Efficient Load Balancing for Blockchain-Based Healthcare System in Smart Cities
Abstract
1. Introduction
- The proposed scheme reduces the delay in nonce computation tasks by offering a load balancing mechanism and thus computes more nonce calculation tasks in a specific time. This is achieved by optimally distributing the data blocks to different mining nodes to compute their respective SHA-256-based hash values.
- proposes an algorithm for the load balancer to optimally distribute the nonce requesting data blocks on different mining nodes.
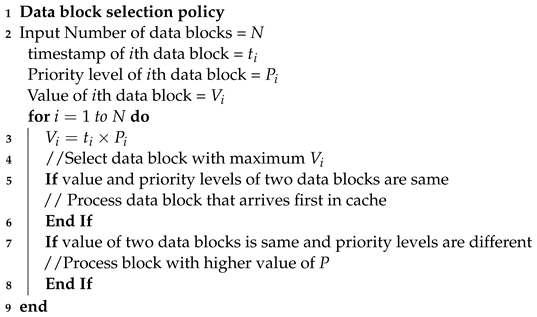
- proposes another algorithm for mining nodes to prioritize the highest-priority patient data blocks over comparatively low-priority data blocks.
2. Related Work
2.1. Blockchain in Healthcare
2.2. Efficient Mining of Blockchain Tasks
2.3. Load Balancing in Blockchain Networks
2.4. Novelty of the Proposed Technique
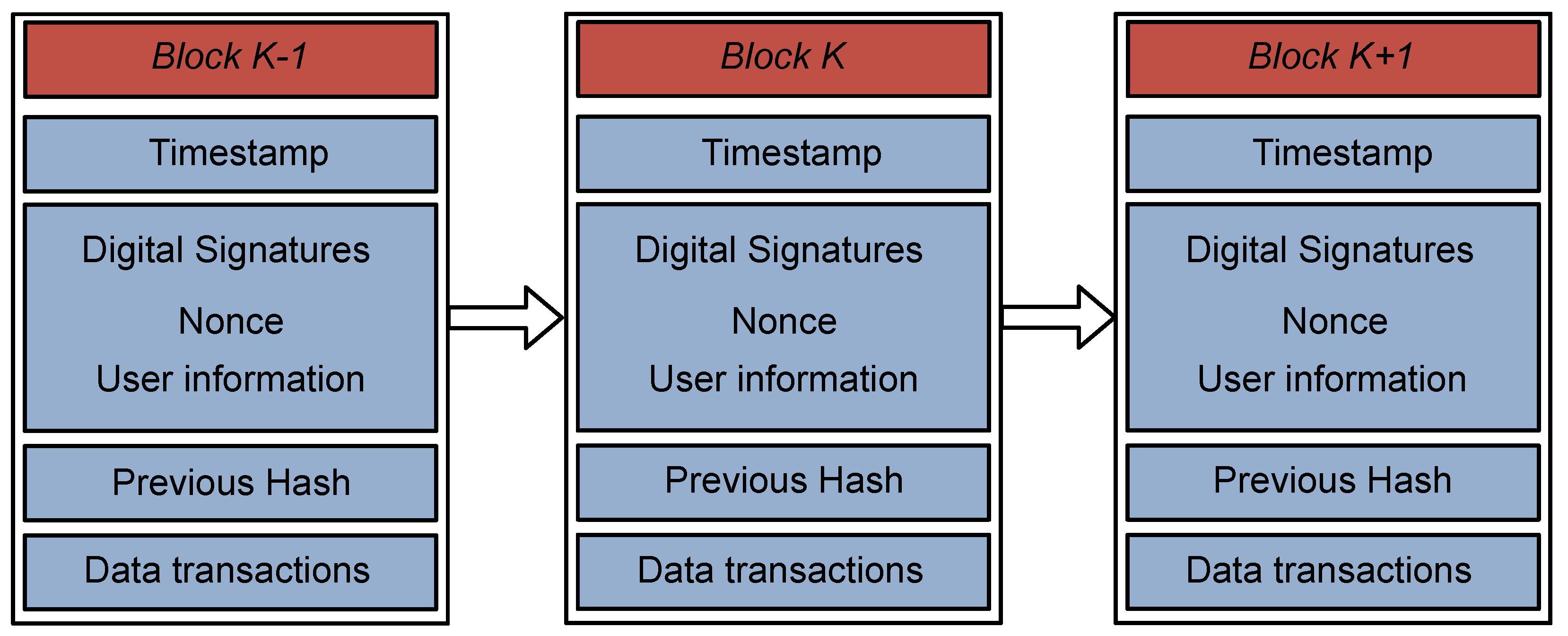
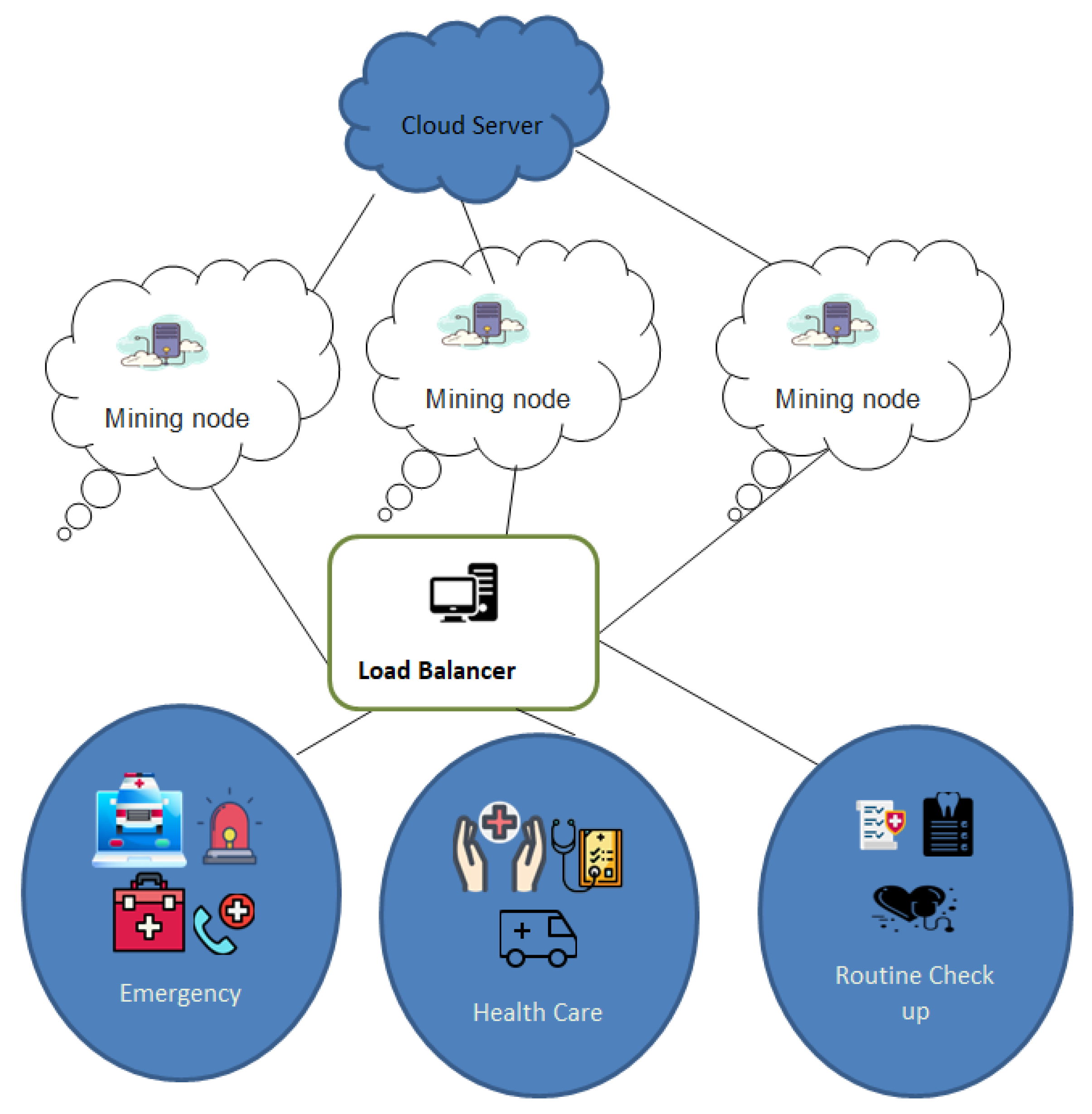
3. System Model
4. Proposed Scheme
4.1. Proposed Algorithm for Load Balancing Node
- Rearrange the entire data blocks according to their computing time relating to data block size in descending order.
- Assign the longest data block to the mining node with the lowest computing load.
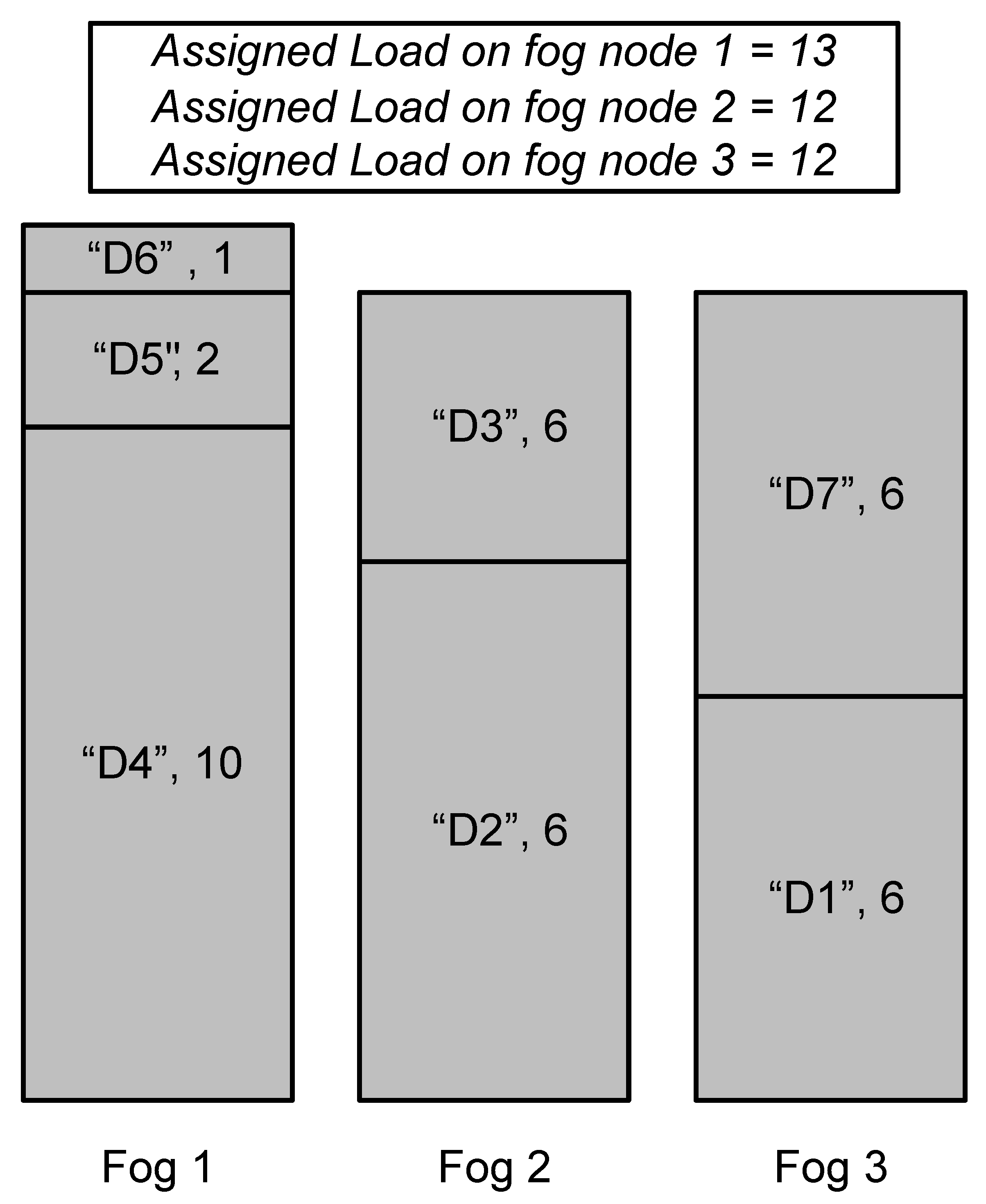
- Calculate the total data block sizes and divide them by the number of fog mining machines to get an average of the data load that needs to be assigned on any machine. The optimum data capacity in this case is determined as:The maximum caching load on any of the machines cannot be less than this average load. For example, if there are three data blocks D1, D2, D4, and D5 with data sizes of 2, 3, 1, 2, and 2, respectively, and they are required to be allocated on two machines, then each machine will be assigned a load of 5, which is the average of the load by allocating 3 and 2 data blocks each.
- When there is a single large-size data block and the rest are smaller, then the large block is assigned to one fog mining machine and all the rest to other fog mining machines. In this case, the optimal load assignment on a machine is calculated asIn this case, the maximum caching load on a single machine will be equal to the size of the biggest data block. For example, there are three data blocks D1, D2, and D3 with data sizes of 2, 1, and 6, respectively, that are required to be assigned on two machines, then one machine will be allocated D3, where D1 and D2 are allocated on other machines, resulting in a maximum caching load of 6.
| Algorithm 1: Proposed algorithm for load balancing |
 |
4.2. Nonce Computing Algorithm
| Algorithm 2: Pseudo code of nonce computing by mining node |
 |
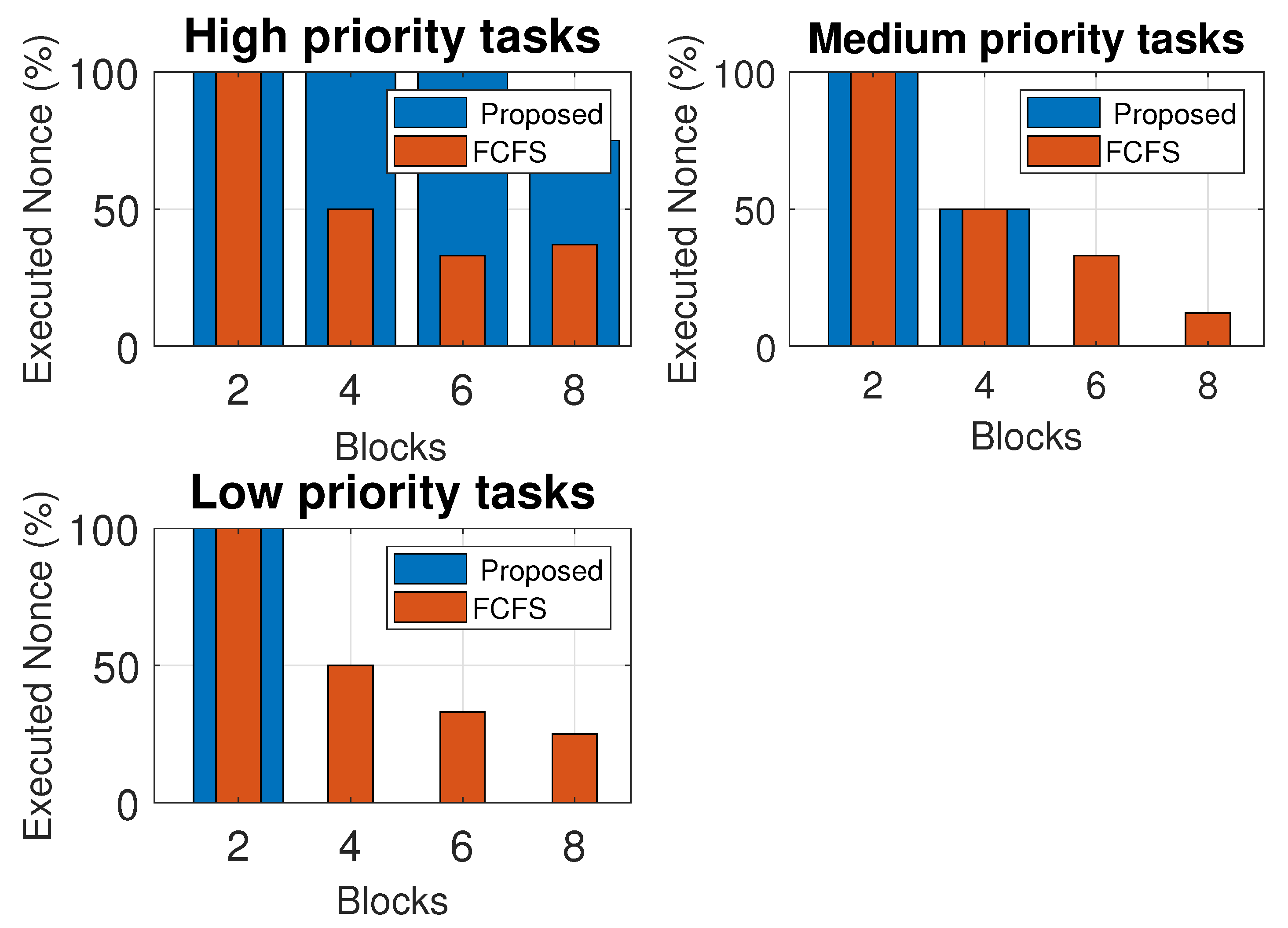
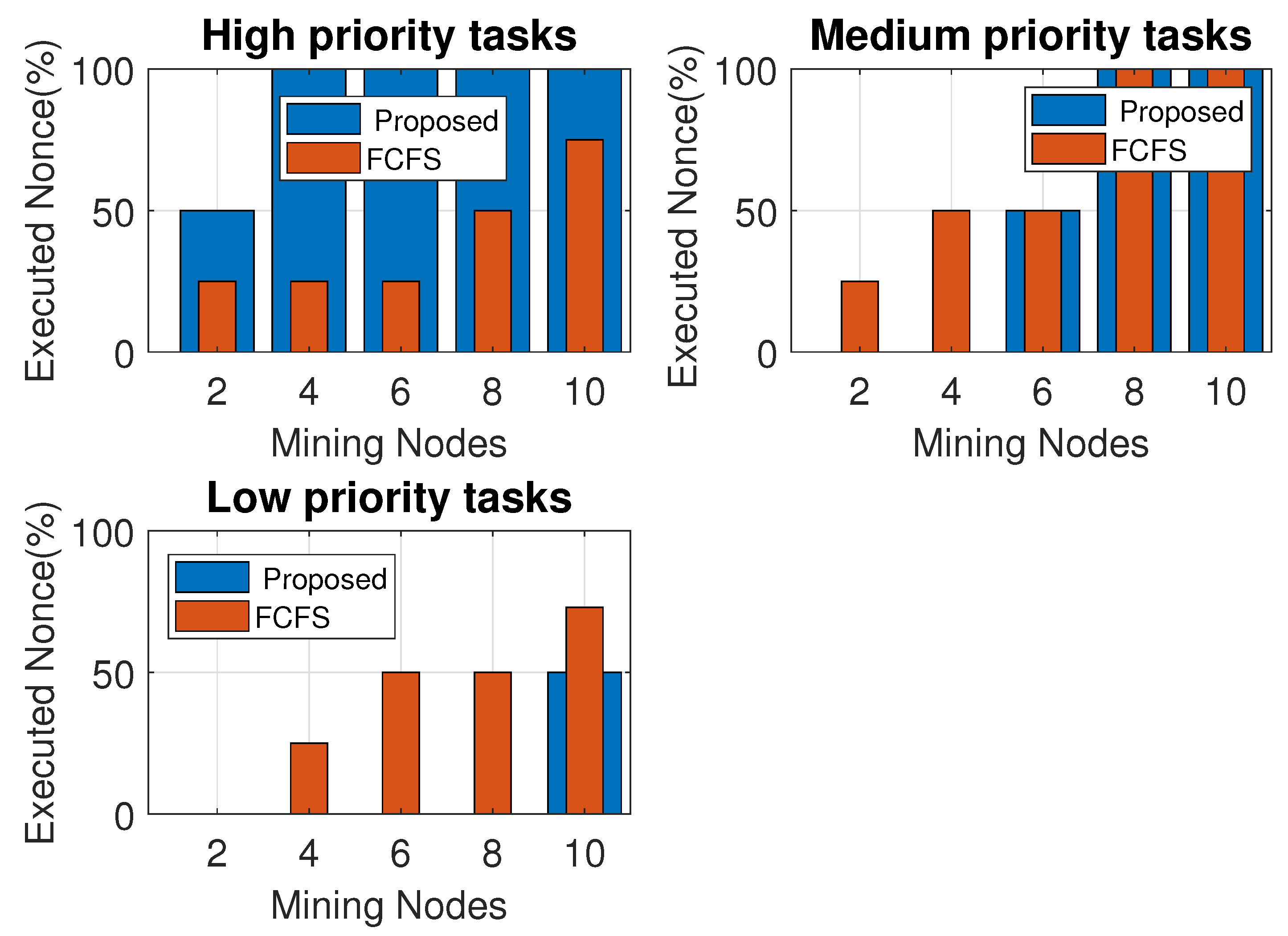
5. Results and Analysis
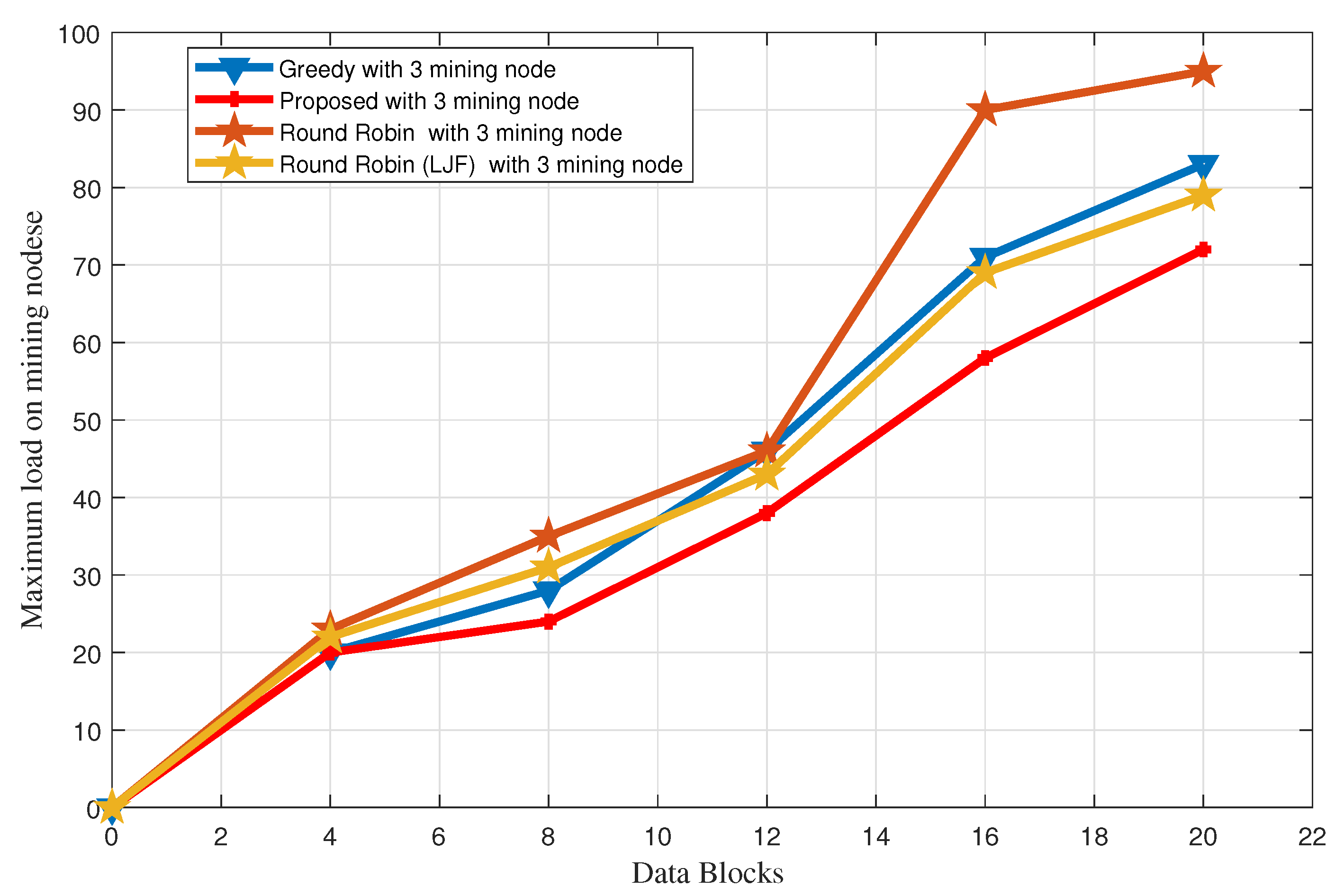
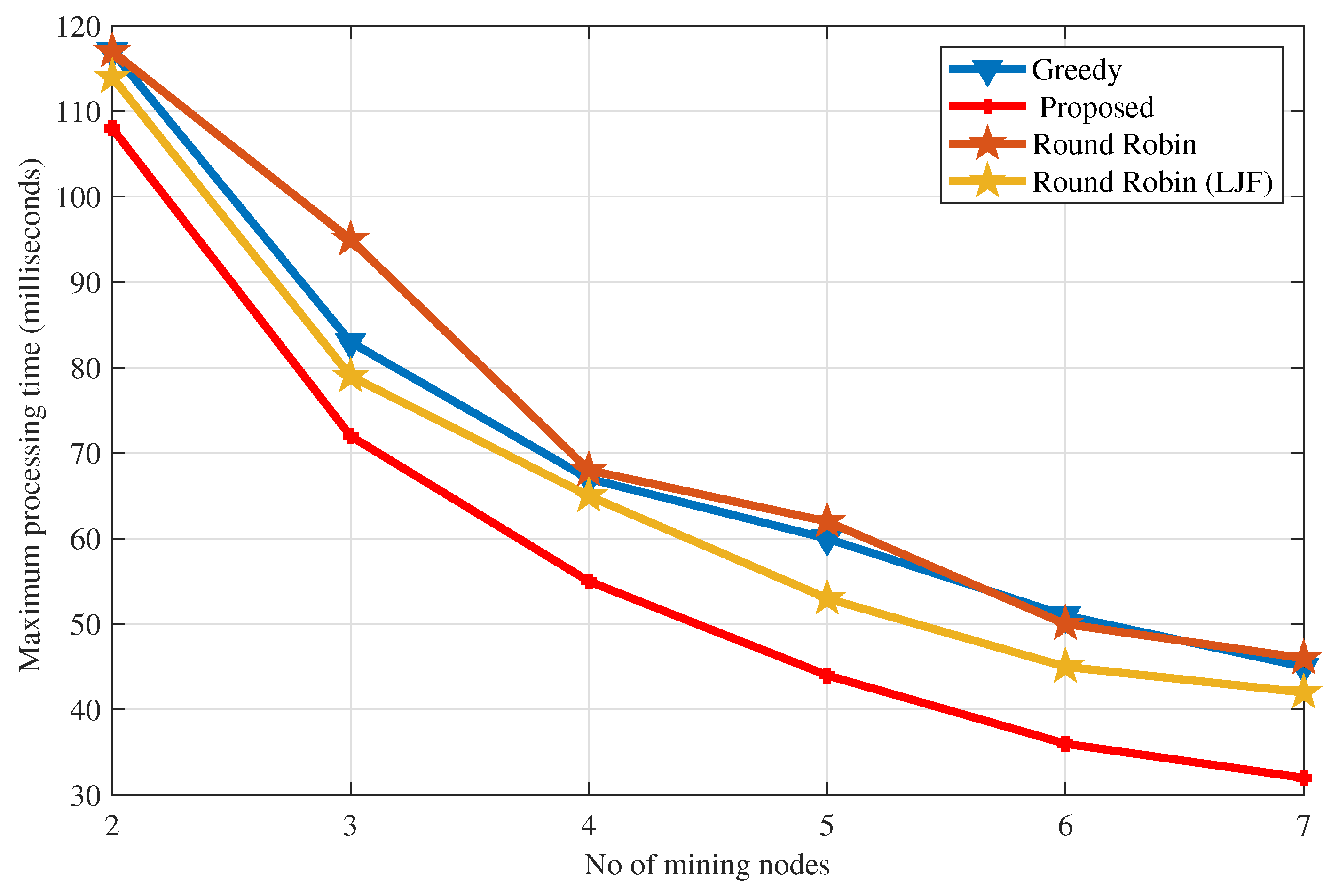
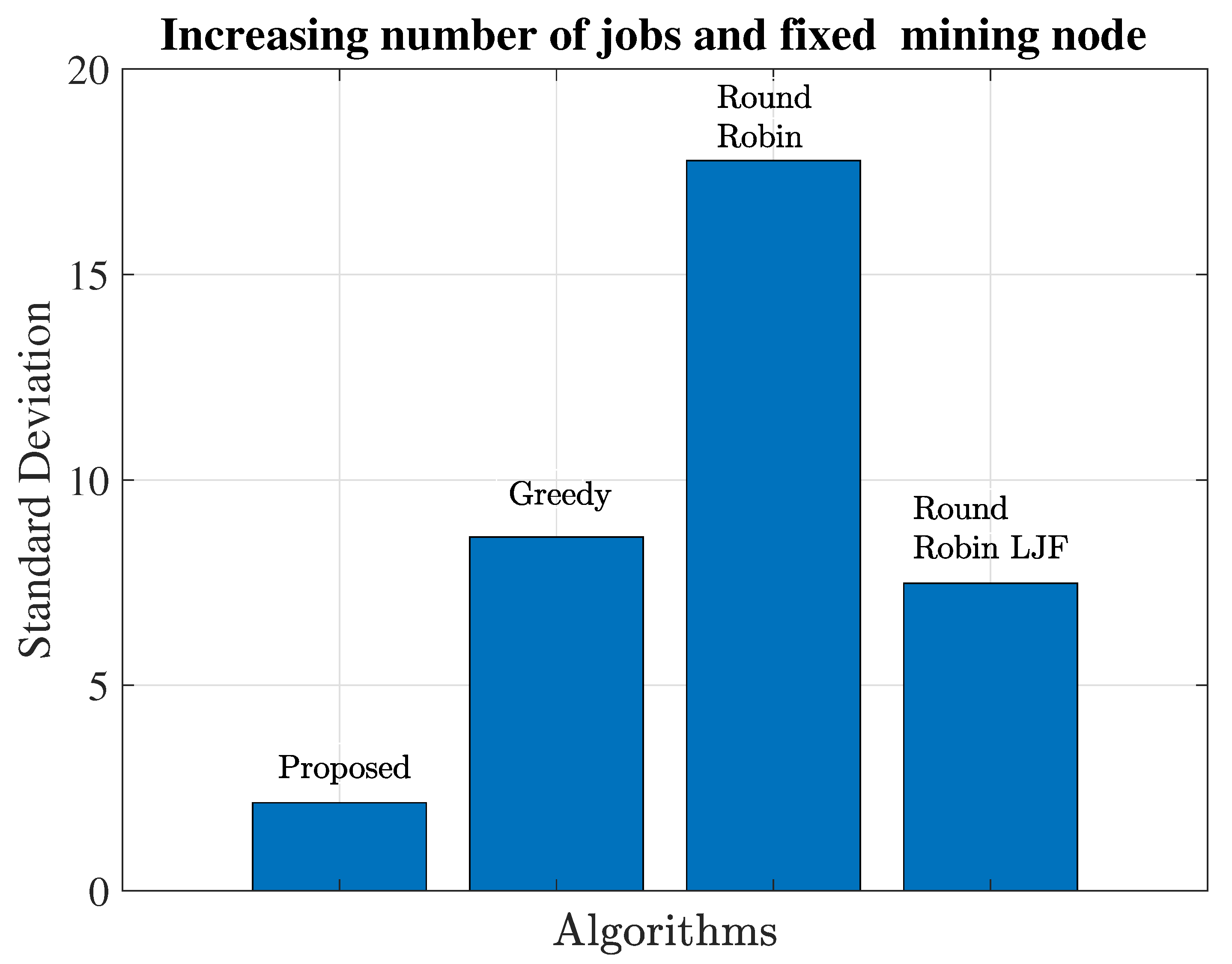
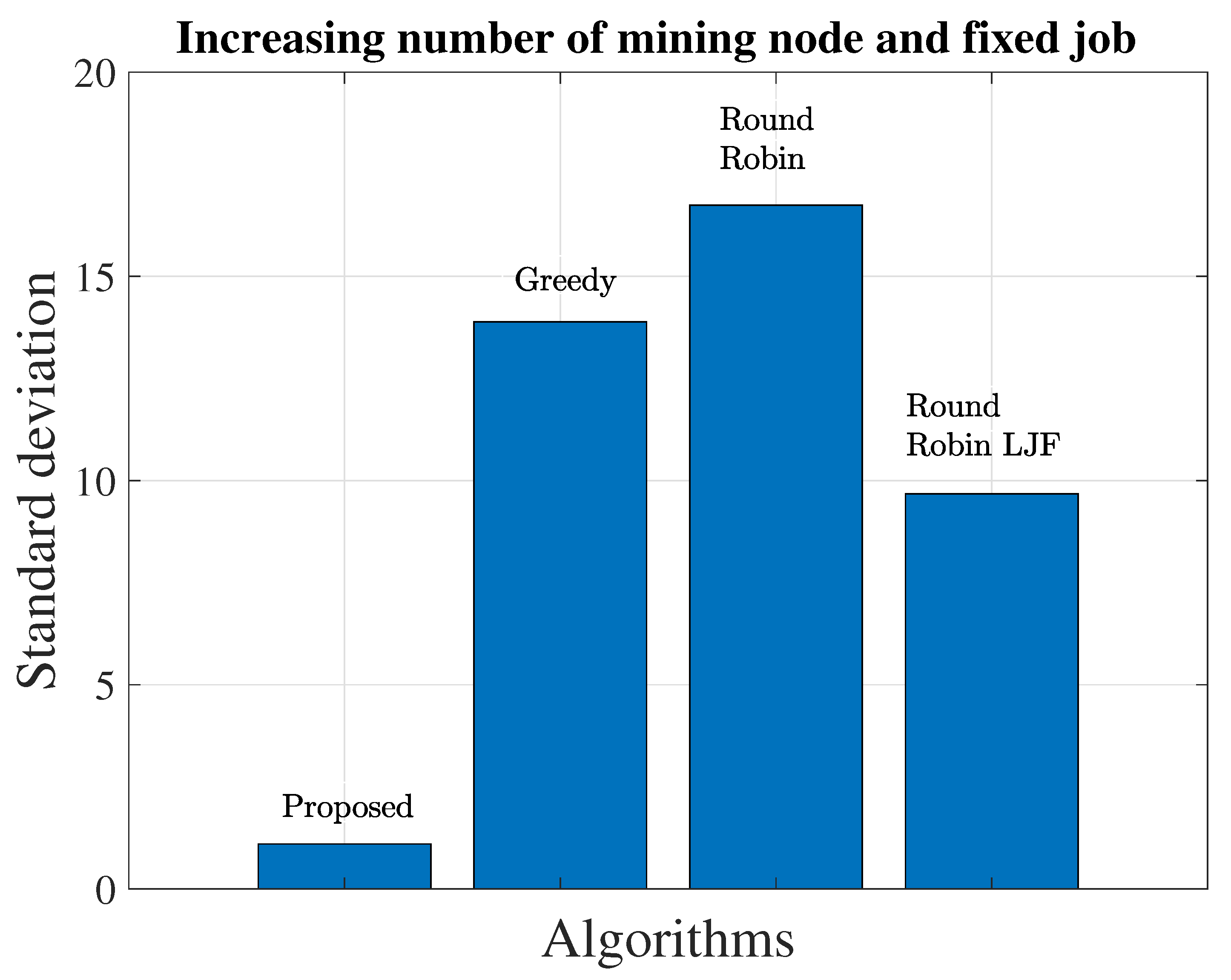
5.1. Load Balancing Greedy vs. Proposed Algorithm vs. Round Robin vs. Round Robin with LJF
5.2. Proposed Job Sequencing with the Deadline
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Zeadally, S.; Javed, M.A.; Hamida, E.B. Vehicular Communications for ITS: Standardization and Challenges. IEEE Commun. Stand. Mag. 2020, 4, 11–17. [Google Scholar] [CrossRef]
- Esposito, C.; Castiglione, A.; Frattini, F.; Cinque, M.; Yang, Y.; Choo, K.K.R. On Data Sovereignty in Cloud-Based Computation Offloading for Smart Cities Applications. IEEE Internet Things J. 2019, 6, 4521–4535. [Google Scholar] [CrossRef]
- Javed, M.A.; Nguyen, T.N.; Mirza, J.; Ahmed, J.; Ali, B. Reliable Communications for Cybertwin driven 6G IoVs using Intelligent Reflecting Surfaces. IEEE Trans. Ind. Inform. 2022, 18, 7454–7462. [Google Scholar] [CrossRef]
- Du, R.; Santi, P.; Xiao, M.; Vasilakos, A.V.; Fischione, C. The Sensable City: A Survey on the Deployment and Management for Smart City Monitoring. IEEE Commun. Surv. Tutorials 2019, 21, 1533–1560. [Google Scholar] [CrossRef]
- Javed, M.A.; Zeadally, S.; Hamida, E.B. Data analytics for Cooperative Intelligent Transport Systems. Veh. Commun. 2019, 15, 63–72. [Google Scholar] [CrossRef]
- Malik, U.M.; Javed, M.A.; Zeadally, S.; Islam, S.U. Energy-Efficient Fog Computing for 6G-Enabled Massive IoT: Recent Trends and Future Opportunities. IEEE Internet Things J. 2022, 9, 14572–14594. [Google Scholar] [CrossRef]
- Malik, U.M.; Javed, M.A. Ambient Intelligence assisted fog computing for industrial IoT applications. Comput. Commun. 2022, 196, 117–128. [Google Scholar] [CrossRef]
- Rahim, M.; Ali, S.; Alvi, A.N.; Javed, M.A.; Imran, M.; Azad, M.A.; Chen, D. An intelligent content caching protocol for connected vehicles. Emerg. Telecommun. Technol. 2021, 32, 1–14. [Google Scholar] [CrossRef]
- Martinez, I.; Hafid, A.S.; Jarray, A. Design, Resource Management, and Evaluation of Fog Computing Systems: A Survey. IEEE Internet Things J. 2021, 8, 2494–2516. [Google Scholar] [CrossRef]
- Rahim, M.; Javed, M.A.; Alvi, A.N.; Imran, M. An efficient caching policy for content retrieval in autonomous connected vehicles. Transp. Res. Part A Policy Pract. 2020, 140, 142–152. [Google Scholar] [CrossRef]
- Ali, B.; Adeel Pasha, M.; Islam, S.u.; Song, H.; Buyya, R. A Volunteer-Supported Fog Computing Environment for Delay-Sensitive IoT Applications. IEEE Internet Things J. 2021, 8, 3822–3830. [Google Scholar] [CrossRef]
- Malik, U.M.; Javed, M.A.; Frnda, J.; Rozhon, J.; Khan, W.U. Efficient Matching-Based Parallel Task Offloading in IoT Networks. Sensors 2022, 22, 6906. [Google Scholar] [CrossRef]
- Reis, J.; Marques, P.A.; Marques, P.C. Where Are Smart Cities Heading? A Meta-Review and Guidelines for Future Research. Appl. Sci. 2022, 12, 8328. [Google Scholar] [CrossRef]
- Esashika, D.; Masieroa, G.; Maugerb, Y. An investigation into the elusive concept of smart cities: A systematic review and meta-synthesis. Technol. Anal. Strateg. Manag. 2021, 33, 957–969. [Google Scholar] [CrossRef]
- Zhang, L.; You, W.; Mu, Y. Secure Outsourced Attribute-Based Sharing Framework for Lightweight Devices in Smart Health Systems. IEEE Trans. Serv. Comput. 2022, 15, 3019–3030. [Google Scholar] [CrossRef]
- Venkatesh, J.; Aksanli, B.; Chan, C.S.; Akyurek, A.S.; Rosing, T.S. Modular and Personalized Smart Health Application Design in a Smart City Environment. IEEE Internet Things J. 2018, 5, 614–623. [Google Scholar] [CrossRef]
- Ahmed, J.; Nguyen, T.N.; Ali, B.; Javed, A.; Mirza, J. On the Physical Layer Security of Federated Learning based IoMT Networks. IEEE J. Biomed. Health Inform. 2023, 27, 691–697. [Google Scholar] [CrossRef] [PubMed]
- Corsini, R.R.; Costa, A.; Fichera, S.; Pluchino, A.; Parrinello, V. System design of outpatient chemotherapy oncology departments through simulation and design of experiments. Int. J. Manag. Sci. Eng. Manag. 2022, 1–14. [Google Scholar] [CrossRef]
- Edwards, L.; Hermis, K.; LeGette, C.R.; Lujan, L.A. Acuity-Based Scheduling: Outcomes in Ambulatory Oncology Centers. Clin. J. Oncol. Nurs. 2017, 21, 250–253. [Google Scholar] [CrossRef] [PubMed]
- Kallen, M.A.; Terrell, J.A.; Lewis-Patterson, P.; Hwang, J.P. Improving Wait Time for Chemotherapy in an Outpatient Clinic at a Comprehensive Cancer Center. JCO Oncol. Pract. 2012, 8, e1–e7. [Google Scholar] [CrossRef] [PubMed]
- Menon, S.; Jain, K. Blockchain Technology for Transparency in Agri-Food Supply Chain: Use Cases, Limitations, and Future Directions. IEEE Trans. Eng. Manag. 2021, 1–15. [Google Scholar] [CrossRef]
- Ahmad, R.W.; Salah, K.; Jayaraman, R.; Yaqoob, I.; Omar, M.; Ellahham, S. Blockchain-Based Forward Supply Chain and Waste Management for COVID-19 Medical Equipment and Supplies. IEEE Access 2021, 9, 44905–44927. [Google Scholar] [CrossRef] [PubMed]
- Ahamed, N.N.; Thivakaran, T.K.; Karthikeyan, P. Perishable Food Products Contains Safe in Cold Supply Chain Management Using Blockchain Technology. In Proceedings of the 2021 7th International Conference on Advanced Computing and Communication Systems (ICACCS), Coimbatore, India, 19–20 March 2021; Volume 1, pp. 167–172. [Google Scholar] [CrossRef]
- Guo, S.; Dai, Y.; Guo, S.; Qiu, X.; Qi, F. Blockchain Meets Edge Computing: Stackelberg Game and Double Auction Based Task Offloading for Mobile Blockchain. IEEE Trans. Veh. Technol. 2020, 69, 5549–5561. [Google Scholar] [CrossRef]
- Zhang, X.; Chen, X. Data Security Sharing and Storage Based on a Consortium Blockchain in a Vehicular Ad-hoc Network. IEEE Access 2019, 7, 58241–58254. [Google Scholar] [CrossRef]
- Shrestha, R.; Nam, S.Y. Regional Blockchain for Vehicular Networks to Prevent 51% Attacks. IEEE Access 2019, 7, 95033–95045. [Google Scholar] [CrossRef]
- Khan, A.S.; Balan, K.; Javed, Y.; Tarmizi, S.; Abdullah, J. Secure Trust-Based Blockchain Architecture to Prevent Attacks in VANET. Sensors 2019, 19, 4954. [Google Scholar] [CrossRef]
- Hegde, M.; Rao, R.R.; Nikhil, B.M. DDMIA: Distributed Dynamic Mutual Identity Authentication for Referrals in Blockchain-Based Health Care Networks. IEEE Access 2022, 10, 78557–78575. [Google Scholar] [CrossRef]
- Vardhini, B.; Dass, S.N.; R, S.; Chinnaiyan, R. A Blockchain based Electronic Medical Health Records Framework using Smart Contracts. In Proceedings of the 2021 International Conference on Computer Communication and Informatics (ICCCI), Coimbatore, India, 27–29 January 2021; pp. 1–4. [Google Scholar] [CrossRef]
- Zhuang, Y.; Sheets, L.R.; Chen, Y.W.; Shae, Z.Y.; Tsai, J.J.; Shyu, C.R. A Patient-Centric Health Information Exchange Framework Using Blockchain Technology. IEEE J. Biomed. Health Inform. 2020, 24, 2169–2176. [Google Scholar] [CrossRef]
- Indumathi, J.; Shankar, A.; Ghalib, M.R.; Gitanjali, J.; Hua, Q.; Wen, Z.; Qi, X. Block Chain Based Internet of Medical Things for Uninterrupted, Ubiquitous, User-Friendly, Unflappable, Unblemished, Unlimited Health Care Services (BC IoMT U6 HCS). IEEE Access 2020, 8, 216856–216872. [Google Scholar] [CrossRef]
- Vasilateanu, A.; Diaconu, A.T. Ambient Assisted Living Environment based on Blockchain for Elderly Care. In Proceedings of the 2020 International Conference on e-Health and Bioengineering (EHB), Iasi, Romania, 29–30 October 2020; pp. 1–4. [Google Scholar] [CrossRef]
- Alamri, B.; Crowley, K.; Richardson, I. Blockchain-Based Identity Management Systems in Health IoT: A Systematic Review. IEEE Access 2022, 10, 59612–59629. [Google Scholar] [CrossRef]
- Nguyen, D.C.; Pathirana, P.N.; Ding, M.; Seneviratne, A. Privacy-Preserved Task Offloading in Mobile Blockchain With Deep Reinforcement Learning. IEEE Trans. Netw. Serv. Manag. 2020, 17, 2536–2549. [Google Scholar] [CrossRef]
- Zhang, K.; Cao, J.; Leng, S.; Shao, C.; Zhang, Y. Mining Task Offloading in Mobile Edge Computing Empowered Blockchain. In Proceedings of the 2019 IEEE International Conference on Smart Internet of Things (SmartIoT), Tianjin, China, 9–11 August 2019; pp. 234–239. [Google Scholar] [CrossRef]
- Nguyen, D.; Ding, M.; Pathirana, P.; Seneviratne, A.; Li, J.; Poor, V. Cooperative Task Offloading and Block Mining in Blockchain-based Edge Computing with Multi-agent Deep Reinforcement Learning. IEEE Trans. Mob. Comput. 2021. [Google Scholar] [CrossRef]
- Luo, S.; Li, H.; Wen, Z.; Qian, B.; Morgan, G.; Longo, A.; Rana, O.; Ranjan, R. Blockchain-Based Task Offloading in Drone-Aided Mobile Edge Computing. IEEE Netw. 2021, 35, 124–129. [Google Scholar] [CrossRef]
- Samy, A.; Elgendy, I.A.; Yu, H.; Zhang, W.; Zhang, H. Secure Task Offloading in Blockchain-Enabled Mobile Edge Computing with Deep Reinforcement Learning. IEEE Trans. Netw. Serv. Manag. 2022, 19, 4872–4887. [Google Scholar] [CrossRef]
- Jameel, F.; Javed, M.A.; Zeadally, S.; Jäntti, R. Efficient Mining Cluster Selection for Blockchain-Based Cellular V2X Communications. IEEE Trans. Intell. Transp. Syst. 2021, 22, 4064–4072. [Google Scholar] [CrossRef]
- Xu, X.; Zhang, X.; Gao, H.; Xue, Y.; Qi, L.; Dou, W. BeCome: Blockchain-Enabled Computation Offloading for IoT in Mobile Edge Computing. IEEE Trans. Ind. Inform. 2020, 16, 4187–4195. [Google Scholar] [CrossRef]
- Yahaya, A.S.; Javaid, N.; Javed, M.U.; Shafiq, M.; Khan, W.Z.; Aalsalem, M.Y. Blockchain-Based Energy Trading and Load Balancing Using Contract Theory and Reputation in a Smart Community. IEEE Access 2020, 8, 222168–222186. [Google Scholar] [CrossRef]
- Khalid, R.; Javaid, N.; Almogren, A.; Javed, M.U.; Javaid, S.; Zuair, M. A Blockchain-Based Load Balancing in Decentralized Hybrid P2P Energy Trading Market in Smart Grid. IEEE Access 2020, 8, 47047–47062. [Google Scholar] [CrossRef]
- Kaneko, Y.; Asaka, T. DHT Clustering for Load Balancing Considering Blockchain Data Size. In Proceedings of the 2018 Sixth International Symposium on Computing and Networking Workshops (CANDARW), Takayama, Japan, 27–30 November 2018; pp. 71–74. [Google Scholar] [CrossRef]
- Fan, C.; Lin, C.; Khazaei, H.; Musilek, P. Performance Analysis of Hyperledger Besu in Private Blockchain. In Proceedings of the 2022 IEEE International Conference on Decentralized Applications and Infrastructures (DAPPS), Newark, CA, USA, 15–18 August 2022; pp. 64–73. [Google Scholar] [CrossRef]
- Mukherjee, M.; Liu, Y.; Lloret, J.; Guo, L.; Matam, R.; Aazam, M. Transmission and Latency-Aware Load Balancing for Fog Radio Access Networks. In Proceedings of the 2018 IEEE Global Communications Conference (GLOBECOM), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Ahmad, N.; Javaid, N.; Mehmood, M.; Hayat, M.; Ullah, A.; Khan, H.A. Fog-Cloud Based Platform for Utilization of Resources Using Load Balancing Technique. In Advances in Network-Based Information Systems: The 21st International Conference on Network-Based Information Systems; Barolli, L., Kryvinska, N., Enokido, T., Takizawa, M., Eds.; Springer International Publishing: Cham, Switzerland, 2019; pp. 554–567. [Google Scholar]

| Blockchain Network Used | Load Balancing Technique | Key Idea |
|---|---|---|
| Vehicular network [39] | Auction mechanism | Clustering mechanism Transmission rate improvement Fairness |
| IoT [40] | Genetic algorithm Simple additive weighting Multicriteria decision making | Find feasible resource allocation multi-objective optimization |
| Electric vehicles [41] | Contract incentive mechanism | Incentive based energy cooperation |
| Smart grids [42] | P2P energy trading | Smart contract for energy trading |
| Financial systems [43] | Kademlia based DHT | Data sharing based on DHT |
| Financial systems [44] | Round Robin | Block creation performance Block validation performance |
| IoT (Our technique) | Minimum makespan Prioritization | Fair distribution of nonce tasks Quick execution of sensitive data |
| Data Blocks | Priority Levels | Time Since Arrival | Priority Value () |
|---|---|---|---|
| DB1 | High | 12 | 3600 |
| DB2 | High | 15 | 4500 |
| DB3 | Medium | 20 | 1400 |
| DB4 | Medium | 25 | 1750 |
| DB5 | Low | 30 | 300 |
| Parameter | Value |
|---|---|
| Fog Mining Node coverage area | 1500 m |
| Distance between fog mining node and Nonce requesting data blocks | 50–1500 |
| Number of simultaneous data blocks for each mining node | 6–30 |
| Number of mining nodes | 2–10 |
| Downloading data rate from cloud mining server | 2 Mbps |
| Downloading data rate from fog mining node | 8 Mbps |
| Number of Nonce computing by fog mining node | 2 |
| Emergency data blocks | 2–10 |
| Medium level sensitive data blocks | 2–10 |
| Least sensitive data blocks | 2–10 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tareen, F.N.; Alvi, A.N.; Malik, A.A.; Javed, M.A.; Khan, M.B.; Saudagar, A.K.J.; Alkhathami, M.; Abul Hasanat, M.H. Efficient Load Balancing for Blockchain-Based Healthcare System in Smart Cities. Appl. Sci. 2023, 13, 2411. https://doi.org/10.3390/app13042411
Tareen FN, Alvi AN, Malik AA, Javed MA, Khan MB, Saudagar AKJ, Alkhathami M, Abul Hasanat MH. Efficient Load Balancing for Blockchain-Based Healthcare System in Smart Cities. Applied Sciences. 2023; 13(4):2411. https://doi.org/10.3390/app13042411
Chicago/Turabian StyleTareen, Faheem Nawaz, Ahmad Naseem Alvi, Asad Ali Malik, Muhammad Awais Javed, Muhammad Badruddin Khan, Abdul Khader Jilani Saudagar, Mohammed Alkhathami, and Mozaherul Hoque Abul Hasanat. 2023. "Efficient Load Balancing for Blockchain-Based Healthcare System in Smart Cities" Applied Sciences 13, no. 4: 2411. https://doi.org/10.3390/app13042411
APA StyleTareen, F. N., Alvi, A. N., Malik, A. A., Javed, M. A., Khan, M. B., Saudagar, A. K. J., Alkhathami, M., & Abul Hasanat, M. H. (2023). Efficient Load Balancing for Blockchain-Based Healthcare System in Smart Cities. Applied Sciences, 13(4), 2411. https://doi.org/10.3390/app13042411







