Peer-to-Peer System Design Trade-Offs: A Framework Exploring the Balance between Blockchain and IPFS
Abstract
1. Introduction
2. Decentralization Technologies
- Content Addressability:
- In centralized and federated systems, content is frequently referenced with addresses that include location information: Uniform Resource Locators (URLs) [39]. However, references to content can also be independent from their location, using Universal Resource Identifiers (URIs) [40]. In peer-to-peer systems, agents cannot rely on the location of other agents to access content because the content could be provided by any agent. The hash of any content can be used as its URI (hash functions are one-way collision-free functions; i.e., functions that result in a negligible probability of guessing which input produced an output). Thus, these hash URIs are used in multiple distributed systems such as IPFS to build scalable content-addressable networks [32,41,42,43].
- Merkle Links and Structures:
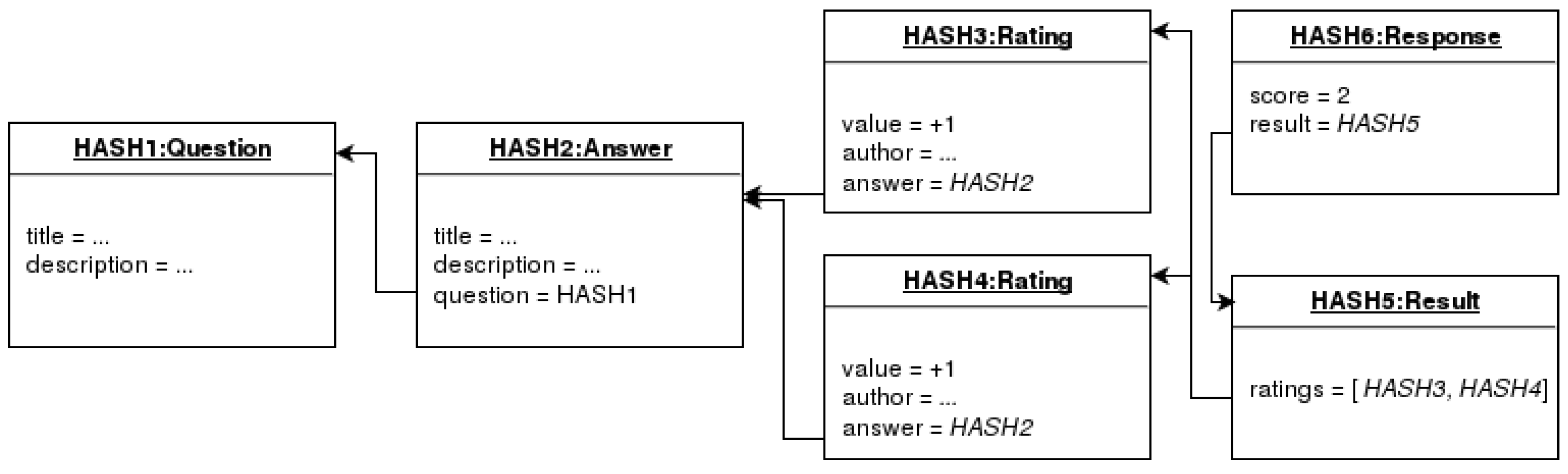
- The use of hash values (see previous subsection) to reference data in data structures was first introduced in 1987 by Merkle [30]. Complex data structures can use these links (See Figure 1 for an example). Merkle-linked structures are key to the building of technologies such as Git [44], Blockchain [31], and IPFS [32], among others. Section 6.2 proposes the use of these structures for the data representation of the system.
- Blockchain:
- Blockchain was the first technology that enabled a fully distributed digital currency (Bitcoin) [31], solving the double-spending problem in distributed systems (see Figure 2). It uses a Merkle-linked list of blocks of transactions (a Blockchain) to build a distributed ledger of transactions. To address the double-spending problem, it made it computationally difficult to propose a candidate for the next block in the distributed ledger and incentivized nodes to try to propose those blocks with valid transactions. Then, the protocol considers the largest observed chain the actual ledger to trust. Therefore, in order to forge a Blockchain, an actor would need half of the computing power of the system, bringing security to the consistency of the data recorded in the ledger. Section 4.4 proposes the use of the Blockchain to provide consistency to open distributed systems.
- IPFS:
- Some peer-to-peer systems such as P2P sharing software [41] use a hash of the content to address it (See Figure 3). Other technologies such as Git use complex Merkle-linked structures [44]. IPFS integrates both the use of complex Merkle-linked structures with the data-addressability of P2P file-sharing systems. The content is distributed over a peer-to-peer network. Section 6.1 proposes the use of IPFS for the storage and distribution of data in the framework.
3. The Open Distributed Systems Considered
3.1. Shared State and Agreed Rules
- Agreed rules: A consensus on the rules of the system across the network. Thus, the participants on the network agree on how the shared state can change and who can change it. Cryptographic identities are used to ensure that the people who are performing the operations are allowed to do so. For instance, they may agree that only the owner of a cryptocurrency account can send money from that account.
- Trusted state: This is achieved using a tamper-proof, cryptographically-linked data structure named the Blockchain. Thus, every agent can access the complete history of transactions (the chain of blocks) and verify that the rules have been respected (e.g., that no one has sent more money than they initially had).
- Incentivized consistency: This ensures the maintenance required for the consistency of the shared state is performed appropriately. This is achieved by rewarding the “miners” for their maintenance work, typically through a Proof of Work or Proof of Stake algorithm.
- The hard requirement of a single data structure (such as the blockchain) to maintain all the information is not suitable for multiple distributed systems. Thus, this paper proposes that other distributed architectures such as an IPFS network may store and distribute such information.
- Similarly, maintaining consistency through an elaborate incentive system (such as the famous Proof of Work algorithm) is not a must for multiple distributed systems. Thus, the proposed design guidelines help users to assess whether a Blockchain is needed or if other consistency strategies may be followed (namely, consistency as logical monotonicity, or CRDTs).
3.2. Openness
3.3. Peer-to-Peer Full Distribution
4. Design Trade-Offs of Distributed Open Systems
4.1. CAP Theorem
- Consistency: The requests of the distributed system should behave as if they were handled by a single node with updated information.
- Availability: Every request should be responded to.
- Partition resistance: The system should be able to operate in the presence of network partitions.
4.2. CALM Principle
- Order independence:
- This is a needed condition for logical monotonicity [52]; i.e., if the system behavior depends on the order in which the information is received, then it is non-monotonic. For instance, in the double-spending problem, where an agent tries to spend “the same coin” twice, the state depends on which payment was made first. Therefore, it is a non-monotonic problem.
- Monotonicity:
- By definition, if new information may revoke a previously valid response to a query, the query is non-monotonic. For instance, counting the number of positive votes for an answer in a Q&A system is non-monotonic, since new votes would change the response.
- Formal analysis:
- This can prove the logical monotonicity of a system [52].
4.3. Eventual Consistency
4.4. Blockchain for Distributed Consistency
5. Applying the Guidelines to Well-Known Decentralized Systems
5.1. PGP Keyservers
5.2. Git
6. Designing a Distributed Questions and Answers System
6.1. Accessing Data
6.2. Data Provenance
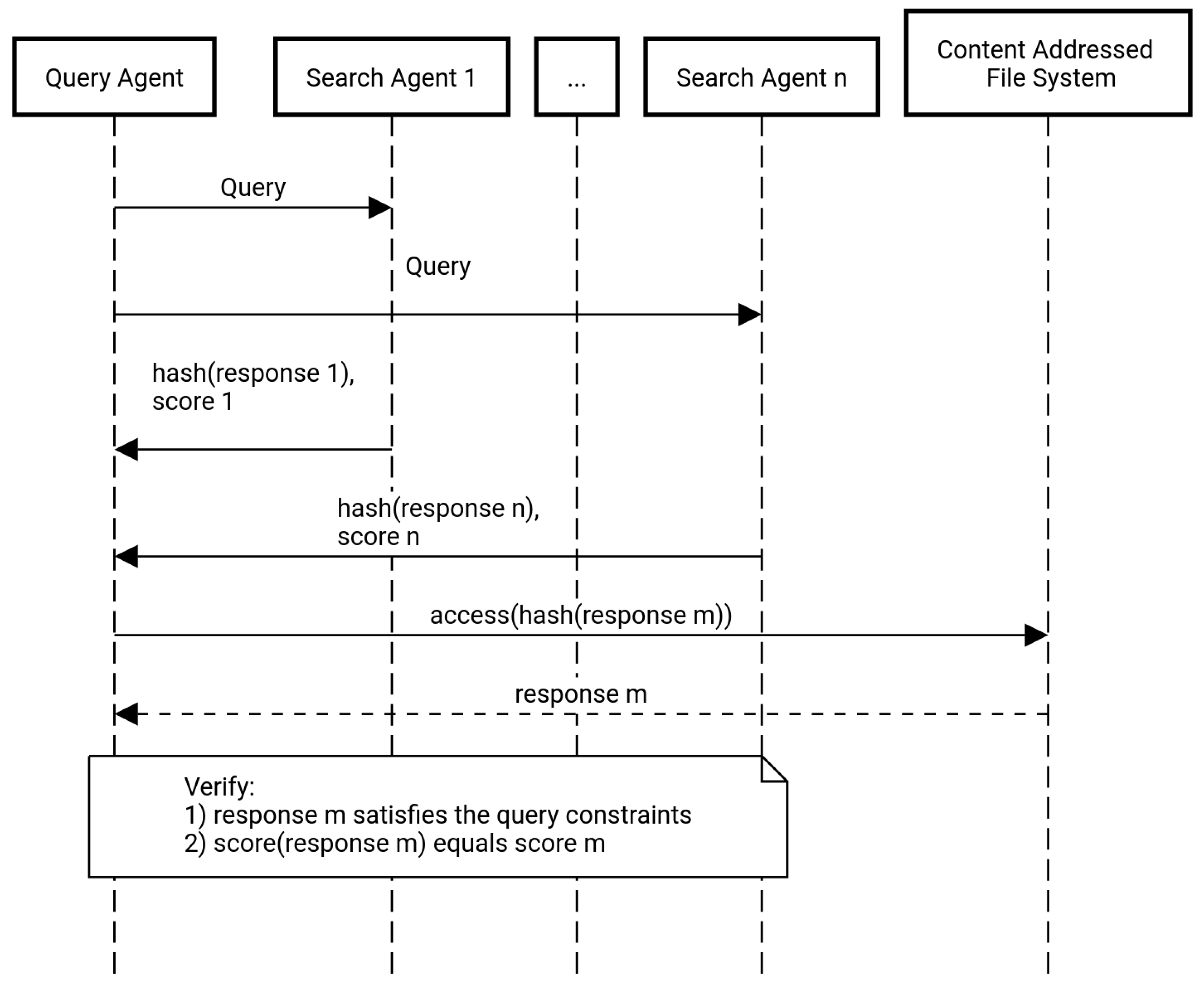
6.3. Data Discovery Using a Trustless Distributed Protocol
- An agent sends a query (with constraints and a score function).
- Any agent can reply, with a response consisting of a content-centric link to the data satisfying the query and its corresponding score.
- The querying agent accesses the data and verifies the responses and scores.
- Lightweight communication: Responses consist of a short link and a numeric value. Their length is then a few bytes long, even though they may represent complex, large data structures.
- Early distributed ranking: Responses may be ranked without accessing their data.
- Trustless ranking and validity: Similarly to how any node can verify that all the transactions in a Blockchain are valid without needing to trust a third party, the validity and ranking of the responses in the proposed protocol can be assessed without trusting the agents providing the responses or the data (e.g., checking the digital signatures for authorship and the validity of the linked votes).
7. Discussion and Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| CALM | Consistency as Logical Monotonicity |
| CAP | Consistency, Availability, Partition resistance |
| CDN | Content Delivery Network |
| CRDT | Conflict-Free Replicated Data Types |
| IPFS | Inter-Planetary File System |
| IPNS | Peer-to-peer |
| MAS | Multi-Agent System |
| OAuth | Originally “Open Authorization”, open standard for access delegation |
| OStatus | Originally “Open Status”, open standard for federated microblogging |
| P2P | Peer-to-peer |
| PGP | Pretty Good Privacy |
| Q&A | Questions and answers |
| URI | Universal Resource Identifier |
| URL | Uniform Resource Allocator |
| XMPP | Extensible Messaging and Presence Protocol (originally, Jabber) |
References
- De Filippi, P.; McCarthy, S. Cloud Computing: Centralization and Data Sovereignty. Eur. J. Law Technol. 2012, 3. Available online: https://ssrn.com/abstract=2167372 (accessed on 25 October 2021).
- Tim, O. What Is Web 2.0? Design Patterns and Business Models for the Next Generation of Software. 2005. Available online: https://mpra.ub.uni-muenchen.de/4580/ (accessed on 25 October 2021).
- Dolata, U. Apple, Amazon, Google, Facebook, Microsoft: Market Concentration-Competition-Innovation Strategies; Technical Report, Stuttgarter Beiträge zur Organisations-und Innovationsforschung, SOI Discussion Paper; 2017; Available online: https://ideas.repec.org/p/zbw/stusoi/201701.html (accessed on 25 October 2021).
- Haucap, J.; Heimeshoff, U. Google, Facebook, Amazon, eBay: Is the Internet driving competition or market monopolization? Int. Econ. Econ. Policy 2014, 11, 49–61. [Google Scholar] [CrossRef]
- Rubinstein, I.; Van Hoboken, J. Privacy and Security in the Cloud: Some Realism about Technical Solutions to Transnational Surveillance in the Post-Snowden era. 2014. Available online: https://papers.ssrn.com/sol3/papers.cfm?abstract_id=2443604 (accessed on 3 March 2021).
- Fuster Morell, M. Governance of Online Creation Communities: Provision of Infrastructure for the Building of Digital Commons. Ph.D. Thesis, European University Institute, Fiesole, Italy, 2010. [Google Scholar]
- Lyon, D. Surveillance, Snowden, and big data: Capacities, consequences, critique. Big Data Soc. 2014, 1. [Google Scholar] [CrossRef]
- Kandukuri, B.R.; Rakshit, A. Cloud security issues. In Proceedings of the SCC’09 IEEE International Conference on Services Computing, Bangalore, India, 21–25 September 2009; pp. 517–520. [Google Scholar]
- Brown, I.; Marsden, C.T. Regulating Code: Good Governance and Better Regulation in the Information Age; MIT Press: Cambridge, MA, USA, 2013. [Google Scholar]
- Voss, W.G. European union data privacy law reform: General data protection regulation, privacy shield, and the right to delisting. Bus. Lawyer 2017, 72, 221–234. [Google Scholar]
- Hill, B.M. Franklin Street statement on freedom and network services. Autonomo. us 2008. Available online: https://web.archive.org/web/20150203102659/http://autonomo.us/2008/07/14/franklin-street-statement/ (accessed on 1 February 2021).
- Cabello, F.; Franco, M.G.; Haché, A. The Social Web beyond’Walled Gardens’: Interoperability, Federation and the Case of Lorea/n-1. PsychNology J. 2013, 11, 43–65. [Google Scholar]
- Alsaleh, M.; Adams, C. Enhancing consumer privacy in the liberty alliance identity federation and web services frameworks. In International Workshop on Privacy Enhancing Technologies; Springer: Berlin/Heidelberg, Germany, 2006; pp. 59–77. [Google Scholar]
- Tapiador, A.; Hassan, S. Understanding Federation: An Analytical Framework for the Interoperability of Social Networking Sites. arXiv 2018, arXiv:1805.06474. [Google Scholar]
- Saint-Andre, P. Extensible Messaging and Presence Protocol (XMPP): Address Format; Technical Report; 2015; Available online: https://xmpp.org/rfcs/rfc6122.html (accessed on 25 October 2021).
- W3C. The Basics—OStatus Community Group. 2012. Available online: http://www.w3.org/community/ostatus/wiki/The_Basics (accessed on 25 October 2021).
- Webber Lemmer, C.; Tallon, J.; Shepherd, E.; Guy, A.; Prodromou, E. ActivityPub. 2018. Available online: https://www.w3.org/TR/activitypub/ (accessed on 1 January 2020).
- Hammer-Lahav, E. The OAuth 1.0 Protocol, Internet Engineering Task Force (IETF). 2010. Available online: https://datatracker.ietf.org/doc/html/rfc6749 (accessed on 25 October 2021).
- Ojanguren-Menendez, P.; Tenorio-Fornés, A.; Hassan, S. Building Real-Time Collaborative Applications with a Federated Architecture. Int. J. Interact. Multimed. Artif. Intell. 2015, 3, 47–52. [Google Scholar] [CrossRef]
- Yeung, C.M.A.; Liccardi, I.; Lu, K.; Seneviratne, O.; Berners-Lee, T. Decentralization: The future of online social networking. In W3C Workshop on the Future of Social Networking Position Papers; 2009; Volume 2, pp. 2–7. Available online: https://www.w3.org/2008/09/msnws/papers/decentralization.pdf (accessed on 2 February 2020).
- Sambra, A.V.; Mansour, E.; Hawke, S.; Zereba, M.; Greco, N.; Ghanem, A.; Zagidulin, D.; Aboulnaga, A.; Berners-Lee, T. Solid: A Platform for Decentralized Social Applications Based on Linked Data; Technical Report; MIT CSAIL & Qatar Computing Research Institute: Cambridge, MA, USA, 2016. [Google Scholar]
- Rajabi, E.; Sanchez-Alonso, S.; Sicilia, M.A. Analyzing broken links on the web of data: An experiment with DBpedia. J. Assoc. Inf. Sci. Technol. 2014, 65, 1721–1727. [Google Scholar] [CrossRef]
- Levison, L. Secrets, lies and Snowden’s email: Why I was forced to shut down Lavabit. Guardian 2014. Available online: https://www.theguardian.com/commentisfree/2014/may/20/why-did-lavabit-shut-down-snowden-email (accessed on 25 October 2021).
- Pouwelse, J.A.; Garbacki, P.; Wang, J.; Bakker, A.; Yang, J.; Iosup, A.; Epema, D.H.; Reinders, M.; Van Steen, M.R.; Sips, H.J. TRIBLER: A social-based peer-to-peer system. Concurr. Comput. Pract. Exp. 2008, 20, 127–138. [Google Scholar] [CrossRef]
- Kermarrec, A.M. Towards a personalized Internet: A case for a full decentralization. Philos. Trans. R. Soc. Lond. A Math. Phys. Eng. Sci. 2013, 371, 20120380. [Google Scholar] [CrossRef][Green Version]
- Clarke, I.; Sandberg, O.; Wiley, B.; Hong, T.W. Freenet: A distributed anonymous information storage and retrieval system. In Designing Privacy Enhancing Technologies; Springer: Berlin/Heidelberg, Germany, 2001; pp. 46–66. [Google Scholar]
- Cohen, B. The BitTorrent Protocol Specification. 2008. Available online: http://cs.ecs.baylor.edu/~donahoo/classes/5321/projects/bittorrent/BitTorrent%20Protocol%20Specification.doc (accessed on 25 October 2021).
- Lamport, L.; Shostak, R.; Pease, M. The Byzantine generals problem. ACM Trans. Program. Lang. Syst. (TOPLAS) 1982, 4, 382–401. [Google Scholar] [CrossRef]
- Wachs, M.; Schanzenbach, M.; Grothoff, C. On the feasibility of a censorship resistant decentralized name system. In Foundations and Practice of Security; Springer: Cham, Switzerland, 2014; pp. 19–30. [Google Scholar]
- Merkle, R.C. A digital signature based on a conventional encryption function. In Conference on the Theory and Application of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 1987; pp. 369–378. [Google Scholar]
- Nakamoto, S. Bitcoin: A peer-to-peer electronic cash system. Decentralized Bus. Rev. 2008, 21260. Available online: https://www.debr.io/article/21260.pdf (accessed on 25 October 2021).
- Benet, J. IPFS-content addressed, versioned, P2P file system. arXiv 2014, arXiv:1407.3561. [Google Scholar]
- Caldarelli, G.; Ellul, J. Trusted Academic Transcripts on the Blockchain: A Systematic Literature Review. Appl. Sci. 2021, 11, 1842. [Google Scholar] [CrossRef]
- Benshoof, B.; Rosen, A.; Bourgeois, A.G.; Harrison, R.W. Distributed Decentralized Domain Name Service. In Proceedings of the 2016 IEEE International Parallel and Distributed Processing Symposium Workshops, Chicago, IL, USA, 23–27 May 2016; pp. 1279–1287. [Google Scholar]
- El Faqir, Y.; Arroyo, J.; Hassan, S. An Overview of Decentralized Autonomous Organizations on the Blockchain. In Proceedings of the 16th International Symposium on Open Collaboration, OpenSym 2020, Madrid, Spain, 26–27 August 2020; Association for Computing Machinery: New York, NY, USA, 2020. [Google Scholar] [CrossRef]
- Rozas, D.; Tenorio-Fornés, A.; Díaz-Molina, S.; Hassan, S. When Ostrom Meets Blockchain: Exploring the Potentials of Blockchain for Commons Governance. SAGE Open 2021, 11, 21582440211002526. [Google Scholar] [CrossRef]
- Hassan, S.; Brekke, J.K.; Atzori, M.; Bodó, B.; Meiklejohn, S.; De Filippi, P.; Beecroft, K. Scanning the European Ecosystem of Distributed Ledger Technologies for Social and Public Good: What, Why, Where, How, and Ways to Move Forward; Publications Office of the European Union: Luxembourg, 2020. [Google Scholar]
- Shapiro, M.; Preguiça, N.; Baquero, C.; Zawirski, M. Conflict-free replicated data types. In Symposium on Self-Stabilizing Systems; Springer: Berlin/Heidelberg, Germany, 2011; pp. 386–400. [Google Scholar]
- Berners-Lee, T.; Masinter, L.; McCahill, M. Uniform Resource Locators (URL); Technical Report; 1994; Available online: https://www.hjp.at/doc/rfc/rfc1738.html (accessed on 25 October 2021).
- Jacobs, I. URIs, Addressability, and the use of HTTP GET and POST. 2004. Available online: https://www.w3.org/2001/tag/doc/whenToUseGet.html (accessed on 25 October 2021).
- Ratnasamy, S.; Francis, P.; Handley, M.; Karp, R.; Shenker, S. A Scalable Content-Addressable Network; ACM: New York, NY, USA, 2001; Volume 31. [Google Scholar]
- Morris, R.; Kaashoek, M.F.; Karger, D.; Balakrishnan, H.; Stoica, I.; Liben-Nowell, D.; Dabek, F. Chord: A scalable peer-to-peer look-up protocol for internet applications. IEEE/ACM Trans. Netw. 2003, 11, 17–32. [Google Scholar]
- Janak, J.; Lee, J.W.; Schulzrinne, H. GRAND: Git Revisions as Named Data; Department of Computer Science, Columbia University: New York, NY, USA, 2011. [Google Scholar]
- Loeliger, J.; McCullough, M. Version Control with Git: Powerful Tools and Techniques for Collaborative Software Development; O’Reilly Media, Inc.: Sevastopol, CA, USA, 2012. [Google Scholar]
- Zimmermann, H. OSI reference model–The ISO model of architecture for open systems interconnection. IEEE Trans. Commun. 1980, 28, 425–432. [Google Scholar] [CrossRef]
- Demazeau, Y.; Costa, A.R. Populations and publishers in open multi-agent systems. In Proceedings of the 1st National Symposium on Parallel and Distributed AI, Hyderabad, India, 23–26 October 1996; pp. 1–13. [Google Scholar]
- Hewitt, C.; De Jong, P. Open systems. In On Conceptual Modelling; Springer: New York, NY, USA, 1984; pp. 147–164. [Google Scholar]
- Groen, F.C.; Spaan, M.T.; Kok, J.R.; Pavlin, G. Real world multi-agent systems: Information sharing, coordination and planning. In International Tbilisi Symposium on Logic, Language, and Computation; Springer: Berlin/Heidelberg, Germany, 2005; pp. 154–165. [Google Scholar]
- Simon, H.A. Cognitive science: The newest science of the artificial. Cogn. Sci. 1980, 4, 33–46. [Google Scholar] [CrossRef]
- Berners-Lee, T. Long live the web. Sci. Am. 2010, 303, 80–85. [Google Scholar] [CrossRef]
- Brewer, E. CAP twelve years later: How the “rules” have changed. Computer 2012, 45, 23–29. [Google Scholar] [CrossRef]
- Alvaro, P.; Conway, N.; Hellerstein, J.M.; Marczak, W.R. Consistency Analysis in Bloom: A CALM and Collected Approach. In Proceedings of the CIDR 2011—5th Biennial Conference on Innovative Data Systems Research, Conference Proceedings, Asilomar, CA, USA, 9–12 January 2011; pp. 249–260. [Google Scholar]
- Zimmermann, P.R. The Official PGP User’s Guide; MIT Press: Cambridge, MA, USA, 1995. [Google Scholar]
- Yakubov, A.; Shbair, W.; State, R. BlockPGP: A Blockchain-Based Framework for PGP Key Servers. In Proceedings of the 2018 Sixth International Symposium on Computing and Networking Workshops (CANDARW), Takayama, Japan, 27–30 November 2018; pp. 316–322. [Google Scholar] [CrossRef]
- Nizamuddin, N.; Salah, K.; Ajmal Azad, M.; Arshad, J.; Rehman, M. Decentralized document version control using ethereum blockchain and IPFS. Comput. Electr. Eng. 2019, 76, 183–197. [Google Scholar] [CrossRef]
- Stack Overflow. Available online: https://stackoverflow.com (accessed on 1 May 2021).
- Buterin, V. Ethereum: A Next-Generation Smart Contract and Decentralized Application Platform. 2014. Available online: https://github.com/ethereum/wiki/wiki/White-Paper (accessed on 25 October 2021).
- Jun, K.; Boloni, L.; Palacz, K.; Marinescu, D.C. Agent-based resource discovery. In Proceedings of the 9th Heterogeneous Computing Workshop (HCW 2000) (Cat. No.PR00556), Cancun, Mexico, 1 May 2000; pp. 43–52. [Google Scholar]
- Greschbach, B.; Kreitz, G.; Buchegger, S. The devil is in the metadata—New privacy challenges in Decentralised Online Social Networks. In Proceedings of the 2012 IEEE International Conference on Pervasive Computing and Communications Workshops, Lugano, Switzerland, 19–23 March 2012; pp. 333–339. [Google Scholar] [CrossRef]
- De Filippi, P. The interplay between decentralization and privacy: The case of blockchain technologies. J. Peer Prod. 2016, 9. Available online: http://peerproduction.net/issues/issue-9-alternative-internets/peer-reviewed-papers/the-interplay-between-decentralization-and-privacy-the-case-of-blockchain-technologies/ (accessed on 25 October 2021).
- Cohen, B. Incentives build robustness in BitTorrent. In Workshop on Economics of Peer-to-Peer Systems; University of California: Berkeley, CA, USA, 2003; Volume 6, pp. 68–72. [Google Scholar]
- Zhou, Q.; Huang, H.; Zheng, Z.; Bian, J. Solutions to Scalability of Blockchain: A Survey. IEEE Access 2020, 8, 16440–16455. [Google Scholar] [CrossRef]
- Labs, P. Filecoin: A Decentralized Storage Network. 2017. Available online: https://filecoin.io/filecoin.pdf (accessed on 25 October 2021).


| Weak Consistency | Eventual Consistency | Strong Consistency | |
|---|---|---|---|
| Weakavailability | No need for coordination technologies (Guideline 2) | Logical Monotonicity or Blockchain (Guidelines 1, 4) | |
| Strong availability | CRDTs (Guideline 3) | Not possible, considering CAP Theorem |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tenorio-Fornés, Á.; Hassan, S.; Pavón, J. Peer-to-Peer System Design Trade-Offs: A Framework Exploring the Balance between Blockchain and IPFS. Appl. Sci. 2021, 11, 10012. https://doi.org/10.3390/app112110012
Tenorio-Fornés Á, Hassan S, Pavón J. Peer-to-Peer System Design Trade-Offs: A Framework Exploring the Balance between Blockchain and IPFS. Applied Sciences. 2021; 11(21):10012. https://doi.org/10.3390/app112110012
Chicago/Turabian StyleTenorio-Fornés, Ámbar, Samer Hassan, and Juan Pavón. 2021. "Peer-to-Peer System Design Trade-Offs: A Framework Exploring the Balance between Blockchain and IPFS" Applied Sciences 11, no. 21: 10012. https://doi.org/10.3390/app112110012
APA StyleTenorio-Fornés, Á., Hassan, S., & Pavón, J. (2021). Peer-to-Peer System Design Trade-Offs: A Framework Exploring the Balance between Blockchain and IPFS. Applied Sciences, 11(21), 10012. https://doi.org/10.3390/app112110012






