Robust Resource Allocation and Trajectory Planning of UAV-Aided Mobile Edge Computing in Post-Disaster Areas
Abstract
:1. Introduction
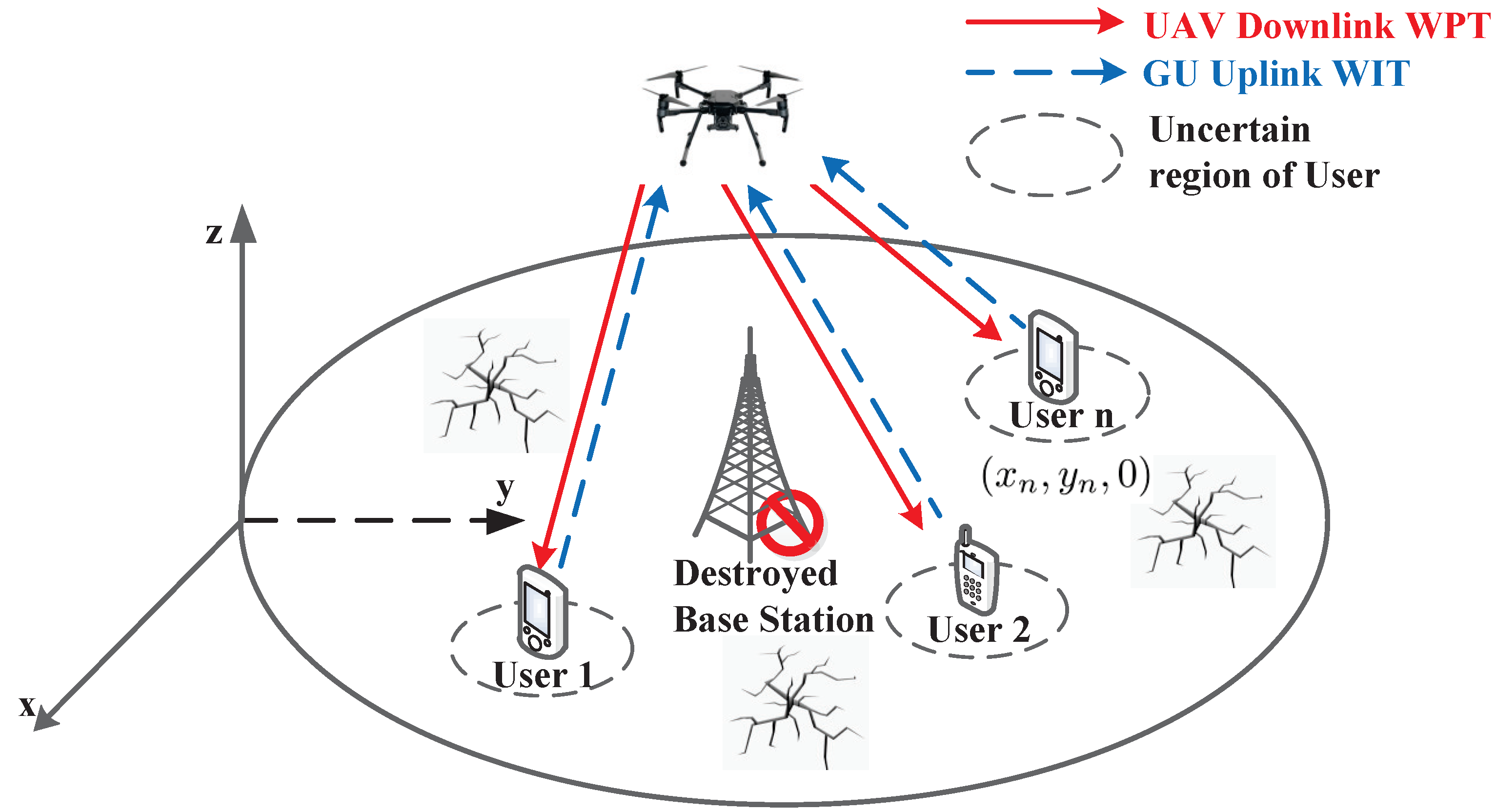
- We propose a UAV-enabled wireless-powered MEC system in a post-disaster area, while the imperfect location of users is considered. To ensure users have enough power in the post-disaster area, UAV provides charging and computing services for users.
- We propose a joint resource allocation and trajectory planning algorithm under known users’ location to solve the strong coupling between optimization variables.
- We propose a robust cutting-set method to degrade the influence of worst-case location of users on optimization.
2. System Model and Problem Formulation
3. Joint Resource Allocation and Trajectory Planning under Known Users’ Location
3.1. Computation Offloading Optimization
3.2. UAV’s Trajectory Planning
3.3. Alternative Algorithm for Solving P2
| Algorithm 1 Joint Resource Allocation and Trajectory Planning Algorithm under known users’ location |
Input: Initialize , , , with feasible solution. Initialization: Set the radio environment parameters B, , , the operation parameters , , , , , and the tolerance error , For each iteration i Calculate , by Theorem 1 and calculate according to (17); Update , and by subgradient formula; , , , . For each iteration j Using CVX to solve P4.1 for given , , and obtain ; If , , break End If update ; End For If , break End If update ; End For Output, , , . |
4. Robust Design Based on Cutting-Set Method
4.1. Optimization Step under Finite Subsets of Users’ Location
4.2. Pessimization Step under Given UAV Trajectory
4.3. Total Algorithm of Robust Resource Allocation and Trajectory Planning
| Algorithm 2 Robust Offloading Trajectory and Computation Offloading Algorithm with uncertainty of users’ location |
Initialization: Set the iterative number . Input: Initialize finite subset . repeat calculate , , and by Algorithm 1; compute for given ; update finite subset ; update ; until reach the stable point or the maximum iterative number k Output , , , . |
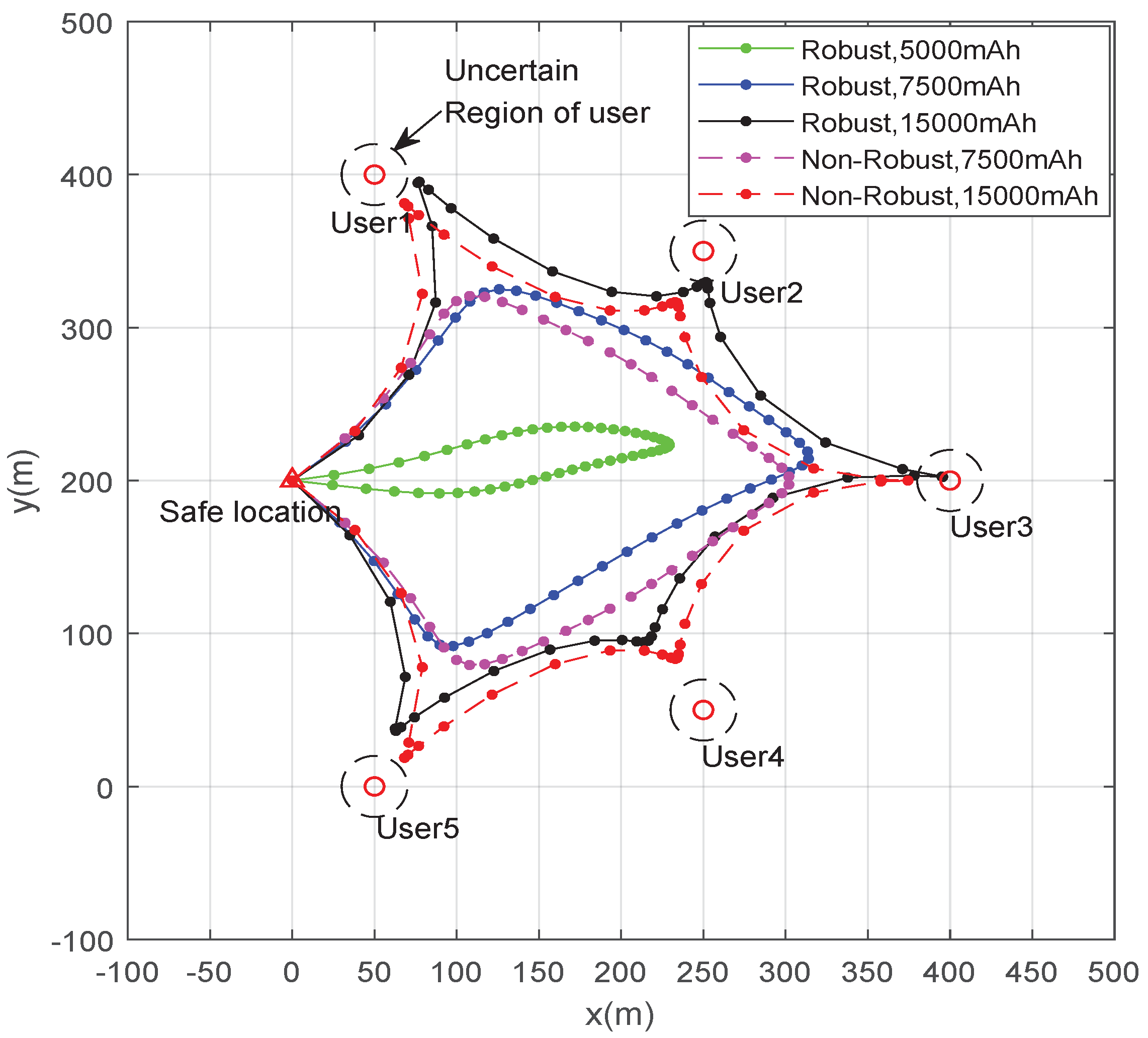
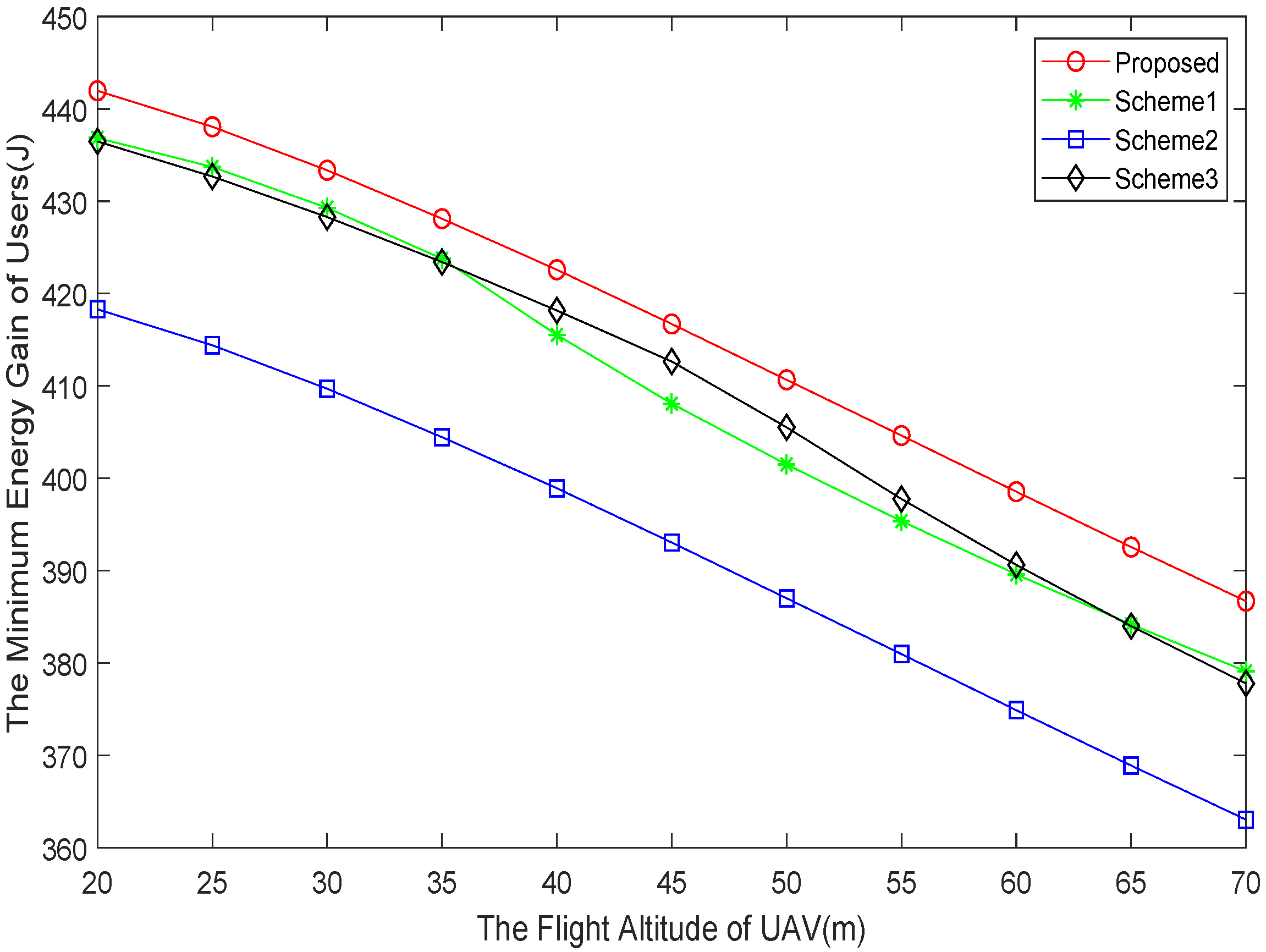
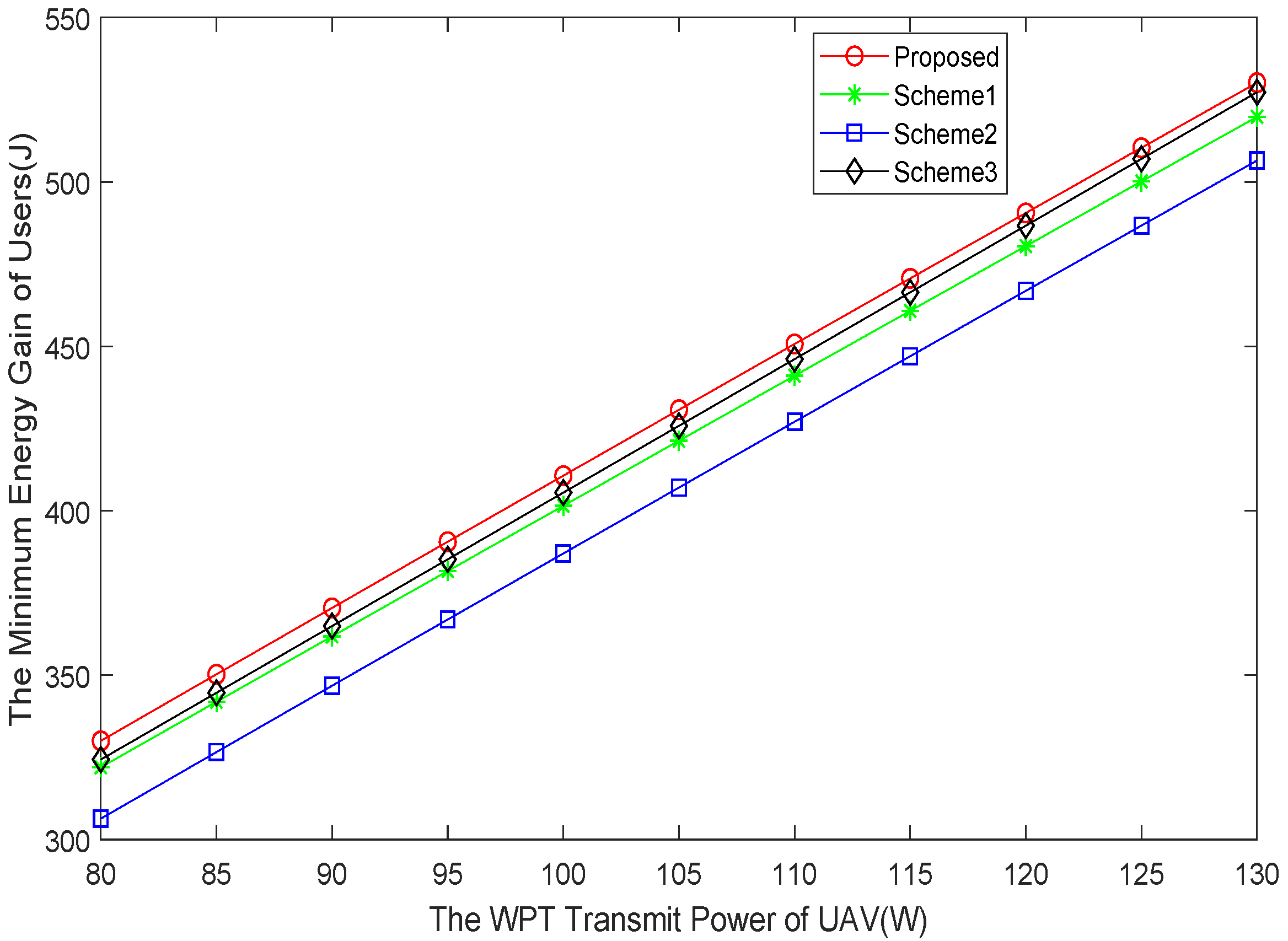
5. Numerical Results
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| UAV | Unmanned aerial vehicle |
| MEC | Mobile edge computing |
| WPT | Wireless power transfer |
| WIT | Wireless information transfer |
| RF | Radio frequency |
| SCA | Successive convex approximation |
Appendix A
References
- Erdelj, M.; Natalizio, E.; Chowdhury, K.R.; Akyildiz, I.F. Help from the Sky: Leveraging UAVs for Disaster Management. IEEE Pervasive Comput. 2017, 16, 24–32. [Google Scholar] [CrossRef]
- Yao, Z.; Cheng, W.; Zhang, W.; Zhang, H. Resource Allocation for 5G-UAV-Based Emergency Wireless Communications. IEEE J. Sel. Areas Commun. 2021, 39, 3395–3410. [Google Scholar] [CrossRef]
- Chen, W.; Su, Z.; Xu, Q.; Luan, T.H.; Li, R. VFC-Based Cooperative UAV Computation Task Offloading for Post-disaster Rescue. In Proceedings of the IEEE INFOCOM 2020-IEEE Conference on Computer Communications, Toronto, ON, Canada, 6–9 July 2020; pp. 228–236. [Google Scholar]
- Zhang, S.; Liu, J. Analysis and Optimization of Multiple Unmanned Aerial Vehicle-Assisted Communications in Post-Disaster Areas. IEEE Trans. Veh. Technol. 2018, 67, 12049–12060. [Google Scholar] [CrossRef]
- Gao, M.; Zhang, B.; Wang, L. A Dynamic Priority Packet Scheduling Scheme for Post-disaster UAV-assisted Mobile Ad Hoc network. In Proceedings of the 2021 IEEE Wireless Communications and Networking Conference (WCNC), Nanjing, China, 29 March–1 April 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Saif, A.; Dimyati, K.; Noordin, K.A.; Shah, N.S.M.; Abdullah, Q.; Mukhlif, F. Unmanned Aerial Vehicles for Post-Disaster Communication Networks. In Proceedings of the 2020 IEEE 10th International Conference on System Engineering and Technology (ICSET), Shah Alam, Malaysia, 9 November 2020; pp. 273–277. [Google Scholar] [CrossRef]
- Tang, H.; Wu, Q.; Xu, J.; Chen, W.; Li, B. A Novel Alternative Optimization Method for Joint Power and Trajectory Design in UAV-Enabled Wireless Network. IEEE Trans. Veh. Technol. 2019, 68, 11358–11362. [Google Scholar] [CrossRef]
- Ouyang, T.; Zhou, Z.; Chen, X. Follow Me at the Edge: Mobility-Aware Dynamic Service Placement for Mobile Edge Computing. IEEE J. Sel. Areas Commun. 2018, 36, 2333–2345. [Google Scholar] [CrossRef] [Green Version]
- Cao, P.; Liu, Y.; Yang, C.; Xie, S.; Xie, K. MEC-Driven UAV-Enabled Routine Inspection Scheme in Wind Farm Under Wind Influence. IEEE Access 2019, 7, 179252–179265. [Google Scholar] [CrossRef]
- Yang, C.; Lou, W.; Liu, Y.; Xie, S. Resource Allocation for Edge Computing-Based Vehicle Platoon on Freeway: A Contract-Optimization Approach. IEEE Trans. Veh. Technol. 2020, 69, 15988–16000. [Google Scholar] [CrossRef]
- Wu, Z.; Yang, Z.; Yang, C.; Lin, J.; Liu, Y.; Chen, X. Joint deployment and trajectory optimization in UAV-assisted vehicular edge computing networks. J. Commun. Netw. 2021, 1–12. [Google Scholar] [CrossRef]
- Li, P.; Xu, J. Fundamental Rate Limits of UAV-Enabled Multiple Access Channel With Trajectory Optimization. IEEE Trans. Wirel. Commun. 2020, 19, 458–474. [Google Scholar] [CrossRef] [Green Version]
- Xie, L.; Xu, J.; Zhang, R. Throughput Maximization for UAV-Enabled Wireless Powered Communication Networks. IEEE Internet Things J. 2019, 6, 1690–1703. [Google Scholar] [CrossRef] [Green Version]
- Liu, Y.; Yang, C.; Jiang, L.; Xie, S.; Zhang, Y. Intelligent Edge Computing for IoT-Based Energy Management in Smart Cities. IEEE Netw. 2019, 33, 111–117. [Google Scholar] [CrossRef]
- Lv, B.; Yang, C.; Chen, X.; Yao, Z.; Yang, J. Task Offloading and Serving Handover of Vehicular Edge Computing Networks Based on Trajectory Prediction. IEEE Access 2021, 9, 130793–130804. [Google Scholar] [CrossRef]
- Zhang, X.; Zhong, Y.; Liu, P.; Zhou, F.; Wang, Y. Resource Allocation for a UAV-Enabled Mobile-Edge Computing System: Computation Efficiency Maximization. IEEE Access 2019, 7, 113345–113354. [Google Scholar] [CrossRef]
- Liu, Y.; Xie, S.; Zhang, Y. Cooperative Offloading and Resource Management for UAV-Enabled Mobile Edge Computing in Power IoT System. IEEE Trans. Veh. Technol. 2020, 69, 12229–12239. [Google Scholar] [CrossRef]
- Zhou, F.; Wu, Y.; Hu, R.Q.; Qian, Y. Computation Rate Maximization in UAV-Enabled Wireless Powered Mobile-Edge Computing Systems. IEEE J. Sel. Areas Commun. 2018, 36, 1927–1941. [Google Scholar] [CrossRef] [Green Version]
- Liu, Y.; Xie, S.; Yang, Q.; Zhang, Y. Joint Computation Offloading and Demand Response Management in Mobile Edge Network With Renewable Energy Sources. IEEE Trans. Veh. Technol. 2020, 69, 15720–15730. [Google Scholar] [CrossRef]
- Liu, Y.; Xiong, K.; Ni, Q.; Fan, P.; Letaief, K.B. UAV-Assisted Wireless Powered Cooperative Mobile Edge Computing: Joint Offloading, CPU Control, and Trajectory Optimization. IEEE Internet Things J. 2020, 7, 2777–2790. [Google Scholar] [CrossRef]
- Liu, Y.; Qiu, M.; Hu, J.; Yu, H. Incentive UAV-Enabled Mobile Edge Computing Based on Microwave Power Transmission. IEEE Access 2020, 8, 28584–28593. [Google Scholar] [CrossRef]
- Xie, L.; Xu, J.; Zeng, Y. Common Throughput Maximization for UAV-Enabled Interference Channel With Wireless Powered Communications. IEEE Trans. Commun. 2020, 68, 3197–3212. [Google Scholar] [CrossRef] [Green Version]
- Zhang, S.; Zhang, H.; Di, B.; Song, L. Cellular UAV-to-X Communications: Design and Optimization for Multi-UAV Networks. IEEE Trans. Wirel. Commun. 2019, 18, 1346–1359. [Google Scholar] [CrossRef] [Green Version]
- Zhong, W.; Xie, K.; Liu, Y.; Yang, C.; Xie, S.; Zhang, Y. Multi-Resource Allocation of Shared Energy Storage: A Distributed Combinatorial Auction Approach. IEEE Trans. Smart Grid 2020, 11, 4105–4115. [Google Scholar] [CrossRef]
- Zhong, W.; Xie, K.; Liu, Y.; Xie, S.; Xie, L. Chance Constrained Scheduling and Pricing for Multi-Service Battery Energy Storage. IEEE Trans. Smart Grid 2021, 12, 5030–5042. [Google Scholar] [CrossRef]
- Zhong, W.; Xie, S.; Xie, K.; Yang, Q.; Xie, L. Cooperative P2P Energy Trading in Active Distribution Networks: An MILP-Based Nash Bargaining Solution. IEEE Trans. Smart Grid 2021, 12, 1264–1276. [Google Scholar] [CrossRef]
- Gao, Y.; Tang, H.; Li, B.; Yuan, X. Robust Trajectory and Power Control for Cognitive UAV Secrecy Communication. IEEE Access 2020, 8, 49338–49352. [Google Scholar] [CrossRef]
- Cui, M.; Zhang, G.; Wu, Q.; Ng, D.W.K. Robust Trajectory and Transmit Power Design for Secure UAV Communications. IEEE Trans. Veh. Technol. 2018, 67, 9042–9046. [Google Scholar] [CrossRef] [Green Version]
- Zhou, Y.; Zhou, F.; Zhou, H.; Ng, D.W.K.; Hu, R.Q. Robust Trajectory and Transmit Power Optimization for Secure UAV-Enabled Cognitive Radio Networks. IEEE Trans. Commun. 2020, 68, 4022–4034. [Google Scholar] [CrossRef]
- Yang, T.; Taghizadeh, O.; Hu, Y.; Xu, H.; Caire, G. Robust Secure UAV Communication Systems with Full-Duplex Jamming. In Proceedings of the 2021 IEEE Wireless Communications and Networking Conference (WCNC), Nanjing, China, 29 March–1 April 2021; pp. 1–6. [Google Scholar] [CrossRef]


| B | 5 MHz | The channel bandwidth. |
| −50 dB | The channel power gain at distance m. | |
| W | The receiver noise power. | |
| 0.5 W | The maximum WIT transmit power of user. | |
| 50 W | The WPT transmit power of UAV. | |
| 0.15 | The energy conversion efficiency of user. | |
| cycles/bit | The number of CPU cycles. | |
| The effective switched capacitance. | ||
| 10 GHz | The maximum frequency of CPU. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Cao, P.; Liu, Y.; Yang, C. Robust Resource Allocation and Trajectory Planning of UAV-Aided Mobile Edge Computing in Post-Disaster Areas. Appl. Sci. 2022, 12, 2226. https://doi.org/10.3390/app12042226
Cao P, Liu Y, Yang C. Robust Resource Allocation and Trajectory Planning of UAV-Aided Mobile Edge Computing in Post-Disaster Areas. Applied Sciences. 2022; 12(4):2226. https://doi.org/10.3390/app12042226
Chicago/Turabian StyleCao, Peng, Yi Liu, and Chao Yang. 2022. "Robust Resource Allocation and Trajectory Planning of UAV-Aided Mobile Edge Computing in Post-Disaster Areas" Applied Sciences 12, no. 4: 2226. https://doi.org/10.3390/app12042226
APA StyleCao, P., Liu, Y., & Yang, C. (2022). Robust Resource Allocation and Trajectory Planning of UAV-Aided Mobile Edge Computing in Post-Disaster Areas. Applied Sciences, 12(4), 2226. https://doi.org/10.3390/app12042226






