A Comprehensive Survey of Threats in Platooning—A Cloud-Assisted Connected and Autonomous Vehicle Application
Abstract
:1. Introduction
- The paper presents an comprehensive survey of the threat landscape for CCAVs, compiling an extensive list of 132 threats from the literature, 64 documented real-life incidents (with timeline), and 22 specific threats related to platooning microservices.
- The study maps out a detailed attack taxonomy using identified threats, outlining 8 unique attack vectors for understanding 48 threats in CCAVs and platooning applications.
- The research identified and defines significant trust domains in a three-tier CCAV system, including 11 for CCAV, 12 for edge cloud, and 8 for core cloud.
- The paper emphasises the need for further research on dynamic, multifaceted optimal security strategies, including continuous security lifecycle management, adaptive threat modeling, and the implementation of Zero Trust principles.
2. Methodology
3. Related Works
4. Advancements in Connected and Autonomous Vehicles
4.1. VANETS and Intelligent Transportation Systems
- Enhanced data exchange and precise data processing, leading to improved traffic safety and efficiency, ultimately resulting in standardised transportation [39].
- Collaborative vehicular applications that are networked with information-rich infotainment services.
- Proactive notification of real-time vehicle dynamics (location, speed, braking, etc.) by broadcasting awareness messages including unsafe and urgent local conditions (accidents, potholes, etc.) [40].
- An ecosystem whereby vehicles synchronise local events with CCAVs to make advanced analytical decisions.
- Standardised architectures result in the loss of distinctive competitive advantages;
- A standardised framework creates a single point of dependency, where any flaw in a dependent system can impact all vehicles;
- Establishing a national architecture and ensuring system-wide assurance poses significant challenges.
4.2. An Overview of CCAV
- Vehicle-to-Vehicle (V2V): Vehicles can communicate wirelessly with one another and preserve traffic safety by exchanging Basic Safety Messages (BSM) or Cooperative Awareness Messages (CAMs) to maintain a safe distance between vehicles, thus avoiding road accidents.
- Vehicle-to-Infrastructure (V2I): CCAVs and RSU are being developed to communicate with the external network (cloud, edge cloud, third-party, internet, etc.) by broadcasting or exchanging data related to road/traffic information and conditions in urban or highway scenarios. This is in addition to receiving the most up-to-date information about the local area. This enables vehicles to perform detailed analysis to make decisions based on the application. V2I-based applications are more bandwidth-intensive and require more CPU power than V2V-based applications [50].
- Cloud and Edge Cloud: The literature has proposed two-tier architectures for CCAV applications, such as platooning [51]. However, they fail to discuss the stringent criteria of safety-critical CCAV applications due to the expected exponential growth in latency caused by communication and distributed computation. To address this, an intermediate layer called edge cloud was introduced to facilitate fog computing [52,53]. The edge cloud facilitates low-latency localised computation for CCAVs by establishing continuous communication with trusted infrastructures such as the core cloud and reliable third-party services while minimising communication latency. Consequently, a three-tier architecture is being considered for CCAVs, as depicted in Figure 2 for the platooning use case. This architecture comprises the core cloud, edge cloud, CCAVs, third-party services, and RSU infrastructures, as highlighted in various studies [53,54,55,56]. All such hardware and associated software would contribute towards the dynamics of a fully operable CCAV. Further information about the characteristics of CCAVs using their communication capabilities is detailed in Table 3.
4.3. Key Communication Developments for CCAVs
4.4. CCAV Applications
- Information Services: Fault prediction and response, data collection and generation, data dissemination and distribution, efficiency improvement, and convenience services;
- Safety Services: Collision avoidance, hazard reporting, and driver profile and monitoring;
- Individual and Group Motion Control: Connected and autonomous driving and vehicular platooning.
- To support drivers with vehicles classified under specific SAE automation levels, ranging from Level 2 (Partial Automation) to Level 5 (Full Automation), by providing proactive collision warning signals to drivers, passengers, and pedestrians in order to reduce traffic accidents;
- To deliver real-time alerts to assist in traffic management by offering the most up-to-date road conditions and navigational services, as well as planned detours in the event of an accident;
- To provide value-added services, such as keeping track of a driver’s profile and a vehicle’s profile personalised entertainment options.
Platooning
- Formation: This functionality enables multiple CCAVs to come together and form a cohesive unit, typically through communication and coordination with other vehicles and traffic management systems;
- Management: This functionality encompasses tasks such as maintaining safe inter-vehicle distance, adjusting speed to match traffic conditions, and ensuring the safe and efficient operation of all vehicles in the platoon;
- Joining: This functionality allows integrating additional CCAVs into an existing platoon, typically through communication and coordination with the platoon leader and other vehicles;
- Leaving: This functionality allows for the safe exit of a CCAV from a platoon, typically through communication and coordination with the platoon leader and other vehicles;
- Merging: This functionality enables the consolidation of multiple platoons into a larger unit, typically through communication and coordination with the platoon leaders and other vehicles;
- Splitting: This functionality allows dividing a platoon into smaller units, typically through communication and coordination with the platoon leader and other vehicles;
- Ending: This functionality enables the safe dissolution of a platoon, typically through communication and coordination with the platoon leader and other vehicles;
- Leader Change: This functionality allows transferring leadership responsibility within a platoon, typically through communication and coordination with the current platoon leader and other vehicles.
5. Advancements in CCAV Security
5.1. Fundamentals of CCAV Security
- Confidentiality: CCAV systems should be capable of encrypting and decrypting data on a need-to-know basis. Data storage that is not confidential may result in data exposure, leading to potential data breaches and passive attacks such as eavesdropping.
- Integrity: Transmitted data packets will update the edge cloud and cloud. These include CAM, DENM, and value-added services. Data integrity checks protect against manipulation, alteration, or erasure. Validation tests using hash algorithms ensure data integrity during transmission and storage. Data integrity attacks include manipulation, fake data generation, and impersonation.
- Availability: To ensure uninterrupted access to safety-critical applications, the edge cloud and cloud systems must be resilient against hardware or software failures, power outages, and cyberattacks. Availability is essential. Denial-of-Service (DoS) attacks, jamming, greedy behaviour, blackholes, grey-holes, sinkholes, wormholes, broadcast manipulation, malware, and spam are all threats to the availability of CCAVs.
- Auditability, Traceability, Accountability, Non-Repudiation, and Revocability: Malicious messages can impact CCAVs, causing errors, incidents, and even accidents. Techniques for detecting altered data post-processing should exist for auditability. For example, CCAVs should record each message shared by the edge cloud using unique message IDs in order to create auditability and accountability. As a result, anomalies are monitored by the edge cloud’s Intrusion Detection System (IDS) and Intrusion Prevention Systems (IPS), and hostile nodes are identified and reported to the Trusted Authority (TA). This approach enables the withdrawal of security permissions for suspicious or malicious nodes and any other erroneous entities.
- Authenticity and Verifiability: CCAVs must develop confidence in the edge cloud and neighbouring vehicles. As a result, verifying the authenticity of messages is important for time-sensitive and safety-critical applications. Verifying messages for real-time situational awareness requires optimally efficient deterministic schemes. Tunnelling, node impersonation, GPS spoofing, and Sybil attacks are some techniques that may jeopardise the validity of messages (CAM/DENM/etc.).
- Privacy: Personally Identifiable Information (PII) of the vehicle owners, drivers, and passengers should not be disclosed by CCAV systems. For example, organisations may wish to share CCAV IDs with third-party organisations. Users should be given a choice to control their respective data. Long-term anonymity and differential privacy are some methods that are being researched to protect the CCAV system.
5.2. Key Developments for CCAV Security
5.2.1. Harmonization Task Groups
5.2.2. ISO 26262
- Modifications to existing systems and their components that have been deployed for production prior to the latest standard by customising the safety lifecycle for each modification;
- Integration of older systems by modifying the safety lifecycle;
- Tackles potential dangers resulting from the defective activities of safety-related E/E systems, including their interaction.
5.2.3. ISO/SAE 21434
- Develop policies for cybersecurity;
- Manage associated security risks;
- Foster developing security practices and culture within the organisation.
5.2.4. SAE J3061
- Integrating cybersecurity into cyber-physical vehicular systems across the development, manufacturing, operation, maintenance, and decommissioning processes;
- Describes some current tools and methodologies for creating, verifying, and validating CAV systems;
- Introducing key cybersecurity principles for automotive systems and establishing the framework for future vehicle security standards.
6. Threat Analysis
6.1. General Threats
6.1.1. Threats from the Literature
6.1.2. Threats from Real-Life Incidents
6.2. Platooning Threats
6.3. Impacted Trust Domains
- The trust domain “V-TD1” (Wireless Communications) has the highest number of platooning threats, followed by “V-TD11” (Devices and Peripherals) and “V-TD10” (Data Analysis). In the edge cloud and cloud, the trust domain “E-TD1, C-TD1” (Edge Communication) has the highest number of threats, followed by “E-TD12” (Roadside Infrastructures) and “E-TD5, C-TD2” (Edge Processing and Data Analysis). This suggests that these areas might be the most vulnerable in the context of platooning.
- The trust domain “V-TD9” (Actuators) has the highest number of real-life threats followed by “V-TD2, V-TD7” (Infotainment, Human Machine Interface (HMI)). In the edge cloud and cloud, the trust domain “E-TD6, C-TD5” (Data Storage) has the highest number of threats, followed by “E-TD12” (Roadside Infrastructures) and “E-TD3, C-TD4” (Application Program Interface (API)). This indicates that these domains have been exploited in real-world scenarios, and thus, require significant attention.
- The trust domain “V-TD4” (Vehicle Sensors) has the highest number of literature threats. This is because vehicle sensors are a critical component of autonomous vehicles and any compromise in their functioning can lead to subsequent inferences and severe consequences.
- Some trust domains, such as the Physical Input/Output, Monitoring, and Logging trust domains, have relatively fewer threats across all categories. However, this does not necessarily mean that they are less important. The impact of a threat also depends on the severity of its consequences; however, they may have a low likelihood.
7. Discussion
- It is seen that the number of threats affecting each trust domain gives us an idea of which trust domains present a high concentration of threats. For example, in the CCAV, trust domains “V-TD1”, “V-TD9”, “V-TD10”, and “V-TD11” are affected by most identified threats in L, R, and P. In the edge cloud, the trust domains “E-TD1”, “E-TD2”, “E-TD5”, “E-TD6”, and “E-TD12” are affected by most identified threats in L, R, and P. This suggests that these trust domains may be more vulnerable and may require additional security measures discussed in Section 8. In addition, from analysing platooning, it is also observed that the ’Black Hole’ threat appears across all trust domains in both the edge cloud and CCAV, which indicates it is a threat that can have severe consequences if an adversary can exploit it.
- The comparison between the edge cloud and CCAV shows that the distribution of threats across trust domains is different. This suggests that the security measures and strategies may need to be tailored differently for the edge cloud and CCAV.
- The frequency of threats across trust domains can help in prioritising security measures. Trust domains that are associated with a higher number of threats or with more severe threats might need to be prioritised.
- The bar graphs can also be used for security planning. By knowing which trust domains are most affected by threats, security teams can plan and allocate resources more effectively. For example, more resources might need to be allocated to protect trust domains that are affected by a higher number of threats. This information can be used to develop targeted security measures for each trust domain based on the threats they are most likely to face.
8. Open Challenges
8.1. Addressing Security Concerns in the Lifecycle Management of CCAV Systems
8.2. Enhancing CCAV Security through Adaptive Threat Modeling and Dynamic Risk Assessment
8.3. Securing a Resource Constrained CCAV System
8.4. Developing a Multi-Dimensional Approach to Strengthening CCAV Systems
8.5. Embracing Zero Trust Principles for Enhanced Security in Dynamic Environments
8.6. Assessing, Prioritising, and Mitigating Privacy Risks
8.7. Addressing Data Scarcity
9. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Appendix A
| CCAV Applications | ||
|---|---|---|
| V2I Safety | Environment | Mobility |
| Red Light Violation Warning | Eco-Approach and Departure at Signalised Intersections | Advanced Traveller Information System |
| Curve Speed Warning | Eco-Traffic Signal Timing | Intelligent Traffic Signal System |
| Stop Sign Gap Assist | Eco-Traffic Signal Priority | Signal Priority (transit, freight) |
| Stop Weather Impact Warning | Information Disclosure | CCAV platooning |
| Reduced Speed/Work Zone Warning | Connected Eco-Driving | Mobile Accessible Pedestrian Signal System |
| Pedestrian in signalised crosswalk warning | Wireless Inductive/Resonance Charging | Emergency Vehicle Preemption |
| V2V Safety | Eco-Lanes Management | Dynamic Speed Harmonisation |
| Emergency Electronic Brake Lights | Eco-Cooperative Adaptive Cruise Control | Queue Warning |
| Forward Collision Warning | Eco-Speed Harmonisation | Cooperative Adaptive Cruise Control |
| Intersection Movement Assist | Eco-Cooperative Adaptive Cruise Control | Incident Scene Pre-Arrival Staging |
| Left Turn Assist | Eco-Traveler Information | Guidance for Emergency |
| Blind Spot/Lane Change Warning | Eco ramp metering | Responders |
| Do not pass warning | Low-emission zone management | Incident Scene Work Zone Alerts for Drivers and Workers |
| Vehicle turning right in front of bus warning | AFV Charging/Fueling Information | Emergency communications and evacuations |
| Agency Data | Eco-Smart Parking | Connection Protection |
| Probe-based pavement maintenance | Dynamic Eco-Routing | Dynamic Transit Operations |
| Probe-enabled traffic monitoring | Decision Support System | Dynamic Ridesharing |
| Vehicle classification based traffic studies | Road Weather | Freight-specific Dynamic Travel planning and performance |
| Turning Movement and Intersection Analysis | Motorist Advisories and Warnings | Drayage Optimisation |
| Origin Destination Studies | Enhanced MDSS | Smart Roadside |
| Work zone traveller information | Vehicle Data Translator | Wireless Inspection |
| Weather Response Traffic Information | Smart Truck Parking | |
| CCAV Platooning Attacks | |||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| PL-IC | Threat | CCAV TD | Edge TD | STRIDE | F | M | J | L | Mg | S | E | CL | Threat Description |
| PL-IC1 | Covert Channel | V-TD1, V-TD3, V-TD9, V-TD10, V-TD11 | E-TD1, E-TD2, E-TD5, E-TD6, E-TD12 | S, T, D, E | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
|
| PL-IC2 | Black Hole | V-TD1, V-TD3, V-TD10, V-TD11 | E-TD1, E-TD2, E-TD5, E-TD6, E-TD12 | S, T, D, E | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
|
| PL-IC3 | Worm Hole | V-TD1, V-TD10 | E-TD1, E-TD2 | T, D, E | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| |
| PL-IC4 | Packet dropping | V-TD1, V-TD3, V-TD10, V-TD11 | E-TD1, E-TD2, E-TD5, E-TD6, E-TD12 | S, T, D, E | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
|
| PL-IC5 | Jamming Attack | V-TD1, V-TD10 | E-TD1, E-TD2 | D | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
|
| PL-IC6 | Jamming and Spoofing Sensors | V-TD1, V-TD4, V-TD11 | E-TD1, E-TD2, E-TD5, E-TD12 | S, T, D | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
|
| PL-IC7 | False Data injection | V-TD1, V-TD10, V-TD11 | E-TD1, E-TD2, E-TD5, E-TD12 | T, D | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
|
| PL-IC8 | Eaves- dropping | V-TD1, V-TD11 | E-TD1, E-TD12 | I |
| ||||||||
| PL-IC9 | Data collection and Information theft | V-TD1, V-TD11 | E-TD1, E-TD12 | I |
| ||||||||
| PL-IC10 | Location Disclosure | V-TD1, V-TD11 | E-TD1, E-TD12 | I |
| ||||||||
| PL-IC11 | Man-in-the-Middle | V-TD1, V-TD10, V-TD11 | E-TD1, E-TD2, E-TD5, E-TD9, E-TD6, E-TD12 | T, D | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
|
| PL-IC12 | Tunnel Attack | V-TD1, V-TD6, V-TD10, V-TD11 | E-TD1, E-TD3, E-TD12 | S, T, E | ✓ | ✓ | ✓ | ✓ | ✓ |
| |||
| PL-IC13 | Fake Positioning | V-TD1, V-TD11, V-TD4, V-TD10 | E-TD1, E-TD2, E-TD5, E-TD12 | S, T | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| ||
| PL-IC14 | Fake Manoeuvering | V-TD1, V-TD11, V-TD4, V-TD10, V-TD9 | E-TD1, E-TD2, E-TD5, E-TD12 | S, T, D, E | ✓ | ✓ | ✓ | ✓ | ✓ |
| |||
| PL-IC15 | Session Hijack | V-TD1, V-TD10, V-TD11 | E-TD3, E-TD5, E-TD10 | S, D | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
|
| PL-IC16 | Malware or Ransomware | ALL | ALL | S, T, R, I, D, E | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
|
| PL-IC17 | Repudiation attack | ALL | E-TD1, ETD2, E-TD5, E-TD12 | S, R, E | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
|
| PL-IC18 | Flooding | V-TD1, V-TD3, V-TD10, V-TD12 | E-TD1, E-TD2, E-TD5, E-TD6, E-TD3, E-TD12 | T, D | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
|
| PL-IC19 | Replay attack | V-TD1, V-TD4, V-TD9, V-TD10, V-TD11 | E-TD1, E-TD6, E-TD10, E-TD11 | S | ✓ | ✓ | ✓ | ✓ |
| ||||
| PL-IC20 | Impersonation Attack | ALL | E-TD1, E-TD2, E-TD5, E-TD12 | S, E | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
|
| PL-IC21 | Illusion Attack | V-TD1, V-TD3, V-TD4, V-TD11 | E-TD1, E-TD3, E-TD5, E-TD12, E-TD6, E-TD11 | S, T | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| |
| PL-IC22 | Sybil Attack | V-TD1, V-TD10, V-TD6, V-TD11 | E-TD1, E-TD2, E-TD5, E-TD6, E-TD11, E-TD12 | S, R, D, E | ✓ | ✓ | ✓ | ✓ |
| ||||
| CCAV Reference Architecture | ||
|---|---|---|
| Trust Domain | Data Process | Description |
| V-TD1: Wireless Communication | Data Transmission | CAVs communicate with the Edge Cloud, other cars, and CAVs, possible technologies linked to road users, infrastructures, and radio stations on a frequent basis, depending on the receiver and transmitter’s position and vicinity. DSRC, 5G, 4G/LTE, and other protocols may be used for sharing data, depending on the application. |
| V-TD2: Infotainment | Physical Interaction and Data Transmission | It is a group of hardware and software components installed in automobiles that offer audio and visual entertainment. It began with radios with cassette or CD players and has expanded to include navigation systems, video players, USB and Bluetooth connection, internet, and WiFi. Examples include CarPlay and Android Auto. The internal components (wireless communication module, I/O ports and data storage) can transmit data to this module |
| V-TD3: Data Storage | Database Access | Vehicles would need storage for data related to audio, video, maps, firmware and its versions, and vehicle status. These records are partitioned and securely stored. |
| V-TD4: Vehicle Sensors | Data Processing | Vehicles are often equipped with a plethora of sensors that monitor the vehicle’s motion dynamics and vehicle system. GNSS, LIDAR, RADAR, and cameras are all important sensors for CAVs. Additionally, sensors such as tyre pressure monitoring sensors, light sensors, parking sensors, wheel and vehicle speed sensors, and others are considered in this study. |
| Physical Interaction | The on-board sensors may be exposed to environment specific threats, | |
| V-TD5: Physical Input/Outputs | Physical Interaction | This module refers to the physical inputs and outputs on the device, such as the USB port and the on-board diagnostic port (OBD-II), Type1-4 battery chargers. It is difficult to exploit these ports since they need physical access. |
| V-TD6: Monitoring | Data processing | This module is used to describe the vehicle’s monitoring function. Here, the vehicle’s operation is verified against its specifications, its history is verified, and the vehicle’s maintenance is documented and logged. A good commercial example is the black box. |
| V-TD7: HMI | Phy. interaction, data processing & trans. | The Human–Machine Interface (HMI) is a collection of hardware and software elements that enables an individual to engage actively with the CAV system. It may be used as a user interface for steering wheels equipped with sophisticated on-board displays. |
| V-TD8: Energy System | Physical Interaction | The on-board energy system may be vulnerable to environmental challenges. It mainly consists of batteries and a fuel tank (petrol or diesel). |
| V-TD9: Actuators | Data Processing | This module discusses components that have the potential to influence the physical environment. This includes adjusting the wheel speed and angle, activating the brakes, air conditioning, and windows, as well as locking the doors and trunk. |
| Physical Interaction | Physical components receive their energy unit to interact with the environment | |
| V-TD10: Data Analysis | Data Processing | This module is in charge of conducting analysis on the data that have been saved. This might be for data localisation, object recognition, sensor fusion and analysis, action engine decision-making, vehicle control automation, warning, and basic safety message analysis, as well as vehicular applications. |
| Physical Interaction | Physical components receive their energy unit to interact with the environment | |
| V-TD11 Devices and Peripherals | Data Processing and Physical interaction | Smartphones, Bluetooth devices, laptops, and desktop computers are all examples of devices and peripherals. Admins, users, and operators would use these devices to communicate with CCAV and devices to use the system. These are additional methods via which an adversary may breach the system. COHDA units are used to represent roadside infrastructure. These devices would be utilised by traffic controllers, CAVs, and other edge devices to carry out ITS-based prompts. |
| Edge Cloud Reference Architecture | ||
|---|---|---|
| Trust Domain | Data Process | Description |
| E-TD1: Wireless Communication | Data Transmission | The communication module presented here is expected to establish wireless connections with nearby automobiles, cloud technologies, RSI, and other peripheral devices through a cellular network or DSRC. They are also linked through fibre optic cables to the Wide Area Network (WAN). |
| E-TD2: Microservices | Data Processing and data transmission | The microservices module is in charge of offering services that are composed of multiple services. They are well known for providing unique services through facilitating scalability and testing. For example, intersection management. |
| E-TD3: API | Data transmission and interaction | Application Program Interfaces (APIs) are used by users and software modules to get access to a specific service. |
| E-TD4: Physical I/O | Phy. interaction & data trans. | Connection to the Edge infrastructure is made possible via the Physical IO ports. Physical security mechanisms should be used to protect these ports from physical attack. Users connecting over these ports should be properly authenticated, and digital records of these connection attempts should be maintained. |
| E-TD5: Process & Data Analysis | Data Processing | Actuators on the edge may have an effect on the surroundings. The edge may be capable of altering the behaviour and security of cars. |
| E-TD6: Data Storage | Database access | Data storage at the Edge will be centralised in a single piece of memory hardware. Due of its exposure to manipulation, it is critical to provide safeguards such as encryption, access control, and authentication to the whole disc to prevent threats. |
| E-TD7: Energy System | Physical Interaction | Electricity will be used to power edge systems. Alternative energy sources (such as batteries and renewable energy sources such as solar) may be employed in places where supplying electricity is difficult. |
| E-TD8: Actuators | Physical Interaction | Actuators on the edge may have an effect on the surroundings. The edge may be capable of altering the behaviour and security of cars. |
| E-TD9: Monitoring | Data Processing | Both the Edge and the Cloud will need to keep track of their activities. This enables analysts to comprehend why a certain series of events happened. They will also be required to comprehend the system’s performance characteristics. |
| E-TD10: Sensors | Data Processing and transmission | The Edge is equipped with both internal and exterior sensors. Individual devices inside an edge may have sensors that provide information about the status of the environment within the systems. Meanwhile external sensors may provide information about the edge of its environment, such as its surroundings. |
| E-TD11: Devices | Data Processing and transmission | Smartphones, Bluetooth devices, laptops, and desktop computers are all examples of devices and peripherals. Admins and operators would use these devices to communicate with the edge in order to maintain or operate the system. These are additional methods via which an adversary may breach the system. |
| E-TD12: Roadside Infrastructures | Physical interaction, data processing and transmission | COHDA units are used to represent roadside infrastructure. These devices would be utilised by traffic controllers, CAVs, and other edge devices to carry out ITS activities. |
| Cloud Reference Architecture | ||
|---|---|---|
| Trust Domain | Data Process | Description |
| C-TD1: Wireless Communication | Data Transmission | Cloud communication presents a significant challenge due to the need for advanced scalability, performance, dependability, durability, and resilience. To achieve optimal results, the cloud must feature a sophisticated architecture consisting of multiple edge clouds interconnected via multiple gateways, operating with maximum efficiency. |
| C-TD2: Data analysis | Data processing and data transmission | Advanced data analysis in the cloud due to large data volume enables various functionalities such as traffic control and timely distribution. The cloud predicts future trends by evaluating data from edge requests. |
| C-TD3: Microservices | Data processing and data transmission | The microservices module is responsible for delivering services comprised of multiple individual services. It is renowned for its ability to provide unique services while promoting scalability and ease of testing, for example, Intersection management. |
| C-TD4: APIs | Physical Interaction and data transmission | Application Program Interfaces (APIs) are used by users and software modules to get access to a specific service. |
| C-TD5: Data storage | Data Processing | Edge data storage will be centralised in memory hardware. Given its susceptibility to manipulation-based attacks, it is imperative to implement security measures such as encryption, access control, and authentication to secure the entire disk. The Edge’s actuators can impact the environment and have the potential to modify the behavior and security of vehicles. |
| C-TD6: Monitoring and Logging | Data Processing | Cloud-based decisions made while monitoring the environment, traffic, and other characteristics are saved for future verification. This would allow assessment in the event of a system anomaly or real-world mishap. This is a characteristic of accountability. |
| C-TD7: Physical I/O | Physical Interaction | Connection to the Cloud infrastructure is made possible via the Physical IO ports. Traffic Operators connect over these ports to access, update, create, delete, and maintain services. Such personnel should be properly authenticated, and digital records of these connection attempts is to be maintained. |
| C-TD8: Energy Systems | Physical Interaction | Cloud data storage is vulnerable to natural disasters, power outages, cyber attacks, and human errors that can cause data loss and breaches. Energy providers must implement security measures, backups, and redundancies with disaster recovery plans whilst being informed on current threats. |
| Trust Domain | Entry Point | Threat Description | Impact |
|---|---|---|---|
| V-TD1: Wireless Communication (Wifi, Cellular, 5G/LTE) | Wireless Communication (Wifi, 5G/LTE) |
|
|
| Long-range cellular wireless access [104] |
|
| |
| V-TD2: Infotainment, V-TD7: HMI |
|
|
|
|
|
| |
| V-TD3: Data Storage |
|
|
|
| V-TD4: Vehicle Sensors | Camera [104] |
| |
| Ultrasonic [121] |
|
| |
| LIDAR [104,122,123] |
|
| |
| Global Navigation Satellite System (GNSS) [124] |
|
| |
| Global Navigation Satellite System (GNSS) [124] |
|
| |
| Auxiliary Sensors: Vehicle’s custom telematics features such as UConnect. This includes on-board connectivity feature using wireless sensors and CAN bus vulnerabilities |
|
| |
| V-TD5: Physical Input/Outputs |
|
|
|
| V-TD6: Monitoring | White box and black box attack |
|
|
| V-TD8: Energy System | Energy and fuel storage, power generation |
|
|
| V-TD9: Actuators | Body Control Module (BCM) |
|
|
| V-TD9: Actuators | Electronic Control Module (ECM) |
|
|
| Electronic Brake Control Module (EBCM) |
|
| |
| Autolock feature for doors, trunk, charging port and fuel lid—Passive key less entry system—Key fob [138] |
|
| |
| Autolock doors and trunk- Passive key less entry system—Key fob [104] |
|
| |
| V-TD10: Data Analysis |
|
| |
|
|
| |
| V-TD11: Devices and Peripherals |
|
|
|
|
|
|
| Trust Domain | Entry Point | Threat Description | Impact |
|---|---|---|---|
| E-TD1, C-TD1 Edge/Cloud Communication (Wifi, Cellular, 5G/LTE) | Wireless Communication (Wifi, 5G/LTE) |
|
|
| E-TD2, C-TD3: Microservices | Wireless communication, virtualisation servers |
|
|
| E-TD3, C-TD4: API | Local infrastructure interface, Vehicle-to-Car Interfaces |
|
|
| E-TD4, C-TD7: Physical Input/Outputs | Edge ports with devices and peripherals |
|
|
| E-TD5, C-TD2: Edge Process & Data Analysis | Wrong data, protocols and data from communication, microservices and data storage module [25,103] |
|
|
| E-TD6, C-TD5: Data Storage |
|
|
|
| E-TD7, CTD8: Energy System | Energy and Fuel Storage, Power Generation |
|
|
| E-TD8: Actuators | Edge processing and physical access |
|
|
| E-TD9, C-TD6: Monitoring | White box and black box attack |
|
|
| E-TD10: Edge Sensors | Internal sensors which relies on the network layer [172] |
|
|
| External sensors include rain sensors, pH sensors, smart meters, temperature sensors, humidity sensors, sound sensors, vibration sensors, chemical sensors, pressure sensors [172] |
| ||
| E-TD11: Devices | User devices (insider, guest, bring-your-own-device for employees) [104] |
|
|
| E-TD12: Roadside Infrastructure | These devices could be end-notes such as COHDA units or internet-of-things devices |
|
|
| Real Life Incidents | ||||
|---|---|---|---|---|
| RL-IC | TD | Date | Incident Title | Threat Description |
| RL-IC0 [162] | E-TD6, E-TD11, C-TD5 | 08-Aug-11 | First remote hack of a vehicle, gaining control of a Chevy Malibu was established |
|
| RL-IC1 [162] | E-TD6, E-TD11, C-TD5 | 26-Jun-15 | Information on 100,000 Citroen owners may have been leaked |
|
| RL-IC2 [72] | V-TD1, V-TD9 | 21-Jul-15 | Jeep and Chrysler can be remotely hijacked, Chrysler recalls 1.4 million cars and trucks |
|
| RL-IC3 [97,175] | V-TD1, V-TD11, V-TD9 | 30-Jul-15 | GM’s Onstar system has a security flaw |
|
| RL-IC4 [139] | V-TD9 | 25-Dec-15 | Volvo, BYD, Buick Regal door lock remote control rolling code mechanism is bypassed |
|
| RL-IC5 [159] | E-TD3, C-TD4 | 24-Feb-16 | Controlling vehicle features of Nissan Leafs across the globe via vulnerable APIs |
|
| RL-IC6 [105] | C-TD1,V-TD2, C-TD4, C-TD3, C-TD5 | 06-Mar-16 | C4max TGU is improperly configured and exposed to the public network |
|
| RL-IC7 [98] | V-TD1, V-TD9 | 05-Jun-16 | Pen test partners controls Mitsubishi Outlander with Wi-Fi |
|
| RL-IC8 [106] | V-TD9, V-TD3, V-TD2 | 08-Aug-16 | Mirrorlink buffer overflow vulnerability |
|
| RL-IC9 [158] | E-TD11, V-TD11 | 25-Apr-17 | Hyundai blue link phone app information leaked |
|
| RL-IC10 [107] | V-TD2, V-TD11 | 23-May-17 | BMW 330i 2011 format string DoS vulnerability (CVE-2017-9212) |
|
| RL-IC11 [108] | V-TD7, V-TD2-D, V-TD11, E-TD12, E-TD5 | 27-Jul-17 | Vulnerabilities in Ford, BMW, Infiniti, and Nissan TCUs can be hacked remotely |
|
| RL-IC12 [99] | V-TD2, V-TD1, V-TD10, V-TD9 | 30-Apr-18 | Volkswagen, Audi in-vehicle entertainment system vulnerabilities |
|
| RL-IC13 [140] | V-TD9 | 10-Sep-18 | Hackers can copy keys to steal Tesla model s in seconds (CVE-2018-16806) |
|
| RL-IC14 [156] | V-TD11, E-TD12 | 14-Oct-18 | An online car-hailing driver was jailed for stealing electricity 382 times in half a year using the pinch gun method and card second method |
|
| RL-IC15 [115] | V-TD3, V-TD5 | 28-Nov-18 | FHI Subaru Starlink Harman local update verification flaw (CVE-2018-18203) |
|
| RL-IC16 [134] | V-TD8, V-TD11 | 13-Dec-18 | Chargepoint’s home chargers have multiple vulnerabilities |
|
| RL-IC17 [141] | V-TD9 | 03-May-19 | Ford key vulnerability replay attack |
|
| RL-IC18 [109] | V-TD4 | 19-Jun-19 | Tesla model 3 GPS spoofing |
|
| RL-IC19 [163] | V-TD2, V-TD3 | 14-Jul-19 | 10,000 USD XSS vulnerability in Tesla |
|
| RL-IC20 [127] | C-TD5 | 31-Jul-19 | Honda leaks 40 GB of internal data due to improper database configuration |
|
| RL-IC21 [157] | V-TD11, C-TD5 | 19-Oct-19 | Mercedes-Benz app can see other car owners’ information in the US’ explosion security breach |
|
| RL-IC22 [142] | V-TD11, V-TD9 | 14-Nov-19 | Tesla iBeacon privacy leak |
|
| RL-IC23 [100] | V-TD1, V-TD3 | 02-Jan-20 | Exploitation of Marvell wireless protocol stack vulnerabilities on Tesla Model S |
|
| RL-IC24 [119] | V-TD10 | 19-Feb-20 | Using machine learning to adversarially attack Telsa and Mobileye’s ADAS |
|
| RL-IC25 [164] | V-TD7, V-TD9 | 23-Mar-20 | Tesla model 3 central control denial of service vulnerability (CVE-2020-10558) |
|
| RL-IC26 [110] | V-TD9, V-TD2 | 30-Mar-20 | Tencent keen lab: Lexus car safety research summary report |
|
| RL-IC27 [135] | C-TD5 | 18-May-20 | Mercedes-Benz on-board logic unit (OLU) source code leaked |
|
| RL-IC28 [155] | E-TD12, V-TD11 | 28-May-20 | CVE-2020-12493: traffic lights exposed serious loopholes, which can be manipulated to cause traffic paralysis |
|
| RL-IC29 [94] | V-TD1, V-TD2, E-TD1, E-TD2, E-TD3 | 20-Jul-20 | 360 Sky-Go team releases Mercedes-Benz security research report: 19 vulnerabilities, work together to fix |
|
| RL-IC30 [130] | V-TD4 | 23-Jul-20 | Tesla NFC relay attack (CVE-2020-15912) |
|
| RL-IC31 [173] | E-TD12 | 24-Oct-20 | There are serious security loopholes in non-inductive payment charging piles, and there are hidden dangers of stealing brushes |
|
| RL-IC32 [111] | V-TD2, V-TD3 | 10-Nov-20 | CVE-2020-28656: VW Polo local upgrade check bypass |
|
| RL-IC33 [117] | V-TD9, V-TD11, V-TD3 | 23-Nov-20 | Tesla Model X bluetooth key vulnerability |
|
| RL-IC34 [143] | V-TD2, V-TD9 | 28-Apr-21 | Two white-hat hackers ’hacked’ Tesla with drones |
|
| RL-IC35 [79] | V-TD2 | 21-May-21 | Tencent keen lab: Mercedes-Benz car information security research summary report |
|
| RL-IC36 [144] | V-TD9, V-TD11 | 04-Jun-21 | Canadian programmers discover Bluetooth key vulnerability that allows anyone to unlock a Tesla |
|
| RL-IC37 [165] | C-TD5 | 11-Jun-21 | Data of 3.3 million Volkswagen customers leaked |
|
| RL-IC38 [166] | C-TD5 | 24-Jun-21 | The data of nearly 1000 Mercedes-Benz users were leaked, including driver’s license and credit card information |
|
| RL-IC39 [160] | E-TD12, E-TD5 | 13-Jul-21 | Schneider charging pile vulnerability |
|
| RL-IC40 [145] | V-TD9 | 04-Aug-21 | Honda Accord, Civic, Acura, and other vehicles have wireless key replay attack vulnerabilities |
|
| RL-IC41 [153] | V-TD10 | 17-Aug-21 | QNX is affected by the Badalloc vulnerability |
|
| RL-IC42 [95] | V-TD1 | 22-Sep-21 | The man blocked with a melon seed bag and evaded fees 22 times worth over 40,000 CNY in 3 months |
|
| RL-IC43 [167] | C-TD5 | 20-Dec-21 | Volvo cars reveals security breach that led to R&D data being stolen |
|
| RL-IC44 [146] | V-TD9 | 31-Dec-21 | There is a defect in the rolling code of the Honda car key, and the wireless signal can be replayed (CVE-2021-46145) |
|
| RL-IC45 [168] | C-TD5 | 01-Mar-22 | Supplier hit by cyber attack, Toyota shuts all factories in Japan for one day |
|
| RL-IC46 [147] | V-TD9 | 13-Mar-22 | Replay vulnerability in Tesla charging cover (CVE-2022-27948) |
|
| RL-IC47 [169] | C-TD5 | 14-Mar-22 | Denso German branch was attacked by cyber attack and 1.4tb of data were stolen |
|
| RL-IC48 [148] | V-TD9 | 25-Mar-22 | Honda car keyless entry system replay attack (CVE-2022-27254) |
|
| RL-IC49 [161] | E-TD12, E-TD5 | 29-Apr-22 | Xingyu lab discloses a variety of charging pile vulnerabilities |
|
| RL-IC50 [149] | V-TD9 | 15-May-22 | Tesla Model3/Y Bluetooth relay attack |
|
| RL-IC51 [150] | V-TD9 | 09-Jun-22 | Create any Tesla bluetooth key |
|
| RL-IC52 [112] | V-TD2 | 12-Jun-22 | Hyundai/Kia local upgrades cracked |
|
| RL-IC53 [151] | V-TD9 | 07-Jul-22 | Rolling pawn: wireless key rolling code rollback vulnerability |
|
| RL-IC54 [128] | C-TD4, V-TD4 | 19-Jul-22 | Micodus vehicle tracker security vulnerability affects over a million cars worldwide |
|
| RL-IC55 [113] | V-TD4, V-TD7 | 23-Aug-22 | Some brands of cars in Shanghai display screen prompts “there is a gunfight on the road?” |
|
| RL-IC56 [129] | V-TD4, V-TD10 | 01-Sep-22 | Yandex taxi was manipulated by hackers, and there was a traffic jam in Moscow |
|
| RL-IC57 [170] | C-TD5 | 02-Oct-22 | 6.99 GB of internal files leaked from Italian supercar maker Ferrari |
|
| RL-IC58 [96] | V-TD9, V-TD1 | 30-Nov-22 | Internet of vehicles service provider Sirius XM API vulnerability, unauthorised remote control of Honda, Nissan, Infiniti, and Acura cars |
|
| RL-IC59 [96] | E-TD3, C-TD4 | 30-Nov-22 | Hyundai, Genesis auto account hijacking |
|
| RL-IC60 [174] | E-TD12 | 07-Dec-22 | Replay attack: numerous traffic lights in Germany are vulnerable to manipulation |
|
| RL-IC61 [101] | V-TD1, V-TD2, V-TD3 | 07-Dec-22 | Multiple vulnerabilities disclosed in Black Hat Europe VW iD series |
|
| RL-IC62 [171] | C-TD5 | 20-Dec-22 | Nio data leaked and blackmailed |
|
| RL-IC63 [152] | V-TD9 | 31-Dec-22 | Luxury cars are gone in 90 s with thief kit |
|
| Attack Vector | |||
|---|---|---|---|
| Attack Level 1 | Attack Level 2 | Attack Level 3 | Description |
| Manipulate System Resources | Infrastructructure Manipulation | Black Hole Attack [65] | In a platooning context, a black hole attack involves a malicious vehicle falsely advertising itself as having the shortest path to the destination. This leads other vehicles to send data through it, but the malicious vehicle drops all the packets, disrupting communication and coordination. This attack can cause significant disruptions in platooning operations, including loss of critical data and misguiding the platoon about route and safety-related information. It undermines the integrity and availability of the platooning system, posing risks to both operational efficiency and vehicle safety. |
| Engage in deceptive intersections | Identity spoofing | Sybil Attack [176] | A Sybil attack involves a single malicious vehicle creating multiple fake identities to gain a disproportionate influence in the platooning network. This can lead to manipulation of collective platooning decisions, such as route selection or speed adjustments, and can disrupt the normal operation of the platoon. The attack undermines the trust and authenticity within the platooning system, posing significant challenges to its coordination and safety mechanisms. |
| Subvert access control | Exploiting trust in client | Man-In-the-Middle [177] | In this attack, an attacker intercepts and potentially alters the communication between two platooning vehicles without their knowledge. This can result in the leakage of sensitive information or introduction of false commands. It can severely impact the decision-making process in platooning, as altered commands or data can lead to incorrect manoeuvres, increasing the risk of collisions or inefficient routing. This attack compromises the confidentiality and integrity of the platoon’s communication, leading to potential operational and safety hazards. |
| Abuse existing functionality | Flooding | Flooding attack [178] | A flooding attack in a platooning system involves overwhelming the network with excessive traffic, which can lead to delays or blocking of legitimate communication among the vehicles. This could result in reduced responsiveness of the platoon to dynamic traffic conditions, increasing the risk of accidents and reducing operational efficiency. The attack primarily affects the availability of the platoon network, leading to potential communication and coordination failures. |
| Inject unexpected items | Traffic injection | Message Injection attack [179] | In a platooning scenario, a Message Injection Attack involves an attacker inserting false or malicious data into the communication stream of the platoon. This could be false sensor readings, misleading location data, or incorrect routing information. The injected false data can lead to misguided decisions by the platooning vehicles, such as incorrect route adjustments, speed changes, or even evasive manoeuvres, potentially causing disarray in the platoon formation and increasing the risk of accidents. This type of attack targets the integrity and authenticity of the data being shared within the platoon, severely compromising the reliability and safety of the platooning operations. |
| Collect and analyse information | Interception | Eavesdropping [180] | In platooning, an Eavesdropping Attack involves unauthorised interception of communications between vehicles. This could be capturing vehicle status data, platoon formation details, or sensitive operational information. This attack can compromise the confidentiality of the platoon’s communications, leading to potential misuse of sensitive data. It could also facilitate further attacks by providing crucial insights into the platoon’s operations and vulnerabilities. The major risk here is the breach of privacy and security, as sensitive data can be exploited to manipulate or disrupt platooning operations, or even for malicious purposes outside the immediate context of platooning. |
| Employ probabilistic techniques | Employ probabilistic techniques | packet fuzzing [181] | In platooning microservices, a Packet Fuzzing Attack involves sending malformed or random data packets to the network or vehicles within the platoon. The goal is to test the robustness of the system and identify vulnerabilities that can be exploited. This type of attack can lead to various issues, such as triggering unexpected behavior in vehicle control systems, causing communication disruptions, or even crashing systems if they are not properly handling malformed data. The primary risks of packet fuzzing attacks in a platooning context are the potential to uncover and exploit security vulnerabilities, leading to operational disruptions or safety hazards. Effective handling and validation of data packets are essential to mitigate these risks. |
| Manipulate timing and state | Manipulate timing and state | Timing Attack [182] | In the context of platooning, a Timing Attack could involve analyzing the time taken by processes or communications to extract sensitive information or to infer internal states of the platoon’s control systems. This type of attack could be used to subtly disrupt or manipulate the coordination and timing of platoon operations, such as altering the response times of vehicles to commands. It poses a risk to the reliability and predictability of platoon behaviors, potentially leading to inefficiencies or safety hazards. Session Hijacking in a platooning context involves an attacker taking over a vehicle’s session after it has been authenticated within the platoon. This allows the attacker to gain unauthorised control over the vehicle’s operations within the platoon. This could result in the hijacked vehicle exhibiting unexpected or dangerous behaviors, such as deviating from the planned route or making sudden manoeuvres, potentially leading to disorganisation or accidents within the platoon. The attack mainly compromises the session management of the platooning system, affecting its authenticity and authorisation mechanisms, thereby posing a threat to the operational security and safety of the platoon. |
References
- Granovskii, M.; Dincer, I.; Rosen, M.A. Economic and environmental comparison of conventional, hybrid, electric and hydrogen fuel cell vehicles. J. Power Sources 2006, 159, 1186–1193. [Google Scholar] [CrossRef]
- NHTSA. Federal Automated Vehicles Policy; U.S. Department of Transportation, NHTSA: Washington, DC, USA, 2016.
- Foxx, A.R. Beyond Traffic: 2045 Final Report; Department of Transportation: Washington, DC, USA, 2017.
- Miller, C.; Valasek, V. Remote Exploitation of an Unaltered Passenger Vehicle. Black Hat USA 2015, 2015, 13–85. [Google Scholar]
- Koscher, K.; Czeskis, A.; Roesner, F.; Patel, S.; Kohno, T.; Checkoway, S.; McCoy, D.; Kantor, B.; Anderson, D.; Shacham, H.; et al. Experimental security analysis of a modern automobile. In Proceedings of the 2010 IEEE Symposium on Security and Privacy, Oakland, CA, USA, 16–19 May 2010; pp. 447–462. [Google Scholar]
- Salek, M.S.; Khan, S.M.; Rahman, M.; Deng, H.W.; Islam, M.; Khan, Z.; Chowdhury, M.; Shue, M. A Review on Cybersecurity of Cloud Computing for Supporting Connected Vehicle Applications. IEEE Internet Things J. 2022, 9, 8250–8268. [Google Scholar] [CrossRef]
- NHTSA. Vehicle Cybersecurity. Available online: https://www.nhtsa.gov/technology-innovation/vehicle-cybersecurity (accessed on 20 August 2023).
- Ge, X.; Han, Q.L.; Wang, J.; Zhang, X.M. Scalable and resilient platooning control of cooperative automated vehicles. IEEE Trans. Veh. Technol. 2022, 71, 3595–3608. [Google Scholar] [CrossRef]
- Montanaro, U.; Dixit, S.; Fallah, S.; Dianati, M.; Stevens, A.; Oxtoby, D.; Mouzakitis, A. Towards connected autonomous driving: Review of use-cases. Veh. Syst. Dyn. 2019, 57, 779–814. [Google Scholar] [CrossRef]
- Jia, D.; Lu, K.; Wang, J.; Zhang, X.; Shen, X. A survey on platoon-based vehicular cyber-physical systems. IEEE Commun. Surv. Tutorials 2015, 18, 263–284. [Google Scholar] [CrossRef]
- Amoozadeh, M.; Deng, H.; Chuah, C.N.; Zhang, H.M.; Ghosal, D. Platoon management with cooperative adaptive cruise control enabled by VANET. Veh. Commun. 2015, 2, 110–123. [Google Scholar] [CrossRef]
- Vasconcelos Filho, Ê.; Severino, R.; Salgueiro dos Santos, P.M.; Koubaa, A.; Tovar, E. Cooperative vehicular platooning: A multi-dimensional survey towards enhanced safety, security and validation. Cyber-Phys. Syst. 2023, 9, 1–53. [Google Scholar] [CrossRef]
- Mousavinejad, E.; Yang, F.; Han, Q.L.; Ge, X.; Vlacic, L. Distributed cyber attacks detection and recovery mechanism for vehicle platooning. IEEE Trans. Intell. Transp. Syst. 2019, 21, 3821–3834. [Google Scholar] [CrossRef]
- CAPEC. Common Attack Pattern Enumeration and Classification. Available online: https://capec.mitre.org/data/definitions/1000.html (accessed on 20 August 2023).
- Mejri, M.N.; Ben-Othman, J.; Hamdi, M. Survey on VANET security challenges and possible cryptographic solutions. Veh. Commun. 2014, 1, 53–66. [Google Scholar] [CrossRef]
- Petit, J.; Shladover, S.E. Potential Cyberattacks on Automated Vehicles. IEEE Trans. Intell. Transp. Syst. 2014, 16, 546–566. [Google Scholar] [CrossRef]
- Hamida, E.; Noura, H.; Znaidi, W. Security of Cooperative Intelligent Transport Systems: Standards, Threats Analysis and Cryptographic Countermeasures. Electronics 2015, 4, 380–423. [Google Scholar] [CrossRef]
- Sakiz, F.; Sen, S. A survey of attacks and detection mechanisms on intelligent trasnportation system—VANETS and IoV. Ad Hoc Netw. 2017, 61, 33–50. [Google Scholar] [CrossRef]
- Parkinson, S.; Ward, P.; Wilson, K.; Miller, J. Cyber Threats Facing Autonomous and Connected Vehicles: Future Challenges. IEEE Trans. Intell. Transp. Syst. 2017, 18, 2898–2915. [Google Scholar] [CrossRef]
- Raya, M.; Hubaux, J.P. Securing vehicular ad hoc networks. J. Comput. Secur. 2007, 15, 39–68. [Google Scholar] [CrossRef]
- Studnia, I.; Nicomette, V.; Alata, E.; Deswarte, Y.; Kaâniche, M.; Laarouchi, Y. Survey on security threats and protection mechanisms in embedded automotive networks. In Proceedings of the 43rd Annual IEEE/IFIP Conference on Dependable Systems and Networks Workshop (DSN-W), Budapest, Hungary, 24–27 June 2013; pp. 1–12. [Google Scholar]
- Thing, V.L.L.; Wu, J. Autonomous Vehicle Security: A Taxonomy of Attacks and Defences. In Proceedings of the 2016 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Chengdu, China, 15–18 December 2016. [Google Scholar]
- Al-Kahtani, M.S. Survey on security attacks in Vehicular Ad hoc Networks (VANETs). In Proceedings of the Survey on Security Attacks in Vehicular Ad Hoc Networks (VANETs), Gold Coast, Australia, 12–14 December 2012; pp. 1–9. [Google Scholar]
- Gillani, S.; Shahzad, F.; Qayyum, A.; Mehmood, R. A survey on security in vehicular ad hoc networks. In Proceedings of the Communication Technologies for Vehicles: 5th International Workshop, Nets4Cars/Nets4Trains 2013, Villeneuve d’Ascq, France, 14–15 May 2013; Proceedings 5; Springer: Cham, Switzerland, 2013; pp. 59–74. [Google Scholar]
- Othmane, L.B.; Weffers, H.; Mohamad, M.M.; Wolf, M. A survey of security and privacy in connected vehicles. In Wireless Sensor and Mobile Ad-Hoc Networks Vehicular and Space Applications; Springer: New York, NY, USA, 2015; pp. 217–247. [Google Scholar]
- Yan, G.; Wen, D.; Olariu, S.; Weigle, M.C. Security challenges in vehicular cloud computing. IEEE Trans. Intell. Transp. Syst. 2013, 14, 284–294. [Google Scholar] [CrossRef]
- Engoulou, R.G.; Bellaiche, M.; Pierre, S.; Quintero, A. VANET security surveys. Comput. Commun. 2014, 44, 1–13. [Google Scholar] [CrossRef]
- Siegel, J.E.; Erb, D.C.; Sarma, S.E. A Survey of the Connected Vehicle Landscape Architectures, Enabling Technologies, Applications, and Development Areas. IEEE Trans. Intell. Transp. Syst. 2017, 99, 2391–2406. [Google Scholar] [CrossRef]
- Hasrouny, H.; Samhat, A.E.; Bassil, C.; Laouiti, A. VANet security challenges and solutions: A survey. Veh. Commun. 2017, 7, 7–20. [Google Scholar] [CrossRef]
- Boumiza, S.; Braham, R. Intrusion threats and security solutions for autonomous vehicle networks. In Proceedings of the 2017 IEEE/ACS 14th International Conference on Computer Systems and Applications (AICCSA), Hammamet, Tunisia, 30 October–3 November 2017; pp. 120–127. [Google Scholar]
- Kelarestaghi, K.B.; Foruhandeh, M.; Heaslip, K.; Gerdes, R. Survey on vehicular ad hoc networks and its access technologies security vulnerabilities and countermeasures. arXiv 2019, arXiv:1903.01541. [Google Scholar]
- Sheikh, M.S.; Liang, J. A comprehensive survey on VANET security services in traffic management system. Wirel. Commun. Mob. Comput. 2019, 2019, 2423915. [Google Scholar] [CrossRef]
- Sommer, F.; Dürrwang, J.; Kriesten, R. Survey and classification of automotive security attacks. Information 2019, 10, 148. [Google Scholar] [CrossRef]
- Jadhav, S.; Kshirsagar, D. A survey on security in automotive networks. In Proceedings of the 2018 Fourth International Conference on Computing Communication Control and Automation (ICCUBEA), Pune, India, 16–18 August 2018; pp. 1–6. [Google Scholar]
- Yoshizawa, T.; Preneel, B. Survey of security aspect of v2x standards and related issues. In Proceedings of the 2019 IEEE Conference on Standards for Communications and Networking (CSCN), Granada, Spain, 28–30 October 2019; pp. 1–5. [Google Scholar]
- Masood, A.; Lakew, D.S.; Cho, S. Security and privacy challenges in connected vehicular cloud computing. IEEE Commun. Surv. Tutorials 2020, 22, 2725–2764. [Google Scholar] [CrossRef]
- Sun, X.; Yu, F.R.; Zhang, P. A survey on cyber-security of connected and autonomous vehicles (CAVs). IEEE Commun. Surv. Tutorials 2021, 23, 6240–6259. [Google Scholar] [CrossRef]
- Zeadally, S.; Hunt, R.; Chen, Y.S.; Irwin, A.; Hassan, A. Vehicular ad hoc networks (VANETS): Status, results, and challenges. Telecommun. Syst. 2012, 50, 217–241. [Google Scholar] [CrossRef]
- Di Pietro, R.; Guarino, S.; Verde, N.V.; Domingo-Ferrer, J. Security in wireless ad-hoc networks–a survey. Comput. Commun. 2014, 51, 1–20. [Google Scholar] [CrossRef]
- ETSI. Intelligent transport systems (ITS); vehicular communications; basic set of applications; part 2: Specification of cooperative awareness basic service. Eur. Stand. 2014, 20, 448–451. [Google Scholar]
- ISO 21434; Road Vehicles—Cybersecurity Engineering. ISO: Geneva, Switzerland, 2021.
- ISO 26262; Road Vehicles—Functional Safety. ISO: Geneva, Switzerland, 2018.
- SAE J3061; Cybersecurity Guidebook for Cyber-Physical Automotive Systems. SAE-Society of Automotive Engineers: Warrendale, PA, USA, 2016.
- Cadzow, S.; Eichbrecht, P.; Evensen, K.; Fischer, H.J.; Davila-Gonzalez, E.; Hoefs, W.; Kargl, F.; Koenders, E.; Lykkja, O.M.; Moring, J.; et al. EU-US Standards Harmonization Task Group Report: Summary of Lessons Learned; No. FHWA-JPO-13-076; United States Joint Program Office for Intelligent Transportation Systems: Washington, DC, USA, 2012.
- ETSI. Intelligent Transport Systems (ITS); Communication Architecture for Multi-Channel Operation (MCO); Release 2; European Telecommunications Standards Institute: Paris, France, 2021. [Google Scholar]
- Hubaux, J.P.; Capkun, S.; Jun, L. The security and privacy of smart vehicles. IEEE Secur. Priv. 2004, 2, 49–55. [Google Scholar] [CrossRef]
- McKerral, A.; Pammer, K.; Gauld, C. Supervising the self-driving car: Situation awareness and fatigue during highly automated driving. Accid. Anal. Prev. 2023, 187, 107068. [Google Scholar] [CrossRef]
- Coppola, R.; Morisio, M. Connected car: Technologies, issues, future trends. ACM Comput. Surv. (CSUR) 2016, 49, 1–36. [Google Scholar] [CrossRef]
- Bae, J.K.; Park, M.C.; Yang, E.J.; Seo, D.W. Implementation and performance evaluation for DSRC-based vehicular communication system. IEEE Access 2020, 9, 6878–6887. [Google Scholar] [CrossRef]
- Sheik, A.T.; Maple, C. Edge Computing to Support Message Prioritisation in Connected Vehicular Systems. In Proceedings of the 2019 IEEE Global Conference on Internet of Things (GCIoT), Dubai, United Arab Emirates, 4–7 December 2019; pp. 1–7. [Google Scholar] [CrossRef]
- McEnroe, P.; Wang, S.; Liyanage, M. A survey on the convergence of edge computing and AI for UAVs: Opportunities and challenges. IEEE Internet Things J. 2022, 9, 15435–15459. [Google Scholar] [CrossRef]
- Montanaro, U.; Fallah, S.; Dianati, M.; Oxtoby, D.; Mizutani, T.; Mouzakitis, A. On a fully self-organizing vehicle platooning supported by cloud computing. In Proceedings of the 2018 Fifth International Conference on Internet of Things: Systems, Management and Security, Valencia, Spain, 15–18 October 2018; pp. 295–302. [Google Scholar]
- Stevens, A.; Dianati, M.; Katsaros, K.; Han, C.; Fallah, S.; Maple, C.; McCullough, F.; Mouzakitis, A. Cooperative automation through the cloud: The CARMA project. In Proceedings of the 12th ITS European Congress, Strasbourg, France, 19–22 June 2017; pp. 1–6. [Google Scholar]
- Arthurs, P.; Gillam, L.; Krause, P.; Wang, N.; Halder, K.; Mouzakitis, A. A taxonomy and survey of edge cloud computing for intelligent transportation systems and connected vehicles. IEEE Trans. Intell. Transp. Syst. 2021, 23, 6206–6221. [Google Scholar] [CrossRef]
- Gillam, L.; Katsaros, K.; Dianati, M.; Mouzakitis, A. Exploring edges for connected and autonomous driving. In Proceedings of the IEEE INFOCOM 2018-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Honolulu, HI, USA, 15–19 April 2018; pp. 148–153. [Google Scholar]
- Shi, W.; Cao, J.; Zhang, Q.; Li, Y.; Xu, L. Edge computing: Vision and challenges. IEEE Internet Things J. 2016, 3, 637–646. [Google Scholar] [CrossRef]
- Javed, A.M.; Zeadally, S.; Hamid, Z. Trust-based security adaptation mechanism for Vehicular Sensor Networks. Comput. Netw. 2018, 137, 27–36. [Google Scholar] [CrossRef]
- Al-Sultan, S.; Al-Doori, M.M.; Al-Bayatti, A.H.; Zedan, H. A comprehensive survey on vehicular ad hoc network. J. Netw. Comput. Appl. 2014, 37, 380–392. [Google Scholar] [CrossRef]
- Raw, R.S.; Kumar, M.; Singh, N. Security challenges, issues and their solutions for VANET. Int. J. Netw. Secur. Its Appl. 2013, 5, 5. [Google Scholar]
- Arena, F.; Pau, G.; Severino, A. A review on IEEE 802.11 p for intelligent transportation systems. J. Sens. Actuator Netw. 2020, 9, 22. [Google Scholar] [CrossRef]
- Wahlström, J.; Skog, I.; Händel, P. Smartphone-based vehicle telematics: A ten-year anniversary. IEEE Trans. Intell. Transp. Syst. 2017, 18, 2802–2825. [Google Scholar] [CrossRef]
- Siegel, J.E. CloudThink and the Avacar: Embedded Design to Create Virtual Vehicles for Cloud-Based Informatics, Telematics, and Infotainment; Massachusetts Institute of Technology: Cambridge, MA, USA, 2013. [Google Scholar]
- Cho, K.Y.; Bae, C.H.; Chu, Y.; Suh, M.W. Overview of telematics: A system architecture approach. Int. J. Automot. Technol. 2006, 7, 509–517. [Google Scholar]
- Hou, J.; Chen, G.; Huang, J.; Qiao, Y.; Xiong, L.; Wen, F.; Knoll, A.; Jiang, C. Large-Scale Vehicle Platooning: Advances and Challenges in Scheduling and Planning Techniques. Engineering 2023, in press. [Google Scholar] [CrossRef]
- Taylor, S.J.; Ahmad, F.; Nguyen, H.N.; Shaikh, S.A. Vehicular platoon communication: Architecture, security threats and open challenges. Sensors 2023, 23, 134. [Google Scholar] [CrossRef] [PubMed]
- Brooks, D.J. What is security: Definition through knowledge categorization. Secur. J. 2010, 23, 225–239. [Google Scholar] [CrossRef]
- Fischer, R.; Edward Halibozek, M.; Halibozek, E.P.; Walters, D. Introduction to Security; Butterworth-Heinemann: Oxford, UK, 2012. [Google Scholar]
- Maple, C. Security and privacy in the internet of things. J. Cyber Policy 2017, 2, 155–184. [Google Scholar] [CrossRef]
- Roman, R.; Lopez, J.; Mambo, M. Mobile edge computing, fog et al.: A survey and analysis of security threats and challenges. Future Gener. Comput. Syst. 2018, 78, 680–698. [Google Scholar] [CrossRef]
- ISO 27000; Information Technology, Security Techniques, Information Security Management Systems. ISO: Geneva, Switzerland, 2020.
- Hamida, E.B.; Javed, M.A. Channel-Aware ECDSA Signature Verification of Basic Safety Messages with K-Means Clustering in VANETs. In Proceedings of the 2016 IEEE 30th International Conference on Advanced Information Networking and Applications (AINA), Crans-Montana, Switzerland, 23–25 March 2016. [Google Scholar]
- Guzman, Z. Hackers Remotely Kill Jeep’s Engine on Highway. Available online: https://www.cnbc.com/2015/07/21/hackers-remotely-kill-jeep-engine-on-highway.html (accessed on 20 August 2023).
- Liu, N.; Nikitas, A.; Parkinson, S. Exploring expert perceptions about the cyber security and privacy of Connected and Autonomous Vehicles: A thematic analysis approach. Transp. Res. Part F Traffic Psychol. Behav. 2020, 75, 66–86. [Google Scholar] [CrossRef]
- Hariharan, J.; Sheik, A.; Maple, C.; Beech, N.; Atmaca, U. Customers’ perception of cybersecurity risks in E-commerce websites. In Proceedings of the International Conference on AI and the Digital Economy (CADE 2023), Venice, Italy, 26–28 June 2023. [Google Scholar]
- Checkoway, S.; McCoy, D.; Kantor, B.; Anderson, D.; Shacham, H.; Savage, S.; Koscher, K.; Czeskis, A.; Roesner, F.; Kohno, T. Comprehensive experimental analyses of automotive attack surfaces. In Proceedings of the 20th USENIX Security Symposium (USENIX Security 11), San Francisco, CA, USA, 10–12 August 2011. [Google Scholar]
- Bendiab, G.; Hameurlaine, A.; Germanos, G.; Kolokotronis, N.; Shiaeles, S. Autonomous Vehicles Security: Challenges and Solutions Using Blockchain and Artificial Intelligence. IEEE Trans. Intell. Transp. Syst. 2023, 24, 3614–3637. [Google Scholar] [CrossRef]
- Nie, S.; Liu, L.; Du, Y. Free-fall: Hacking tesla from wireless to can bus. Briefing Black Hat USA 2017, 25, 1–16. [Google Scholar]
- Tencent Security Keen Lab. Experimental Security Assessment of BMW Cars by KeenLab. Available online: https://bit.ly/34ICOBC (accessed on 20 August 2023).
- Tencent Security Keen Lab. Tencent Security Keen Lab: Experimental Security Assessment of Mercedes-Benz Cars. Available online: https://bit.ly/34Gpqhj (accessed on 20 August 2023).
- Ghosal, A.; Sagong, S.U.; Halder, S.; Sahabandu, K.; Conti, M.; Poovendran, R.; Bushnell, L. Truck platoon security: State-of-the-art and road ahead. Comput. Netw. 2021, 185, 107658. [Google Scholar] [CrossRef]
- Pekaric, I.; Sauerwein, C.; Haselwanter, S.; Felderer, M. A taxonomy of attack mechanisms in the automotive domain. Comput. Stand. Interfaces 2021, 78, 103539. [Google Scholar] [CrossRef]
- Ali, I.; Gervais, M.; Ahene, E.; Li, F. A blockchain-based certificateless public key signature scheme for vehicle-to-infrastructure communication in VANETs. J. Syst. Archit. 2019, 99, 101636. [Google Scholar] [CrossRef]
- Zhao, M. Advanced driver assistant system, threats, requirements, security solutions. Intel Labs 2015, 2–3. [Google Scholar]
- Radanliev, P.; De Roure, D.; Page, K.; Van Kleek, M.; Santos, O.; Maddox, L.; Burnap, P.; Anthi, E.; Maple, C. Design of a dynamic and self-adapting system, supported with artificial intelligence, machine learning and real-time intelligence for predictive cyber risk analytics in extreme environments–cyber risk in the colonisation of Mars. Saf. Extrem. Environ. 2020, 2, 219–230. [Google Scholar] [CrossRef]
- Erdogan, G.; Garcia-Ceja, E.; Hugo, Å.; Nguyen, P.H.; Sen, S. A Systematic Mapping Study on Approaches for Al-Supported Security Risk Assessment. In Proceedings of the 2021 IEEE 45th Annual Computers, Software, and Applications Conference (COMPSAC), Madrid, Spain, 12–16 July 2021; pp. 755–760. [Google Scholar]
- Patel, A.R.; Liggesmeyer, P. Machine learning based dynamic risk assessment for autonomous vehicles. In Proceedings of the 2021 International Symposium on Computer Science and Intelligent Controls (ISCSIC), Rome, Italy, 12–14 November 2021; pp. 73–77. [Google Scholar]
- Ali, E.S.; Hasan, M.K.; Hassan, R.; Saeed, R.A.; Hassan, M.B.; Islam, S.; Nafi, N.S.; Bevinakoppa, S. Machine learning technologies for secure vehicular communication in internet of vehicles: Recent advances and applications. Secur. Commun. Netw. 2021, 2021, 8868355. [Google Scholar] [CrossRef]
- Yuan, E.; Esfahani, N.; Malek, S. A systematic survey of self-protecting software systems. ACM Trans. Auton. Adapt. Syst. (TAAS) 2014, 8, 1–41. [Google Scholar] [CrossRef]
- Rose, S.; Borchert, O.; Mitchell, S.; Connelly, S. Zero Trust Architecture; Technical Report; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2020.
- UCISA. Privacy Impact Assessment Toolkit. Available online: https://www.ucisa.ac.uk/PIAToolkit (accessed on 20 August 2023).
- Azam, N.; Michala, L.; Ansari, S.; Truong, N.B. Data Privacy Threat Modelling for Autonomous Systems: A Survey from the GDPR’s Perspective. IEEE Trans. Big Data 2022, 9, 388–414. [Google Scholar] [CrossRef]
- Huang, H.; Li, H.; Shao, C.; Sun, T.; Fang, W.; Dang, S. Data redundancy mitigation in V2X based collective perceptions. IEEE Access 2020, 8, 13405–13418. [Google Scholar] [CrossRef]
- Tremblay, J.; Prakash, A.; Acuna, D.; Brophy, M.; Jampani, V.; Anil, C.; To, T.; Cameracci, E.; Boochoon, S.; Birchfield, S. Training deep networks with synthetic data: Bridging the reality gap by domain randomization. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition Workshops, Salt Lake City, UT, USA, 18–22 June 2018; pp. 969–977. [Google Scholar]
- Skygo. Security Research Report on Mercedes Benz Cars—SkyGo Blog. Available online: https://skygo.360.net/archive/Security-Research-Report-on-Mercedes-Benz-Cars-en.pdf (accessed on 20 August 2023).
- Thoughts, B.Y. Man Block ETC with Melon Seed Bags and Evades Fees 22 Times over 40,000 in 3 Months. Available online: https://www.youtube.com/watch?v=Bzw7pA0rHCk (accessed on 20 August 2023).
- Curry, S. More Car Hacking! Available online: https://twitter.com/samwcyo/status/1597792097175674880 (accessed on 20 August 2023).
- Finkle, J.; Woodall, B. Researcher Says Can Hack GM’s OnStar App, Open Vehicle, Start Engine. Available online: https://www.reuters.com/article/us-gm-hacking-idUSKCN0Q42FI20150730 (accessed on 20 August 2023).
- Lodge, D. Hacking the Mitsubishi Outlander Phev Hybrid. Available online: https://www.pentestpartners.com/security-blog/hacking-the-mitsubishi-outlander-phev-hybrid-suv/ (accessed on 20 August 2023).
- Computest. Car Hack Project Volkswagen/Audi. Available online: https://www.computest.nl/en/knowledge-platform/rd-projects/car-hack/ (accessed on 20 August 2023).
- Tencent. Tesla Model S Wi-Fi Protocol Stack Vulnerability. Available online: https://v.qq.com/x/page/v304513meir.html (accessed on 20 August 2023).
- BlackHat. Multiple Vulnerabilities Disclosed in Black Hat Europe VW ID Series. Available online: https://www.blackhat.com/eu-22/ (accessed on 20 August 2023).
- Vakhter, V.; Soysal, B.; Schaumont, P.; Guler, U. Threat modeling and risk analysis for miniaturized wireless biomedical devices. IEEE Internet Things J. 2022, 9, 13338–13352. [Google Scholar] [CrossRef]
- Arif, M.; Wang, G.; Bhuiyan, M.Z.A.; Wang, T.; Chen, J. A survey on security attacks in VANETs: Communication, applications and challenges. Veh. Commun. 2019, 19, 100179. [Google Scholar] [CrossRef]
- Francillon, A.; Danev, B.; Capkun, S. Relay attacks on passive keyless entry and start systems in modern cars. In Proceedings of the Network and Distributed System Security Symposium (NDSS), San Diego, CA, USA, 24–28 April 2011; Volume 2011. [Google Scholar]
- Norte, J.C. Hacking Industrial Vehicles from the Internet. Available online: http://jcarlosnorte.com/security/2016/03/06/hacking-tachographs-from-the-internets.html (accessed on 20 August 2023).
- Mazloom, S.; Rezaeirad, M.; Hunter, A.; McCoy, D. A Security Analysis of an In-Vehicle Infotainment and App Platform. In Proceedings of the 10th USENIX Workshop on Offensive Technologies (WOOT 16), Austin, TX, USA, 8–9 August 2016. [Google Scholar]
- Obzy. BMW 330I 2011 Format String DOS Vulnerability (CVE-2017-9212). Available online: https://twitter.com/__obzy__/status/864704956116254720 (accessed on 20 August 2023).
- CISA. ICS Advisory. Available online: http://shorturl.at/fhp78 (accessed on 20 August 2023).
- Samcurry. Cracking My Windshield and Earning $10,000 on the Tesla Bug Bounty Program. Available online: https://bit.ly/3XXgJFC (accessed on 20 August 2023).
- Cylect. Dosla—Tesla Vulnerability—CVE-2020-10558|Cylect.io. Available online: https://cylect.io/blog/cybr-2/dosla-tesla-vulnerability-cve-2022-10558-1 (accessed on 20 August 2023).
- NIST. CVE-2020-28656 Detail. Available online: https://nvd.nist.gov/vuln/detail/CVE-2020-28656 (accessed on 20 August 2023).
- GeekPwn. Find a Few Key Keys on Google, and Then Crack Your Own Car? Available online: https://mp.weixin.qq.com/s/-xlV8nPjIy5nUT4Zt4a5rg (accessed on 20 August 2023).
- Dengdeng. Many Car Owners in Shanghai Were Reminded That “There Is a Gunfight on the Road”? Available online: https://mp.weixin.qq.com/s/Zc-_Z0PyZQ8qSvZEXU2U3Q (accessed on 20 August 2023).
- Hoppe, T.; Kiltz, S.; Dittmann, J. Security threats to automotive CAN networks—Practical examples and selected short-term countermeasures. Reliab. Eng. Syst. Saf. 2011, 96, 11–25. [Google Scholar] [CrossRef]
- Sgayou. Subaru Starlink Persistent Root Code Execution. Available online: https://github.com/sgayou/subaru-starlink-research (accessed on 20 August 2023).
- Garip, M.T.; Gursoy, M.E.; Reiher, P.; Gerla, M. Congestion attacks to autonomous cars using vehicular botnets. In Proceedings of the NDSS Workshop on Security of Emerging Networking Technologies (SENT), San Diego, CA, USA, 8 February 2015. [Google Scholar]
- Liu, J. Belgian Security Researchers from KU Leuven and IMEC Demonstrate Serious Flaws in Tesla Model X Keyless Entry System. Available online: https://bit.ly/3XJa81V (accessed on 20 August 2023).
- Zehavi, I.; Shamir, A. Facial Misrecognition Systems: Simple Weight Manipulations Force DNNs to Err Only on Specific Persons. arXiv 2023, arXiv:2301.03118. [Google Scholar]
- Nassi, B.; Nassi, D.; Ben-Netanel, R.; Mirsky, Y.; Drokin, O.; Elovici, Y. Phantom of the Adas: Phantom Attacks on Driver-Assistance Systems. Cryptology ePrint Archive. 2020. Available online: https://eprint.iacr.org/2020/085 (accessed on 22 October 2023).
- Petit, J.; Stottelaar, B.; Feiri, M.; Kargl, F. Remote attacks on automated vehicles sensors: Experiments on camera and lidar. Black Hat Eur. 2015, 11, 995. [Google Scholar]
- Yan, C.; Xu, W.; Liu, J. Can you trust autonomous vehicles: Contactless attacks against sensors of self-driving vehicle. Def Con 2016, 24, 109. [Google Scholar]
- Deng, Y.; Zhang, T.; Lou, G.; Zheng, X.; Jin, J.; Han, Q.L. Deep learning-based autonomous driving systems: A survey of attacks and defenses. IEEE Trans. Ind. Inform. 2021, 17, 7897–7912. [Google Scholar] [CrossRef]
- Muhammad, K.; Ullah, A.; Lloret, J.; Del Ser, J.; de Albuquerque, V.H.C. Deep learning for safe autonomous driving: Current challenges and future directions. IEEE Trans. Intell. Transp. Syst. 2020, 22, 4316–4336. [Google Scholar] [CrossRef]
- Pham, M.; Xiong, K. A survey on security attacks and defense techniques for connected and autonomous vehicles. Comput. Secur. 2021, 109, 102269. [Google Scholar] [CrossRef]
- Meng, Q.; Hsu, L.T.; Xu, B.; Luo, X.; El-Mowafy, A. A GPS spoofing generator using an open sourced vector tracking-based receiver. Sensors 2019, 19, 3993. [Google Scholar] [CrossRef]
- Narain, S.; Ranganathan, A.; Noubir, G. Security of GPS/INS based on-road location tracking systems. In Proceedings of the 2019 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 19–23 May 2019; pp. 587–601. [Google Scholar]
- CyberRegulus. Tesla Model S and Model 3 Prove Vulnerable to GPS Spoofing Attacks as Autopilot Navigation Steers Car off Road, Research from Regulus Cyber Shows. Available online: https://bit.ly/3kNhRgM (accessed on 20 August 2023).
- Bitsight. Bitsight Discovers Critical Vulnerabilities in Widely Used Vehicle GPS Tracker. Available online: https://bit.ly/3je70fd (accessed on 20 August 2023).
- AnonymousTV. The Largest Taxi Service in Russia ’Yandex Taxi’ Was Hacked by the #Anonymous Collective. Available online: https://twitter.com/YourAnonTV/status/1565555525378506752 (accessed on 20 August 2023).
- Mitre. CVE-2020-15912. Available online: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-15912 (accessed on 20 August 2023).
- Foster, I.; Prudhomme, A.; Koscher, K.; Savage, S. Fast and vulnerable: A story of telematic failures. In Proceedings of the 9th USENIX Workshop on Offensive Technologies (WOOT 15), Washington, DC, USA, 10–11 August 2015. [Google Scholar]
- Burakova, Y.; Hass, B.; Millar, L.; Weimerskirch, A. Truck Hacking: An Experimental Analysis of the SAE J1939 Standard. In Proceedings of the 10th USENIX Workshop on Offensive Technologies (WOOT’ 16), Austin, TX, USA, 8–9 August 2016; Volume 16, pp. 211–220. [Google Scholar]
- Kumar, K.N.; Vishnu, C.; Mitra, R.; Mohan, C.K. Black-box adversarial attacks in autonomous vehicle technology. In Proceedings of the 2020 IEEE Applied Imagery Pattern Recognition Workshop (AIPR), Washington, DC, USA, 13–15 October 2020; pp. 1–7. [Google Scholar]
- Denis, K. Remotely Controlled EV Home Chargers—The Threats and Vulnerabilities. Available online: https://securelist.com/remotely-controlled-ev-home-chargers-the-threats-and-vulnerabilities/89251/ (accessed on 20 August 2023).
- Tencent. Tencent Keen Security Lab: Experimental Security Assessment on Lexus Cars. Available online: https://bit.ly/3XIZhos (accessed on 20 August 2023).
- Xie, G.; Yang, L.T.; Yang, Y.; Luo, H.; Li, R.; Alazab, M. Threat analysis for automotive CAN networks: A GAN model-based intrusion detection technique. IEEE Trans. Intell. Transp. Syst. 2021, 22, 4467–4477. [Google Scholar] [CrossRef]
- Smith, C. 2014 Car Hackers Handbook-Open Garages. 2014. Available online: https://www.oreilly.com/library/view/the-car-hackers/9781457198847/ (accessed on 22 August 2023).
- Verdult, R.; Garcia, F.D.; Ege, B. Dismantling Megamos Crypto: Wirelessly Lockpicking a Vehicle Immobilizer. In Proceedings of the USENIX Security Symposium, Washington, DC, USA, 14–16 August 2013; pp. 703–718. [Google Scholar]
- Sina. Volvo, BYD, etc. Were Exposed to the Defect of Anti-Theft System with 1 Minute Keyless Unlocking. Available online: https://finance.sina.com.cn/consume/puguangtai/20151125/155223849739.shtml (accessed on 20 August 2023).
- Greenberg, A. Hackers Can Steal a Tesla Model S in Seconds by Cloning Its Key Fob. Available online: https://www.wired.com/story/hackers-steal-tesla-model-s-seconds-key-fob/ (accessed on 20 August 2023).
- Rosenblatt, S. This Hack Could Take Control of Your Ford—The Parallax. Available online: https://www.the-parallax.com/hacker-ford-key-fob-vulnerability/ (accessed on 20 August 2023).
- Seth, R. This App Can Track Tesla Model 3 Location. Available online: https://www.the-parallax.com/tesla-radar-model-3-phone-key-ibeacon/ (accessed on 20 August 2023).
- Kunnamon. TBONE: A Zero-Click Exploit for Tesla MCUs. Available online: https://kunnamon.io/tbone/ (accessed on 20 August 2023).
- John, D. Canadian Software Developer Discovers Bluetooth Key Vulnerability That Allows Anyone to Unlock a Tesla. Available online: https://bit.ly/408iH88 (accessed on 20 August 2023).
- HackingIntoYourHeart. Unoriginal Rice Patty Is My Personal Title for the Replay-Based Attack on Honda and Acura Vehticles. Available online: https://github.com/HackingIntoYourHeart/Unoriginal-Rice-Patty (accessed on 20 August 2023).
- ReverseKevin. Honda Civic Replay Attack. Available online: https://www.youtube.com/watch?v=NjbjepeILrk (accessed on 20 August 2023).
- Pompel123. Firmware to Open Any and All Tesla Vehicle Charging Ports in Range! Available online: https://github.com/pompel123/Tesla-Charging-Port-Opener (accessed on 20 August 2023).
- Sharma, A. Honda Bug Lets a Hacker Unlock and Start Your Car via Replay Attack. Available online: https://www.bleepingcomputer.com/news/security/honda-bug-lets-a-hacker-unlock-and-start-your-car-via-replay-attack/ (accessed on 20 August 2023).
- Khan, S. Technical Advisory—Tesla Ble Phone-as-a-Key Passive Entry Vulnerable to Relay Attacks. Available online: https://bit.ly/3DiuZ3M (accessed on 20 August 2023).
- Trifinite. Project Tempa. Available online: https://trifinite.org/stuff/project_tempa/ (accessed on 20 August 2023).
- Rollingpwn. Rolling Pwn Attack. Available online: https://rollingpwn.github.io/rolling-pwn/ (accessed on 20 August 2023).
- Clatworthy, B. Luxury Cars Are Gone in 90 Seconds with Thief Kit. Available online: https://www.thetimes.co.uk/article/luxury-cars-are-gone-in-90-seconds-with-thief-kit-z300g0njf (accessed on 20 August 2023).
- Blackberry. QNX-2021-001 Vulnerability in the C Runtime Library Impacts BlackBerry QNX Software Development Platform (SDP), QNX OS for Medical, and QNX OS for Safety. Available online: https://support.blackberry.com/kb/articleDetail?articleNumber=000082334 (accessed on 20 August 2023).
- Oka, D.K.; Furue, T.; Langenhop, L.; Nishimura, T. Survey of vehicle IoT bluetooth devices. In Proceedings of the 2014 IEEE 7th International Conference on Service-Oriented Computing and Applications, Matsue, Japan, 17–19 November 2014; pp. 260–264. [Google Scholar]
- VDECert. SWARCO: Critical Vulnerability in CPU LS4000. Available online: https://cert.vde.com/de/advisories/VDE-2020-016/ (accessed on 20 August 2023).
- Sohu. An Online Car-Hailing Driver Was Jailed for Stealing Electricity 382 Times in Half a Year Using the ‘Pinch Gun Method’ and ‘Card Second Method’. Available online: https://www.sohu.com/a/259418261_391288 (accessed on 20 August 2023).
- Whittaker, Z. Mercedes-Benz App Glitch Exposed Car Owners’ Information to Other Users. Available online: https://bit.ly/3HdD7Uh (accessed on 20 August 2023).
- Beardsley, T. R7-2017-02: Hyundai Blue Link Potential Info Disclosure (Fixed): Rapid7 blog. Available online: https://www.rapid7.com/blog/post/2017/04/25/r7-2017-02-hyundai-blue-link-potential-info-disclosure-fixed/ (accessed on 20 August 2023).
- Hunt, T. Controlling Vehicle Features of Nissan Leafs across the Globe via Vulnerable Apis. Available online: https://www.troyhunt.com/controlling-vehicle-features-of-nissan/ (accessed on 20 August 2023).
- Schneider. Schneider Electric Security Notification. Available online: https://download.schneider-electric.com/files?p_Doc_Ref=SEVD-2021-194-06 (accessed on 20 August 2023).
- XiunoBBS. Vulnerability Mining Practice of Charging Piles. Available online: https://bbs.kanxue.com/thread-272546.htm (accessed on 20 August 2023).
- Di, W. Information on 100,000 Citroen Owners May Have Been Leaked. Available online: http://shorturl.at/beSTV (accessed on 20 August 2023).
- Xxdesmus. Honda Motor Company Leaks Database with 134 Million Rows of Employee Computer Data. Available online: https://rainbowtabl.es/2019/07/31/honda-motor-company-leak/ (accessed on 20 August 2023).
- ZDNET. Mercedes-Benz Onboard Logic Unit (OLU) Source Code Leaks Online. Available online: https://www.zdnet.com/article/mercedes-benz-onboard-logic-unit-olu-source-code-leaks-online/ (accessed on 20 August 2023).
- Valdes-Dapena, P. Volkswagen Hack: 3 Million Customers Have Had Their Information Stolen|CNN Business. Available online: https://edition.cnn.com/2021/06/11/cars/vw-audi-hack-customer-information/index.html (accessed on 20 August 2023).
- MBUSA. Mercedes-Benz USA Announces Initial Findings of Data Investigation Affecting Customers and Interested Buyers. Available online: https://bit.ly/3wS6Hu5 (accessed on 20 August 2023).
- Volvo. Notice of Cyber Security Breach by Third Party. Available online: https://www.media.volvocars.com/global/en-gb/media/pressreleases/292817/notice-of-cyber-security-breach-by-third-party-1 (accessed on 20 August 2023).
- Asia, N. Toyota Halts Operations at All Japan Plants due to Cyberattack. Available online: https://asia.nikkei.com/Spotlight/Supply-Chain/Toyota-halts-operations-at-all-Japan-plants-due-to-cyberattack (accessed on 20 August 2023).
- Denso. Notice of Unauthorized Access to Group Company: Newsroom: News: Denso Global Website. Available online: https://www.denso.com/global/en/news/newsroom/2022/20220314-g01/ (accessed on 20 August 2023).
- Redazione. La Ferrari è Stata Colpita dal Ransomware Ransomexx. 7 GB di Dati Scaricabili Online. Available online: https://www.redhotcyber.com/post/la-ferrari-e-stata-colpita-dal-ransomware-ransomexx-7gb-di (accessed on 20 August 2023).
- Nio. Statement on Data Security Incidents. Available online: https://app.nio.com/app/web/v2/share_comment?id=2284166&type=essay (accessed on 20 August 2023).
- Puthal, D.; Nepal, S.; Ranjan, R.; Chen, J. Threats to networking cloud and edge datacenters in the Internet of Things. IEEE Cloud Comput. 2016, 3, 64–71. [Google Scholar] [CrossRef]
- Huiyu, W. X-in-the-Middle: Attacking Fast Charging Electric Vehicles. Available online: https://conference.hitb.org/hitbsecconf2021ams/sessions/x-in-the-middle-attacking-fast-charging-electric-vehicles/ (accessed on 20 August 2023).
- Eckert, S. Replay Attack: Numerous Traffic Lights in Germany Are Vulnerable to Manipulation. Available online: https://twitter.com/sveckert/status/1600443031915663360 (accessed on 20 August 2023).
- Topman, N.; Adnane, A. Mobile applications for connected cars: Security analysis and risk assessment. In Proceedings of the NOMS 2022 IEEE/IFIP Network Operations and Management Symposium, Budapest, Hungary, 25–29 April 2022; pp. 1–6. [Google Scholar]
- Santhosh, J.; Sankaran, S. Defending against sybil attacks in vehicular platoons. In Proceedings of the 2019 IEEE International Conference on Advanced Networks and Telecommunications Systems (ANTS), Goa, India, 16–19 December 2019; pp. 1–6. [Google Scholar]
- Nazat, S.; Abdallah, M. Anomaly Detection Framework for Securing Next Generation Networks of Platoons of Autonomous Vehicles in a Vehicle-to-Everything System. In Proceedings of the 9th ACM Cyber-Physical System Security Workshop, Melbourne, Australia, 19 July 2023; pp. 24–35. [Google Scholar]
- Zeng, W.; Khalid, M.A.; Chowdhury, S. In-vehicle networks outlook: Achievements and challenges. IEEE Commun. Surv. Tutorials 2016, 18, 1552–1571. [Google Scholar] [CrossRef]
- Wolf, M.; Willecke, A.; Müller, J.C.; Garlichs, K.; Griebel, T.; Wolf, L.; Buchholz, M.; Dietmayer, K.; van der Heijden, R.W.; Kargl, F. Securing CACC: Strategies for mitigating data injection attacks. In Proceedings of the 2020 IEEE Vehicular Networking Conference (VNC), New York, NY, USA, 16–18 December 2020; pp. 1–7. [Google Scholar]
- Li, K.; Lu, L.; Ni, W.; Tovar, E.; Guizani, M. Cooperative secret key generation for platoon-based vehicular communications. In Proceedings of the ICC 2019 IEEE International Conference on Communications (ICC), Shanghai, China, 20–24 May 2019; pp. 1–6. [Google Scholar]
- Wang, Z.; Wei, H.; Wang, J.; Zeng, X.; Chang, Y. Security Issues and Solutions for Connected and Autonomous Vehicles in a Sustainable City: A Survey. Sustainability 2022, 14, 12409. [Google Scholar] [CrossRef]
- Bianchin, G.; Pasqualetti, F. Time-delay attacks in network systems. Cyber-Phys. Syst. Secur. 2018, 157–174. [Google Scholar]
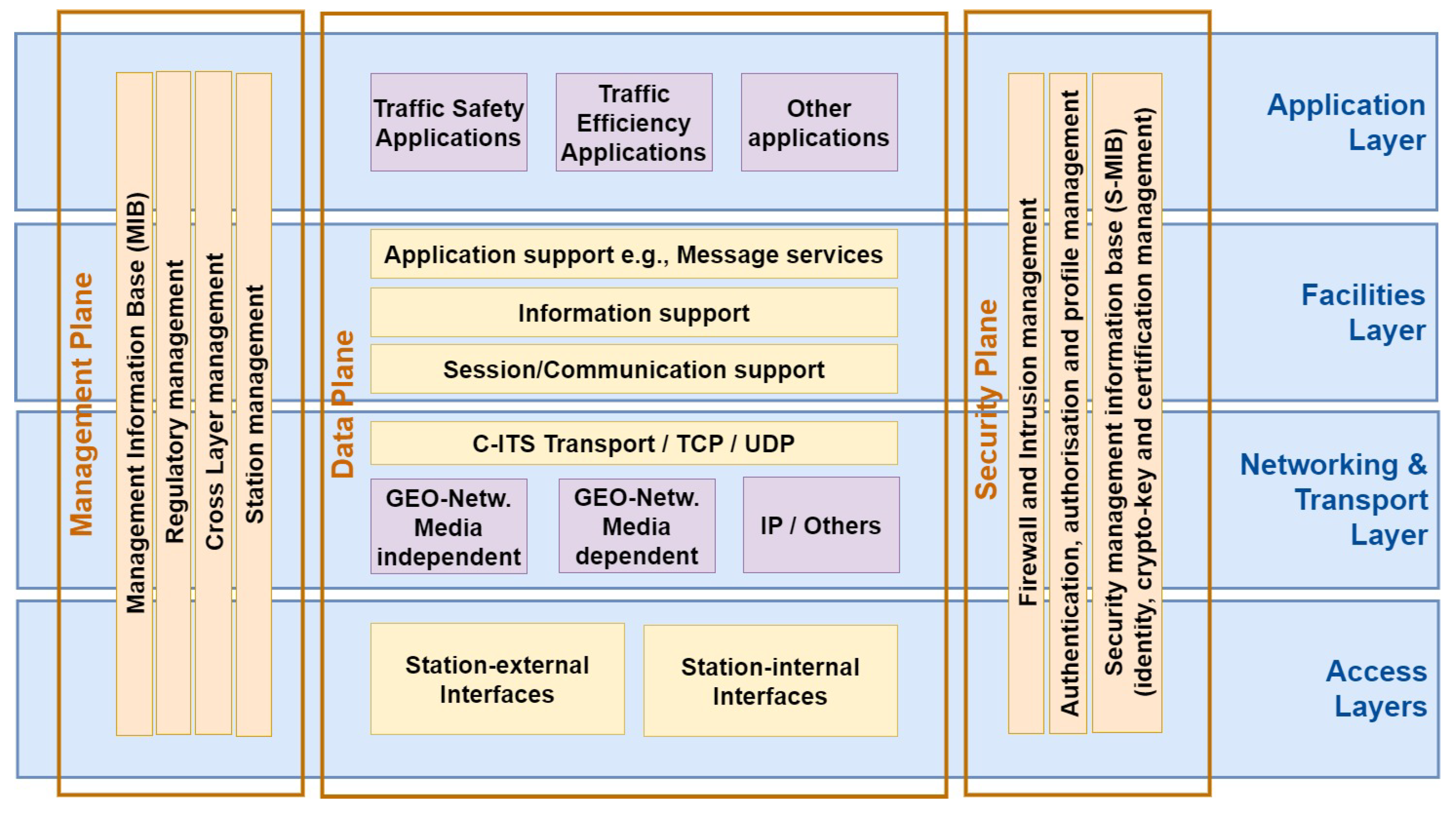
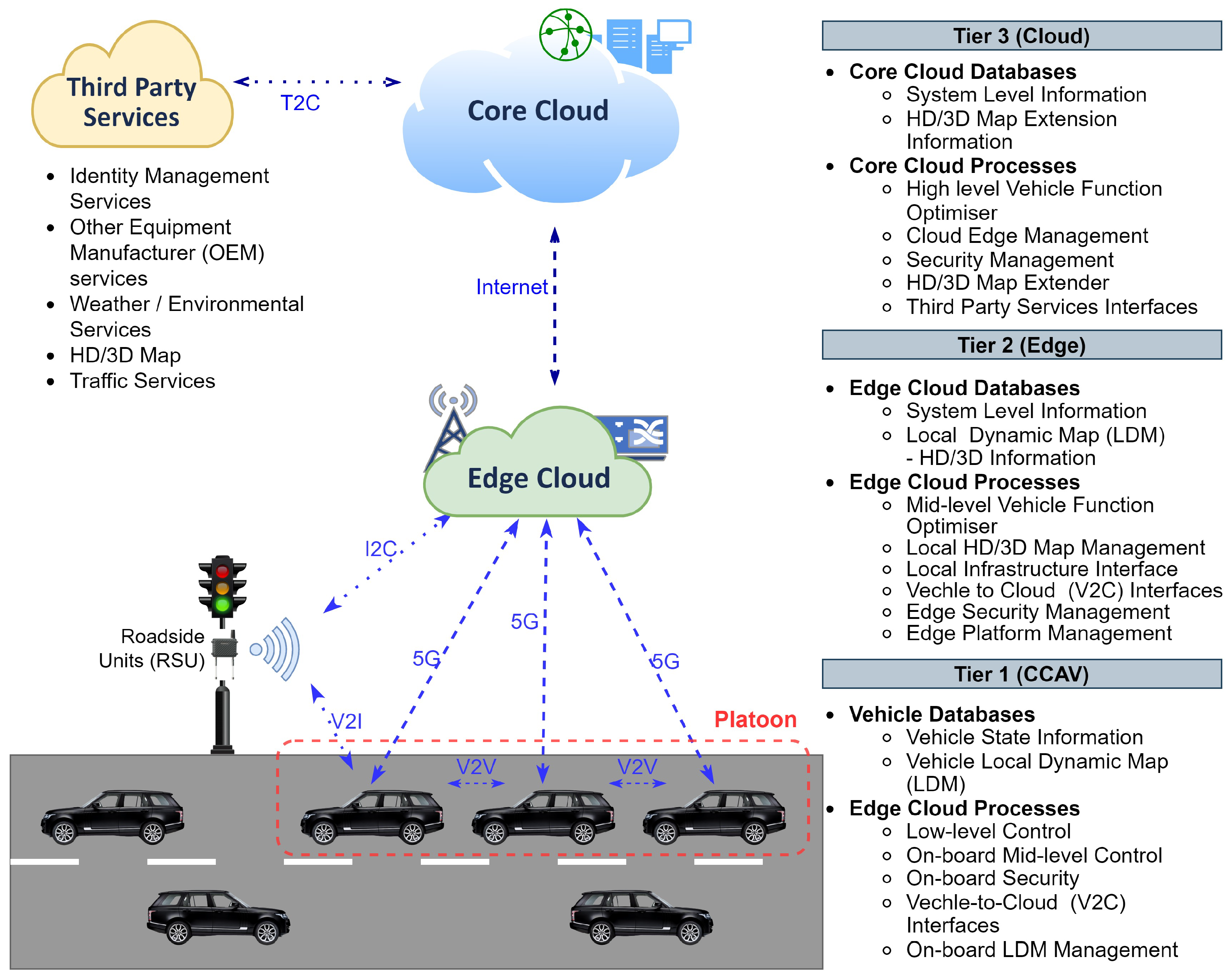
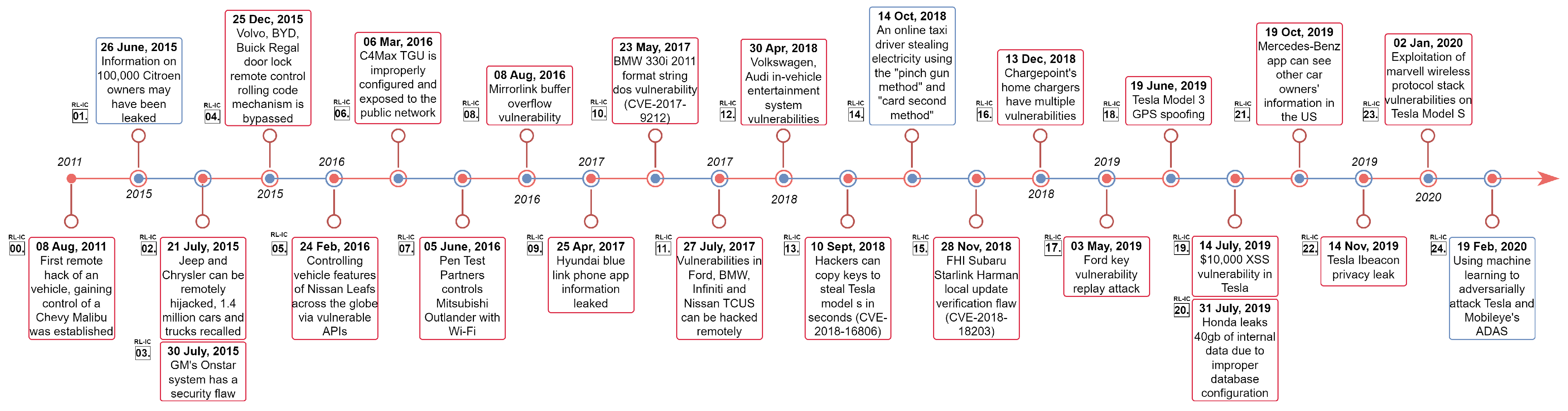


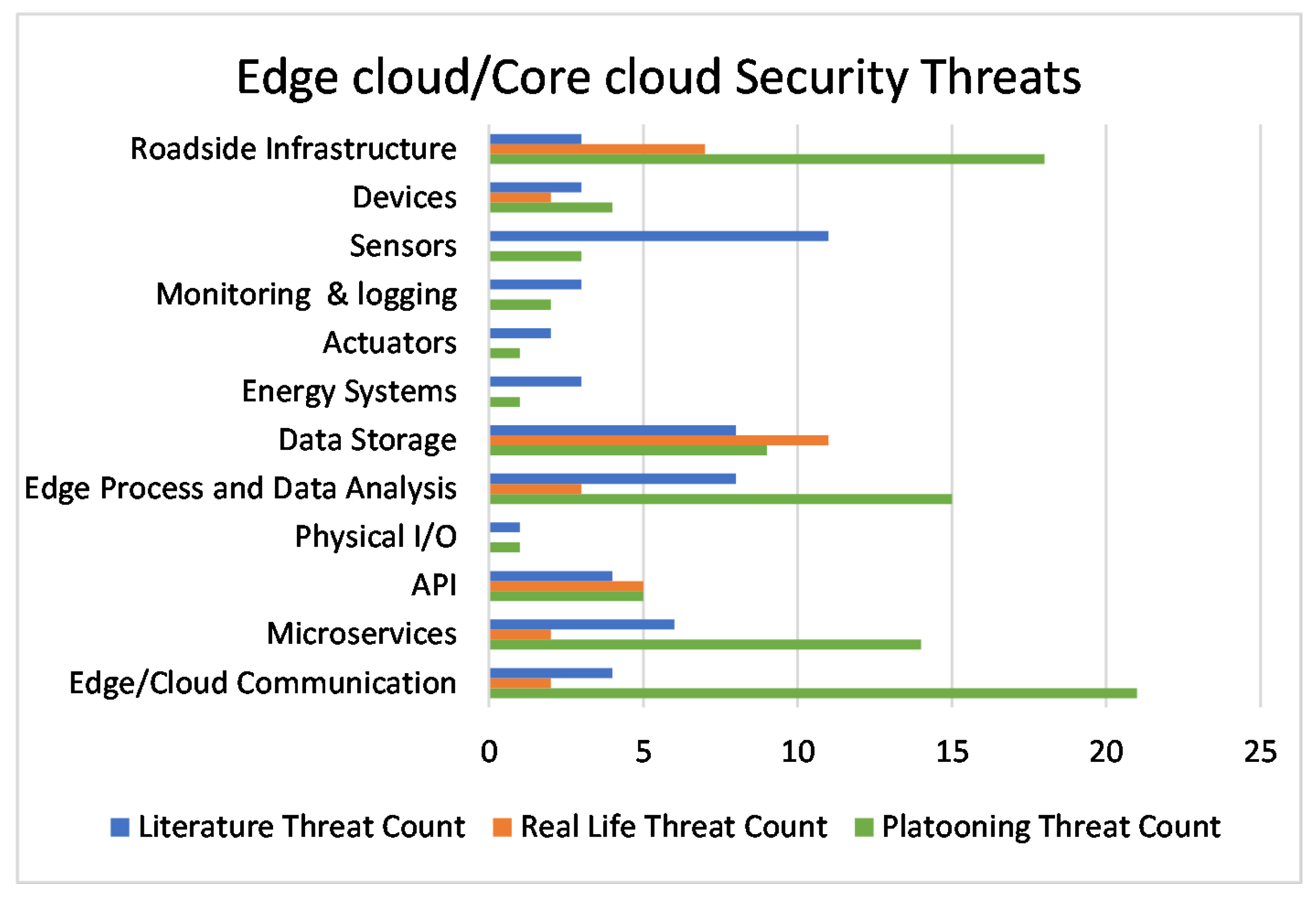
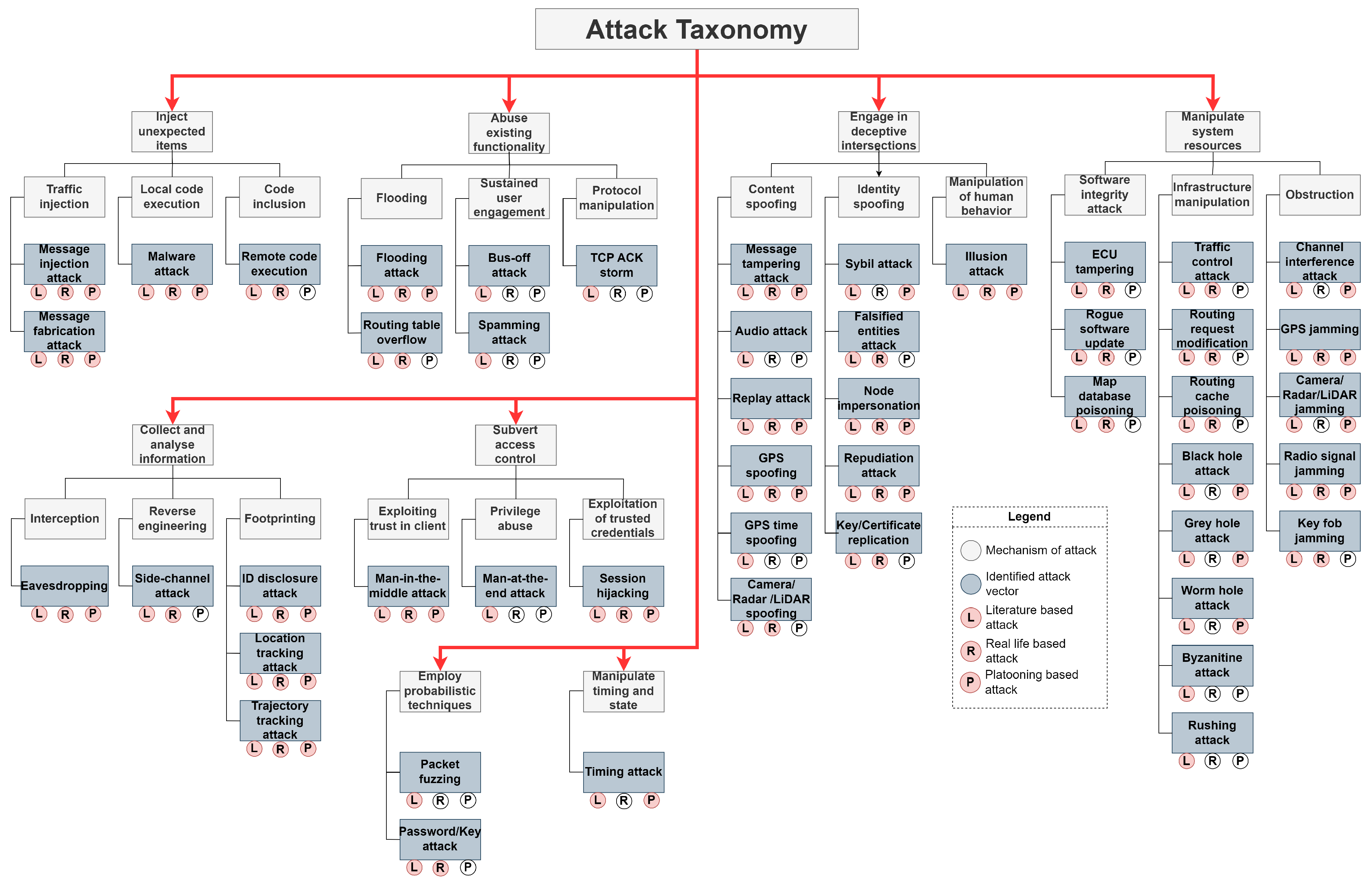
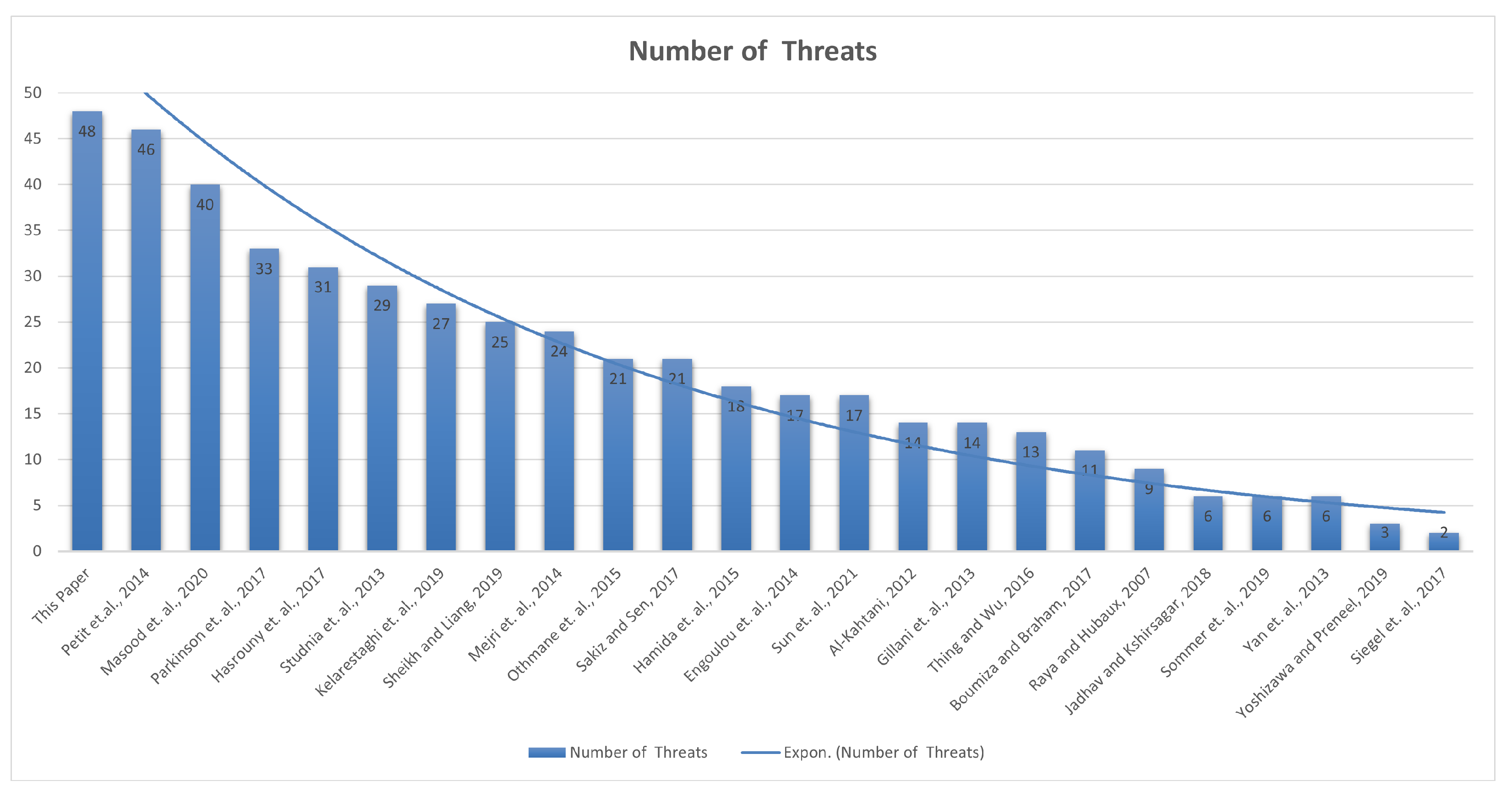
| Surveys | CCAVs | Edge/Cloud | V2V/V2I Communication | Threat Analysis | Attack Taxonomy | Real-Life Incident Timeline | Standards | Platooning |
|---|---|---|---|---|---|---|---|---|
| [15] | ✗ | ✗ | ✓ | ✗ | ✓ | ✗ | ✗ | ✗ |
| [16] | ✗ | ✗ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ |
| [17] | ✗ | ✗ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ |
| [18] | ✗ | ✗ | ✓ | ✗ | ✓ | ✗ | ✗ | ✗ |
| [19] | ✗ | ✗ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ |
| [20] | ✗ | ✗ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ |
| [21,22] | ✗ | ✗ | ✓ | ✗ | ✓ | ✗ | ✗ | ✗ |
| [23] | ✗ | ✗ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ |
| [24] | ✗ | ✗ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ |
| [25] | ✗ | ✗ | ✓ | ✗ | ✓ | ✗ | ✗ | ✗ |
| [26,27] | ✗ | ✗ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ |
| [28] | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ |
| [29] | ✗ | ✗ | ✓ | ✗ | ✓ | ✗ | ✗ | ✗ |
| [30] | ✗ | ✗ | ✓ | ✗ | ✓ | ✗ | ✗ | ✗ |
| [31] | ✗ | ✗ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ |
| [32] | ✗ | ✗ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ |
| [33] | ✗ | ✗ | ✓ | ✗ | ✓ | ✗ | ✗ | ✗ |
| [34] | ✗ | ✗ | ✗ | ✓ | ✓ | ✗ | ✗ | ✗ |
| [35] | ✗ | ✗ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ |
| [36] | ✓ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ |
| [37] | ✗ | ✗ | ✓ | ✓ | ✓ | ✗ | ✓ | ✗ |
| This Paper | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| SAE Level | Description |
|---|---|
| Level 0: No Automation |
|
| Level 1: Driver Assistance |
|
| Level 2: Partial Automation |
|
| Level 3: Conditional Automation |
|
| Level 4: High Automation |
|
| Level 5: Full Automation |
|
| Characteristics of V2I Features | |
|---|---|
| Core cloud, edge cloud and RSU capabilities | Cloud infrastructures can execute remote functions to ease computation of resource-intensive tasks, providing eventful intelligence overall traffic, and vehicle management. The edge cloud could provide localised value-added services such as traffic updates, local events, and so on. |
| Heterogeneous size | Cloud services are envisioned to cater to individual and varying groups of CCAVs across several geographical regions. |
| Large scalable and unbounded network | Urban and rural areas, including highways, are to be connected across the nation. The network should be highly scalable and unbounded. |
| Dynamic network topology | CCAVs’ mobility and change in the network can lead to wireless interference, challenging accurate and timely information for vehicular awareness. |
| Energy and real-time computation power | Connected infrastructures have powerful computational capabilities and should ensure high availability and reliability for CCAVs in order to provide real-time updates. |
| Communication | Regular communication of data packets will be through discrete and hybrid wireless communication channels, such as DSRC, WAVE, IEEE 802.11p, 5G, and 4G LTE. |
| Physical protection | Cloud, edge cloud, and RSUs would be installed with state-of-the-art technologies to support CCAVs. Physical protection of RSU is vital to prevent adversaries from tampering with any infrastructure components. |
| Predictability | The infrastructure units are needed to learn about the changing environment by collecting periodic updates. Through this data analysis, it is expected that additional information may be extracted to predict upcoming events, accidents, failures, traffic, etc. |
| Characteristics of V2V features | |
| Optimal processing power based on CCAV models | Different CCAVs have different capabilities which should be standardised to process messages through novel adaptive techniques. |
| Message broadcast | CCAV can broadcast periodic messages notifying the neighbouring vehicles of their whereabouts. This message would contain information about vehicle movement dynamics. |
| Trust Domains | |||
|---|---|---|---|
| Sr. No. | CCAV (V-TD) | Edge Cloud (E-TD) | Cloud (C-TD) |
| 1 | Wireless Communications | Wireless Communications | Wireless Communications |
| 2 | Infotainment | Microservices | Data Analysis |
| 3 | Data Storage | API | Microservices |
| 4 | Vehicle Sensors | Physical I/O | API |
| 5 | Physical Input/Output | Process | Data Analysis & Data Storage |
| 6 | Monitoring | Data Storage | Monitoring & logging |
| 7 | HMI | Energy Systems | Physical I/O |
| 8 | Energy System | Actuators | Energy System |
| 9 | Actuators | Monitoring | |
| 10 | Data analysis | Sensors | |
| 11 | Devices and peripherals | Devices | |
| 12 | Roadside Infrastructure | ||
| Threats | CCAV | Edge/Cloud |
|---|---|---|
| Literature | 76 | 56 |
| Real Life | 86 | 32 |
| Platooning | 86 | 94 |
| Starting Secure | Running Secure | Staying Secure |
|---|---|---|
| Root of trust establishment | Trustworthy system | Integrity protection |
| Hardware and software | Validated inputs | Update through trusted and authenticated source |
| Integrity policies | Detection and prevention runtime attacks | Updating only authorised modules |
| Freshness in update process | ||
| Maintaining trustworthiness through re-establishment of updated components |
| Future Works | Description |
|---|---|
| Advancements in Secure System Lifecycle Management |
|
| Evolution of Threat Modeling and Risk Assessment methods |
|
| Optimising Security for Resource-Constrained CCAVs |
|
| Establishment of Multifaceted Trust Mechanisms and Framework for CCAVs |
|
| Implementing Zero Trust Architecture in CCAVs |
|
| Strategies for Mitigating Privacy Risks |
|
| Addressing Data Scarcity in CCAV Development |
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sheik, A.T.; Maple, C.; Epiphaniou, G.; Dianati, M. A Comprehensive Survey of Threats in Platooning—A Cloud-Assisted Connected and Autonomous Vehicle Application. Information 2024, 15, 14. https://doi.org/10.3390/info15010014
Sheik AT, Maple C, Epiphaniou G, Dianati M. A Comprehensive Survey of Threats in Platooning—A Cloud-Assisted Connected and Autonomous Vehicle Application. Information. 2024; 15(1):14. https://doi.org/10.3390/info15010014
Chicago/Turabian StyleSheik, Al Tariq, Carsten Maple, Gregory Epiphaniou, and Mehrdad Dianati. 2024. "A Comprehensive Survey of Threats in Platooning—A Cloud-Assisted Connected and Autonomous Vehicle Application" Information 15, no. 1: 14. https://doi.org/10.3390/info15010014
APA StyleSheik, A. T., Maple, C., Epiphaniou, G., & Dianati, M. (2024). A Comprehensive Survey of Threats in Platooning—A Cloud-Assisted Connected and Autonomous Vehicle Application. Information, 15(1), 14. https://doi.org/10.3390/info15010014










