Ensemble-Based Deep Learning Models for Enhancing IoT Intrusion Detection
Abstract
:1. Introduction
- we introduce a flexible and highly efficient approach that utilizes ensemble-based deep learning models to swiftly and accurately detect intrusions in IoT environments while mitigating false positives and negatives;
- we evaluate and characterize the performance of deep learning algorithms;
- we provide a systematic and comparative experimental analysis.
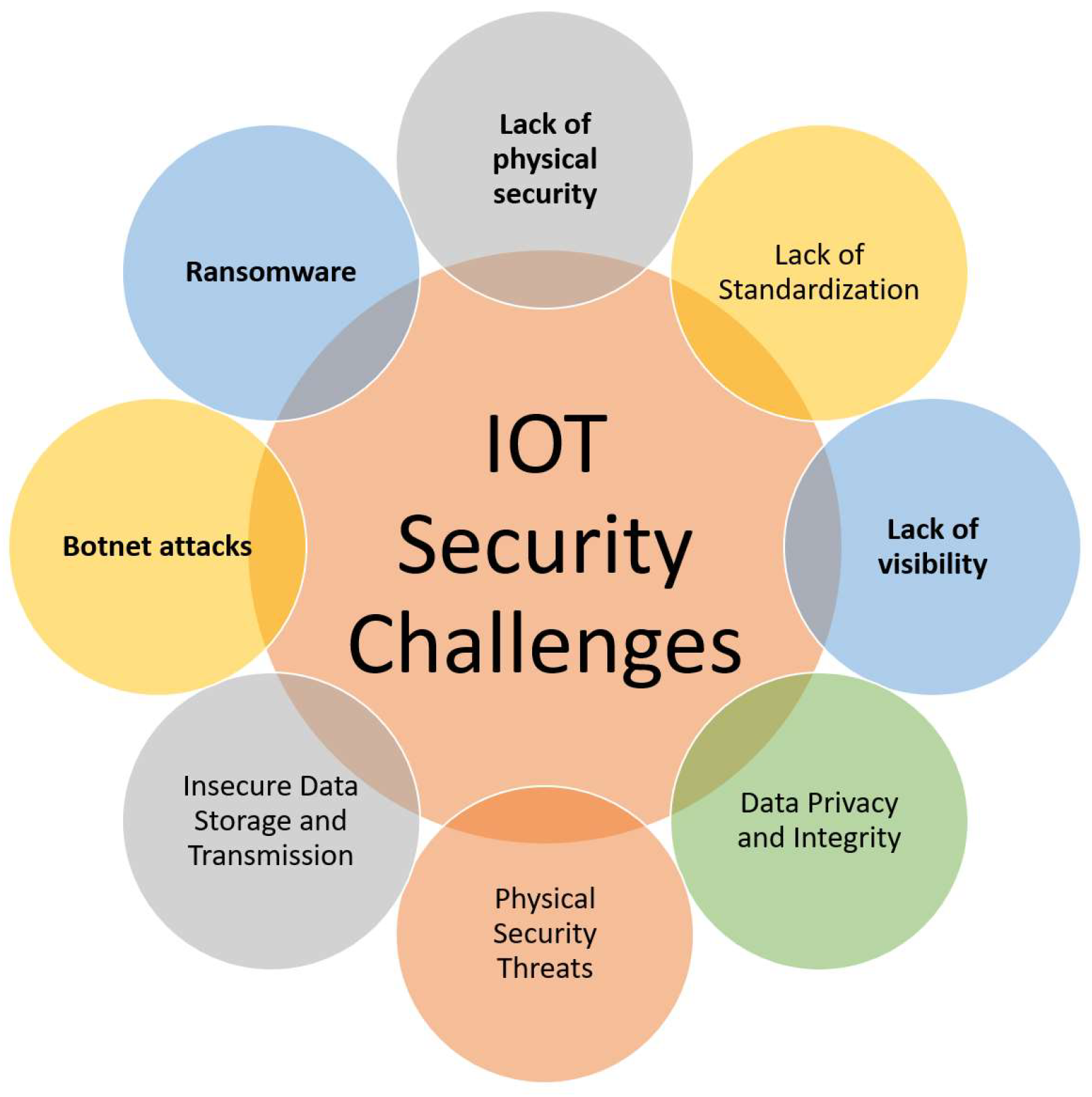
1.1. IoT Security Challenges
1.1.1. Lack of Physical Security
1.1.2. Lack of Standardization
1.1.3. Lack of Visibility
1.1.4. Data Privacy and Integrity
1.1.5. Physical Security Threats
1.1.6. Insecure Data Storage and Transmission
1.1.7. Botnet Attacks
1.1.8. Ransomware
1.2. Intrusion Detection Systems (IDS)
2. Intrusion Detection in the Internet of Things
2.1. Placement Strategy
- Edge-based IDS: deployed on edge devices or gateways.
- Cloud-based IDS: utilizes cloud resources for intrusion detection.
- Hybrid: combines both edge and cloud-based approaches.
2.2. Detection Method
- Signature-based: uses predefined patterns or signatures of known threats.
- Anomaly-based: establishes a “normal” behavior baseline and detects deviations from this baseline.
- Specification-based: defines a set of rules or specifications that determine valid behavior.
- Hybrid: combines multiple methods for more comprehensive detection.
2.3. Security Threat
- Physical attacks: direct tampering with IoT devices.
- Network attacks: DDoS attacks, man-in-the-middle attacks, etc.
- Software attacks: malware, ransomware, etc.
- Side-channel attacks: exploits that target the physical implementation of IoT systems.
2.4. Validation Strategy
- Simulation: using software to emulate an IoT environment and test the IDS.
- Testbed: a controlled physical environment where real IoT devices are used.
- Real-world deployment: implementing the IDS in a live IoT environment.
- Theoretical analysis: using mathematical or conceptual models to validate the IDS’s effectiveness.
3. Related Works
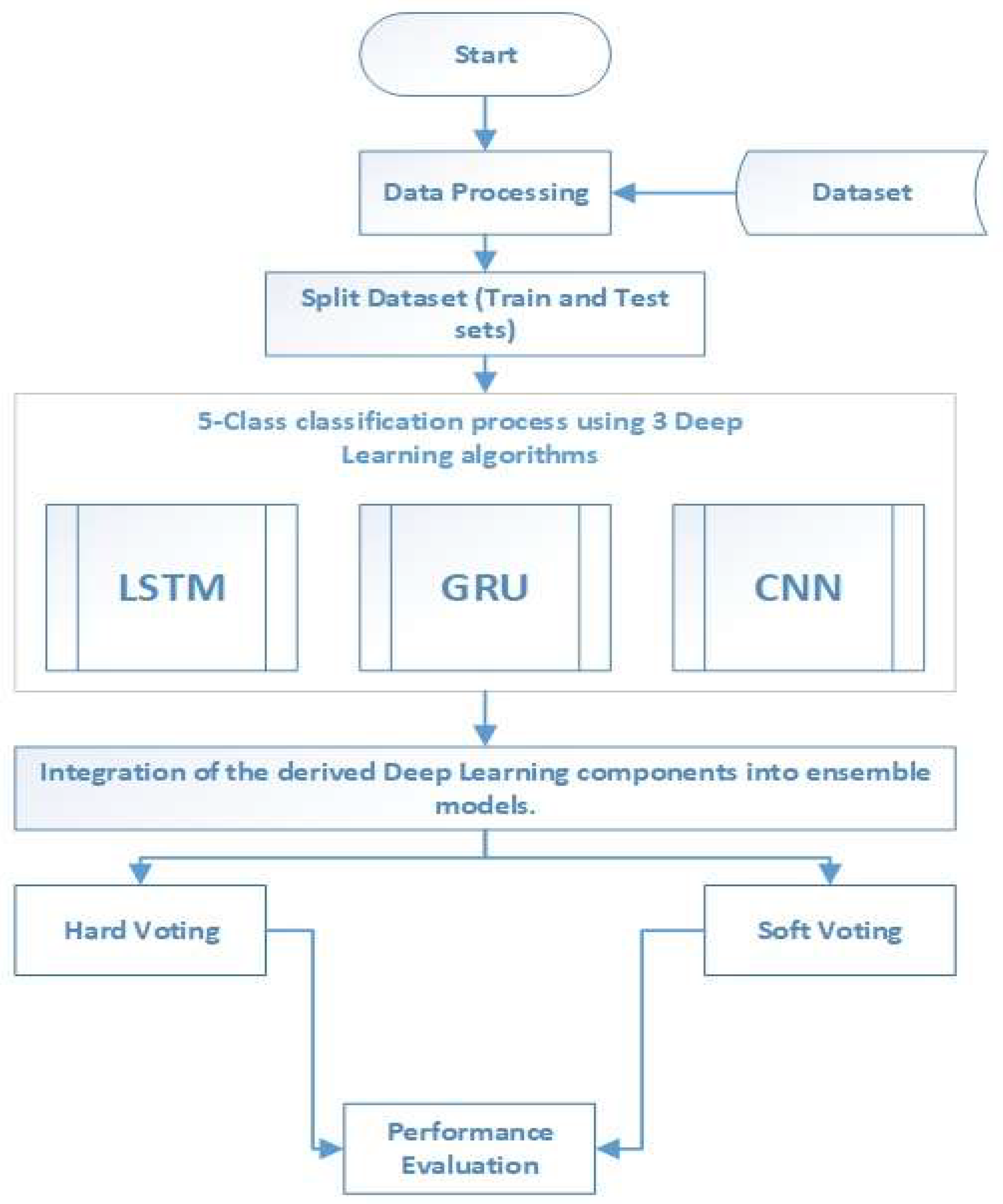
4. Proposed Ensemble of Deep Learning Models for IoT Intrusion Detection
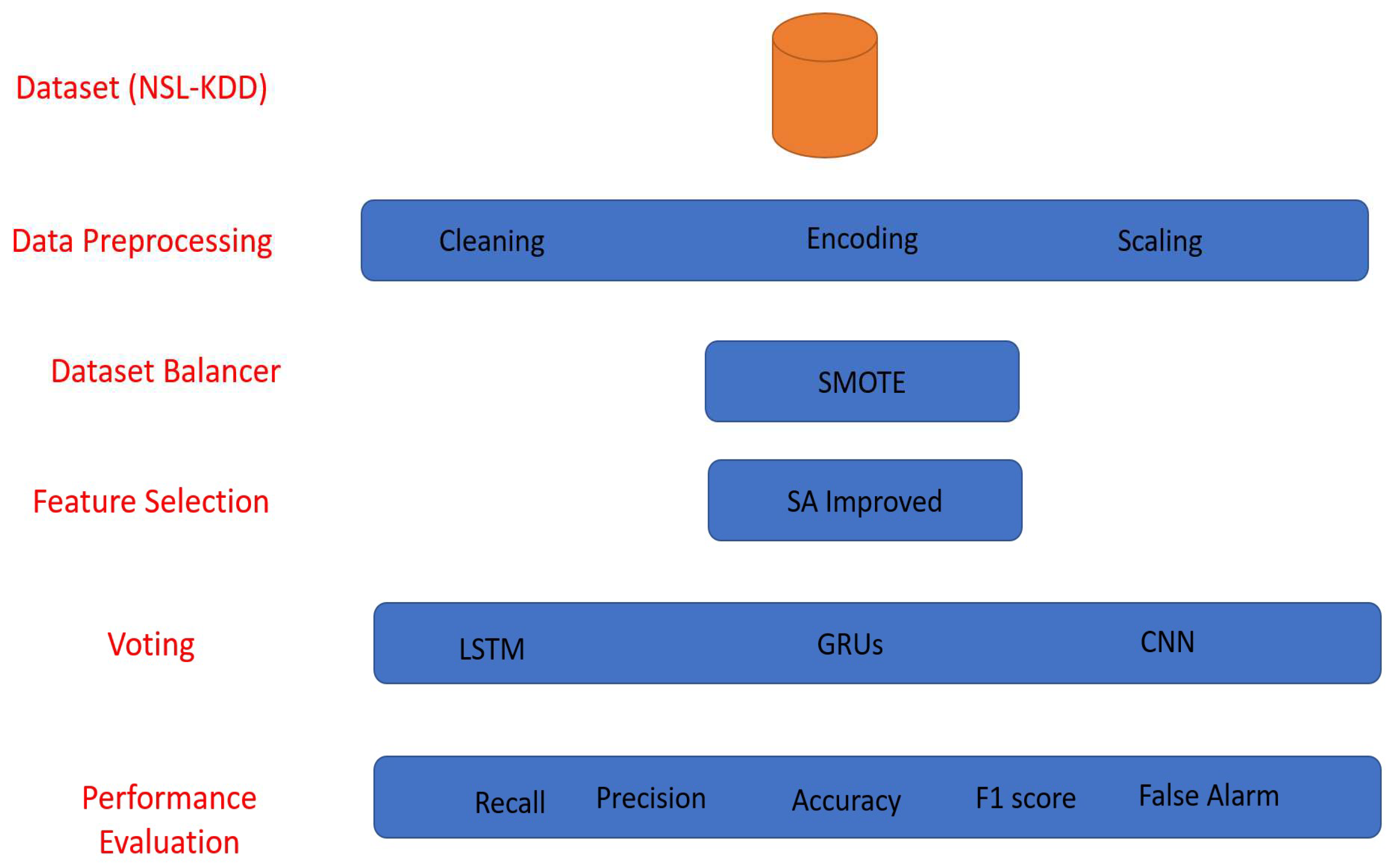
4.1. Step 1: Data Preprocessing
- Data cleaning: In this stage, we meticulously examine the datasets, eliminating duplicate entries, addressing missing values, and removing irrelevant or redundant information. This process ensures the dataset’s integrity and quality.
- Data encoding: IoT datasets often contain categorical variables that require transformation into a numerical format for machine learning models. We employ appropriate encoding techniques to convert these categorical features into a format suitable for deep learning.
- Data scaling: To bring uniformity to the dataset, we apply data scaling techniques, such as normalization or standardization, to ensure that all features have comparable scales. This step facilitates the model’s convergence during training.

4.2. Step 2: Data Balancing
- Compute the imbalance ratio (I.R.):
- Generate synthetic samples for D2 Using SMOTE (Synthetic Minority Over-sampling Technique).
4.3. Step 3: Feature Selection
4.4. Step 4: Classification Using Deep Learning Models
4.5. Step 5: Training, Testing, and Evaluation
5. Experimental Evaluation
5.1. Dataset
5.2. Performance Measures
5.3. Result and Discussion
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Hassan, W.H. Current research on Internet of Things (IoT) security: A survey. Comput. Netw. 2019, 148, 283–294. [Google Scholar]
- Ibrahim, H. A Review on the Mechanism Mitigating and Eliminating Internet Crimes using Modern Technologies: Mitigating Internet crimes using modern technologies. Wasit J. Comput. Math. Sci. 2022, 1, 76–108. [Google Scholar]
- Rizvi, S.; Kurtz, A.; Pfeffer, J.; Rizvi, M. Securing the Internet of things (IoT): A security taxonomy for IoT. In Proceedings of the 2018 17th IEEE International Conference on Trust, Security and Privacy in Computing and Communications/12th IEEE International Conference on Big Data Science and Engineering (TrustCom/BigDataSE), New York, NY, USA, 1–3 August 2018. [Google Scholar]
- Al-Garadi, M.A.; Mohamed, A.; Al-Ali, A.K.; Du, X.; Ali, I.; Guizani, M. A survey of machine and deep learning methods for Internet of things (IoT) security. IEEE Commun. Surv. Tutor. 2020, 22, 1646–1685. [Google Scholar] [CrossRef]
- Gupta, B.B.; Quamara, M. An overview of Internet of Things (IoT): Architectural aspects, challenges, and protocols. Concurr. Comput. Pract. Exp. 2020, 32, e4946. [Google Scholar] [CrossRef]
- Køien, G.M. Zero-Trust Principles for Legacy Components: 12 Rules for Legacy Devices: An Antidote to Chaos. Wirel. Pers. Commun. 2021, 121, 1169–1186. [Google Scholar] [CrossRef]
- Chen, Z.; Liu, J.; Shen, Y.; Simsek, M.; Kantarci, B.; Mouftah, H.T.; Djukic, P. Machine learning-enabled iot security: Open issues and challenges under advanced persistent threats. ACM Comput. Surv. 2022, 55, 1–37. [Google Scholar] [CrossRef]
- Le-Dang, Q.; Le-Ngoc, T. Internet of Things (IoT) infrastructures for smart cities. In Handbook of Smart Cities: Software Services and Cyber Infrastructure; Springer: Berlin/Heidelberg, Germany, 2018; pp. 1–30. [Google Scholar]
- Shaukat, K.; Alam, T.M.; Hameed, I.A.; Khan, W.A.; Abbas, N.; Luo, S. A review on security challenges in Internet of things (IoT). In Proceedings of the 2021 26th International Conference on Automation and Computing (ICAC), Portsmouth, UK, 2–4 September 2021. [Google Scholar]
- Ahanger, T.A.; Aljumah, A. Internet of Things: A comprehensive study of security issues and defense mechanisms. IEEE Access 2018, 7, 11020–11028. [Google Scholar] [CrossRef]
- Omolara, A.E.; Alabdulatif, A.; Abiodun, O.I.; Alawida, M.; Alabdulatif, A.; Arshad, H. The internet of things security: A survey encompassing unexplored areas and new insights. Comput. Secur. 2022, 112, 102494. [Google Scholar] [CrossRef]
- Sengupta, J.; Ruj, S.; Bit, S.D. A comprehensive survey on attacks, security issues and blockchain solutions for IoT and IIoT. J. Netw. Comput. Appl. 2020, 149, 102481. [Google Scholar] [CrossRef]
- Cuppari, R.; Schmeier, S.; Demuth, S. Preventing Conflicts, Fostering Cooperation—The Many Roles of Water Diplomacy; ICWRGC: Koblenz, Germany, 2017. [Google Scholar]
- Kotenko, I.; Izrailov, K.; Buinevich, M. Static analysis of information systems for IoT cyber security: A survey of machine learning approaches. Sensors 2022, 22, 1335. [Google Scholar] [CrossRef]
- Burhan, M.; Rehman, R.A.; Khan, B.; Kim, B.-S. IoT elements, layered architectures and security issues: A comprehensive survey. Sensors 2018, 18, 2796. [Google Scholar] [CrossRef] [PubMed]
- Qin, J.; Wang, J.; Lei, T.; Sun, G.; Yue, J.; Wang, W.; Chen, J.; Qian, G. Deep learning-based software and hardware framework for a noncontact inspection platform for aggregate grading. Measurement 2023, 211, 112634. [Google Scholar] [CrossRef]
- Chen, X.; Wang, Z.; Hua, Q.; Shang, W.-L.; Luo, Q.; Yu, K. AI-empowered speed extraction via port-like videos for vehicular trajectory analysis. IEEE Trans. Intell. Transp. Syst. 2022, 24, 4541–4552. [Google Scholar] [CrossRef]
- Shen, Y.; Zhu, J.; Deng, Z.; Lu, W.; Wang, H. EnsDeepDP: An Ensemble Deep Learning Approach for Disease Prediction Through Metagenomics. IEEE/ACM Trans. Comput. Biol. Bioinform. 2022, 20, 986–998. [Google Scholar] [CrossRef] [PubMed]
- Ali, B.; Awad, A.I. Cyber and physical security vulnerability assessment for IoT-based smart homes. Sensors 2018, 18, 817. [Google Scholar] [CrossRef]
- Attkan, A.; Ranga, V. Cyber-physical security for IoT networks: A comprehensive review on traditional, blockchain and artificial intelligence based key-security. Complex Intell. Syst. 2022, 8, 3559–3591. [Google Scholar] [CrossRef]
- Kumar, N.M.; Mallick, P.K. Blockchain technology for security issues and challenges in IoT. Procedia Comput. Sci. 2018, 132, 1815–1823. [Google Scholar] [CrossRef]
- Frustaci, M.; Pace, P.; Aloi, G. Securing the IoT world: Issues and perspectives. In Proceedings of the 2017 IEEE Conference on Standards for Communications and Networking (CSCN), Helsinki, Finland, 18–20 September 2017. [Google Scholar]
- Ahmed, S.; Kalsoom, T.; Ramzan, N.; Pervez, Z.; Azmat, M.; Zeb, B.; Ur Rehman, M. Towards supply chain visibility using Internet of things: A dyadic analysis review. Sensors 2021, 21, 4158. [Google Scholar] [CrossRef]
- Kothari, S.S.; Jain, S.V.; Venkteshwar, A. The impact of IOT in supply chain management. Int. Res. J. Eng. Technol 2018, 5, 257–259. [Google Scholar]
- Wang, T.; Bhuiyan, M.Z.A.; Wang, G.; Qi, L.; Wu, J.; Hayajneh, T. Preserving balance between privacy and data integrity in edge-assisted Internet of Things. IEEE Internet Things J. 2019, 7, 2679–2689. [Google Scholar] [CrossRef]
- Kim, T.; Ochoa, J.; Faika, T.; Mantooth, H.A.; Di, J.; Li, Q.; Lee, Y. An overview of cyber-physical security of battery management systems and adoption of blockchain technology. IEEE J. Emerg. Sel. Top. Power Electron. 2020, 10, 1270–1281. [Google Scholar] [CrossRef]
- Khalaf, O.I.; Abdulsahib, G.M. Optimized dynamic storage of data (ODSD) in IoT based on blockchain for wireless sensor networks. Peer Peer Netw. Appl. 2021, 14, 2858–2873. [Google Scholar] [CrossRef]
- Zhang, L.; Peng, M.; Wang, W.; Jin, Z.; Su, Y.; Chen, H. Secure and efficient data storage and sharing scheme for blockchain-based mobile-edge computing. Trans. Emerg. Telecommun. Technol. 2021, 32, e4315. [Google Scholar] [CrossRef]
- Injadat, M.; Moubayed, A.; Shami, A. Detecting botnet attacks in IoT environments: An optimized machine learning approach. In Proceedings of the 2020 32nd International Conference on Microelectronics (ICM), Aqaba, Jordan, 14–17 December 2020. [Google Scholar]
- Ali, I.; Ahmed, A.I.A.; Almogren, A.; Raza, M.A.; Shah, S.A.; Khan, A.; Gani, A. Systematic literature review on IoT-based botnet attack. IEEE Access 2020, 8, 212220–212232. [Google Scholar] [CrossRef]
- Humayun, M.; Jhanjhi, N.; Alsayat, A.; Ponnusamy, V. Internet of things and Ransomware: Evolution, mitigation and prevention. Egypt. Inform. J. 2021, 22, 105–117. [Google Scholar] [CrossRef]
- Zahra, S.R.; Chishti, M.A. Ransomware and Internet of things: A new security nightmare. In Proceedings of the 2019 9th International Conference on Cloud Computing, Data Science & Engineering (Confluence), Noida, India, 10–11 January 2019. [Google Scholar]
- Abu Al-Haija, Q.; Al Badawi, A. High-performance intrusion detection system for networked UAVs via deep learning. Neural Comput. Appl. 2022, 34, 10885–10900. [Google Scholar] [CrossRef]
- Alsulami, A.A.; Abu Al-Haija, Q.; Tayeb, A.; Alqahtani, A. An Intrusion Detection and Classification System for IoT Traffic with Improved Data Engineering. Appl. Sci. 2022, 12, 12336. [Google Scholar] [CrossRef]
- Prajapati, P.; Bhatt, B.; Zalavadiya, G.; Ajwalia, M.; Shah, P. A review on recent intrusion detection systems and intrusion prevention systems in IoT. In Proceedings of the 2021 11th International Conference on Cloud Computing, Data Science & Engineering (Confluence), Noida, India, 28–29 January 2021. [Google Scholar]
- Kumar, A.; Abhishek, K.; Ghalib, M.R.; Shankar, A.; Cheng, X. Intrusion detection and prevention system for an IoT environment. Digit. Commun. Netw. 2022, 8, 540–551. [Google Scholar] [CrossRef]
- Pandu, V.; Mohan, J.; Kumar, T. Network intrusion detection and prevention systems for attacks in IoT systems. In Countering Cyber Attacks and Preserving the Integrity and Availability of Critical Systems; IGI Global: Hershey, PA, USA, 2019; pp. 128–141. [Google Scholar]
- Jakka, G.; Alsmadi, I.M. Ensemble Models for Intrusion Detection SystemClassification. Int. J. Smart Sens. Adhoc Netw. 2022, 3, 8. [Google Scholar]
- Smys, S.; Basar, A.; Wang, H. Hybrid intrusion detection system for Internet of things (IoT). J. ISMAC 2020, 2, 190–199. [Google Scholar] [CrossRef]
- Ge, M.; Syed, N.F.; Fu, X.; Baig, Z.; Robles-Kelly, A. Towards a deep learning-driven intrusion detection approach for Internet of Things. Comput. Netw. 2021, 186, 107784. [Google Scholar] [CrossRef]
- Gassais, R.; Ezzati-Jivan, N.; Fernandez, J.M.; Aloise, D.; Dagenais, M.R. Multi-level host-based intrusion detection system for Internet of things. J. Cloud Comput. 2020, 9, 62. [Google Scholar] [CrossRef]
- Khraisat, A.; Gondal, I.; Vamplew, P.; Kamruzzaman, J.; Alazab, A. A novel ensemble of hybrid intrusion detection system for detecting Internet of things attacks. Electronics 2019, 8, 1210. [Google Scholar] [CrossRef]
- Yang, Z.; Liu, X.; Li, T.; Wu, D.; Wang, J.; Zhao, Y.; Han, H. A systematic literature review of methods and datasets for anomaly-based network intrusion detection. Comput. Secur. 2022, 116, 102675. [Google Scholar] [CrossRef]
- Sudqi Khater, B.; Abdul Wahab, A.W.B.; Idris, M.Y.I.B.; Abdulla Hussain, M.; Ahmed Ibrahim, A. A lightweight perceptron-based intrusion detection system for fog computing. Appl. Sci. 2019, 9, 178. [Google Scholar] [CrossRef]
- Tianfield, H. Cyber security situational awareness. In Proceedings of the 2016 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Chengdu, China, 15–18 December 2016. [Google Scholar]
- Krishna, A.; Lal, A.; Mathewkutty, A.J.; Jacob, D.S.; Hari, M. Intrusion detection and prevention system using deep learning. In Proceedings of the 2020 International Conference on Electronics and Sustainable Communication Systems (ICESC), Coimbatore, India, 2–4 July 2020. [Google Scholar]
- Althubiti, S.A.; Jones, E.M.; Roy, K. LSTM for anomaly-based network intrusion detection. In Proceedings of the 2018 28th International telecommunication networks and applications conference (ITNAC), Sydney, NSW, Australia, 21–23 November 2018. [Google Scholar]
- Latif, S.; e Huma, Z.; Jamal, S.S.; Ahmed, F.; Ahmad, J.; Zahid, A.; Dashtipour, K.; Aftab, M.U.; Ahmad, M.; Abbasi, Q.H. Intrusion detection framework for the Internet of things using a dense random neural network. IEEE Trans. Ind. Inform. 2021, 18, 6435–6444. [Google Scholar] [CrossRef]
- Kumar, P.; Gupta, G.P.; Tripathi, R.; Garg, S.; Hassan, M.M. DLTIF: Deep learning-driven cyber threat intelligence modeling and identification framework in IoT-enabled maritime transportation systems. IEEE Trans. Intell. Transp. Syst. 2021, 24, 2472–2481. [Google Scholar] [CrossRef]
- Kan, X.; Fan, Y.; Fang, Z.; Cao, L.; Xiong, N.N.; Yang, D.; Li, X. A novel IoT network intrusion detection approach based on adaptive particle swarm optimization convolutional neural network. Inf. Sci. 2021, 568, 147–162. [Google Scholar] [CrossRef]
- Meidan, Y.; Bohadana, M.; Mathov, Y.; Mirsky, Y.; Shabtai, A.; Breitenbacher, D.; Elovici, Y. N-baiot—Network-based detection of iot botnet attacks using deep autoencoders. IEEE Pervasive Comput. 2018, 17, 12–22. [Google Scholar] [CrossRef]
- Li, Y.; Xu, Y.; Liu, Z.; Hou, H.; Zheng, Y.; Xin, Y.; Zhao, Y.; Cui, L. Robust detection for network intrusion of industrial IoT based on multi-CNN fusion. Measurement 2020, 154, 107450. [Google Scholar] [CrossRef]
- Derhab, A.; Aldweesh, A.; Emam, A.Z.; Khan, F.A. Intrusion detection system for Internet of things based on temporal convolution neural network and efficient feature engineering. Wirel. Commun. Mob. Comput. 2020, 2020, 6689134. [Google Scholar] [CrossRef]
- Li, A.; Yi, S. Intelligent intrusion detection method of industrial Internet of things based on CNN-BiLSTM. Secur. Commun. Netw. 2022, 2022, 5448647. [Google Scholar] [CrossRef]
- Hanif, S.; Ilyas, T.; Zeeshan, M. Intrusion detection in IoT using artificial neural networks on UNSW-15 dataset. In Proceedings of the 2019 IEEE 16th International Conference on Smart Cities: Improving Quality of Life using ICT & IoT and A.I. (HONET-ICT), Charlotte, NC, USA, 6–9 October 2019. [Google Scholar]
- Moustafa, N.; Slay, J. UNSW-NB15: A comprehensive data set for network intrusion detection systems (UNSW-NB15 network data set). In Proceedings of the 2015 Military Communications and Information Systems Conference (MilCIS), Canberra, ACT, Australia, 10–12 November 2015. [Google Scholar]
- Hodo, E.; Bellekens, X.; Hamilton, A.; Dubouilh, P.-L.; Iorkyase, E.; Tachtatzis, C.; Atkinson, R. Threat analysis of IoT networks using artificial neural network intrusion detection system. In Proceedings of the 2016 International Symposium on Networks, Computers and Communications (ISNCC), Yasmine Hammamet, Tunisia, 11–13 May 2016. [Google Scholar]
- Al-Zewairi, M.; Almajali, S.; Ayyash, M. Unknown security attack detection using shallow and deep ANN classifiers. Electronics 2020, 9, 2006. [Google Scholar] [CrossRef]
- Azumah, S.W.; Bellekens, X.; Hamilton, A.; Dubouilh, P.-L.; Iorkyase, E.; Tachtatzis, C.; Atkinson, R. A deep lstm based approach for intrusion detection iot devices network in smart home. In Proceedings of the 2021 IEEE 7th World Forum on Internet of Things (WF-IoT), New Orleans, LA, USA, 14 June–31 July 2021. [Google Scholar]
- Diro, A.; Chilamkurti, N. Leveraging LSTM networks for attack detection in fog-to-things communications. IEEE Commun. Mag. 2018, 56, 124–130. [Google Scholar] [CrossRef]
- Shiravi, A.; Shiravi, H.; Tavallaee, M.; Ghorbani, A.A. Towrd developing a systematic approach to generate benchmark datasets for intrusion detection. Comput. Secur. 2012, 31, 357–374. [Google Scholar] [CrossRef]
- Hossain, M.D.; Inoue, H.; Ochiai, H.; Fall, D.; Kadobayashi, Y. LSTM-based intrusion detection system for in-vehicle can bus communications. IEEE Access 2020, 8, 185489–185502. [Google Scholar] [CrossRef]
- Ajaeiya, G.A.; Adalian, N.; Elhajj, I.H.; Kayssi, A.; Chehab, A. Flow-based intrusion detection system for SDN. In Proceedings of the 2017 IEEE Symposium on Computers and Communications (ISCC), Heraklion, Greece, 3–6 July 2017. [Google Scholar]
- Hadem, P.; Saikia, D.K.; Moulik, S. An SDN-based intrusion detection system using SVM with selective logging for IP traceback. Comput. Netw. 2021, 191, 108015. [Google Scholar] [CrossRef]
- Ye, J.; Cheng, X.; Zhu, J.; Feng, L.; Song, L. A DDoS attack detection method based on SVM in software defined network. Secur. Commun. Netw. 2018, 2018, 9804061. [Google Scholar] [CrossRef]
- ElSayed, M.S.; Le-Khac, N.-A.; Albahar, M.A.; Jurcut, A. A novel hybrid model for intrusion detection systems in SDNs based on CNN and a new regularization technique. J. Netw. Comput. Appl. 2021, 191, 103160. [Google Scholar] [CrossRef]
- Sarker, I.H.; Abushark, Y.B.; Alsolami, F.; Khan, A.I. Intrudtree: A machine learning based cyber security intrusion detection model. Symmetry 2020, 12, 754. [Google Scholar] [CrossRef]
- Amouri, A.; Alaparthy, V.T.; Morgera, S.D. A machine learning based intrusion detection system for mobile Internet of Things. Sensors 2020, 20, 461. [Google Scholar] [CrossRef] [PubMed]
- Nasir, M.; Javed, A.R.; Tariq, M.A.; Asim, M.; Baker, T. Feature engineering and deep learning-based intrusion detection framework for securing edge IoT. J. Supercomput. 2022, 78, 8852–8866. [Google Scholar] [CrossRef]
- Althobaiti, M.M.; Kumar, K.P.M.; Gupta, D.; Kumar, S.; Mansour, R.F. An intelligent cognitive computing based intrusion detection for industrial cyber-physical systems. Measurement 2021, 186, 110145. [Google Scholar] [CrossRef]

| IDS Proposals for IoT | Subcategories | Advantages | Disadvantage |
|---|---|---|---|
| Placement strategy | Edge-based IDS | Low latency, bandwidth efficiency, data privacy | Resource constraints, Scalability |
| Cloud-based IDS | Computational power, scalability, Centralized management. | Latency, Bandwidth consumption, Data privacy concerns | |
| Hybrid IDS | Flexibility, Optimized bandwidth, Enhanced coverage | Complexity | |
| Detection method | Signature-based | High accuracy in detecting known threats, fast response | Ineffective against polymorphic attacks |
| Anomaly-based | Detects unknown threats, offers a holistic view | Resource-intensive may miss subtle attacks | |
| Specification-based | Highly customizable, effective for enforcing compliance | Limited to known specifications, Can be complex to configure | |
| Hybrid | Improved accuracy, greater flexibility | Increased complexity, resource-intensive, costly | |
| Security threat | Physical attacks | Immediate detection | Limited to physical proximity, False alarms |
| Network attacks | Broad coverage, scalability | Limited visibility, potential false positives | |
| Software attacks | Detects common threats, fast response | Limited to known threats, may not prevent initial infection | |
| Side-channel attacks | Protection against specialized attacks | Specialized knowledge required | |
| Validation strategy | Simulation | Cost efficiency Scalability Risk mitigation | Model accuracy Limited realism Validation gap |
| Testbed | Real-world environment Integration testing Controlled conditions | Costly setup Limited scalability Resource constraints Repeatability issues | |
| Real-world deployment | Authentic validation User feedback Scalability testing | High risk Costly fixes Limited control Time consuming | |
| Theoretical analysis | Early assessment Low cost Insightful |
| Study | Dataset | Techniques Used | Accuracy Range |
|---|---|---|---|
| [44,45] | NSL-KDD | MLP | 85.2~87.8% |
| [48] | NSL-KDD | Dense random neural network | 88.3% |
| [49] | NSL-KDD | RNN | 89.5% |
| [50] | NSL-KDD | APSO-CNN | 88.7 |
| [51] | N-BaIoT | CNN | 85.7 |
| [52,53,54] | NSL-KDD | CNN | 90.5 |
| [55] | NSL-KDD | ANN | 92.5% |
| [56] | UNSW-15 | RNN | 92.3% |
| [57] | NSL-KDD | MLP | 87.6% |
| [58] | NSL-KDD | RNN | 88.1~90.3% |
| [59] | NSL-KDD | LSTM | 88.7% |
| [60] | NSL-KDD | LSTM | 89.4% |
| [61] | ISCX2012 | logistic regression | 88.7% |
| [62] | NSL-KDD | LSTM | 89~93% |
| [63] | NSL-KDD | Random forest | 84.5% |
| [64] | NSL-KDD | SVM and selective logging | 87.7~89.6% |
| [65] | Authors generated their dataset using network traffic in a controlled testing environment | SVM | 93% |
| [66] | NSL-KDD | CNN and random forest | 97% |
| [70] | NSL-KDD | LSTM | 93% |
| F# | Feature Name | F# | Feature Name | F# | Feature Name |
|---|---|---|---|---|---|
| F1 | Duration | F15 | Su attempted | F29 | Same srv rate |
| F2 | Protocol type | F16 | Num root | F30 | Diff srv rate |
| F3 | Service | F17 | Num file creations | F31 | Srv diff host rate |
| F4 | Flag | F18 | Num shells | F32 | Dst host count |
| F5 | Source bytes | F19 | Num access files | F33 | Dst host srv count |
| F6 | Destination bytes | F20 | Num outbound cmds | F34 | Dst host same srv rate |
| F7 | Land | F21 | Is host login | F35 | Dst host diff srv rate |
| F8 | Wrong fragment | F22 | Is guest login | F36 | Dst host same src port rate |
| F9 | Urgent | F23 | Count | F37 | Dst host srv diff host rate |
| F10 | Hot | F24 | Srv count | F38 | Dst host serror rate |
| F11 | Number failed logins | F25 | Serror rate | F39 | Dst host srv serror rate |
| F12 | Logged in | F26 | Srv serror rate | F40 | Dst host rerror rate |
| F13 | Num compromised | F27 | Rerror rate | F41 | Dst host srv rerror rate |
| F14 | Root shell | F28 | Srv rerror rate | F42 | Class label |
| Methodology | Classifier 1 | Classifier 2 | Classifier 3 |
|---|---|---|---|
| Hard voting | CNN | GRU | LSTM |
| Soft voting | CNN | GRU | LSTM |
| Deep Learning Algorithms | |||||
|---|---|---|---|---|---|
| Dataset | CNN | GRU | LSTM | Hard Voting Ensemble | Soft Voting Ensemble |
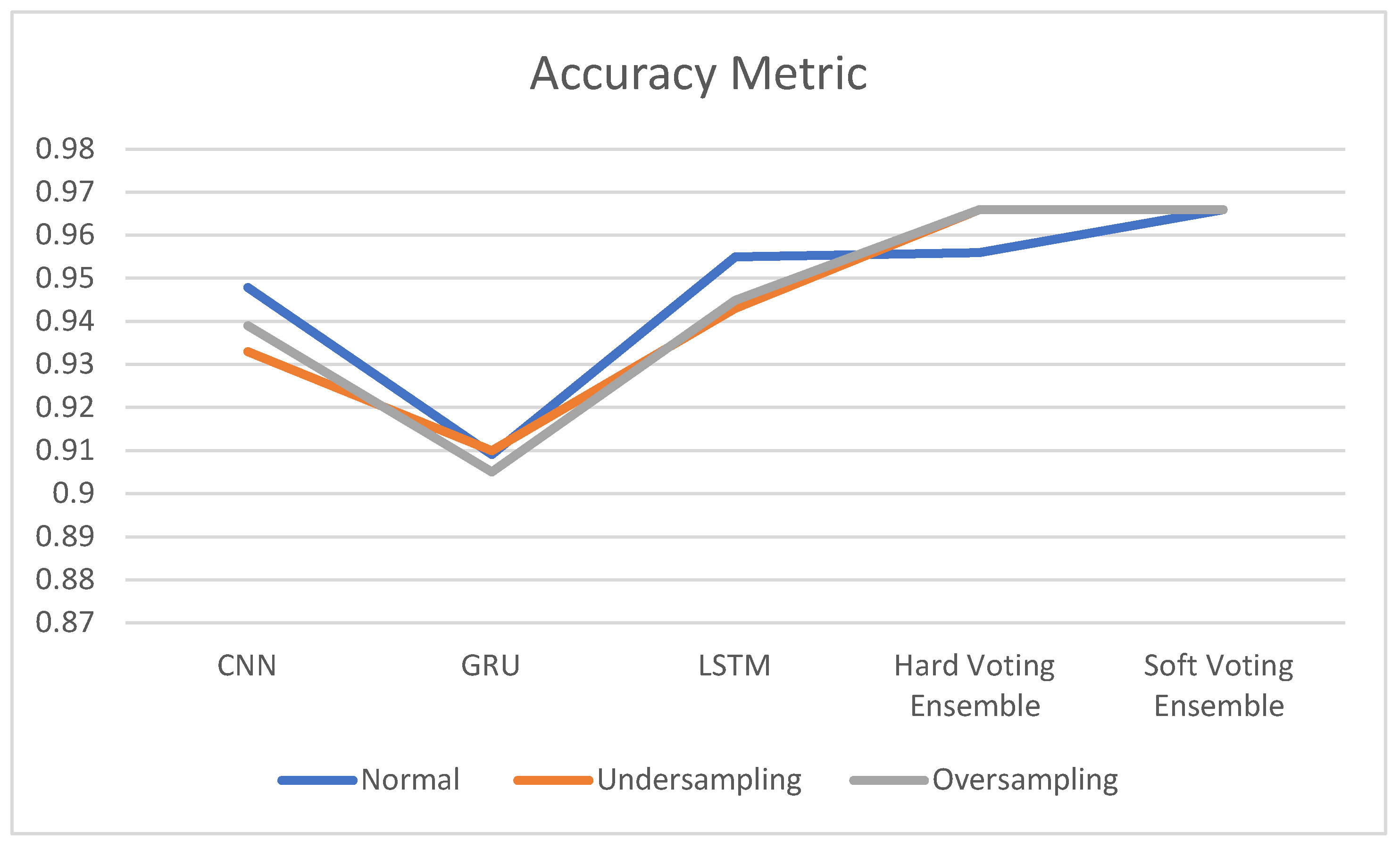
| Normal | 0.947867 | 0.909091 | 0.95498 | 0.956 | 0.966 |
| Under Sampling | 0.933 | 0.91 | 0.943 | 0.966 | 0.966 |
| Oversampling | 0.939 | 0.905 | 0.945 | 0.966 | 0.966 |
| Accuracy | Precision | Recall | F1-Score | |
|---|---|---|---|---|
| CNN → LSTM | 0.99734 | 0.997009 | 0.999001 | 0.998004 |
| CNN → GRU | 0.996016 | 0.995025 | 0.999001 | 0.997009 |
| CNN | 0.947867 | 0.970874 | 0.769231 | 0.858369 |
| GRU | 0.909091 | 0.909091 | 0.952381 | 0.930233 |
| LSTM | 0.95498 | 0.985222 | 0.869565 | 0.923788 |
| Study | Techniques Used | Accuracy Range |
|---|---|---|
| [44,45] | MLP | 85.2~87.8% |
| [48] | Dense random neural network | 88.3% |
| [49] | RNN | 89.5% |
| [50] | APSO-CNN | 88.7 |
| [52,53,54] | CNN | 90.5 |
| [55] | ANN | 92.5% |
| [57] | MLP | 87.6% |
| [58] | RNN | 88.1~90.3% |
| [59] | LSTM | 88.7% |
| [60] | LSTM | 89.4% |
| [62] | LSTM | 89~93% |
| [63] | Random forest | 84.5% |
| [66] | CNN and random forest | 97% |
| [70] | LSTM | 93% |
| Proposed model 1 | CNN → LSTM | 99.7% |
| Proposed model 2 | CNN → GRU | 99.6% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Odeh, A.; Abu Taleb, A. Ensemble-Based Deep Learning Models for Enhancing IoT Intrusion Detection. Appl. Sci. 2023, 13, 11985. https://doi.org/10.3390/app132111985
Odeh A, Abu Taleb A. Ensemble-Based Deep Learning Models for Enhancing IoT Intrusion Detection. Applied Sciences. 2023; 13(21):11985. https://doi.org/10.3390/app132111985
Chicago/Turabian StyleOdeh, Ammar, and Anas Abu Taleb. 2023. "Ensemble-Based Deep Learning Models for Enhancing IoT Intrusion Detection" Applied Sciences 13, no. 21: 11985. https://doi.org/10.3390/app132111985
APA StyleOdeh, A., & Abu Taleb, A. (2023). Ensemble-Based Deep Learning Models for Enhancing IoT Intrusion Detection. Applied Sciences, 13(21), 11985. https://doi.org/10.3390/app132111985








