclonable Fuctions: Properties and Applications. In Proceedings of the 2020 European Conference on Circuit Theory and Design (ECCTD), Sofia, Bulgaria, 7–10 September 2020; pp. 1–4. [Google Scholar]
- Rukhin, A.; Soto, J.; Nechvatal, J.; Smid, M.; Barker, E. A Statistical Test Suite for Random and Pseudorandom Number Generators for Cryptographic Applications; 800-22 Revision 1.a; DTIC: Fort Belvoir, VA, USA, 2010. [Google Scholar]






| Property | Sign Bit | Bit 1 to 14 | Bit 15 | Bit 16 | Bit 17 | Bit 18 | Bit 19 | Bit 20 to 31 |
|---|---|---|---|---|---|---|---|---|
| Intra-HD (%) | 0.0 to | 45.266 to | ||||||
| Inter-HD (%) | 0.0 to | 49.919 to |
| Selected Bit | ||||||
|---|---|---|---|---|---|---|
| p-Value | Proportion | Pass? | p-Value | Proportion | Pass? | |
| Sign Bit | 0.002 | 38/40 | Yes | 0.001 | 39/40 | Yes |
| Bit 17 | 0.078 | 40/40 | Yes | 0.106 | 40/40 | Yes |
| Sign Bit + 17 | 0.312 | 40/40 | Yes | 0.187 | 40/40 | Yes |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Fernández-Aragón, J.; Diez-Señorans, G.; Garcia-Bosque, M.; Aparicio-Téllez, R.; López-Pinar, G.; Celma, S. Improving Physically Unclonable Functions’ Performance Using Second-Order Compensated Measurement. Information 2025, 16, 166. https://doi.org/10.3390/info16030166
Fernández-Aragón J, Diez-Señorans G, Garcia-Bosque M, Aparicio-Téllez R, López-Pinar G, Celma S. Improving Physically Unclonable Functions’ Performance Using Second-Order Compensated Measurement. Information. 2025; 16(3):166. https://doi.org/10.3390/info16030166
Chicago/Turabian StyleFernández-Aragón, Jorge, Guillermo Diez-Señorans, Miguel Garcia-Bosque, Raúl Aparicio-Téllez, Gabriel López-Pinar, and Santiago Celma. 2025. "Improving Physically Unclonable Functions’ Performance Using Second-Order Compensated Measurement" Information 16, no. 3: 166. https://doi.org/10.3390/info16030166
APA StyleFernández-Aragón, J., Diez-Señorans, G., Garcia-Bosque, M., Aparicio-Téllez, R., López-Pinar, G., & Celma, S. (2025). Improving Physically Unclonable Functions’ Performance Using Second-Order Compensated Measurement. Information, 16(3), 166. https://doi.org/10.3390/info16030166






