Low-Quality Integrated Circuits Image Verification Based on Low-Rank Subspace Clustering with High-Frequency Texture Components
Abstract
1. Introduction
- (1)
- Unlike SEM, which uses a narrowly focused high-energy electron beam to scan the sample and sweep the image elements from left to right and from top to bottom on a sample to obtain a high-precision, full-range image in a single pass, the workflow of a normal camera with a microscope is still to capture different partial views several times and finally combine them into a complete large image.
- (2)
- For the sensor on the camera, the unstable temperature and light source of the acquisition environment can bring about changes in the signal-to-noise ratio (SNR), and images with low SNRs often contain a variety of noises.
- (3)
- Image data may be corrupted when uploading from the camera to the server, such as due to multiplicative noise caused by unsatisfactory channels.
2. Background Knowledge
2.1. Low-Rank Representation
2.2. High-Frequency Texture Component
3. The Proposed Approach
3.1. Proposed Framework
3.2. Solution to HFLRSC
| Algorithm 1: The algorithm of HFLRSC. |
 |
4. Experimental Study
4.1. Data Preparation
4.2. Comparison Methods
4.3. Results and Analyses
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Hao, Q.; Zhang, Z.; Xu, D.; Wang, J.; Liu, J.; Zhang, J.; Ma, J.; Wang, X. A hardware security-monitoring architecture based on data integrity and control flow integrity for embedded systems. Appl. Sci. 2022, 12, 7750. [Google Scholar] [CrossRef]
- Lu, H.; Capecci, D.E.; Ghosh, P.; Forte, D.; Woodard, D.L. Computer vision for hardware security. In Emerging Topics in Hardware Security; Springer: Cham, Switzerland, 2021; pp. 493–525. [Google Scholar]
- Wang, X.; Zhang, Z.; Xu, Y.; Zhang, L.; Yan, R.; Chen, X. Real-time minor defect recognition of pseudo-terahertz images via the improved yolo network. In Proceedings of the 2021 International Conference on Sensing, Measurement & Data Analytics in the era of Artificial Intelligence (ICSMD), Nanjing, China, 21–23 October 2021; pp. 1–6. [Google Scholar]
- Zhou, B.; Aksoylar, A.; Vigil, K.; Adato, R.; Tan, J.; Goldberg, B.; Ünlü, M.S.; Joshi, A. Hardware trojan detection using backside optical imaging. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. 2020, 40, 24–37. [Google Scholar] [CrossRef]
- Rosso, D. Annual Semiconductor Sales Increase 21.6 Percent, Top 400 Billion for First Time; Semiconductor Industry Association: Washington, DC, USA, 2018; Volume 1. [Google Scholar]
- Xue, M.; Bian, R.; Wang, J.; Liu, W. Building an accurate hardware trojan detection technique from inaccurate simulation models and unlabelled ics. IET Comput. Digit. Tech. 2019, 13, 348–359. [Google Scholar] [CrossRef]
- Ye, M.; Zhang, D.; Yap, Y.K. Recent advances in electronic and optoelectronic devices based on two-dimensional transition metal dichalcogenides. Electronics 2017, 6, 43. [Google Scholar] [CrossRef]
- Kaintura, A.; Dhaene, T.; Spina, D. Review of polynomial chaos-based methods for uncertainty quantification in modern integrated circuits. Electronics 2018, 7, 30. [Google Scholar] [CrossRef]
- Jin, Y.; Makris, Y. Hardware trojan detection using path delay fingerprint. In Proceedings of the 2008 IEEE International Workshop on Hardware-Oriented Security and Trust, Anaheim, CA, USA, 9 June 2008; pp. 51–57. [Google Scholar]
- Gayatri, R.; Gayatri, Y.; Mitra, C.; Mekala, S.; Priyatharishini, M. System level hardware trojan detection using side-channel power analysis and machine learning. In Proceedings of the 2020 5th International Conference on Communication and Electronics Systems (ICCES), Coimbatore, India, 10–12 June 2020; pp. 650–654. [Google Scholar]
- Liakos, K.G.; Georgakilas, G.K.; Plessas, F.C. Hardware trojan classification at gate-level netlists based on area and power machine learning analysis. In Proceedings of the 2021 IEEE Computer Society Annual Symposium on VLSI (ISVLSI), Tampa, FL, USA, 7–9 July 2021; pp. 412–417. [Google Scholar]
- Nasr, A.A.; Abdulmageed, M.Z. Automatic feature selection of hardware layout: A step toward robust hardware trojan detection. J. Electron. Test. 2016, 32, 357–367. [Google Scholar] [CrossRef]
- Kulkarni, A.; Pino, Y.; Mohsenin, T. Svm-based real-time hardware trojan detection for many-core platform. In Proceedings of the 2016 17th International Symposium on Quality Electronic Design (ISQED), Santa Clara, CA, USA, 15–16 March 2016; pp. 362–367. [Google Scholar]
- Hasegawa, K.; Oya, M.; Yanagisawa, M.; Togawa, N. Hardware trojans classification for gate-level netlists based on machine learning. In Proceedings of the 2016 IEEE 22nd International Symposium on On-Line Testing and Robust System Design (IOLTS), Sant Feliu de Guixols, Spain, 4–6 July 2016; pp. 203–206. [Google Scholar]
- Kulkarni, A.; Pino, Y.; Mohsenin, T. Adaptive real-time trojan detection framework through machine learning. In Proceedings of the 2016 IEEE International Symposium on Hardware Oriented Security and Trust (HOST), McLean, VA, USA, 3–5 May 2016; pp. 120–123. [Google Scholar]
- Vishnupriya, R.; Devi, M.N. Hardware trojan detection using deep learning-deep stacked auto encoder. In Proceedings of the International Conference on Recent Trends in Machine Learning, IoT, Smart Cities and Applications, Hyderabad, India, 28–29 March 2021; Springer: Singapore, 2021; pp. 345–353. [Google Scholar]
- Yasaei, R.; Yu, S.-Y.; Faruque, M.A.A. Gnn4tj: Graph neural networks for hardware trojan detection at register transfer level. In Proceedings of the 2021 Design, Automation & Test in Europe Conference & Exhibition (DATE), Grenoble, France, 1–5 February 2021; pp. 1504–1509. [Google Scholar]
- Muralidhar, N.; Zubair, A.; Weidler, N.; Gerdes, R.; Ramakrishnan, N. Contrastive graph convolutional networks for hardware trojan detection in third party ip cores. In Proceedings of the 2021 IEEE International Symposium on Hardware Oriented Security and Trust (HOST), Tysons Corner, VA, USA, 12–15 December 2021. [Google Scholar]
- Sharma, R.; Sharma, G.; Pattanaik, M. A few shot learning based approach for hardware trojan detection using deep siamese cnn. In Proceedings of the 2021 34th International Conference on VLSI Design and 2021 20th International Conference on Embedded Systems (VLSID), Guwahati, India, 20–24 February 2021; pp. 163–168. [Google Scholar]
- Hasegawa, K.; Yamashita, K.; Hidano, S.; Fukushima, K.; Hashimoto, K.; Togawa, N. Node-wise hardware trojan detection based on graph learning. arXiv 2021, arXiv:2112.02213. [Google Scholar]
- Wei, L.; Wang, X.; Wu, A.; Zhou, R.; Zhu, C. Robust subspace segmentation by self-representation constrained low-rank representation. Neural Process. Lett. 2018, 48, 1671–1691. [Google Scholar] [CrossRef]
- Göçeri, E. Impact of deep learning and smartphone technologies in dermatology: Automated diagnosis. In Proceedings of the 2020 Tenth International Conference on Image Processing Theory, Tools and Applications (IPTA), Paris, France, 9–12 November 2020; pp. 1–6. [Google Scholar]
- Liu, G.; Lin, Z.; Yan, S.; Sun, J.; Yu, Y.; Ma, Y. Robust recovery of subspace structures by low-rank representation. IEEE Trans. Pattern Anal. Mach. Intell. 2012, 35, 171–184. [Google Scholar] [CrossRef] [PubMed]
- Bertsekas, D.P. On penalty and multiplier methods for constrained minimization. SIAM J. Control. Optim. 1976, 14, 216–235. [Google Scholar] [CrossRef]
- Elhamifar, E.; Vidal, R. Sparse subspace clustering: Algorithm, theory, and applications. IEEE Trans. Pattern Anal. Mach. Intell. 2013, 35, 2765–2781. [Google Scholar] [CrossRef] [PubMed]
- Cai, X.; Huang, D.; Wang, C.-D.; Kwoh, C.-K. Spectral clustering by subspace randomization and graph fusion for high-dimensional data. In Pacific-Asia Conference on Knowledge Discovery and Data Mining; Springer: Cham, Switzerland, 2020; pp. 330–342. [Google Scholar]
- Huang, D.; Wang, C.-D.; Wu, J.-S.; Lai, J.-H.; Kwoh, C.-K. Ultra-scalable spectral clustering and ensemble clustering. IEEE Trans. Knowl. Data Eng. 2019, 32, 1212–1226. [Google Scholar] [CrossRef]
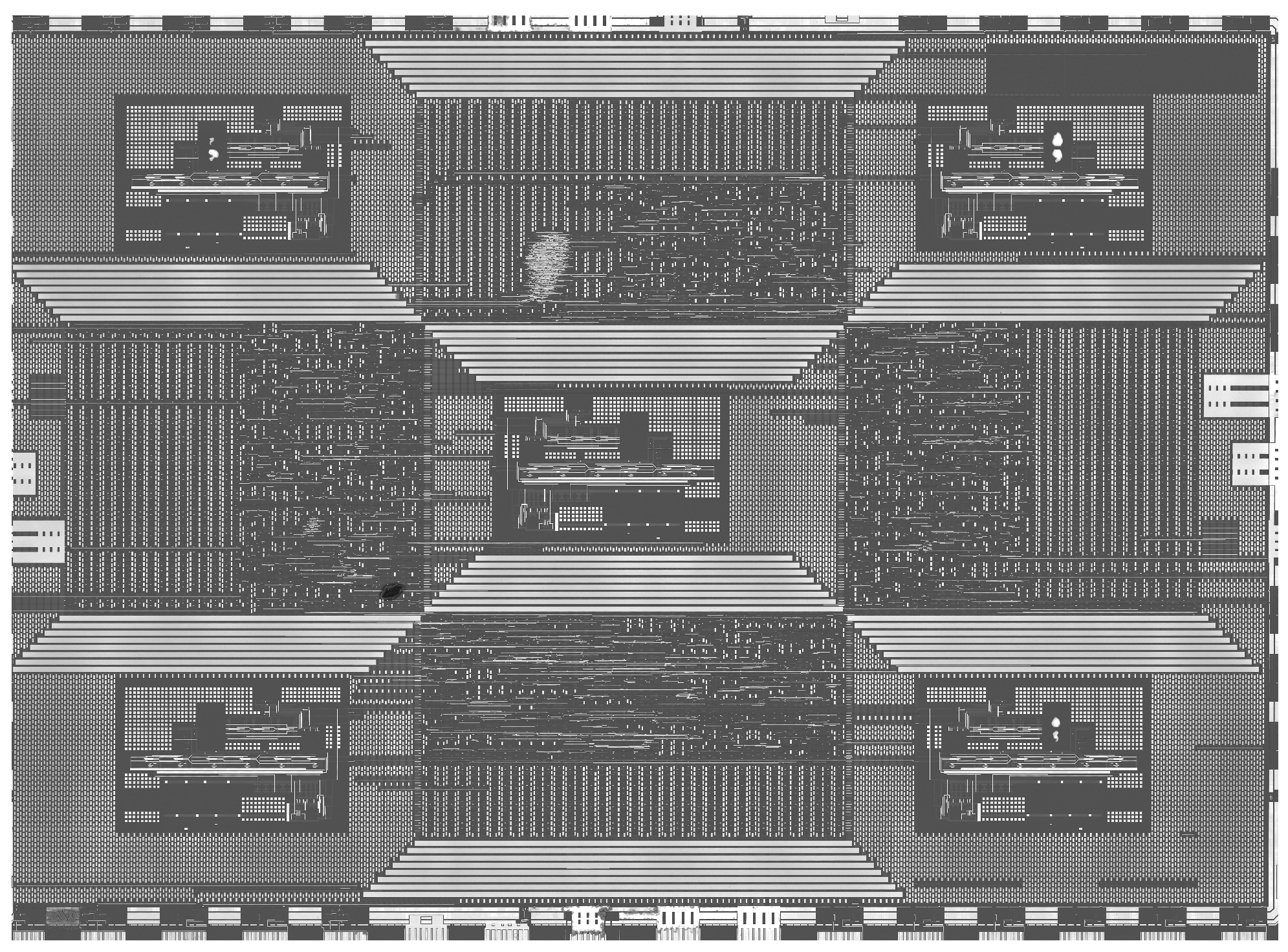


| Index | Noise | Defects |
|---|---|---|
| 1 | Gaussian 0.1 | 10 |
| 2 | Gaussian 0.2 | 10 |
| 3 | Gaussian 0.4 | 10 |
| 4 | Gaussian 0.6 | 10 |
| 5 | Salt-and-Pepper 0.1 | 10 |
| 6 | Salt-and-Pepper 0.2 | 10 |
| 7 | Salt-and-Pepper 0.4 | 10 |
| 8 | Salt-and-Pepper 0.6 | 10 |
| 9 | Multiplicative 0.01 | 10 |
| 10 | Multiplicative 0.1 | 10 |
| 11 | Multiplicative 0.15 | 10 |
| 12 | Multiplicative 0.2 | 10 |
| Datasets | Methods | ACC | NMI | Purity | F | ARI |
|---|---|---|---|---|---|---|
| 1 | HFLRSC | 100.00 | 100.00 | 100.00 | 100.00 | 100.00 |
| NCut | 88.20 | 94.31 | 90.17 | 88.11 | 87.01 | |
| K-means | 73.94 | 85.24 | 76.54 | 73.46 | 70.79 | |
| LRR | 97.97 | 99.16 | 98.50 | 98.11 | 97.95 | |
| SSC | 100.00 | 100.00 | 100.00 | 100.00 | 100.00 | |
| SC-SRGF | 92.22 | 96.58 | 94.02 | 92.54 | 91.89 | |
| USENC | 100.00 | 100.00 | 100.00 | 100.00 | 100.00 | |
| 2 | HFLRSC | 98.33 | 97.75 | 98.33 | 96.49 | 96.20 |
| NCut | 87.03 | 93.32 | 89.50 | 86.69 | 85.49 | |
| K-means | 68.03 | 79.23 | 70.63 | 64.85 | 61.20 | |
| LRR | 97.42 | 98.98 | 98.17 | 97.65 | 97.45 | |
| SSC | 93.33 | 92.33 | 93.33 | 86.47 | 85.34 | |
| SC-SRGF | 88.33 | 95.35 | 91.67 | 89.27 | 88.33 | |
| USENC | 93.13 | 95.95 | 93.88 | 92.33 | 91.64 | |
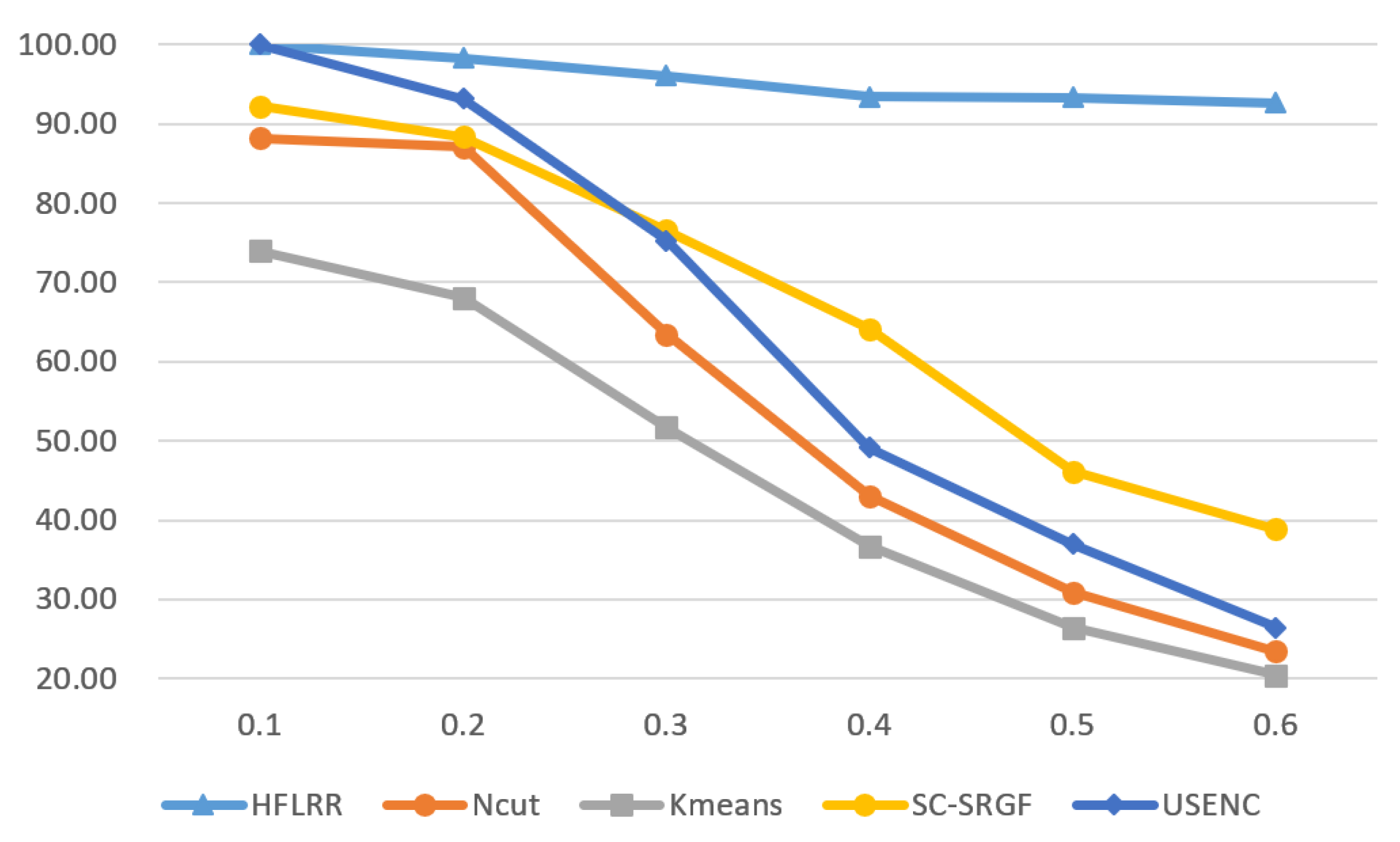
| 3 | HFLRSC | 93.40 | 91.37 | 93.40 | 86.47 | 85.36 |
| NCut | 43.05 | 47.87 | 44.77 | 28.59 | 22.31 | |
| K-means | 36.75 | 41.23 | 38.78 | 26.42 | 18.13 | |
| LRR | 80.81 | 79.46 | 81.13 | 66.37 | 63.50 | |
| SSC | 73.50 | 67.50 | 73.92 | 48.18 | 43.20 | |
| SC-SRGF | 64.15 | 63.65 | 65.97 | 46.61 | 42.06 | |
| USENC | 49.17 | 53.75 | 50.58 | 35.59 | 29.90 | |
| 4 | HFLRSC | 92.62 | 90.72 | 92.62 | 83.74 | 82.37 |
| NCut | 23.42 | 25.77 | 24.60 | 12.17 | 2.75 | |
| K-means | 20.46 | 19.53 | 21.45 | 11.62 | 0.00 | |
| LRR | 37.12 | 38.93 | 38.85 | 19.50 | 12.31 | |
| SSC | 27.17 | 32.20 | 28.83 | 13.44 | 5.53 | |
| SC-SRGF | 38.90 | 39.82 | 40.83 | 22.05 | 15.26 | |
| USENC | 26.46 | 28.86 | 27.58 | 14.47 | 5.43 | |
| 5 | HFLRSC | 100.00 | 100.00 | 100.00 | 100.00 | 100.00 |
| NCut | 90.92 | 95.91 | 92.67 | 91.37 | 90.59 | |
| K-means | 71.10 | 82.77 | 73.69 | 69.34 | 66.18 | |
| LRR | 100.00 | 100.00 | 100.00 | 100.00 | 100.00 | |
| SSC | 100.00 | 100.00 | 100.00 | 100.00 | 100.00 | |
| SC-SRGF | 100.00 | 100.00 | 100.00 | 100.00 | 100.00 | |
| USENC | 100.00 | 100.00 | 100.00 | 100.00 | 100.00 | |
| 6 | HFLRSC | 100.00 | 100.00 | 100.00 | 100.00 | 100.00 |
| NCut | 88.65 | 94.13 | 90.45 | 88.40 | 87.35 | |
| K-means | 68.06 | 78.75 | 70.55 | 64.68 | 61.15 | |
| LRR | 95.67 | 98.23 | 96.83 | 96.01 | 95.66 | |
| SSC | 100.00 | 100.00 | 100.00 | 100.00 | 100.00 | |
| SC-SRGF | 94.72 | 94.92 | 95.02 | 91.77 | 91.08 | |
| USENC | 96.63 | 98.22 | 97.04 | 96.40 | 96.08 | |
| 7 | HFLRSC | 100.00 | 100.00 | 100.00 | 100.00 | 100.00 |
| NCut | 78.98 | 86.87 | 81.40 | 76.16 | 74.02 | |
| K-means | 59.77 | 64.94 | 62.67 | 49.17 | 44.34 | |
| LRR | 92.08 | 95.83 | 93.70 | 91.57 | 90.83 | |
| SSC | 96.58 | 96.41 | 96.58 | 93.40 | 92.86 | |
| SC-SRGF | 90.42 | 92.94 | 91.55 | 87.14 | 86.05 | |
| USENC | 90.29 | 93.79 | 91.25 | 88.48 | 87.48 | |
| 8 | HFLRSC | 95.23 | 93.75 | 95.23 | 89.61 | 88.75 |
| NCut | 59.30 | 66.47 | 61.17 | 49.10 | 44.68 | |
| K-means | 48.69 | 50.90 | 51.68 | 32.89 | 26.73 | |
| LRR | 85.78 | 86.94 | 85.83 | 76.80 | 74.85 | |
| SSC | 75.50 | 73.28 | 75.50 | 52.70 | 48.12 | |
| SC-SRGF | 71.47 | 71.77 | 72.40 | 55.89 | 52.17 | |
| USENC | 54.67 | 57.16 | 56.46 | 37.81 | 32.37 | |
| 9 | HFLRSC | 100.00 | 100.00 | 100.00 | 100.00 | 100.00 |
| NCut | 91.37 | 95.97 | 92.83 | 91.63 | 90.87 | |
| K-means | 71.67 | 84.18 | 74.62 | 71.70 | 68.83 | |
| LRR | 99.12 | 99.63 | 99.33 | 99.17 | 99.09 | |
| SSC | 100.00 | 100.00 | 100.00 | 100.00 | 100.00 | |
| SC-SRGF | 100.00 | 100.00 | 100.00 | 100.00 | 100.00 | |
| USENC | 98.46 | 98.94 | 98.67 | 98.02 | 97.84 | |
| 10 | HFLRSC | 100.00 | 100.00 | 100.00 | 100.00 | 100.00 |
| NCut | 82.82 | 89.03 | 85.10 | 80.15 | 78.36 | |
| K-means | 57.20 | 63.51 | 61.38 | 44.61 | 38.83 | |
| LRR | 98.90 | 99.54 | 99.17 | 98.95 | 98.86 | |
| SSC | 95.83 | 95.31 | 95.83 | 91.69 | 91.00 | |
| SC-SRGF | 89.93 | 89.72 | 89.95 | 83.10 | 81.70 | |
| USENC | 88.79 | 89.46 | 89.63 | 82.50 | 80.99 | |
| 11 | HFLRSC | 100.00 | 100.00 | 100.00 | 100.00 | 100.00 |
| NCut | 71.45 | 76.92 | 72.77 | 63.55 | 60.35 | |
| K-means | 52.20 | 55.65 | 55.89 | 36.86 | 30.48 | |
| LRR | 89.37 | 89.41 | 90.38 | 80.02 | 78.26 | |
| SSC | 87.83 | 85.71 | 87.83 | 76.05 | 73.98 | |
| SC-SRGF | 83.50 | 84.49 | 84.73 | 75.85 | 73.83 | |
| USENC | 81.46 | 81.76 | 82.79 | 70.22 | 67.62 | |
| 12 | HFLRSC | 99.17 | 98.88 | 99.17 | 98.24 | 98.10 |
| NCut | 58.32 | 63.05 | 60.10 | 45.04 | 40.29 | |
| K-means | 46.56 | 48.47 | 50.24 | 29.39 | 22.36 | |
| LRR | 83.68 | 83.71 | 83.92 | 69.75 | 67.04 | |
| SSC | 85.58 | 82.37 | 85.58 | 70.23 | 67.62 | |
| SC-SRGF | 75.73 | 73.50 | 75.98 | 59.88 | 56.50 | |
| USENC | 46.96 | 48.12 | 48.54 | 27.86 | 21.27 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tan, G.; Liang, Z.; Chi, Y.; Li, Q.; Peng, B.; Liu, Y.; Li, J. Low-Quality Integrated Circuits Image Verification Based on Low-Rank Subspace Clustering with High-Frequency Texture Components. Appl. Sci. 2023, 13, 155. https://doi.org/10.3390/app13010155
Tan G, Liang Z, Chi Y, Li Q, Peng B, Liu Y, Li J. Low-Quality Integrated Circuits Image Verification Based on Low-Rank Subspace Clustering with High-Frequency Texture Components. Applied Sciences. 2023; 13(1):155. https://doi.org/10.3390/app13010155
Chicago/Turabian StyleTan, Guoliang, Zexiao Liang, Yuan Chi, Qian Li, Bin Peng, Yuan Liu, and Jianzhong Li. 2023. "Low-Quality Integrated Circuits Image Verification Based on Low-Rank Subspace Clustering with High-Frequency Texture Components" Applied Sciences 13, no. 1: 155. https://doi.org/10.3390/app13010155
APA StyleTan, G., Liang, Z., Chi, Y., Li, Q., Peng, B., Liu, Y., & Li, J. (2023). Low-Quality Integrated Circuits Image Verification Based on Low-Rank Subspace Clustering with High-Frequency Texture Components. Applied Sciences, 13(1), 155. https://doi.org/10.3390/app13010155






