The Role of Privacy Fatigue in Privacy Paradox: A PSM and Heterogeneity Analysis
Abstract
:1. Introduction
- (1)
- Is privacy fatigue among users of mobile social media the reason leading to the phenomenon of the privacy paradox?
- (2)
- Would individual differences among users of mobile social media affect the explanatory strength of privacy fatigue in the privacy paradox phenomenon?
2. Literature Review
2.1. Privacy Paradox
2.2. Privacy Fatigue
3. Theoretical Background and Hypothesis Development
3.1. Elaboration Likelihood Model Theory
3.2. Hypothesis Development
3.2.1. Central Route: Privacy Fatigue and Privacy Paradox
3.2.2. Peripheral Route: Heterogeneous Influences on Privacy Paradox
4. Methodology and Data Collection
4.1. Designing the Research Method
4.2. Defining Variables
4.2.1. Core Variables
4.2.2. Control Variables
4.3. Source of Data and Sample Selection
5. Empirical Analysis
5.1. Estimation of Propensity Score
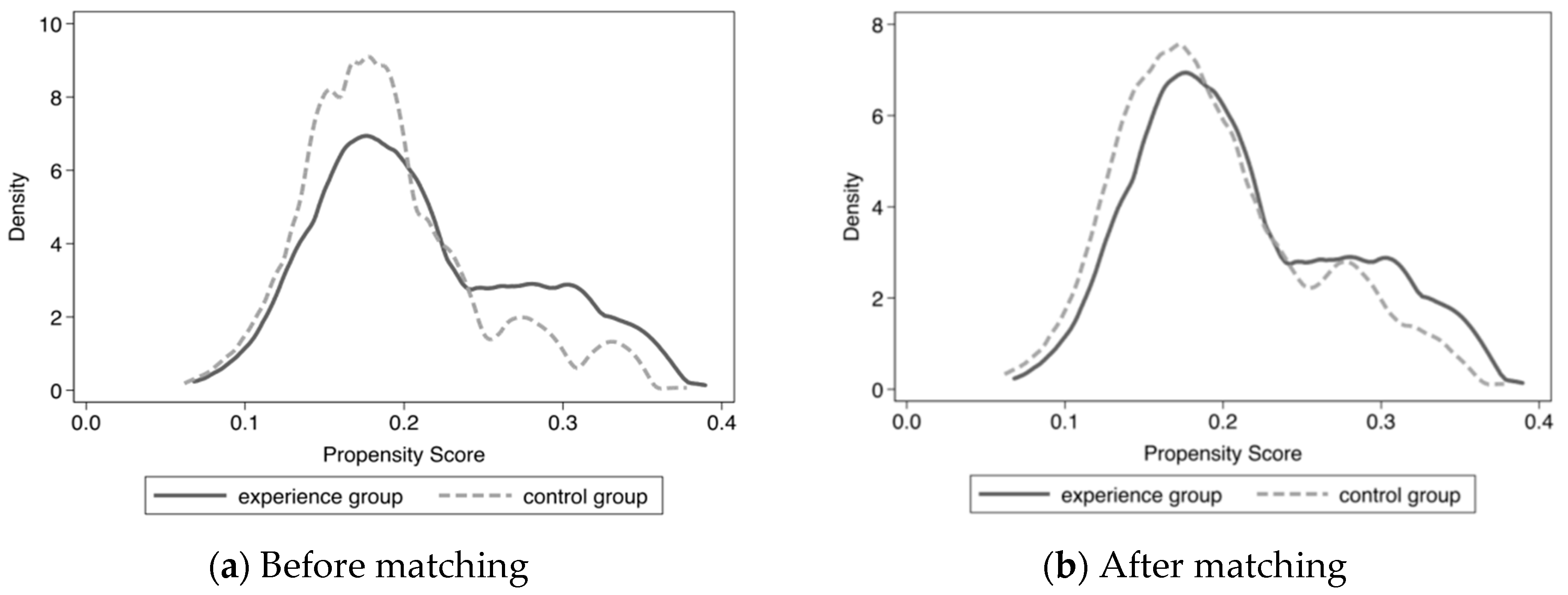
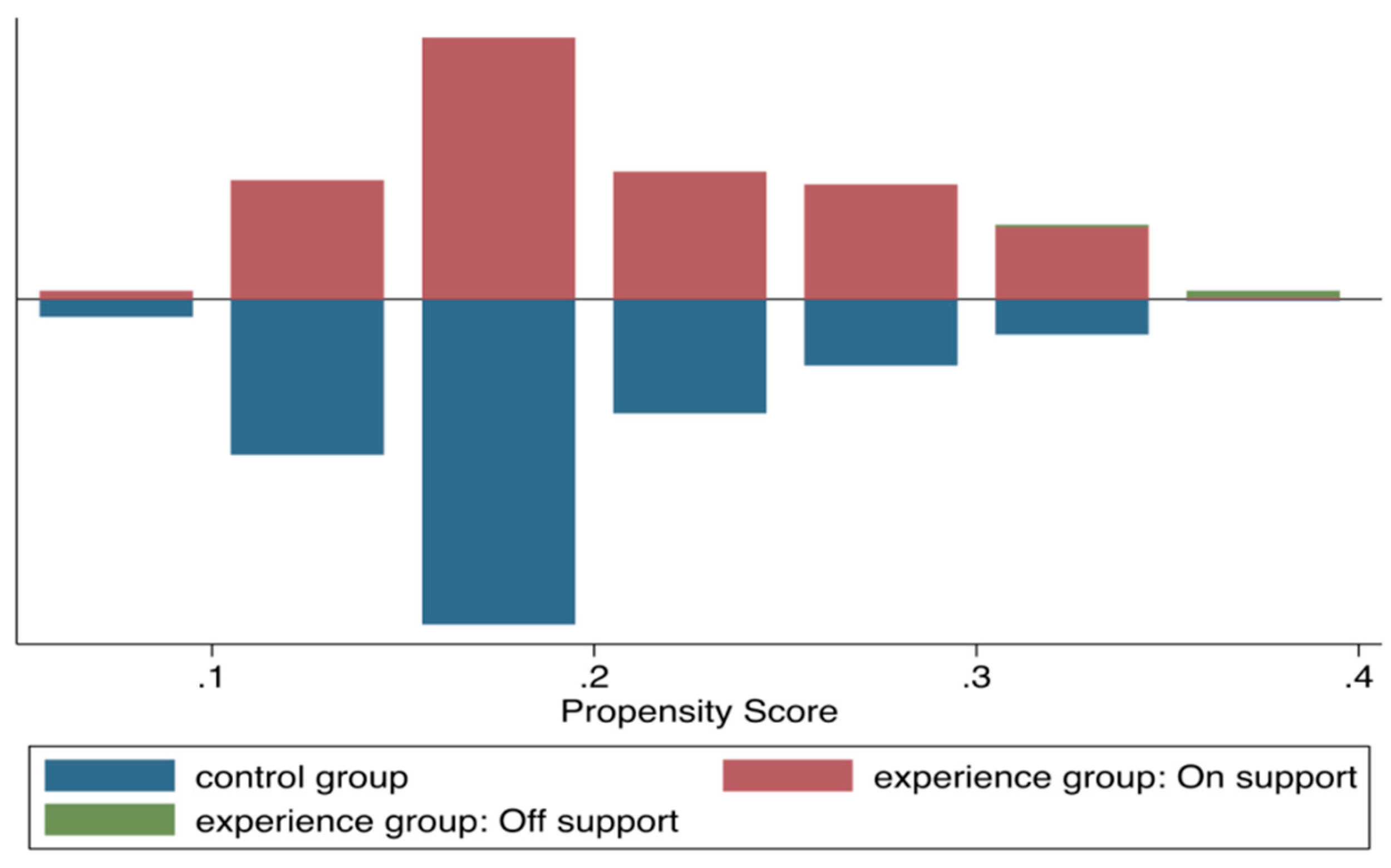
5.2. Assessing the Matching Quality
5.3. Analysis of Empirical Results
5.4. Robustness Test
5.5. Heterogeneity Analysis
6. Conclusion and Insights
6.1. Main Findings
6.2. Theoretical Significance
6.3. Practical Implications
6.4. Limitations and Further Studies
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Awad, N.F.; Krishnan, M.S. The personalization privacy paradox: An empirical evaluation of information transparency and the willingness to be profiled online for personalization. Mis Q. 2006, 30, 13–28. [Google Scholar] [CrossRef]
- Tufekci, Z.; Wilson, C. Social Media and the Decision to Participate in Political Protest: Observations From Tahrir Square. J. Commun. 2012, 62, 363–379. [Google Scholar] [CrossRef]
- Bernhard, D.; Lovejoy, J.P.; Ann-Kathrin, H.; Brittany, N.H. Facebook and Online Privacy: Attitudes, Behaviors and Unintended Consequences. J. Comput.-Mediat. Commun. 2009, 15, 83–108. [Google Scholar]
- Reynolds, B.; Venkatanathan, J.; Gonalves, J.; Kostakos, V. Sharing Ephemeral Information in Online Social Networks: Privacy Perceptions and Behaviours. In IFIP Conference on Human-Computer Interaction; Conference Paper; Springer: Berlin/Heidelberg, Germany, 2011; pp. 204–215. [Google Scholar]
- Barth, S.; Jong, M.D.; Junger, M.; Hartel, P.H.; Roppelt, J.C. Putting the privacy paradox to the test: Online privacy and security behaviors among users with technical knowledge, privacy awareness, and financial resources. Telemat. Inform. 2019, 41, 55–69. [Google Scholar] [CrossRef]
- Spiekermann, S.; Berendt, B.; Grossklags, J. E-privacy in 2nd Generation E-Commerce: Privacy Preferences Versus Actual Behavior. Social Science Electronic Publishing. In Proceedings of the 3rd ACM Conference on Electronic Commerce, Tampa, FL, USA, 14–17 October 2001; pp. 38–47. [Google Scholar]
- Norberg, P.A.; Horne, D.R.; Horne, D.A. The Privacy Paradox: Personal Information Disclosure Intentions versus Behaviors. J. Consum. Aff. 2007, 41, 100–126. [Google Scholar] [CrossRef]
- Masur, P.K. Understanding the effects of conceptual and analytical choices on ‘finding’ the privacy paradox: A specification curve analysis of large-scale survey data. Inf. Commun. Soc. 2021, 1–19. [Google Scholar] [CrossRef]
- Choi, H.; Park, J.; Jung, Y. The role of privacy fatigue in online privacy behavior. Comput. Hum. Behav. 2018, 81, 42–51. [Google Scholar] [CrossRef]
- Kwon, J.; Johnson, M.E. The Market Effect of Healthcare Security: Do Patients Care about Data Breaches? Workshop on the Economics of Information Security. Neth. Delft 2015, 6, 22–23. [Google Scholar]
- Kaspersky. The True Value of Digital Privacy: Are Consumers Selling Themselves Short? 2019. Available online: https://www.kaspersky.com/blog/privacy-report-2019/ (accessed on 20 August 2022).
- Junglas, I.A.; Spitzmüller, C. Personality Traits and Privacy Perceptions: An Empirical Study in the Context of Location-Based Services. Eur. J. Inf. Syst. 2008, 17, 387–402. [Google Scholar] [CrossRef]
- Warren, S.D.; Brandeis, L.D. The right to privacy. Harv. Law Rev. 1890, 4, 193–220. [Google Scholar] [CrossRef]
- Dhir, A.; Kaur, P.; Chen, S.; Pallesen, S. Antecedents and consequences of social media fatigue. Int. J. Inf. Manag. 2019, 48, 193–202. [Google Scholar] [CrossRef]
- Dienlin, T.; Trepte, S. Is the privacy paradox a relic of the past? An in-depth analysis of privacy attitudes and privacy behaviors. Eur. J. Soc. Psychol. 2015, 45, 285–297. [Google Scholar] [CrossRef]
- Barness, B. A privacy paradox: Social networking in the United States. First Monday 2006, 11, 5–7. [Google Scholar] [CrossRef]
- Baek, Y.M.; Kim, E.M.; Bae, Y. My privacy is okay, but theirs is endangered: Why comparative optimism matters in online privacy concerns. Comput. Hum. Behav. 2014, 31, 48–56. [Google Scholar] [CrossRef]
- Cho, H.; Lee, J.S.; Chung, S. Optimistic bias about online privacy risks: Testing the moderating effects of perceived controllability and prior experience. Comput. Hum. Behav. 2010, 26, 987–995. [Google Scholar] [CrossRef]
- Jensen, C.; Potts, C.; Jensen, C. Privacy practices of Internet users: Self-reports versus observed behavior. Int. J. Hum.-Comput. Stud. 2005, 63, 203–227. [Google Scholar] [CrossRef]
- Wilson, D.W.; Valacich, J.S. Unpacking the Privacy Paradox: Irrational Decision-Making within the Privacy Calculus. Proceedings of the 33rd International Conference on Information Systems. Florida 2012, 41, 114–125. [Google Scholar]
- Karwatzki, S.; Dytynko, O.; Trenz, M.; Veit, D. Beyond the personalization–privacy paradox: Privacy valuation, transparency features, and service personalization. J. Manag. Inf. Syst. 2017, 34, 369–400. [Google Scholar] [CrossRef]
- Stutzman, F.; Capra, R.; Thompson, J. Factors mediating disclosure in social network sites. Comput. Hum. Behav. 2011, 27, 590–598. [Google Scholar] [CrossRef]
- Xu, H.; Teo, H.H.; Tan, B.; Agarwal, R. The role of push pull technology in privacy calculus: The case of location based services. J. Manag. Inf. Syst. 2010, 26, 135–174. [Google Scholar] [CrossRef]
- Piper, B.F.; Lindsey, A.M.; Dodd, M.J. Fatigue mechanisms in cancer patients: Developing nursing theory. Oncol. Nurs. Forum 1987, 14, 17–23. [Google Scholar] [PubMed]
- Tang, J.; Akram, U.; Shi, W. Why people need privacy? The role of privacy fatigue in app users’ intention to disclose privacy: Based on personality traits. J. Enterp. Inf. Manag. 2020, 8, 1–24. [Google Scholar] [CrossRef]
- Hargittai, E.; Marwick, A. What Can I Really Do?: Explaining Online Apathy and the Privacy Paradox. Soc. Sci. Electron. Publ. 2015, 10, 3737–3757. [Google Scholar]
- Bansal, G.; Zahedi, F.; Gefen, D. The impact of personal dispositions on information sensitivity, privacy concern and trust in disclosing health information online. Decis. Support Syst. 2010, 49, 138–150. [Google Scholar] [CrossRef]
- Chen, H.; Beaudoin, C.E.; Hong, T. Securing online privacy: An empirical test on internet scam victimization, online privacy concerns, and privacy protection behaviors. Comput. Hum. Behav. 2017, 70, 291–302. [Google Scholar] [CrossRef]
- Furnell, S.; Thomson, K.L. Recognising and addressing ‘security fatigue’. Comput. Fraud Secur. 2009, 11, 7–11. [Google Scholar] [CrossRef]
- Petty, R.E.; Cacioppo, J.T. The Elaboration Likelihood Model of Persuasion; Communication and Persuasion; Springer: New York, NY, USA, 1986; pp. 1–24. [Google Scholar]
- Bhattacharjee, A.; Sanford, C. Influence processes for information technology acceptance: An elaboration likelihood model. MIS Q. 2006, 30, 805–825. [Google Scholar] [CrossRef]
- Lee, J.; Park, D.H.; Han, I. The effect of negative online consumer reviews on product attitude: An information processing view. Electron. Commer. Res. Appl. 2008, 7, 341–352. [Google Scholar] [CrossRef]
- Bi, S.; Liu, Z.; Usman, K. The influence of online information on investing decisions of reward-based crowdfunding. J. Bus. Res. 2017, 71, 10–18. [Google Scholar] [CrossRef]
- Zhu, M.; Wu, C.; Huang, S.; Zheng, K.; Young, S.D.; Yan, X.; Yuan, Q. Privacy paradox in mHealth applications: An integrated elaboration likelihood model incorporating privacy calculus and privacy fatigue. Telemat. Inform. 2021, 61, 101601. [Google Scholar] [CrossRef]
- Park, D.H.; Lee, J.; Han, I. The effect of on-line consumer reviews on consumer purchasing intention: The moderating role of involvement. Int. J. Electron. Commer. 2007, 11, 125–148. [Google Scholar] [CrossRef]
- Zhou, T.; Lu, Y.; Wang, B. Examining online consumers’ initial trust building from an elaboration likelihood model perspective. Inf. Syst. Front. 2016, 18, 265–275. [Google Scholar] [CrossRef]
- Mamonov, S.; Benbunan-Fich, R. Exploring factors affecting social e-commerce service adoption: The case of Facebook gifts. Int. J. Inf. Manag. 2017, 37, 590–600. [Google Scholar] [CrossRef]
- Feng, Y.; Xie, W. Teens concern for privacy when using social net-working sites: An analysis of socializations agents and relationships with privacy-protecting behaviors. Comput. Hum. Behav. 2014, 33, 153–162. [Google Scholar] [CrossRef]
- Carver, C.S.; Scheier, M.F.; Weintraub, J.K. Assessing coping strategies: A theoretically based approach. J. Personal. Soc. Psycho 1989, 56, 267–283. [Google Scholar] [CrossRef]
- Lee, E. Why do people leave SNS? The Influences of the Users’ Characteristics and SNS Fatigue. J. HCI Soc. Korea 2018, 13, 11–19. [Google Scholar] [CrossRef]
- Adhikari, K.; Panda, R.K. Evaluation of brand relationship quality using formative index: A novel measurement approach. J. Prod. Brand Manag. 2019, 29, 505–516. [Google Scholar] [CrossRef]
- Ravindran, T.; Kuan, A.C.Y.; Lian, D.G.H. Antecedents and effects of social network fatigue. J. Assoc. Inf. Sci. Technol. 2014, 65, 2306–2320. [Google Scholar] [CrossRef]
- Kim, M.S.; Lee, D.J. The role of digital fatigue and flow in SNS usage. E-Bus. Stud. 2012, 13, 67–87. [Google Scholar]
- Tu, F. WeChat and civil society in China. Commun. Public 2016, 3, 343–350. [Google Scholar] [CrossRef]
- Tencent. Second Quarter and Annual Results Announcement. 2022. Available online: https://view.inews.qq.com/k/20220817A06YCJ00?web_channel=wap&openApp=false (accessed on 20 August 2022).
- Rubin, D.B. Using propensity scores to help design observational studies: Application to the tobacco litigation. Health Serv. Outcomes Res. Methodol. 2001, 2, 169–188. [Google Scholar] [CrossRef]
- Cyr, D.; Head, M.; Lim, E.; Stibe, A. Using the elaboration likelihood model to examine online persuasion through website design. Inf. Manag. 2018, 55, 807–821. [Google Scholar] [CrossRef]
- Shankar, A.; Jebarajakirthy, C.; Ashaduzzaman, M. How do electronic word of mouth practices contribute to mobile banking adoption? Retail. Consum. Serv. 2020, 52, 101920. [Google Scholar] [CrossRef]
- Crlab, C.; Eza, D.; Jthab, C. Adoption of online follow-up service by patients: An empirical study based on the elaboration likelihood model. Comput. Hum. Behav. 2020, 114, 106581. [Google Scholar]

| Variables | Items asked | |
|---|---|---|
| Privacy fatigue | Cynicism | 1. I am starting to hold a skeptical attitude towards the importance of the privacy issue on social networks. |
| 2. I believe measures I have adopted to protect privacy (such as masking identity information, setting visible zone for friends’ circle) have no big effect on preventing my privacy from being threatened. | ||
| 3. If someone wants to invade my privacy on social media, relying on my own to defend it is far from enough. | ||
| Emotional exhaustion | 1. I loathe taking privacy protection measures (such as signing privacy agreements, setting visible zone for friends’ circle) in the social network environment. | |
| 2. Privacy leaks occur frequently, so I would not take further measures. | ||
| 3. Information on privacy in social media is too complicated, exceeding what I can handle. | ||
| Privacy paradox | Privacy concern | 1. When WeChat asks for my personal information, I would think it over carefully. |
| 2. I worry that WeChat would sell my personal information to other companies for other uses. | ||
| 3. I worry that other people can discover my personal information on WeChat (friends’ circle). | ||
| Intention for privacy protection behavior | 1. When WeChat requires me to register, I supply false personal information. | |
| 2. I don’t provide my information (such as day of birth, photo, location, etc.) which can identify me on WeChat, as much as possible. | ||
| 3. When WeChat suggests saving my log-in and password for later use, I would reject. | ||
| Variables’ Dimensions | Choices and Values | |
|---|---|---|
| Individual characteristics | Gender | “Male” = 1 |
| “Female” = 2 | ||
| Age | “Under 20” = 1 | |
| “20–30” = 2 | ||
| “30–40” = 3 | ||
| “40–50” = 4 | ||
| “Over 50” = 5 | ||
| Level of education | “High school and under” = 1 | |
| “Undergraduate and tertiary” = 2 | ||
| “Master’s student” = 3 | ||
| “Doctor’s student” = 4 | ||
| Usage characteristics | No. of friends on WeChat | “Under 100” = 1 |
| “100–300” = 2 | ||
| “300–600” = 3 | ||
| “600–1000” = 4 | ||
| “Over 1000” = 5 | ||
| Usage duration | “Under one hour per day” = 1 | |
| “1–3 h daily” = 2 | ||
| “3–5 h daily” = 3 | ||
| “5–8 h daily” = 4 | ||
| “Over 8 h per day” = 5 | ||
| Characteristic Variables | Variables | Choices | Number | Percentage (%) |
|---|---|---|---|---|
| Demographic characteristics | Gender | Male | 439 | 25.3 |
| Female | 1295 | 74.7 | ||
| Age | Under 20 | 214 | 12.3 | |
| 20–30 | 406 | 23.4 | ||
| 30–40 | 802 | 46.3 | ||
| 40–50 | 265 | 15.3 | ||
| Over 50 | 47 | 2.7 | ||
| Level of education | High school and under | 961 | 55.4 | |
| Undergraduate and tertiary | 631 | 36.4 | ||
| Master’s student | 99 | 5.7 | ||
| Doctor’s student | 43 | 2.5 | ||
| Mobile social media usage characteristics | Intensity of WeChat usage | Under one hour per day | 193 | 11.1 |
| 1–3 h daily | 556 | 32.1 | ||
| 3–5 h daily | 549 | 31.6 | ||
| 5–8 h daily | 218 | 12.6 | ||
| Over 8 h per day | 218 | 12.6 | ||
| Number of friends on WeChat | Under 100 | 651 | 37.5 | |
| 100–300 | 675 | 38.9 | ||
| 300–600 | 258 | 14.9 | ||
| 600–1000 | 81 | 4.7 | ||
| Over 1000 | 69 | 4.0 |
| Variable | Coef. | Std. Err. | Z |
|---|---|---|---|
| pro | 0.049 ** | 0.023 | 2.13 |
| sex | −0.246 * | 0.138 | −1.78 |
| age | −0.271 *** | 0.064 | −4.24 |
| edu | 0.179 * | 0.093 | 1.93 |
| freq | −0.014 | 0.056 | −0.26 |
| friends | −0.172 ** | 0.073 | −2.35 |
| _cons | −1.038 ** | 0.520 | −1.99 |
| Variable | Sample | Mean | %Bias | %Reduct Bias | t | |
|---|---|---|---|---|---|---|
| Experience Group | Control Group | |||||
| pro | Unmatched | 17.438 | 17.083 | 11.9 | 98.7 | 1.89 * |
| Matched | 17.380 | 17.375 | 0.2 | 0.02 | ||
| sex | Unmatched | 1.694 | 1.760 | −14.9 | 50.9 | −2.51 ** |
| Matched | 1.696 | 1.728 | −7.3 | −0.92 | ||
| age | Unmatched | 2.515 | 2.777 | −26.5 | 97.4 | −4.53 *** |
| Matched | 2.521 | 2.514 | 0.7 | 0.08 | ||
| edu | Unmatched | 1.566 | 1.549 | 2.1 | −368.4 | 0.37 |
| Matched | 1.539 | 1.464 | 10 | 1.32 | ||
| freq | Unmatched | 2.753 | 2.853 | −8.4 | 27.2 | −1.41 |
| Matched | 2.753 | 2.680 | 6.1 | 0.76 | ||
| friends | Unmatched | 1.857 | 2.017 | −15.3 | 31.5 | −2.55 ** |
| Matched | 1.855 | 1.746 | 10.5 | 1.39 | ||
| Variable | (1) | (2) | (3) |
|---|---|---|---|
| pc1 | 0.066 *** | ||
| (−0.021) | |||
| pc1 × D | −0.110 *** | ||
| (−0.017) | |||
| pro | −0.001 | −0.001 | −0.001 |
| (−0.009) | (−0.009) | (−0.009) | |
| sex | −0.094 | −0.097 | −0.103 |
| (−0.064) | (−0.064) | (−0.064) | |
| age | 0.015 | 0.012 | 0.014 |
| (−0.028) | (−0.028) | (−0.027) | |
| edu | 0.057 | 0.037 | 0.049 |
| (−0.041) | (−0.041) | (−0.041) | |
| freq | −0.041 * | −0.040 * | −0.041 * |
| (−0.024) | (−0.024) | (−0.024) | |
| friends | −0.018 | −0.020 | −0.020 |
| (−0.029) | (−0.029) | (−0.029) | |
| pc2 | 0.099 *** | ||
| (−0.021) | |||
| pc2 × D | −0.108 *** | ||
| (−0.018) | |||
| pc3 | 0.102 *** | ||
| (−0.023) | |||
| pc3 × D | −0.117 *** | ||
| (−0.017) | |||
| Constant | 2.364 *** | 2.294 *** | 2.273 *** |
| (−0.231) | (−0.230) | (−0.232) | |
| Observations | 905 | 905 | 905 |
| R-squared | 0.058 | 0.065 | 0.070 |
| Variable | (1) | (2) | (3) |
|---|---|---|---|
| pc1 | 0.091 *** | ||
| (−0.019) | |||
| pc1 × D | −0.079 *** | ||
| (−0.013) | |||
| pro | −0.104 * | −0.098 * | −0.107 * |
| (−0.055) | (−0.055) | (−0.055) | |
| sex | 0.014 | 0.008 | 0.011 |
| (−0.025) | (−0.025) | (−0.025) | |
| age | 0.012 | −0.003 | 0.009 |
| (−0.036) | (−0.037) | (−0.036) | |
| edu | −0.020 | −0.023 | −0.022 |
| (−0.021) | (−0.021) | (−0.021) | |
| freq | −0.021 | −0.023 | −0.022 |
| (−0.025) | (−0.025) | (−0.025) | |
| friends | 0.002 | 0.003 | 0.002 |
| (−0.007) | (−0.007) | (−0.007) | |
| pc2 | 0.113 *** | ||
| (−0.019) | |||
| pc2 × D | −0.077 *** | ||
| (−0.014) | |||
| pc3 | 0.112 *** | ||
| (−0.021) | |||
| pc3 × D | −0.074 *** | ||
| (−0.014) | |||
| Constant | 2.327 *** | 2.267 *** | 2.263 *** |
| (−0.197) | (−0.196) | (−0.199) | |
| Observations | 1181 | 1181 | 1181 |
| R-squared | 0.042 | 0.048 | 0.043 |
| Variable | (1) | (2) | (3) | (4) |
|---|---|---|---|---|
| pc1 | 0.064 *** | 0.058 *** | 0.081 *** | 0.067 *** |
| (−0.018) | (−0.016) | (−0.020) | (−0.021) | |
| pc1 × D | −0.141 *** | −0.128 *** | −0.092 *** | −0.081 *** |
| (−0.017) | (−0.015) | (−0.014) | (−0.029) | |
| pro | −0.004 | 0.005 | 0.008 | 0.004 |
| (−0.013) | (−0.007) | (−0.008) | (−0.023) | |
| sex | −0.041 | −0.092 * | −0.122 ** | −0.072 |
| (−0.062) | (−0.049) | (−0.057) | (−0.068) | |
| age | 0.010 | 0.017 | −0.004 | 0.026 |
| (−0.027) | (−0.022) | (−0.026) | (−0.031) | |
| edu | 0.018 | 0.012 | 0.017 | −0.057 |
| (−0.045) | (−0.033) | (−0.038) | (−0.061) | |
| freq | −0.026 | −0.026 | −0.017 | −0.021 |
| (−0.024) | (−0.019) | (−0.022) | (−0.027) | |
| friends | 0.014 | −0.002 | −0.025 | 0.025 |
| (−0.032) | (−0.023) | (−0.026) | (−0.040) | |
| Constant | 2.377 *** | 2.307 *** | 2.335 *** | 2.256 *** |
| (−0.272) | (−0.175) | (−0.202) | (−0.447) | |
| Observations | 1249 | 1734 | 1123 | 1077 |
| R-squared | 0.060 | 0.047 | 0.050 | 0.022 |
| Variable | Sex | Age | Level of Education | |||
|---|---|---|---|---|---|---|
| Male | Female | Under 30 | Over 30 | Lower Education Levels | Higher Education Levels | |
| pc1 | 0.074 * | 0.063 *** | 0.085 ** | 0.060 *** | 0.081 *** | 0.034 |
| (−0.041) | (−0.021) | (−0.037) | (−0.021) | (−0.023) | (−0.032) | |
| pc1 × cy | −0.181 *** | −0.132 *** | −0.179 *** | −0.122 *** | −0.204 *** | −0.066 *** |
| (−0.041) | (−0.019) | (−0.030) | (−0.021) | (−0.023) | (−0.025) | |
| age | −0.010 | 0.019 | −0.050 | −0.024 | −0.049 | −0.018 |
| (−0.051) | (−0.033) | (−0.108) | (−0.076) | (−0.070) | (−0.135) | |
| edu | 0.034 | 0.014 | 0.143 * | −0.048 | 0.014 | −0.003 |
| (−0.110) | (−0.049) | (−0.075) | (−0.059) | (−0.033) | (−0.051) | |
| freq | 0.026 | −0.038 | −0.085 * | 0.002 | −0.037 | −0.014 |
| (−0.061) | (−0.025) | (−0.044) | (−0.028) | (−0.029) | (−0.041) | |
| friends | 0.035 | 0.007 | −0.019 | 0.025 | 0.046 | −0.016 |
| (−0.086) | (−0.035) | (−0.066) | (−0.036) | (−0.043) | (−0.048) | |
| pro | 0.014 | −0.010 | 0.009 | −0.027 | −0.009 | 0.000 |
| (−0.026) | (−0.015) | (−0.016) | (−0.024) | (−0.030) | (−0.015) | |
| Constant | 1.891 *** | 2.427 *** | 2.160 *** | 2.785 *** | 2.455 *** | 2.393 *** |
| (−0.544) | (−0.314) | (−0.365) | (−0.467) | (−0.563) | (−0.414) | |
| Observations | 284 | 965 | 370 | 879 | 797 | 452 |
| R-squared | 0.075 | 0.059 | 0.112 | 0.045 | 0.103 | 0.018 |
| Variable | Intensity of WeChat Usage | Number of Friends on WeChat | ||
|---|---|---|---|---|
| Under 3 h Daily | Over 3 h Daily | Under 100 | Over 100 | |
| pc1 | 0.105 *** | 0.041 | 0.066 ** | 0.061 ** |
| (−0.027) | (−0.026) | (−0.028) | (−0.025) | |
| pc1 × cy | −0.155 *** | −0.126 *** | −0.158 *** | −0.125 *** |
| (−0.024) | (−0.024) | (−0.026) | (−0.023) | |
| age | 0.004 | −0.137 | −0.028 | −0.057 |
| (−0.080) | (−0.095) | (−0.084) | (−0.092) | |
| edu | −0.049 | 0.094 ** | 0.021 | −0.005 |
| (−0.034) | (−0.045) | (−0.036) | (−0.045) | |
| freq | −0.037 | 0.045 | −0.027 | 0.004 |
| (−0.075) | (−0.057) | (−0.102) | (−0.050) | |
| friends | 0.034 | −0.019 | −0.043 | −0.024 |
| (−0.060) | (−0.038) | (−0.036) | (−0.030) | |
| pro | 0.020 | −0.010 | 0.041 | −0.005 |
| (−0.029) | (−0.015) | (−0.049) | (−0.014) | |
| Constant | 1.845 *** | 2.459 *** | 1.598 * | 2.529 *** |
| (−0.558) | (−0.338) | (−0.895) | (−0.327) | |
| Observations | 581 | 668 | 555 | 694 |
| R-squared | 0.089 | 0.052 | 0.077 | 0.049 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tian, X.; Chen, L.; Zhang, X. The Role of Privacy Fatigue in Privacy Paradox: A PSM and Heterogeneity Analysis. Appl. Sci. 2022, 12, 9702. https://doi.org/10.3390/app12199702
Tian X, Chen L, Zhang X. The Role of Privacy Fatigue in Privacy Paradox: A PSM and Heterogeneity Analysis. Applied Sciences. 2022; 12(19):9702. https://doi.org/10.3390/app12199702
Chicago/Turabian StyleTian, Xinluan, Lina Chen, and Xiaojuan Zhang. 2022. "The Role of Privacy Fatigue in Privacy Paradox: A PSM and Heterogeneity Analysis" Applied Sciences 12, no. 19: 9702. https://doi.org/10.3390/app12199702
APA StyleTian, X., Chen, L., & Zhang, X. (2022). The Role of Privacy Fatigue in Privacy Paradox: A PSM and Heterogeneity Analysis. Applied Sciences, 12(19), 9702. https://doi.org/10.3390/app12199702







