Abstract
The rapid expansion of device connectivity and the increasing demand for data traffic have become pivotal aspects of our daily lives, especially within the Internet of Things (IoT) ecosystem. Consequently, operators are striving to identify the most innovative and robust solutions capable of accommodating these escalating requirements. The emergence of the sliced fifth-generation mobile network (sliced 5G) offers a promising architecture that leverages a novel Radio Access Technology known as New Radio (NR), promising significantly enhanced data rate experiences. By integrating the network slicing (NS) architecture, greater flexibility and isolation are introduced into the preexisting infrastructure. The isolation effect of NS is particularly advantageous in mitigating interference between slices, as it empowers each slice to function independently. This paper addresses the user association challenge within a sliced 5G (NR)-IoT network. To this end, we present an Unconstrained-Markov Decision Process (U-MDP) model formulation of the problem. Subsequently, we propose the U-MDP association algorithm, which aims to determine the optimal user-to-slice associations. Unlike existing approaches that typically rely on static user association or separate optimization strategies, our U-MDP algorithm dynamically optimizes user-to-slice associations within a sliced 5G-IoT architecture, thereby enhancing adaptability to varying network conditions and improving overall system performance. Our numerical simulations validate the theoretical model and demonstrate the effectiveness of our proposed solution in enhancing overall system performance, all while upholding the quality of service requirements for all devices.
1. Introduction
Nowadays, the significant expansion of smart object connectivity and application demand is still increasing exponentially. Connecting multiple devices with higher data rate, low latency, and increased bandwidth requirements has become a major challenge for operators and the industry [1]. Accordingly, existing 3G and 4G mobile network technologies will not be sufficient to meet these increasing demands [2]. Therefore, mobile operators are encouraged to develop efficient solutions to overcome these challenges. The 5G New Radio (NR) is considered a promising mobile technology solution that will meet the above-mentioned requirements. This is particularly important for IoT infrastructure [3].
The 5G NR is described according to the 3GPP standard in the 15th and 16th releases [4]. And, it promises to attempt faster internet speeds with better battery life and cost, enhancing spectrum efficiency as well as improving network capacity by connecting billions of devices. Furthermore, communicating between multiple devices in 5G-IoT can result in many other challenges, such as the interference problem, which is caused by massive transmissions among users and base stations (BSs) [5,6]. For this reason, current 5G networks are trying to progress towards improved virtualization. Therefore, network slicing (NS) can be an effective approach to address this problem [7,8].
NS is based on creating several isolated logical networks (called slices) from the same physical infrastructure that various network operators share. Therefore, deploying an innovative architecture such as NS can significantly decrease the CAPEX and OPEX of these operators due to the softwarization and virtualization of used technologies. Furthermore, in addition to considering both Radio Access Network (RAN) [9] and core network [10] characteristics, NS offers greater scalability, isolation, and flexibility for network slices. The latter can be personalized and optimized to efficiently respond to the different quality of service (QoS) requirements as well as overcome the challenging end-to-end slicing in several potential domains such as smart environments and e-health care services [11]. This work aims to resolve the multi-device association problem in a 5G (NR)-IoT infrastructure (as described in Figure 1). NS architecture is proposed to eliminate interference, improving the global network performance while connecting a maximum number of devices, with respect to their QoS needs regarding data rate and service cost.
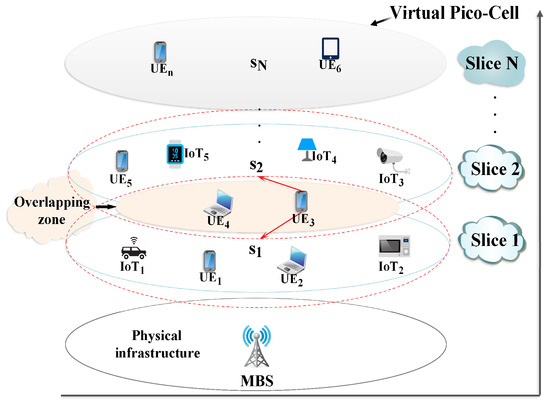
Figure 1.
The proposed 5G-IoT network slicing architecture.
The remainder of this paper is organized as follows: Section 2 proposes a detailed overview of the most interesting related works. After describing the network model as well as explaining the association problem formulation in Section 3, the proposed algorithm and the suggested solution will be discussed in Section 4. Then, to validate the proposed model and analyze its performance, the numerical simulation results are shown in Section 5. Finally, concluding remarks are given in Section 6.
2. Related Works
In the past decade, the proliferation of smart objects communicating with their surroundings and exchanging data has become a defining feature of our daily lives [12]. These devices, which we interact with frequently, offer an expanding range of services that streamline our activities. Connected objects encompass a wide variety, ranging from increasingly intelligent household items to the overarching concept of a smart city [13].
According to a recent report by IoT Analytics [14], the number of connected objects worldwide is expected to reach around 27.1 billion by the end of 2025. This impressive growth confirms the rapid expansion of the IoT landscape. Projections also suggest that this number could exceed 40 billion by 2030 [15]. As the number of devices keeps increasing and the demand for smart services intensifies, several challenges arise. These include improving network capacity, ensuring service quality, and managing resources efficiently while maintaining energy constraints for connected objects.
To address these challenges, 5G-IoT introduces pioneering architectures and novel functionalities that promise significantly higher data rates [16]. Consequently, it emerges as a prime solution compared to its predecessors in mobile network technologies. Extensive literature is dedicated to identifying the most effective models for deploying 5G-IoT networks. Rahimi et al. [17] proposed a novel 5G-IoT network model incorporating innovative technologies such as Machine-Type Communication (MTC) [18], Device-to-Device (D2D) communication, Wireless Software Defined Networks (WSDN), and Wireless Network Function Virtualization (WNFV). These technologies render their models more efficient compared to existing architectures like conventional Software-Defined Networking (SDN) [19], QoS, and three-level architectures. Other research leverages the benefits of 5G technology for IoT architecture authentication. Torroglosa-Garcia et al. [20] introduced a handover roaming structure for the Low-Range Wide Area Network (LoRaWAN) protocol, leveraging the dependable 5G network for IoT devices’ key management and authentication, ensuring interoperability between 5G and LoRaWAN. This solution has proven its viability and utility in enhancing security.
In a different context, 5G deployment addresses QoS for a multitude of communicating IoT devices [21]. Accordingly, Asad et al. proposed in [22] a client-centric access device selection method in multiple scenarios of Radio Access Technologies (RATs) to provide the capacity to define node-specific QoS needs for each device, a very good access node selection, as well as enhanced network scalability. Thereafter, they suggested a new algorithm with cubic complexity in the absence of multihoming [23] capability and linear-complexity when only two access nodes are considered. As a result, the proposed method outperforms conventional access node selection techniques such as Best SNR (B-SNR) and Maximum Bandwidth (M-BW).
In the near future, 5G will offer IoT networks the opportunity to have a widely strong and stable infrastructure with new smart services and applications. Gupta et al. [24] studied the 5G-IoT architecture, giving some fundamental information about it. Then, they proposed a new layered 5G-IoT infrastructure based on some crucial technologies such as Network Function Virtualization (NFV), SDN, as well as cloud computing. The architecture’s performance is substantiated through analysis, highlighting 5G’s suitability to power IoT systems.
Notwithstanding the importance of the above-cited research addressing IoT network new technologies and challenges, the 5G-IoT infrastructure still grapples with the interference effects of massive device transmissions [25]. NS emerges as a pivotal technology for 5G-IoT infrastructure development to meet varied service requirements [26]. The 5G slicing model classifies into three primary use cases: 5G Mobile Broadband (MBB), 5G Massive IoT (MIoT), and 5G Ultra-Low Latency High Reliability [27]. This study combines the first two use cases and aims to respond to the resultant environmental requirements.
In [28], Lin et al. have proven NS’s efficiency to meet the 5G-IoT application’s needs. Thus, they considered MIoT, MBB, and Critical IoT (CIoT) applications in their performance study, where they emulated transport NS traffic using SimTalk, an emulator for IoT application traffic. The proposed method’s effectiveness is analyzed in terms of throughput, latency, and packet loss. Result analysis shows that the proposed slicing transport network mechanism gave important results. Escolar et al. [29] presented an NS framework for 5G-IoT networks based on an SDN approach in order to dynamically manage a wide number of heterogeneous IoT network slices on demand. To validate the theoretical proposed solution, an empirical test was performed for five realistic vertical-oriented IoT use cases. According to the results, the suggested framework gave convincing returns in terms of flexibility, stability, isolation, as well as meeting extreme QoS needs even in the most delicate scenarios.
In terms of resource allocation [30,31] presents a key problem to resolve in 5G-IoT networks, especially for network slicing architecture [32]. The latter needs to independently share different resources with several slices offering various services in order to meet the device’s QoS requirements. Fossati et al. [33] studied the multiple fair resource allocation problem among slices, notably in the difficult scenario where the network does not have sufficient resources to respond to all slice demands. Thus, they formulated the aforementioned problem as a multi-resource allocation model. Then, they proposed a polyvalent optimization framework using the Ordered Weighted Average (OWA) method to resolve the problem while considering different fairness approaches. As a result, the proposed solution allowed the implementation of new multi-resource allocation schemes in addition to the other existing ones. Another innovative solution is suggested by Wang et al. [34], who they studied NS dimensioning with the resource pricing strategy. Then, they developed an NS dimensioning optimization model, wherein the Slice Customer’s Problem (SCP) increases the Slice Customer’s (SC) gain, and the Slice Provider’s Problem (SPP) boosts net social well-being (resource efficiency). Thereafter, they found that increasing the net social well-being and enhancing the SP’s gain are two coherent goals when there is a lack of resource; otherwise, there is a trade-off. Accordingly, they proposed a low-complexity distributed algorithm to reach near-optimal net social well-being with a guarantee of SP/SC gains. The numerical simulation results validate the proposal’s efficiency. To resolve the user equipment (UE) association problem in sliced 5G UD-HetNets, Amine et al. [35] suggested a novel NS structure using the matching game. They proposed the UE-Slice Association Algorithm (U-S.AA) to compute the stable matching between UE and different network slices. Then, they validated the proposed model by numerical simulations. Numerical results prove the effectiveness of the proposal to improve the global system performance with respect to the UE’s QoS while enhancing its energy efficiency (EE).
Markov decision process (MDP) is a useful mathematical tool to study optimization problems [36,37] that can be resolved using dynamic programming [38]. Hence, it can be adopted for modeling an innovative 5G-IoT framework, especially for resource allocation problems where there are various and conflicting metrics that need to be optimally balanced in order to obtain a trade-off situation. To improve the system’s QoS, Tang et al. [39] proposed a slice-based virtual resource scheduling architecture using NOMA technology. They formulated the power granularity allocation and subcarrier allocation problems as a constrained MDP model to maximize the total user data rate. Then, to resolve the above-mentioned problems, they developed an adaptive resource allocation algorithm using approximate dynamic programming. According to simulation results, the suggested model can effectively enhance the user data rate while reducing the outage probability. In order to ensure network QoS with low service cost, Xi et al. [40] discussed the resource allocation problem in a sliced 5G infrastructure, taking into account the real-time resource demand of the network slice user. Therefore, they recommended a semi-Markov decision system model that allows the virtual network provider to respond well to the various user needs in real-time. Using deep reinforcement learning (DRL), they proposed a resource slicing algorithm to enhance the long-term advantages of slicing resource utilization and virtual network providers. Performance evaluation proves the efficiency of the proposed algorithm to improve network performance while reaching long-term advantages.
In recent years, DRL has gained traction for solving various network optimization problems. For instance, Li et al. [41] proposed a DRL-based framework for dynamic resource allocation in network slicing environments. Their approach focuses primarily on inter-slice resource distribution, without addressing the user-to-slice association problem under QoS constraints. You et al. [42] introduced a user-oriented robust reinforcement learning method to ensure reliable decision-making under uncertain environments. While promising, their model emphasizes robustness at the decision level rather than supporting slice-aware association schemes. In a different context, Li et al. [43] leveraged DRL for network topology optimization by adapting the physical layer configuration, which differs from our focus on logical association of IoT users to virtual slices. More recently, Wang et al. [44] proposed an energy-aware slice design policy using a deep actor–critic reinforcement learning model. Although their approach improves energy efficiency during slice deployment, it does not consider user-to-slice association or fine-grained QoS-driven decisions for individual users. Compared to these works, our contribution specifically targets fine-grained user–slice association in a sliced 5G-IoT network, leveraging a U-MDP formulation to explicitly consider user QoS requirements and slice capacity constraints.
In parallel with the rapid development of a new generation of networks and the growing demand for resources, especially in the massive presence of smart connected objects, NS implementation represents the best way to efficiently manage resources. However, it allows increasing network performance while reducing service cost consumption. To the best of our knowledge, most of the research works in the literature have studied resource allocation problems considering multiple network slices. Each slice offers a unique service different from the others. In this paper, massive slices are considered. Each one can offer multiple services simultaneously. Hence, each device can choose a suitable network slice depending on its capacity, depending on the service requested. Consequently, the key suggestions and contributions of this work can be outlined as follows:
- To resolve the device association problem in a massive 5G (NR)-IoT infrastructure, a green attractive solution is proposed based on NS architecture;
- The aforementioned problem is formulated as a U-MDP model. And the U-MDP association algorithm is suggested to find the optimal association between devices and the different slices;
- The main objective of this work is to eliminate the interference effect caused by massively connected object transmissions to improve the global system performance as well as all devices’ QoS requirements.
To facilitate the understanding of existing work and to clearly position our contribution, we present a comparative summary of prior approaches in Table 1.

Table 1.
Summary of related works.
3. System Model
3.1. Network Model
For the proposed model, we consider a sliced 5G-IoT system using NR access technology. The overall network is connected and managed by a Macro Base Station (MBS), such as , which serves all network slices, user equipment, and IoT devices. Network slices are defined by , i.e., the set of Virtual Pico Base Stations (VP-BSs), where each VP-BS is represented by one slice. The sets of all UE and IoT devices are combined into one set, which is defined by . Figure 2 describes a simplified network slicing scenario.
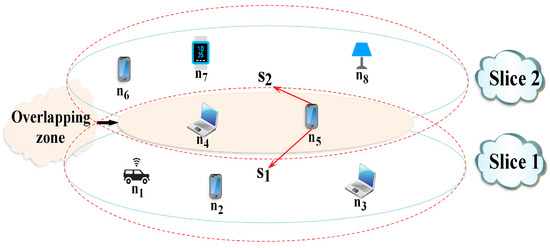
Figure 2.
Sliced 5G-IoT network scenario.
3.1.1. State Space
To model our system, a state space S is defined, wherein a controlled continuous-time stochastic process is considered. Each state is represented as a one tuple , where i is the number of devices connected to VPs. The user devices’ arrivals and departures in the system constitute the events. Hence, two types of possible events are defined, as follows:
It is assumed that at any time an event occurs, the MBS reacts and makes a decision (action) according to the event type. Thus, based on both the event type and the action taken by the MBS, a state transition may happen. Furthermore, for each transition, we can only have one event per slice.
3.1.2. Action Space
The main objective of this work is to optimally associate the maximum number of UE and IoT nodes to the different network slices. The set of all possible associations is defined according to the predefined events and system states by , as follows:
Hereafter, a state set is defined, where the action is chosen based on the event with and , such as
- In the case of the event, the possible actions that can be chosen are defined bywhere B is the maximum user number that can be connected to the VP.
- And for the event, we have
It is observed that for , when a user arrives in the system, the set of all possible actions that can be chosen by the MBS is . However, the action becomes impossible if the system state does not exist in , when the event happens. In addition, represents the possible action that can be chosen in all of the states. But, it will be the only one to be chosen if a user leaves the system.
3.1.3. State Transitions
For the proposed model, a system state is considered at time t. Thereafter, at , the system moves to a different state , while taking into account the predefined event and action chosen by the MBS. Note that each transition is denoted by . Accordingly, the new possible state values are defined in Table 2, and the state transition diagram from state is described in Figure 3.

Table 2.
Transition probability table.

Figure 3.
State transition diagram.
3.1.4. Transition Probabilities
According to the system state at time t, the transition probability matrix is defined from the state to a different state under the action by . And we have
Note that since for both and actions, we have an identical transition state as described in Table 2.
3.1.5. Reward Functions
In this work, the reward function represents the total network slices’ capacity in terms of data rate. Thus, it is represented by based on the state s, the event , and the action . As depicted in Table 3, each user n has its own data rate requirement value , which can vary from (minimum data rate requirement value) to (user data rate threshold value), depending on the network slices capacity.

Table 3.
Data rate reward functions.
3.2. User Association Problem Formulation
The aim of this paper is to optimally associate the maximum number of user devices with different VPs. Hence, the problem is formulated as a continuous-time Unconstrained MDP model (U-MDP), considering a pure optimal policy. The possible actions that will be taken at the state and the decision time , for all future states , are defined by the policies set . The average reward function is defined based on the policy by . Given that the key objective is to maximize the total system data rate, the optimization problem can be formulated as follows:
with is the expectation operator considering the policy .
3.2.1. U-MDP Solution
To simplify the problem resolution, the continuous-time U-MDP must first be converted to an equivalent discrete-time U-MDP using uniformization. Then, the optimal policy can be calculated using the Value Iteration Method (VIM). Note that for the converted model, there will be no change for the action space, the state space, and the policies. Afterward, we define such that , where is the predicted time until the next event. And we have
The optimization problem is formulated as the following programming equation:
Remark 1.
Although our model considers three possible actions for each user, we are aware that the total action space grows with the number of connected devices. However, thanks to the structure of the U-MDP formulation, decisions are made independently for each user. This separation allows us to maintain a manageable level of complexity, even in moderately dense environments. Additionally, we intentionally use a simplified state transition model that does not explicitly include factors such as interference or channel noise. These aspects are abstracted within the reward function, ensuring that the model remains mathematically tractable while still capturing key performance trade-offs relevant to the user–slice association problem.
3.2.2. The Considered Metrics
In this work, we aim to resolve the user association problem in a sliced 5G-IoT network. To this end, we propose a green solution based on the U-MDP model to enhance the EE, user’s QoS, and the overall network performance while optimally managing interference among user devices and the different network slices. Therefore, to formulate the aforementioned problem, we will describe at the outset all system requirements.
- Energy efficiency (EE)
To evaluate the system efficiency, it is necessary to consider this metric which is defined by
where represents the maximum network data rate introduced as a Shannon capacity, is the signal transmit power, defines the transmitted signal bandwidth, and is the noise power spectral density.
- Spectrum efficiency (SE)
This criterion provides information on the bandwidth usage efficiency and it is expressed by the ratio between the maximum network data rate and the signal bandwidth that is already defined:
- Deployment efficiency (DE)
DE is defined as the ratio between the number of maximum transmitted bits and the network deployment cost , such that
DE is a very important criterion when the network infrastructure is very expensive (e.g., ultra-dense cellular networks).
The main objective is to find a trade-off between increasing system performance related to the desired QoS and optimizing energy consumption in the context of green or eco-radio communications.
4. The Proposed U-MDP Association Algorithm
4.1. Algorithmic Framework Overview
The main objective of this work is to find an optimal and efficient solution for the user-to-slice association in 5G-IoT HetNets. Accordingly, Algorithm 1 is proposed to resolve the aforementioned problem. The latter is based on the U-MDP model and undergoes two fundamental procedures. After the initialization of input parameters (line 1), the first one is the optimal policy researching depending on Equation (4)’s resolution. Then, the U value is updated until a very small positive difference between and is obtained, such that , where is a small positive real number. At that time, we can say that and are the optimal solution and policy, respectively (lines 2–15). The theorem below clearly describes the relation between the optimal policy and the optimality equation solution.
| Algorithm 1 The Proposed U-MDP Association Algorithm |
|
Theorem 1.
If is defined as a solution to the optimality equation, there exists an optimal Markov stationary policy , such as
Remark 2.
Theorem 1 is based on classical MDP results. If the value function satisfies the Bellman optimality equation, then at least one optimal stationary policy exists [36]. This policy is not necessarily unique, since different policies can lead to the same optimal value function. However, this does not impact the convergence of the value iteration algorithm, which always converges to a unique value function . As a result, any policy derived from it remains optimal, which guarantees the correctness and convergence of the proposed U-MDP algorithm.
The second procedure concerns the optimal policy identification (lines 16–38). Hence, for each user ’s arrival in the system, if n is situated in the overlapping area among two network slices and , , for example, it will automatically be served by the one that satisfies its needs in terms of data rate depending on the threshold value , while respecting the network slice capacity B (lines 17–22). In the case of the saturation of all slices, a minimum data rate value is assigned to all users connected to these slices in order to find a slice that can meet the user’s need. Otherwise, it will be connected to the (lines 23–30). Since only one event can occur per transition, the action will be chosen for each user departing from the system (lines 35–36). The slice choice represents the action chosen by the . This process is repeated until convergence to the optimal user-to-slice association or there is no user to associate.
To further clarify the state/action space and illustrate how user transitions are handled within the U-MDP framework, we consider the network scenario depicted in Figure 2, where device is located in the overlapping zone between Slice 1 and Slice 2. Upon arrival, device will be associated with the slice that best satisfies its QoS needs, primarily based on the achievable data rate while considering the threshold value and the available capacity of each slice. If both slices are saturated, the system will trigger the assignment of a minimum data rate to all users connected to these slices, allowing the network to balance capacity and maintain service continuity. This dynamic reassignment mechanism ensures that devices like can seamlessly transition between slices as network conditions and QoS requirements evolve.
4.2. Model Complexity Analysis
The computational complexity of the proposed U-MDP-based user-to-slice association model is primarily driven by the number of states and actions considered in each user’s local decision process. However, unlike centralized formulations that handle the global state space, our approach decomposes the problem into user-specific decision processes, leveraging the Unconstrained MDP structure. This user-level decomposition contributes to reducing the overall computational burden, as the policy derivation is handled individually per user. Consequently, the algorithm exhibits linear scalability with respect to the number of users and available slices. This property makes the proposed scheme well suited for real-time deployment in dense 5G-IoT environments, without introducing significant computational overhead.
Moreover, the U-MDP formulation enables pre-computation of optimal policies for representative network scenarios. These pre-trained policies can then be applied during runtime with minimal adaptation, further reducing the need for intensive online computations. Such a design ensures a good balance between decision quality and computational efficiency, which is crucial in large-scale, resource-constrained IoT deployments.
5. Numerical Results
To provide evidence of the efficiency of the proposed U-MDP algorithm in solving the user-to-slice association problem in 5G-IoT HetNets, simulations were conducted using the Matlab environment, adhering to the 5G LTE/NR 3GPP standard and NS deployment specifications. The simulation scenario is presented in Figure 4. We chose the simulation parameters listed in Table 4 to embrace realistic values usually met in 5G-IoT scenarios, whilst being computationally affordable for comprehensive performance assessment. We chose the number of user devices (100) and PBSs (40) to represent a moderately dense deployment, e.g., smart city or industrial automation applications. These values serve as a compromise between the complexity of the model and clarity of the results, and have also been reported in similar simulation-based studies in the literature. The plotted values represent the averages of 1000 independent simulations. Although confidence intervals are not depicted, the Empirical Cumulative Distribution Functions (ECDFs) provide full visibility into the distribution of user-level outcomes, and each curve is based on 1000 independent simulation runs, ensuring statistically robust performance trends.
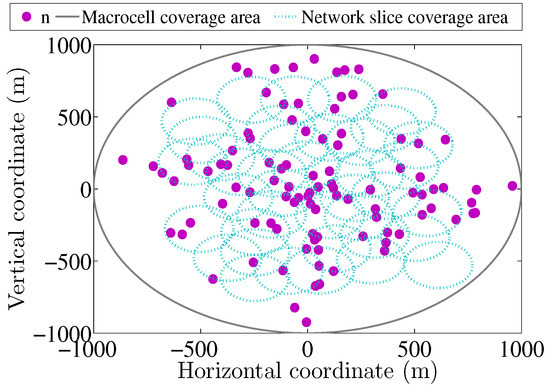
Figure 4.
Network scenario.

Table 4.
Simulation parameters.
In order to analyze the performance of the suggested U-MDP-NS (5G-NR) solution, a comparison was performed with default maximum signal-to-interference-plus-noise ratio (Max-SINR-NS (5G-NR)), maximum received signal strength indication (Max-RSSI-NS (5G-NR)), the same proposed solution but using 5G-LTE technology (U-MDP-NS (5G-LTE)), as well as the traditional association scheme between pico base stations (PBSs) and users (U-MDP (5G-LTE)), deployed without network slicing. Here, PBSs are randomly distributed within the MBS coverage area and serve multiple users.
5.1. Impact on the User’ QoS Requirements
In this subsection, the impact of the proposed U-MDP-NS (5G-NR) solution on the users’ QoS requirements is studied. Thus, it is compared to Max-SINR-NS (5G-NR), Max-RSSI-NS (5G-NR), U-MDP-NS (5G-LTE), and U-MDP (5G-LTE) association schemes.
The ECDF displayed in Figure 5a demonstrates the superior performance of the U-MDP-NS (5G-NR) proposal in comparison to other solutions. While the Max-SINR-NS (5G-NR) and Max-RSSI-NS (5G-NR) schemes prioritize directing users to the VP/PBS with the highest data rate, our proposed solution effectively meets users’ QoS data rate requirements within the VP/PBS capacity. Utilizing LTE technology, the U-MDP-NS (5G-LTE) offers a lower data rate compared to 5G-NR. Furthermore, U-MDP (5G-LTE) faces degradation due to interference, which is mitigated by NS isolation in previous solutions.
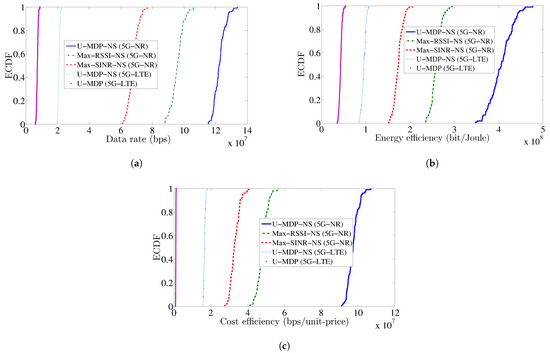
Figure 5.
ECDF of (a) user data rate, (b) user EE, and (c) user service CE.
The ECDF in Figure 5a illustrates that the proposed U-MDP-NS (5G-NR) enables the majority of users to achieve data rates surpassing bps, while Max-SINR-NS (5G-NR) and Max-RSSI-NS (5G-NR) reach approximately bps and bps, respectively. This significant difference highlights the superior capacity of our approach in meeting high-throughput requirements, ensuring balanced load distribution and efficient resource utilization.
Consequently, the predescribed criteria are applied to EE, as shown in Figure 5b. The ECDF indicates that U-MDP-NS (5G-NR) users achieve energy efficiency values up to bit/Joule, surpassing Max-SINR-NS (5G-NR), peaking around bit/Joule, and Max-RSSI-NS (5G-NR) concentrated between and bit/Joule.
Figure 5c displays the ECDF of user service cost efficiency (CE). The traditional U-MDP (5G-LTE) solution experiences severe CE degradation due to the absence of NS (and logical network isolation). The proposed U-MDP-NS (5G-NR) solution significantly enhances user service CE. It offers higher data rates due to 5G-NR technology while adhering to the cost constraint for all users. Thus, it represents an optimal solution for user service CE. The ECDF shows that U-MDP-NS (5G-NR) achieves cost efficiency values exceeding bps/unit-price, significantly outperforming Max-SINR-NS (5G-NR), which is mostly distributed between and , and Max-RSSI-NS (5G-NR), which ranges around to . LTE-based approaches remain markedly less efficient.
To enhance the comparative analysis, we decided to use ECDFs as the main tool for visualizing performance. This choice was made because ECDFs can show the full distribution of user-level metrics, such as data rate, energy efficiency, and cost efficiency, instead of just providing mean or quartile values. In diverse 5G-IoT environments, this comprehensive insight is vital for identifying outliers in performance and ensuring fairness for all users. The steepness and shifts in the ECDF curves in Figure 5a–c confirm the benefits of our proposed U-MDP-NS (5G-NR) solution, which consistently outperforms baseline methods across all percentiles.
5.2. Impact on the Global Network Performance
As for this subsection, the impact of the U-MDP-NS (5G-NR) proposal on the global system performance is elaborated with regard to the other conventional solutions.
Figure 6a illustrates the variation in the average sum data rate as the number of VPs/PBSs increases. The network throughput capacity increases with the growth of VP/PBS numbers. Leveraging 5G-NR technology empowers the U-MDP-NS (5G-NR) solution to offer high data rates compared to U-MDP-NS (5G-LTE) and U-MDP (5G-LTE) association schemes. Additionally, NS enhances its efficiency by mitigating interference compared to the U-MDP (5G-LTE) solution. In contrast, the Max-SINR-NS (5G-NR) and Max-RSSI-NS (5G-NR) models, which connect users to VP/PBS with the highest SINR and RSSI values, respectively, offer less significant results compared to the proposed solution. This can be attributed to network congestion effects, which also impact EE (as shown in Figure 6b) and SE (as depicted in Figure 6c).
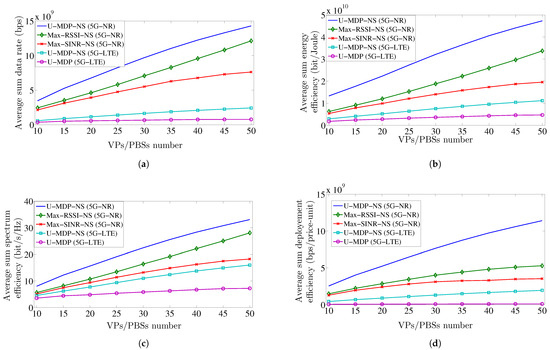
Figure 6.
Variation in average sum: (a) data rate, (b) EE, (c) SE, and (d) DE.
Figure 6d displays the variation in the average sum deployment efficiency of the system. The observed degradation in U-MDP (5G-LTE) results compared to other solutions is due to the higher deployment cost of various PBSs, especially in dense scenarios. NS enhances the proposed solution’s efficiency in terms of network deployment cost compared to the traditional solution. Additionally, adopting a robust model like U-MDP enables a trade-off between enhancing network throughput and minimizing deployment costs, resulting in better performance for the proposed solution compared to the Max-SINR-NS (5G-NR) and Max-RSSI-NS (5G-NR) association schemes. Consequently, the proposed U-MDP-NS (5G-NR) solution represents the most effective approach to enhancing overall network DE.
The superior performance of U-MDP-NS (5G-NR) stems from several architectural and algorithmic strengths. Unlike conventional schemes that statically associate users based solely on signal metrics (e.g., SINR or RSSI), the proposed solution formulates the user association problem as an Unconstrained Markov Decision Process (U-MDP). This framework enables joint optimization and dynamic load balancing across network slices, preventing both resource saturation and underutilization. It also contributes to interference mitigation by considering the state of neighboring slices when making association decisions. The policy adapts effectively to real-time variations in user QoS requirements and network conditions, ensuring fair and efficient resource allocation. While the method introduces a higher computational demand than heuristic alternatives, it remains computationally tractable in moderately dense deployment scenarios, thus providing a balanced compromise between performance gains and practical scalability.
5.3. Performance Summary
To consolidate the findings from the previous subsections, this part provides a comprehensive performance comparison of the evaluated user-to-slice association schemes. Table 5 presents a synthesized view of the main metrics, grouped into two principal categories: user QoS and global network performance.

Table 5.
Performance summary of user-to-slice association schemes.
As clearly illustrated, the proposed U-MDP-NS (5G-NR) framework consistently outperforms all baseline methods in both user-centric and system-wide evaluations. Specifically, it yields higher user data rates, significantly enhanced energy efficiency, and improved cost efficiency, resulting in better alignment with user QoS demands. The empirical cumulative distribution functions (ECDFs) in Figure 5a–c confirm these trends across the entire range of user scenarios.
On the network side, the proposed approach also demonstrates superior performance in terms of spectrum utilization, deployment cost-effectiveness, and scalability. Figure 6a–d show consistent gains in aggregate metrics. These improvements are attributed to the ability of the U-MDP formulation to dynamically adapt to varying traffic loads and slice-level constraints. By integrating 5G-NR enhancements and network slicing principles, our method achieves balanced load distribution and robust interference mitigation across heterogeneous deployments. The summarized comparison is detailed in Table 5 below.
Overall, this performance summary reinforces the effectiveness of U-MDP-NS (5G-NR) in addressing both individual user requirements and broader system-level efficiency, establishing it as a scalable and adaptive solution for future 5G-IoT deployments.
6. Conclusions and Future Work
This paper introduces an innovative green solution to address the device association challenge in sliced 5G (NR)-IoT networks and to handle high data traffic demands. By leveraging the U-MDP model, we propose the U-MDP association algorithm to optimize associations between connected objects and different slices. The validity of the theoretical model is demonstrated through numerical simulations using Matlab. The proposed U-MDP-NS (5G-NR) solution effectively enhances system performance—throughput, EE, SE, and DE—while upholding devices’ QoS, outperforming Max-SINR-NS (5G-NR), Max-RSSI-NS (5G-NR), U-MDP-NS (5G-LTE), and U-MDP (5G-LTE) schemes.
In future studies, we aim to extend the evaluation of our proposed architecture to other wireless technologies such as Wi-Fi, particularly in scenarios involving large-scale deployment of connected devices with multihoming capabilities.
From a deployment perspective, the proposed U-MDP-NS (5G-NR) algorithm is well suited for integration into the control plane of 5G network slicing management systems. It can be implemented as part of a slice orchestrator or a network function at the edge, where real-time user–slice association decisions are needed. While the U-MDP formulation introduces increased computational demands compared to rule-based policies, its decision space remains manageable in moderately dense environments. Moreover, since association updates occur at a slower time scale than user data-plane events, the algorithm’s latency overhead is limited. For large-scale, national deployments, scalability can be achieved by adopting distributed U-MDP agents or hierarchical coordination schemes, which are promising directions for future work. This would allow the algorithm to maintain efficiency and responsiveness across broader heterogeneous network domains.
Our work makes some practical simplifications. For example, we assume that each system change (or transition) happens one at a time, which helps keep the model clear and easier to simulate. In real 5G networks, multiple events can co-occur and interact with each other. Moreover, while our evaluation relies on standard-compliant simulations, future studies could incorporate real-world traffic datasets to validate the model’s performance in practical deployment scenarios. In the future, we hope to explore smarter techniques, like reinforcement learning, to allow the system to react more flexibly to changes. It would also be helpful to study how network signals, delays, and communication between slices affect performance when this solution is deployed.
Author Contributions
Conceptualization, M.A. and A.K.; Data curation, M.A.; Formal analysis, M.A.; Investigation, M.A.; Methodology, M.A.; Project administration, A.K.; Resources, A.K., J.B.-O. and M.E.K.; Software, M.A.; Supervision, A.K.; Validation, M.A., A.K., J.B.-O. and M.E.K.; Writing—original draft, M.A.; Writing—review and editing, A.K., J.B.-O. and M.E.K. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
No new data were created or analyzed in this study. Data sharing is not applicable to this article.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Vitturi, S.; Zunino, C.; Sauter, T. Industrial Communication Systems and Their Future Challenges: Next-Generation Ethernet, IIoT, and 5G. Proc. IEEE 2019, 107, 944–961. [Google Scholar] [CrossRef]
- Chandramouli, D.; Liebhart, R.; Pirskanen, J. Next Generation Network Architecture. In 5G for the Connected World; John Wiley & Sons, Inc.: Hoboken, NJ, USA, 2019; pp. 127–223. [Google Scholar] [CrossRef]
- Akpakwu, G.A.; Silva, B.J.; Hancke, G.P.; Abu-Mahfouz, A.M. A Survey on 5G Networks for the Internet of Things: Communication Technologies and Challenges. IEEE Access 2018, 6, 3619–3647. [Google Scholar] [CrossRef]
- Ghosh, A.; Maeder, A.; Baker, M.; Chandramouli, D. 5G Evolution: A View on 5G Cellular Technology Beyond 3GPP Release 15. IEEE Access 2019, 7, 127639–127651. [Google Scholar] [CrossRef]
- Sadjina, S.; Motz, C.; Paireder, T.; Huemer, M.; Pretl, H. A Survey of Self-Interference in LTE-Advanced and 5G New Radio Wireless Transceivers. IEEE Trans. Microw. Theory Tech. 2020, 68, 1118–1131. [Google Scholar] [CrossRef]
- Gkonis, P.K.; Trakadas, P.T.; Kaklamani, D.I. A Comprehensive Study on Simulation Techniques for 5G Networks: State of the Art Results, Analysis, and Future Challenges. Electronics 2020, 9, 468. [Google Scholar] [CrossRef]
- Subedi, P.; Alsadoon, A.; Prasad, P.W.C.; Rehman, S.; Giweli, N.; Imran, M.; Arif, S. Network slicing: A next generation 5G perspective. EURASIP J. Wirel. Commun. Netw. 2021, 2021, 102. [Google Scholar] [CrossRef]
- Zanzi, L.; Sciancalepore, V.; Garcia-Saavedra, A.; Schotten, H.D.; Costa-Pérez, X. LACO: A Latency-Driven Network Slicing Orchestration in Beyond-5G Networks. IEEE Trans. Wirel. Commun. 2021, 20, 667–682. [Google Scholar] [CrossRef]
- Wen, R.; Feng, G. Robust RAN Slicing. In Radio Access Network Slicing and Virtualization for 5G Vertical Industries; John Wiley & Sons, Inc.: Hoboken, NJ, USA, 2021; pp. 189–208. [Google Scholar] [CrossRef]
- Sattar, D.; Matrawy, A. Optimal Slice Allocation in 5G Core Networks. IEEE Netw. Lett. 2019, 1, 48–51. [Google Scholar] [CrossRef]
- Shafique, K.; Khawaja, B.A.; Sabir, F.; Qazi, S.; Mustaqim, M. Internet of Things (IoT) for Next-Generation Smart Systems: A Review of Current Challenges, Future Trends and Prospects for Emerging 5G-IoT Scenarios. IEEE Access 2020, 8, 23022–23040. [Google Scholar] [CrossRef]
- Ding, J.; Nemati, M.; Ranaweera, C.; Choi, J. IoT Connectivity Technologies and Applications: A Survey. IEEE Access 2020, 8, 67646–67673. [Google Scholar] [CrossRef]
- Deepa, S.K.; Viswabharathi, K.; Priyadharshini, M.D.; Mithra, N. A Comprehensive Approach for IoT Based Smart Home Applications Using 5G. Int. J. Adv. Res. Sci. Commun. Technol. 2021, 12, 170–174. [Google Scholar] [CrossRef]
- IoT Analytics. State of IoT—Summer 2024 Report. 2024. Available online: https://iot-analytics.com/wp-content/uploads/2024/09/INSIGHTS-RELEASE-Number-of-connected-IoT-devices-vf.pdf (accessed on 1 July 2025).
- Autobits Labs. How Many IoT Devices Are There in 2024? [Updated]. 2024. Available online: https://autobitslabs.com/how-many-iot-devices-are-there/ (accessed on 1 July 2025).
- Chettri, L.; Bera, R. A Comprehensive Survey on Internet of Things (IoT) Toward 5G Wireless Systems. IEEE Internet Things J. 2020, 7, 16–32. [Google Scholar] [CrossRef]
- Rahimi, H.; Zibaeenejad, A.; Safavi, A.A. A Novel IoT Architecture based on 5G-IoT and Next Generation Technologies. In Proceedings of the 2018 IEEE 9th Annual Information Technology, Electronics and Mobile Communication Conference (IEMCON), Vancouver, BC, Canada, 1–3 November 2018; pp. 81–88. [Google Scholar] [CrossRef]
- Taleb, T.; Ksentini, A.; Kobbane, A. Lightweight Mobile Core Networks for Machine Type Communications. IEEE Access 2014, 2, 1128–1137. [Google Scholar] [CrossRef]
- Filali, A.; Mlika, Z.; Cherkaoui, S.; Kobbane, A. Dynamic SDN-Based Radio Access Network Slicing with Deep Reinforcement Learning for URLLC and eMBB Services. IEEE Trans. Netw. Sci. Eng. 2022, 9, 2174–2187. [Google Scholar] [CrossRef]
- Torroglosa-Garcia, E.M.; Calero, J.M.A.; Bernabe, J.B.; Skarmeta, A. Enabling Roaming Across Heterogeneous IoT Wireless Networks: LoRaWAN MEETS 5G. IEEE Access 2020, 8, 103164–103180. [Google Scholar] [CrossRef]
- Chen, X.; Ng, D.W.K.; Yu, W.; Larsson, E.G.; Al-Dhahir, N.; Schober, R. Massive Access for 5G and Beyond. IEEE J. Sel. Areas Commun. 2021, 39, 615–637. [Google Scholar] [CrossRef]
- Asad, M.; Qaisar, S.; Basit, A. Client-Centric Access Device Selection for Heterogeneous QoS Requirements in Beyond 5G IoT Networks. IEEE Access 2020, 8, 219820–219836. [Google Scholar] [CrossRef]
- Amine, M.; Walid, A.; Kobbane, A.; Cherkaoui, S. A many-to-many matching game in ultra-dense LTE HetNets. In Proceedings of the 2017 13th International Wireless Communications and Mobile Computing Conference (IWCMC), Valencia, Spain, 26–30 June 2017; pp. 1245–1250. [Google Scholar]
- Gupta, N.; Sharma, S.; Juneja, P.K.; Garg, U. SDNFV 5G-IoT: A Framework for the Next Generation 5G enabled IoT. In Proceedings of the 2020 International Conference on Advances in Computing, Communication Materials (ICACCM), Dehradun, India, 21–22 August 2020; pp. 289–294. [Google Scholar] [CrossRef]
- Rizou, S.; Alexandropoulou-Egyptiadou, E.; Psannis, K.E. GDPR Interference With Next Generation 5G and IoT Networks. IEEE Access 2020, 8, 108052–108061. [Google Scholar] [CrossRef]
- Marquez, C.; Gramaglia, M.; Fiore, M.; Banchs, A.; Costa-Pérez, X. Resource Sharing Efficiency in Network Slicing. IEEE Trans. Netw. Serv. Manag. 2019, 16, 909–923. [Google Scholar] [CrossRef]
- Wijethilaka, S.; Liyanage, M. Survey on Network Slicing for Internet of Things Realization in 5G Networks. IEEE Commun. Surv. Tutor. 2021, 23, 957–994. [Google Scholar] [CrossRef]
- Lin, Y.B.; Tseng, C.C.; Wang, M.H. Effects of Transport Network Slicing on 5G Applications. Future Internet 2021, 13, 69. [Google Scholar] [CrossRef]
- Escolar, A.M.; Alcaraz-Calero, J.M.; Salva-Garcia, P.; Bernabe, J.B.; Wang, Q. Adaptive Network Slicing in Multi-Tenant 5G IoT Networks. IEEE Access 2021, 9, 14048–14069. [Google Scholar] [CrossRef]
- Zhao, N.; Liang, Y.C.; Niyato, D.; Pei, Y.; Wu, M.; Jiang, Y. Deep Reinforcement Learning for User Association and Resource Allocation in Heterogeneous Cellular Networks. IEEE Trans. Wirel. Commun. 2019, 18, 5141–5152. [Google Scholar] [CrossRef]
- Heidarpour, M.R.; Manshaei, M.H. Resource allocation in future HetRAT networks: A general framework. Wirel. Netw. 2020, 26, 2695–2706. [Google Scholar] [CrossRef]
- Leconte, M.; Paschos, G.S.; Mertikopoulos, P.; Kozat, U.C. A Resource Allocation Framework for Network Slicing. In Proceedings of the IEEE INFOCOM 2018—IEEE Conference on Computer Communications, Honolulu, HI, USA, 16–19 April 2018; pp. 2177–2185. [Google Scholar] [CrossRef]
- Fossati, F.; Moretti, S.; Perny, P.; Secci, S. Multi-Resource Allocation for Network Slicing. IEEE/ACM Trans. Netw. 2020, 28, 1311–1324. [Google Scholar] [CrossRef]
- Wang, G.; Feng, G.; Tan, W.; Qin, S.; Wen, R.; Sun, S. Resource Allocation for Network Slices in 5G with Network Resource Pricing. In Proceedings of the GLOBECOM 2017—2017 IEEE Global Communications Conference, Singapore, 4–8 December 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Amine, M.; Kobbane, A.; Ben-Othman, J. New Network Slicing Scheme for UE Association Solution in 5G Ultra Dense HetNets. In Proceedings of the ICC 2020—2020 IEEE International Conference on Communications (ICC), Dublin, Ireland, 7–11 June 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Puterman, M.L. Markov Decision Processes: Discrete Stochastic Dynamic Programming; John Wiley & Sons: Hoboken, NJ, USA, 2014. [Google Scholar]
- Hu, Q.; Yue, W. Markov Decision Processes with Their Applications; Springer Science & Business Media: Dordrecht, The Netherlands, 2007; Volume 14. [Google Scholar]
- Réveillac, J.M. 4—Dynamic Programming. In Optimization Tools for Logistics; Réveillac, J.M., Ed.; Elsevier: Amsterdam, The Netherlands, 2015; pp. 55–75. [Google Scholar]
- Tang, L.; Tan, Q.; Shi, Y.; Wang, C.; Chen, Q. Adaptive Virtual Resource Allocation in 5G Network Slicing Using Constrained Markov Decision Process. IEEE Access 2018, 6, 61184–61195. [Google Scholar] [CrossRef]
- Xi, R.; Chen, X.; Chen, Y.; Li, Z. Real-Time Resource Slicing for 5G RAN via Deep Reinforcement Learning. In Proceedings of the 2019 IEEE 25th International Conference on Parallel and Distributed Systems (ICPADS), Tianjin, China, 4–6 December 2019; pp. 625–632. [Google Scholar] [CrossRef]
- Li, R.; Zhao, Z.; Sun, Q.; I, C.; Yang, C.; Chen, X.; Zhao, M.; Zhang, H. Deep Reinforcement Learning for Resource Management in Network Slicing. IEEE Access 2018, 6, 74429–74441. [Google Scholar] [CrossRef]
- You, H.; Yu, B.; Jin, H.; Yang, Z.; Sun, J. User-Oriented Robust Reinforcement Learning. Proc. AAAI Conf. Artif. Intell. 2023, 37, 15269–15277. [Google Scholar] [CrossRef]
- Li, Z.; Wang, X.; Pan, L.; Zhu, L.; Wang, Z.; Feng, J.; Deng, C.; Huang, L. Network topology optimization via deep reinforcement learning. IEEE Trans. Commun. 2023, 71, 2847–2859. [Google Scholar] [CrossRef]
- Wang, R.; Friderikos, V.; Aghvami, A.H. Energy-Aware Design Policy for Network Slicing Using Deep Reinforcement Learning. IEEE Trans. Serv. Comput. 2024, 17, 2378–2391. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).