Securing Remote State Estimation against Sequential Logic Attack of Sensor Data
Abstract
1. Introduction
2. Related Work
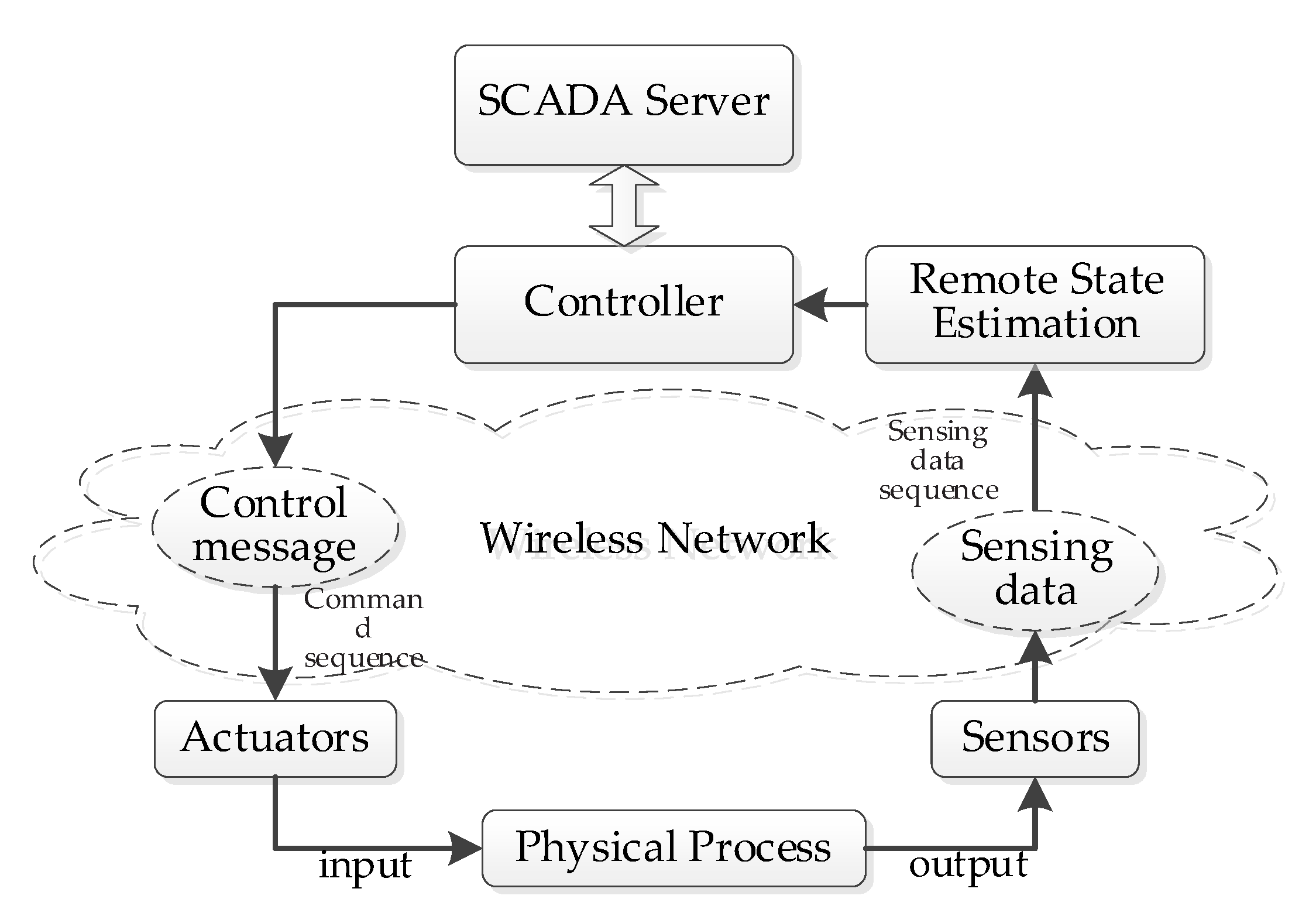
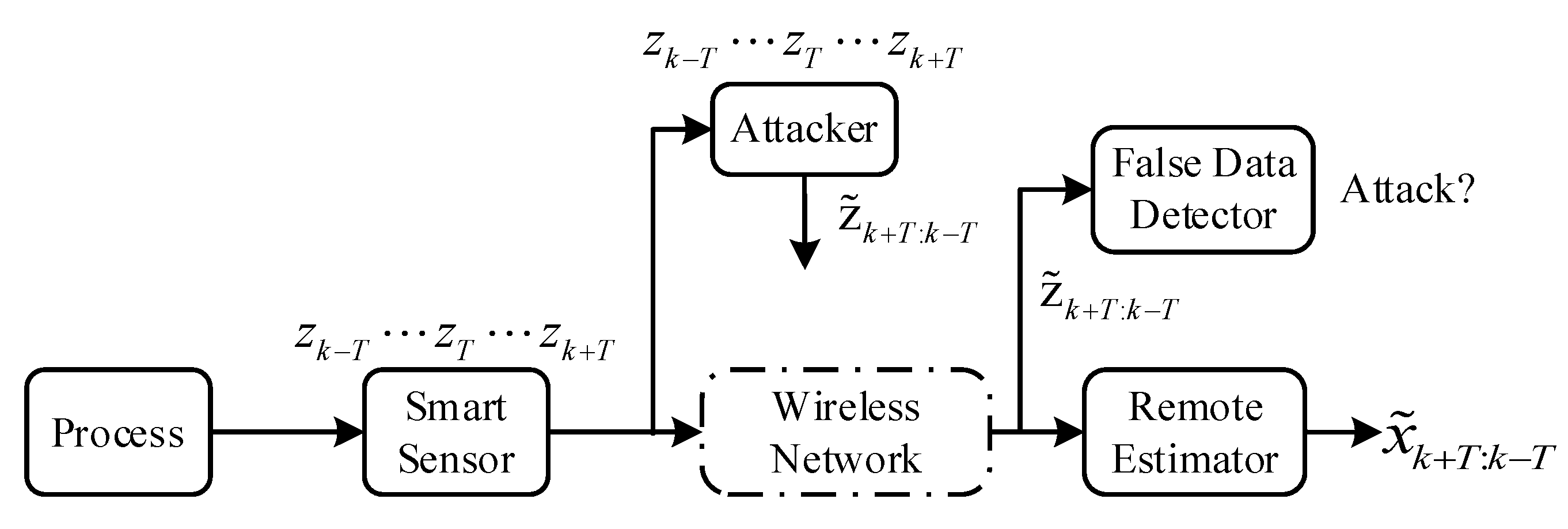
3. Network and Attack Model
4. Sequential Signature Transmission Scheme for Sensor Data
| Algorithm 1. Sequential signature algorithm |
| Key generation of the remote state estimation system (R): Input: The parameter n represents the number of strings, l represents the length of the string, and k represents the number of substrings. . with different lengths; ; ; . Signature generation of sensor node (SN): . . ; with a length of log2 n bit; ; of ; Signature verification of the remote state estimation system (R): ; is the threshold value; If the conditions are met, verify the signature further, otherwise discard the data; ; with a length of log2 n bit ; , it is accepted; otherwise it is rejected. |
5. Security Analysis and Proof
5.1. Security Analysis
5.2. Security Proof
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Serpanos, D. The Cyber-Physical Systems Revolution. Computer 2018, 51, 70–73. [Google Scholar] [CrossRef]
- Ochoa, S.F.; Fortino, G.; Fatta, G.D. Cyber-physical systems, internet of things and big data. Futur. Gener. Comput. Syst. 2017, 75, 82–84. [Google Scholar] [CrossRef]
- Asghar, M.R.; Hu, Q.; Zeadally, S. Cybersecurity in industrial control systems: Issues, technologies, and challenges. Comput. Netw. 2019, 165, 106946. [Google Scholar] [CrossRef]
- Yadav, G.; Paul, K. Architecture and security of SCADA systems: A review. Int. J. Crit. Infrastruct. Prot. 2021, 34, 100433. [Google Scholar] [CrossRef]
- Rodofile, N.R.; Radke, K.; Foo, E. Extending the cyber-attack landscape for SCADA-based critical infrastructure. Int. J. Crit. Infrastruct. Prot. 2019, 25, 14–35. [Google Scholar] [CrossRef]
- Pliatsios, D.; Sarigiannidis, P.; Lagkas, T.; Sarigiannidis, A.G. A Survey on SCADA Systems: Secure Protocols, Incidents, Threats and Tactics. IEEE Commun. Surv. Tutor. 2020, 22, 1942–1976. [Google Scholar] [CrossRef]
- Caselli, M.; Zambon, E.; Petit, J.; Kargl, F. Modeling Message Sequences for Intrusion Detection in Industrial Control Systems. In Proceedings of the International Conference on Critical Infrastructure Protection, Arlington, VA, USA, 16–18 March 2015; Springer International Publishing: Berlin/Heidelberg, Germany, 2015. [Google Scholar]
- Fovino, I.N.; Carcano, A.; Murel, T.D.L.; Trombetta, A.; Masera, M. Modbus/DNP3 State-Based Intrusion Detection System. In Proceedings of the 2010 24th IEEE International Conference on Advanced Information Networking and Applications, Perth, WA, Australia, 20–23 April 2010; pp. 729–736. [Google Scholar]
- Ellis, J.; Fisher, D.; Longstaff, T.; Pesante, L.; Pethia, R. Report to the President’s Commission on Critical Infrastructure Protection; Carnegie-Mellon Univ Pittsburgh PA Software Engineering Inst: Pittsburgh, PA, USA, 1997. [Google Scholar]
- Nourian, A.; Madnick, S. A Systems Theoretic Approach to the Security Threats in Cyber Physical Systems Applied to Stuxnet. IEEE Trans. Dependable Secur. Comput. 2018, 15, 2–13. [Google Scholar] [CrossRef]
- Kleinmann, A.; Amichay, O.; Wool, A.; Tenenbaum, D.; Bar, O.; Lev, L. Stealthy Deception Attacks against SCADA Systems. In Proceedings of the Computer Security, SECPRE 2017, CyberICPS 2017, Oslo, Norway, 14–15 September 2017; Springer: Cham, Switzerland, 2017. [Google Scholar]
- Ghaleb, A.; Zhioua, S.; Almulhem, A. On PLC network security. Int. J. Crit. Infrastruct. Prot. 2018, 22, 62–69. [Google Scholar] [CrossRef]
- Hu, Y.; Sun, Y.; Wang, Y.; Wang, Z. An Enhanced Multi-Stage Semantic Attack against Industrial Control Systems. IEEE Access. 2019, 7, 156871–156882. [Google Scholar] [CrossRef]
- Karimipour, H.; Dinavahi, V. On false data injection attack against dynamic state estimation on smart power grids. In Proceedings of the 2017 IEEE International Conference on Smart Energy Grid Engineering (SEGE), Oshawa, ON, Canada, 14–17 August 2017; pp. 388–393. [Google Scholar]
- Khatibi, M.; Ahmed, S. Optimal resilient defense strategy against false data injection attacks on power system state estimation. In Proceedings of the 2018 IEEE Power & Energy Society Innovative Smart Grid Technologies Conference (ISGT), Washington, DC, USA, 19–22 February 2018; pp. 1–5. [Google Scholar]
- Liu, H.; Ni, Y.; Xie, L.; Johansson, K.H. An Optimal Linear Attack Strategy on Remote State Estimation. IFAC-PapersOnLine 2020, 53, 3527–3532. [Google Scholar] [CrossRef]
- Govil, N.; Agrawal, A.; Tippenhauer, N.O. On Ladder Logic Bombs in Industrial Control Systems. In Proceedings of the Computer Security, SECPRE 2017, CyberICPS 2017, Oslo, Norway, 14–15 September 2017; Springer: Cham, Switzerland, 2017; Volume 10683. [Google Scholar]
- Guo, Z.; Johansson, K.H.; Shi, L. A study of packet-reordering integrity attack on remote state estimation. In Proceedings of the 35th IEEE Chinese Control Conference (CCC), Chengdu, China, 27–29 July 2016; pp. 7250–7255. [Google Scholar]
- IEEE Std 1815-2012; IEEE Standard for Electric Power Systems Communications. Distributed Network Protocol. 2012. Available online: https://standards.ieee.org/findstds/standard/1815-2012.html (accessed on 20 December 2021).
- LAMPORTL. Constructing Digital Signatures from a One-Way Function; Technical Report; Technical Report CSL-98; SRI International: Menlo Park, CA, USA, 1979. [Google Scholar]
- Shor, W.P. Algorithms for quantum computation: Discrete logarithms and factoring. In Proceedings of the 35th Annual Symposium on Foundations of Computer Science, Santa Fe, NM, USA, 20–22 November 1994; pp. 124–134. [Google Scholar]
- Perrig, A. The BiBa one-time signature and broadcast authentication protocol. In Proceedings of the ACM CCS, Philadelphia, PA, USA, 5–8 November 2001; pp. 28–37. [Google Scholar]
- Reyzin, L.; Reyzin, N. Better than BiBa: Short one-time signatures with fast signing and verifying. In Proceedings of the Information Security and Privacy Conference, Melbourne, Australia, 3–5 July 2002; LNCS 2384. pp. 144–153. [Google Scholar]
- Park, Y.; Cho, Y. Efficient one-time signature schemes for stream authentication. J. Inf. Sci. Eng. 2006, 22, 611–624. [Google Scholar]
- Mitzenmacher, M.; Perrig, A. Bounds and Improvements for BiBa Signature Schemes; No. TR-02-02; Harvard University Computer Science Group Technical Report TR-02-02; Harvard University Computer Science Group: Cambridge, MA, USA, 2002; pp. 1–15. [Google Scholar]
- Wang, Q.; Khurana, H.; Huang, Y.; Nahrstedt, K. Time valid onetime signature for time-critical multicast data authentication. In Proceedings of the IEEE INFOCOM 2009, Rio de Janeiro, Brazil, 19–25 April 2009; pp. 1233–1241. [Google Scholar]
- Pieprzyk, J.; Wang, H.; Xing, C. Multiple-time signature schemes against adaptive chosen message attacks. In Proceedings of the Selected Areas in Cryptography, Ottawa, ON, Canada, 14–15 August 2003; LNCS 3000. pp. 88–100. [Google Scholar]
- Zaverucha, G.M.; Stinson, D.R. Short One-Time Signatures. Adv. Math. Commun. 2011, 5, 473–488. [Google Scholar]
- Kalach, K.; Safavi-Naini, R. An efficient post-quantum one-time signature scheme. In Proceedings of the International Conference on Selected Areas in Cryptography, Sackville, NB, Canada, 12–14 August 2015; Springer International Publishing: Berlin/Heidelberg, Germany, 2015; pp. 331–351. [Google Scholar]
- Abe, M.; David, B.; Kohlweiss, M. Tagged one-time signatures: Tight security and optimal tag size. In Proceedings of the International Workshop on Public Key Cryptography, Nara, Japan, 26 February–1 March 2013; Springer: Berlin/Heidelberg, Germany, 2013; pp. 312–331. [Google Scholar]
- Merkle, R. A digital signature based on a conventional encryption function. In Proceedings of the Advances in Cryptology—CRYPTO1987, Santa Barbara, CA, USA, 16–20 August 1987; Springer: Berlin/Heidelberg, Germany, 1988; pp. 369–378. [Google Scholar]
- Shoufan, A.; Huber, N.; Molter, H.G. A novel crypto processor architecture for chained Merkle signature scheme. Microprocess. Microsyst. 2011, 35, 34–47. [Google Scholar] [CrossRef]
- Katti, R.S.; Sule, R.; Kavasseri, R.G. Multicast authentication in the smart grid with one-time signatures from sigma-protocols. In Proceedings of the ACM/IEEE 4th International Conference on Cyber-Physical Systems, Philadelphia, PA, USA, 8–11 April 2013; p. 239. [Google Scholar]
- Li, Q.; Cao, G. Multicast authentication in the smart grid with one-time signature. IEEE Trans. Smart Grid 2011, 2, 686–696. [Google Scholar] [CrossRef]
- Zhang, J.W.; Ma, J.F.; Wen, X.Z. Universally composable one-time signature and broadcast authentication. Sci. China Inf. Sci. 2010, 40, 272–284. [Google Scholar] [CrossRef][Green Version]
- Groza, B.; Murvay, S. Secure broadcast with one-time signatures in controller area networks. In Proceedings of the 2011 IEEE Sixth International Conference on Availability, Reliability and Security (ARES), Vienna, Austria, 22–26 August 2011; pp. 371–376. [Google Scholar]
- Buchmann, J.; Dahmen, E.; Ereth, S.; Hülsing, A.; Rückert, M. On the security of the Winternitz one-time signature scheme. In Proceedings of the International Conference on Cryptology in Africa, Dakar, Senegal, 5–7 July 2011; Springer: Berlin/Heidelberg, Germany, 2011; pp. 363–378. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, J.; Feng, T. Securing Remote State Estimation against Sequential Logic Attack of Sensor Data. Appl. Sci. 2022, 12, 2259. https://doi.org/10.3390/app12042259
Wang J, Feng T. Securing Remote State Estimation against Sequential Logic Attack of Sensor Data. Applied Sciences. 2022; 12(4):2259. https://doi.org/10.3390/app12042259
Chicago/Turabian StyleWang, Jing, and Tao Feng. 2022. "Securing Remote State Estimation against Sequential Logic Attack of Sensor Data" Applied Sciences 12, no. 4: 2259. https://doi.org/10.3390/app12042259
APA StyleWang, J., & Feng, T. (2022). Securing Remote State Estimation against Sequential Logic Attack of Sensor Data. Applied Sciences, 12(4), 2259. https://doi.org/10.3390/app12042259




