Study About the Performance of Ascon in Arduino Devices
Abstract
1. Introduction
2. The Ascon Cipher Suite
2.1. Ascon as Authenticated Encryption
- The master key, K, which has a length bits.
- The rate, r, defining the data block size.
- The number of the permutation rounds, a, in the initialization and finalization phases.
- The number of permutation rounds, b, in the intermediate phase.
2.2. Ascon Hash Functionality
2.3. State of Ascon
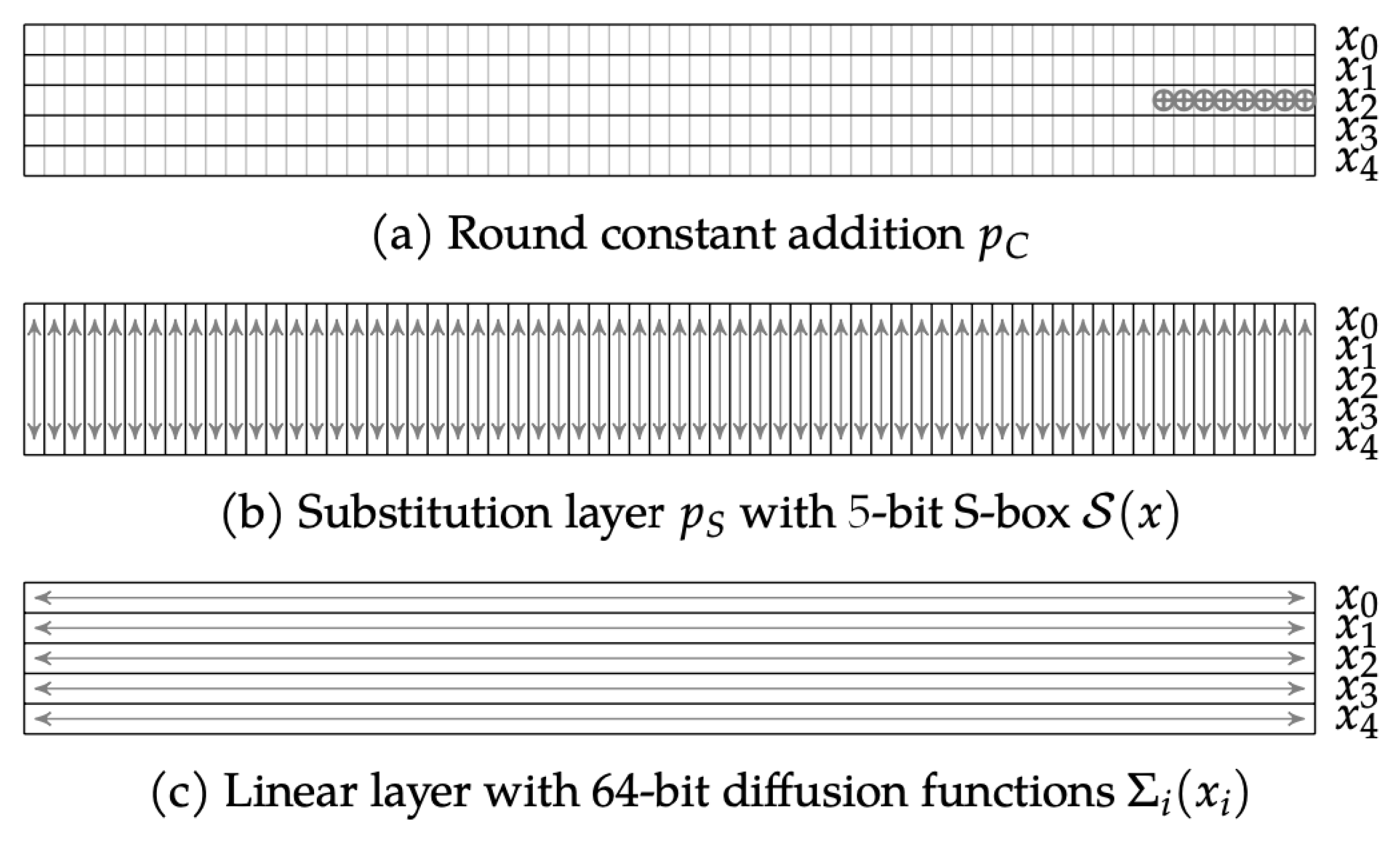
2.4. The Ascon Permutation
2.4.1. Addition of Constants Layer,
2.4.2. Substitution Layer,
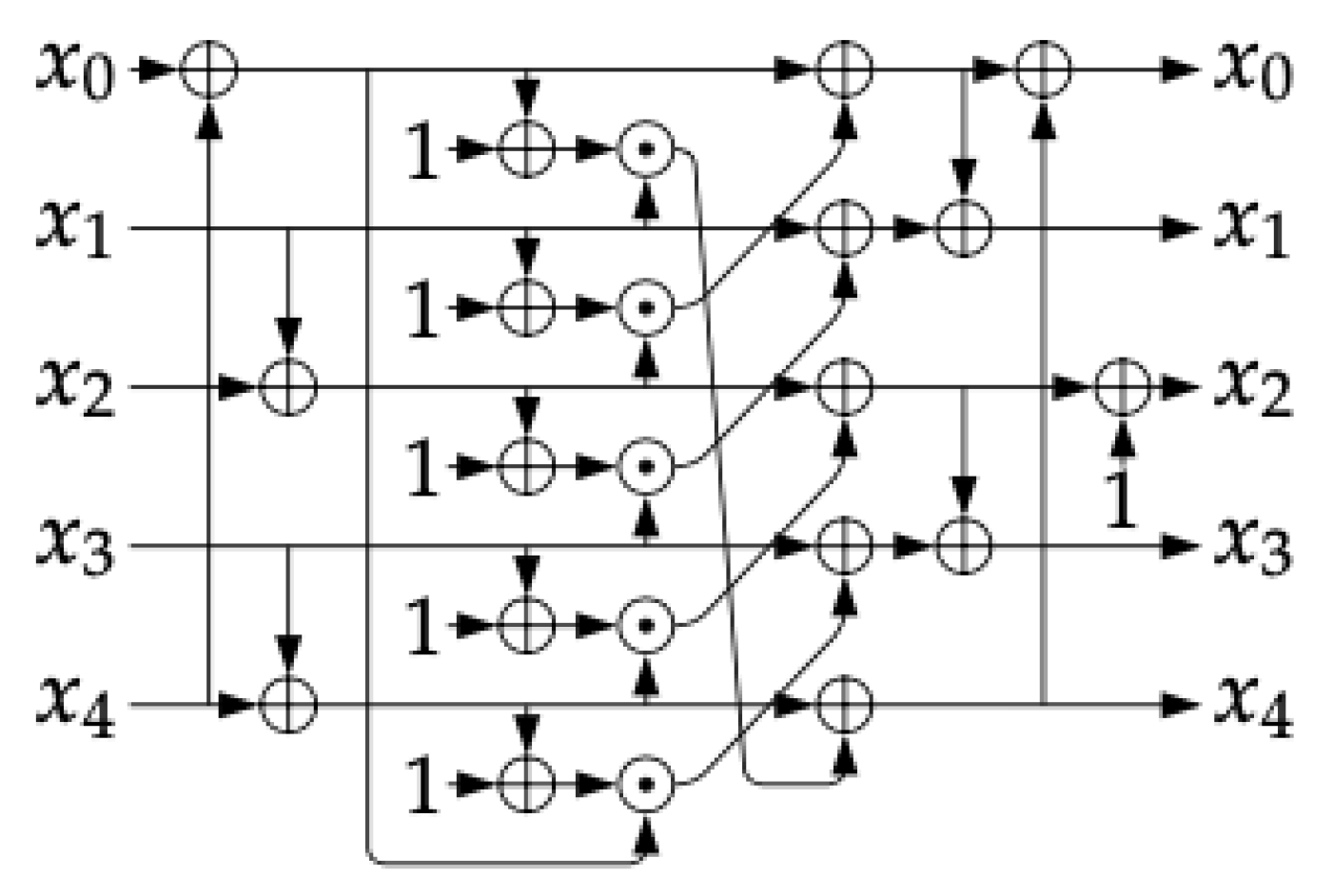
2.4.3. Linear Diffusion Layer
3. Ascon as Authenticated Encryption
3.1. MonkeyDuplex Construction
- It is an object that, upon creation, is loaded with a message authentication code (MAC), a key, and a nonce. Once initialized, duplex calls can be performed by providing an input string and requesting an output string. Its main characteristic is that the output string depends on all the previous input strings, the key, and the nonce.
- The initialization of the b-bit state of the construction is performed by concatenating the key and the nonce, among others, subject to n initial rounds. This is where permutation comes in. If the permutation is good enough in terms of security, the state values of MonkeyDuplex objects with different nonce values can be considered to be independent. In this case, state recovery by an attacker with access to multiple objects gains no advantage over state recovery from a single object.
- The duplexing calls are quantitatively the same as in the Duplex construction. It is possible to reduce the number of rounds of the permutation, without compromising the scheme’s robustness, provided that an initialization protocol is established. As such, differential attacks will be unfeasible, i.e., an attacker would have no knowledge of the difference between the different objects in the MonkeyDuplex construction.
- The difficulty of recovering a state is directly proportional to the number n of rounds of the permutation, and inversely proportional to the size of r. The efficiency is determined by the parameter .Indeed, a larger value of r allows one to process a larger amount of data per iteration, while a smaller value of n reduces the number of permutation operations required per data block, speeding up the computation. Consequently, the ratio represents the number of useful bits processed per round of permutation applied. The greater , the more efficient the scheme, since the amount of data processed per computational unit is maximized.
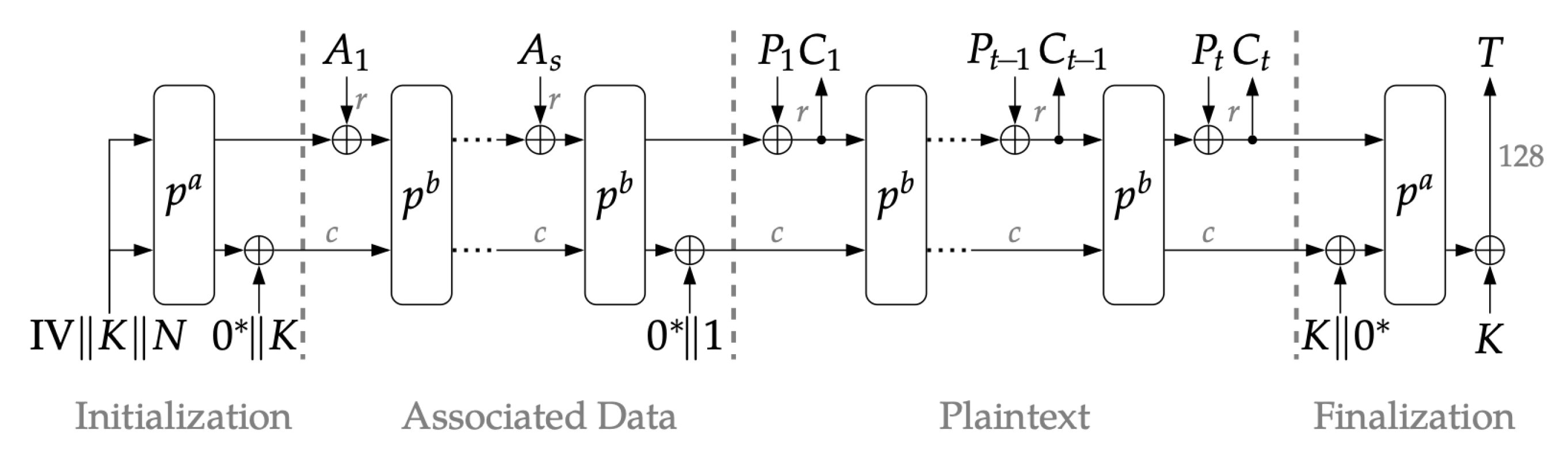
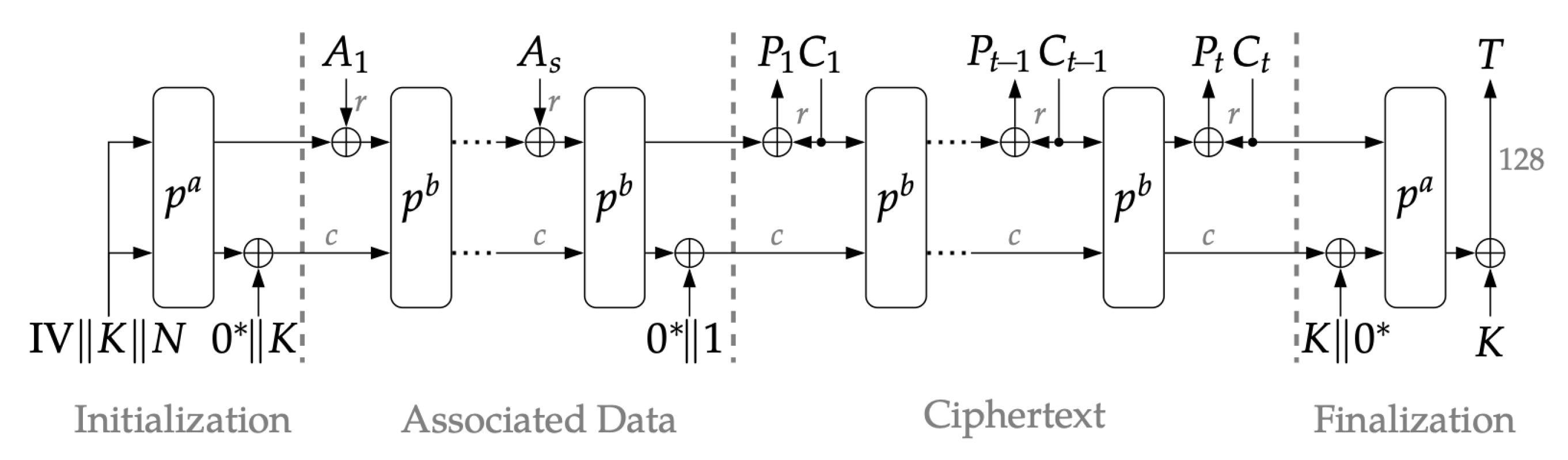
3.2. Ascon AEAD Operation
| Algorithm 1 Initialization process |
Input: key , and nonce Output: update S (modifies internal state) |
| Algorithm 2 Processing associated data |
Input: associated data and internal state S if then divide A into r-bits blocks by concatenating (padded to make the last block exactly r-bits long) for do end for end if Output: update S (modifies internal state) |
| Algorithm 3 Encryption (processing plaintext) |
Input: plaintext and internal state S divide P into r-bits blocks by concatenating (padded to make the last block exactly r-bits long) fordo end for Output: ciphertext and updated state S |
| Algorithm 4 Decryption (processing ciphertext) |
Input: ciphertext and internal state S r-bit blocks of C, for
do end for Output: plaintext and updated state S |
| Algorithm 5 Finalization process (encryption) |
Input: key , and internal state S Output: tag |
| Algorithm 6 Finalization process (verification of decryption) |
Input: key , and internal state S ifthen else end if Output: F |
3.3. Some Application Domains for Ascon in Arduino-Based Systems
- Home automation and smart devices: In smart home applications, Arduino boards are commonly used to control lighting systems, electronic locks, motion detectors, and environmental sensors. These devices typically communicate over Wi-Fi, Bluetooth, or Zigbee protocols, making them susceptible to replay, spoofing, and man-in-the-middle attacks. Ascon’s lightweight authenticated encryption enables secure communication between nodes, especially in constrained devices with less than 32 KB of RAM [15].
- Smart agriculture and environmental monitoring: Low-power sensor nodes deployed in agricultural environments often rely on boards like Arduino MKR WAN 1310 with LoRa (long-range) connectivity to monitor soil moisture, temperature, or air quality. Because these sensors operate autonomously for long periods, data encryption must be both energy-efficient and robust. Ascon meets these requirements, offering authenticated encryption with a code footprint of less than 10 KB, and minimal CPU usage [16].
- Urban sensing and smart cities: Academic and experimental deployments in smart city infrastructures frequently use Arduino-based networks to monitor variables such as CO2 levels, traffic density, and ambient noise. These applications require secure transmission of public data across distributed systems. Incorporating Ascon allows end-to-end encryption and data integrity checks, without impacting real-time data acquisition and transmission performance.
4. Security Analysis
4.1. Algebraic Attacks
4.1.1. Differential and Linear Cryptanalysis
4.1.2. Cube Attacks
4.2. Side-Channel Attacks
4.3. Side-Channel Attacks Against Arduino Devices
4.4. Security Bound for Ascon
5. Performance Analysis of the Ascon Implementation
5.1. Selected Arduino Devices
- Arduino DUE (Arduino S.r.l., Somerville, MA, USA) is based on a powerful 32-bit SAM3X8E ARM Cortex-M3 ARM microcontroller, with 96 KB of SRAM memory (divided into two banks, one of 64 KB and the other one of 32 KB), and with a 512 KB flash memory for the user application, and a clock speed of 84 MHz.
- Arduino Mega2560 (Arduino S.r.l., Somerville, MA, USA) (less powerful than the previous one) is a board based on the 8-bit AVR CPU core ATmega2560 microcontroller, 256 KB flash memory, of which 8 KB are used by the bootloader, and a clock speed of 16 MHz.
- Arduino Nano Every (Arduino S.r.l., Somerville, MA, USA) is based on an 8-bit AVR CPU core ATMega4809 microcontroller with hardware multiplier, 48 KB flash memory, and a higher clock speed of 20 MHz.
- Arduino Nano ESP32 (Arduino S.r.l., Somerville, MA, USA) has the u-Blox NORA-W106-10B processor, which is based on SP32-S3 RISC-V microcontroller of dual core Xtensa LX7. Note that we have used only one core. It can reach speeds of up to 240 MHz. Its memory has 512 KB SRAM, 384 KB ROM, 8 MB PSRAM, and 16 MB flash.
| Algorithm 7 Random data generation for Ascon |
void RandGen(){ for (i = 0; i < C RYPTO_NPUBBYTES; i++) n[i] = rand()%0xFF; for (i = 0; i < CRYPTO_KEYBYTES;i++) k[i]=rand()%0xFF; for (i = 0; i < 16; i++) { a[i] = r and()%0xFF; m[i] = r and()%0xFF; } } |
5.2. Measures in the Encryption/Decryption Operations with Ascon
5.3. Measures in the Encryption/Decryption Operations with AES
| Algorithm 8 Random keys and random data for AES. |
void RandGen(){ for(i = 0; i < 16; i++){ plain[i] = rand()%0xFF; key[i] = rand()%0xFF; } } |
5.4. Analysis of the Results
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| AEAD | Authenticated Encryption algorithm with Associated Data |
| AES | Advanced Encryption Standard |
| CPA | Correlation Power Analysis |
| CPU | Central Processing Unit |
| DDT | Differential Distribution Table |
| DFA | Differential Fault Analysis |
| DL | Deep Learning |
| DoS | Denial of Service |
| DP | Differential Probability |
| DPA | Differential Power Analysis |
| ECG | Electrocardiogram |
| FPGA | Field Programmable Gate Array |
| GDPR | General Data Protection Regulation |
| HDL | Hardware Description Language |
| HIPAA | Health Insurance Portability and Accountability Act |
| ICS | Industrial Control Systems |
| IDE | Integrated Development Environment |
| IoT | Internet of Things |
| Initialization vector | |
| LDT | Linear Approximation Table |
| LoRa | Long Range |
| LSB | Lest Significant Bit |
| LSTM | Long Short-Term Memory |
| LwC | Lightweight Cryptography |
| MAC | Message Authentication Code |
| MDP | Maximum probability of DP |
| MILP | Mixed Integer Linear Programming |
| ML | Machine Learning |
| MSB | Most Significant Bit |
| NIST | National Institute of Standards and Technology |
| PC | Personal Computer |
| PLC | Programmable Logic Controllers |
| QKD | Quantum Key Distribution |
| RAM | Random-Access Memory |
| RF | Radio Frequency |
| SAT | Boolean Satisfiability |
| SCARL | Side-Channel Attack with Reinforcement Learning |
| SIFA | Statistical Ineffective Fault Analysis |
| SPA | Simple Power Analysis |
| SPN | Substitution–Permutation Network |
| VHDL | VHSIC + HDL |
| VHSIC | Very High Speed Integrated Circuit |
References
- Babbage, S.; Bernstein, D.J.; Biryukov, A.; Canteaut, A.; Cid, C.; Daemen, J.; Dunkelman, O.; Gilbert, H.; Iwata, T.; Lucks, S.; et al. CAESAR: Competition for Authenticated Encryption: Security, Applicability, and Robustness. Technical Report, National Institute of Standards and Technology, NIST IR 8454. 2023. Available online: https://competitions.cr.yp.to/caesar.html (accessed on 18 February 2025).
- NIST. Lightweight Cryptography; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2023. Available online: https://csrc.nist.gov/projects/lightweight-cryptography (accessed on 18 February 2025).
- NIST. Ascon-Based Lightweight Cryptography Standards for Constrained Devices: Authenticated Encryption, Hash, and Extendable Output Functions. Technical Report, National Institute of Standards and Technology, NIST SP 800-232 (Initial Public Draft). 2024. Available online: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-232.ipd.pdf (accessed on 18 February 2025).
- Khan, S.; Lee, W.K.; Hwang, S.O. Scalable and efficient hardware architectures for authenticated encryption in IoT applications. IEEE Internet Things J. 2021, 8, 11260–11275. [Google Scholar] [CrossRef]
- Hernández-Álvarez, L.; Bullón Pérez, J.J.; Kristel Batista, F.; Queiruga-Dios, A. Security Threats and Cryptographic Protocols for Medical Wearables. Mathematics 2022, 10, 886. [Google Scholar] [CrossRef]
- Ul Islam, M.; Nazish, M.; Sultan, I.; Tariq Banday, M. ASCON Lightweight Security Standard for the Internet of Things Devices—A Study. In Proceedings of the International Conference on Innovative Computing and Communication (ICICC 2024), Lecture Notes Networks Systems, London, UK, 16–17 March 2024; Volume 1024, pp. 503–517. [Google Scholar] [CrossRef]
- Radhakrishnan, I.; Jadon, S.; Honnavalli, P.B. Efficiency and Security Evaluation of Lightweight Cryptographic Algorithms for Resource-Constrained IoT Devices. Sensors 2024, 24, 4008. [Google Scholar] [CrossRef] [PubMed]
- Tripathi, D.R.; Akhtar, H.N.N.; Bhandarkar, R.R. Enhancing IOT Security: Encryption Algorithms for Resource-Constrained Devices. Int. J. Res. App. Sci. Eng. Technol. 2024, 12, 350–357. [Google Scholar] [CrossRef]
- García-Callejo, A.; Sarasa Laborda, V.; Hernández Encinas, L.; Fernández, V. QKD authentication using quantum-safe lightweight cryptography: Analysis and Use Cases. In Proceedings of the Poster, 10th ETSI/IQC Quantum Safe Cryptography Event, Berlin, Germany, 18–20 June 2024; Available online: https://digital.csic.es/bitstream/10261/362304/1/QKD_Authentication%20.pdf (accessed on 18 February 2025).
- Dobraunig, C.; Eichlseder, M.; Mendel, F.; Schläffer, M. Ascon v1.2: Lightweight Authenticated Encryption and Hashing. J. Cryptol. 2021, 34, 33. [Google Scholar] [CrossRef]
- Shor, P.W. Polynomial-Time Algorithms for Prime Factorization and Discrete Logarithms on a quantum Computer. SIAM J. Comput. 1997, 26, 1484. [Google Scholar] [CrossRef]
- Grover, L.K. A fast quantum mechanical algorithm for database search. In Proceedings of the 28th Annual Symposium on the Theory of Computing (STOC’96), Philadelphia, PA, USA, 22–24 May 1996; pp. 212–219. [Google Scholar] [CrossRef]
- Bertoni, G.; Daemen, J.; Peeters, M.; Van Assche, G. Permutation-Based Encryption, Authentication and Authenticated Encryption. Keccack Team. 2012. Available online: https://keccak.team/files/KeccakDIAC2012.pdf (accessed on 18 February 2025).
- Dobraunig, C.; Eichlseder, M.; Mendel, F.; Rechberger, C. Ascon—Lightweight Authenticated Encryption and Hash Function. 2019. Available online: https://ascon.iaik.tugraz.at (accessed on 17 February 2025).
- Kandi, A.; Baksi, A.; Gerlich, T.; Guilley, S.; Gan, P.; Breier, J.; Chattopadhyay, A.; Shrivastwa, R.R.; Martinasek, Z.; Bhasin, S. Hardware Implementation of Ascon for Lightweight Cryptography. Presented at NIST Lightweight Cryptography Workshop. 2023. Available online: https://csrc.nist.gov/csrc/media/events/2023/lightweight-cryptography-workshop-2023/documents/accepted-papers/07-hardware-implementation-of-ascon.pdf (accessed on 18 February 2025).
- Salami, B.; Bagula, A. LoRa-based Smart Agriculture: A Case Study. Sensors 2020, 20, 4546. [Google Scholar]
- Safrata, D. Remote Keyless Entry Systems Security Analysis. Master’s Thesis, Czech Technical University in Prague, Faculty of Information Technology, Prague, Czech Republic, 2020. Available online: https://dspace.cvut.cz/bitstream/handle/10467/87825/F8-DP-2020-Safrata-David-thesis.pdf (accessed on 17 February 2025).
- Electronic Design. How to Stop Automotive Key Fob Encryption Hacks. 2020. Available online: https://www.electronicdesign.com/markets/automotive/article/21130290/how-to-stop-automotive-key-fob-encryption-hacks (accessed on 18 February 2025).
- Basha, E.; Farag, H. Energy-Efficient Security in IoT Wearables Using Lightweight Cryptography. Sensors 2022, 22, 1050. [Google Scholar]
- El-Hajj, M.; Mousawi, H.; Fadlallah, A. Analysis of Lightweight Cryptographic Algorithms on IoT Hardware Platforms. Fut. Internet 2023, 15, 54. [Google Scholar] [CrossRef]
- Heys, H.M. A tutorial on Linear and Differential Cryptoanalysis; Memorial University of Newfoundland: St. John’s, NL, Canada, 2017; Available online: http://www.cs.bc.edu/~straubin/crypto2017/heys.pdf (accessed on 17 February 2025).
- Dobraunig, C.; Mendel, F.; Eichlseder, M.; Schlaffer, M. Status Update on Ascon v1.2, Update to the NIST Lightweight Cryptography Standardization Process. Technical Report, NIST. 2022. Available online: https://csrc.nist.gov/CSRC/media/Projects/lightweight-cryptography/documents/round-2/status-update-sep2020/ascon_update.pdf (accessed on 17 February 2025).
- Baudrin, J.; Canteaut, A.; Perrin, L. Practical Cube Attack Against Nonce-Misused Ascon. IACR Trans. Symmetric Cryptol. 2022, 84, 120–144. [Google Scholar] [CrossRef]
- Yadav, T.; Kumar, M. ML based Improved Differential Distinguisher with High Accuracy: Application to GIFT-128 and ASCON. In Proceedings of the Security, Privacy, and Applied Cryptography Engineering—SPACE 2024, Lecture Notes Computer Science, Singapore, 4–6 December 2024; Volume 15351, pp. 287–316. [Google Scholar] [CrossRef]
- Chang, D.; Hong, D.; Kang, J.; Sonmez Turan, M. Resistance od Ascon Family against Conditional Cube Attacks in Nonce-Misuse Setting. IEEE Access 2022, 11, 4501–4516. Available online: https://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=9957054 (accessed on 18 February 2025). [CrossRef]
- Lefevre, C.; Mennink, B. Generic Security of the Ascon Mode: On the Power of Key Blinding. Cryptology ePrint Archive, Report 2023/796. 2023. Available online: https://eprint.iacr.org/2023/796 (accessed on 17 February 2025).
- NIST. Active and Passive Side-Channel Key Recovery Attacks on Ascon. Technical Report, NIST Computer Security Research Center. 2020. Available online: https://csrc.nist.gov/CSRC/media/Events/lightweight-cryptography-workshop-2020/documents/papers/active-passive-recovery-attacks-ascon-lwc2020.pdf (accessed on 19 February 2025).
- Ramezanpour, K.; Ampadu, P.; Diehl, W. SCARL: Side-Channel Analysis with Reinforcement Learning on the Ascon Authenticated Cipher. arXiv 2020, arXiv:2006.03995. [Google Scholar] [CrossRef]
- Jana, A. Differential Fault Attack on Ascon Cipher, Report 2023/1923. 2023. Available online: https://eprint.iacr.org/2023/1923 (accessed on 17 February 2025).
- Jana, A. Differential Fault Attack on Ascon Cipher. In Proceedings of the Progress in Cryptology—INDOCRYPT 2024, Lecture Notes Computer Science, New Delhi, India, 15–18 December 2024; Volume 15496, pp. 53–72. [Google Scholar] [CrossRef]
- Samwel, N. Side-Channel Analysis of Keccak and Ascon. Master’s Thesis, Radboud University Nijmegen, Nijmegen, The Netherlands, 2016. Available online: https://www.cs.ru.nl/masters-theses/2016/N_Samwel___Side-channel_analysis_of_Keccak_and_Ascon.pdf (accessed on 19 February 2025).
- Samwel, N.; Daemen, J. DPA on Hardware Implementations of Ascon and Keyak. 2017, pp. 415–424. Available online: https://dl.acm.org/doi/abs/10.1145/3075564.3079067 (accessed on 19 February 2025).
- Kang, Y.J.; Kim, T.Y.; Jo, J.B.; Lee, H.J. An Experimental CPA attack for Arduino Cryptographic Module and Analysis in Software-based CPA Countermeasures. Int. J. Secur. Its Appl. 2014, 8, 261–270. [Google Scholar] [CrossRef]
- Gamaarachchi, H.; Ganegoda, H. Power Analysis Based Side Channel Attack. arXiv 2018, arXiv:1801.00932. [Google Scholar]
- Durvaux, F.; Durvaux, M. SCA-Pitaya: A Practical and Affordable Side-Channel Attack Setup for Power Leakage-Based Evaluations. Digit. Threat. Res. Pract. 2020, 1, 1–16. [Google Scholar] [CrossRef]
- Nakanose, M.; Kodera, Y.; Kusaka, T.; Nogami, Y. Consideration of the side-channel attack to SPECK implemented on Arduino Uno. In Proceedings of the Ninth International Symposium on Computing and Networking Workshops (CANDARW), Nagasaki, Japan, 23–26 November 2021; pp. 339–345. [Google Scholar] [CrossRef]
- Enami, H.; Kodera, Y.; Kusaka, T.; Nogami, Y. Consideration of the side-channel attack to SIMON implemented on Arduino Uno. In Proceedings of the Ninth International Symposium on Computing and Networking Workshops (CANDARW), Nagasaki, Japan, 23–26 November 2021; pp. 412–415. [Google Scholar] [CrossRef]
- Maro, E.; Girichev, V.; Us, I. Power Analysis of Kuznyechik cipher on Arduino Nano board. In Proceedings of the Ural Symposium on Biomedical Engineering, Radioelectronics and Information Technology (USBEREIT), Yekaterinburg, Russia, 13–14 May 2021; pp. 440–443. [Google Scholar] [CrossRef]
- Dolmatov, V. GOST R 34.12-2015: Block Cipher “Kuznyechik”. RFC 7801 2016. Available online: https://www.rfc-editor.org/rfc/pdfrfc/rfc7801.txt.pdf (accessed on 19 February 2025).
- Jevtic, R.; Perez-Tirador, P.; Cabezaolias, C.; Carnero, P.; Caffarena, G. Side-channel Attack Countermeasure Based on Power Supply Modulation. In Proceedings of the 30th European Signal Processing Conference (EUSIPCO), Belgrade, Serbia, 29 August–2 September 2022; pp. 618–622. [Google Scholar] [CrossRef]
- Chakraborty, B.; Dhar, C.; Nandi, M. Exact Security Analysis of ASCON. In Proceedings of the Advances in Cryptology—ASIACRYPT 2023, Lecture Notes Computer Science, Guangzhou, China, 4–8 December 2023; Volume 14440, pp. 346–369. [Google Scholar] [CrossRef]
- Rohit, R.; Hu, K.; Sarkar, S.; Sun, S. Misuse-Free Key-Recovery and Distinguishing Attacks on 7-Round Ascon. IACR Trans. Symmetric Cryptol. 2021, 1, 130–155. [Google Scholar] [CrossRef]
- Qin, L.; Hua, J.; Dong, X.; Yan, H.; Wang, X. Meet-in-the-Middle Preimage Attacks on Sponge-Based Hashing. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Advances in Cryptology—EUROCRYPT 2023, Lecture Notes Computer Science, Lyon, France, 23–27 April 2023; Volume 14007, pp. 158–188. [Google Scholar] [CrossRef]
- Joshi, P.; Mazumdar, B. A Subset Fault Analysis of ASCON. Cryptology ePrint Archive, Report 2019/1370. 2019. Available online: https://eprint.iacr.org/2019/1370 (accessed on 18 February 2025).
- Degré, M.; Derbez, P.; Lahaye, L.; Schrottenloher, A. New Models for the Cryptanalysis of ASCON. Cryptology ePrint Archive, Report 2024/298. 2024. Available online: https://eprint.iacr.org/2024/298 (accessed on 17 February 2025).
- Weissbart, L.; Picek, S. Lightweight but Not Easy: Side-Channel Analysis of the Ascon Authenticated Cipher on a 32-bit Microcontroller. Cryptology ePrint Archive, Report 2023/1598. 2023. Available online: https://eprint.iacr.org/2023/1598 (accessed on 17 February 2025).
- Rezaeezade, A.; Basurto-Becerra, A.; Weissbart, L.; Perin, G. One for All, All for Ascon: Ensemble-based Deep Learning Side-channel Analysis. In Proceedings of the Applied Cryptography and Network Security Workshops: ACNS 2024 Satellite Workshops, Abu Dhabi, United Arab Emirates, 5–8 March 2024; pp. 139–157. [Google Scholar] [CrossRef]
- Li, H.; He, L.; Chen, S.; Guo, J.; Qiu, W. Automatic Preimage Attack Framework on Ascon Using a Linearize-and-Guess Approach. IACR Trans. Symmetric Cryptol. 2023, 3, 74–100. [Google Scholar] [CrossRef]
- Guo, J.; Liu, M.; Song, L. Linear structures: Applications to cryptanalysis of round-reduced Keccak. In Proceedings of the Advances in Cryptology—ASIACRYPT 2016, Lecture Notes Computer Science, Hanoi, Vietnam, 4–8 December 2016; Volume 10031, pp. 249–274. [Google Scholar] [CrossRef]
- Li, T.; Sun, Y. Preimage attacks on round-reduced Keccak-224/256 via an allocating approach. In Proceedings of the Advances in Cryptology—ASIACRYPT 2016, Lecture Notes Computer Science, Kobe, Japan, 8–12 December 2019; Volume 11478, pp. 556–584. [Google Scholar] [CrossRef]
- Fu, Q.; Luo, Y.; Yang, Q.; Song, L. Preimage and Collision Attacks on Reduced Ascon Using Algebraic Strategies. Cryptology ePrint Archive, Report 2023/1453. 2023. Available online: https://eprint.iacr.org/2023/1453 (accessed on 17 February 2025).
- Baek, S.; Kim, G.; Kim, J. Preimage Attacks on Reduced-Round Ascon-Xof. Cryptology ePrint Archive, Report 2024/371. 2024. Available online: https://eprint.iacr.org/2024/371 (accessed on 18 February 2025).
- Lefevre, C.; Mennink, B. SoK: Security of the Ascon Modes. Cryptology ePrint Archive, Report 2024/1969. 2024. Available online: https://eprint.iacr.org/2024/1969 (accessed on 18 February 2025).
- Chakraborty, B.; Dhar, C.; Nandi, M. Tight Multiuser Security of Ascon and Its Large Key Extension. In Australasian Conference on Information Security and Privacy; Springer Nature: Singapore, 2024; Volume 14895, pp. 57–76. [Google Scholar] [CrossRef]
- Guo, C.; Pereira, O.; Peters, T.; Standaert, F.X. Towards Low-Energy Leakage-Resistant Authenticated Encryption from the Duplex Sponge Construction. Cryptology ePrint Archive, Report 2019/193. 2019. Available online: https://eprint.iacr.org/2019/193 (accessed on 14 February 2025).
- Andreeva, E.; Bogdanov, A.; Luykx, A.; Mennink, B.; Mouha, N.; Yasuda, K. How to Securely Release Unverified Plaintext in Authenticated Encryption. In International Conference on the Theory and Application of Cryptology and Information Security; Springer: Berlin/Heidelberg, Germany, 2014; Volume 8873, pp. 105–125. [Google Scholar] [CrossRef]
- Schläffer, M. Improve Combined and Low-End Implementations. Github Repository. Available online: https://github.com/ascon/ascon-c (accessed on 14 February 2025).
- NIST. Advanced Encryption Standard (AES). Technical Report, National Institute of Standards and Technology, FIPS 197. 2023. Available online: https://nvlpubs.nist.gov/nistpubs/FIPS/NIST.FIPS.197-upd1.pdf (accessed on 18 February 2025).
- Kokke. kokke/tiny-AES-c. Github Repository. Available online: https://github.com/kokke/tiny-AES-c (accessed on 14 February 2025).
- RWeather. Lightweight Crypto Performance Benchmarks on Embedded Systems. 2025. Available online: https://rweather.github.io/lightweight-crypto/performance.html (accessed on 14 February 2025).
| Name | Algorithms | Bit Size | Number of Rounds | ||||
|---|---|---|---|---|---|---|---|
| K | N | T | r | a | b | ||
| Ascon-128 | 128 | 128 | 128 | 64 | 12 | 6 | |
| Ascon-128a | 128 | 128 | 128 | 128 | 12 | 8 | |
| Ascon-80pq | 160 | 128 | 128 | 64 | 12 | 6 | |
| Name | Algorithm | Bit Size | Number of Rounds p | ||||
|---|---|---|---|---|---|---|---|
| H | r | i | a | c | b | ||
| Ascon-HASH | 256 | 64 | 12 | 12 | 12 | 12 | |
| Ascon-HASHa | 256 | 64 | 12 | 8 | 12 | 8 | |
| Ascon-XOF | l | 64 | 12 | 12 | 12 | 12 | |
| Ascon-XOFa | l | 64 | 12 | 8 | 12 | 8 | |
| Constant | Constant | ||||||
|---|---|---|---|---|---|---|---|
| 0 | 000000000000000000f0 | 6 | 2 | 0 | 00000000000000000096 | ||
| 1 | 000000000000000000e1 | 7 | 3 | 1 | 00000000000000000087 | ||
| 2 | 000000000000000000d2 | 8 | 4 | 2 | 00000000000000000078 | ||
| 3 | 000000000000000000c3 | 9 | 5 | 3 | 00000000000000000069 | ||
| 4 | 0 | 000000000000000000b4 | 10 | 6 | 4 | 0000000000000000005a | |
| 5 | 1 | 000000000000000000a5 | 11 | 7 | 5 | 0000000000000000004b |
| x | 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 | 12 | 13 | 14 | 15 |
| 4 | 11 | 31 | 20 | 26 | 21 | 9 | 2 | 27 | 5 | 8 | 18 | 29 | 3 | 6 | 28 | |
| x | 16 | 17 | 18 | 19 | 20 | 21 | 22 | 23 | 24 | 25 | 26 | 27 | 28 | 29 | 30 | 31 |
| 30 | 19 | 7 | 14 | 0 | 13 | 17 | 24 | 16 | 12 | 1 | 25 | 22 | 10 | 15 | 23 |
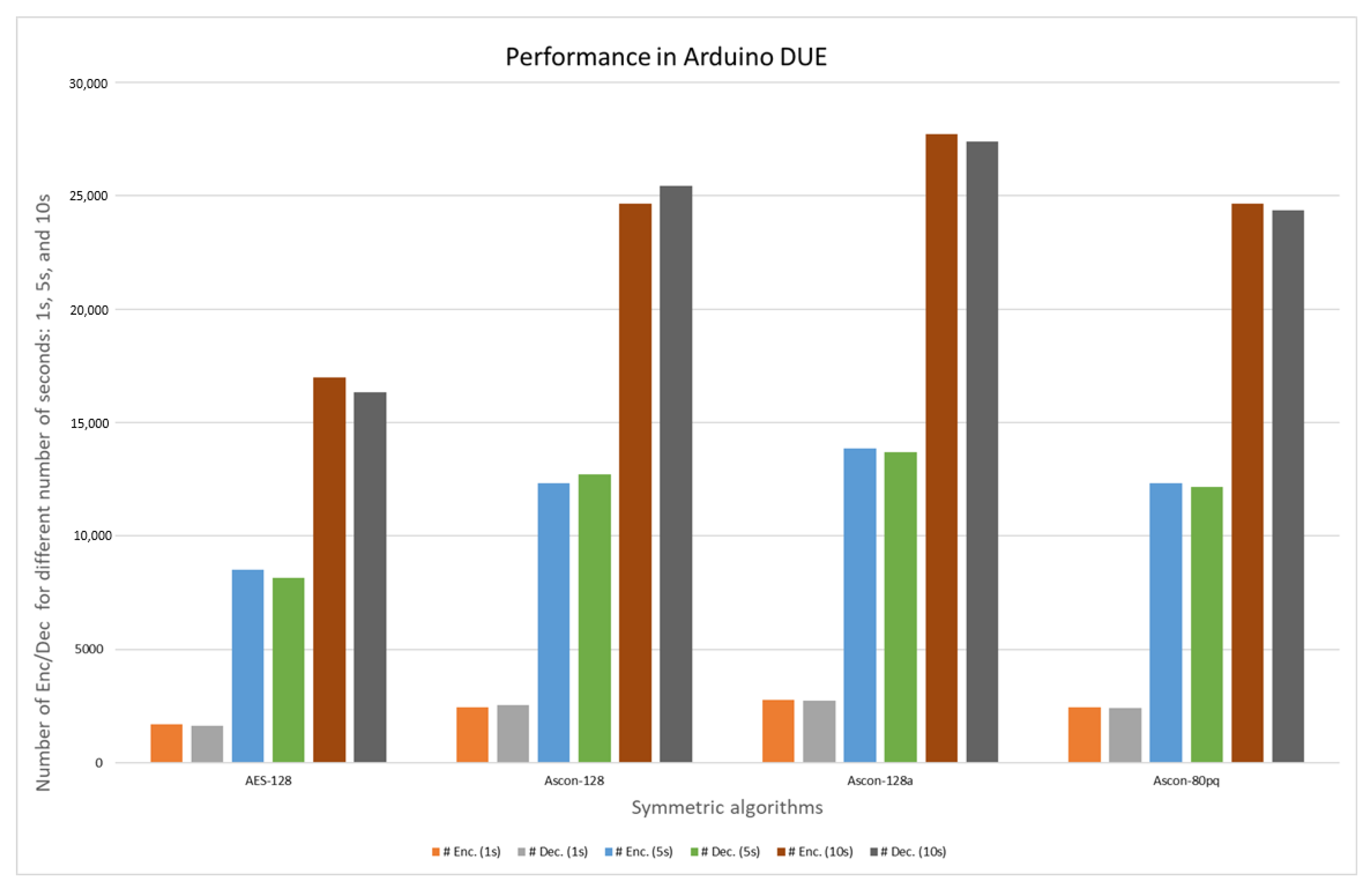
| Variant | Number of Cycles and Encryptions in the Encryption Process. Arduino DUE | |||||
|---|---|---|---|---|---|---|
| # Cyc. (1 s) | # Enc. (1 s) | # Cyc. (5 s) | # Enc. (5 s) | # Cyc. (10 s) | # Enc. (10 s) | |
| Ascon-128 | 84,025,452 | 2464 | 420,008,820 | 12,320 | 840,003,108 | 24,640 |
| Average | 33,015 | — | 33,011 | — | 33,011 | — |
| Ascon-128a | 84,012,768 | 2772 | 420,010,248 | 13,860 | 840,007,812 | 27,720 |
| Average | 30,661 | — | 30,664 | — | 30,663 | — |
| Ascon-80pq | 84,015,876 | 2464 | 420,022,512 | 12,320 | 840,030,492 | 24,640 |
| Average | 34,097 | — | 34,092 | — | 34,092 | — |
| Variant | Number of Cycles and Decryptions in the Decryption Process. Arduino DUE | |||||
|---|---|---|---|---|---|---|
| # Cyc. (1 s) | # Dec. (1 s) | # Cyc. (5 s) | # Dec. (5 s) | # Cyc. (10 s) | # Dec. (10 s) | |
| Ascon-128 | 84,013,860 | 2545 | 420,003,696 | 12,723 | 840,006,636 | 25,446 |
| Average | 33,011 | — | 33,011 | — | 33,011 | — |
| Ascon-128a | 84,018,480 | 2740 | 420,000,840 | 13,697 | 840,000,924 | 27,394 |
| Average | 30,663 | — | 30,663 | — | 30,663 | — |
| Ascon-80pq | 84,028,644 | 2436 | 420,031,332 | 12,178 | 840,016,884 | 24,355 |
| Average | 34,494 | — | 34,490 | — | 34,490 | — |
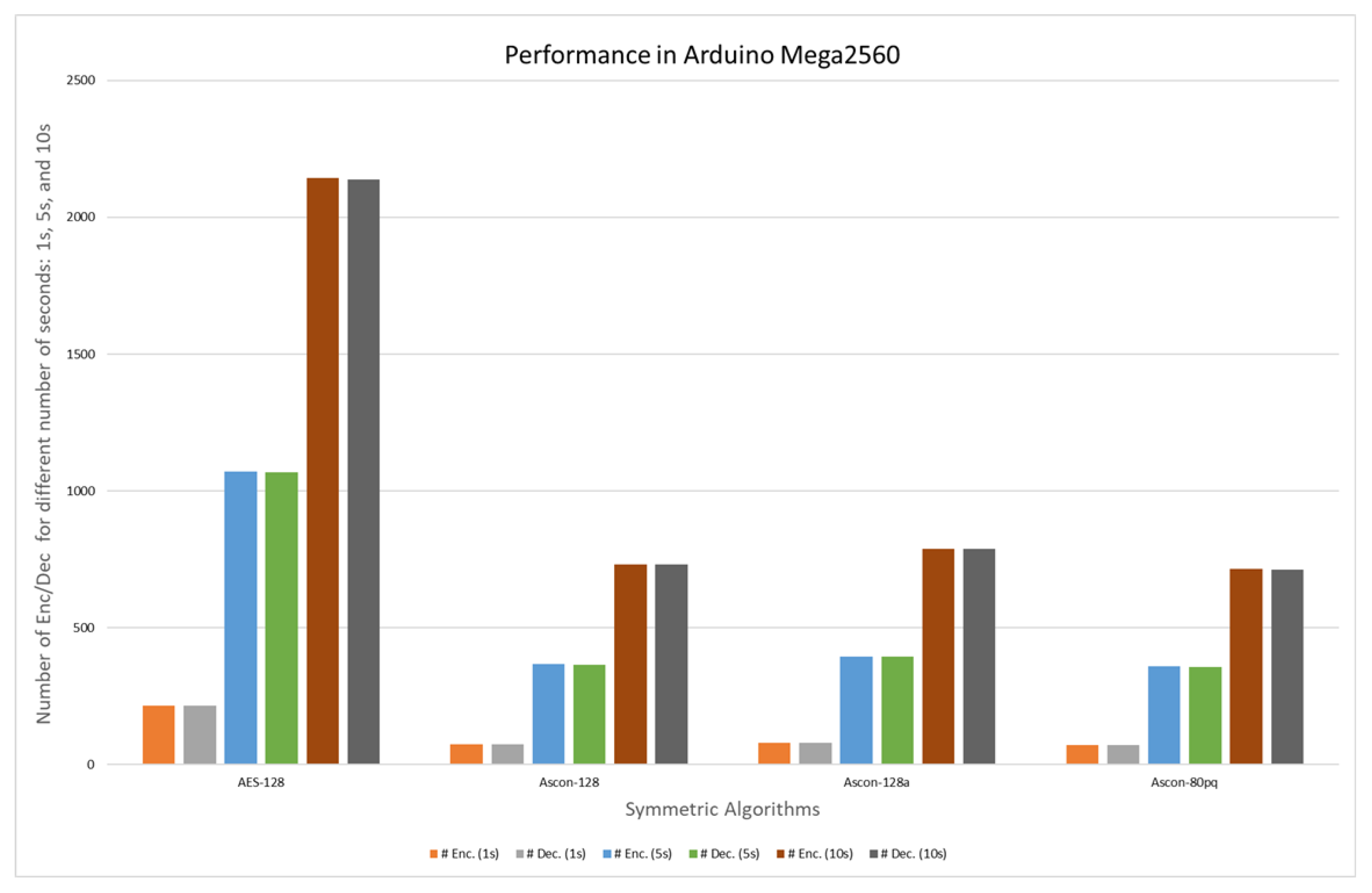
| Variant | Number of Cycles and Encryptions in the Encryption Process. Arduino Mega2560 | |||||
|---|---|---|---|---|---|---|
| # Cyc. (1 s) | # Enc. (1 s) | # Cyc. (5 s) | # Enc. (5 s) | # Cyc. (10 s) | # Enc. (10 s) | |
| Ascon-128 | 16,185,472 | 74 | 80,021,696 | 366 | 160,035,008 | 732 |
| Average | 221,718 | — | 219,237 | — | 219,226 | — |
| Ascon-128a | 16,033,152 | 79 | 80,134,848 | 395 | 160,057,088 | 789 |
| Average | 202,951 | — | 203,387 | — | 203,376 | — |
| Ascon-80pq | 16,128,000 | 72 | 80,161,024 | 358 | 160,088,832 | 715 |
| Average | 224,000 | — | 223,913 | — | 223,900 | — |
| Variant | Number of Cycles and Decryptions in the Decryption Process. Arduino Mega2560 | |||||
|---|---|---|---|---|---|---|
| # Cyc. (1 s) | # Dec. (1 s) | # Cyc. (5 s) | # Dec. (5 s) | # Cyc. (10 s) | # Dec. (10 s) | |
| Ascon-128 | 16,010,816 | 73 | 80,053,568 | 365 | 160,108,736 | 730 |
| Average | 219,326 | — | 219,324 | — | 219,327 | — |
| Ascon-128a | 16,075,200 | 79 | 80,173,568 | 394 | 160,145,664 | 787 |
| Average | 203,483 | — | 203,486 | — | 203,488 | — |
| Ascon-80pq | 16,195,008 | 72 | 80,027,072 | 356 | 160,043,072 | 712 |
| Average | 224,930 | — | 224,795 | — | 224,779 | — |
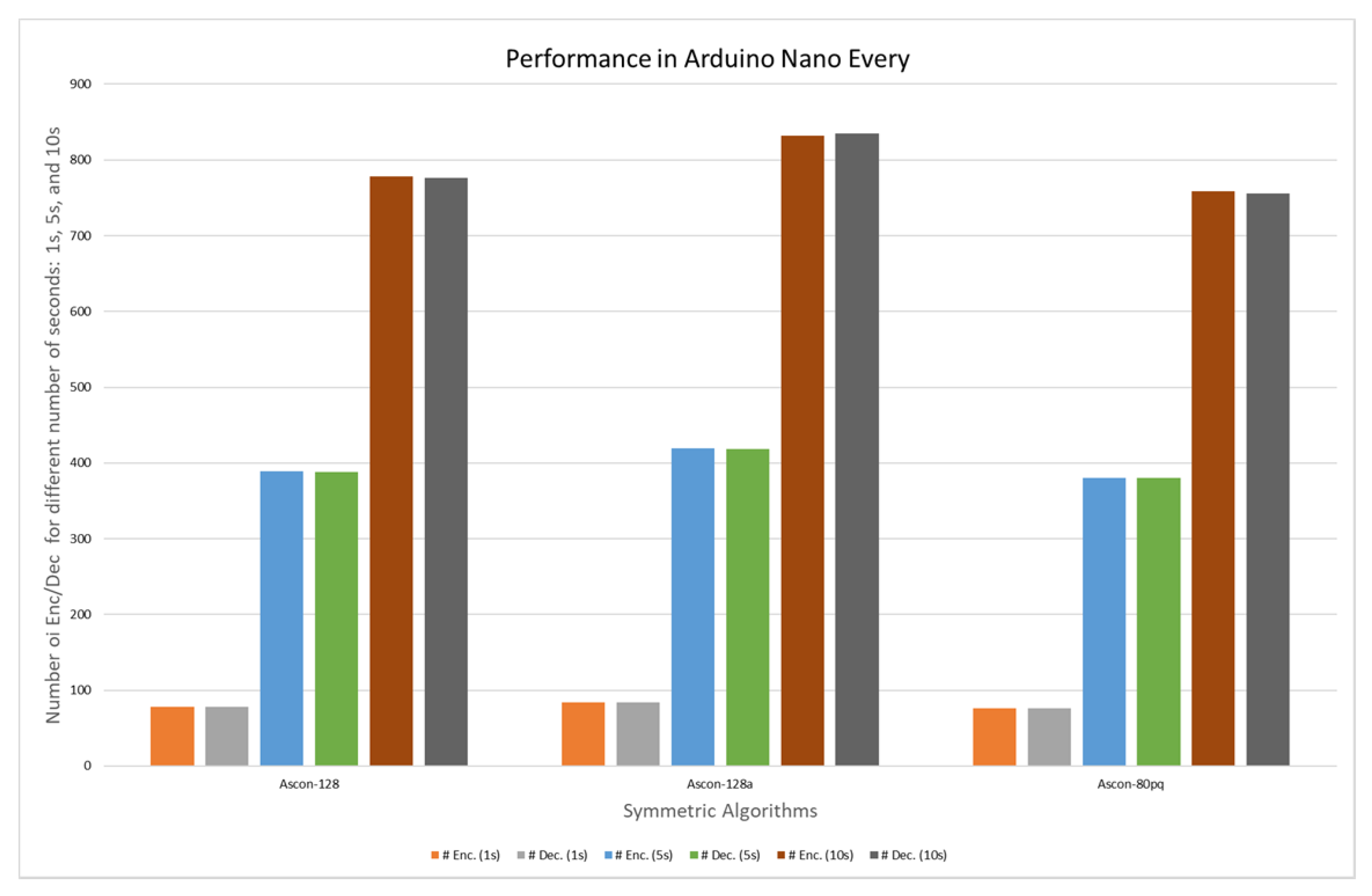
| Variant | Number of Cycles and Encryptions in the Encryption Process. Arduino Nano Every | |||||
|---|---|---|---|---|---|---|
| # Cyc. (1 s) | # Enc. (1 s) | # Cyc. (5 s) | # Enc. (5 s) | # Cyc. (10 s) | # Enc. (10 s) | |
| Ascon-128 | 16,053,696 | 78 | 80,037,120 | 389 | 160,065,600 | 778 |
| Average | 205,816 | — | 206,281 | — | 206,270 | — |
| Ascon-128a | 16,054,656 | 84 | 80,055,168 | 419 | 160,102,592 | 832 |
| Average | 191,126 | — | 191,519 | — | 191,739 | — |
| Ascon-80pq | 16,029,760 | 76 | 80,122,624 | 380 | 160,025,984 | 759 |
| Average | 210,917 | — | 210,849 | — | 210,837 | — |
| Variant | Number of Cycles and Decryptions in the Decryption Process. Arduino Nano Every | |||||
|---|---|---|---|---|---|---|
| # Cyc. (1 s) | # Dec. (1 s) | # Cyc. (5 s) | # Dec. (5 s) | # Cyc. (10 s) | # Dec. (10 s) | |
| Ascon-128 | 16,097,920 | 78 | 80,077,056 | 388 | 160,156,672 | 776 |
| Average | 206,383 | — | 206,384 | — | 206,387 | — |
| Ascon-128a | 16,098,240 | 84 | 80,110,912 | 418 | 160,030,656 | 835 |
| Average | 191,645 | — | 191,652 | — | 191,653 | — |
| Ascon-80pq | 16,097,664 | 76 | 80,022,400 | 378 | 160,034,944 | 756 |
| Average | 211,811 | — | 211,699 | — | 211,686 | — |
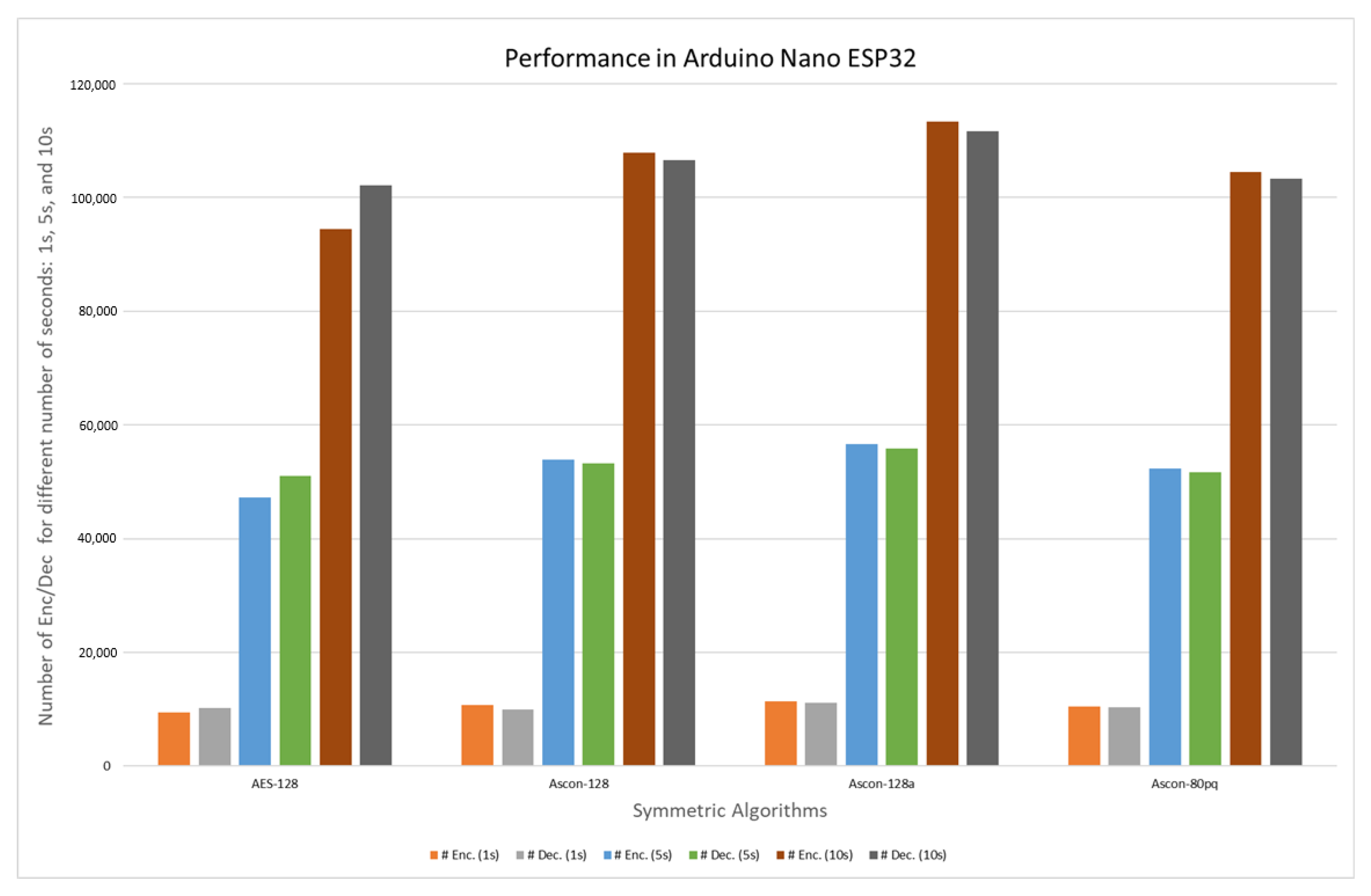
| Variant | Number of Cycles and Encryptions in the Encryption Process. Arduino Nano ESP32 | |||||
|---|---|---|---|---|---|---|
| # Cyc. (1 s) | # Enc. (1 s) | # Cyc. (5 s) | # Enc. (5 s) | # Cyc. (10 s) | # Enc. (10 s) | |
| Ascon-128 | 240,016,080 | 10,785 | 1,200,012,240 | 53,925 | 2,400,014,160 | 107,857 |
| Average | 22,524 | — | 22,523 | — | 22,523 | — |
| Ascon-128a | 240,003,120 | 11,328 | 1,200,005,760 | 56,643 | 2,400,004,800 | 113,287 |
| Average | 21,486 | — | 21,487 | — | 21,487 | — |
| Ascon-80pq | 240,021,360 | 10,453 | 1,200,013,680 | 52,264 | 2,400,010,800 | 104,528 |
| Average | 22,961 | — | 22,960 | — | 22,960 | — |
| Variant | Number of Cycles and Decryptions in the Decryption Process. Arduino Nano ESP32 | |||||
|---|---|---|---|---|---|---|
| # Cyc. (1 s) | # Dec. (1 s) | # Cyc. (5 s) | # Dec. (5 s) | # Cyc. (10 s) | # Dec. (10 s) | |
| Ascon-128 | 240,018,720 | 10,656 | 1,200,006,960 | 53,279 | 2,400,009,600 | 106,558 |
| Average | 2,252,410,656 | — | 22,523 | — | 22,523 | — |
| Ascon-128a | 240,021,120 | 11,170 | 1,200,019,920 | 55,846 | 2,400,018,720 | 111,691 |
| Average | 21,488 | — | 21,488 | — | 21,488 | — |
| Ascon-80pq | 240,003,840 | 10,328 | 1,200,008,880 | 51,644 | 2,400,016,080 | 103,289 |
| Average | 23,238 | — | 23,236 | — | 23,235 | — |
| Name | Nano ESP32 | DUE | Nano Every | Mega250 | ||||
|---|---|---|---|---|---|---|---|---|
| Enc. | Dec. | Enc. | Dec. | Enc. | Dec. | Enc. | Dec. | |
| Average | 10,855.3 | 10,718 | 2566.6 | 2573.6 | 79.3 | 79.3 | 75 | 74.6 |
| Variant | Number of Cycles and Encryptions in the Encryption Process. Linux PC | |||||
|---|---|---|---|---|---|---|
| # Cyc. (1 s) | # Enc. (1 s) | # Cyc. (5 s) | # Enc. (5 s) | # Cyc. (10 s) | # Enc. (10 s) | |
| Ascon-128 | 3,591,863,479 | 291,229 | 17,958,761,656 | 1,472,122 | 35,918,379,472 | 2,957,498 |
| Average | 12,333 | — | 12,199 | — | 12,144 | — |
| Ascon-128a | 3,591,926,172 | 314,703 | 17,958,959,274 | 1,566,612 | 35,917,241,994 | 3,144,722 |
| Average | 11,413 | — | 11,463 | — | 11,421 | — |
| Ascon-80pq | 3,591,780,396 | 287,878 | 17,959,007,943 | 1,441,062 | 35,924,275,362 | 2,637,573 |
| Average | 12,476 | — | 12,462 | — | 13,620 | — |
| Variant | Number of Cycles and Decryptions in the Decryption Process. Linux PC | |||||
|---|---|---|---|---|---|---|
| # Cyc. (1 s) | # Dec. (1 s) | # Cyc. (5 s) | # Dec. (5 s) | # Cyc. (10 s) | # Dec. (10 s) | |
| Ascon-128 | 3,591,701,259 | 291,683 | 17,959,028,616 | 1,452,898 | 35,918,447,850 | 2,921,770 |
| Average | 12,332 | — | 12,199 | — | 12,144 | — |
| Ascon-128a | 3,597,313,614 | 312,045 | 17,958,729,660 | 1,552,602 | 35,917,223,979 | 3,103,935 |
| Average | 11,430 | — | 11,463 | — | 11,421 | — |
| Ascon-80pq | 3,591,724,317 | 285,235 | 17,958,627,285 | 1,432,774 | 35,918,518,506 | 2,625,828 |
| Average | 12,476 | — | 12,462 | — | 13,618 | — |
| AES-128 | Number of Cycles and Encryptions in the Encryption Process. Arduino Devices | |||||
|---|---|---|---|---|---|---|
| # Cyc. (1 s) | # Enc. (1 s) | # Cyc. (5 s) | # Enc. (5 s) | # Cyc. (10 s) | # Enc. (10 s) | |
| DUE | 84,028,476 | 1701 | 420,004,872 | 8503 | 840,000,420 | 17,006 |
| Average | 51,393 | – | 51,401 | – | 51,404 | – |
| Mega2560 | 16,064,384 | 215 | 80,065,216 | 1072 | 160,047,360 | 2143 |
| Average | 75,067 | – | 74,897 | – | 74,858 | – |
| Nano ESP 32 | 240,010,320 | 9442 | 1,200,001,440 | 47,211 | 2,400,015,360 | 94,423 |
| Average | 23,507 | – | 23,507 | – | 23,507 | – |
| AES-128 | Number of Cycles and Decryptions in the Decryption Process. Arduino Devices | |||||
|---|---|---|---|---|---|---|
| # Cyc. (1 s) | # Dec. (1 s) | # Cyc. (5 s) | # Dec. (5 s) | # Cyc. (10 s) | # Dec. (10 s) | |
| DUE | 84,049,140 | 1635 | 420,041,244 | 8171 | 840,027,552 | 16,341 |
| Average | 51,406 | – | 51,406 | – | 51,406 | – |
| Mega2560 | 16,016,320 | 214 | 80,008,000 | 1069 | 160,014,912 | 2138 |
| Average | 74,842 | – | 74,843 | – | 74,843 | – |
| Nano ESP 32 | 240,015,840 | 10,210 | 1,200,011,280 | 51,047 | 2,400,021,360 | 102,094 |
| Average | 23,507 | – | 23,507 | – | 23,507 | – |
| Algorithm | DUE | Mega2560 | Nano Every | Nano ESP32 | ||||
|---|---|---|---|---|---|---|---|---|
| Stor. | Dyn. | Stor. | Dyn. | Stor. | Dyn. | Stor. | Dyn. | |
| Ascon-128 | 14,708 | — | 11,830 | 343 | 13,476 | 343 | 290,553 | 30,736 |
| Ascon-128a | 15,300 | — | 12,990 | 752 | 14,641 | 343 | 291,289 | 30,736 |
| Ascon-80pq | 14,980 | — | 12,854 | 694 | 14,508 | 351 | 297,329 | 31,112 |
| AES-128 | 21,200 | — | 11,478 | 4922 | 12,826 | 265 | 293,841 | 30,656 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sarasa Laborda, V.; Hernández-Álvarez, L.; Hernández Encinas, L.; Sánchez García , J.I.; Queiruga-Dios, A. Study About the Performance of Ascon in Arduino Devices. Appl. Sci. 2025, 15, 4071. https://doi.org/10.3390/app15074071
Sarasa Laborda V, Hernández-Álvarez L, Hernández Encinas L, Sánchez García JI, Queiruga-Dios A. Study About the Performance of Ascon in Arduino Devices. Applied Sciences. 2025; 15(7):4071. https://doi.org/10.3390/app15074071
Chicago/Turabian StyleSarasa Laborda, Ventura, Luis Hernández-Álvarez, Luis Hernández Encinas, José Ignacio Sánchez García , and Araceli Queiruga-Dios. 2025. "Study About the Performance of Ascon in Arduino Devices" Applied Sciences 15, no. 7: 4071. https://doi.org/10.3390/app15074071
APA StyleSarasa Laborda, V., Hernández-Álvarez, L., Hernández Encinas, L., Sánchez García , J. I., & Queiruga-Dios, A. (2025). Study About the Performance of Ascon in Arduino Devices. Applied Sciences, 15(7), 4071. https://doi.org/10.3390/app15074071







