Abstract
The blockchain-based searchable symmetric encryption (SSE) scheme allows the retrieval and verification of outsourced data on cloud servers in sixth generation (6G) networks while ensuring the privacy of data. However, existing schemes are challenging to comprehensively meet the requirements of 6G-based intelligent application systems for low latency, high security, and high reliability. To address these limitations, we present VSSE, a novel blockchain-based SSE scheme designed for 6G-based intelligent application systems. Our scheme constructs a state chain structure to resist file injection attacks, thereby ensuring forward privacy. Moreover, we execute the search and verification operations separately on the cloud server and blockchain, while introducing a bitmap index structure and message authentication code (MAC) technology to achieve efficient searching and dynamic verification. Notably, VSSE also includes access control functionality, permitting only authorized users to access relevant files. The combination of remarkable efficiency and strong security establishes our VSSE as an ideal solution suitable for implementation in G-based intelligent application systems.
1. Introduction
With the widespread adoption of fifth generation (5G) mobile communication technology, cloud computing-based intelligent applications, such as smart logistics, smart medical care, and smart homes, have greatly facilitated the quality of daily life and work. Massive data are collected by the physical device deployed in the intelligent applications, which also stores data in a cloud server and analyzes the data by cloud computing techniques. The breakthrough development of sixth generation (6G) mobile communication technology provides a more reliable and faster computing environment for the intelligent application systems [1]. However, the emergence of 6G communication technology has led to a significant increase in application data, and cloud servers may not always be trusted. Therefore, protecting the privacy of data becomes particularly critical. To protect data privacy in the 6G network, employing traditional encryption methods to encrypt the data helps maintain its privacy [2]. Nevertheless, encrypted data become non-retrievable, resulting in a substantial reduction in data accessibility. On the other hand, searchable encryption (SE) technology successfully achieves the capability of ciphertext retrieval.
Symmetric searchable encryption (SSE) is a ciphertext retrieval technique based on symmetric cryptographic primitives. In general, SSE operates as follows: the data owner encrypts files and constructs an encrypted index for each file, then uploads both to the server. When a data user wants to retrieve the files containing a specific keyword, they send search tokens related to this keyword to the server. Subsequently, the server executes a search algorithm using the search tokens and the encrypted index, and returns the corresponding results to the data user.
The initial SSE scheme was presented by Song et al. [3]. Afterward, searchable encryption rapidly became a prominent research topic of interest. Most of the subsequent work has been conducted under the ideal assumption that the cloud server is honest but curious. Goh et al. [4] established an inverted-index-based searchable encryption scheme using Bloom filters. This article formally discusses the security model that searchable encryption needs to satisfy for the first time. Curtmola et al. [5] were pioneers in defining several types of leaked information and identified issues in the existing security models. Additionally, they constructed the first inverted-index-based SSE scheme, which achieved sub-linear search efficiency. These schemes are all designed based on static databases and cannot meet the requirements of real-time data updates (addition or deletion) in intelligent application systems. Therefore, a practically valuable SSE scheme should possess dynamic updating capabilities. To enable SSE to support dynamic updates, Kamara et al. [6] proposed the first dynamic searchable encryption (DSSE) scheme. Subsequently, several DSSE schemes have been proposed in various studies [7,8]. However, these schemes overlook the threat of file injection attacks [9] on leaked information during the update. Such powerful attacks recover keywords by establishing a connection between previous search tokens and currently updated files, which seriously compromises data privacy. Therefore, the need to counteract file injection attacks becomes a crucial factor for consideration. Stefanov et al. [10] were the pioneers in introducing the concept of forward privacy as a defense mechanism against file injection attacks. Bost et al. [11] presented a groundbreaking public-key-based hash-link structure to construct a DSSE scheme with forward privacy. Song et al. [12] and Wei et al. [13] both implemented DSSE schemes with forward privacy by using symmetric cryptographic primitives based on the scheme in [11]. Zuo et al. [14] utilized homomorphic encryption with bitmap index to achieve forward privacy in their scheme. These schemes employed various methods to achieve forward privacy, making significant contributions to the security of SSE schemes and widely acknowledging the role of forward privacy. Subsequently, several works have revolved around the DSSE function [15,16,17], security [18,19,20], and efficiency [21,22,23], providing numerous excellent schemes. Additionally, certain files could contain a significant volume of sensitive messages, such as personal health records, which should not be accessed indiscriminately. Only specific authorized users should be able to access the corresponding files. Therefore, while investigating the functionality, efficiency, and security of DSSE, introducing access control functionality can effectively enhance the practicality of the schemes [24,25,26].
The SSE schemes mentioned above all assume that the server will honestly return the correct search results. However, in practical settings, the server should be semi-honest and curious, meaning it might return incorrect search results to save computational resources or gain service fees dishonestly. Therefore, incorporating verification functionality into DSSE schemes has become a challenge. Some verifiable searchable symmetric encryption schemes attempt to verify search results locally by users [27,28,29]. However, the verification techniques in these schemes rely on specific indexing structures, lacking generality and impeding the expandability of the scheme’s expressive capabilities. In addition, in cases where users are dishonest or maliciously repudiate, such methods still cannot guarantee a fair verification of search results. Blockchain is a distributed database with the property of immutability and decentralization. Compared to traditional networks, the information recorded on the blockchain is more reliable, addressing the issue of mutual distrust among different parties. Therefore, introducing blockchain as a trusted third party into searchable encryption schemes can effectively resolve the problem of fair verification between servers and users. Hu et al. [30] proposed a fair verifiable DSSE scheme by utilizing smart contracts to replace the server. Cai et al. [31] achieved ciphertext retrieval in distributed storage and utilized blockchain for verification. Yan et al. [32] and Li et al. [33] both achieved static verification of search results on the blockchain by using message authentication codes. However, static verification cannot meet the requirements for frequent data updates in the 6G network. These schemes can be combined with blockchain technology to achieve the verification of search results and mitigate the potential for dishonest or malicious denial by users. However, there are still some challenges and issues that need to be addressed. The existing blockchain-based verifiable DSSE schemes either lack consideration for forward privacy and access control, or trade frequent transactions for ciphertext retrieval and result verification. The reason for frequent transactions is that both retrieval and verification operations are executed on the blockchain, which reduces the efficiency of the scheme. Hence, the challenge of devising an efficient and comprehensive DSSE scheme for 6G-based intelligent application systems remains an unresolved issue.
In response to the requirements of low latency, high security, and high reliability in 6G-based intelligent application systems, we propose a novel blockchain-based DSSE scheme, referred to as VSSE. Firstly, VSSE possesses forward privacy to consist file-injection attacks, which greatly enhances the security of the scheme. We construct a state chain structure to achieve forward privacy. For each update, a new state is randomly generated for the keyword, and each state is linked by encrypted entries. The cloud server cannot deduce the most recent state of the keyword by relying on past search tokens. Building upon this foundation, to further enhance the efficiency of the scheme, our approach establishes the search operations on the server side, thereby reducing the frequency of interactions with the blockchain during the search and contributing to efficiency improvement. Next, in order to comprehensively meet the high reliability requirements of 6G systems, our scheme validates search results based on the tamper-resistant property of the blockchain. Once the search is completed, the results are sent from the server to the blockchain. After that, the blockchain performs verification based on verification information and returns the verification result and the search result to the data user. Meanwhile, we introduce a bitmap index structure to represent file identifiers and combine it with message authentication code (MAC) technology to attain dynamic verification of outcomes. Moreover, VSSE encompasses access control functionality, enabling users with distinct permissions to access relevant files. The aforementioned designs collectively fulfill the characteristics of 6G-based intelligent application systems. Ultimately, our scheme’s security analysis and experimental outcomes affirm its robust security and operational efficiency.
2. Problem Formulation
This section introduces the system model of our scheme, as well as the cryptographic background and notations used in the rest of paper.
2.1. System Model
Figure 1 shows the system model diagram of our scheme, VSSE. Within VSSE, four entities are involved: , , and .
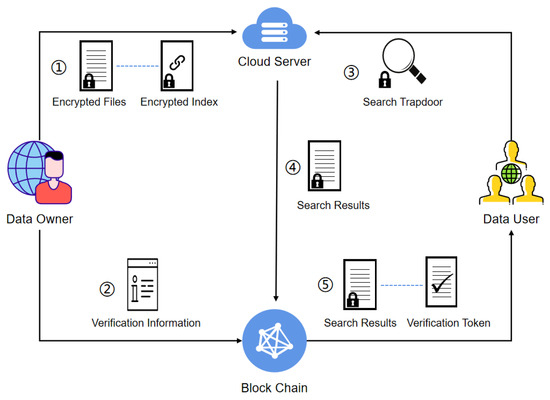
Figure 1.
Overview of system model.
: These entities aim to store the collected extensive and critical data on a cloud server. Specifically, encrypts each file and constructs secure indexes, which are then uploaded to . Furthermore, is tasked with generating verification information and subsequently uploading it to the Blockchain .
: is tasked with executing the search protocol and returning the corresponding search results to the blockchain for verification. Specifically, upon receiving the search traps sent by , uses secure index to execute search query. Then, also has to determine which users have the authority to access which files. In addition, due to the potential of the server returning inaccurate search outcomes to , is required to transmit the results to for verification.
: These entities would like to obtain reliable search results. Specifically, generates search trapdoor based on the keywords and transmits them to . Any legitimate will receive search results and verification information, while unauthorized will not be able to obtain any results.
: The responsibility of verifying the outcomes to determine the reliability of search results obtained by lies with . Specifically, upon receiving the search results, utilizes a verification contract to validate the search results and returns it along with the verification identifier to .
2.2. Notations
Table 1 presents the common notations in VSSE.

Table 1.
Common Notations.
2.3. Dynamic Searchable Encryption
A dynamic searchable encryption scheme typically consists of the Setup, Update, and Search algorithms.
The role of the Setup algorithm is to generate keys and construct the encrypted database. Specifically, it takes the security parameter and the database as inputs, and outputs the data owner’s key , state , and an encrypted database .
The Update algorithm is jointly executed by the data owner and the server, and its purpose is to insert or delete data from the database. Specifically, the data owner provides the key, state, keyword–document pairs, and update type as inputs, while the server provides the encrypted database as input. This algorithm will return an updated state and an updated encrypted database to the data owner and the server, respectively.
The Search algorithm is executed collaboratively by the data user and the server, aiming to search for files related to keyword w. Specifically, the data user provides the key and the keyword w as input, while the server provides the encrypted database as input. The algorithm returns a collection of files related to w to the data user.
The above content follows the general definition of searchable encryption as outlined in reference [34,35,36]. Additionally, our scheme includes the Verify algorithm, which will be elaborated in detail later in this paper.
2.4. Forward Privacy
Forward privacy focuses on preserving the confidentiality of keywords during file addition operations, ensuring that an addition query does not disclose any information about the keywords [37,38]. An SSE scheme lacking forward privacy may unintentionally leak information when inserting a new file. Exploiting this vulnerability, tests the previously submitted search token during a new update, checking whether the old search token matches the new update. A file injection attack takes advantage of this behavior to extract information about the keyword. First, can trick the into injecting some files containing certain specific keywords. After uploads the injected files, employs the search token provided by to search within the injected files, recovering the corresponding keyword based on the search result. As forward privacy guarantees that the past search token cannot be linked to a newly added file, this type of attack can be thwarted.
2.5. Bitmap Index
VSSE verifies the accuracy of search results through blockchain, a system that only allows for the appending of information, i.e., data can only be added and not deleted. However, updating (adding or deleting) data is a common operation in real-world DSSE applications. In order to update the data while completing the search result validation, we incorporate a bitmap index to uniquely identify and manage file identifiers. Specifically, assuming that the database can hold at most m files, it can be represented as m bits by using the bitmap index. From right to left, the i-th bit of the bitmap index represents the i-th file . A bit value of 1 indicates that the file has been added, while a value of 0 signifies that the file has been deleted or does not exist.
Figure 2 shows a sample bitmap index for . Figure 2a shows the state of the bitmap index when files and are present. Figure 2b depicts the addition of file based on the original state. We first need to generate the bit string 00001 for and then perform an XOR operation with the original bit string. The final state of the bitmap index is 001011. Figure 2c depicts the deletion of file based on the previous operations. Similar to the addition operation, we generate the bit string 001000 for and perform an XOR operation with the original bit string 001011. The resulting state of the bitmap index is 000011.
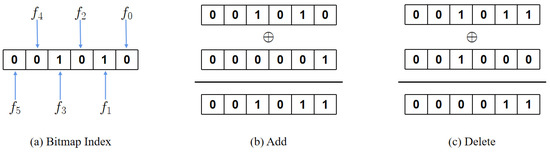
Figure 2.
An example of bitmap index.
3. Construction of Our Work
In this section, we present VSSE in detail, a verifiable dynamic searchable symmetric encryption scheme based on blockchain.
3.1. Detailed Construction
VSSE defines four protocols: Setup, Update, Search, and Verify. We first describe the symbols and functions that may be involved in each protocol. is a security parameter to generate secret keys. The value of m represents the maximum capacity of the database and also indicates the maximum length of the bitmap index, and , are both hash function used to generate keyword state locations and encrypted entries, respectively. Algorithms 1–4 summarize Setup, Update, Search, and Verify protocols of VSSE, respectively. Specifically, the structure of state chains is shown in Figure 3, while Setup, Update, and Search protocols are detailed below.
| Algorithm 1 VSSE.Setup. |
| : The security parameter . |
| : The security key and empty maps , Σ and . |
| 1: |
| 2: |
| 3: |
| : |
| 4: Σ, Tag |
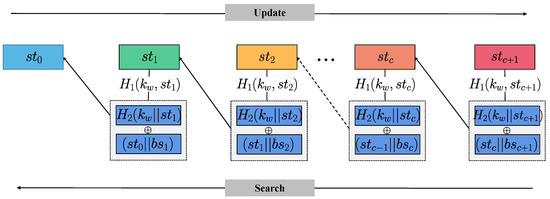
Figure 3.
The structure of state chain.
Setup. In the this protocol, generates the secret key , and an empty maps, . The key and are secreted by a -bits random string that are used to encrypt keywords and users. The map is employed to maintain the most recent state of each keyword, organized as a dynamic list with two columns. Keywords and their latest states are sequentially arranged in the two columns of . maintains two empty map and . is a dynamic list with two columns to construct secure index, where the first column is used to store the location of update and the second column corresponds to the updated file identifiers. is used to map the information about the user. It consist of two columns: the user’s identifier and user’s file access authority are located in the two columns of in order. also maintains two empty maps, Σ and . Σ is employed to store the user’s identifier and the corresponding file identifier for a specific keyword. is a dynamic list to store verification tag in the form of two columns. The user’s identifiers and keywords are located in the first column of , and the MAC values corresponding to search results are in the second column.
Update. When updating (adds or deletes) a file with identifier that contains keyword w, initiates the process by initially retrieving the previous state associated with the keyword w from . Subsequently, a new state is generated at random. is also updated accordingly. Next, computes and separately. represents the location of encrypted index entry e on the server, and is used to compute the encrypted index entry e. As the state is generated randomly, each observed state by the server during an update appears as if it has been drawn randomly. Consequently, the server remains incapable of deducing the subsequent state based on the current search token. This imparts a guarantee of forward privacy. also needs to encrypt the authorized user’s identifiers to facilitate the storage of corresponding information on the server and the blockchain. Finally, sends to the server, which then stores the encrypted entries and associated file identifiers. Meanwhile, sends to the blockchain to complete the result verification process, and the blockchain updates and stores the accessible files for the user along with their corresponding message authentication codes.
| Algorithm 2 VSSE.Update. |
| : The security key , the file identifier , the keyword w and user . |
| : The latest state , the index location , the index information . |
| : |
| 1: |
| 2: |
| 3: |
| 4: |
| 5: |
| 6: |
| 7: |
| 8: |
| 9: |
| 10: |
| 11: |
| 12: |
| 13: |
| 14: |
| 15: |
| 16: |
| 17: |
| 18: |
| : |
| 19: |
| 20: |
| 21: |
| 22: |
Search. When searching for the files containing keyword w, encrypts keyword w by using and a pseudorandom function F, and retrieves the current state from . Then, sends to . uses the to obtain the location of current state and retrieves the corresponding encrypted entry from . By decrypting the encrypted entry, obtains the file identifier associated with the current state and the previous state . Finally, after c iterations, XORs each bitmap to obtain the final result , which includes all the results involving the keyword w. For different , the server retrieves the files that the current is authorized to access from by the user’s identifier. After completing the search for files containing w, must determine whether the user has permission to access these files, i.e., it performs an AND operation between and . The final result is not directly returned to the but is sent by the server to the blockchain for further verification.
| Algorithm 3 VSSE.Search. |
| : The security key , the keyword w and user . |
| : The search result . |
| : |
| 1: |
| 2: |
| 3: |
| 4: |
| 5: |
| 6: |
| 7: |
| 8: |
| 9: |
| 10: |
| 11: |
| 12: |
| 13: |
| 14: |
| Algorithm 4 VSSE.Verify. |
| : The encrypted keyword , the encrypted user and search result . |
| : The search result and the verify information . |
| : |
| 1: |
| 2: |
| 3: |
| 4: |
| 5: |
| 6: |
| 7: |
| 8: |
Verify. In this protocol, the blockchain utilizes a verification contract to validate the correctness of search results. The verification contract constructs a key-value pair list in the form of (addr, val), where the first column contains user and keyword information used to locate a specific entry, and the second column stores the MAC for the corresponding result. Upon receiving encrypted keywords , encrypted user identifiers , and search results from the server, the verification contract retrieves the MAC value for the corresponding result by using and as indices in the . Then, the verification contract computes the corresponding MAC value based on the search result and compares with . If they match, the verification token is set to 1, indicating that the search result is correct; otherwise, the verification token is set to 0. Finally, the blockchain sends the verification token along with the search result to , which employs to ascertain the correctness of the search outcome.
To illustrate the verification process of the scheme on the blockchain more intuitively, we provide an explanation using a simple example. Figure 4 depicts the verification process when the cloud server sends the keyword , user identifier information , and the corresponding search result to the blockchain. Upon receiving the aforementioned information, the blockchain employs the verification contract to extract the correct MAC value stored in the list for the combination of , i.e. . Subsequently, the verification contract computes the MAC value for the result sent by the cloud server and compares it with the extracted from the . Since is equal to , the verification token is set to 1. Finally, the blockchain returns the verification token along with the search result to the user.
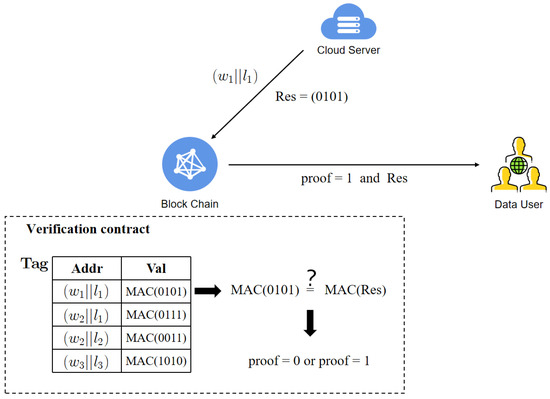
Figure 4.
The example of verification.
3.2. Security Analysis
Forward privacy is a crucial security attribute that a DSSE scheme should possess, as it involves the update and search operations common to all DSSE schemes. Therefore, our security analysis primarily focuses on threats associated with the update and search operations. VSSE satisfies definition of forward security. Specifically, in VSSE, each state of the keyword is randomly generated, the value of each state is indistinguishable from a random value in the server’s view, and the server is incapable of deducing the forthcoming state using the present state of the keyword. As a result, the forward privacy of VSSE remains ensured.
The theorem regarding the security of VSSE is as follows.
Theorem 1.
Assume that F is a secure pseudorandom function, and and are hash functions in random oracle model. The leakage functions are denoted as and , where and are used to capture the leakage during the update and search, is the access pattern, and is the search pattern. Then VSSE is an -adaptively secure SSE scheme with forward privacy.
Proof of Theorem 1.
The security of VSSE is proven through a sequence of games involving the real game and the ideal game . By demonstrating the indistinguishability between two adjacent games, we establish the equivalence between the real and ideal games.
Game : is game.
Game : In , instead of using a pseudo-random function F to generate , we randomly select and store it in the mapping . For the subsequent query on w, we can directly retrieve the corresponding from . Since we cannot distinguish between a F and a true random function, and are indistinguishable.
Game : no longer calls to generate location in the update protocol, but uses random numbers instead. Specifically, it involves using instead of and performing , where is a mapping held by . Then, is executed in the search protocol, where is the table of . It can be seen that is not updated in real time, so when the adversary accesses before the search query is issued, will randomly generate a value that is different from v. When the adversary accesses once more following the subsequent search, it will obtain the value v that has been updated into . By comparing the differences between the two access results, the adversary will know that it is in . However, the probability of such case occurring is negligible.
Based on the above, this case only happens when the adversary accesses using . Given that is randomly generated, the likelihood of the adversary selecting is . Assuming a PPT adversary makes up to guesses, the probability of this occurrence is , which can be negligible. Therefore, and are indistinguishable.
Game : In the update protocol of , is processed in the same way as in . Since the likelihood of the adversary guessing is , and the probability after polynomial queries by the adversary is , it follows that and are indistinguishable.
Game : In , the value of is generated instantaneously during the search. Algorithm 5 shows the algorithmic changes on the . utilizes to record the update query that occurred after the last search, and extracts the number of updates and . randomly selects the query result of a random oracle without the information about . Subsequently, is generated and used to update the random oracle during the execution of the search operation. From the adversary’s perspective, since and output two random strings during the update phase and both output during the search, and are completely indistinguishable.
Simulator: In the ideal game , the simulator constructs a view by utilizing the leakage function. Algorithm 6 details , which maintains two mappings and an update counter. The values of each mapping are also randomly generated during the update. Unlike , uses to represent the first time to search keywords w and uses the update history as input to parse the number of keyword updates and update requests, rather than computing based on . Afterwards, randomly generates and updates the random oracle with the information above. The simulator and are entirely equivalent.
| Algorithm 5 Game |
| Setup(λ) |
| 1: |
| 2: |
| Update(ks,W,w, bs; T) |
| : |
| 3: |
| 4: |
| 5: |
| 6: |
| 7: |
| Search(ks,W,w; T) |
| : |
| 8: |
| 9: |
| 10: |
| 11: |
| 12: |
| 13: |
| 14: |
| 15: |
| 16: |
| 17: |
| 18: |
| 19: |
| 20: |
| 21: |
| 22: |
| 23: |
| Algorithm 6 Simulator |
| Setup() |
| : |
| 1: |
| 2: |
| Update() |
| 3: |
| 4: |
| 5: |
| 6: |
| Search(sp(w), uh(w)) |
| : |
| 7: |
| 8: |
| 9: |
| 10: |
| 11: |
| 12: |
| 13: |
| 14: |
| 15: |
| 16: , |
| 17: |
| 18: |
| 19: |
| 20: |
| 21: |
| 22: |
□
4. Experimental Evaluation
This section presents a comparative analysis between VSSE and other existing schemes, considering both functionality and performance aspects.
4.1. Function Comparison
Table 2 offers a functional comparison between our scheme and other existing schemes. The schemes in refs. [11,24,25] did not consider the possibility of incorrect search results and do not possess the capability for result verification. The schemes in [31,33] and our scheme all take into account the scenario where the server maliciously returns incorrect search results, and they all rely on blockchain technology to accomplish the verification of search results. However, the schemes in refs. [31,33] lack consideration for forward security during the update, and they are only applicable to single-user scenarios. The scheme in refs. [33] also fails to achieve dynamic verification of search results.

Table 2.
Function comparison of various scheme.
Our scheme ensures forward security during the data update by a state chain structure and achieves dynamic verification of search results using blockchain and bitmap index. Additionally, we employ access control operations to enable the scheme to achieve secure search functionality in multi-user scenarios.
4.2. Performance Analysis
Implementation and settings. In order to provide a more realistic evaluation of the scheme’s performance in practical applications, we conducted tests using the Enron email dataset, which reflects real-world scenarios. This dataset contains email information from approximately 150 users across different folders. We selected 30,109 files from the Enron email dataset to form the file collection. Then, we utilized the method described in refs. [39,40] to extract 77,000 keywords from these files. We implemented VSSE in Python. Specifically, we used AES-256 and SHA-256 to implement the pseudo-random function and hash function, respectively. For the verification module, we used Solidity to build Ethereum smart contracts and utilize Ganache to evaluate the smart contracts. We have conducted a comparative analysis between VSSE and the existing schemes presented in refs. [26,32] to demonstrate the advantages of our proposed scheme. In particular, the scheme in refs. [32] is a blockchain-based solution and is also the primary comparison object in our study.
Index Generation Performance. Constructing a secure index is the foundation for performing effective search operations. Figure 5 illustrates the correlation between the index generations time and the amount of keywords. Illustrated in Figure 5, r index generation time across all schemes exhibits a proportional relationship with the number of keywords. Specifically, to balance search efficiency, the scheme in ref. [26] constructs a dual-index structure, which requires more time. On the other hand, in scheme [32], the index is constructed with less time cost by using key-value pairs, but lacks consideration for forward security. Compared to the schemes in refs. [26,32], VSSE outperforms [32] and takes more time than [26]. However, the index generated by VSSE fully considers the forward privacy and contributes to the search efficiency. Subsequent experiments will demonstrate this.
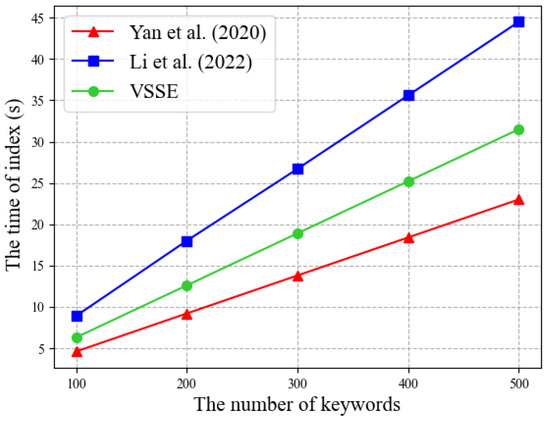
Figure 5.
Time of index generation. Yan et al. (2020) refers to the scheme in ref. [32], and Li et al. (2022) refers to the scheme in ref. [26].
Search Performance.Figure 6 illustrates the correlation between search time and factors such as the quantity of keywords, the number of users, and the count of matching files. In Figure 6a, we demonstrate the influence of the quantity of keywords and the count of matching files on the search time. In Figure 6a, distinct colors of bars are employed to indicate varying quantities of matching files. It is evident that the search time exhibits a direct proportionality with the number of matching files and remains unaffected by the number of keywords. This observation is attributed to the construction of the inverted index. Moreover, Figure 6b illustrates the search efficiency of each scheme under different numbers of matching documents. VSSE outperforms the scheme in refs. [26,32]. The scheme in ref. [32] is worse than [26] and VSSE, which is because this scheme requires additional interaction with the blockchain during search operations. The search performance of [26] matches VSSE, but it lacks a verification feature. VSSE does not require additional interaction with the blockchain during the search and achieves search result verification functionality. Figure 6c depicts the impact of varying numbers of users and matching documents on search time. It can be observed that, with a fixed number of matching files, search time increases with the quantity of users grows. Similarly, with a constant number of users, search time also increases with the scale of files. The increase in search time due to the growth in the number of users is foreseeable. Figure 6d further illustrates the influence of varying numbers of users on the search time for each scheme. It is evident from the graph that the search time for all schemes is directly proportional to the number of users. However, compared to [32], both the scheme in ref. [26] and VSSE exhibit greater advantages.
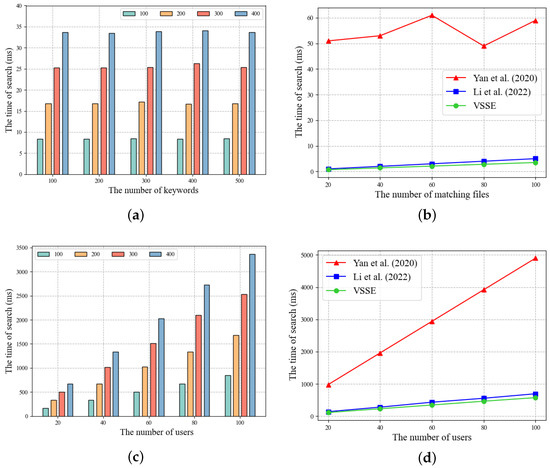
Figure 6.
Time of search. (a) The influence of the quantity of keywords and the count of matching files on the search time. (b) The search efficiency of each scheme under different numbers of matching files. (c) The impact of varying numbers of users and matching files on search time. (d) The influence of varying numbers of users on the search time for each scheme. Yan et al. (2020) refers to the scheme in ref. [32], and Li et al. (2022) refers to the scheme in ref. [26].
Verification Performance. In this section, since the scheme in ref. [26] lacks the verification capability, we only compare the scheme in ref. [32] with VSSE. Figure 7 illustrates the correlations between the quantity of matching files and the storage capacity of the blockchain. As depicted in Figure 7, the storage requirement of the scheme proposed in ref. [32] escalates as the number of matching files increases. When the number of matching files rises from 1000 to 5000, the storage space usage also increases from 76.3 KB to 380.4 KB. This is because the scheme in ref. [32] requires storing the verification information for each file sequentially on the blockchain, and as the number of files increases, so does the required storage space. For VSSE, we only need to store a fixed bitmap index on the blockchain, which contains information about all the relevant files. Therefore, the storage cost of VSSE is hardly affected by the number of files, and our storage cost is much lower than that of the scheme in ref. [32] (e.g., for the number of matching files is 5000, VSSE incurs a storage cost of 13.8KB, while the scheme in ref. [32] takes 380.4 KB). Moreover, we compare the verification efficiency of the two schemes. Figure 8 illustrates the correlation between verification time and factors such as the length of bitmap index and the count of matching files. In Figure 8a, the verification time of the scheme in ref. [32] is proportional to the number of matching files, and the verification time of VSSE remains nearly constant and is faster than the scheme in ref. [32] in most scenarios (e.g., for the number of matching files is 5000, the verification time of VSSE is 2.5 s, while the scheme in ref. [32] takes 5.4 s). This is because the scheme in ref. [32] requires the computation of verification information for each file during the verification phase, and the number of files directly affects the verification time. In contrast, VSSE only needs to compute verification information for the bitmap index, and the verification time is solely related to the length of the bitmap index, unaffected by the number of matching files. Figure 8b further illustrates the impact of the bitmap index length on the verification time of VSSE. Distinct colors of bars indicate varying numbers of matching files. With the bitmap length increasing from 1000 to 5000, the verification time also increases from 0.53 s to 2.53 s. However, when the bitmap index length is fixed, the verification time remains almost the same.
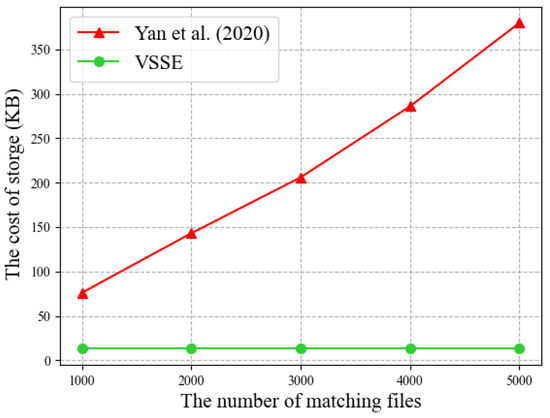
Figure 7.
The cost of storage. Yan et al. (2020) refers to the scheme in ref. [32].
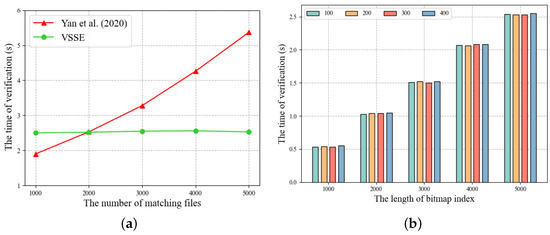
Figure 8.
Time of verification. (a) The influence of varying numbers of matching files on the verification time for each scheme. (b) The impact of the bitmap index length on the verification time of VSSE. Yan et al. (2020) refers to the scheme in ref. [32].
5. Conclusions and Future Work
In this work, we present VSSE, a verifiable DSSE scheme based on blockchain for 6G-based intelligent application systems. This scheme ensures forward privacy of data in the 6G network through a state chain structure. VSSE leverages the immutable nature of blockchain to perform verification operations on the blockchain. Meanwhile, it combines bitmap index and MAC technology to achieve dynamic verification of search results. Our scheme also possesses effective access control functionality. Finally, the evaluation of the scheme’s functionality and performance demonstrates that VSSE aligns with the requirements of 6G-based intelligent application systems.
Regarding future work, in this paper, we conducted a security analysis focusing solely on threats related to update and search operations. However, potential threats still exist in the verification process between the cloud server and the blockchain, as well as in the access control mechanism for users with different privileges. Therefore, a more comprehensive security analysis of VSSE is needed, including the consideration of various attack scenarios, such as collusion attacks, and the proposal of corresponding security measures. Furthermore, although the scheme presented in this paper exhibits high search efficiency for single keyword, the search cost increases linearly with the number of keywords when users perform conjunctive searches involving multiple keywords. This is not favorable for a truly practical DSSE scheme. Therefore, our future research direction will focus on extending our scheme from single-keyword searches to multi-keyword searches while maximizing search efficiency. When our scheme achieves both rich expressive capability and efficient search performance, along with dynamic verification functionality, it will represent a more ideal DSSE solution in the context of 6G networks.
Author Contributions
Writing—original draft, T.P.; Writing—review & editing, J.Z.; Funding acquisition, B.G. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported in part by the National Key Research and Development Project of China under Grant 2019YFB2102303, and in part by the National Natural Science Foundation of China under Grant 61971014.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The data presented in this study are available on reasonable request from the corresponding author.
Conflicts of Interest
The authors declare no conflict of interest.
References
- You, X.; Wang, C.X.; Huang, J.; Gao, X.; Zhang, Z.; Wang, M.; Huang, Y.; Zhang, C.; Jiang, Y.; Wang, J.; et al. Towards 6G Wireless Communication Networks: Vision, Enabling Technologies, and New Paradigm Shifts. Sci. China Inf. Sci. 2021, 64, 110301. [Google Scholar] [CrossRef]
- Shi, J.; Yu, Y.; Yu, Q.; Li, H.; Wang, L. Toward Data Security in 6G Networks: A Public-Key Searchable Encryption Approach. IEEE Netw. 2022, 36, 166–173. [Google Scholar] [CrossRef]
- Song, D.X.; Wagner, D.; Perrig, A. Practical techniques for searches on encrypted data. In Proceedings of the IEEE Symposium Security and Privacy, Berkeley, CA, USA, 14–17 May 2000; pp. 44–55. [Google Scholar]
- Goh, E. Secure indexes. IACR Cryptol. ePrint Arch. 2003, 2003, 216–234. [Google Scholar]
- Curtmola, R.; Garay, J.; Kamara, S.; Ostrovsky, R. Searchable symmetric encryption: Improved definitions and efficient constructions. J. Comput. Secur. 2011, 19, 895–934. [Google Scholar] [CrossRef]
- Kamara, S.; Papamanthou, C.; Roeder, T. Dynamic searchable symmetric encryption. In Proceedings of the CCS 2012, Raleigh, NC, USA, 16–18 October 2012; pp. 965–976. [Google Scholar]
- Sun, S.F.; Liu, J.K.; Sakzad, A.; Steinfeld, R.; Yuen, T.H. An efficient non-interactive multi-client searchable encryption with support for boolean queries. In Proceedings of the ESORICS 2016, Heraklion, Greece, 26–30 September 2016; pp. 154–172. [Google Scholar]
- Xia, Z.; Wang, X.; Sun, X.; Wang, Q. A secure and dynamic multi-keyword ranked search scheme over encrypted cloud data. IEEE Trans. Parallel Distrib. Syst. 2016, 27, 340–352. [Google Scholar] [CrossRef]
- Zhang, Y.; Katz, J.; Papamanthou, C. All your queries are belong to us: The power of file-injection attacks on searchable encryption. In Proceedings of the 25th USENIX Security Symposium (USENIX Security 16), Austin, TX, USA, 10–12 August 2016; pp. 707–720. [Google Scholar]
- Stefanov, E.; Papamanthou, C.; Shi, E. Practical dynamic searchable encryption with small leakage. In Proceedings of the NDSS 2014, San Diego, CA, USA, 23–26 February 2014; pp. 1–15. [Google Scholar]
- Bost, R. ∑oϕoξ: Forward secure searchable encryption. In Proceedings of the CCS 2016, Vienna, Austria, 24–28 October 2016; pp. 1143–1154. [Google Scholar]
- Song, X.F.; Dong, C.; Yuan, D.; Xu, Q.; Zhao, M. Forward private searchable symmetric encryption with optimized I/O efficiency. IEEE Trans. Dependable Secur. Comput. 2020, 17, 912–927. [Google Scholar] [CrossRef]
- Wei, Y.; Lv, S.; Guo, X.; Liu, Z.; Huang, Y.; Li, B. FSSE: Forward secure searchable encryption with keyed-block chains. Inf. Sci. 2019, 500, 113–126. [Google Scholar] [CrossRef]
- Zuo, C.; Sun, S.F.; Liu, J.K.; Shao, J.; Pieprzyk, J. Dynamic searchable symmetric encryption with forward and stronger backward privacy. In Proceedings of the ESORICS 2019, Luxembourg, 23–27 September 2019; pp. 1–21. [Google Scholar]
- Zhang, P.; Chui, Y.; Liu, H.; Yang, Z.; Wu, D.; Wang, R. Efficient and privacy-preserving search over edge-cloud collaborative entity in IoT. IEEE Internet Things J. 2023, 10, 3192–3205. [Google Scholar] [CrossRef]
- Zhou, R.; Zhang, X.; Wang, X.; Yang, G.; Dai, H.N.; Liu, M. Device-oriented keyword searchable encryption scheme for cloud-assisted industrial IoT. IEEE Internet Things J. 2022, 9, 17098–17109. [Google Scholar] [CrossRef]
- Liu, Y.-R.; Yu, J.; Fan, J.; Vijayakumar, P.; Chang, V. Achieving privacy-preserving DSSE for intelligent IoT healthcare system. IEEE Trans. Ind. Inform. 2021, 18, 2010–2020. [Google Scholar] [CrossRef]
- Niu, J.; Li, X.; Gao, J.; Han, Y. Blockchain-based anti-key-leakage key aggregation searchable encryption for IoT. IEEE Internet Things J. 2020, 7, 1502–1518. [Google Scholar] [CrossRef]
- Demertzis, I.; Papadopoulos, D.; Papamanthou, C. Searchable encryption with optimal locality: Achieving sublogarithmic read efficiency. In Proceedings of the CRYPTO 2018, Santa Barbara, CA, USA, 19–23 August 2018; pp. 371–406. [Google Scholar]
- Tong, Q.; Miao, Y.; Liu, X.; Choo, K.K.R.; Deng, R.H.; Li, H. VPSL: Verifiable privacy-preserving data search for cloud-assisted Internet of Things. IEEE Trans. Cloud Comput. 2022, 10, 2964–2976. [Google Scholar] [CrossRef]
- Cash, D.; Jarecki, S.; Jutla, C.; Krawczyk, H.; Roşu, M.C.; Steiner, M. Highly-scalable searchable symmetric encryption with support for boolean queries. In Proceedings of the CRYPTO 2013, Santa Barbara, CA, USA, 18–22 August 2013; pp. 353–373. [Google Scholar]
- Cui, J.; Lu, J.; Zhong, H.; Zhang, Q.; Gu, C.; Liu, L. Parallel key-insulated multiuser searchable encryption for industrial internet of things. IEEE Trans. Ind. Inform. 2021, 18, 4875–4883. [Google Scholar] [CrossRef]
- Chen, G.; Chen, S.; Xiao, Y.; Zhang, Y.; Lin, Z.; Lai, T.H. SgxPectre attacks: Stealing Intel secrets from SGX enclaves via speculative execution. In Proceedings of the EuroS&P 2019, Stockholm, Sweden, 17–19 June 2019; pp. 142–157. [Google Scholar]
- Li, H.; Yang, Y.; Dai, Y.; Yu, S.; Xiang, Y. Achieving secure and efficient dynamic searchable symmetric encryption over medical cloud data. IEEE Trans. Cloud Comput. 2020, 8, 484–494. [Google Scholar] [CrossRef]
- Li, M.; Yu, S.; Ren, K.; Lou, W. Securing personal health records in cloud computing: Patient-centric and fine-grained data access control in multi-owner settings. In Security and Privacy in Communication Networks, Proceesings of the 6th Iternational ICST Conference, SecureComm 2010, Singapore, 7–9 September 2010; Springer: Berlin/Heidelberg, Germany, 2010; pp. 89–106. [Google Scholar]
- Li, S.; Xu, C.; Zhang, Y.; Du, Y.; Wen, X.; Chen, K.; Ma, J. Efficient Data Retrieval Over Encrypted Attribute-Value Type Databases in Cloud-Assisted Ehealth Systems. IEEE Syst. J. 2022, 16, 3096–3107. [Google Scholar] [CrossRef]
- Sun, W.; Liu, X.; Lou, W.; Hou, Y.T.; Li, H. Catch you if you lie to me: Efficient verifiable conjunctive keyword search over large dynamic encrypted cloud data. In Proceedings of the IEEE Conference on Computer Communications (INFOCOM), Hong Kong, China, 26 April 2015–1 May 2015; pp. 2110–2118. [Google Scholar]
- Zhu, X.; Liu, Q.; Wang, G. A Novel Verifiable and Dynamic Fuzzy Keyword Search Scheme over Encrypted Data in Cloud Computing. In Proceedings of the IEEE Trustcom/BigDataSE/ISPA, Tianjin, China, 23–26 August 2016; pp. 845–851. [Google Scholar]
- Ge, X.; Yu, J.; Zhang, H.; Hu, C.; Li, Z.; Qin, Z.; Hao, R. Towards Achieving Keyword Search over Dynamic Encrypted Cloud Data with Symmetric-Key Based Verification. IEEE Trans. Dependable Secur. Comput. 2021, 18, 490–504. [Google Scholar] [CrossRef]
- Hu, S.; Cai, C.; Wang, Q.; Wang, C.; Luo, X.; Ren, K. Searching an Encrypted Cloud Meets Blockchain: A Decentralized, Reliable and Fair Realization. In Proceedings of the IEEE Conference on Computer Communications, Honolulu, HI, USA, 16–19 April 2018; pp. 792–800. [Google Scholar]
- Cai, C.; Weng, J.; Yuan, X.; Wang, C. Enabling Reliable Keyword Search in Encrypted Decentralized Storage with Fairness. IEEE Trans. Dependable Secur. Comput. 2021, 18, 131–144. [Google Scholar] [CrossRef]
- Yan, X.X.; Yuan, X.H.; Tang, Y.L.; Chen, Y.L. Verifiable attribute-based searchable encryption scheme based on blockchain. J. Commun. 2020, 41, 187–198. [Google Scholar]
- Li, H.G.; Tian, H.B.; Zhang, F.G.; He, J.J. Blockchain-based searchable symmetric encryption scheme. Comput. Electr. Eng. 2019, 73, 32–45. [Google Scholar] [CrossRef]
- Demertzis, I.; Chamani, J.G.; Papadopoulos, D.; Papamanthou, C. Dynamic searchable encryption with small client storage. In Proceedings of the NDSS 2020, San Diego, CA, USA, 23–26 February 2020; pp. 1–17. [Google Scholar]
- Sun, S.-F.; Steinfeld, R.; Lai, S.; Yuan, X.; Sakzad, A.; Liu, J.K.; Nepal, S.; Gu, D. Practical non-interactive searchable encryption with forward and backward privacy. In Proceedings of the NDSS 2021, Virtual, 21–25 February 2021; pp. 1–18. [Google Scholar]
- Xu, P.; Susilo, W.; Wang, W.; Chen, T.; Wu, Q.; Liang, K.; Jin, H. ROSE: Robust searchable encryption with forward and backward security. IEEE Trans. Inf. Forensics Secur. 2022, 17, 1115–1130. [Google Scholar] [CrossRef]
- Bost, R.; Minaud, B.; Ohrimenko, O. Forward and backward private searchable encryption from constrained cryptographic primitives. In Proceedings of the CCS 2017, Dallas, TX, USA, 30 October–3 November 2017; pp. 1465–1482. [Google Scholar]
- Chamani, J.G.; Papadopoulos, D.; Papamanthou, C.; Jalili, R. New constructions for forward and backward private symmetric searchable encryption. In Proceedings of the CCS 2018, Toronto, ON, Canada, 15–19 October 2018; pp. 1038–1055. [Google Scholar]
- Shang, Z.W.; Simon, O.; Andreas, P.; Florian, K. Obfuscated access and search patterns in searchable encryption. In Proceedings of the NDSS 2021, Virtual, 21–25 February 2021. [Google Scholar]
- Islam, M.S.; Kuzu, M.; Kantarcioglu, M. Access pattern disclosure on searchable encryption: Ramification, attack and mitigation. In Proceedings of the NDSS 2012, San Diego, CA, USA, 5–8 February 2012; pp. 1–15. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).