Fully Homomorphic Encryption with Optimal Key Generation Secure Group Communication in Internet of Things Environment
Abstract
:1. Introduction
2. Literature Review
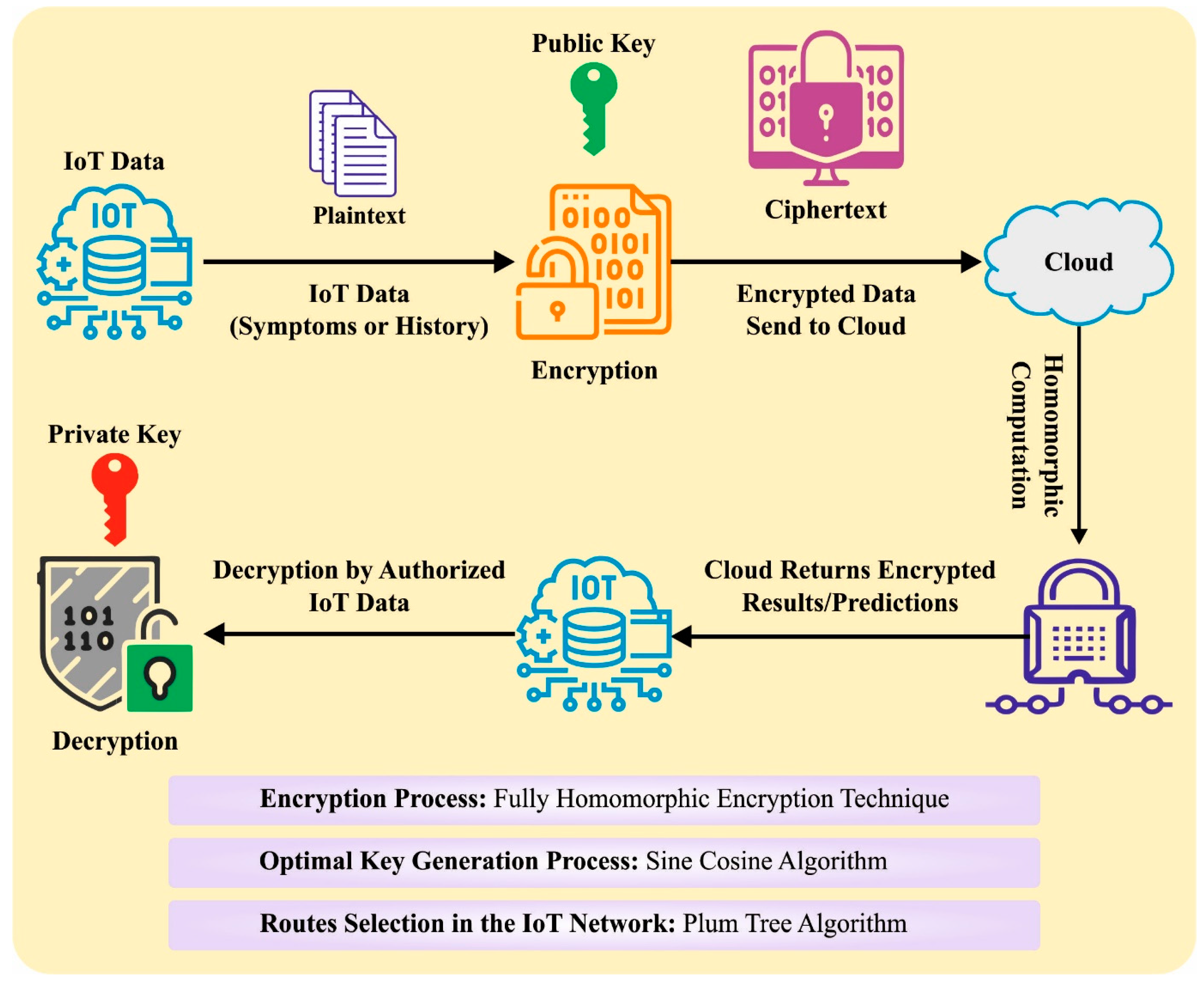
3. The Proposed Model
3.1. Fully Homomorphic Encryption
- Enc obtains as input a plaintext and outputs a c ciphertext so that c refers to the homomorphic image of m, viz., ;
- Dec proceeds to input a c ciphertext and output a plaintext m so that m denotes the homomorphic image of c;
- Enc and Dec are calculated as effective.
3.2. Optimal Key Generation Process
- i.
- r1 determines the direction within the space among the solution and the space outside the solution or the destination.
- ii.
- r2 gives the distance to travel toward or outward from the target.
- iii.
- r3 shows random weight to highlight the weight of exploitation (r3 < 1) or exploration (r3 > 1).

3.3. PTA-Based Route Selection in Group Communication
| Algorithm 1: Pseudocode of PTA |
| Input OF, Output flowers initialized in the -dimension space with ranges from plums are initialized to the locations of the flowers Apply OF to calculate the plum’s fitness and the flowers and upgrade For , do Calculate the ripe location of Calculate the unripe location For every flower, do Upgrade to a random integer ranging from If , then Upgrade the flower based on Equation (8) Else if , then Upgrade the flower based on Equation (9) Else Upgrade the flower based on Equations (10) and (11) End if Adjust the flower to be in the interval End for For every plum, do Upgrade the plum based on Equation (12) End for Upgrade the End for Return |
3.4. Security and Group Key Management Center
4. Results and Discussion
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Ghosal, A.; Conti, M. Key management systems for smart grid advanced metering infrastructure: A survey. IEEE Commun. Surv. Tutor. 2019, 21, 2831–2848. [Google Scholar] [CrossRef]
- Apsara, M.B.; Dayananda, P.; Sowmyarani, C.N. A Review on Secure Group Key Management Schemes for Data Gathering in Wireless Sensor Networks. Eng. Technol. Appl. Sci. Res. 2020, 10, 5108–5112. [Google Scholar] [CrossRef]
- Wazid, M.; Bagga, P.; Das, A.K.; Shetty, S.; Rodrigues, J.J.; Park, Y. AKM-IoV: Authenticated key management protocol in fog computing-based Internet of vehicles deployment. IEEE Internet Things J. 2019, 6, 8804–8817. [Google Scholar] [CrossRef]
- Rawat, A.S.; Deshmukh, M. Computation and communication efficient secure group key exchange protocol for low con-figuration system. Int. J. Inf. Technol. 2021, 13, 839–843. [Google Scholar]
- Parthasarathi, P.; Shankar, S. Decision Tree Based Key Management for Secure Group Communication. Comput. Syst. Sci. Eng. 2022, 42, 561–575. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Kumar, N.; Vasilakos, A.V. Design of secure key management and user authentication scheme for fog computing services. Futur. Gener. Comput. Syst. 2019, 91, 475–492. [Google Scholar] [CrossRef]
- Jha, S.; Jha, N.; Prashar, D.; Ahmad, S.; Alouffi, B.; Alharbi, A. Integrated IoT-based secure and efficient key management framework using hashgraphs for autonomous vehicles to ensure road safety. Sensors 2022, 22, 2529. [Google Scholar] [CrossRef]
- Hegde, N.; Manvi, S.S. Secure Group Key Management Scheme for Dynamic Vehicular Cloud Computing. Int. J. Adv. Netw. Appl. 2021, 13, 4821–4826. [Google Scholar] [CrossRef]
- Hassan, M.R.; Alnaimait, F.A.; Kharma, Q.; Sharah, A.; Al-Shqeerat, K.H. Secure Group Key Management Protocol for Grid Computing. Webology 2021, 18, 1055–1065. [Google Scholar] [CrossRef]
- Aliev, H.; Kim, H.; Choi, S. A Scalable and Secure Group Key Management Method for Secure V2V Communication. Sensors 2020, 20, 6137. [Google Scholar] [CrossRef]
- Dammak, M.; Senouci, S.M.; Messous, M.A.; Elhdhili, M.H.; Gransart, C. Decentralized lightweight group key manage-ment for dynamic access control in IoT environments. IEEE Trans. Netw. Serv. Manag. 2020, 17, 1742–1757. [Google Scholar] [CrossRef]
- Kandi, M.A.; Kouicem, D.E.; Lakhlef, H.; Bouabdallah, A.; Challal, Y. A blockchain-based key man-agement protocol for secure device-to-device communication in the internet of things. In Proceedings of the 2020 IEEE 19th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), Guangzhou, China, 29 December 2020–1 January 2021; pp. 1868–1873. [Google Scholar]
- Wang, J.; Wu, L.; Choo, K.-K.R.; He, D. Blockchain-Based Anonymous Authentication with Key Management for Smart Grid Edge Computing Infrastructure. IEEE Trans. Ind. Inform. 2019, 16, 1984–1992. [Google Scholar] [CrossRef]
- Tian, Y.; Wang, Z.; Xiong, J.; Ma, J. A Blockchain-Based Secure Key Management Scheme with Trustworthiness in DWSNs. IEEE Trans. Ind. Inform. 2020, 16, 6193–6202. [Google Scholar] [CrossRef]
- Ma, M.; Shi, G.; Li, F. Privacy-Oriented Blockchain-Based Distributed Key Management Architecture for Hierarchical Access Control in the IoT Scenario. IEEE Access 2019, 7, 34045–34059. [Google Scholar] [CrossRef]
- Xue, K.; Meng, W.; Zhou, H.; Wei, D.S.L.; Guizani, M. A Lightweight and Secure Group Key Based Handover Authentication Protocol for the Software-Defined Space Information Network. IEEE Trans. Wirel. Commun. 2020, 19, 3673–3684. [Google Scholar] [CrossRef]
- De Ree, M.; Mantas, G.; Rodriguez, J.; Otung, I.E. DECENT: Decentralized and Efficient Key Management to Secure Communication in Dense and Dynamic Environments. IEEE Trans. Intell. Transp. Syst. 2022, 1–13. [Google Scholar] [CrossRef]
- Choudhury, B.; Nag, A.; Nandi, S. DTLS based secure group communication scheme for Internet of Things. In Proceedings of the 2020 IEEE 17th International Conference on Mobile Ad Hoc and Sensor Systems (MASS), Delhi, India, 10–13 December 2020; pp. 156–164. [Google Scholar]
- Wang, X.A.; Xhafa, F.; Ma, J.; Cao, Y.; Tang, D. Reusable garbled gates for new fully homomorphic encryption service. Int. J. Web Grid Serv. 2017, 13, 25–48. [Google Scholar] [CrossRef]
- Naresh, V.S.; Allavarpu, V.V.L.D.; Reddi, S. Blockchain IOTA Sharding based Scalable Secure Group Communication in Large VANETs. IEEE Internet Things J. 2022, 10, 5205–5213. [Google Scholar] [CrossRef]
- Raj, S.R.S.; Prakash, M.V.; Prince, T.; Shankar, K.; Varadarajan, V.; Nonyelu, F. Web Based Database Security in Internet of Things Using Fully Homomorphic Encryption and Discrete Bee Colony Optimization. Malays. J. Comput. Sci. 2020, 1–14. [Google Scholar] [CrossRef]
- Wibawa, F.; Catak, F.O.; Sarp, S.; Kuzlu, M. BFV-Based Homomorphic Encryption for Privacy-Preserving CNN Models. Cryptography 2022, 6, 34. [Google Scholar] [CrossRef]
- Pham, V.H.S.; Nguyen, V.N. Cement Transport Vehicle Routing with a Hybrid Sine Cosine Optimization Algorithm. Adv. Civ. Eng. 2023, 2023, 2728039. [Google Scholar] [CrossRef]
- Moldovan, D. Plum Tree Algorithm and Weighted Aggregated Ensembles for Energy Efficiency Estimation. Algorithms 2023, 16, 134. [Google Scholar] [CrossRef]
- Pustokhina, I.V.; Pustokhin, D.A.; Lydia, E.L.; Elhoseny, M.; Shankar, K. Energy efficient neuro-fuzzy cluster based to-pology construction with metaheuristic route planning algorithm for unmanned aerial vehicles. Comput. Netw. 2021, 196, 108214. [Google Scholar] [CrossRef]
- Viswanathan, S.; Bhuvaneswaran, R.S.; Ganapathy, S.; Kannan, A. Euler Phi Function and Gamma Function Based Elliptic Curve Encryption for Secured Group Communication. Wirel. Pers. Commun. 2022, 125, 421–451. [Google Scholar] [CrossRef]


| File Size (Bytes) | AES Protocol | FGECDH Protocol | EESRA Protocol | FHEOKG-SGC |
|---|---|---|---|---|
| Key Generation Time (ms) | ||||
| 1024 | 1696 | 1678 | 1661 | 1616 |
| 2048 | 1773 | 1753 | 1739 | 1678 |
| 4096 | 1951 | 1886 | 1825 | 1802 |
| 8192 | 2216 | 2160 | 2124 | 2105 |
| Encryption Time (ms) | ||||
| 1024 | 2264 | 2182 | 2171 | 2107 |
| 2048 | 2338 | 2312 | 2283 | 2245 |
| 4096 | 2511 | 2461 | 2443 | 2431 |
| 8192 | 3020 | 2947 | 2916 | 2903 |
| Decryption Time (ms) | ||||
| 1024 | 2676 | 2238 | 1831 | 1625 |
| 2048 | 2665 | 2196 | 1817 | 1621 |
| 4096 | 2654 | 2125 | 1766 | 1592 |
| 8192 | 2541 | 2026 | 1725 | 1558 |
| Encrypted File Size (Bytes) | ||||
| 1024 | 1912 | 1780 | 1584 | 1531 |
| 2048 | 3624 | 1893 | 1829 | 1812 |
| 4096 | 5757 | 2060 | 2026 | 2107 |
| 8192 | 13246 | 8273 | 8794 | 8170 |
| Packet Loss Rate (%) | |||||
|---|---|---|---|---|---|
| No. of Tests | LEACH | AES Protocol | FGECDH Protocol | EESRA Protocol | FHEOKG-SGC |
| Test-1 | 26.75 | 27.35 | 24.59 | 22.72 | 19.45 |
| Test-2 | 25.23 | 26.32 | 22.37 | 21.67 | 19.1 |
| Test-3 | 23.89 | 24.68 | 22.12 | 20.97 | 19.48 |
| Test-4 | 24.16 | 25.74 | 23.87 | 19.51 | 18.98 |
| Test-5 | 26.09 | 23.65 | 21.47 | 18.34 | 17.69 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Albakri, A.; Alshahrani, R.; Alharbi, F.; Ahamed, S.B. Fully Homomorphic Encryption with Optimal Key Generation Secure Group Communication in Internet of Things Environment. Appl. Sci. 2023, 13, 6055. https://doi.org/10.3390/app13106055
Albakri A, Alshahrani R, Alharbi F, Ahamed SB. Fully Homomorphic Encryption with Optimal Key Generation Secure Group Communication in Internet of Things Environment. Applied Sciences. 2023; 13(10):6055. https://doi.org/10.3390/app13106055
Chicago/Turabian StyleAlbakri, Ashwag, Reem Alshahrani, Fares Alharbi, and Saahira Banu Ahamed. 2023. "Fully Homomorphic Encryption with Optimal Key Generation Secure Group Communication in Internet of Things Environment" Applied Sciences 13, no. 10: 6055. https://doi.org/10.3390/app13106055
APA StyleAlbakri, A., Alshahrani, R., Alharbi, F., & Ahamed, S. B. (2023). Fully Homomorphic Encryption with Optimal Key Generation Secure Group Communication in Internet of Things Environment. Applied Sciences, 13(10), 6055. https://doi.org/10.3390/app13106055






