A Cross-Chain Solution to Connect Multiple DNS Blockchains in Consensus Roots System
Abstract
1. Introduction
- 1.
- A 1 + N structure cross-chain scheme for efficient and trustworthy synchronization of the domain name information in the consensus roots system.
- 2.
- A simple atomic swap transaction mechanism to support autonomous participation in the cross-chain system and to protect sensitive participant data.
2. Related Work
2.1. Blockchain-Based DNS
2.2. Cross-Chain
2.3. Atomic Swap
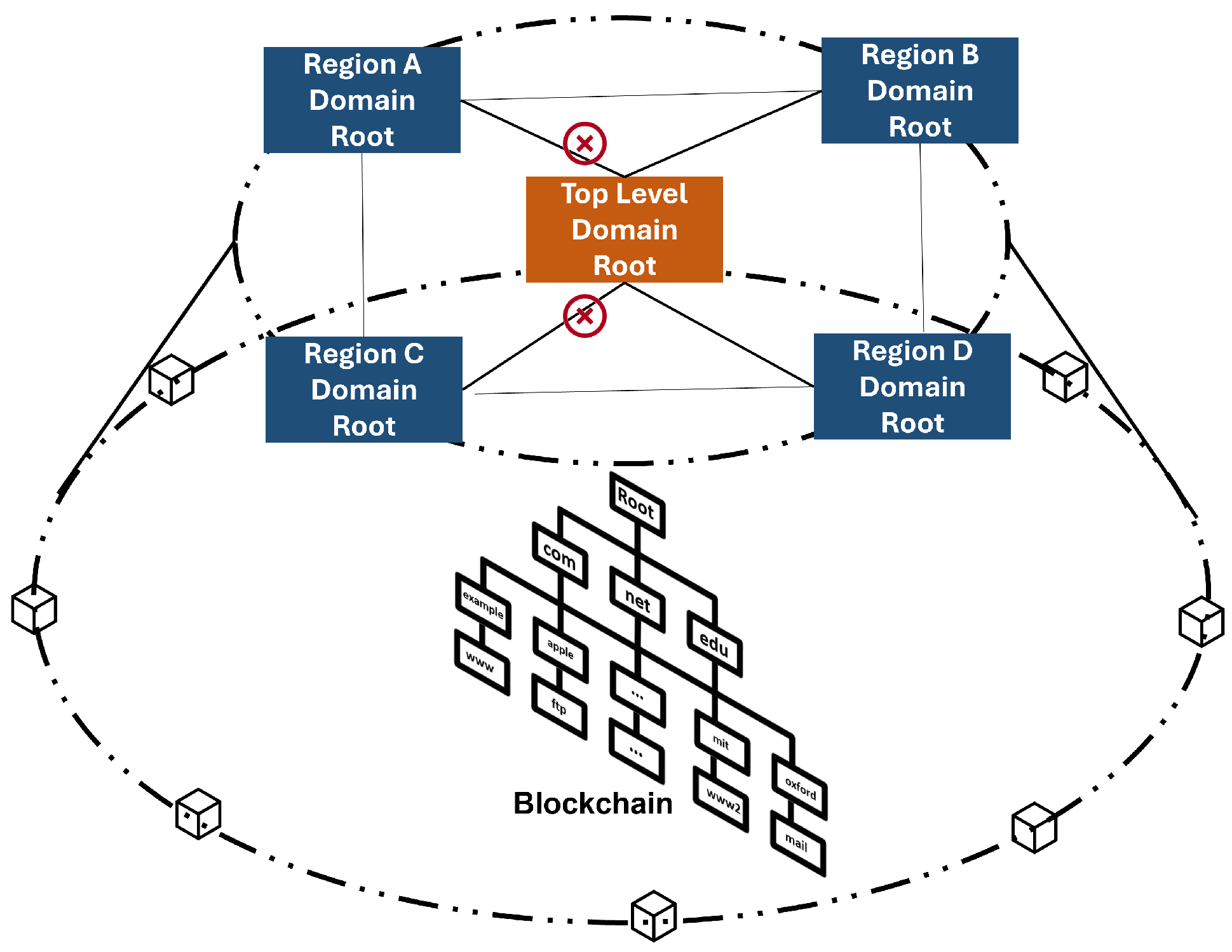
3. System Model
3.1. Master Chain
3.2. Subchain
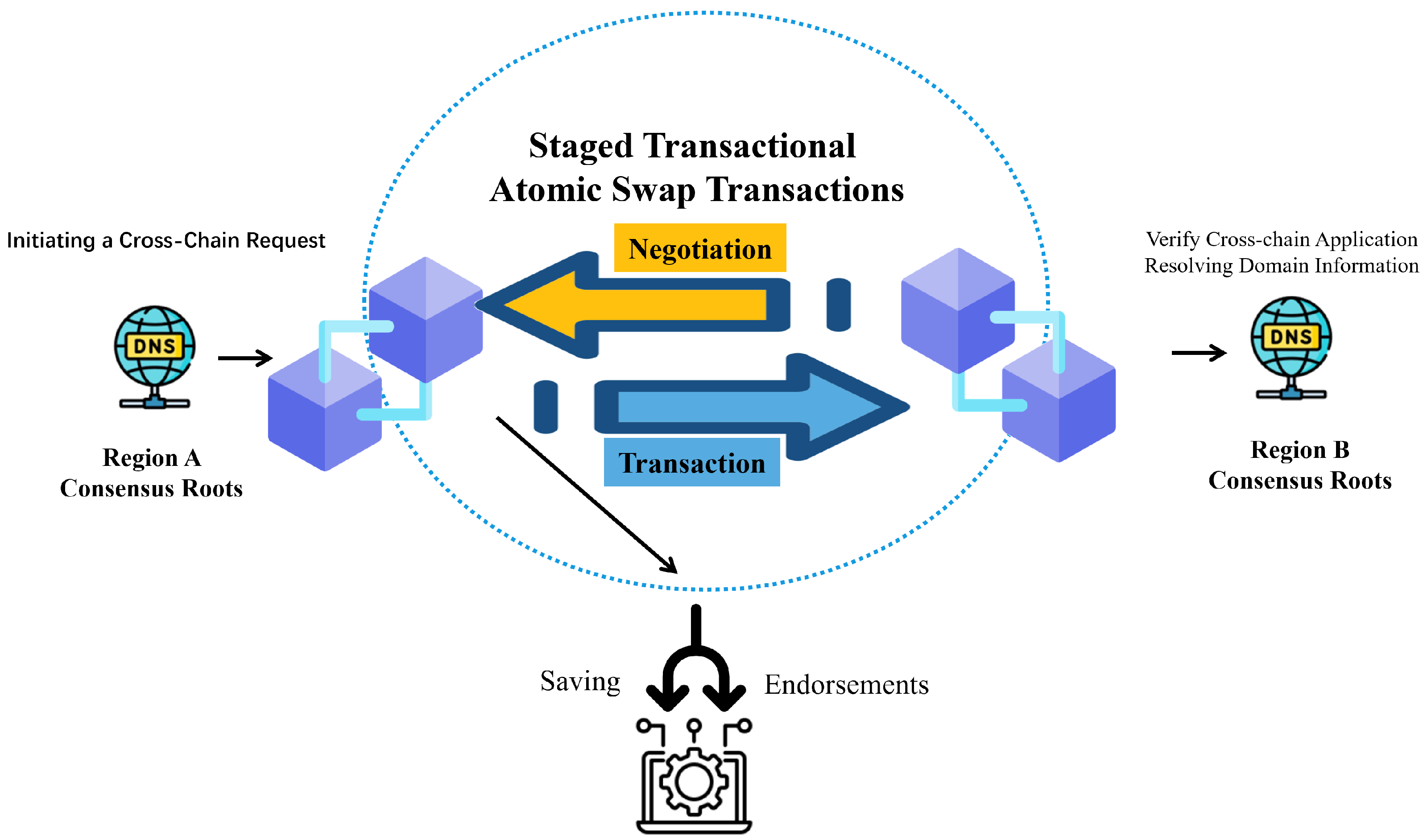
3.3. Atomic Deal
- 1.
- Preparation Phase: Participants initiate transactions and await coordinator responses.
- 2.
- Commit/Rollback Phase: Coordinators request commit or rollback from participants and await their responses. Successful responses result in final commits, while failures trigger rollbacks.
- 1.
- Negotiation phase: The parties find each other through the relay platform and draft an exchange agreement. The agreement confirms the transaction content. Each party decides whether to join and finish the transaction by its own will.
- 2.
- Transaction phase: The parties entrust their transaction content to the relay platform according to the agreement. The platform verifies and records the transaction content on the master chain.
- 3.
- Verification phase: The parties check whether the entrusted transaction content matches the agreement. They decide whether to continue or stop the transaction by their own will.
- 4.
- Commitment phase: The parties confirm that the transaction is completed and send confirmation to the relay platform. The platform records this cross-chain transaction as a security endorsement.
4. Construction of Our System
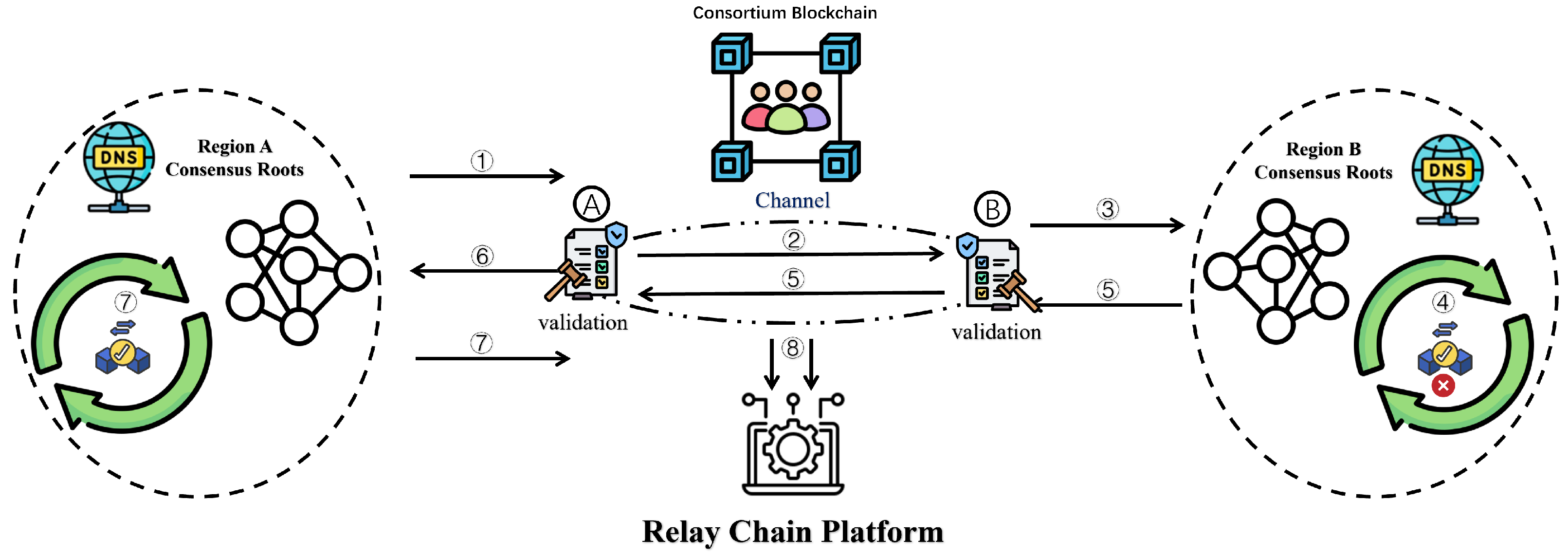
4.1. Proposed System
- 1.
- The A subchain submits a cross-chain request to the main chain, asking to synchronize DNS records with the B subchain. It includes its own identity, the B subchain’s identity, and the target domain name, and it then forwards this information to the A verification node. The A verification node first confirms that the A subchain is registered in the consensus root system.
- 2.
- Upon successful validation, the A verification node relays the cross-chain request to the B verification node on the main chain, carrying the same identity and domain name data.
- 3.
- The B verification node authenticates the request origin via the relay platform and then forwards it to the B subchain for processing.
- 4.
- The B subchain evaluates the request and decides whether to assist with DNS resolution. If it agrees, it returns the resolved record along with its identity to the B verification node; if not, it sends a rejection message, which the B verification node relays back to the A subchain. This exchange constitutes the negotiation phase of a simple atomic-swap protocol.
- 5.
- The B verification node verifies that the response originates from the B subchain and forwards the result to the A verification node on the main chain.
- 6.
- The A verification node authenticates the response source and delivers it to the A subchain.
- 7.
- The A subchain checks that the response matches its original request and the intended transaction parameters, thereby completing both the transaction and verification phases of the atomic-swap protocol. It then sends a completion confirmation to the A verification node.
- 8.
- The main chain generates a cross-chain transaction proof, recording the two blockchain identifiers, the synchronized DNS data, and the timestamp of completion. This proof is immutably stored on-chain, marking the end of the DNS synchronization process.
4.2. Contract Detail
4.3. Cross-Chain Domain Name Synchronization
- 1.
- Initiation by Source Chain: chainA starts the process by sending a synchronization request to chainB. The request contains the IDs of both chains and the domain name information (domain.info).
- 2.
- Initial Request Validation by Relay Node: A relay node obtains the request and validates its legitimacy. If it is valid, the process continues; otherwise, the request is rejected, and chainA is notified.
- 3.
- Request Forwarding and Validation by Target Chain: If the validation is successful, the relay node sends the request to chainB. Then, chainB validates the request according to its own rules and protocols.
- 4.
- Processing and Feedback by Target Chain: After validation, chainB performs the operations related to the domain name information. Then, chainB sends feedback, with its ID and either the result of the domain name operation (domain.result) or the rejection reason, to chainA.
- 5.
- Feedback Forwarding and Validation by Source Chain: The relay node forwards the feedback to chainA, which also validates the feedback to check its authenticity.
- 6.
- Confirmation by Source Chain: If the feedback is valid, chainA sends a confirmation message, with its ID and marking the synchronization status as either “completed” or “failed” based on the feedback, to chainB.
- 7.
- Proof Generation by Relay Node: The relay node generates a proof message (proof) that contains the IDs of both chains and the results of the domain name operation. This proof is an immutable record, providing evidence for the process and its outcome.
| Algorithm 1 Cross-chain domain name synchronization |
|
4.4. Atomic Deal
| Algorithm 2 Atomic deal |
|
4.4.1. Negotiation Phase
4.4.2. Transaction and Verification Phase
4.4.3. Submission Phase
- Identifiers for chainA and chainB (, ).
- Initial domain name (domain).
- Resolved IP address (res).
- Transaction packet (tx).
- Completion timestamp (time()).
4.4.4. Security Endorsement
5. Security Analysis
5.1. Security Proof
5.1.1. Security Properties and Proofs
- 1.
- The challenger initializes the main chain relay platform.
- 2.
- submits a transaction to .
- 3.
- generates block 𝘛𝘟𝘴, .
- 4.
- outputs an altered block such that .
- Forge the consensus signature , violating the EU-CMA security of the signature scheme; or
- Find a hash collision , violating the collision resistance of the hash function.
5.1.2. Privacy-Preserving Negotiation
- Simulating commitments as to preserve the hiding property.
- Extracting inputs only after receiving valid signatures, ensuring the binding property.
5.1.3. Node Authorization
6. Experimental Evaluation
6.1. Experiment Environment
6.2. Evaluation
6.3. Rationale Behind the DNS Simulation Design
7. Discussion
7.1. Comparative Benchmarks Against Existing DNS Solutions
7.2. Compliance Challenges of Cross-Chain DNS in Multi-Jurisdictional Environments
7.3. Decentralization Challenges in Consortium-Based Blockchain DNS
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Schmid, G. Thirty years of DNS insecurity: Current issues and perspectives. IEEE Commun. Surv. Tutor. 2021, 23, 2429–2459. [Google Scholar] [CrossRef]
- Khormali, A.; Park, J.; Alasmary, H.; Anwar, A.; Saad, M.; Mohaisen, D. Domain name system security and privacy: A contemporary survey. Comput. Netw. 2021, 185, 107699. [Google Scholar] [CrossRef]
- Weinberg, J. ICANN and the Problem of Legitimacy. Duke Law J. 2000, 50, 187–205. [Google Scholar] [CrossRef]
- Yli-Huumo, J.; Ko, D.; Choi, S.; Park, S.; Smolander, K. Where is current research on blockchain technology?—A systematic review. PLoS ONE 2016, 11, E0163477. [Google Scholar] [CrossRef] [PubMed]
- Xu, M.; Chen, X.; Kou, G. A systematic review of blockchain. Financ. Innov. 2019, 5, 27. [Google Scholar] [CrossRef]
- Liu, J.; Li, B.; Chen, L.; Hou, M.; Xiang, F.; Wang, P. A data storage method based on blockchain for decentralization DNS. In Proceedings of the 2018 IEEE Third International Conference on Data Science in Cyberspace (DSC), Guangzhou, China, 18–21 June 2018; pp. 189–196. [Google Scholar]
- Zhang, Y.; Xia, C.; Fang, B.; Zhang, H. An autonomous open root resolution architecture for domain name system in the internet. J. Cyber Secur. 2017, 2, 57–69. [Google Scholar]
- Lafourcade, P.; Lombard-Platet, M. About blockchain interoperability. Inf. Process. Lett. 2020, 161, 105976. [Google Scholar] [CrossRef]
- Zou, W.; Lo, D.; Kochhar, P.S.; Le, X.-B.D.; Xia, X.; Feng, Y.; Chen, Z.; Xu, B. Smart contract development: Challenges and opportunities. IEEE Trans. Softw. Eng. 2019, 47, 2084–2106. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 30 June 2025).
- Chen, T.; Li, Z.; Zhu, Y.; Chen, J.; Luo, X.; Lui, J.C.-S.; Lin, X.; Zhang, X. Understanding Ethereum via graph analysis. ACM Trans. Internet Technol. (TOIT) 2020, 20, 1–32. [Google Scholar] [CrossRef]
- Kalodner, H.A.; Carlsten, M.; Ellenbogen, P.M.; Bonneau, J.; Narayanan, A. An empirical study of Namecoin and lessons for decentralized namespace design. WEIS 2015, 1, 1–23. [Google Scholar]
- Ali, M.; Nelson, J.; Shea, R.; Freedman, M.J. Blockstack: A global naming and storage system secured by blockchains. In Proceedings of the 2016 USENIX Annual Technical Conference (USENIX ATC), Denver, CO, USA, 22–24 June 2016; pp. 181–194. [Google Scholar]
- Li, Y.; Wei, J.; Fei, Z.; Fu, Y.; Lee, X. DiSAuth: A DNS-Based Secure Authorization Framework for Protecting Data Decoupled from Applications. Comput. Netw. 2024, 254, 110774. [Google Scholar] [CrossRef]
- Divakarla, U.; Chandrasekaran, K. D-DNS: A Decentralized Domain Name System on the Blockchain: Implementation and Assessment. In Proceedings of the 2024 IEEE International Conference on Blockchain and Distributed Systems Security (ICBDS), Pune, India, 17–19 October 2024; pp. 1–7. [Google Scholar] [CrossRef]
- Samonte, M.J.C.; Abaleta, R.M.; Cayabyab, M.D.; Guerrero, L.G.D. Evaluating the Security and Privacy of Blockchain Integration in Domain Name Systems. In Proceedings of the 2024 IEEE 7th International Conference on Computer and Communication Engineering Technology (CCET), Beijing, China, 16–18 August 2024; pp. 74–79. [Google Scholar] [CrossRef]
- Robinson, P. Survey of cross-chain communications protocols. Comput. Netw. 2021, 200, 108488. [Google Scholar] [CrossRef]
- Jiang, Y.; Wang, C.; Wang, Y.; Gao, L. A cross-chain solution to integrating multiple blockchains for IoT data management. Sensors 2019, 19, 2042. [Google Scholar] [CrossRef] [PubMed]
- Johnson, S.; Robinson, P.; Brainard, J. Sidechains and interoperability. arXiv 2019, arXiv:1903.04077. [Google Scholar]
- Decker, C.; Wattenhofer, R. A fast and scalable payment network with Bitcoin duplex micropayment channels. In Stabilization, Safety, and Security of Distributed Systems: 17th International Symposium (SSS 2015), 18–21 August 2015, Edmonton, AB, Canada; Springer International Publishing: Berlin/Heidelberg, Germany, 2015; pp. 3–18. [Google Scholar]
- Luo, X.; Xue, K.; Sun, Q.; Lu, J. CrossChannel: Efficient and scalable cross-chain transactions through cross-and-off-blockchain micropayment channel. IEEE Trans. Dependable Secur. Comput. 2024, 22, 649–663. [Google Scholar] [CrossRef]
- Yi, W.; Xie, Q.; Kuzmin, S.; Gerasimov, I.; Cheng, X. CCC-TM: Cross-Chain consensus committee method using a trust model. Inf. Sci. 2024, 677, 120930. [Google Scholar] [CrossRef]
- Guo, H.; Liang, H.; Huang, J.; Ou, W.; Han, W.; Zhang, Q.; Zhang, R. A framework for efficient cross-chain token transfers in blockchain networks. J. King Saud Univ.—Comput. Inf. Sci. 2024, 36, 101968. [Google Scholar] [CrossRef]
- Herlihy, M. Atomic cross-chain swaps. In Proceedings of the 2018 ACM Symposium on Principles of Distributed Computing, Egham, UK, 23–27 July 2018; pp. 245–254. [Google Scholar]
- Herlihy, M.; Liskov, B.; Shrira, L. Cross-chain deals and adversarial commerce. arXiv 2019, arXiv:1905.09743. [Google Scholar] [CrossRef]
- Androulaki, E.; Barger, A.; Bortnikov, V.; Cachin, C.; Christidis, K.; De Caro, A.; Enyeart, D.; Ferris, C.; Laventman, G.; Manevich, Y.; et al. Hyperledger Fabric: A distributed operating system for permissioned blockchains. In Proceedings of the Thirteenth EuroSys Conference, Porto, Portugal, 23–26 April 2018; pp. 1–15. [Google Scholar]
- Weiler, S.; Blacka, D. Clarifications and Implementation Notes for DNS Security (DNSSEC). In RFC 6840. 2013. Available online: https://www.rfc-editor.org/info/rfc6840 (accessed on 30 June 2025).
- Gutierrez, C.; Krishnan, R.; Sundaram, R.; Zhou, F. Hard-DNS: Highly-available redundantly-distributed DNS. In Proceedings of the MILCOM Military Communications Conference, San Jose, CA, USA, 31 October–3 November 2010; pp. 2110–2115. [Google Scholar]
- AlFardan, N.J.; Paterson, K.G. An analysis of DepenDNS. In Information Security: 13th International Conference, ISC 2010, Boca Raton, FL, USA, Revised Selected Papers; Springer: Berlin/Heidelberg, Germany, 2011; Volume 6531, pp. 16–30. [Google Scholar]
- Fu, Y.; Wei, J.; Li, Y.; Peng, B.; Li, X. TI-DNS: A Trusted and Incentive DNS Resolution Architecture Based on Blockchain. In Proceedings of the 2023 IEEE 22nd International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), Exeter, UK, 1–3 November 2023; pp. 265–274. [Google Scholar]
- Benshoof, B.; Rosen, A.; Bourgeois, A.; Wang, X.; Pan, D. Distributed Decentralized Domain Name Service. In Proceedings of the 2016 IEEE International Parallel and Distributed Processing Symposium Workshops (IPDPSW), Chicago, IL, USA, 23–27 May 2016; pp. 1279–1287. [Google Scholar]
- Liu, W.F.; Zhang, Y.; Liu, L.; Wang, Y. A Secure Domain Name Resolution and Management Architecture Based on Blockchain. In Proceedings of the 2020 IEEE Symposium on Computers and Communications (ISCC), Rennes, France, 7–10 July 2020; pp. 1–7. [Google Scholar]
- Liu, S.Y.; Guo, S.Y.; Hu, Z.W.; Liu, L.Y. Domain Name Service Mechanism Based on Master–Slave Chain. Intell. Autom. Soft Comput. 2022, 32, 951–962. [Google Scholar] [CrossRef]
- Wang, Z.; Yu, S.; Rose, S. An on-demand defense scheme against DNS cache poisoning attacks. In Security and Privacy in Communication Networks: 13th International Conference, SecureComm 2017, Niagara Falls, ON, Canada, 22–25 October 2017, Proceedings; Springer International Publishing: Berlin/Heidelberg, Germany, 2018; Volume 238, pp. 367–385. [Google Scholar]



| Notation | Description |
|---|---|
| A | Represents Chain A in the blockchain network |
| B | Represents Chain B in the blockchain network |
| domain | The domain name to be synchronized between chains |
| res | The resolved state of the domain after processing |
| The request sent from Chain A to Chain B or vice versa | |
| Feedback sent from Chain B to Chain A or vice versa | |
| Transaction object that holds domain-related data | |
| The result of the transaction | |
| time | The timestamp when the transaction occurs |
| Query Sending Rate (TPS) | ODD | DNSSEC | HARD-DNS | DepenDNS | Our Solution |
|---|---|---|---|---|---|
| 40 | 535 | 530 | 570 | 620 | 460 |
| 80 | 540 | 555 | 615 | 715 | 516 |
| 120 | 555 | 605 | 645 | 890 | 572 |
| 160 | 560 | 600 | 790 | 950 | 628 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhu, L.; Hu, S.; Zhang, Z.; Meng, C. A Cross-Chain Solution to Connect Multiple DNS Blockchains in Consensus Roots System. Appl. Sci. 2025, 15, 7422. https://doi.org/10.3390/app15137422
Zhu L, Hu S, Zhang Z, Meng C. A Cross-Chain Solution to Connect Multiple DNS Blockchains in Consensus Roots System. Applied Sciences. 2025; 15(13):7422. https://doi.org/10.3390/app15137422
Chicago/Turabian StyleZhu, Linkai, Shanwen Hu, Zeyu Zhang, and Changpu Meng. 2025. "A Cross-Chain Solution to Connect Multiple DNS Blockchains in Consensus Roots System" Applied Sciences 15, no. 13: 7422. https://doi.org/10.3390/app15137422
APA StyleZhu, L., Hu, S., Zhang, Z., & Meng, C. (2025). A Cross-Chain Solution to Connect Multiple DNS Blockchains in Consensus Roots System. Applied Sciences, 15(13), 7422. https://doi.org/10.3390/app15137422







