Investigating Wearable Fitness Applications: Data Privacy and Digital Forensics Analysis on Android
Abstract
:1. Introduction
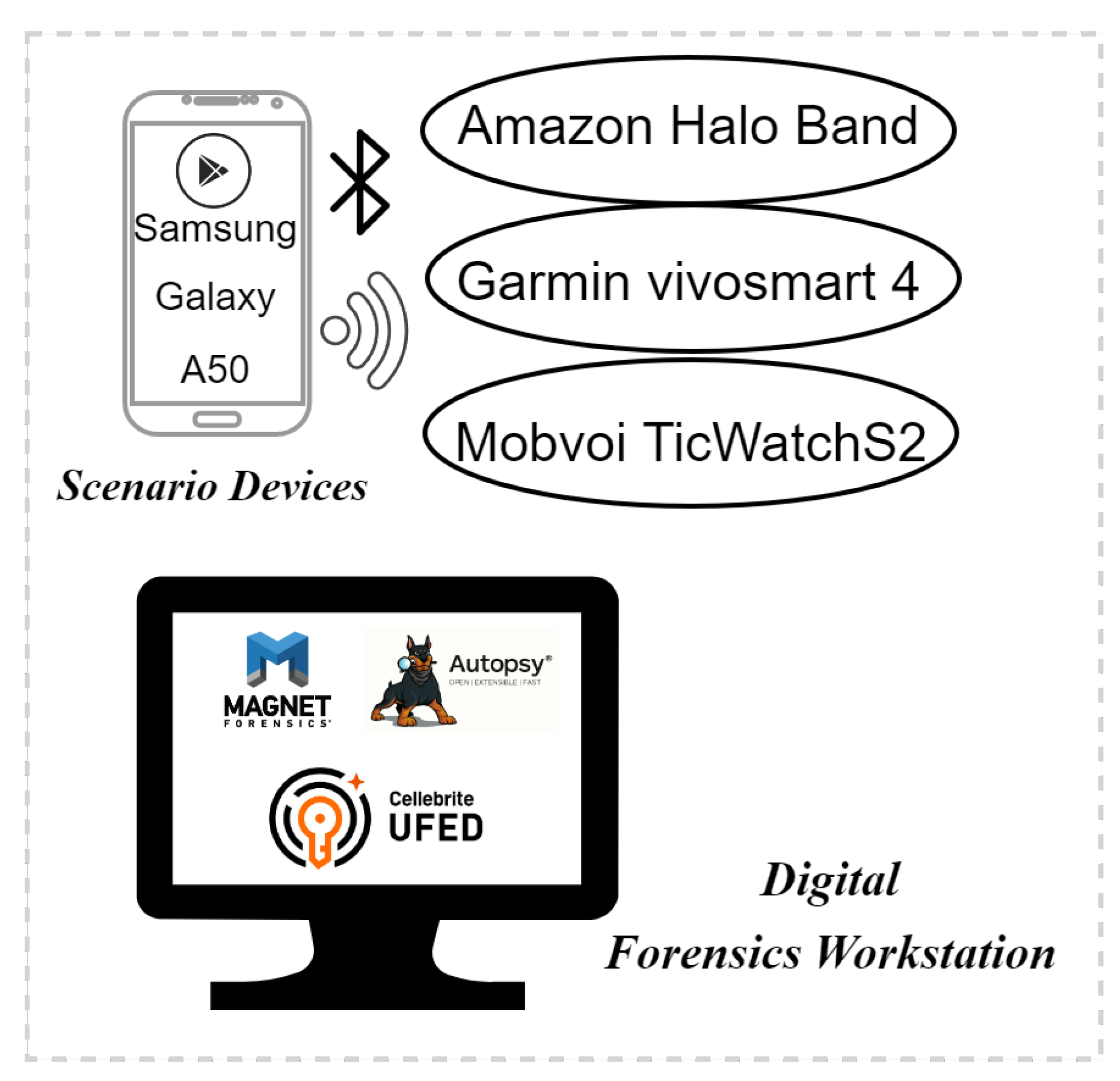
- The authors conducted a forensic analysis of three smartwatch/fitness tracker applications on an Android smartphone to identify privacy concerns that arise due to the way these apps store data on the Android device. The apps investigated are Amazon Halo, Garmin Connect, and Mobvoi.
- Provide the first comprehensive forensic analysis of the Amazon Halo app on Android.
- Compare the findings between Magnet AXIOM and Basis Technology’s Autopsy, taking note of any differences or advantages of using open-sourced tools over proprietary software.
- Provide a forensic roadmap to investigators tasked with examining these and similar smartwatch/fitness tracker devices.
- Identify security and privacy concerns related to the data stored by these three apps on an Android device.
2. Review of the Literature
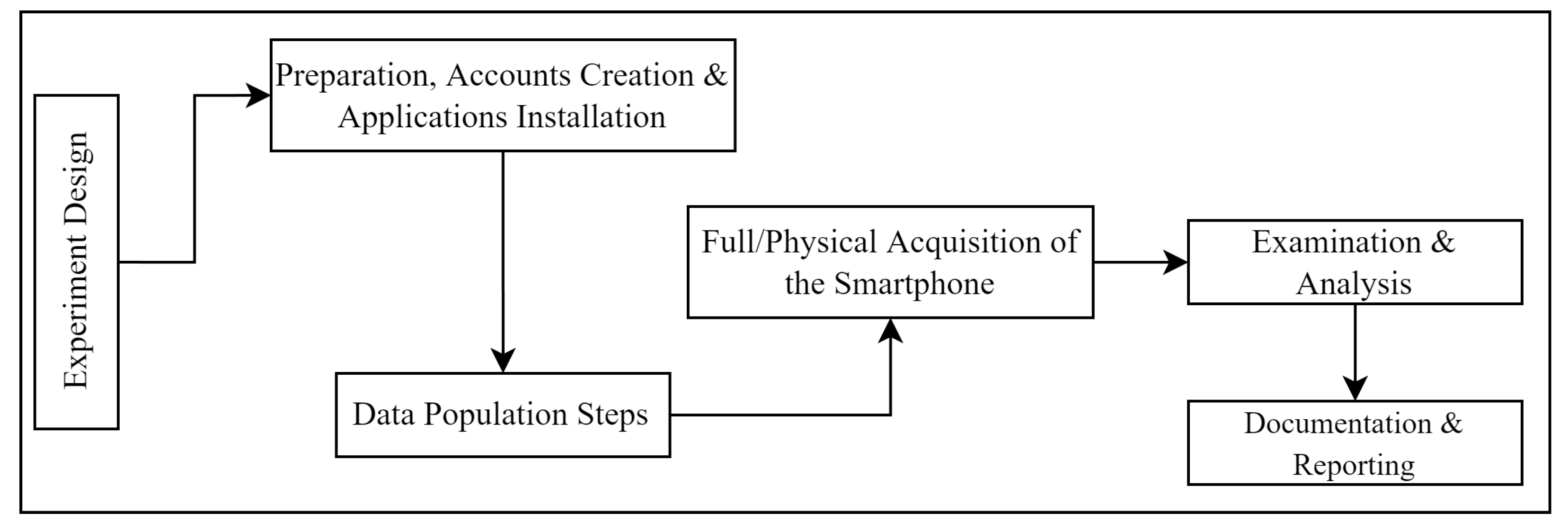
3. Methodology
3.1. Data Population
- Signed into the Google account on the smartphone.
- Download and install the three necessary apps from the Google Play Store:
- Amazon Halo: for the Amazon Halo Band
- Connect: for the Garmin vívosmart® 4 fitness tracker
- Wear OS and Mobvoi: for the TicWatch S2 smartwatch
- For each app, we created an account and connected the fitness tracker/smartwatch to the phone, via their corresponding apps.
- Download and install the Whisper app [25] (to generate notifications)
- Used the free features available to us with each wearable device to generate data. The exact type of activities we performed for each device are provided in Section 3.1.1.
- Performed a full/physical acquisition of the Samsung Galaxy A50 smartphone with Cellebrite UFED.
- Loaded the resultant .raw image file into Magnet AXIOM Process.
- Examined the resultant forensic image of the Samsung Galaxy A50 smartphone with Magnet AXIOM Examine.
3.1.1. Wearable Interactions
- One researcher wore the three wearable devices simultaneously on their wrists each day: the TicWatch and Amazon Halo devices were worn on their right wrist while the Garmin device was worn on their left wrist. All three wearable devices were charged at least one time each day.
- We made sure to use all the features available in each app. These interactions included tracking workouts and sleep, using Alexa/Google, and generating notifications. Table 3 highlights the features tested on each wearable device, where No indicates that the feature is not available or was not tested on the respective wearable.
3.2. Acquisition
3.3. Analysis
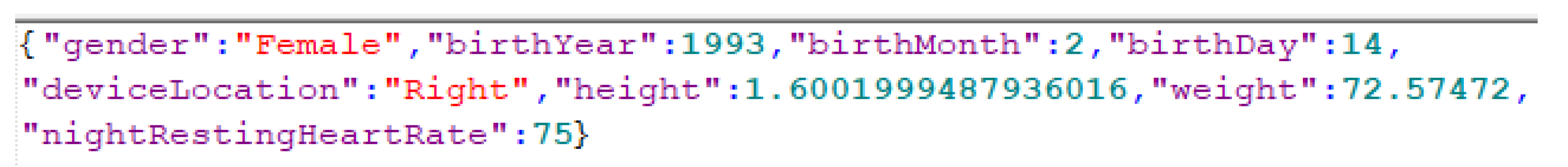
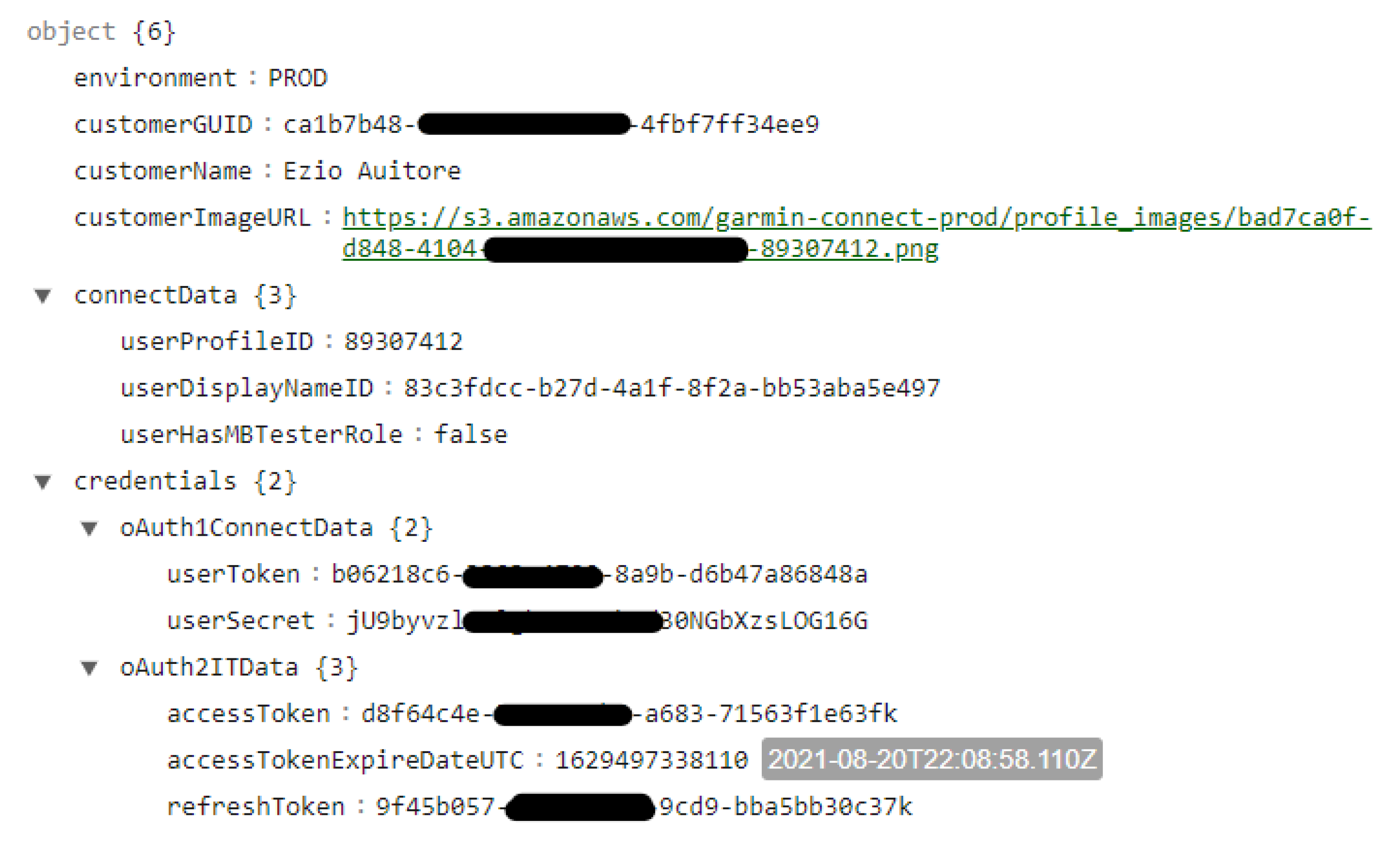
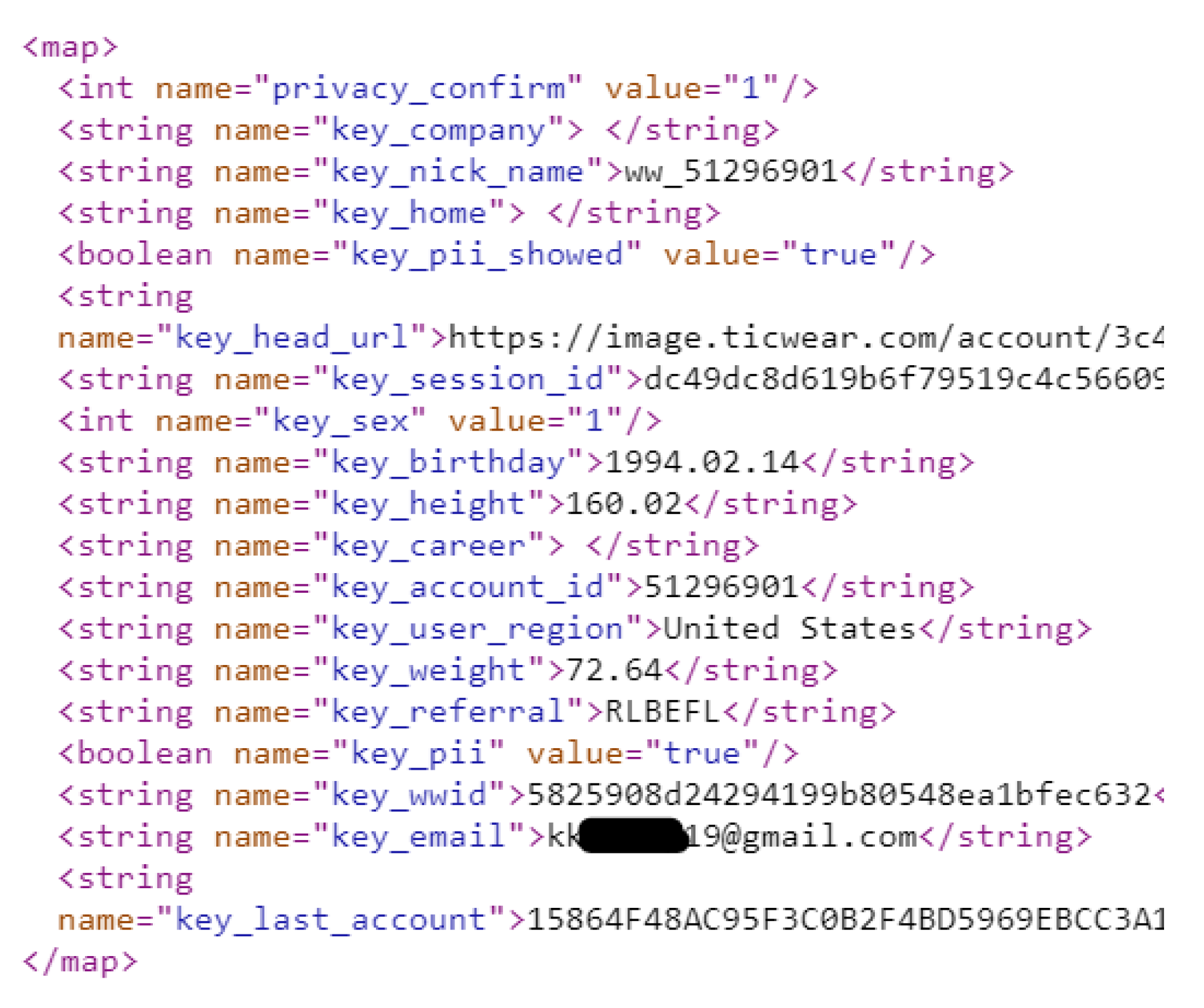
- Direct user identification: Artifacts related to the account and profile setup may be capable of uniquely identifying users. For instance, if possible to recover any combination of the user’s name, date-of-birth, age, home location, and email address, then these artifacts present a serious privacy concern for the app user.
- Facilitate user tracking: The recovery of GPS coordinates can be used to track the user’s movements, especially should these coordinates be accompanied by timestamps. GPS coordinates also allow a malicious person to determine the user’s frequently visited locations. For example, the Fitbit app on Android 7 stores the GPS coordinates associated with an exercise the user tracked via their Versa 2 smartwatch [12].
4. Findings
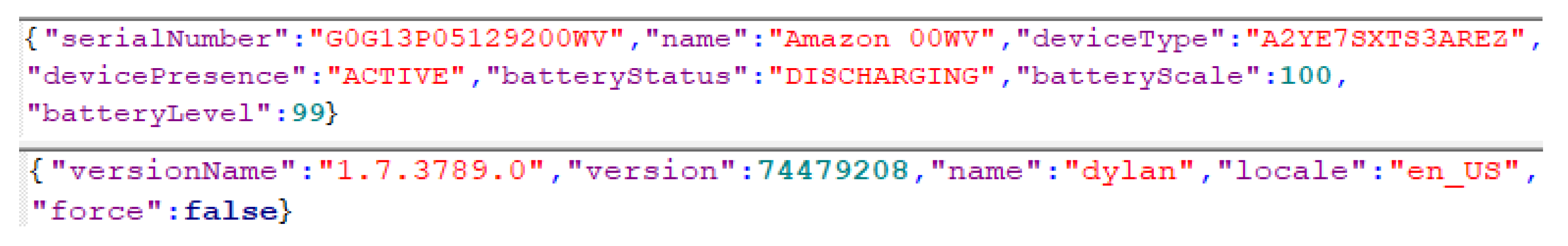
4.1. Amazon Halo Artifacts
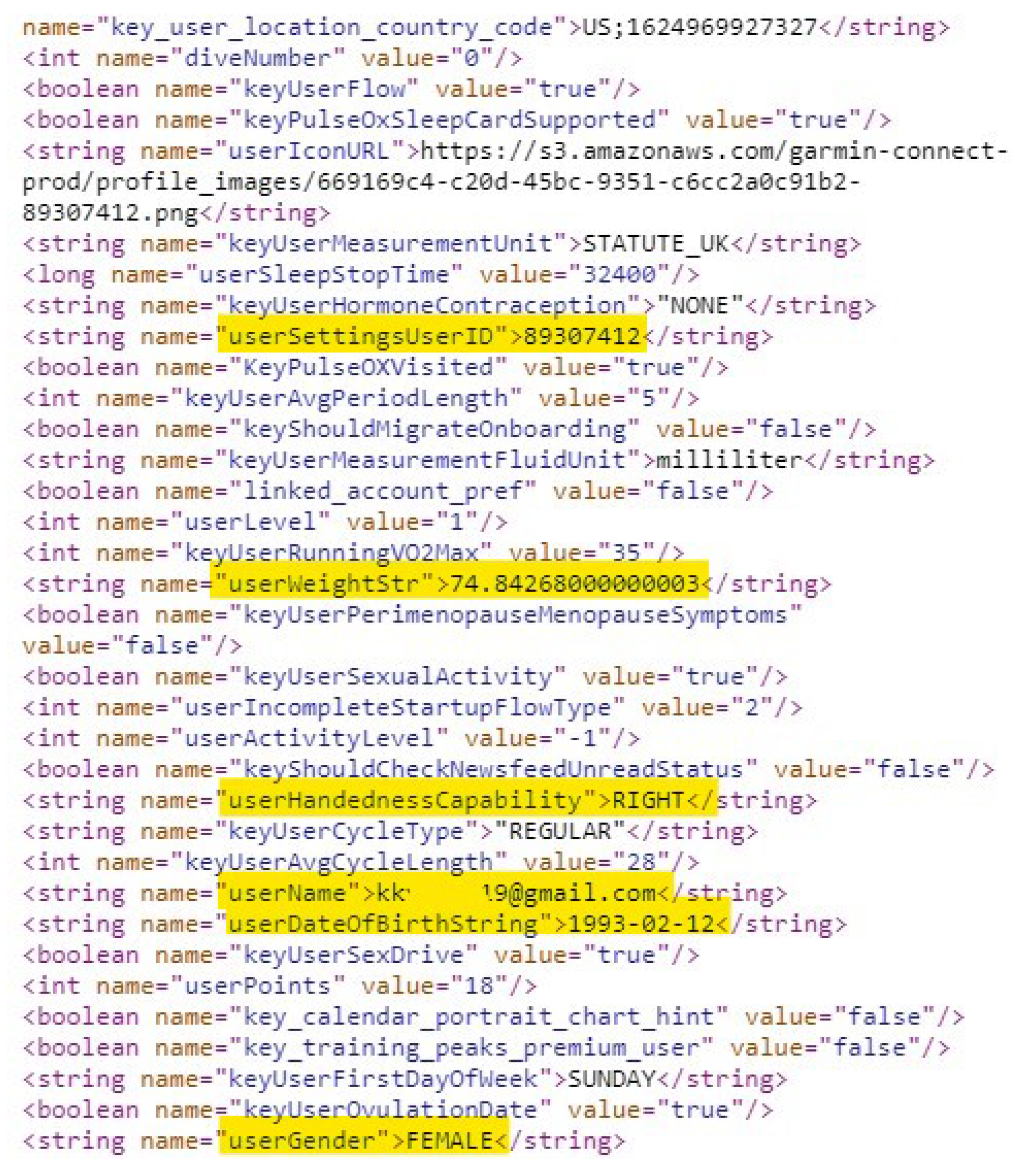
4.1.1. User Profile Artifacts
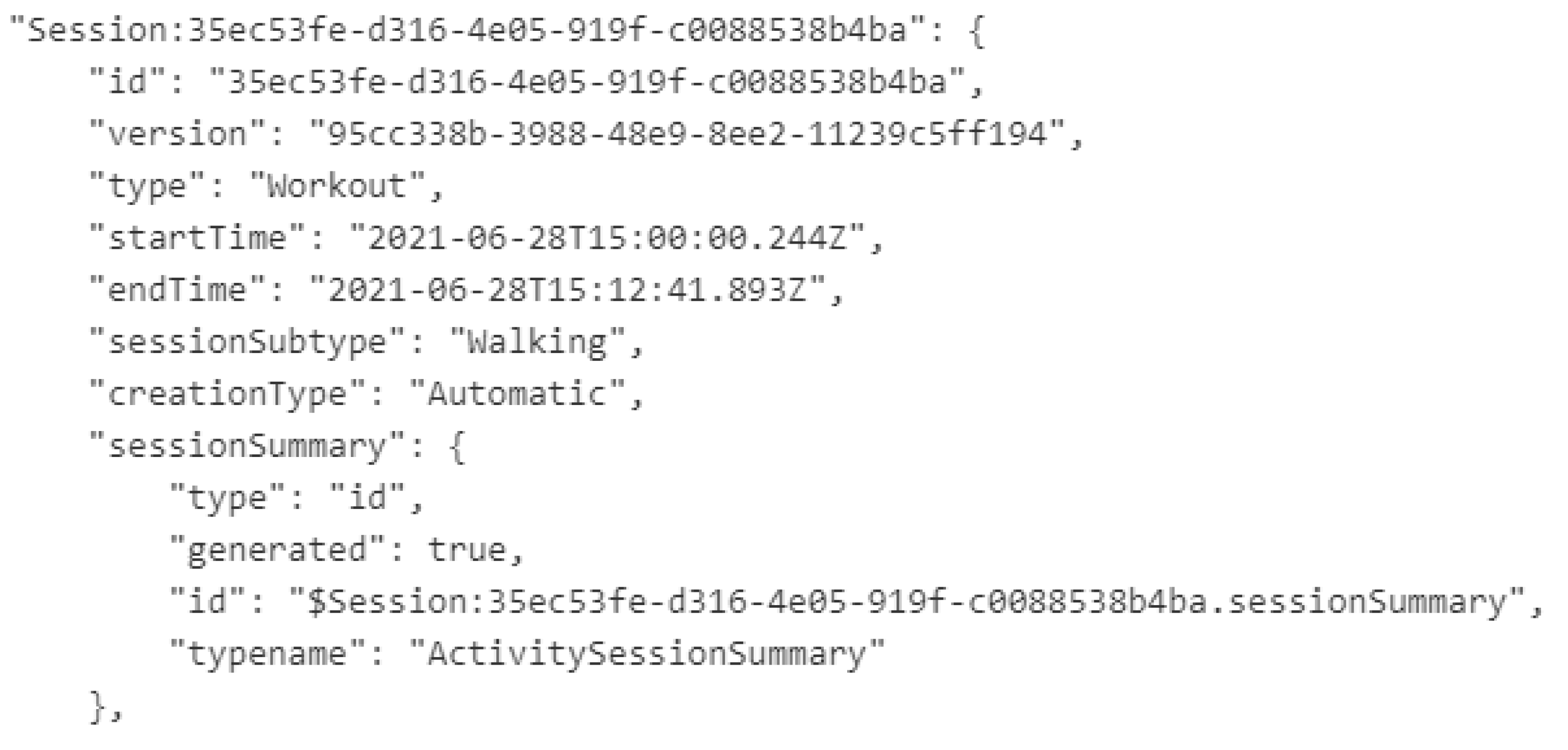
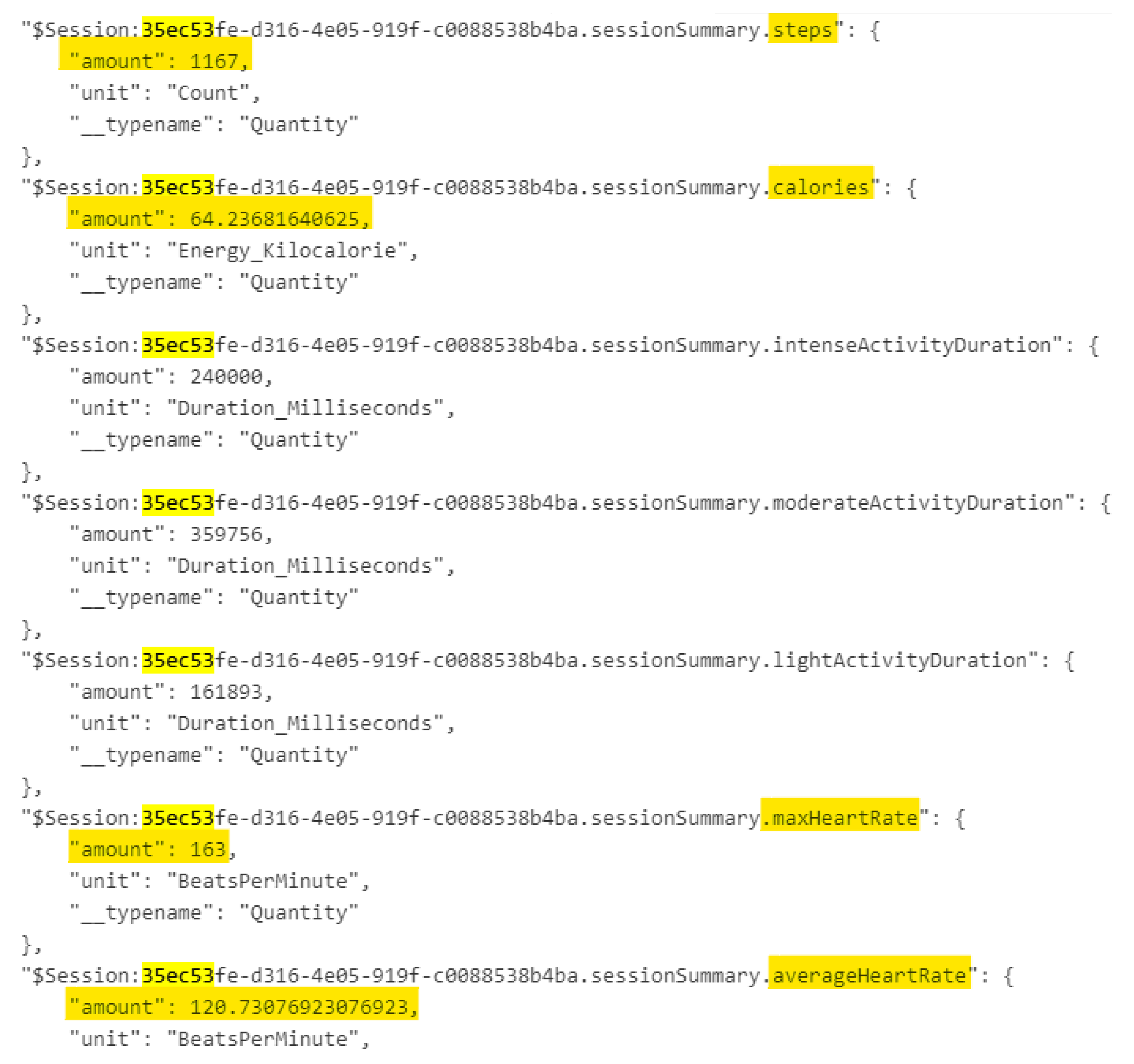
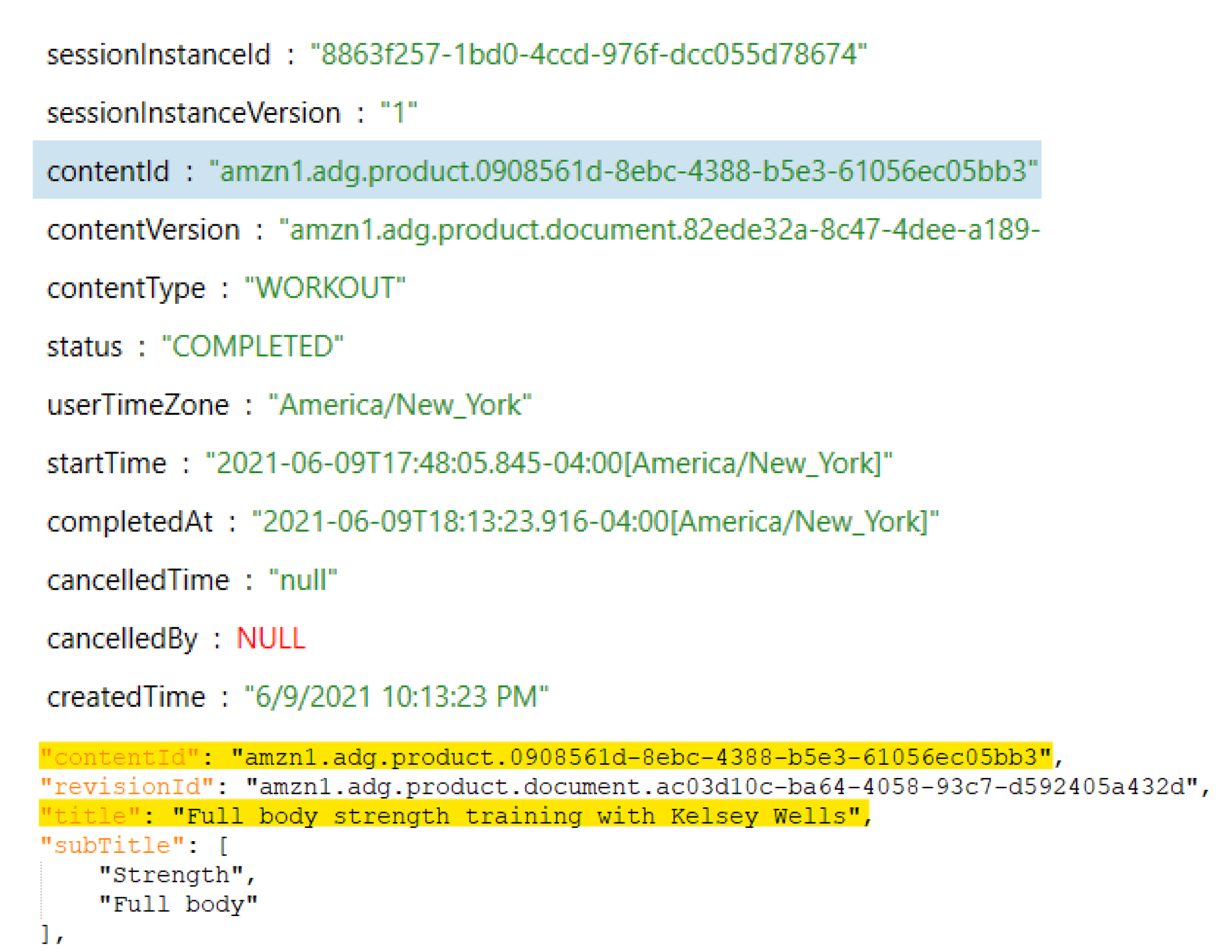
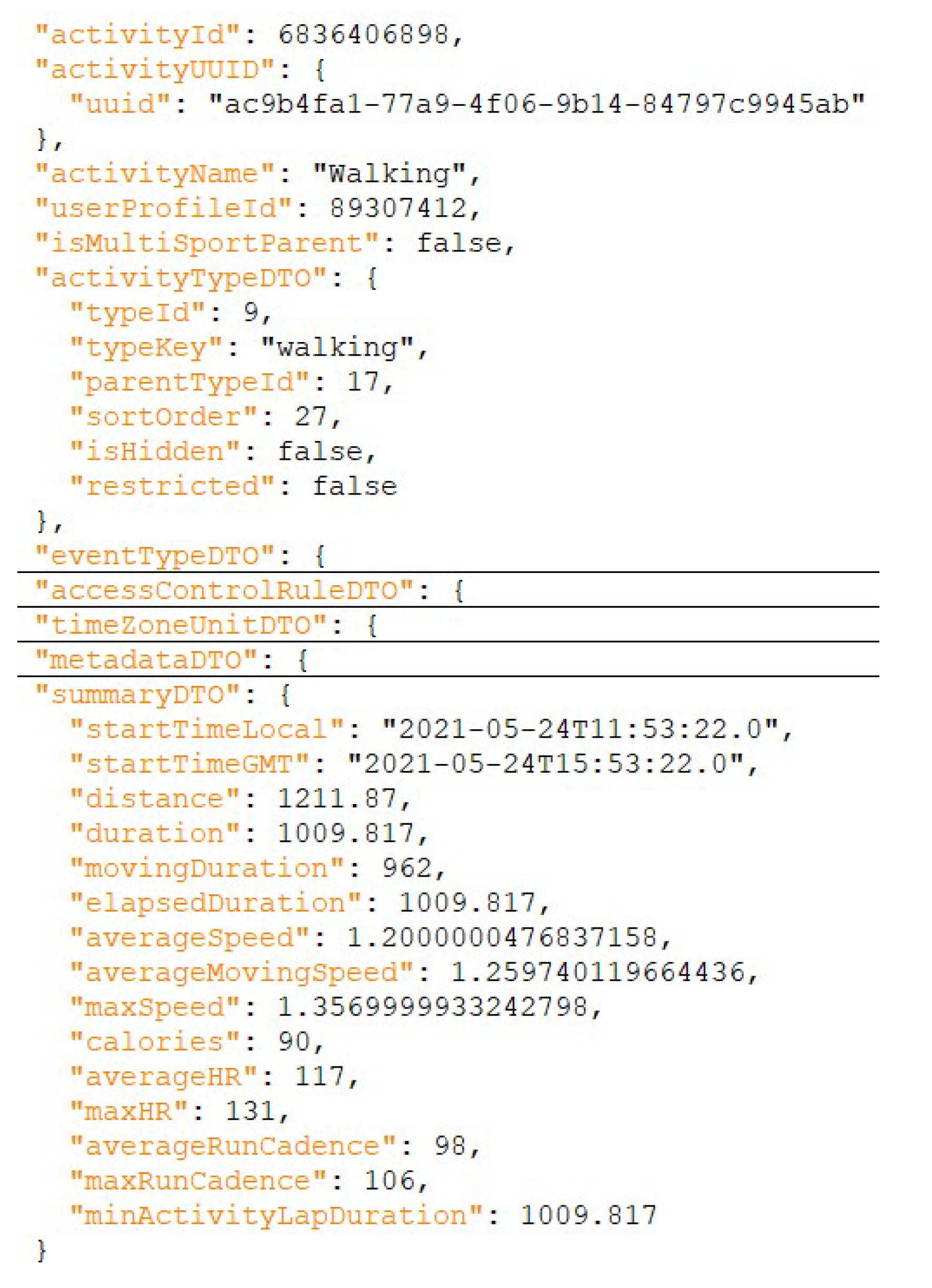
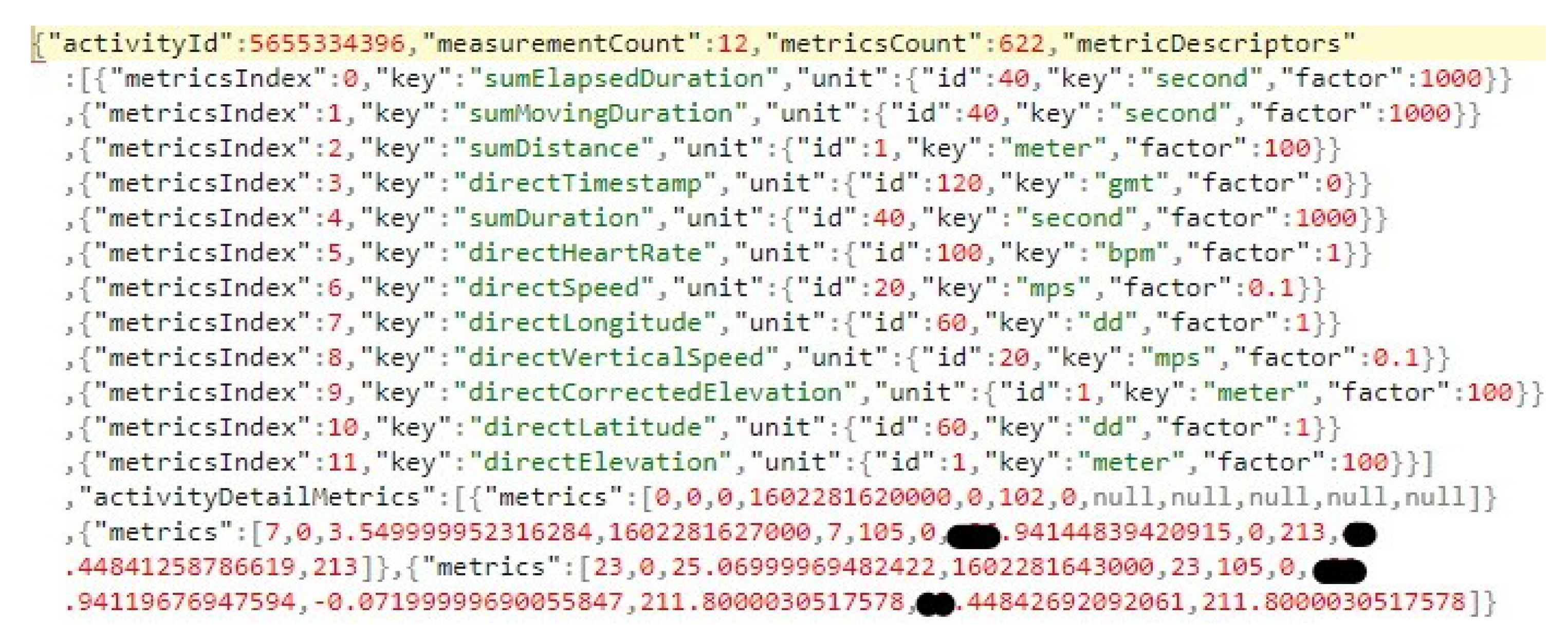
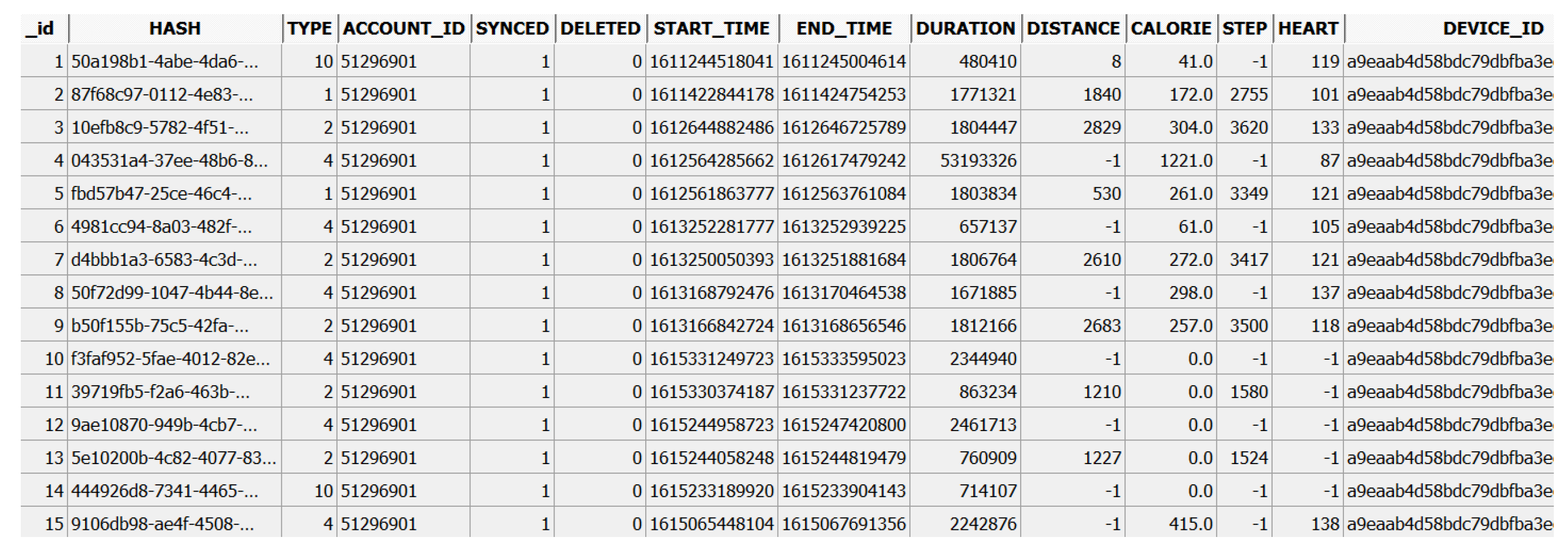
4.1.2. Activity-Related Artifacts
- The following metrics were recorded daily for the last 13 days of our data population, from 25 June 2021 to 7 July 2021:
- -
- Resting Heart Rate
- -
- Maximum and Average Heart Rate, taken every 5 min
- -
- Time spent doing Vigorous, Moderate, Light, and Sedentary Activity, taken every hour
- -
- Calories, taken every hour
- -
- Steps, taken every hour
- -
- Sleep Summary
- The following metrics were recorded weekly for the last two weeks (28 June 2021 to 7 July 2021) of our data population, excluding Sundays:
- -
- Sleep Summary data
- -
- Activity Summary data.
- The following metrics were recorded monthly:
- -
- Sleep Summary data for the last five weeks (1 June 2021 to 7 July 2021) of our data population.
- -
- Activity Summary data for the last week (1 July 2021 to 7 July 2021) of our data population.
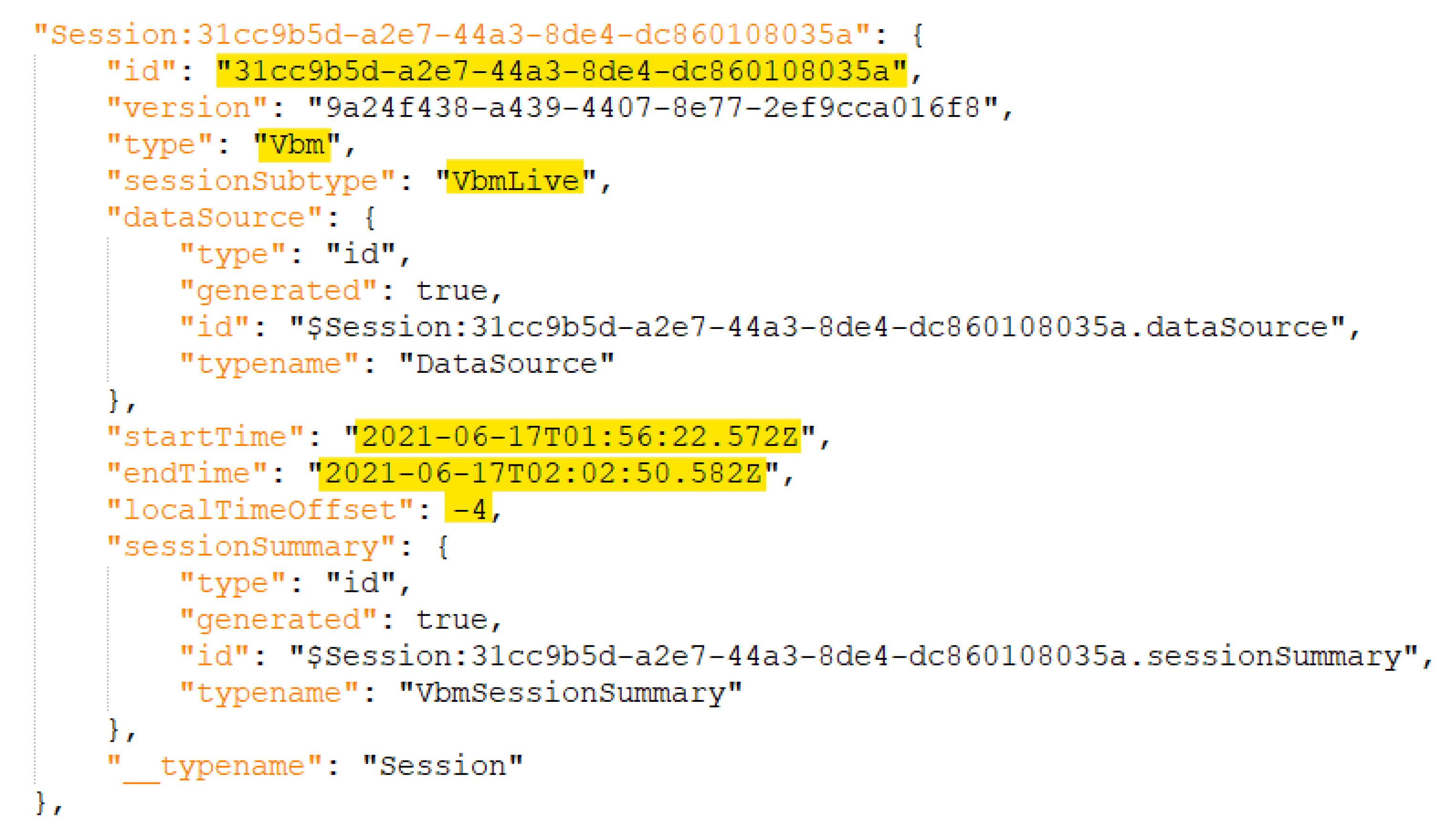
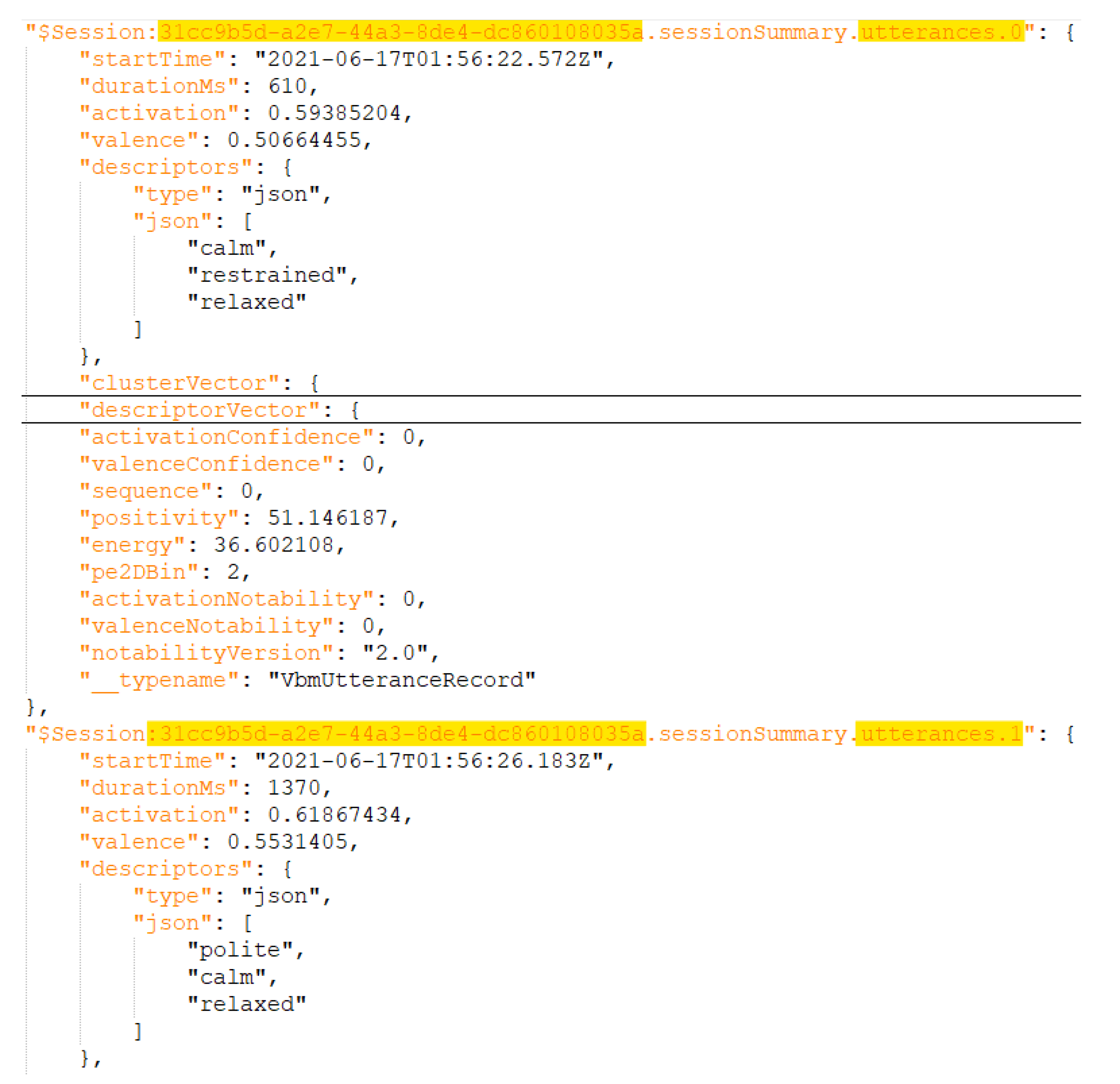
4.1.3. Tone Analysis Artifacts
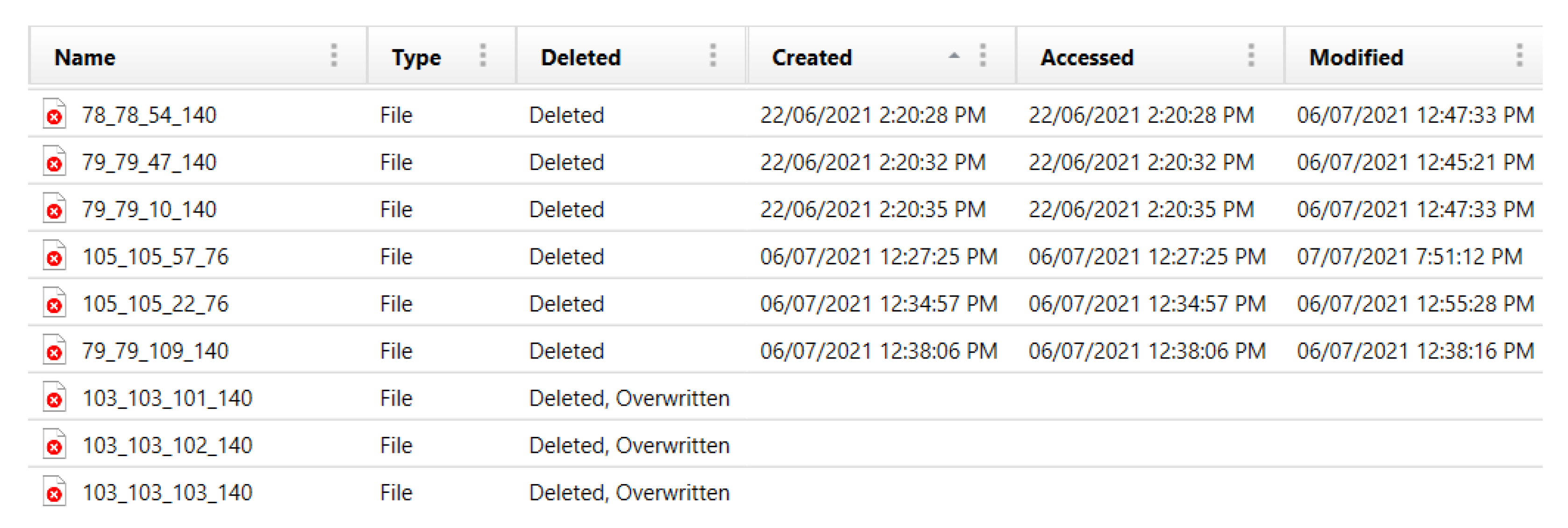
4.1.4. Cache Artifacts
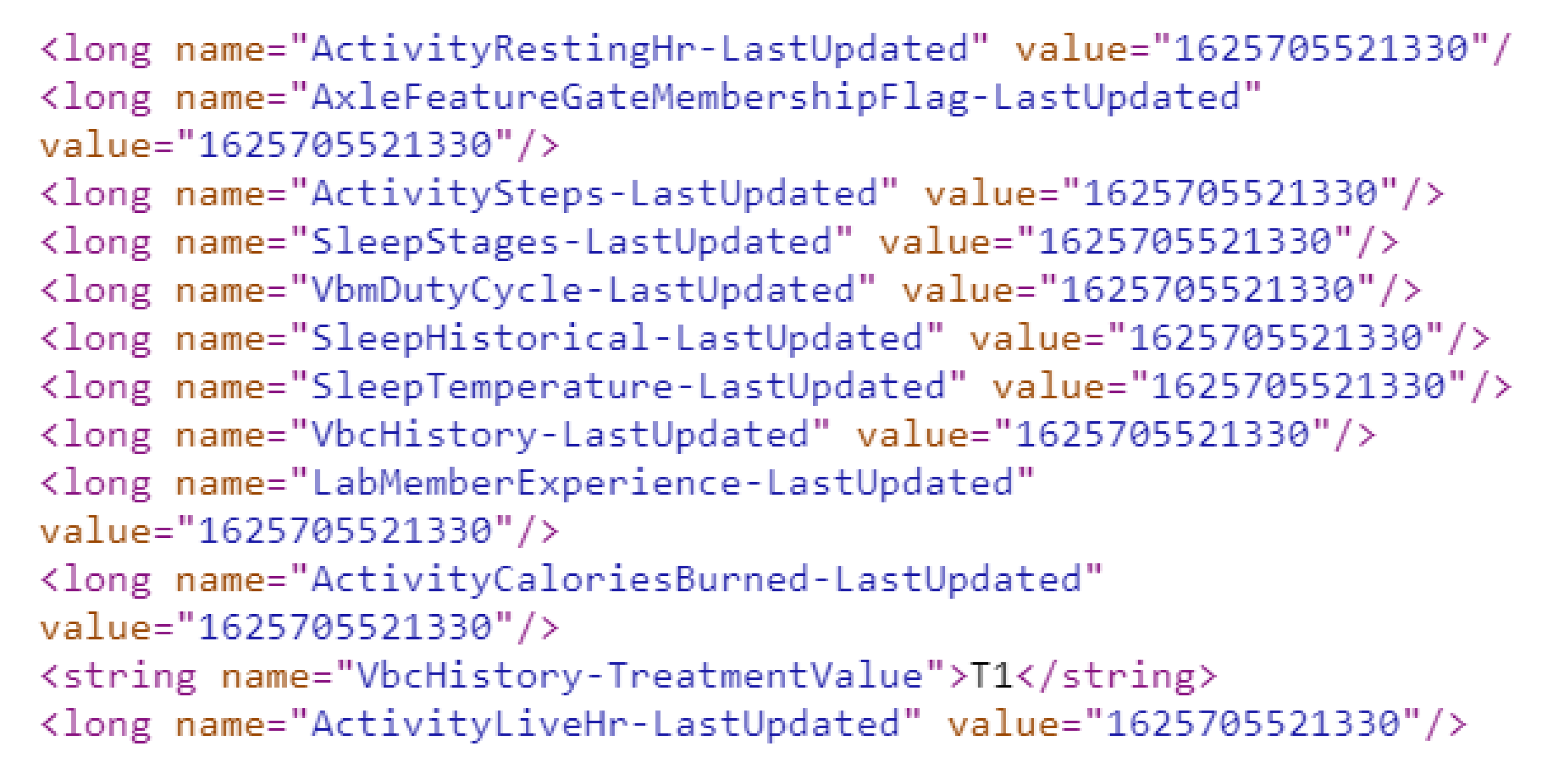
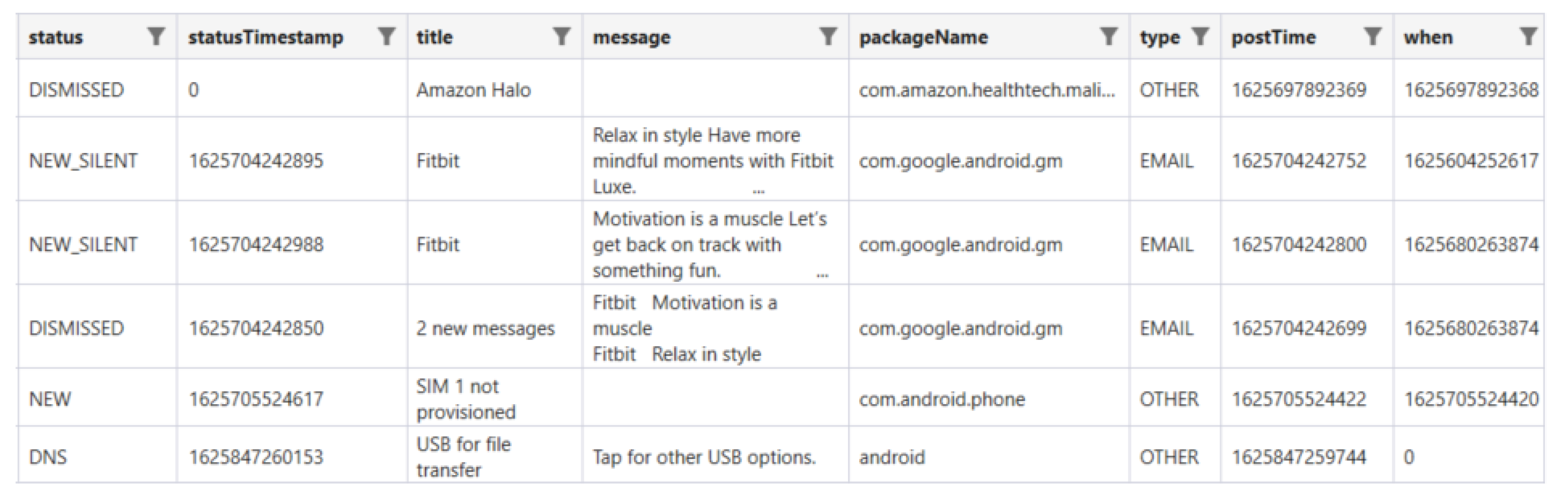
4.1.5. App Usage Artifacts
4.2. Connect (Garmin vívosmart® 4) Artifacts
4.2.1. User Profile Artifacts
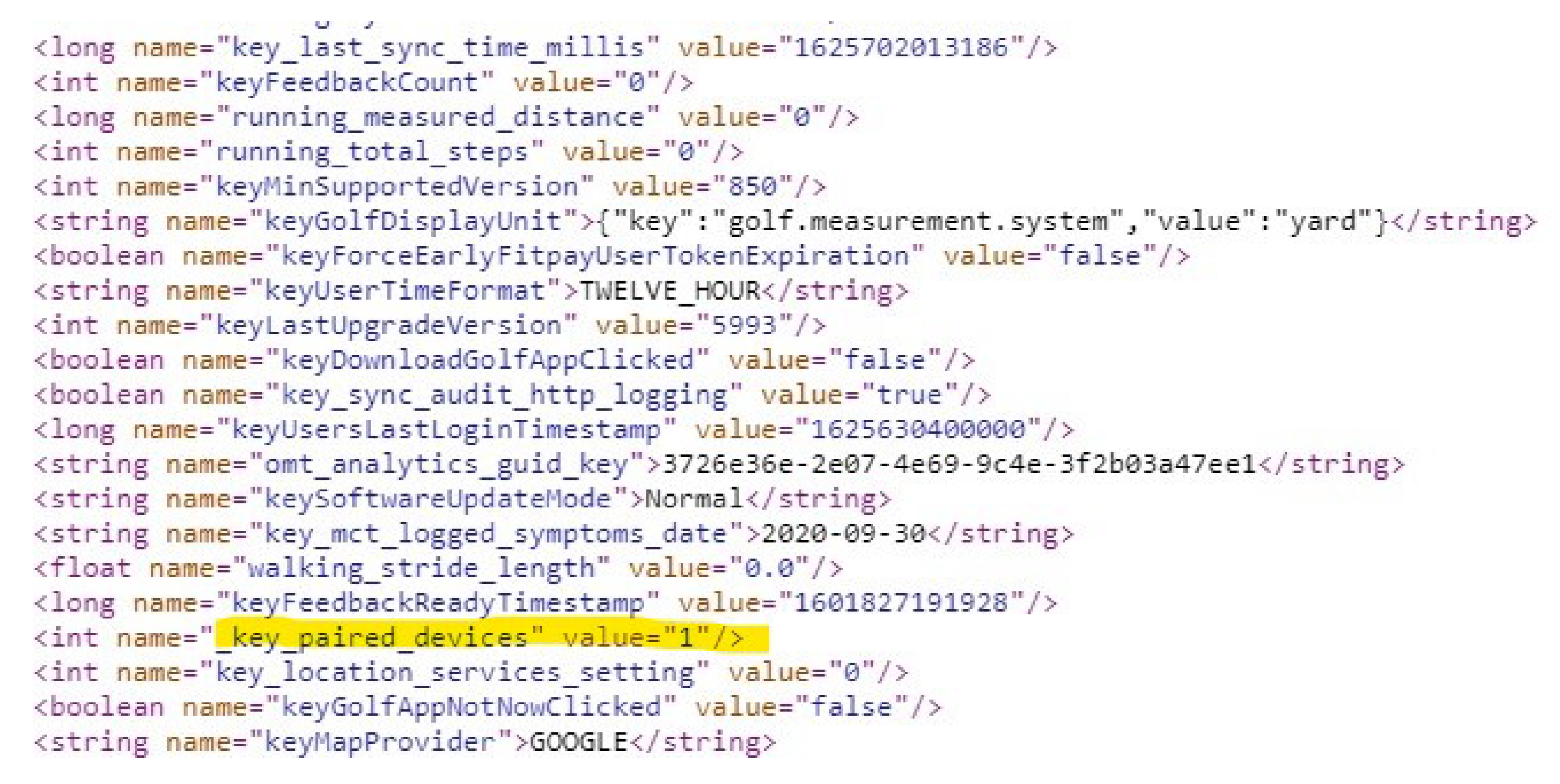
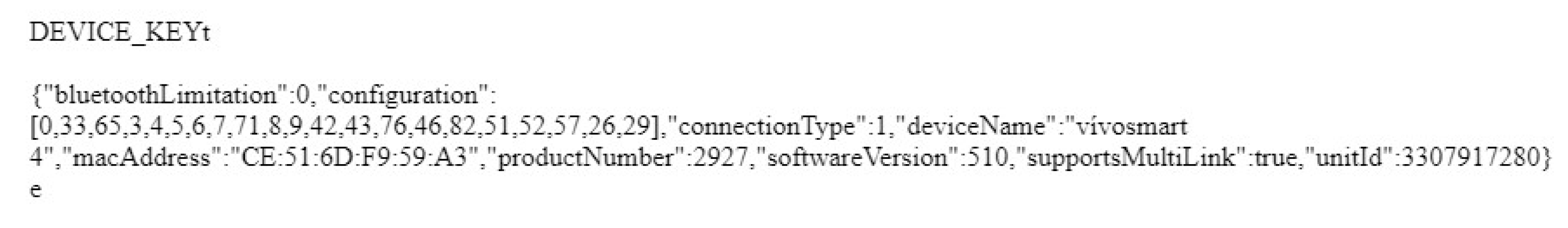
4.2.2. Activity-Related Artifacts
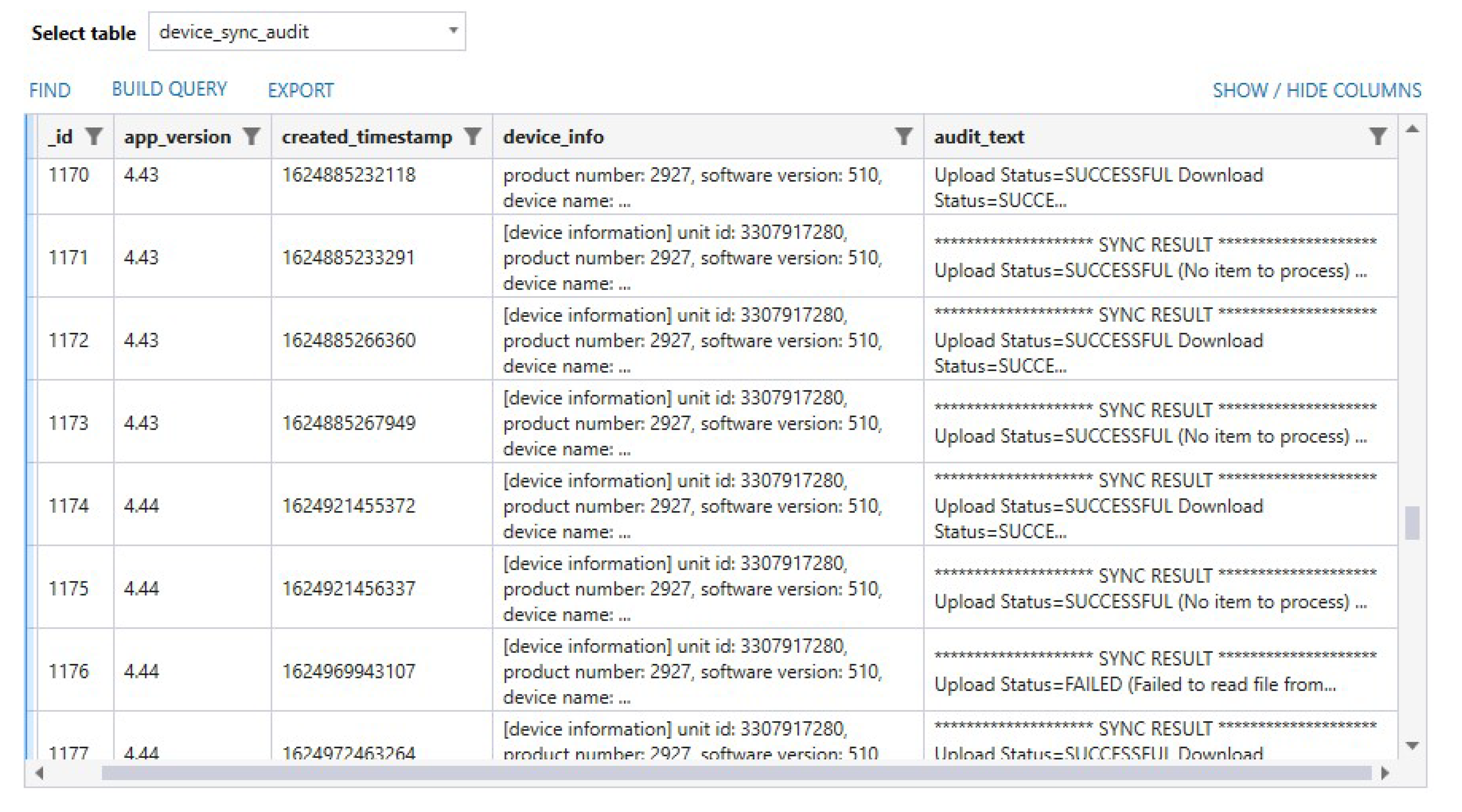
4.2.3. App Usage Artifacts
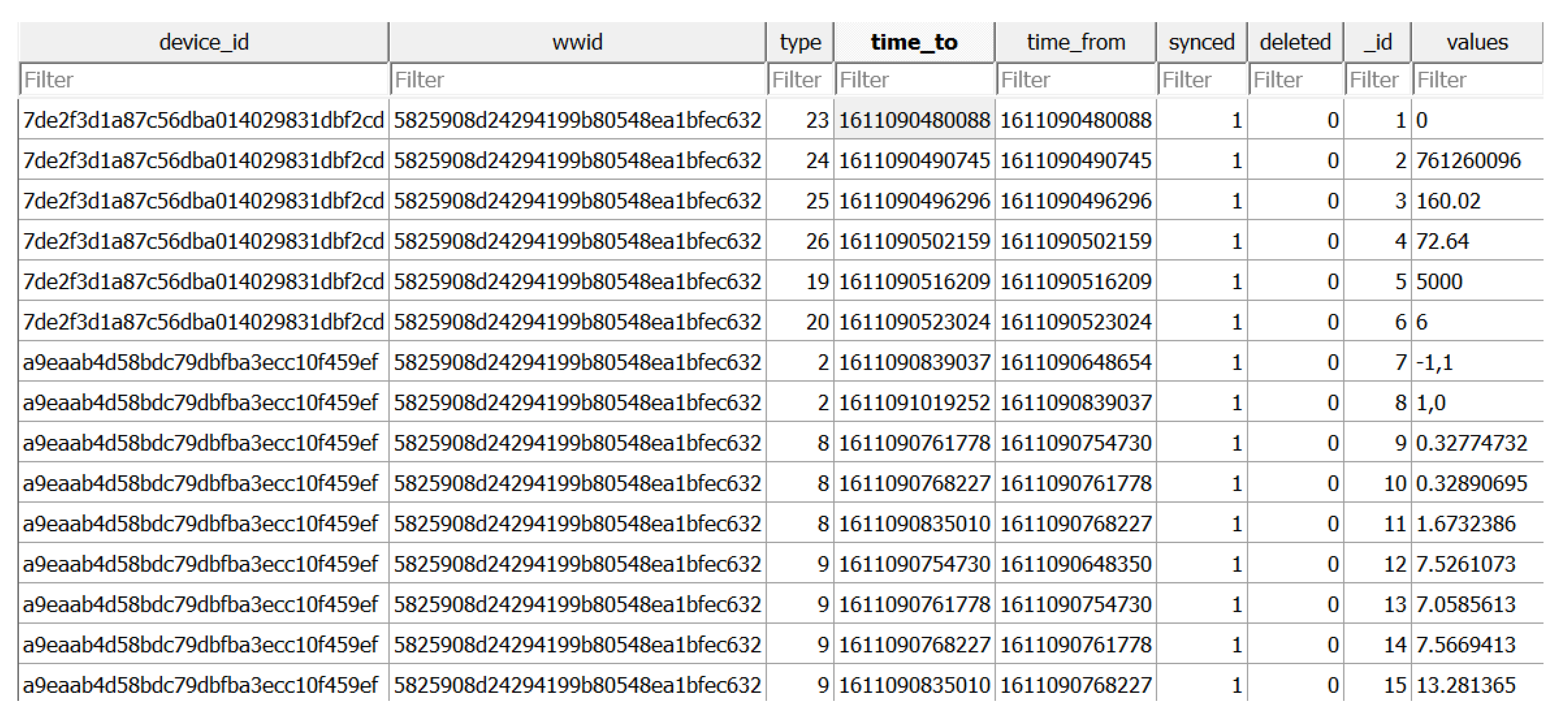
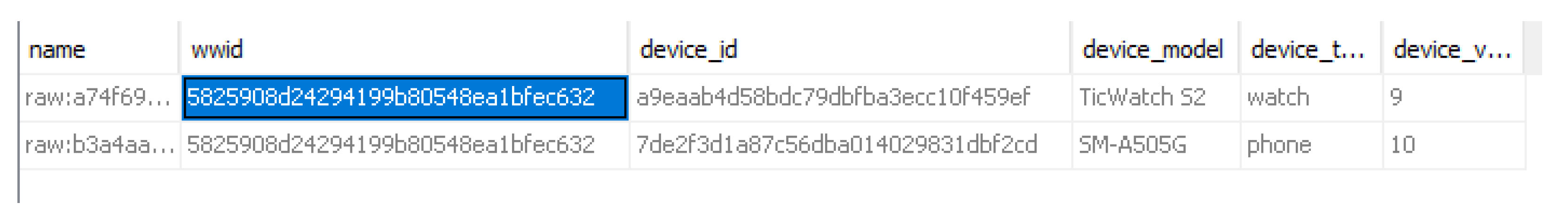
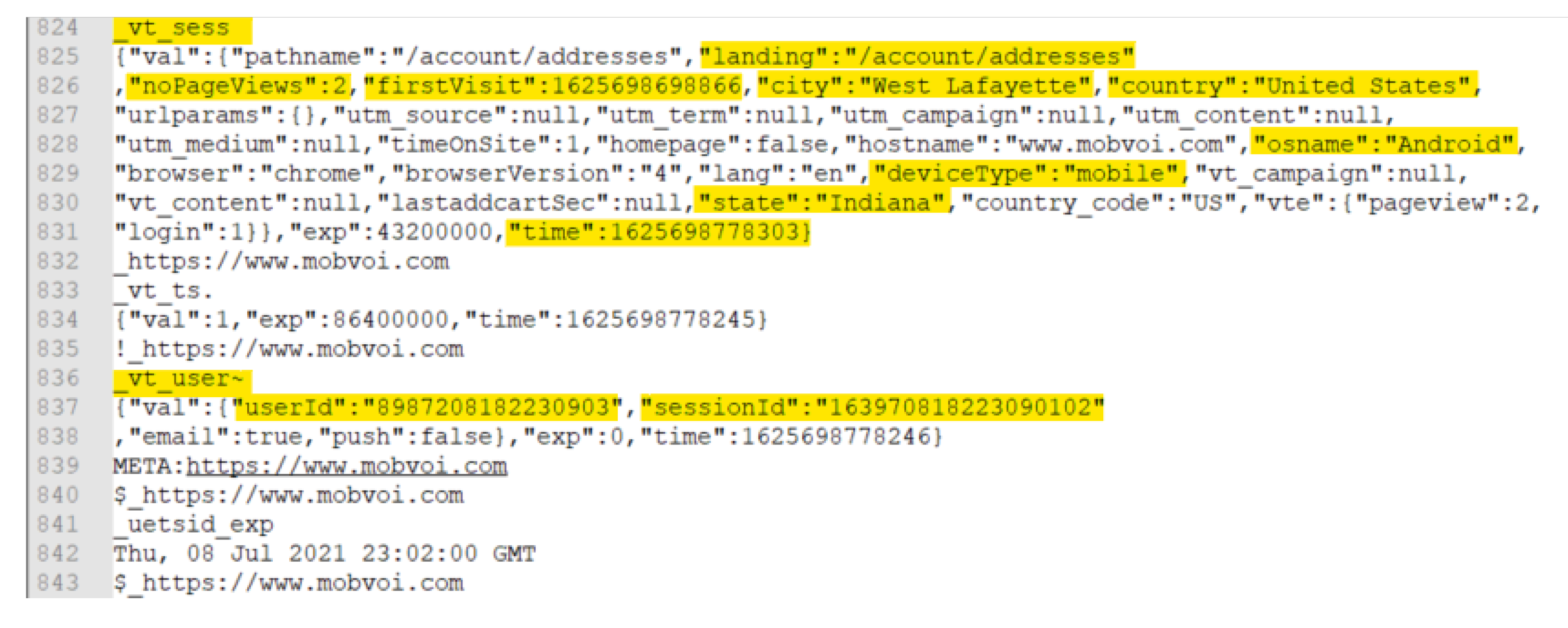
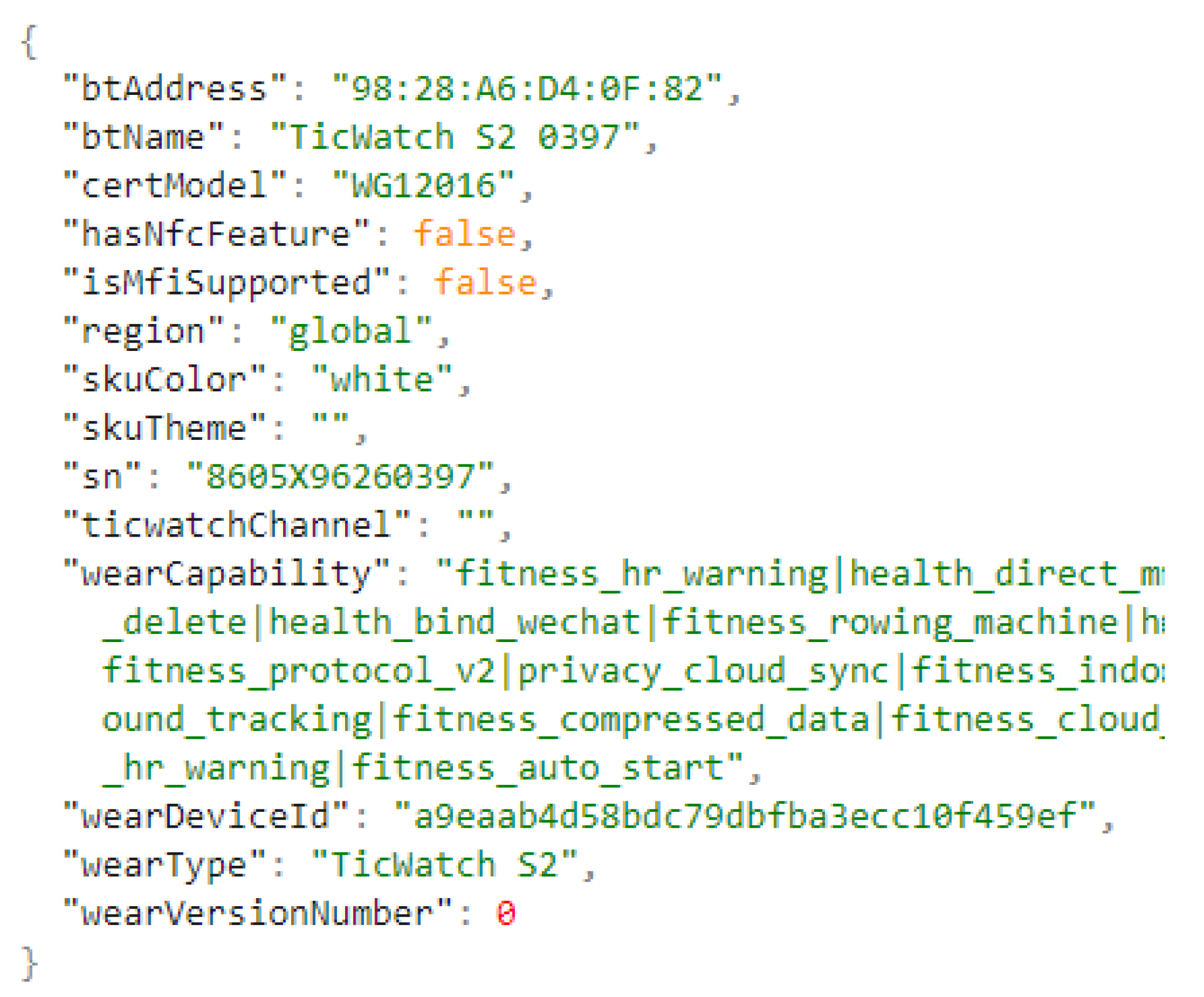
4.3. Mobvoi (TicWatch) Artifacts
4.3.1. User Profile Artifacts
4.3.2. Activity-Related Artifacts
4.3.3. App Usage Artifacts
5. Discussion
5.1. User Privacy Concerns
5.2. Health Data Privacy Concerns
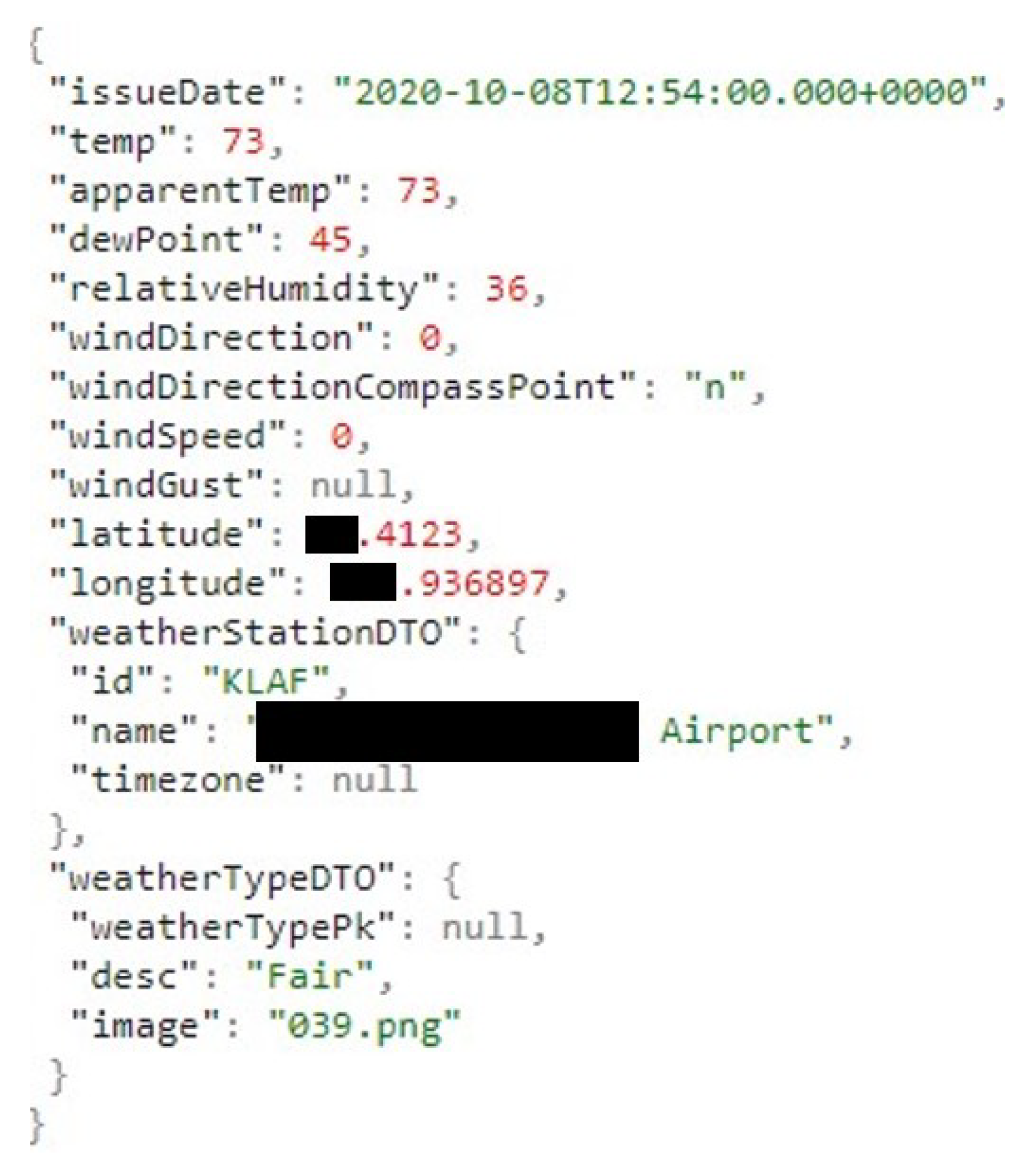
5.3. GPS Locations
5.4. Filesystem Structure and Tool Performance
5.5. Relevance to Forensic Investigations
5.6. Limitations
6. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Wladawsky-Berger, I. The Internet of Things Is Changing the World—WSJ. 2020. Available online: https://www.wsj.com/articles/the-internet-of-things-is-changing-the-world-01578689806 (accessed on 12 August 2021).
- Hayes, A. Wearable Technology Definition. 2020. Available online: https://www.investopedia.com/terms/w/wearable-technology.asp (accessed on 12 August 2021).
- Statista. Wearables Shipments Worldwide 2020 | Statista. 2021. Available online: https://www.statista.com/statistics/437871/wearables-worldwide-shipments/ (accessed on 12 August 2021).
- Global Smartwatch Unit Sales Forecast 2018–2023, Statista_2021. 2021. Available online: https://www.statista.com/statistics/878144/worldwide-smart-wristwear-shipments-forecast (accessed on 12 August 2021).
- Cheap Children Smartwatch Leaks over 5000 Children’s Information Infotech News_2021. 2021. Available online: https://meterpreter.org/cheap-children-smartwatch-leaks-over-5000-childrens-information (accessed on 12 August 2021).
- We have Never Met Six-Year-old KATE—However, a Total Stranger Was Able to Track Her Every Move_2021. 2021. Available online: https://www.abc.net.au/news/2020-02-11/gps-tracking-watch-security-bug-data-breach-personal-info/11909478 (accessed on 12 August 2021).
- Hern, A. Fitness Tracking App Strava Gives Away Location of Secret US Army Bases. 2021. Available online: https://www.theguardian.com/world/2018/jan/28/fitness-tracking-app-gives-away-location-of-secret-us-army-bases (accessed on 12 August 2021).
- Snyder, M. Police: Woman’s Fitness watch DISPROVED Rape Report. Available online: https://www.abc27.com/news/police-womans-fitness-watch-disproved-rape-report/ (accessed on 12 August 2021).
- Lartey, J. Man Suspected in Wife’s Murder after Her Fitbit Data Does not Match His Alibi. 2017. Available online: https://www.theguardian.com/technology/2017/apr/25/fitbit-data-murder-suspect-richard-dabate (accessed on 12 August 2021).
- Wired. A Brutal Murder, a Wearable Witness, and an Unlikely Suspect | WIRED. Available online: https://www.wired.com/story/telltale-heart-fitbit-murder/ (accessed on 21 July 2021).
- BBC. Greece killing: Husband confesses to Caroline Crouch death—BBC News. 2021. Available online: https://www.bbc.com/news/world-europe-57523469 (accessed on 12 August 2021).
- Yoon, Y.H.; Karabiyik, U. Forensic Analysis of Fitbit Versa 2 Data on Android. Electronics 2020, 9, 1431. [Google Scholar] [CrossRef]
- MacDermott, Á.; Lea, S.; Iqbal, F.; Idowu, I.; Shah, B. Forensic analysis of wearable devices: Fitbit, Garmin and HETP Watches. In Proceedings of the 2019 10th IFIP International Conference on New Technologies, Mobility and Security (NTMS), Canary Islands, Spain, 24–26 June 2019; pp. 1–6. [Google Scholar]
- Almogbil, A.; Alghofaili, A.; Deane, C.; Leschke, T. Digital Forensic Analysis of Fitbit Wearable Technology: An Investigator’s Guide. In Proceedings of the 2020 7th IEEE International Conference on Cyber Security and Cloud Computing (CSCloud)/2020 6th IEEE International Conference on Edge Computing and Scalable Cloud (EdgeCom), New York, NY, USA, 1–3 August 2020; pp. 44–49. [Google Scholar]
- Kang, S.; Kim, S.; Kim, J. Forensic analysis for IoT fitness trackers and its application. Peer-to-Peer Netw. Appl. 2020, 13, 564–573. [Google Scholar] [CrossRef]
- Williams, J.; MacDermott, Á.; Stamp, K.; Iqbal, F. Forensic Analysis of Fitbit Versa: Android vs. iOS. In Proceedings of the 2021 IEEE Security and Privacy Workshops (SPW), San Francisco, CA, USA, 27–27 May 2021; pp. 318–326. [Google Scholar]
- Hassenfeldt, C.; Baig, S.; Baggili, I.; Zhang, X. Map My Murder: A Digital Forensic Study of Mobile Health and Fitness Applications. In Proceedings of the 14th International Conference on Availability, Reliability and Security, Canterbury, UK, 26–29 August 2019; pp. 1–12. [Google Scholar]
- Predel, C.; Steger, F. Ethical challenges with smartwatch-based screening for atrial fibrillation: Putting users at risk for marketing purposes? Front. Cardiovasc. Med. 2021, 7, 615927. [Google Scholar] [CrossRef] [PubMed]
- About NIST. 2021. Available online: https://www.nist.gov/about-nist (accessed on 22 September 2022).
- Mobile Android Version Share Worldwide 2018–2021 | Statista_2021. 2021. Available online: https://www.statista.com/statistics/921152/mobile-android-version-share-worldwide/ (accessed on 12 August 2021).
- Root Checker—Apps on Google Play. Available online: https://play.google.com/store/apps/details?id=com.joeykrim.rootcheck&hl=en&gl=US (accessed on 22 December 2021).
- Amazon. Introducing Amazon Halo and Amazon Halo Band—A New Service that Helps Customers Improve Their Health and Wellness. Available online: https://press.aboutamazon.com/news-releases/news-release-details/introducing-amazon-halo-and-amazon-halo-band-new-service-helps (accessed on 4 August 2022).
- Garmin Vivosmart® 4 | Fitness Activity Tracker | Pulse Ox. Available online: https://www.garmin.com/en-US/p/605739#specs (accessed on 4 August 2022).
- TicWatch S2—The Best Smartwatch to Take Your Outdoor Game to the Next Level. Available online: https://www.mobvoi.com/us/pages/ticwatchs2 (accessed on 4 August 2022).
- Whisper—Apps on Google Play. Available online: https://play.google.com/store/apps/details?id=sh.whisper&hl=en_US&gl=US (accessed on 25 January 2022).
- Seçkin, M.; Seçkin, A.Ç.; Gençer, Ç. Biomedical Sensors and Applications of Wearable Technologies on Arm and Hand. Biomed. Mater. Devices 2022, 1–13. [Google Scholar] [CrossRef]
- Forensics, M. Magnet AXIOM—Digital Investigation Platform. Available online: https://www.magnetforensics.com/products/magnet-axiom/ (accessed on 11 August 2021).
- Technology, B. Autopsy. Available online: https://www.basistech.com/autopsy (accessed on 11 August 2021).
- Blythe, J.M.; Johnson, S.D. A systematic review of crime facilitated by the consumer Internet of Things. Secur. J. 2019, 34, 97–125. [Google Scholar] [CrossRef]
- Aktypi, A.; Nurse, J.R.; Goldsmith, M. Unwinding Ariadne’s identity thread: Privacy risks with fitness trackers and online social networks. In Proceedings of the 2017 on Multimedia Privacy and Security, Dallas, TX, USA, 30 October 2017; pp. 1–11. [Google Scholar]
- Kim, M.J. Building a cardiovascular disease prediction model for smartwatch users using machine learning: Based on the Korea National Health and Nutrition Examination Survey. Biosensors 2021, 11, 228. [Google Scholar] [CrossRef] [PubMed]
- Ali, F.; El-Sappagh, S.; Islam, S.R.; Ali, A.; Attique, M.; Imran, M.; Kwak, K.S. An intelligent healthcare monitoring framework using wearable sensors and social networking data. Future Gener. Comput. Syst. 2021, 114, 23–43. [Google Scholar] [CrossRef]
- Moshe, I.; Terhorst, Y.; Asare, K.O.; Sander, L.B.; Ferreira, D.; Baumeister, H.; Mohr, D.C.; Pulkki-Råback, L. Predicting Symptoms of Depression and Anxiety Using Smartphone and Wearable Data. Front. Psychiatry 2021, 12, 625247. [Google Scholar] [CrossRef]
- Quer, G.; Radin, J.M.; Gadaleta, M.; Baca-Motes, K.; Ariniello, L.; Ramos, E.; Kheterpal, V.; Topol, E.J.; Steinhubl, S.R. Wearable sensor data and self-reported symptoms for COVID-19 detection. Nat. Med. 2021, 27, 73–77. [Google Scholar] [CrossRef] [PubMed]
- Amazon.com: Amazon Halo: Amazon Devices & Accessories. Available online: https://www.amazon.com/b?node=23432473011&ref_=ods_hdp_osysk (accessed on 3 November 2021).
- Amazon Halo Privacy—Amazon Customer Service. Available online: https://www.amazon.com/gp/help/customer/display.html?ref_=help_search_1-5&nodeId=GL99TQL4B7ADPBDH&qid=1644432291361&sr=1-5 (accessed on 9 February 2022).
- Artal-Mittelmark, R. Physical Changes During Pregnancy—Women’s Health Issues—Merck Manuals Consumer Version. 2021. Available online: https://www.merckmanuals.com/home/women-s-health-issues/normal-pregnancy/physical-changes-during-pregnancy (accessed on 17 July 2021).
- Acquisti, A.; Fong, C. An experiment in hiring discrimination via online social networks. Manag. Sci. 2020, 66, 1005–1024. [Google Scholar] [CrossRef]
- Post, W. ‘Not Today, Motherf***er’: Runner Takes Down Attacker | HuffPost. Available online: https://www.huffpost.com/entry/kelly-herron-runner-seattle-attack-self-defense-not-today_n_58c654d3e4b054a0ea6b7a4b (accessed on 21 July 2021).
- The Police Successfully Tracked The Whereabouts Of Kidnapping Victims Using The Apple Watch. Available online: https://voi.id/en/technology/28675/the-police-successfully-tracked-the-whereabouts-of-kidnapping-victims-using-the-apple-watch (accessed on 14 February 2022).



| Article Title | Gap | Objective | Shortcoming | Our Solution |
|---|---|---|---|---|
| Forensic Analysis of Fitbit Versa: Android vs. iOS [16] | Limited wearable forensics research | To perform a forensic analysis of the Fitbit Versa using Cellebrite UFED and MSAB XRY | These authors focused on an overstudied device and app (Fitbit) and limited their tools to some of the most expensive in the market. | In the current study, the authors investigate a diversity of wearable fitness devices using both commercial and open-source tools. |
| Forensic Analysis of Fitbit Versa 2 Data on Android [12] | Lack of research regarding new wearables | To perform a forensic investigation of the newly released Fitbit Versa 2 smartwatch using Magnet AXIOM and MSAB XRY. | These authors also investigated the overstudied wearable controlling app (Fitbit) on an older Android OS (Android 7-Nougat) despite the newest Android OS (Android 9-Pie) being available at the time. | The current study improves on this research by performing the forensic investigation on a newer mobile OS (Android 10) and three different wearable fitness brands. |
| Forensic analysis for IoT fitness trackers and its application [15] | Limited wearable forensics research | To perform a forensic investigation of the companion apps for the Mi Band 2 and Fitbit Alta HR fitness trackers on an Android 7 device. | These authors again investigated the overstudied Fitbit app on an older Android OS. The authors also failed to detail the data population methodology followed. | The current study improves on this work by investigating a novel wearable app (Halo) on a newer and more popular Android OS. The current study also provides a detailed methodology covering all stages of the Digital Forensics Investigative process. |
| Digital Forensic Analysis of Fitbit Wearable Technology: An Investigator’s Guide [14] | Need for updated forensic analysis of the Fitbit app | To perform a forensic investigation of two Fitbit devices when used with the Fitbit desktop app. The authors performed their investigation using open source tools like Autopsy and Bulk Extractor Viewer. | The authors focused their inves- tigation on the Windows 10 Fitbit app and did not include the mobile app nor any other popular smartwatch devices at the time. | The current study build on this work by investigating one of the newest fitness bands at the time, the Amazon Halo band. |
| Forensic analysis of wearable devices: Fitbit, Garmin and HETP Watches [13] | Limited wearable forensics research | To perform a forensic investigation of Garmin and Fitbit fitness bands on the device level and Windows 10 app level, respectively. | These authors did not consider the companion mobile apps for these wearables | The current study builds on this work by providing an investigation of the Garmin Connect mobile app. |
| Map My Murder: A Digital Forensic Study of Mobile Health and Fitness Applications [17] | Lack of forensic research regarding health and fitness apps | To perform a forensic investigation of 13 health/fitness apps on Android 6 and Android 7 devices. The authors also investigate the privacy concerns introduced to app users due to using these apps. | This investigation was conducted on some of the older Android OSs at the time. Furthermore, the data population steps are not sufficiently detailed. | The current study explores the privacy concerns introduced to users when they use three of the more affordable, wearable fitness devices, on one of the most popular Android OSs at the time. |
| Device Name | Model/Version | Device ID |
|---|---|---|
| Amazon Halo Band | DYLAN | S/N: G0G13P05129200WV |
| Garmin vívosmart® 4 | - | Unit ID: 3307917280 |
| Mobvoi TicWatch S2 0397 | WG12016 | S/N: 8605X96260397 |
| Samsung Galaxy A50 | SM-A505G/DS | IMEI 1: 354463104240381 IMEI 2: 354463104240389 |
| Feature | Wearable Device | ||
|---|---|---|---|
| Amazon Halo | Garmin vívosmart® 4 | TicWatch S2 | |
| Heart Rate | Yes | Yes | Yes |
| Step Count | Yes | Yes | Yes |
| Exercise Activity | Yes | Yes | Yes |
| GPS Locations | No | Yes | Yes |
| Sleep Data | Yes | Yes | No |
| Stress Data | No | Yes | No |
| Voice Data | Yes | No | No |
| Notifications | No | Yes | Yes |
| Software Name | Version | Usage |
|---|---|---|
| Amazon Halo | 1.0.270609.0-Store_145454 | Health Monitoring |
| Connect | 4.42 | Health Monitoring |
| Mobvoi | 3.22.1-1367.602 | Health Monitoring |
| Wear OS | 2.49.0.381033832.gms | Linking TicWatch with Android phone |
| Whisper | 9.48.1 | Notification Generation |
| Autopsy | 4.19.1 | Examination and Analysis |
| DB Browser for SQLite | 3.12.2 | Viewing database files |
| Cellebrite UFED 4PC | 7.45.1.43 | Acquisition |
| Magnet AXIOM Process | 5.2.0.25407 | Acquisition |
| Magnet AXIOM Examine | 5.3.0.25803 | Examination and Analysis |
| ExifTool | 12.30 | Reading Exif data |
| DCode | 5.5.21194.40 | Forensic Timestamp Decoder |
| Codebeautify.org/jsonviewer | Web version | JSON viewer and formatter |
| Application | Version | Package Path |
|---|---|---|
| Amazon Halo | 1.0.275548.0-Store_160368 | data\data\com.amazon.healthtech.malibu |
| Connect | 4.43 | data\data\com.garmin.android.apps.connectmobile |
| Mobvoi | 4.1.1-1664.650 | data\data\com.mobvoi.companion.aw |
| Artifact Category | Amazon Halo | Garmin Connect | Mobvoi |
|---|---|---|---|
| Profile Information | ✓ | ✓ | ✓ |
| Heart Rate Data | ✓ | P | ✓ |
| Steps Data | ✓ | ✓ | ✓ |
| Exercise Activity Data | ✓ | ✓ | ✓ |
| GPS Data | N/A | P | P |
| Sleep Data | ✓ | ✓ | ✓ |
| Stress Data | N/A | ✓ | N/A |
| Voice Data | P | N/A | N/P |
| App Notifications | N/A | ✓ | X |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hutchinson, S.; Mirza, M.M.; West, N.; Karabiyik, U.; Rogers, M.K.; Mukherjee, T.; Aggarwal, S.; Chung, H.; Pettus-Davis, C. Investigating Wearable Fitness Applications: Data Privacy and Digital Forensics Analysis on Android. Appl. Sci. 2022, 12, 9747. https://doi.org/10.3390/app12199747
Hutchinson S, Mirza MM, West N, Karabiyik U, Rogers MK, Mukherjee T, Aggarwal S, Chung H, Pettus-Davis C. Investigating Wearable Fitness Applications: Data Privacy and Digital Forensics Analysis on Android. Applied Sciences. 2022; 12(19):9747. https://doi.org/10.3390/app12199747
Chicago/Turabian StyleHutchinson, Shinelle, Mohammad Meraj Mirza, Nicholas West, Umit Karabiyik, Marcus K. Rogers, Tathagata Mukherjee, Sudhir Aggarwal, Haeyong Chung, and Carrie Pettus-Davis. 2022. "Investigating Wearable Fitness Applications: Data Privacy and Digital Forensics Analysis on Android" Applied Sciences 12, no. 19: 9747. https://doi.org/10.3390/app12199747
APA StyleHutchinson, S., Mirza, M. M., West, N., Karabiyik, U., Rogers, M. K., Mukherjee, T., Aggarwal, S., Chung, H., & Pettus-Davis, C. (2022). Investigating Wearable Fitness Applications: Data Privacy and Digital Forensics Analysis on Android. Applied Sciences, 12(19), 9747. https://doi.org/10.3390/app12199747










