The Development of a Secure Internet Protocol (IP) Network Based on Asterisk Private Branch Exchange (PBX)
Abstract
1. Introduction
- A single network infrastructure, which Asterisk has, allows a wider range of services to be received both for office maintenance and business services, reducing the cost of technical staff;
- In traditional PBXs, the maximum message recording configuration is limited to 32 h of recording, whereas in Asterisk, the number of voice messages can be limited by the administrator and depends on the capacity of the hard disk;
- Asterisk has a powerful ability to create an interactive voice menu;
- Asterisk has a wide forwarding functionality, which includes forwarding by time of day, presence at the workplace, simultaneous forwarding to several phones, individual forwarding algorithm, etc.;
- Fax reception is carried out to all numbers with automatic sending to e-mail;
- Asterisk runs on operation system Linux, and it is possible to combine the functions of a mini-PBX and an Internet server. For example, when using an E1 channel, the data part and the voice part can be separated. Thus, through the same channel, both voice services and access to the Internet and other services from the same provider can be received [22,23,24].
2. Methodologies
3. Results and Discussion
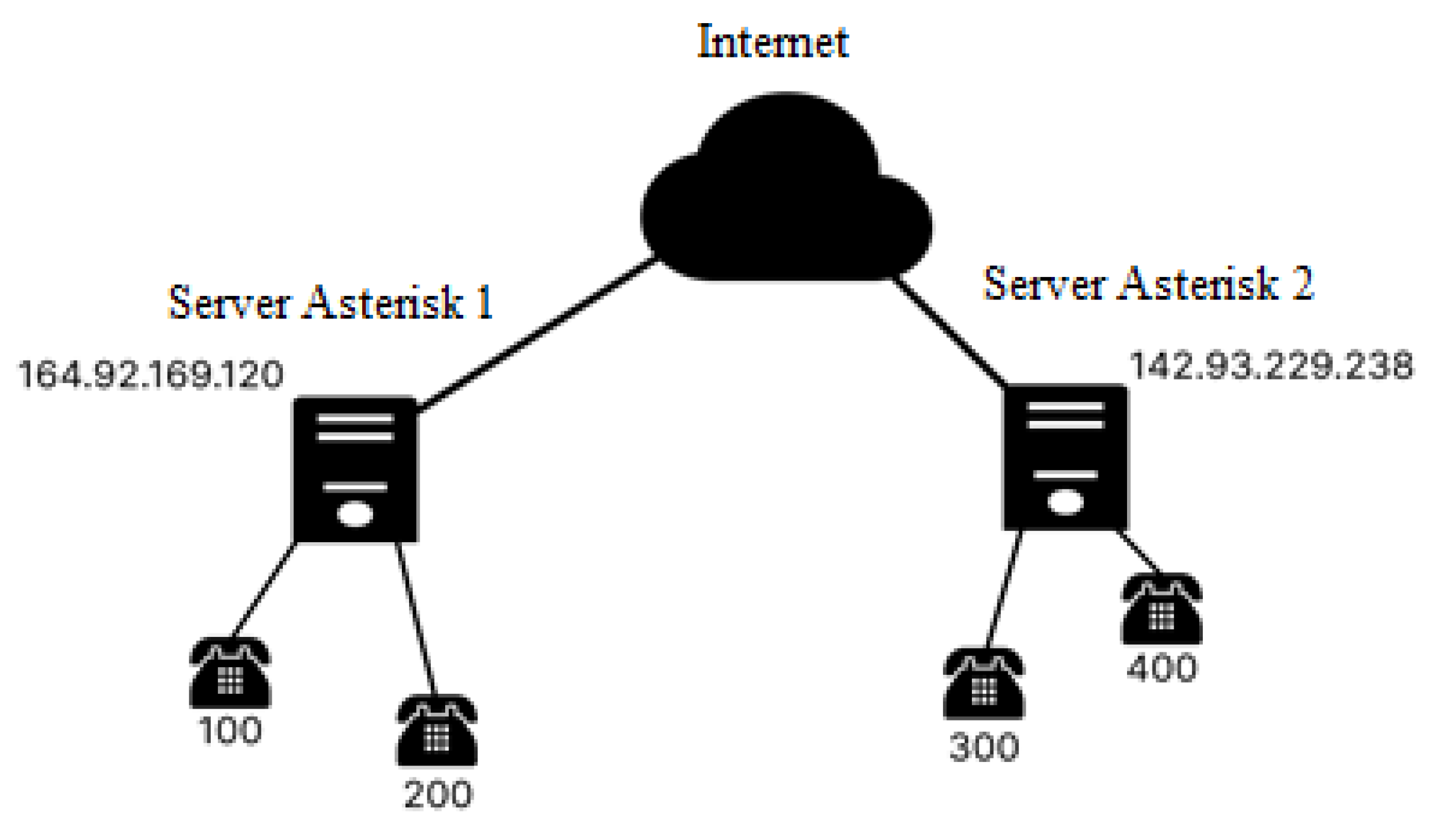
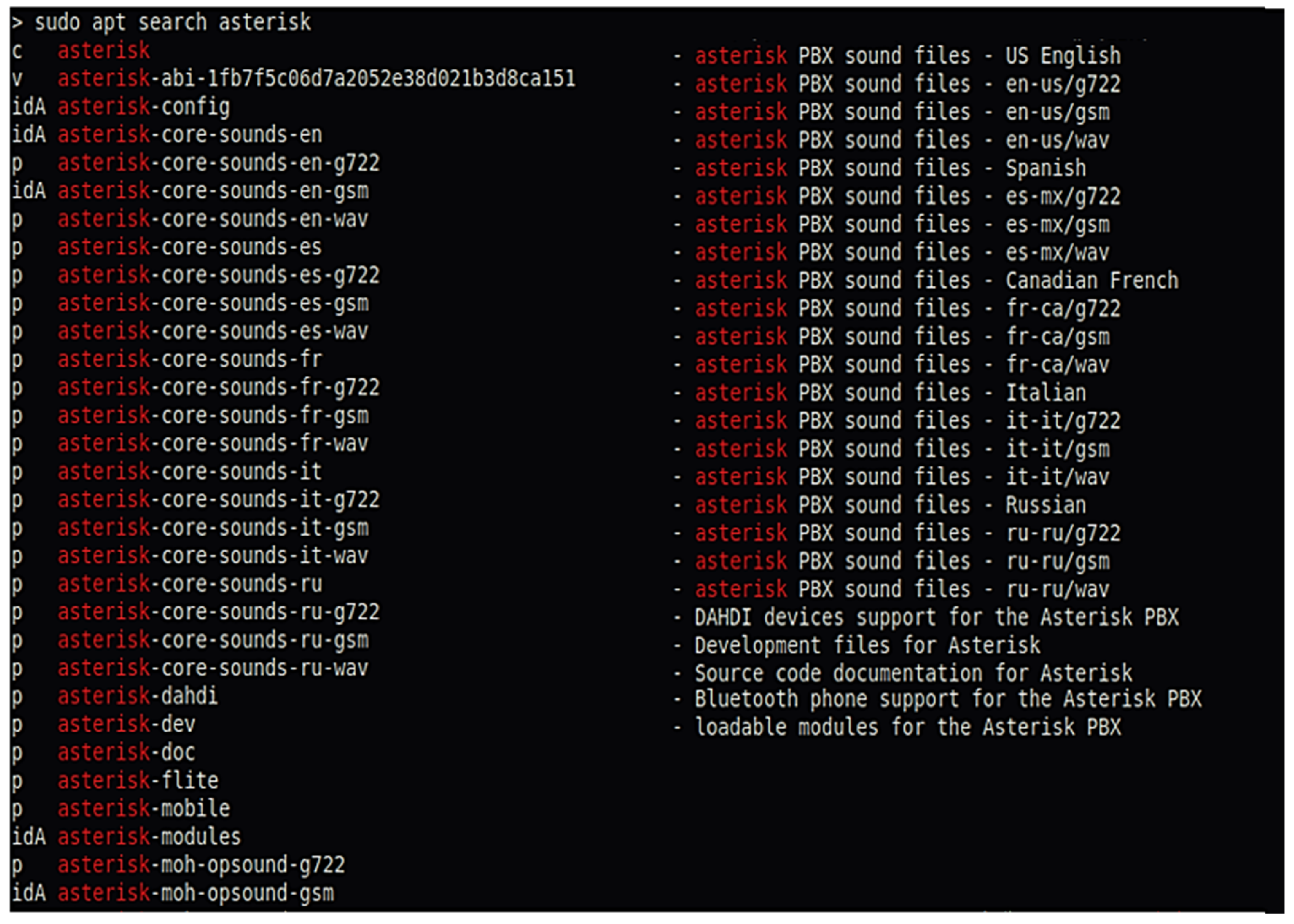
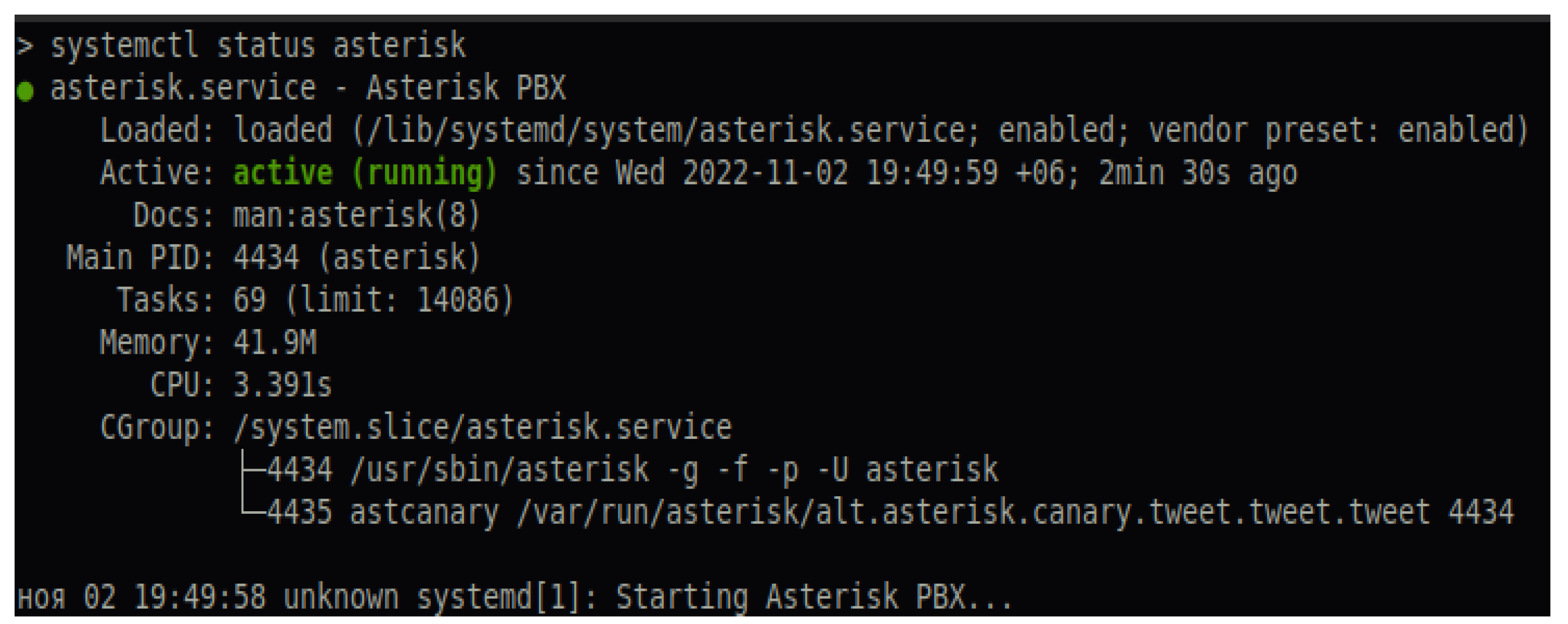
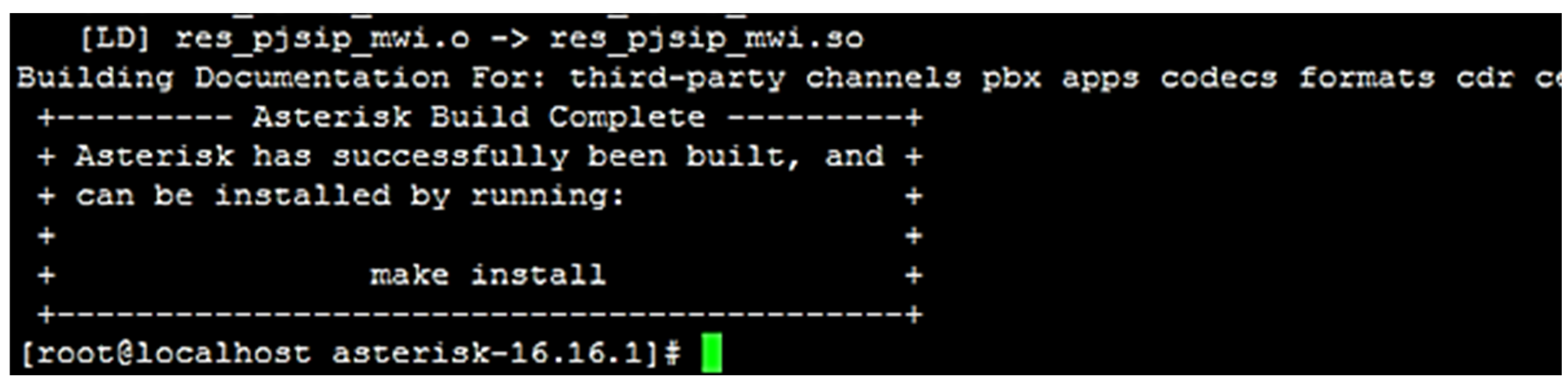
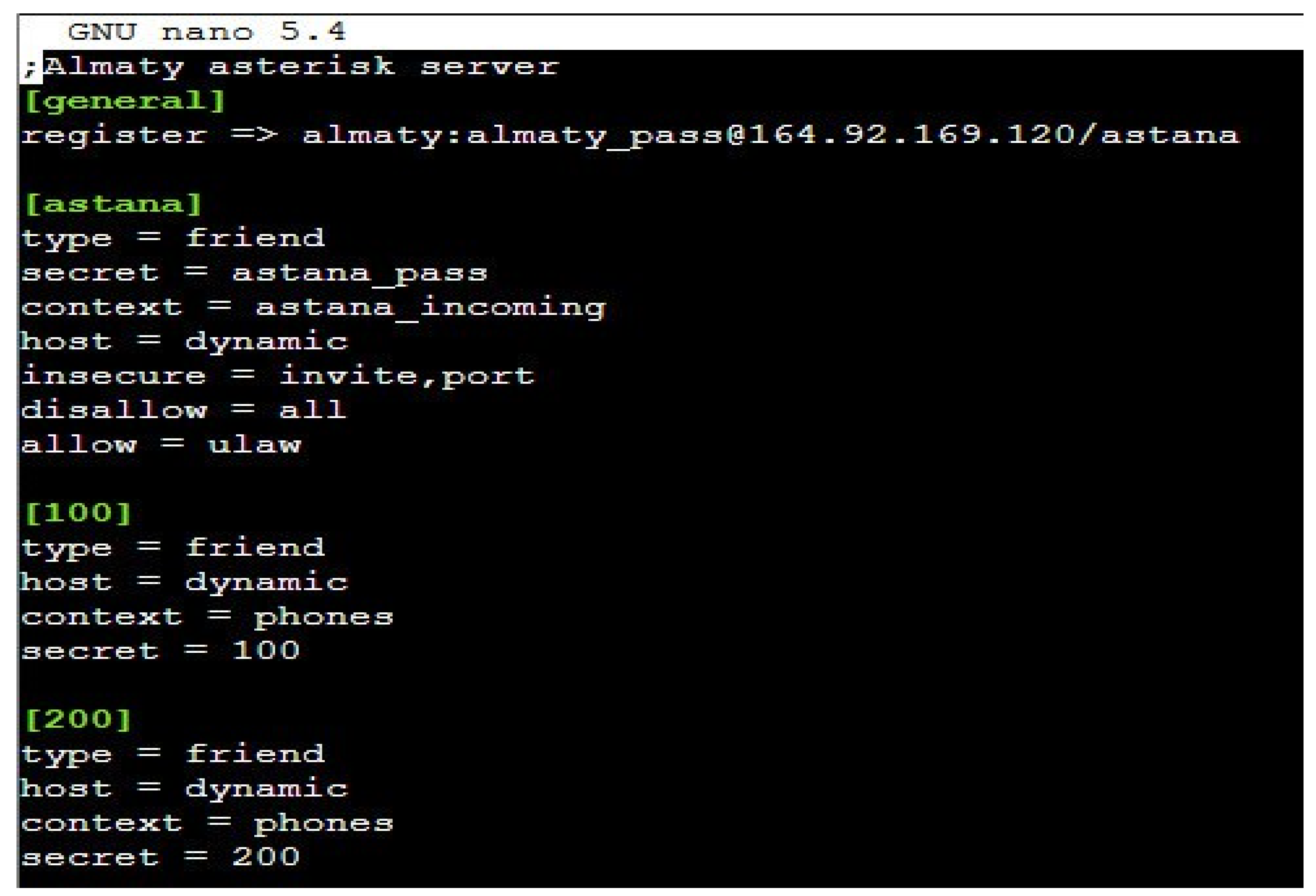
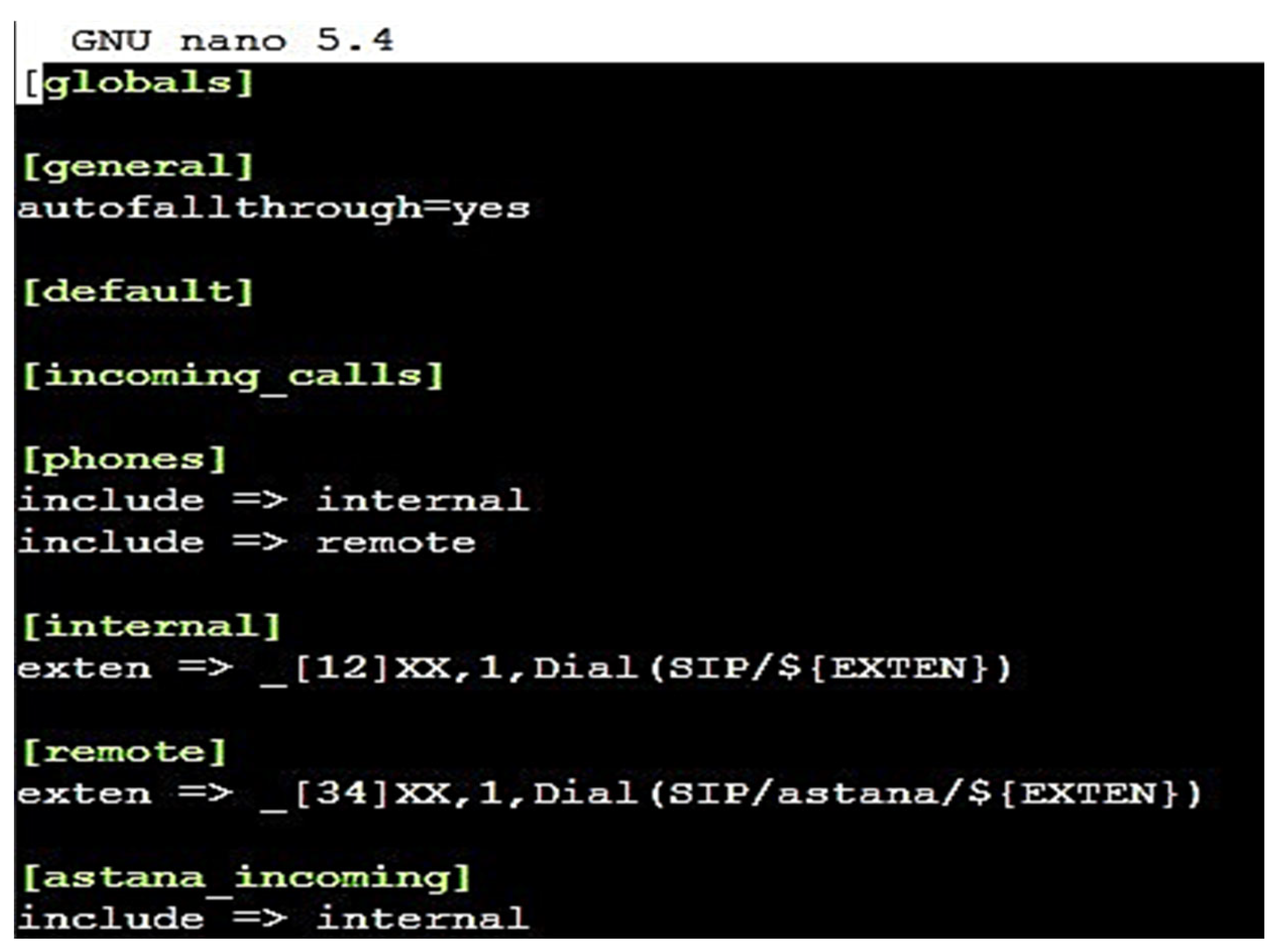
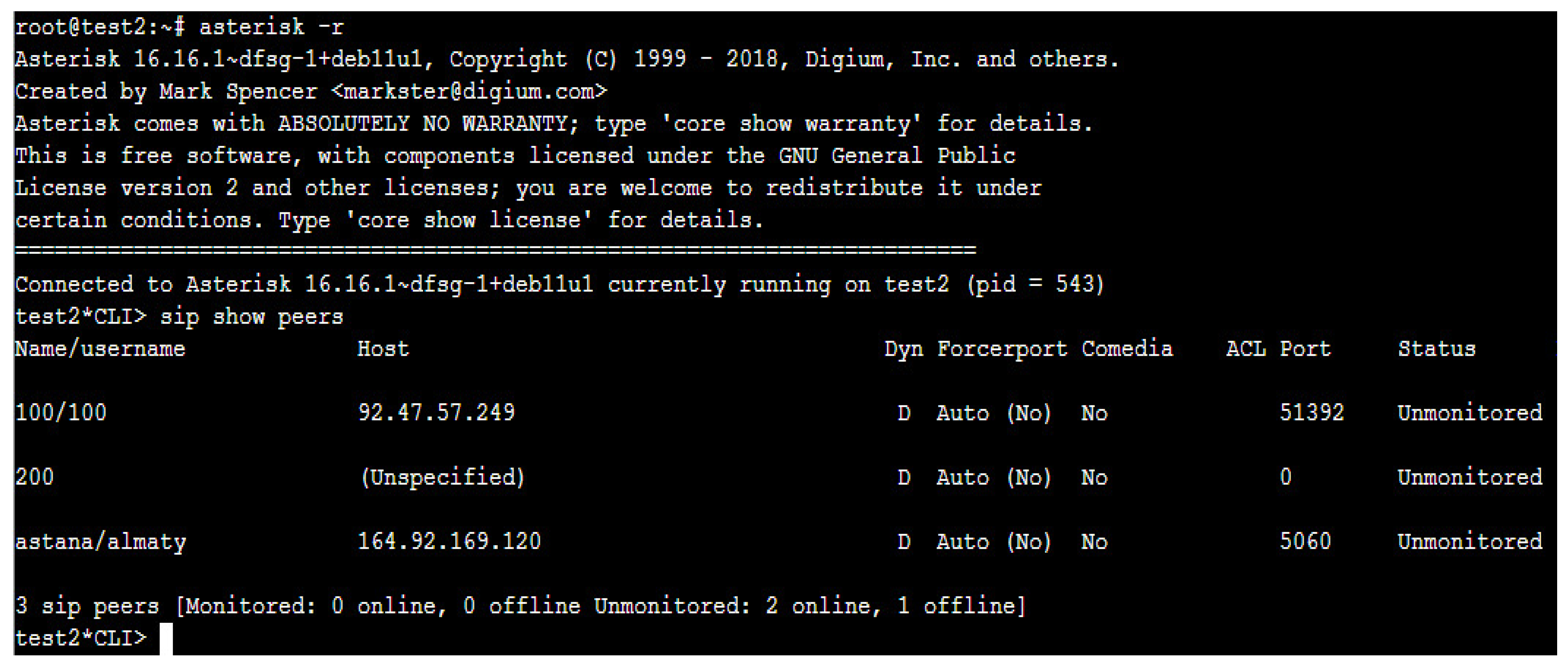
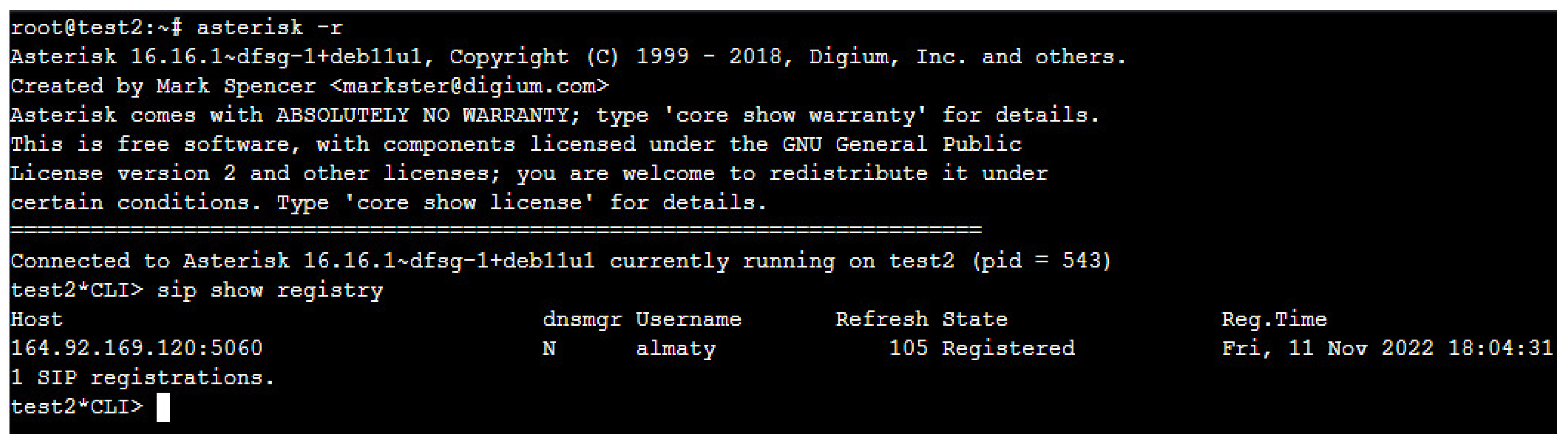
3.1. Development in the Configuration of a Real IP Network Based on Asterisk PBX
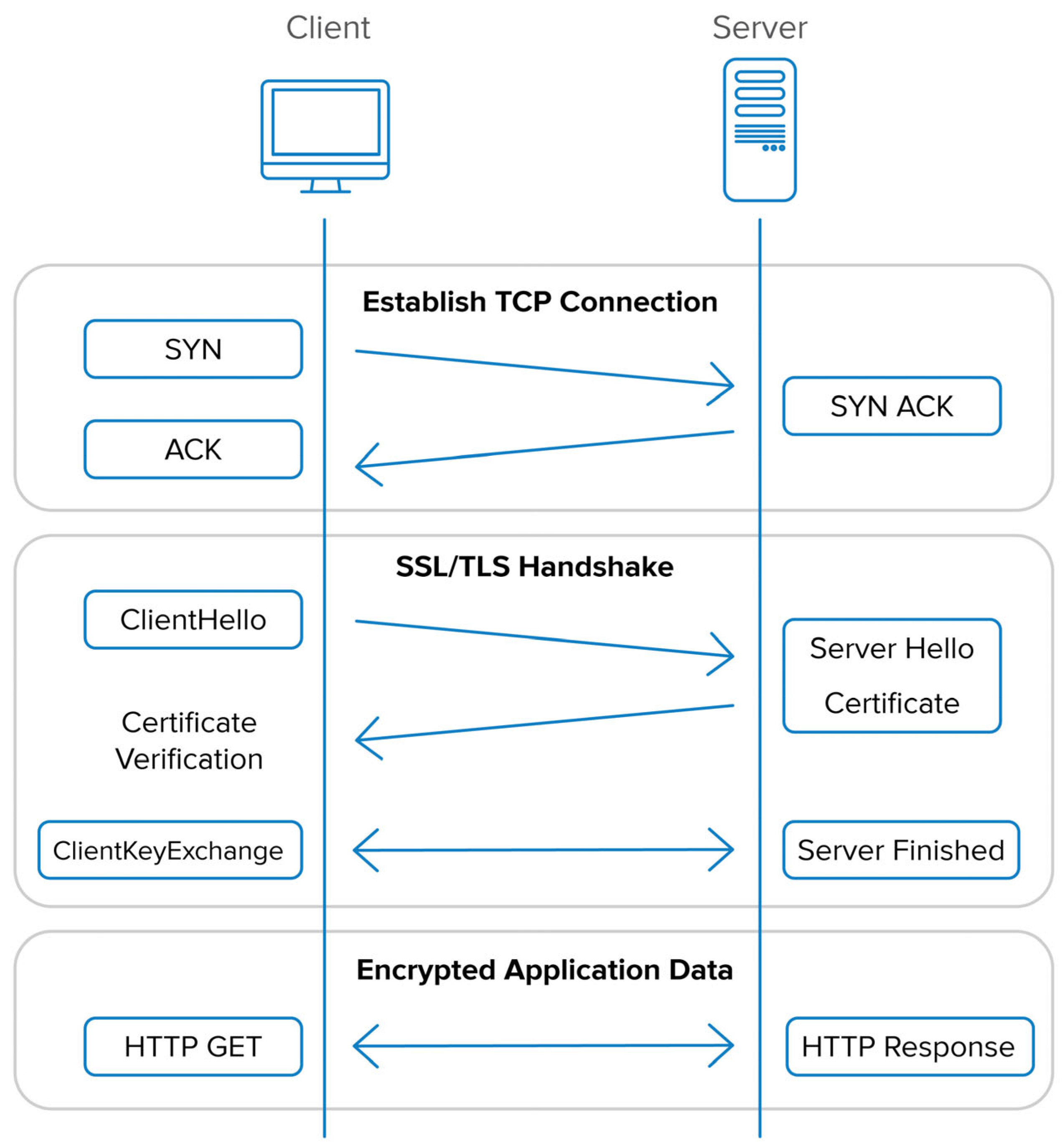
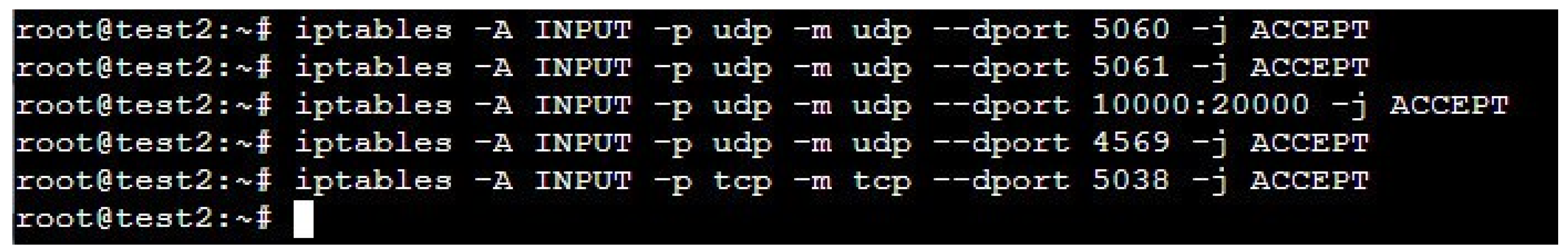
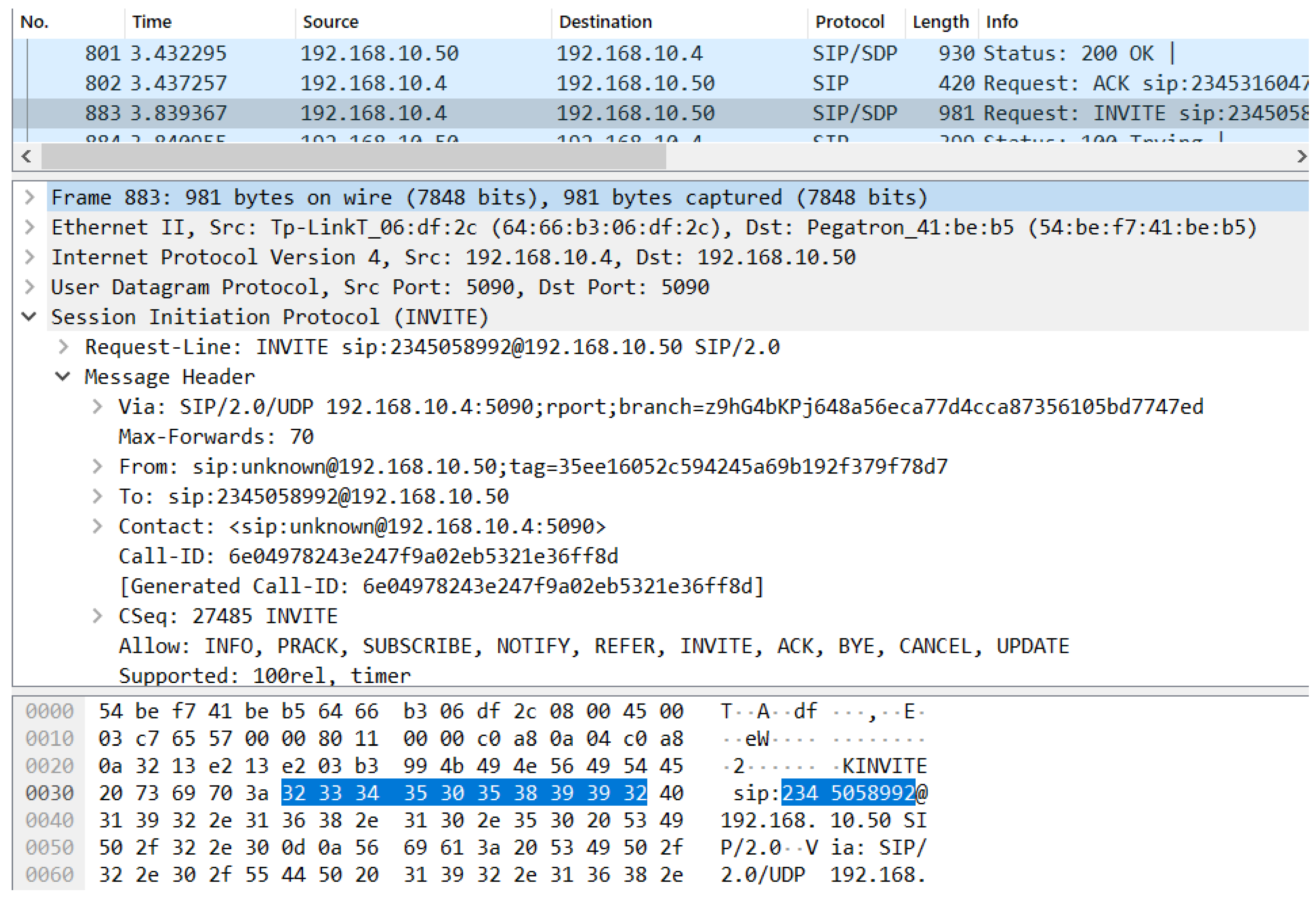
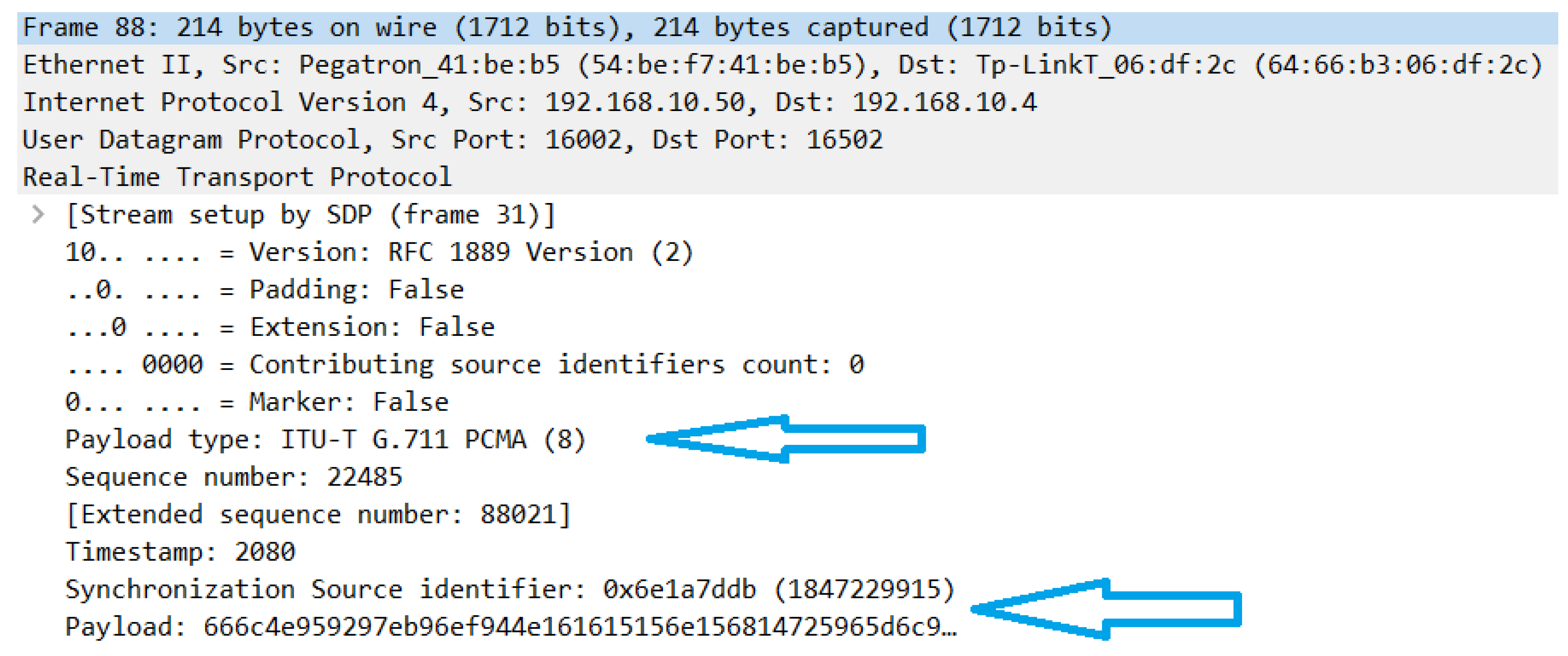
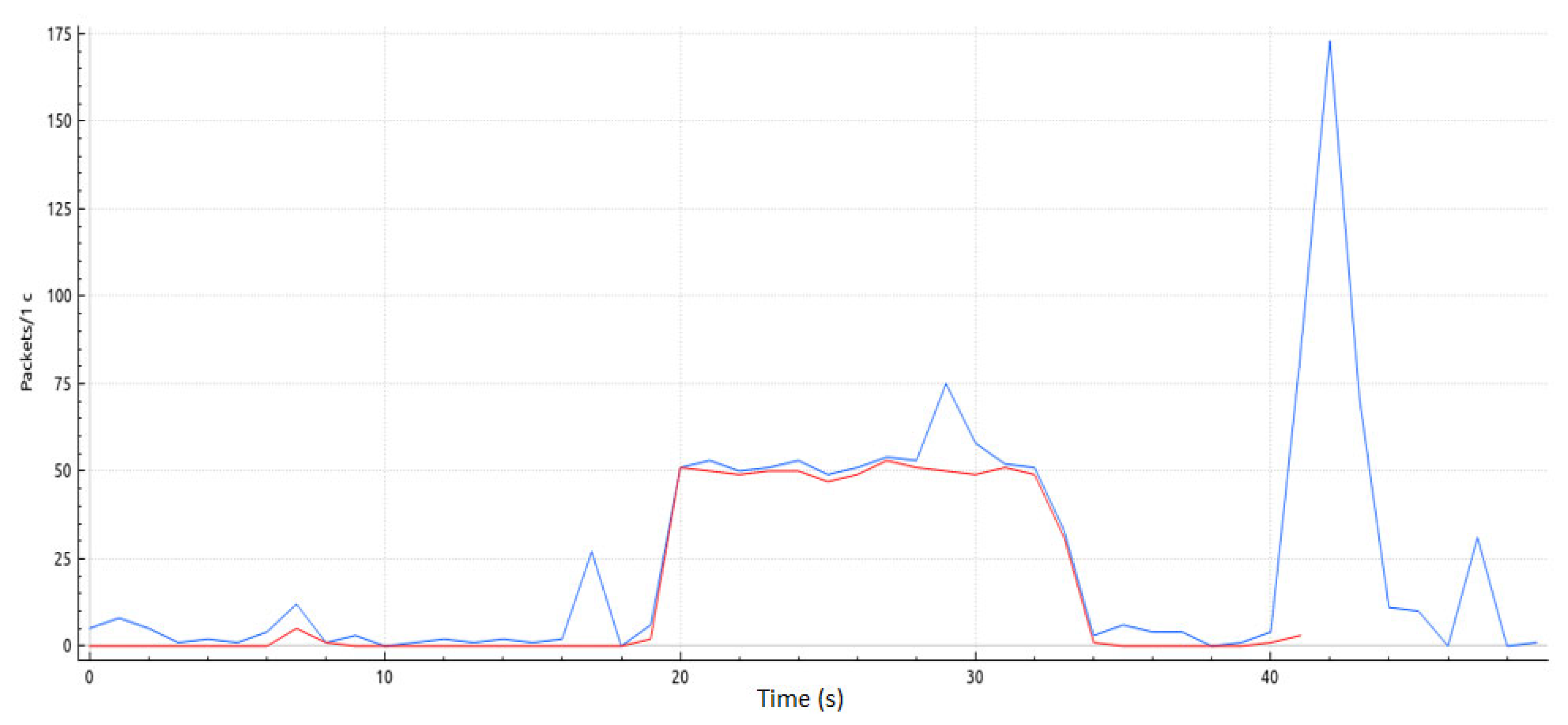
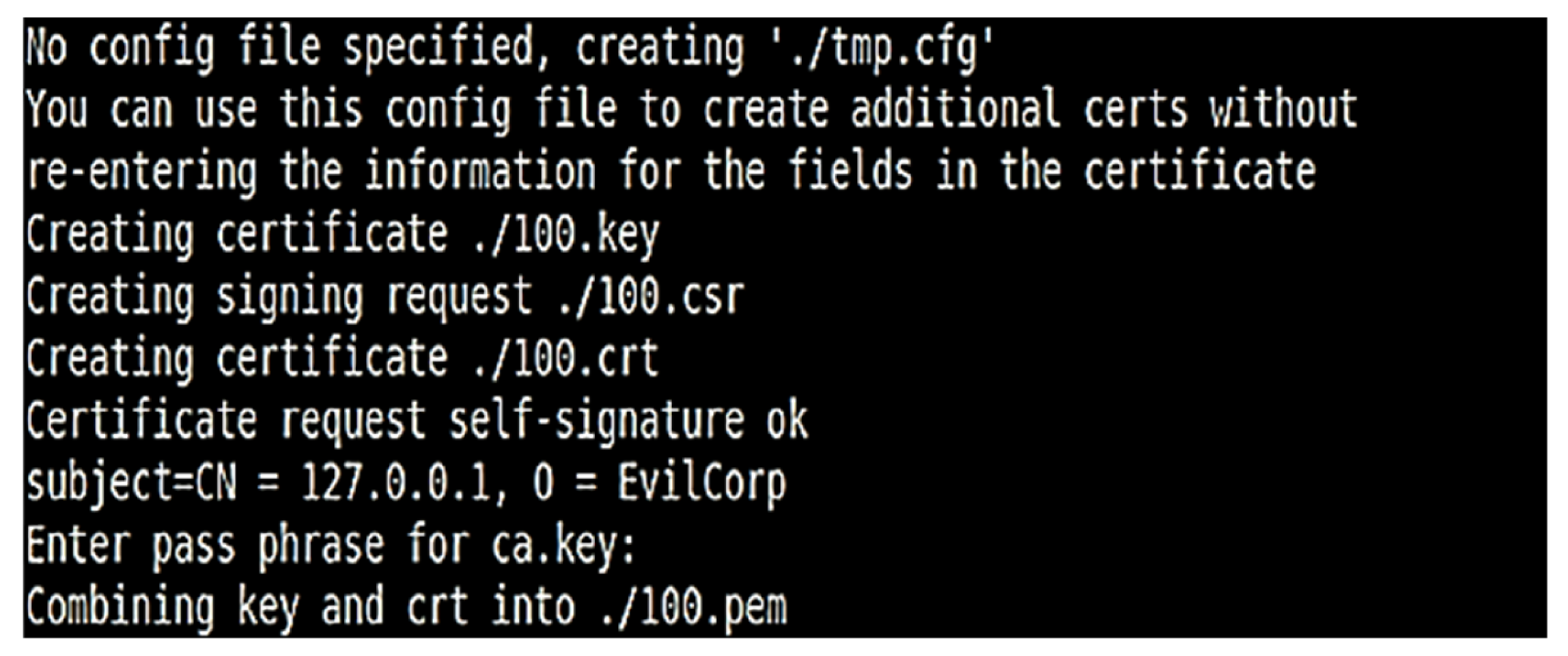
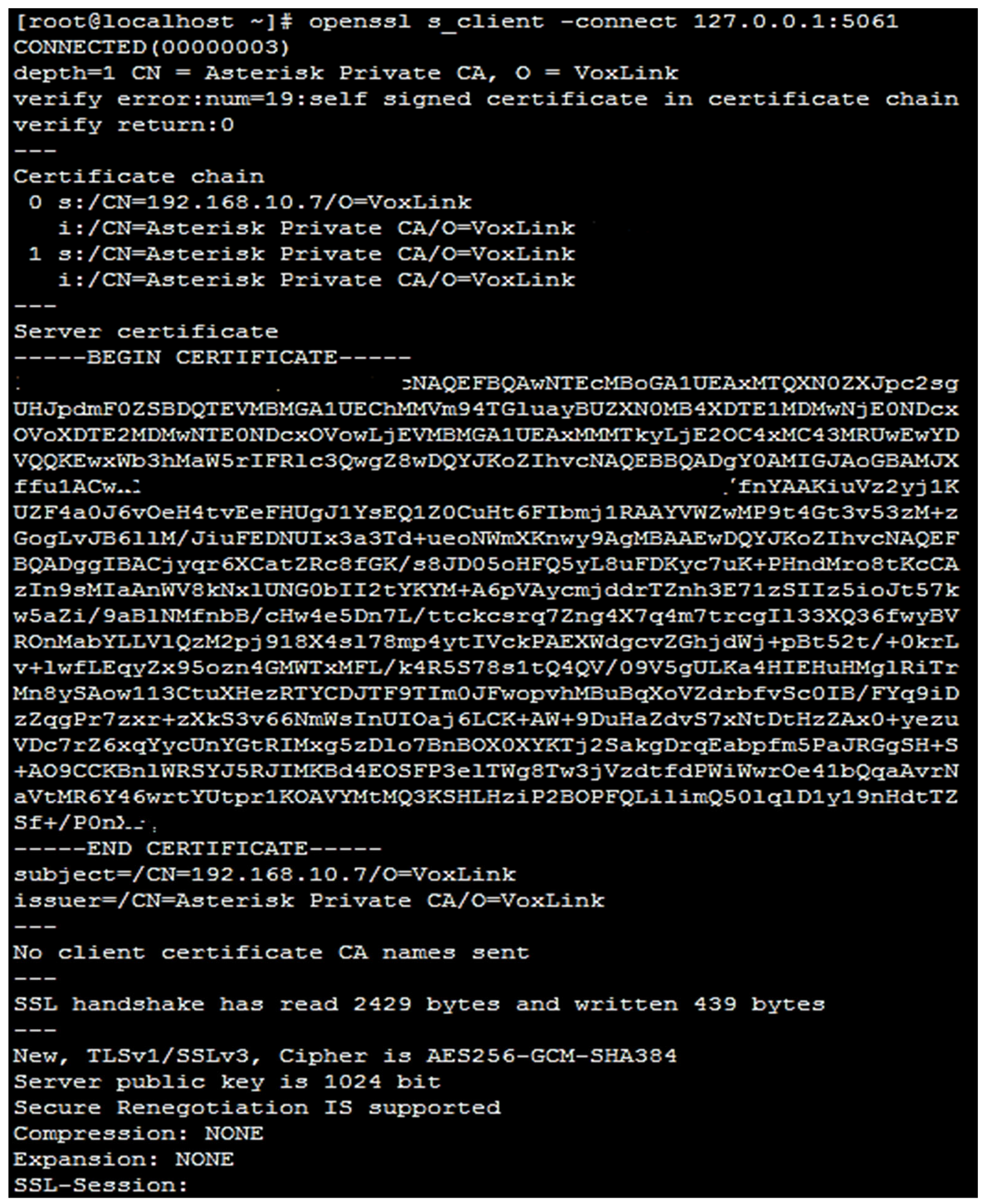
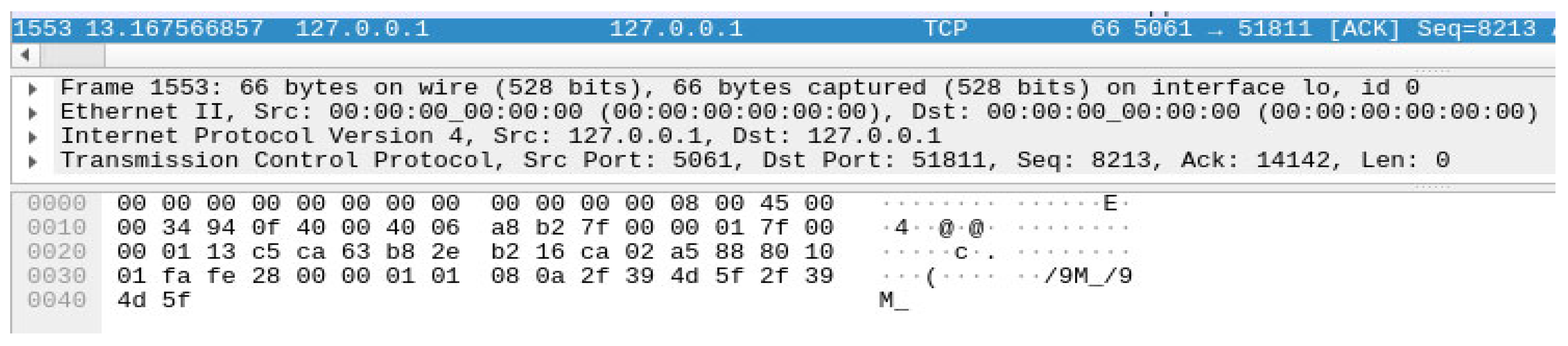
3.2. Development of a Real Network Encryption Method Based on the TLS Protocol
- Authentication and authorization: in our case, users are configured with an access password, so that only authorized users have access to the PBX system and its functions.
- Encryption: it uses the secure SIP protocol setting over TLS to secure communication between devices.
- Firewall: the implementation of a firewall blocks unauthorized access to the PBX system.
- Network segmentation: the segmentation of the PBX network from other networks minimizes the attack surface.
4. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Danylchenko, V.M.; Mykolaychuk, V.R.; Tkalenko, O.M.; Didkivskyy, A.S. Initial setup of PBX server based on Asterisk. Connectivity 2020, 148. [Google Scholar] [CrossRef]
- Kumar, S.S.; Dhivyalekshmi, B.; Preethi, S.; Rengaraju, P. PBX implementation in LAN using Asterisk open source software. Int. J. Appl. Eng. Res. 2015, 10, 66–69. [Google Scholar]
- Khan, B.M.; Fahad, M.; Bilal, R.; Khan, A.H. Performance Analysis of Raspberry Pi 3 IP PBX Based on Asterisk. Electronics 2022, 11, 3313. [Google Scholar] [CrossRef]
- Al-Saadoon, G.M.W. Asterisk Open Source to Implement Voice over Internet Protocol. Int. J. Comput. Sci. Netw. Secur. 2009, 9, 39. [Google Scholar]
- Rahman, M.M.; Islam, N.S. VoIP Implementation Using Asterisk PBX. J. Bus. Manag. 2014, 15, 47–53. [Google Scholar]
- Chinna Rao, R.; Lakshmi, K.; Raja, C.; Varma, P.; Rao, G.R.K.; Patibandla, A. Real-Time Implementation and Testing of VoIP Vocoders with Asterisk PBX Using Wireshark Packet Analyzer. J. Intercon. Netw. 2022, 22, 2141030. [Google Scholar] [CrossRef]
- Nuno, P.; Suarez, C.; Suarez, E.; Bulnes, F.G.; Calle, F.J.; Granda, J.C. A Diagnosis and Hardening Platform for an Asterisk VoIP PBX. Secur. Commun. Netw. 2020, 2020, 8853625. [Google Scholar] [CrossRef]
- Martin, A.; Gamess, E.; Urribarri, D.; Gomez, J. A proposal for a high availability architecture for VoIP telephone systems based on open source software. Int. J. Adv. Comput. Sci. Appl. 2018, 9, 1–11. [Google Scholar] [CrossRef]
- Maar, M.; Sitarova, J.; Orgon, M. Enterprise network with software Asterisk PBX based on the PLC technology. Int. J. Adv. Telecommun. Electrotech. Sig. Syst. 2017, 6, 1–10. [Google Scholar] [CrossRef][Green Version]
- Yessenbayev, Z.; Saparkhojayev, N.; Tibeyev, T. Implementation of the Intelligent Voice System for Kazakh. J. Phys. Conf. Ser. 2014, 495, 012043. [Google Scholar] [CrossRef]
- Saenger, J.; Mazurczyk, W.; Keller, J.; Caviglione, L. VoIP network covert channels to enhance privacy and information sharing. Fut. Gener. Compu. Syst. 2020, 111, 96–106. [Google Scholar] [CrossRef]
- Zhang, L.; Hu, X.; Rasheed, W.; Huang, T.; Zhao, C. An Enhanced Steganographic Code and Its Application in Voice-Over-IP Steganography. IEEE Access 2019, 7, 97187–97195. [Google Scholar] [CrossRef]
- Lomotey, R.K.; Deters, R. Intrusion Prevention in Asterisk-Based Telephony System. In Proceedings of the 2014 IEEE International Conference on Mobile Services, Anchorage, AK, USA, 27 June–2 July 2014; pp. 116–123. [Google Scholar] [CrossRef]
- Khan, N.A.; Chan, A.S.; Saleem, K.; Bhutto, Z.; Ayaze, H. VoIP QoS analysis over asterisk and Axon servers in LAN environment. Int. J. Adv. Comput. Sci. Appl. 2019, 10, 548–554. [Google Scholar] [CrossRef]
- Kim, W.; Song, T.; Kim, T.; Park, H.; Pack, S. VoIP Capacity Analysis in Full Duplex WLANs. IEEE Transact. Vehicular Technol. 2017, 66, 11419–11424. [Google Scholar] [CrossRef]
- Sanchez-Iborra, R.; Cano, M.-D.; Garcia-Haro, J. Performance Evaluation of BATMAN Routing Protocol for VoIP Services: A QoE Perspective. IEEE Transact. Wirel. Commun. 2014, 13, 4947–4958. [Google Scholar] [CrossRef]
- Ali, S.R. Reliability Analysis of VoIP System. In Next Generation and Advanced Network Reliability Analysis: Using Markov Models and Software Reliability Engineering; Springer: Berlin/Heidelberg, Germany, 2018; pp. 211–244. [Google Scholar] [CrossRef]
- Yeh, W.C. Search for MC in modified networks. Comput. Operat. Res. 2001, 28, 177–184. [Google Scholar] [CrossRef]
- Pal, D.; Triyason, T.; Vanijja, V. Asterisk server performance under stress test. In Proceedings of the IEEE 17th International Conference on Communication Technology (ICCT), Chengdu, China, 27–30 October 2017; pp. 1967–1971. [Google Scholar] [CrossRef]
- Costa, L.R.; Nunes, L.S.N.; Bordim, J.L.; Nakan, K. Asterisk PBX Capacity Evaluation. In Proceedings of the IEEE International Parallel and Distributed Processing Symposium Workshop, Hyderabad, India, 25–29 May 2015; pp. 519–524. [Google Scholar] [CrossRef]
- Rughinis, R.V.; Iconaru, C. A Practical Analysis of Asterisk SIP Server Performance. In Proceedings of the 7th RoEduNet Internaional Conference, Cluj-Napoca, Romania, 28–30 August 2008; pp. 61–64. [Google Scholar]
- Muntaka, S.A.; Hussein, F.; Sarfo, P. Implementation of an IP Telephony System Based on Asterisk PBX. Int. J. Comput. Appl. 2019, 177, 8887. [Google Scholar] [CrossRef]
- Murkute, P.V.; Deshmukh, V.M. Implementing the VOIP Communication Principles Using Raspberry Pi as Server. Int. J. Comput. Appl. 2015, 124, 34–38. [Google Scholar] [CrossRef]
- Karapantazis, S.; Pavlidou, F.-N. VoIP: A comprehensive survey on a promising technology. Comput. Netw. 2009, 53, 2050–2090. [Google Scholar] [CrossRef]
- Konshin, S.V.; Yakubova, M.Z.; Nishanbayev, T.N.; Manankova, O.A. Research and development of an IP network model based on PBX asterisk on the opnet mod eler simulation package. In Proceedings of the International Conference on Information Science and Communications Technologies, ICISCT 2020, Tashkent, Uzbekistan, 4–6 November 2020. [Google Scholar] [CrossRef]
- Voznak, M.; Rezac, F. Threats to Voice over IP communications systems. WSEAS Transact. Comput. 2010, 9, 1348–1358. [Google Scholar]
- Ganesan, V.; Msk, M. A scalable detection and prevention scheme for voice over internet protocol (VoIP) signaling attacks using handler with Bloom filter. Int. J. Netw. Manag. 2018, 28, e1995. [Google Scholar] [CrossRef]
- Rehman, U.U.; Abbasi, A.G. Secure layered architecture for Session Initiation Protocol based on SIPSSO: Formally proved by Scyther. In Proceedings of the 12th International Conference on Information Technology—New Generations (ITNG 2015), Las Vegas, NV, USA, 13–15 April 2015; pp. 185–190. [Google Scholar] [CrossRef]
- Jung, S. CAPTCHA-based DDoS defense system of call centers against zombie smart-phone. Int. J. Secur. Appl. 2012, 6, 29–36. [Google Scholar]
- Barison, D.; Miani, R.S.; De Souza Mendes, L. Evaluation of quality and security of a VoIP network based on asterisk and Open VPN. In Proceedings of the International Conference on Security and Cryptography 2009, Milan, Italy, 7–10 July 2009; pp. 144–147. [Google Scholar] [CrossRef]
- Abualhaj, M.M.; Al-Tahrawi, M.M.; Al-Khatib, S.N. Performance evaluation of VoIP systems in cloud computing. J. Eng. Sci. Technol. 2019, 14, 1398–1405. [Google Scholar]
- Wu, H.; Zhu, C.; Cheng, G. Real-Time Application Identification of RTC Media Streams via Encrypted Traffic Analysis. In Proceedings of the International Conference on Computer Communications and Networks (ICCCN 2022), Honolulu, HI, USA, 25–28 July 2022. [Google Scholar] [CrossRef]
- Shen, C.; Nahum, E.; Schulzrinne, H. The impact of TLS on SIP server performance. In Proceedings of the IPTComm 2010—Principles, Systems and Applications of IP Telecommunications 2010, Munich, Germany, 2–3 August 2010. [Google Scholar] [CrossRef]
- Bhujangaa Rao, S.; Apoorva, C. Implementation of RFC 5359 SIP (VoIP) services on asterisk PBX. Int. J. Innov. Technol. Expl. Eng. 2019, 8, 15–21. [Google Scholar]
- Kulin, M.; Kazaz, T.; Mrdovic, S. SIP server security with TLS: Relative performance evaluation. In Proceedings of the 9th International Symposium on Telecommunications, BIHTEL 2012—Proceedings, Sarajevo, Bosnia and Herzegovina, 25–27 October 2012; pp. 1–6. [Google Scholar] [CrossRef]
- Lara-Cueva, R.A.; Pazmino, S.; Acosta, F. Performance evaluation of an Asterisk PBX prototype Beaglebone Black based. In Proceedings of the 17th Iberian Conference on Information Systems and Technologies—CISTI 2022, Madrid, Spain, 22–25 June 2022. [Google Scholar] [CrossRef]
- Asif, K.; Eshtiak, A.; Sami, A.; Bharanidharana, S.; Pronab, G. Mitigating the Latency Induced Delay in IP Telephony through an Enhanced De-Jitter Buffer. In Mobile Computing and Sustainable Informatics; Springer: Singapore, 2022; pp. 1–16. [Google Scholar] [CrossRef]
- Manankova, O.A.; Yakubov, B.M.; Serikov, T.G.; Yakubova, M.Z.; Mukasheva, A.K. Analysis and research of the security of a wireless telecommunications network based on the IP PBX Asterisk in an Opnet environment. J. Theoret. Appl. Inform. Technol. 2021, 99, 3617–3630. [Google Scholar]
- Serikov, T.G.; Yakubova, M.Z.; Mekhtiev, A.D.; Yugay, V.V.; Muratova, A.K.; Razinkin, V.P.; Okhorzina, A.V.; Yurchenko, A.V.; Alkina, A.D. The analysis and modeling of efficiency of the developed telecommunication networks on the basis of IP PBX asterisk now. In Proceedings of the 11th International Forum on Strategic Technology, IFOST 2016, Novosibirsk, Russia, 1–3 June 2016; pp. 510–515. [Google Scholar] [CrossRef]
- Zhang, Z.; De Luca, G.; Archambault, B.; Chavez, J.; Rice, B. Traffic Dataset and Dynamic Routing Algorithm in Traffic Simulation. J. Artif. Intell. Technol. 2022, 2, 111–122. [Google Scholar] [CrossRef]
- Samanta, R.K.; Sadhukhan, B.; Samaddar, H.; Sarkar, S.; Koner, C.; Ghosh, M. Scope of machine learning applications for addressing the challenges in next-generation wireless networks. CAAI Trans. Intell. Technol. 2022, 7, 395–418. [Google Scholar] [CrossRef]
- Montazerolghaemm, A. Softwarization and virtualization of VoIP networks. J. Supercomput. 2022, 78, 14471–14503. [Google Scholar] [CrossRef]
- Dong, F.; Deng, B.; Yu, H.; Xie, W.; Xu, H.; Gu, Z. An Asterisk-shaped Patch Attack for Object Detection. In Proceedings of the 7th IEEE International Conference on Data Science in Cyberspace, DSC 2022, Guilin, China, 11–13 July 2022; pp. 126–133. [Google Scholar] [CrossRef]
- Surasak, T.; Scott, H.C.-H. Enhancing VoIP Security and Efficiency Using VPN. In Proceedings of the International Conference on Computing, Networking and Communications, ICNC 2019, Honolulu, HI, USA, 18–21 February 2019; pp. 180–184. [Google Scholar] [CrossRef]
- Hooshmand, M.K.; Doreswamy, H. Network anomaly detection using deep learning techniques. CAAI Trans. Intell. Technol. 2022, 7, 228–243. [Google Scholar] [CrossRef]
- Romanets, I.; Sachenko, A.; Dubchak, L. Method of Protection against Traffic Termination in VoIP. In Proceedings of the 10th International Conference on Electronics, Computers and Artificial Intelligence, ECAI 2018, Iasi, Romania, 28–30 June 2018. [Google Scholar] [CrossRef]
- Jama, A.M.; Khalifa, O.; Subramaniam, O.; Kumar, N. Novel Approach for IP-PBX Denial of Service Intrusion Detection Using Support Vector Machine Algorithm. Int. J. Commun. Netw. Inf. Secur. 2021, 13, 249–257. [Google Scholar] [CrossRef]
- Wang, S.; Tang, W.; Liu, C.; Li, B.; Tang, M.; Wen, M. Digital Image Correlation Measurement of the Deformation and Failure in PBX Brazilian Discs Reinforced with CFRP Patches. Propellants Explosives Pyrotechnics 2021, 46, 548–554. [Google Scholar] [CrossRef]
- McInnes, N.; Wills, G. The VoIP PBX Honeypot Advance Persistent Threat Analysis. In Proceedings of the International Conference on Internet of Things, Big Data and Security, IoTBDS—2021, Online Streaming, 23–25 April 2021; pp. 70–80. [Google Scholar] [CrossRef]




Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yakubova, M.; Manankova, O.; Mukasheva, A.; Baikenov, A.; Serikov, T. The Development of a Secure Internet Protocol (IP) Network Based on Asterisk Private Branch Exchange (PBX). Appl. Sci. 2023, 13, 10712. https://doi.org/10.3390/app131910712
Yakubova M, Manankova O, Mukasheva A, Baikenov A, Serikov T. The Development of a Secure Internet Protocol (IP) Network Based on Asterisk Private Branch Exchange (PBX). Applied Sciences. 2023; 13(19):10712. https://doi.org/10.3390/app131910712
Chicago/Turabian StyleYakubova, Mubarak, Olga Manankova, Assel Mukasheva, Alimzhan Baikenov, and Tansaule Serikov. 2023. "The Development of a Secure Internet Protocol (IP) Network Based on Asterisk Private Branch Exchange (PBX)" Applied Sciences 13, no. 19: 10712. https://doi.org/10.3390/app131910712
APA StyleYakubova, M., Manankova, O., Mukasheva, A., Baikenov, A., & Serikov, T. (2023). The Development of a Secure Internet Protocol (IP) Network Based on Asterisk Private Branch Exchange (PBX). Applied Sciences, 13(19), 10712. https://doi.org/10.3390/app131910712








