Digital-Twin-Based Security Analytics for the Internet of Things
Abstract
1. Introduction
- We comprehensively align security analytics with digital twins and illustrate how to generate and share cybersecurity knowledge between lifecycle participants.
- We provide a novel formal model for digital twins and security analytics. This formal model assists in implementing digital-twin-based security analytics use cases.
- We envision the DT2SA model for digital twins and security analytics. This model integrates the Industrial IoT and mediates a global understanding for further research and practical adoption.
- We instantiate the DT2SA model by implementing a microservice architecture leveraging digital twin-based security analytics based on a real-world research project. Twinsight enables digital-twin-based threat and incident detection using open-source software.
2. Background and Related Work
2.1. Digital Twins for Security Operations
- Analytics—using state data with statistical analysis.
- Simulation—using specification data with emulation or simulation techniques.
- Replication—using specification and state data with emulation or stimuli techniques.
2.2. Security Analytics
- Descriptive analytics: What has happened?
- Diagnostic analytics: Why did it happen?
- Discovery analytics: What is happening?
- Predictive analytics: What will happen?
- Prescriptive analytics: What should one do?

2.3. Related Work
3. Managing Cybersecurity Knowledge
3.1. Cybersecurity Knowledge Generation
3.2. Cybersecurity Knowledge Sharing
3.3. Requirements
3.4. Intertwining Environments
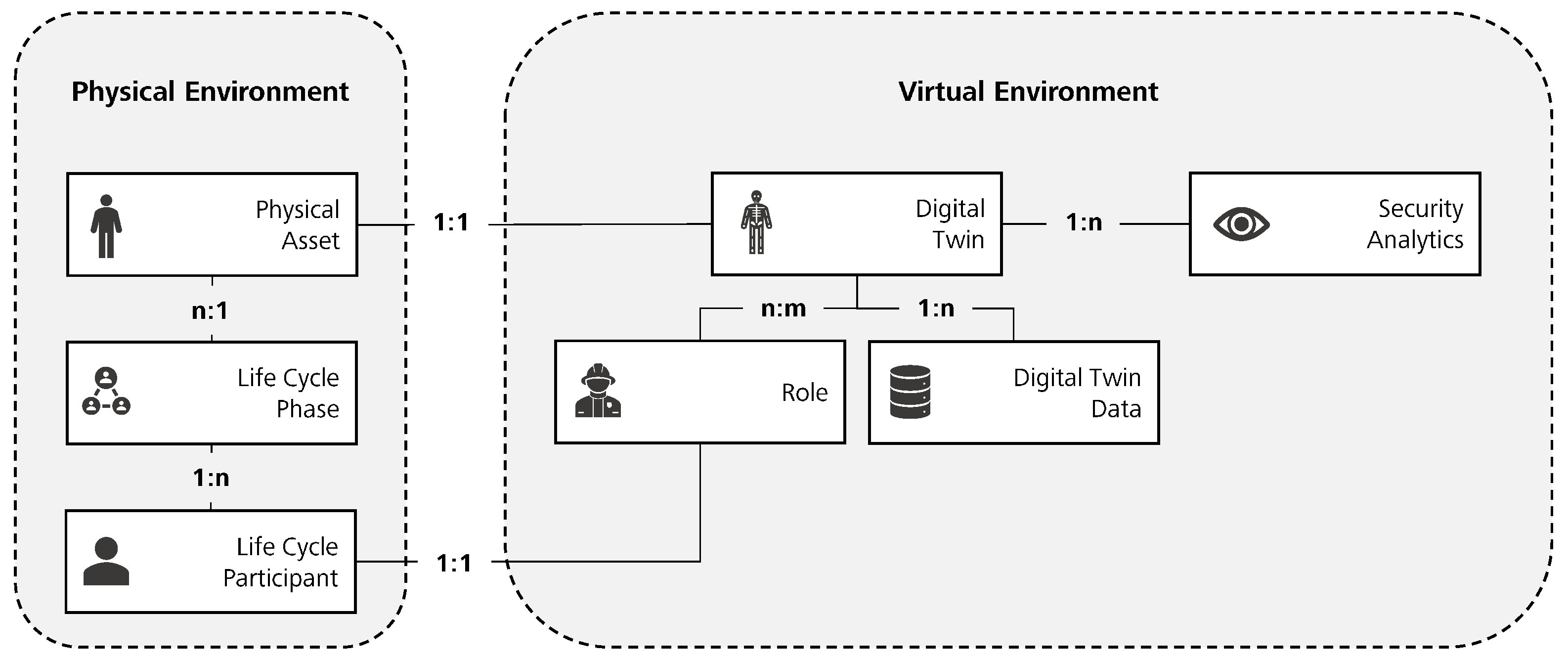
4. Formal Model
4.1. Physical Environment
4.2. Virtual Environment
4.3. Security Analytics
5. DT2SA Model
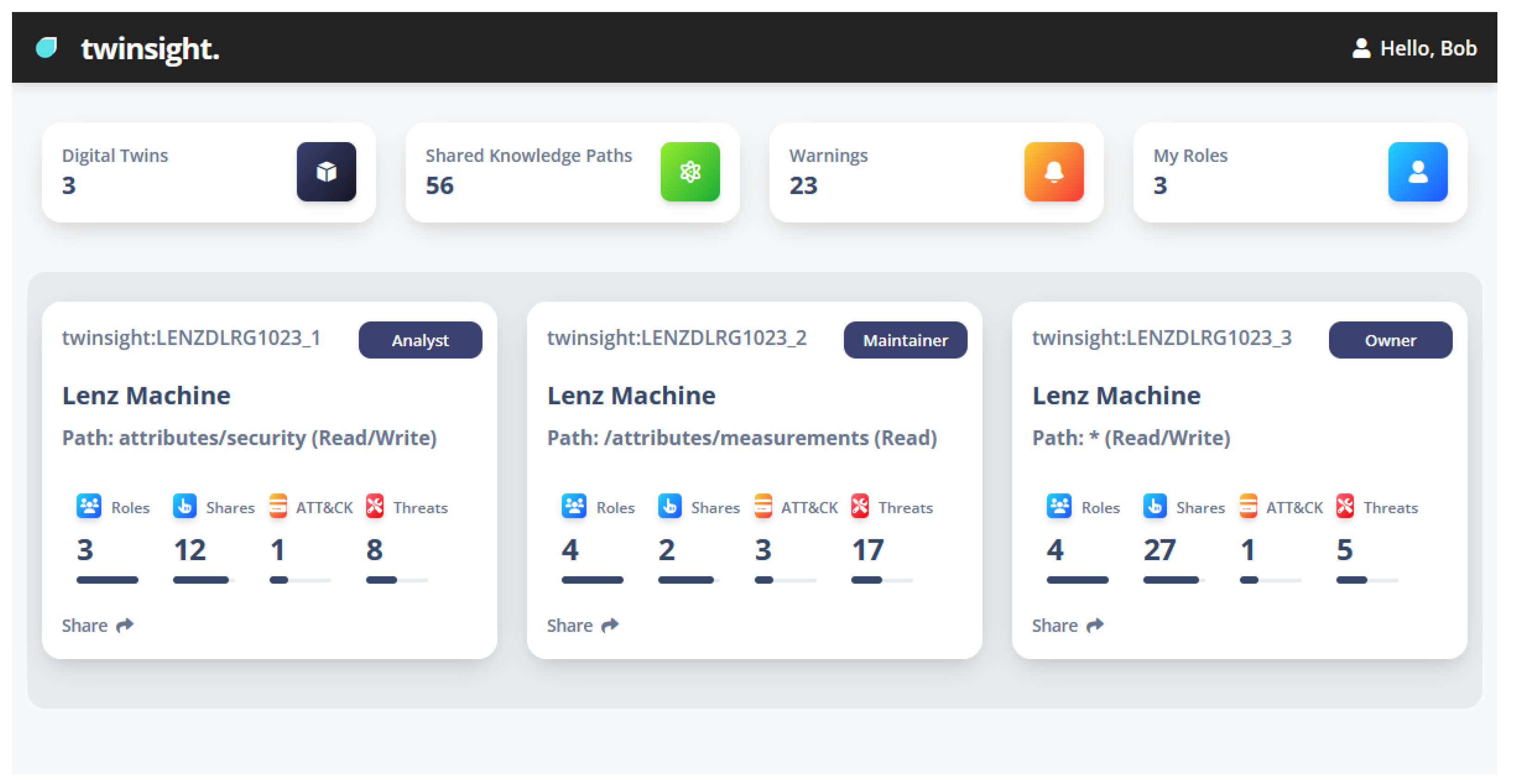
6. Proof of Concept
6.1. DT2SA Components
6.2. Use Case: SISSeC
6.3. Applicability
6.4. Experimental Setup
6.5. Results
| Listing 1. Digital Twin Definition in Eclipse Ditto. |
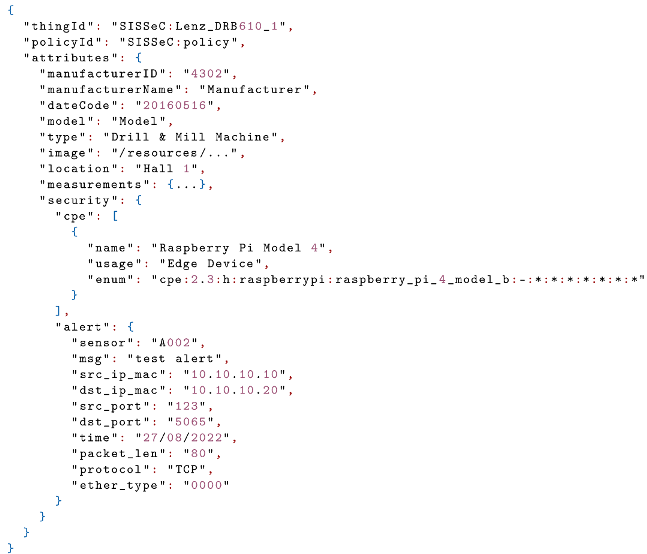 |
6.6. Discussion
7. Conclusions and Future Work
- Future research should address decision support for selecting digital twin modes and analytic operations. In particular, whether an analytic operation supports a particular application scenario should be investigated. The goal is to assist analysts in selecting appropriate operation modes for their scenarios. However, the digital twin offers significant cybersecurity opportunities that need to be more fully explored and exploited.
- There is still a considerable need for research, especially in the area of security analytics, since research has focused only on intrusion detection. For example, research should address different analytics implementations based on digital twins. In particular, security monitoring for IoT is urgently needed, as heterogeneous IoT assets form opaque IoT networks. In addition, security analytics research should compare traditional security analytics approaches, such as those implemented in Wazuh, with system-of-systems approaches. It is of the highest interest to evaluate whether analysts using system-of-systems approaches are even more efficient at detecting incidents. Our Twinsight UI highlights opportunities for this evaluation. In addition, there is a significant need for research in implementing a Wazuh plugin for modeling complex system of systems. Finally, future research should work to leverage digital twin recommendations to secure controllable and addressable IoT networks proactively.
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Appendix A. Security Analytics Using Wazuh
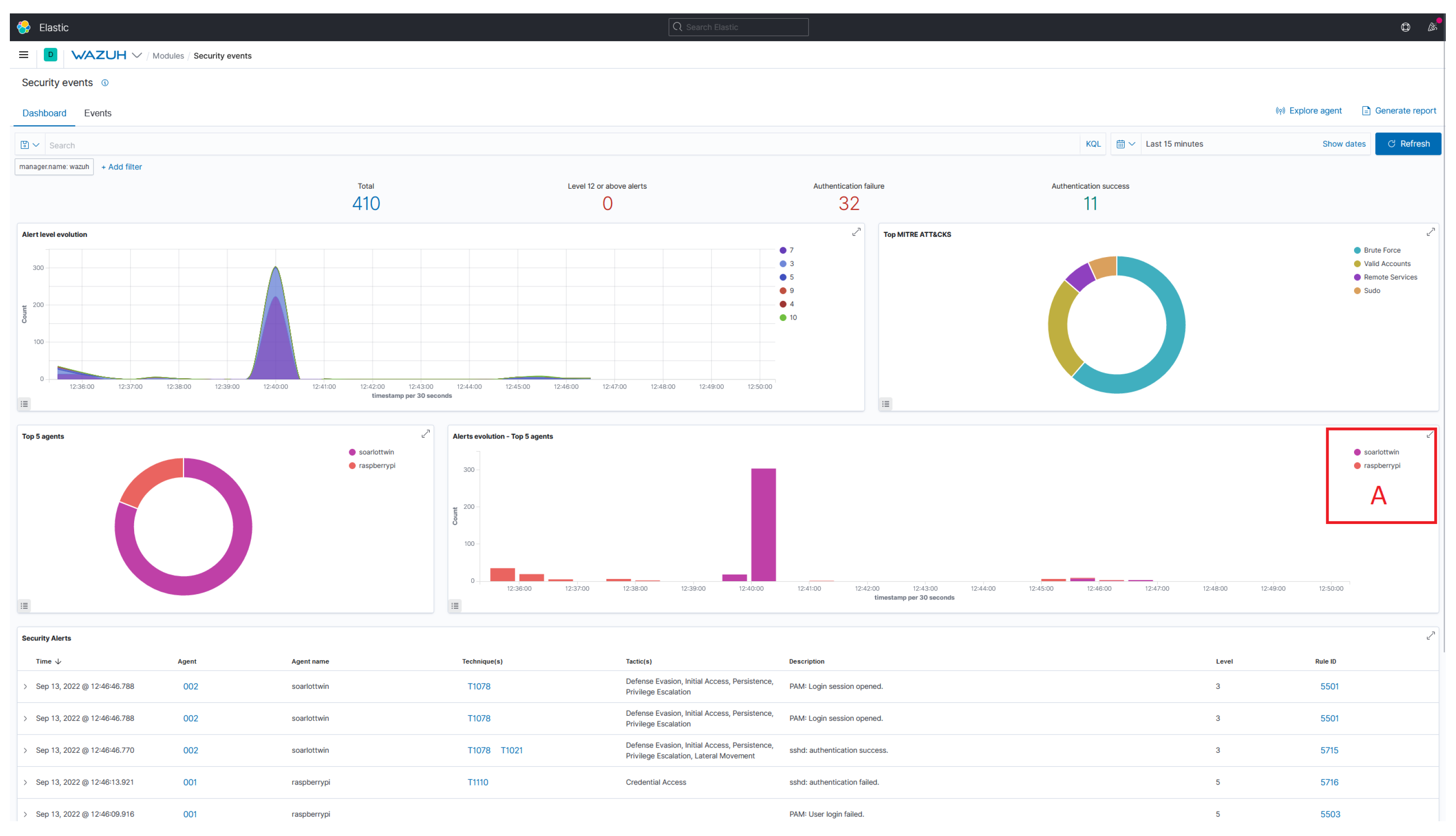
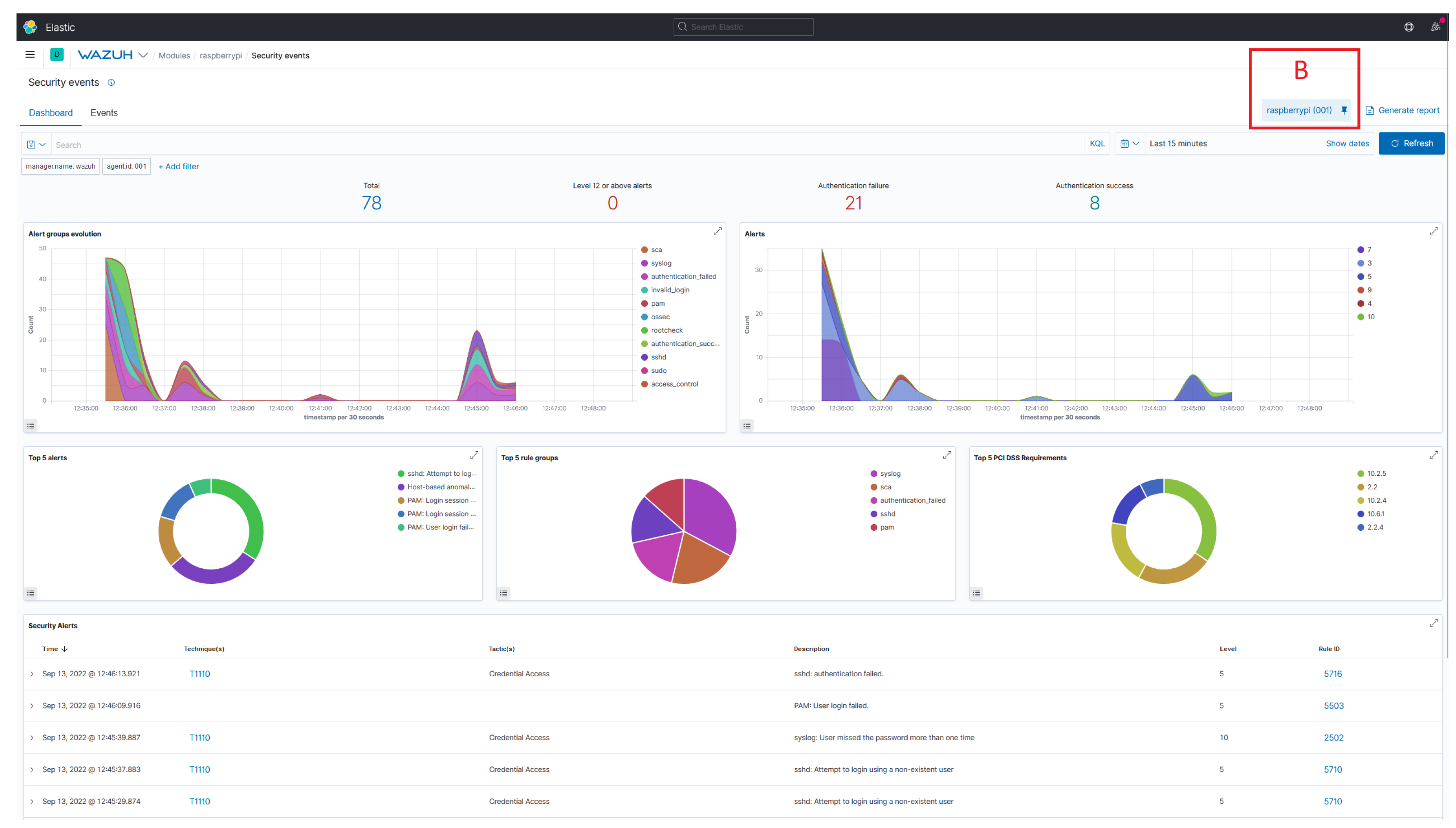
References
- ENISA. Threat Landscape for Supply Chain Attacks; Technical report; ENISA: Athens, Greece, 2021. [Google Scholar]
- Ardagna, C.; Corbiaux, S.; Sfakianakis, A.; Douligeris, C. ENISA Threat Landscape; Technical report; ENISA: Athens, Greece, 2021. [Google Scholar]
- Mahmood, T.; Afzal, U. Security Analytics: Big Data Analytics for Cybersecurity: A Review of Trends, Techniques and Tools. In Proceedings of the 2nd National Conference on Information Assurance (NCIA 2013), Rawalpindi, Pakistan, 11–12 December 2013; pp. 129–134. [Google Scholar]
- Böhm, F.; Vielberth, M.; Pernul, G. Bridging Knowledge Gaps in Security Analytics. In Proceedings of the Proceedings of the 7th International Conference on Information Systems Security and Privacy, ICISSP 2021, Online Streaming, 11–13 February 2021; Mori, P., Lenzini, G., Furnell, S., Eds.; SCITEPRESS: Setubal, Portugal, 2021; pp. 98–108. [Google Scholar] [CrossRef]
- Skouloudi, C.; Malatras, A.; Naydenov, R.; Dede, G. Guidelines for Securing the Internet of Things; Technical report; European Union Agency for Cybersecurity: Athens, Greece, 2020. [Google Scholar]
- Pipikaite, A.; Bueermann, G.; Joshi, A.; Jurgen, J.; Bissell, K.; Aguirre, C.; Browder, T.; Pruitt, J. Global Cybersecurity Outlook 2022: Insight Report; Technical report; European Union Agency for Cybersecurity: Athens, Greece, 2022. [Google Scholar]
- Boschert, S.; Heinrich, C.; Rosen, R. Next Generation Digital Twin. In Proceedings of the 12th International Symposium on Tools and Methods of Competitive Engineering (TMCE), Las Palmas de Gran Canaria, Spain, 7–11 May 2018; Horvath, I., Suarez Riviero, J., Hernandez Castellano, P., Eds.; TMCE 2020 Repository: Dublin, Ireleand, 2018; Volume 2018, pp. 209–218. [Google Scholar]
- Eckhart, M.; Ekelhart, A. Digital Twins for Cyber-Physical Systems Security: State of the Art and Outlook. In Security and Quality in Cyber-Physical Systems Engineering, With Forewords by Robert M. Lee and Tom Gilb; Biffl, S., Eckhart, M., Lüder, A., Weippl, E.R., Eds.; Springer: Cham, Switzerland, 2019; pp. 383–412. [Google Scholar] [CrossRef]
- Pokhrel, A.; Katta, V.; Colomo-Palacios, R. Digital Twin for Cybersecurity Incident Prediction: A Multivocal Literature Review. In Proceedings of the IEEE/ACM 42nd International Conference on Software Engineering Workshops, 2020, ICSEW’20, Seoul, Republic of Korea, 27 June–19 July 2020; pp. 671–678. [Google Scholar] [CrossRef]
- O’Connor, L. Strengthening Security with Digital Cyber Twins. 2021. Available online: https://www.accenture.com/us-en/blogs/technology-innovation/lisa-oconnor-strengthening-security-with-digital-cyber-twins (accessed on 29 May 2022).
- Barricelli, B.R.; Casiraghi, E.; Fogli, D. A Survey on Digital Twin: Definitions, Characteristics, Applications, and Design Implications. IEEE Access 2019, 7, 167653–167671. [Google Scholar] [CrossRef]
- Empl, P.; Schlette, D.; Zupfer, D.; Pernul, G. SOAR4IoT: Securing IoT Assets with Digital Twins. In Proceedings of the 17th International Conference on Availability, Reliability and Security (ARES 2022), Vienna, Austria, 23–26 August 2022; Association for Computing Machinery: New York, NY, USA, 2022. [Google Scholar] [CrossRef]
- Alcaraz, C.; Lopez, J. Digital Twin: A Comprehensive Survey of Security Threats. IEEE Commun. Surv. Tutor. 2022, 24, 1475–1503. [Google Scholar] [CrossRef]
- Win, T.Y.; Tianfield, H.; Mair, Q. Big Data Based Security Analytics for Protecting Virtualized Infrastructures in Cloud Computing. IEEE Trans. Big Data 2018, 4, 11–25. [Google Scholar] [CrossRef]
- Siow, E.; Tiropanis, T.; Hall, W. Analytics for the Internet of Things: A Survey. ACM Comput. Surv. 2018, 51, 74:1–74:36. [Google Scholar] [CrossRef]
- Cárdenas, A.A.; Manadhata, P.K.; Rajan, S.P. Big Data Analytics for Security. IEEE Secur. Priv. 2013, 11, 74–76. [Google Scholar] [CrossRef]
- Alguliyev, R.; Imamverdiyev, Y. Big Data: Big Promises for Information Security. In Proceedings of the 8th IEEE International Conference on Application of Information and Communication Technologies (AICT), Astana, Kazakhstan, 15–17 October 2014; pp. 1–4. [Google Scholar] [CrossRef]
- Ackoff, R.L. From Data to Wisdom. J. Appl. Syst. Anal. 1989, 16, 3–9. [Google Scholar]
- Empl, P.; Pernul, G. A Flexible Security Analytics Service for the Industrial IoT. In Proceedings of the 2021 ACM Workshop on Secure and Trustworthy Cyber-Physical Systems, Virtual Event, Charlotte, NC, USA, 28 April 2021; Gupta, M., Abdelsalam, M., Mittal, S., Eds.; ACM: New York, NY, USA, 2021; pp. 23–32. [Google Scholar] [CrossRef]
- Menges, F.; Pernul, G. A comparative analysis of incident reporting formats. Comput. Secur. 2018, 73, 87–101. [Google Scholar] [CrossRef]
- Eckhart, M.; Ekelhart, A. A Specification-based State Replication Approach for Digital Twins. In Proceedings of the 2018 Workshop on Cyber-Physical Systems Security and PrivaCy, CPS-SPC@CCS 2018, Toronto, ON, Canada, 19 October 2018; Lie, D., Mannan, M., Eds.; ACM: New York, NY, USA, 2018; pp. 36–47. [Google Scholar] [CrossRef]
- Dietz, M.; Vielberth, M.; Pernul, G. Integrating Digital Twin Security Simulations in the Security Operations Center. In Proceedings of the 15th International Conference on Availability, Reliability and Security, Dublin, Ireland, 25–28 August 2020; Volkamer, M., Wressnegger, C., Eds.; 2020. ARES ’20. pp. 18:1–18:9. [Google Scholar] [CrossRef]
- Damjanovic-Behrendt, V. A Digital Twin Architecture for Security, Privacy and Safety. ERCIM News 2018, 2018, 25–26. [Google Scholar]
- Sacha, D.; Stoffel, A.; Stoffel, F.; Kwon, B.C.; Ellis, G.P.; Keim, D.A. Knowledge Generation Model for Visual Analytics. IEEE Trans. Vis. Comput. Graph. 2014, 20, 1604–1613. [Google Scholar] [CrossRef] [PubMed]
- Preut, A.; Kopka, J.P.; Clausen, U. Digital Twins for the Circular Economy. Sustainability 2021, 13, 467. [Google Scholar] [CrossRef]
- Putz, B.; Dietz, M.; Empl, P.; Pernul, G. EtherTwin: Blockchain-based Secure Digital Twin Information Management. Inf. Process. Manag. 2021, 58, 102425. [Google Scholar] [CrossRef]
- Kritzinger, W.; Karner, M.; Traar, G.; Henjes, J.; Sihn, W. Digital Twin in Manufacturing: A Categorical Literature Review and Classification. IFAC-PapersOnLine 2018, 51, 1016–1022. [Google Scholar] [CrossRef]
- Dietz, M.; Pernul, G. Unleashing the Digital Twin’s Potential for ICS Security. IEEE Secur. Priv. 2020, 18, 20–27. [Google Scholar] [CrossRef]
- Dietz, M.; Putz, B.; Pernul, G. A Distributed Ledger Approach to Digital Twin Secure Data Sharing. In Proceedings of the Data and Applications Security and Privacy XXXIII—33rd Annual IFIP WG 11.3 Conference, DBSec 2019, Charleston, SC, USA, 15–17 July 2019; Lecture Notes in Computer, Science. Foley, S.N., Ed.; Springer: Cham, Switzerland, 2019; Volume 11559, pp. 281–300. [Google Scholar] [CrossRef]
- Lin, S.W.; Miller, B.; Durand, J.; Joshi, R.; Didier, P.; Chigani, A.; Torenbeek, R.; Duggal, D.; Martin, R.; Bleakley, G. Industrial Internet Reference Architecture; Technical report; Industry IoT Consortium: Boston, MA, USA, 2015. [Google Scholar]
- Akbarian, F.; Fitzgerald, E.; Kihl, M. Intrusion Detection in Digital Twins for Industrial Control Systems. In Proceedings of the 2020 International Conference on Software, Telecommunications and Computer Networks (SoftCOM), Split, Croatia, 17–19 September 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Atalay, M.; Angin, P. A Digital Twins Approach to Smart Grid Security Testing and Standardization. In Proceedings of the 2020 IEEE International Workshop on Metrology for Industry 4.0 & IoT, Roma, Italy, 3–5 June 2020; pp. 435–440. [Google Scholar] [CrossRef]
- Castellani, A.; Schmitt, S.; Squartini, S. Real-world Anomaly Detection by Using Digital Twin Systems and Weakly Supervised Learning. IEEE Trans. Ind. Inform. 2021, 17, 4733–4742. [Google Scholar] [CrossRef]
- Murillo, A.; Taormina, R.; Tippenhauer, N.; Galelli, S. Co-simulating Physical Processes and Network Data for High-fidelity Cyber-security Experiments. In Proceedings of the Sixth Annual Industrial Control System Security (ICSS) Workshop, 2020, ICSS 2020, Austin, TX, USA, 8 December 2020; pp. 13–20. [Google Scholar] [CrossRef]
- Saad, A.; Faddel, S.; Mohammed, O. Iot-based Digital Twin for Energy Cyber-physical Systems: Design and Implementation. Energies 2020, 13, 4762. [Google Scholar] [CrossRef]
- Suhail, S.; Jurdak, R.; Matulevicius, R.; Seon Hong, C. Securing Cyber-physical Systems through Blockchain-based Digital Twins and Threat Intelligence. arXiv 2021, arXiv:2105.08886. [Google Scholar]
- Chukkapalli, S.S.L.; Pillai, N.; Mittal, S.; Joshi, A. Cyber-physical System Security Surveillance Using Knowledge Graph Based Digital Twins—A Smart Farming Usecase. In Proceedings of the 2021 IEEE International Conference on Intelligence and Security Informatics (ISI), Antonio, TX, USA, 2–3 November 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Danilczyk, W.; Sun, Y.L.; He, H. Smart Grid Anomaly Detection Using a Deep Learning Digital Twin. In Proceedings of the 2020 52nd North American Power Symposium (NAPS), Tempe, AZ, USA, 11–13 April 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Patel, A.; Schenk, T.; Knorn, S.; Patzlaff, H.; Obradovic, D.; Halblaub, A.B. Real-time, Simulation-based Identification of Cyber-security Attacks of Industrial Plants. In Proceedings of the 2021 IEEE International Conference on Cyber Security and Resilience (CSR), Virtual, 26–28 July 2021; pp. 267–272. [Google Scholar] [CrossRef]
- Garcia, H.E.; Aumeier, S.E.; Al-Rashdan, A.Y.; Rolston, B.L. Secure Embedded Intelligence in Nuclear Systems: Framework and Methods. Ann. Nucl. Energy 2020, 140, 107261. [Google Scholar] [CrossRef]
- Tärneberg, W.; Skarin, P.; Gehrmann, C.; Kihl, M. Prototyping Intrusion Detection in an Industrial Cloud-native Digital Twin. In Proceedings of the International Conference on Industrial Technology, Valencia, Spain, 10–12 March 2021. [Google Scholar]
- Dietz, M.; Englbrecht, L.; Pernul, G. Enhancing Industrial Control System Forensics Using Replication-based Digital Twins. In Advances in Digital Forensics XVII; Peterson, G., Shenoi, S., Eds.; Springer International Publishing: Berlin/Heidelberg, Germany, 2021; Volume 612, pp. 21–38. [Google Scholar] [CrossRef]
- Dietz, M.; Schlette, D.; Pernul, G. Harnessing Digital Twin Security Simulations for systematic Cyber Threat Intelligence. In Proceedings of the 2022 IEEE 46th Annual Computers, Software, and Applications Conference (COMPSAC), Los Alamitos, CA, USA, 27 June–1 July 2022; pp. 789–797. [Google Scholar] [CrossRef]



Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Empl, P.; Pernul, G. Digital-Twin-Based Security Analytics for the Internet of Things. Information 2023, 14, 95. https://doi.org/10.3390/info14020095
Empl P, Pernul G. Digital-Twin-Based Security Analytics for the Internet of Things. Information. 2023; 14(2):95. https://doi.org/10.3390/info14020095
Chicago/Turabian StyleEmpl, Philip, and Günther Pernul. 2023. "Digital-Twin-Based Security Analytics for the Internet of Things" Information 14, no. 2: 95. https://doi.org/10.3390/info14020095
APA StyleEmpl, P., & Pernul, G. (2023). Digital-Twin-Based Security Analytics for the Internet of Things. Information, 14(2), 95. https://doi.org/10.3390/info14020095







