Abstract
Due to the prevalence of the order production mode, multi-variety, small-batch manufacturing enterprises frequently delay deliveries to downstream customers. To date, most existing studies on delayed delivery risk have focused on the response to the risk after it occurs, ignoring how the risk arises. For multi-variety, low-volume production companies, any part of the production process could lead to the ultimate risk of delayed delivery, and the risk is transmissible. Therefore, the path of risk transmission needs to be identified to effectively control the risk of late delivery at key production stages. In this paper, from the perspective of risk transmission, a recognition method based on association rules and the Bayesian network was proposed to identify the risk conduction path. This method firstly determined the strong association rules among the risk factors based on historical data stored in the ERP system and determined the Bayesian network topology structures of the risk transmission path by combining the business process and expert experience. Secondly, the prior and conditional probabilities of each node were determined using data statistics, and the risk transmission path of delayed delivery was identified using the forward and backward reasoning of the Bayesian network. Finally, this paper provided a case study to verify the method, and the following conclusions were obtained: (1) the delay in delivery to downstream customers is mainly due to the delayed delivery of upstream suppliers and the sudden change in customer demand, and (2) the adjustment of enterprise production plans is the key node of the delayed delivery risk transmission path. Through the research in this paper, production companies can identify the target of risk management more scientifically and mitigate the risk through the adjustment of key links.
1. Introduction
In recent years, with the diversification of market demand and the personalization of customer demand, there has been an increasing number of manufacturing enterprises in the multi-variety and small-batch production mode. On the one hand, multi-variety and low-volume production enterprises generally adopt the order production mode. On the other hand, due to the characteristics of multi-variety, low-volume production enterprises, these enterprises usually face many risks, such as multi-supplier risks, inventory risks, and production planning risks [1,2,3]. These two causes increase the possibility of late deliveries of orders. The current research on multi-variety, low-volume businesses focuses on production process optimization [4,5], which is essential to increasing business productivity. However, for a manufacturing company, being able to meet delivery deadlines for consumers is still a crucial aspect of the company’s competitiveness [6]. Studying a firm’s risk of late delivery is therefore extremely important [7,8].
Most existing studies on delayed delivery risk have focused on the countermeasures to the risk after it occurs, for example, ensuring delivery through production optimization [9,10] and improving delivery strategies [11,12]. However, current research ignores how risks arise. For multi-variety, low-volume production companies, any environment in the production process can contribute to the eventual risk of delayed delivery. However, risks are conductive: the occurrence of one risk often causes the occurrence of other risks, which leads to the transmission of risks attached to information flow, material flow, and capital flow [13]. For example, human error caused by a distribution agent can lead to overall delays in the supply chain [14], and supply chain disruptions can further lead to risks of late deliveries [15]. Research on the transmission of risk in finances, information, and prices is more abundant [16,17,18,19,20], but research on the transmission of delayed delivery risk in manufacturing firms is not well-developed [21]. Some researchers have studied the risk transmission process in the whole supply chain system from suppliers, manufacturers, wholesalers, and retailers to customers [22], and the risk transmission process in trade from the perspective of the industrial chain [23]. However, it is difficult to directly apply these studies to the risk management of manufacturing enterprises. In our field research on multi-variety and small-batch manufacturing enterprises, we have found that managers want to understand the transmission path of late delivery risk, that is, when a risk emerges, which risk factors also emerge and eventually lead to late delivery risk, but there is not much referable work on late delivery risk in enterprises.
Association rules can reflect the association relationship between risk indicators and risk factors by mining frequent item sets. By mining the association relationship of financial risk indicators, Shang determined credible risk management association rules [24]. Fu constructed a risk interaction network based on strong association rule mining [25]. Moreover, through the mining of management rules, the self-learning and self-tuning of the risk time knowledge ontology database can be realized [26]. It can be seen that the analysis of risk factors by using association rules is the basis of research on risk identification, risk evaluation, risk transmission, risk management, etc. Association rules can be flexibly used in the analysis of multiple data types, such as numerical data and text data, and their use has become a common research method in the field of risk. Bayesian networks are an extension of the Bayesian method and one of the commonly used research methods in the field of uncertain knowledge representation and reasoning. They can provide a quantitative measure of risk. For example, Meng’s research uses Bayesian networks to explore the relationship between risk indicators and the supply chain so as to evaluate the probability of risk occurrence [27]. Moreover, Bayesian networks have the characteristics of networks, and they can conduct a quantitative analysis on each node and realize the identification of key risk sources. Pan used Bayesian networks to identify the risk sources of accidents in large oil-refining enterprises [28]. Daulani used Bayesian networks to map the dependence characteristics of multiple departments within an enterprise and proposed a value chain risk measurement method to evaluate the risk status via the total number of risks [29]. Furthermore, if the nodes of Bayesian networks are regarded as the key nodes in the risk transmission path, the risk transmission path can be identified. Zhang proved the effectiveness of this method in enterprise financial risk [30], but he did not conduct an analysis of the critical path.
With the development of information technology and the popularity of the enterprise resource planning (ERP) system, large amounts of production data are stored on the ERP systems of multi-variety and small-batch production enterprises every day. Using the data in the information management system as the basis for identifying risk transmission paths will greatly improve the objectivity of research results. Therefore, this paper proposes a delayed delivery risk path identification method based on association rules and Bayesian networks, taking a multi-variety, low-volume, high-information manufacturing enterprise as the research object. The method makes full use of the data and information in the system to complete the quantitative identification of the key risk transmission paths. Based on this method, by analyzing the real data of enterprises, we found that the occurrence of late delivery risk is mainly caused by the late deliveries of upstream suppliers and the sudden change in customer demand, and the timely adjustment of the production plan is the key node of the transmission path of late delivery risk. In this paper, we provide a scientific method to identify the transmission path of delayed delivery risk for multi-variety, small-batch production enterprises. Enterprises can effectively control the key nodes based on the identification results to achieve the purpose of risk mitigation.
The remainder of this paper is organized as follows: Section 2 describes the association rules and the Bayesian network. Section 3 discusses the application process of the association rules and the Bayesian network in the identification of the delayed delivery risk transmission paths in multi-variety, low-volume production enterprises. Section 4 describes the experiments and results in this paper. In Section 5, the conclusions are presented.
2. Methods
Association rules and Bayesian networks are common data analysis methods. In this paper, association rules were used to analyze the strong associations between risk factors. On this basis, the inference of Bayesian networks enabled the identification of the risk transmission paths.
2.1. Association Rules
The theory of association rules is widely used in data mining. First proposed by Professor R. Agrawal in the 1990s, it is aimed at mining massive datasets directly to determine the relationship among them [31]. Association rules can be expressed as , where and are term sets, is the sum of all sets, , , and . represents the possibility of the event including item set and item set in the database. There are two important concepts involved in association rules: support and confidence [32].
Support refers to the percentage of the number of tuples that contain both and in all tuples. It is the probability that both and appear in the database. This can be defined as Formula (1):
Confidence refers to the ratio of the number of tuples that contain both and to the number of tuples that contain . It is the probability that can be obtained from . This can be defined as Formula (2):
where is the tuples containing both and
, and represents the total number of tuples.
2.2. Bayesian Network
A Bayesian network, also called a reliability network, is an extension of the Bayesian method, and it is one of the most effective theoretical models in the uncertain knowledge expression and reasoning field. A Bayesian network is a directed acyclic graph (DAG) consisting of representative variable nodes and directed edges connecting these nodes [33]. The nodes represent random variables. The directed edges between the nodes represent the correlation between the nodes. Conditional probability is used to express the relational strength. The prior probability is used to express the information of the nodes without father nodes. If there is no connection edges between the nodes, then the variables corresponding to the nodes are conditionally independent relative to the father nodes. A typical ordinary Bayesian network is shown in Figure 1, where is the parent node, and and are the child nodes. The joint probability distribution function is shown in Formula (3):
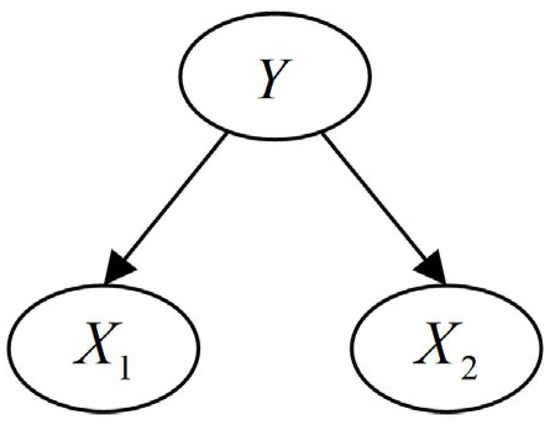
Figure 1.
A typical ordinary Bayesian network.
One of the important characteristics of a Bayesian network is that it can perform bidirectional reasoning, which means that it can infer the result from the reason and infer the reason from the result. The Bayesian network takes advantage of Bayes’ theorem to update the probability of variables when given new information, as shown in Formula (4) [34]. Therefore, after inputting a piece of information into the result variable, the Bayesian network model reproduces the reverse probability and deduces the probability of the cause variable [35].
Here, is the updated joint probability, and is the summation over all values of , except for . Bayesian networks have been extensively employed in the fields of safety, risk, and reliability analyses.
Before using the Bayesian network for deduction, the construction of the Bayesian network should be completed. Bayesian network construction includes the determination of the network topology and the determination of the probability distribution function of each node. The determination of the Bayesian network topology needs to determine the causality between nodes, which is a difficulty in the application process of Bayesian networks. In practical applications of Bayesian networks, it has been found that if the Bayesian network construction is based on expert experience only, the network structures given by various experts are usually different. If the expert can construct the network topology based on objective data analysis results, it will help to improve the objectivity and consistency of the network topology [36]. The determination of the probability distribution function is the key point of Bayesian network application. If the variable is discrete, it is represented by a conditional probability table (CPT), with different values of the nodes considering their parent states [34]. Bayesian network applications are usually limited due to the lack of data and uncertain probabilities. In this paper, the research object is a highly information-based enterprise, so the data are more sufficient, making prior probability and conditional probability easily obtained using statistical methods.
3. Methodology
In this paper, the transmission path of delayed delivery risk is defined as the path where the occurrence of a certain risk factor causes the emergence of related risk factors and eventually leads to the emergence of the risk of delayed delivery to downstream customers of the enterprise. An identification flowchart of the delayed delivery risk transmission path is shown in Figure 2. The identification process mainly includes four steps: data preparation, Bayesian network topology determination, CPT determination, and forward and backward reasoning. Here, the Bayesian network topology is determined based on the association rules among risk factors and the objective information of business processes combined with expert experience.
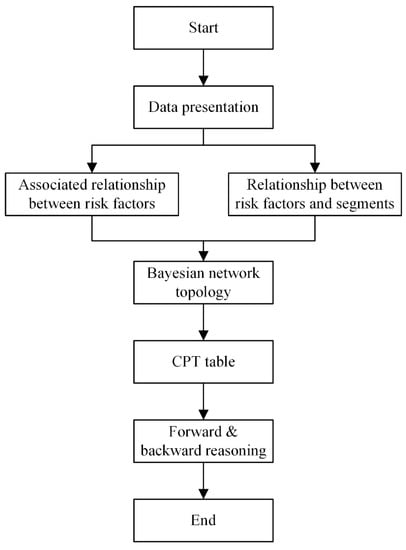
Figure 2.
Identification flowchart of the delayed delivery risk transmission path.
3.1. Data Preparation
A large number of production and management data are stored in an enterprise’s information management system: a customer order is a record, and each record is a transaction. For each transaction, the system includes the scheduled completion time and the actual completion time of many segments, comprising the procurement, the processing, the production, and the assembly in each workshop to the final delivery to the customer after the order is split. When the actual completion time is later than the scheduled completion time, there is a label that marks the reason for the delay, and all these reasons are delayed delivery risk factors. Each segment contains many delayed delivery risk factors, and each risk factor belongs to only one segment.
The purpose of data preparation is to provide support for the correctness and validity of the subsequent data analysis. Suppose there are a total of customer orders (that is, transactions) in the transaction database. In each transaction, there are business processes. According to the order of business processes, each business process is labeled as . For the business process , there are risk factors in the transaction database, which are marked . For each transaction in the database, the risk factors that occur are organized by order and business process, as shown in Table 1. If there is a delay in the delivery of the order, the corresponding transaction is marked with . When one or more risk factors are present in the transaction, the risk factor is marked with the corresponding business process, and when there is no risk factor for late delivery in the transaction, it is not marked. For example, the first transaction record in Table 1 indicates that the order is delayed. By looking at the risk factors, it can be observed that business processes and are delayed and that the risk factors are and , respectively.

Table 1.
Risk factors for orders.
3.2. The Establishment of Bayesian Network Topology
To establish a Bayesian network topology for delayed delivery risk factors, we should first identify the causal relationships between the risk factors. If we identify two risk factors once as risk factors, when their values are large, the identification workload becomes higher. By using the data mining method to identify the strong association rules among risk factors, we can filter out the causal risk factors with lower frequencies of occurrence. Therefore, determining the association rules between risk factors has two roles: one is providing an objective basis for the construction of the Bayesian topology network, and the second is improving the management effectiveness of the follow-up risk management from the perspective of scientific management. The association rules between risk factors can be attained by using the association rules module of WEKA and the data in Table 1 [37].
The association relationships between risk factors do not indicate causality relationships. As shown in Figure 3, the former contains the latter. The risk factors satisfying the association relationship may not satisfy the causal relationship. For example, Equipment A and Equipment B always fail at the same time, and the cause is high air humidity. From the perspective of data mining, “Equipment A breaks down” and “Equipment B breaks down” are associated, but there is no causal relationship between the two risks.
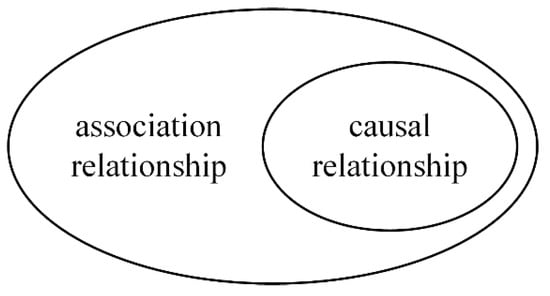
Figure 3.
Association relationship and causal relationship.
There is a time-successive relationship between cause-and-effect events because the cause is the former, and the effect is the latter. When constructing a Bayesian network topology for delayed delivery risk factors, the request of risk factors in a time sequence needs to be satisfied. Furthermore, the relationship between the business process needs to satisfy the request of the causal relationship in time. Therefore, the construction of the Bayesian network topology in this paper is based on the complete process of “from customer’s order to delivery of the order”. The correspondence between risk factors and processes can be observed in Table 1.
3.3. Establishment of CPT Table
In this paper, the risk factors are only “occurrence” and “non-occurrence”, so the risk factors are Boolean variables, labeled as and , respectively. For a node variable with no parent node, it is necessary to determine its prior probability, that is, the probability of the risk factor occurring. For a node variable with a parent node, it is necessary to determine its conditional probability, that is, the probability of the risk factor occurring when the corresponding risk factor in the parent node occurs and does not occur. The priori probability and conditional probability can be calculated based on the risk factor data in Table 1.
3.4. Forward and Backward Reasoning
After establishing the Bayesian networks for delayed delivery risk factors, forward and backward reasoning were carried out. In forward reasoning, we only take one of the risk factors as the evidence to observe the probability changes in the subsequent nodes, determine the transmission path of the risk factor based on the probability, and determine the increasing probability, which ultimately causes the occurrence of delayed delivery risk. In backward reasoning, we only take the final delayed delivery risk as the evidence to observe the changes in other nodes’ probabilities and then determine which risk factors lead to the occurrence of delayed delivery risk. Forward and backward reasoning can provide a powerful basis for the follow-up risk control of enterprises.
4. Experiments and Results
The data in this paper were from an enterprise that produces optoelectronic connectors and whose products are used in equipment in petroleum, electric power, aerospace, and other fields. This enterprise is a typical multi-variety, low-volume enterprise, and it has a high degree of information. We obtained order data covering half a year (about 15,000 customers) from this enterprise. After a downstream customer’s order is received by the enterprise, the required products are decomposed into parts by the system. Standard parts should be purchased, and core parts should be developed. After these parts are fabricated in the production workshop, assembled by the assembly workshop, and tested by the quality inspection department, the orders are delivered to the downstream customer. The business process of the enterprise is shown in Figure 4, including marketing, purchase, research, production, assembly, and testing. The deferred delivery risk factors of each business process are listed in Table 2. A portion of the identification results of the association rules between the factors are listed in Table 3.
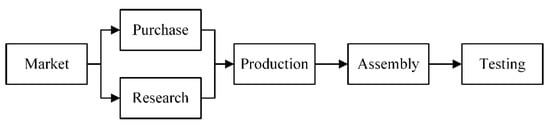
Figure 4.
Business process of the case enterprise.

Table 2.
Business processes and corresponding risk factors.

Table 3.
Association rules of factors.
To achieve a comprehensive and accurate identification of causal relationships between risk factors, expert experience was introduced based on association rules. We invited the following 18 experts to judge the causal relationships between risk factors: experts from outside the enterprise from suppliers (3) and product users (3) and inside the enterprise from the planning (3), production (3), supply chain (3), and marketing (3) departments. Each expert must have been with their company for at least 5 years, in supervisory positions or above. Bayesian networks were constructed based on Table 2 and Table 3 by the experts. For example, the association rules are invalid causations and should be excluded, because they do not conform to the time sequence in the business process. The association rules satisfy the time sequence, and the causality should be judged by experts. is the cause, and is the result. It was judged by expert experience that the association rules have causality. With the above method, the Bayesian network was constructed as shown in Figure 5, and the CPT table is shown in Table 4 and Table 5.
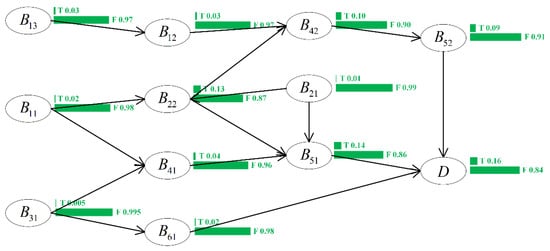
Figure 5.
Bayesian network of the risk conduction path.

Table 4.
CPT(a).

Table 5.
CPT(b).
The delayed delivery risk Bayesian network was constructed, and then reasoning was carried out. The occurrences of , , , and were established as evidence, and then forward reasoning was carried out. The results show that the probabilities of the occurrence of the deferred delivery risk, , were 85%, 50%, 87%, and 80%, respectively, which are shown in Figure 6a–d. The probability of delayed delivery was about 50%, which is due to the inaccurate forecast of the internal market demand in the enterprise and the relative increase in customer orders. The delayed delivery of parts due to various reasons of the suppliers can result in a high probability of delayed delivery. A sudden change in customer demand time can result in a high probability of delayed delivery. A high probability of delayed delivery can also happen when the order of production is affected due to the changes in the structure and process made by the research department. The occurrence of was established as evidence, and then backward reasoning was carried out, which is shown in Figure 6e. The results show that the degree of an increasing probability of particular nodes, such as
and , was the highest.
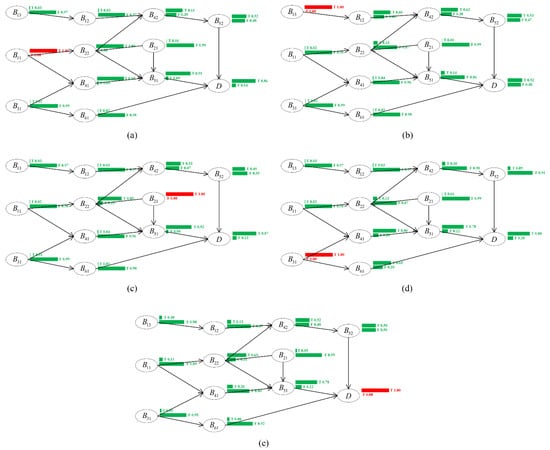
Figure 6.
Process of Bayesian network reasoning for the risk of delayed delivery. (a) The occurrence of as evidence. (b) The occurrence of as evidence. (c) The occurrence of as evidence. (d) The occurrence of as evidence. (e) The occurrence of as evidence.
The following conclusions can be drawn based on the analysis of the above inference result: (1) The main conduction path of the delayed delivery risk was , where represents the customer demand time change, represents the adjustment of the production task order, represents the delay of parts in assembly, and represents deferred delivery to downstream customers. (2) The main reason for the delay in the delivery of the business to the downstream customers is transmitted from the customer demand change and the delayed delivery of suppliers. (3) Enterprise tasks are often adjusted, which indicates that the key node in the risk conduction path is the low degree of flexibility in the arrangement of the production schedule. Improving the flexibility of enterprise production plans will help to reduce the risk of delayed delivery to downstream customers.
5. Conclusions
In this paper, which aimed to solve the problem of delayed delivery risk in multi-variety, low-volume enterprises, a risk transfer path identification method was established from the perspective of risk transmission. This method makes full use of the information of risk events in a database, and the method of association rules was used to identify the risk factors with strong associations. The relationships between the risk factors and the processes were combined, and a network topology of the risk factors for delayed delivery was constructed based on the experience of experts. Finally, the most likely path of risk transmission was identified through the forward and backward reasoning of the Bayesian network. The method made a qualitative and quantitative representation of the risk transmission path of the delayed delivery risk, so the objectivity of risk path recognition was greatly improved. By using a real case for verification and analyses, the results showed that the method can effectively identify the risk transmission path of delayed delivery and provide a basis for follow-up management.
In this paper, we aimed at solving the problem of delayed delivery risk. We took a multi-variety, low-volume manufacturing enterprise and their production processes as the objects, and we proposed corresponding methods to identify the delayed delivery risk, which complemented the current research on the risk transmission of enterprises as a link of the supply chain. Obviously, research on enterprises can better help enterprises identify risk transmission paths and make corresponding adjustments. In the future, the proposed method can be practically applied to the risk management of multi-variety, small-batch production enterprises to help them identify the risk transmission path and take targeted measures. In the future, for more complex products and production processes, the evaluation of the risk transmission path and the optimization of the production process can be further studied and discussed based on this paper.
Author Contributions
Conceptualization, L.Y. and F.Z.; methodology, F.Z.; software, A.L.; validation, L.Y. and X.W.; formal analysis, L.Y.; investigation, X.W.; resources, S.Z. and F.W.; data curation, A.L.; writing—original draft preparation, F.Z.; writing—review and editing, L.Y.; visualization, L.Y.; supervision, F.W.; project administration, S.Z. and F.W.; funding acquisition, S.Z. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the National Natural Science Foundation of China (Grant No. 71971013), the Fundamental Research Funds for the Central Universities (YWF-22-L-943), and the Scientific Research Project of Beijing Institute of Economics and Management (21BSA04). The study was also sponsored by the Teaching Reform Project and Graduate Student Education and Development Foundation of Beihang University.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Restrictions apply to the availability of these data. Please contact Linchao Yang (yanglinchao@buaa.edu.cn) to enquire about data availability.
Acknowledgments
All authors would like to thank those who provided support through funding.
Conflicts of Interest
The authors declare no conflict of interest. The funders had no role in the design of the study; in the collection, analyses, or interpretation of data; in the writing of the manuscript, or in the decision to publish the results.
References
- Zhu, H.; Liu, X.; Chen, Y. Effective inventory control policies with a minimum order quantity and batch ordering. Int. J. Prod. Econ. 2015, 168, 21–30. [Google Scholar] [CrossRef]
- Chang, S.-C.; Chang, C.-T. A multi-stage and multi-supplier inventory model allowing different order quantities. Appl. Math. Model. 2017, 52, 613–625. [Google Scholar] [CrossRef]
- Joglekar, G. Using simulation for scheduling and rescheduling of batch processes. Processes 2017, 5, 66. [Google Scholar] [CrossRef]
- Wang, K.; Zhang, F.; Wang, W.H.; Qian, Y.W.; Iop. The Multi-Varieties Small-Batch Gas Monitor Flexible Digital Job Shop Design and Integration Technology Research. In Proceedings of the 3RD International Conference on Advanced Technologies in Design, Mechanical and Aeronautical Engineering (Atdmae 2019), Shanghai, China, 5–7 July 2019. [Google Scholar]
- Li, Z.P. Management Decisions in Multi-Variety Small-Batch Product Manufacturing Process. Int. J. Simul. Model. 2022, 21, 537–547. [Google Scholar] [CrossRef]
- Chang, Y.S.; Lee, J.K. Case-based modification for optimization agents: AGENT-OPT. Decis. Support Syst. 2004, 36, 355–370. [Google Scholar] [CrossRef]
- Ho, Y.L. Staged improvement of delivery-oriented production. Int. J. Simul. Model. 2015, 14, 17–27. [Google Scholar] [CrossRef]
- Khabbaz, M.; Shaban, K.; Assi, C. Delay-Aware Flow Scheduling In Low Latency Enterprise Datacenter Networks: Modeling and Performance Analysis. IEEE Trans. Commun. 2017, 65, 2078–2090. [Google Scholar] [CrossRef]
- Biçer, I.; Seifert, R.W. Optimal Dynamic Order Scheduling under Capacity Constraints Given Demand-Forecast Evolution. Prod. Oper. Manag. 2017, 26, 2266–2286. [Google Scholar] [CrossRef]
- Chen, H.; Zuo, L.; Wu, C.; Wang, L.; Diao, F.; Chen, J.; Huang, Y. Optimizing detailed schedules of a multiproduct pipeline by a monolithic MILP formulation. J. Pet. Sci. Eng. 2017, 159, 148–163. [Google Scholar] [CrossRef]
- Bushuev, M.A. Delivery performance improvement in two-stage supply chain. Int. J. Prod. Econ. 2018, 195, 66–73. [Google Scholar] [CrossRef]
- Shao, X.-F. Production disruption, compensation, and transshipment policies. Omega 2018, 74, 37–49. [Google Scholar] [CrossRef]
- Li, C.; Wang, K. The risk element transmission theory research of multi-objective risk-time-cost trade-off. Comput. Math. Appl. 2009, 57, 1792–1799. [Google Scholar] [CrossRef]
- Awaysheh, A.; Frohlich, M.T.; Flynn, B.B.; Flynn, P.J. To err is human: Exploratory multilevel analysis of supply chain delivery delays. J. Oper. Manag. 2021, 67, 882–916. [Google Scholar] [CrossRef]
- Paul, S.K.; Asian, S.; Goh, M.; Torabi, S.A. Managing sudden transportation disruptions in supply chains under delivery delay and quantity loss. Ann. Oper. Res. 2019, 273, 783–814. [Google Scholar] [CrossRef]
- Asche, F.; Dahl, R.E.; Valderrama, D.; Zhang, D.J. Price Transmission in New Supply Chains-the Case of Salmon in France. Aquac. Econ. Manag. 2014, 18, 205–219. [Google Scholar] [CrossRef]
- Townsend, R.R. Propagation of Financial Shocks: The Case of Venture Capital. Manag. Sci. 2015, 61, 2782–2802. [Google Scholar] [CrossRef]
- Zhang, L.; Yao, X. An improved method of Granger causality test and application on the stock market risk transmission. Econ. Comput. Econ. Cybern. Stud. Res. 2015, 49, 1–19. [Google Scholar]
- Hou, Y.; Li, S. Information transmission between US and China index futures markets: An asymmetric DCC GARCH approach. Econ. Model. 2016, 52, 884–897. [Google Scholar] [CrossRef]
- Abdin, I.; Li, Y.F.; Zio, E. Risk assessment of power transmission network failures in a uniform pricing electricity market environment. Energy 2017, 138, 1042–1055. [Google Scholar] [CrossRef]
- Jaber, H.; Marle, F.; Vidal, L.A.; Didiez, L. Criticality and propagation analysis of impacts between project deliverables. Res. Eng. Des. 2018, 29, 87–106. [Google Scholar] [CrossRef]
- Wang, J.P.; Zhou, H.; Jin, X.D. Risk transmission in complex supply chain network with multi-drivers. Chaos Solitons Fractals 2021, 143, 110259. [Google Scholar] [CrossRef]
- Hao, H.C.; Xing, W.L.; Wang, A.J.; Song, H.; Han, Y.W.; Zhao, P.; Xie, Z.Q.; Chen, X.M. Multi-layer networks research on analyzing supply risk transmission of lithium industry chain. Resour. Policy 2022, 79, 102933. [Google Scholar] [CrossRef]
- Shang, H.Y.; Lu, D.; Zhou, Q.Y. Early warning of enterprise finance risk of big data mining in internet of things based on fuzzy association rules. Neural Comput. Appl. 2021, 33, 3901–3909. [Google Scholar] [CrossRef]
- Fu, L.P.; Wang, X.Q.; Zhao, H.; Li, M.N. Interactions among safety risks in metro deep foundation pit projects: An association rule mining-based modeling framework. Reliab. Eng. Syst. Saf. 2022, 221, 10831. [Google Scholar] [CrossRef]
- Yang, B. Construction of logistics financial security risk ontology model based on risk association and machine learning. Saf. Sci. 2020, 123, 104437. [Google Scholar] [CrossRef]
- Meng, M.J.; Lin, Q.Y.; Wang, Y.M. The risk assessment of manufacturing supply chains based on Bayesian networks with uncertainty of demand. J. Intell. Fuzzy Syst. 2022, 42, 5753–5771. [Google Scholar] [CrossRef]
- Pan, L.D.; Zheng, Y.; Zheng, J.; Xu, B.; Liu, G.Z.; Wang, M.; Yang, D.D. Characteristics of Chemical Accidents and Risk Assessment Method for Petrochemical Enterprises Based on Improved FBN. Sustainability 2022, 14, 12072. [Google Scholar] [CrossRef]
- Daultani, Y.; Goswami, M.; Vaidya, O.S.; Kumar, S. Inclusive risk modeling for manufacturing firms: A Bayesian network approach. J. Intell. Manuf. 2019, 30, 2789–2803. [Google Scholar] [CrossRef]
- Zhang, Y.; Ji, K.X.; An, Y. Identification of Enterprise Financial Risk Transfer Path Based on Data Mining. In Proceedings of the 2020 3rd International Conference on Artificial Intelligence and Big Data (ICAIBD 2020), Chengdu, China, 28–31 May 2020; pp. 101–105. [Google Scholar]
- Radosav, D.; Brtka, E.; Brtka, V. Mining Association Rules from Empirical Data in the Domain of Education. Int. J. Comput. Commun. Control. 2012, 7, 933–944. [Google Scholar] [CrossRef][Green Version]
- Agapito, G.; Guzzi, P.H.; Cannataro, M. DMET-Miner: Efficient discovery of association rules from pharmacogenomic data. J. Biomed. Inform. 2015, 56, 273–283. [Google Scholar] [CrossRef] [PubMed]
- Khakzad, N.; Khan, F.; Amyotte, P. Dynamic safety analysis of process systems by mapping bow-tie into Bayesian network. Process Saf. Environ. Prot. 2013, 91, 46–53. [Google Scholar] [CrossRef]
- Pasman, H.; Rogers, W. Bayesian networks make LOPA more effective, QRA more transparent and flexible, and thus safety more definable! J. Loss Prev. Process Ind. 2013, 26, 434–442. [Google Scholar] [CrossRef]
- Matellini, D.B.; Wall, A.D.; Jenkinson, I.D.; Wang, J.; Pritchard, R. Modelling dwelling fire development and occupancy escape using Bayesian network. Reliab. Eng. Syst. Saf. 2013, 114, 75–91. [Google Scholar] [CrossRef]
- Sousa, H.S.; Prieto-Castrillo, F.; Matos, J.C.; Branco, J.M.; Lourenco, P.B. Combination of expert decision and learned based Bayesian Networks for multi-scale mechanical analysis of timber elements. Expert Syst. Appl. 2018, 93, 156–168. [Google Scholar] [CrossRef]
- Fan, Z.; Fajie, W.E.I.; Quanbao, L.I. Risk source identification of complex equipment development project. J. Beijing Univ. Aeronaut. Astronaut. 2017, 43, 975–980. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).