Abstract
Reversible data hiding has attracted significant attention from researchers because it can extract an embedded secret message correctly and recover a cover image without distortion. In this paper, a novel, efficient reversible data hiding scheme is proposed for absolute moment block truncation code (AMBTC) compressed images. The proposed scheme is based on the high correlation of neighboring values in two mean tables of AMBTC-compressed images to further losslessly encode these values and create free space for containing a secret message. Experimental results demonstrated that the proposed scheme obtained a high embedding capacity and guaranteed the same PSNRs as the traditional AMBTC algorithm. In addition, the proposed scheme achieved a higher embedding capacity and higher efficiency rate than those of some previous schemes while maintaining an acceptable bit rate.
1. Introduction
Data hiding is an important technique by which a secret message is protected by being embedded into a cover image. Data hiding can be classified into two types of schemes, i.e., irreversible and reversible. One essential property of irreversible data hiding schemes is high embedding capacity [1,2]. However, they distort the cover image significantly. Moreover, this visual quality cannot be reconstructed after secret message extraction. Therefore, this type cannot be used in some special applications, i.e., military and medicine, in which a cover image is required to be restored to its original version. To solve this problem, reversible data hiding schemes [3,4,5,6,7] are a promising solution for these applications because the schemes can recover the original version of cover images without any distortion after the secret message was extracted.
Recently, many data hiding schemes for compressed images have been proposed to save the bandwidth space of the embedding image. This is because the size of the compressed image is much smaller than that of the original image, regardless of whether the secret message has been embedded. Some compression techniques, i.e., JPEG [8,9], vector quantization (VQ) [10,11,12], and block truncation coding (BTC) [13,14,15,16,17,18,19,20], are applied for data hiding to achieve high embedding capacity while maintaining a low bit rate.
In the literature, various data hiding schemes [13,14,15,16,17,18,19,20] have been proposed for BTC-compressed images. In 2004, Lin and Chang [13] introduced a data hiding scheme based on LSB replacement for BTC-compressed images. This scheme obtained a small distortion of a stego image. To improve the visual quality of the stego image, in 2006, Chuang and Chang [14] used smooth regions of the bitmap table in a BTC-compressed image to contain a secret message. However, this scheme is irreversible, meaning that the original BTC-compressed image cannot be recovered after the secret message was extracted. In 2008, Chang et al. [15] proposed a reversible data hiding scheme based on the order of mean values to embed a secret message into BTC-compressed images. Moreover, in 2008, Hong et al. [16] proposed a new reversible data hiding scheme for BTC-compressed images that toggled or preserved the BTC bitmap table to hide the secret bits. In addition, in Hong et al.’s scheme, the relationship between the high mean value and low mean value is used for embedding data. However, when two mean values are the same, the extracted bits will contain errors. To overcome the weakness in Hong et al.’s scheme, Chen et al. [17] proposed an improved reversible data hiding scheme for BTC-compressed images. In this scheme, the difference value of the high mean value and low mean value is calculated and used to determine whether only one secret bit is embedded into the block or more secret bits are embedded into the bitmap table of the block by toggling. In 2011, Li et al. [18] proposed a reversible data hiding scheme for BTC-compressed images by using bitmap flipping and histogram shifting for high mean values and low mean values. However, Li et al.’s scheme obtained low embedding capacity when, on average, only one secret bit is embedded into each image block. To further improve embedding capacity, in 2013, Sun et al. [19] proposed a new reversible data hiding scheme based on the joint neighbor coding algorithm (JNC) to embed a secret message into BTC-compressed images. This scheme can obtain a high embedding capacity, which is four times larger than that of Li et al.’ scheme [18]. However, the efficiency rate of this scheme is still low. Later, in 2017, Hong et al. adopted a median edge detection (MED) predictor to predict the quantization values of blocks first. Next, they further designed a centralization error division (CED) technique to modify the classification rule and ensure all zero prediction errors can be categorized into a new division and no more bits are required. With such an arrangement, Hong et al. successfully shrank the size of the original quantization values of blocks and saved more space to embed secret bits [20].
To improve the embedding capacity and efficiency rate further while maintaining the reconstruction of a cover image after extracting a secret message, in this paper, we propose a new, reversible data hiding scheme for an absolute moment block truncation coding (AMBTC) image, which is a variant of the BTC-compressed image. In the proposed scheme, the high correlation of values in two mean tables of an AMBTC-compressed image is explored to embed a secret message. Experimental results demonstrated that the proposed scheme obtained a high embedding capacity and the same PSNRs as the traditional AMBTC algorithm. In addition, the proposed scheme achieved a higher embedding capacity and higher efficiency rate than those of some previous schemes while maintaining an acceptable bit rate.
The remainder of the paper is organized as follows. Section 2 briefly reviews the original AMBTC compression algorithm and previous AMBTC-based data hiding scheme [4]. Section 3 describes details concerning the proposed scheme. Then, experimental results are analyzed and compared to previous schemes in Section 4. Our conclusions and discussion are provided in Section 5.
2. Related Work
AMBTC is a technique that is the variant of the traditional BTC algorithm. However, the AMBTC technique is computationally simpler than the BTC algorithm, while the performance of the AMBTC technique is the same as that of BTC. Therefore, in this paper, the AMBTC technique is used instead of BTC. To provide the background knowledge of our proposed scheme, in the following subsections, the AMBTC technique will be presented in Section 2.1. In addition, Sun et al.’s scheme [19] is introduced in detail in Section 2.2. The main reason is that this scheme obtained high performance when embedding data into the BTC-compressed image.
2.1. Absolute Moment Block Truncation Coding
To compress both grayscale and color images, in 1984, absolute moment block truncation coding (AMBTC) was proposed by Lema and Mitchell [21]. An image is first divided into n × n blocks. For example, to compress the image block X, the AMBTC algorithm computes mean value M to classify all pixels of block X into two different groups. If the value of pixels is smaller than M, these pixels belong to the first group. Otherwise, these pixels are considered members of the second group. Concurrently, the corresponding bit value, 0 or 1, is recorded in the bitmap, B, if the pixel belongs to the first group or second group, respectively.
After obtaining the two groups, two mean values, Hk and Lk, of the block X are calculated by Equations (1) and (2), respectively:
where Z denotes the number of pixels with the value larger than or equal to the value of M. If Z = n × n, set Hk = Lk = M.
After encoding by AMBTC, each block is represented by a compressed trio (Hk, Lk, B), where Hk and Lk are the two mean values and B is the bitmap. Figure 1 shows an example of the AMBTC algorithm.
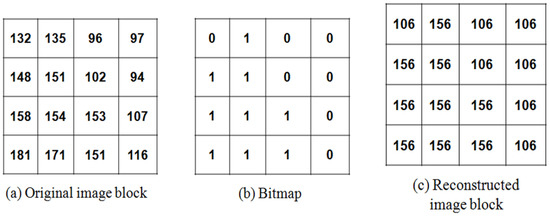
Figure 1.
Example of the AMBTC algorithm.
Assume that the original image block size of 4 × 4 pixels is shown in Figure 1a. The mean value M of the pixel values at each block X is calculated as M = 134. Then, each pixel is compared to the mean value M to generate the bitmap table B of this block, as presented in Figure 1b. According to Equations (1) and (2), two mean values, Hk and Lk, are calculated as Hk = 156 and Lk = 106, respectively. The compressed trio of the block is determined as (156, 106, 0100110011101110), which is sent to a receiver. After obtaining the compressed trio, the receiver can decode it to reconstruct the image block shown in Figure 1c. In general, if an image is sized as 512 × 512 pixels, then its code stream after encoding is sized as bits, which is one-quarter the size of the original image.
2.2. Sun et al.’s Scheme
In 2013, Sun et al. [19] proposed a reversible data hiding scheme for BTC-compressed images based on the joint neighbor coding technique, which was inspired by Wang et al. [22]. In this scheme, the P × Q image is first encoded by the BTC algorithm with an n × n image block to generate a high mean table, H = H1, H2, …, H(P×Q)/(n×n), low mean table, L = L1, L2, …, L(P×Q)/(n×n), and bitmap table, B = B1, B2, …, B(P×Q)/(n×n). Then, the same embedding process is used to embed a secret message into the two mean table tables, H and L. Therefore, the high mean table H is used to demonstrate this embedding process as follows. Let M be a binary pseudo-random sequence, and the length of M is similar to that of the secret message. Figure 2 shows there are four neighboring high mean values, and they are selected to encode the current high mean value Hcur. The set of four neighboring high mean values is denoted as Href, which is marked in the light blue area, and their corresponding indicators are (00), (01), (10), and (11), respectively.
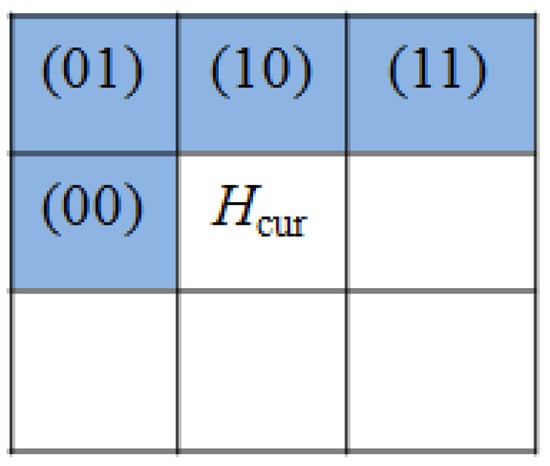
Figure 2.
The current value Hcur and its four reference values.
The embedding process of Sun et al.’s scheme is described in detail as follows.
- Step 1: Read two bits bM from M and two bits bS from the secret message S.
- Step 2: Determine the reference indicator bref = bM XOR bS.
- Step 3: According to the value of bref, select the corresponding Href and calculate the difference value D = Hcur − Href.
- Step 4: Classify D into four cases and encode D to D’ using Equation (3)where m is a predefined parameter and ranges in [1,8], || is the concatenation function, and (Dm)2 and (D8)2 represent the m bits and eight bits of binary information of the difference value D.
- Step 5: Concatenate the reference indicator bref and the value D’ to generate the final codestream of the current high mean value as bref||D’.
- Step 6: Repeat Steps 1 to 5 until the entire high mean values are encoded completely.
After the above six steps are finished, the codestream CSH of the high mean table is obtained. Obviously, Sun et al. used the joint neighbor coding technique to embed a secret message into the two mean tables, H and L. This scheme could guarantee that the successful restoration of the original BTC-compressed image is achieved after the secret message was extracted. However, their scheme offered a low embedding capacity.
3. Proposed Scheme
In this section, we propose a novel reversible data hiding scheme for AMBTC-compressed images to further improve the performance of previous schemes. The main idea of the proposed scheme is that the AMBTC-compressed data that is generated by the AMBTC algorithm is further encoded losslessly based on the high correlation of neighboring mean values in the two mean tables, H and L. Once the hidden secret data have been extracted, the original AMBTC-based image, as shown in Figure 1c, will be completely restored. To achieve our idea, first, the AMBTC algorithm is performed on the input image to obtain the high mean table H, low mean table L, and bitmap table B. Then, the embedding process is used to hide a secret message S into the two mean tables while the bitmap table stays unchanged. The difference values of these two tables are calculated and used to embed the secret message. The proposed scheme has two phases, i.e., the embedding phase and the extracting phase, which are described in Section 3.1 and Section 3.2, respectively.
3.1. Embedding Phase
Assume that a P × Q image I is encoded as an M × N high mean table H, an M × N low mean table L, and a P × Q bitmap table B, where M = P/4 and N = Q/4. After obtaining the three tables, the secret message S can be embedded by encoding the difference values of the two mean tables, H and L, respectively. The final code stream CS generated by the proposed scheme will include four parts, which are guided information (IN), code stream CSH of the high mean table H, code stream CSL of the low mean table L, and code stream CSB of the bit map table B, as shown in Figure 3. As for guide information (IN), it indicates the basic data of the code stream, including the lengths of the secret message S, codestream CSH, codestream CSL, size of cover image size, and value of m. IN is used to tell the data receiver how they can determine the information of data during the extracting process. Figure 4 shows the flow chart of the proposed embedding phase.

Figure 3.
The structure of the code stream CS.
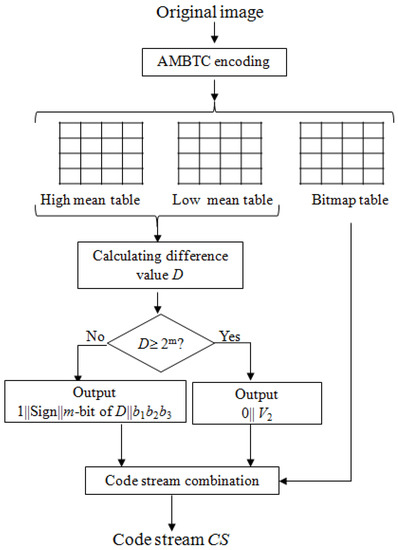
Figure 4.
Flow chart of the proposed embedding phase.
The detailed embedding algorithm is shown as follows.
Step 1: Calculating difference value D.
Firstly, an inverse “S” scan path, shown in Figure 5, is used to scan the high mean table H and low mean table L into sequences of mean values SH (SH1, SH2, ..., SHM×N) and SL (SL1, SL2, ..., SLM×N), respectively. Then, calculate two different value sequences, DH and DL, i.e., DHi+1 = SHi+1 − SHi and DLi+1 = SLi+1 − SLi, where 1 ≤ i ≤ M × N − 1.
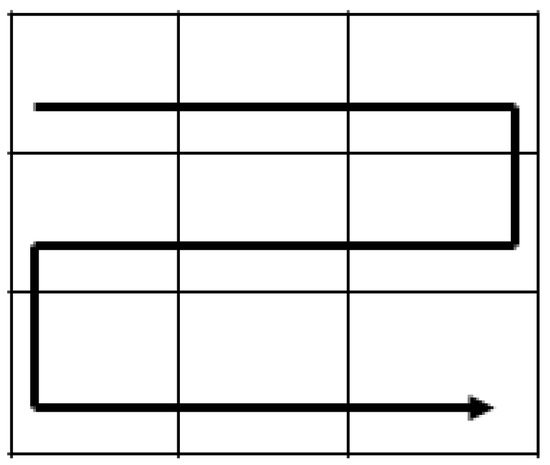
Figure 5.
Example of inverse “S” scan path.
It is clear that the values of two difference sequences, DH and DL, are in range [−255, 255]. The embedding process of DH is similar to that of DL. Therefore, to better explain, let Di be DHi (or DLi) and Vi be the corresponding mean value of SHi (or SLi), respectively.
Step 2: Encoding difference value D.
Due to the high correlation of adjacent values in the two mean tables, most of the difference values of D are ranged around 0. This property is used for embedding data. The value of Di will be encoded as follows.
where, for < 2m, the is encoded by indicator “1,” followed by 1-bit of the sign of the value of , m bits of binary representation of the absolute value of , and concatenated by three secret bits . If < 0, the sign of will be equal to 1; otherwise, the sign of will be equal to 0. Otherwise, if , it is encoded by indicator “0,” and followed by eight bits of binary representation of the original mean value Vi. Then, the compression code of is concatenated into the corresponding output code stream CSH (or CSL).
Step 3: Code stream combination
After all difference values of DH and DL are encoded completely, the final code stream CS is obtained by concatenating IN, CSH, CSL, and the code stream CSB of the bitmap table.
To clarify our embedding phase, Figure 6 shows an example of the embedding phase. Assume the AMBTC algorithm is performed, and a 3 × 3 high mean table is generated as shown in Figure 6a.
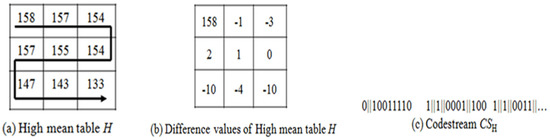
Figure 6.
Example of the embedding algorithm for high mean table: (a) high mean table H; (b) difference value of high mean table H; (c) codestream CSH.
Along the inverse “S” scan path, the difference values are calculated and shown in Figure 6b. Assume the secret message S is “100011011011,” and m = 4 is used. The first difference value Di of DH is equal to “158,” so |Di| = 158 ≥ 24. According to Step 2, no secret message is embedded, and the 1-bit indicator “0” should be used. Then, the difference value Di is encoded as 0||10011110. The second difference value Di is equal to “−1,” so |Di| < 24. Thus, read three secret bits b1b2b3 = 100 from the secret message S. Finally, Di is encoded by Di’ = 1||1||0001||100, and Di’ is sent to code stream CSH. Using the above-described embedding algorithm, all difference values of the high mean table H will be encoded to generate the code stream CSH completely.
3.2. Extracting Phase
After obtaining the code stream CS, the receiver can extract the embedded secret message S exactly and recover the AMBTC-compressed image precisely. The detail of the extracting phase is shown as follows.
- Step 1: Extract the guide information IN from the code stream CS. According to IN, the information of the embedded message S, CSH, CSL, CSB, the size of the cover image, and the value of m are determined.
- Step 2: Read one bit indicator ind from the codestream CSH (or CSL).
- Step 3. If ind = 0, this means that no secret message is extracted. Then, eight consecutive bits are read and converted to decimal value as the reconstructed mean value SHi (or SLi).
- Step 4: If ind = 1, read one next bit d as the sign of the reconstructed difference value D. Then, read m consecutive bits and convert them to decimal values as the reconstructed difference value D. Three next bits are read as three extracted secret bits and concatenated into the secret message S. Then, the value of d is considered to reconstruct the mean value as follows.
If d = 1, the reconstructed mean value SHi (or SLi) is calculated using Equation (5).
If d = 0, the reconstructed mean value SHi (or SLi) is calculated using Equation (6).
where 2 ≤ i ≤ M × N. The reconstructed mean value SHi (or SLi) is sent to the corresponding high or low mean tables.
- Step 5: Steps 2 to 4 are implemented repeatedly until all values of the two mean tables are reconstructed completely.
Once the extracting algorithm is finished, the secret message S is extracted exactly. Moreover, the two mean tables are recovered accurately. Obviously, the original AMTBC-compressed image is recovered without any distortion. Following the example of the embedding phase shown in Figure 6, Figure 7 shows the example of the proposed extracting phase. First, the first bit, ind = 0, is read from code stream CSH. According to Step 3, the consecutive eight bits, 10011110, are read and converted to decimal value as SHi = 158. The next indicator bit, ind = 1, is read from CSH. According to Step 4, read one bit d = 1, then four subsequent bits, 0001, are read and converted to a decimal value as D = 1. Three next bits, 100, are read as three extracted secret bits, . Since d = 1, according to Step 4, the reconstructed mean value SHi is calculated as . The extracting phase is terminated when the entire bits in the code stream CS are processed completely.

Figure 7.
Example of the extracting algorithm for high mean table: (a) codestream CSH; (b) high mean table H.
4. Experimental Results
In this section, tests of the performance of the proposed scheme on six public 512 × 512 images shown in Figure 8 are described. MATLAB R2010a was used to program the proposed scheme and five previous schemes in the experiments, including AMBTC, Chuang and Chang [14], Chang et al. [15], and Hong et al. [16,20]. As for the remaining existing schemes, we cite the experimental results from their published articles. The objective measures, peak signal-to-noise ratio (PSNR), embedding capacity (EC), efficiency rate, and bit rate, were performed to estimate performance in this paper. For the P × Q grayscale image, the PSNR is calculated by Equation (7), where MSE is the mean square error and is defined as shown in Equation (8). It is noted that the proposed scheme has the reversibility feature, and the reconstructed image will be the same as the AMBTC-reconstructed image after hidden secret data have been successfully extracted. To prove our proposed scheme is reversible data hiding for AMBTC-compressed images, the definitions of the original image and reconstructed image are the same as those defined by AMBTC. The bit rate and efficiency rate are calculated by Equations (9) and (10), respectively.
where Xij and X’ij are the pixel values of the original image and the AMBTC-reconstructed image, respectively. EC is the embedding capacity, and |CS| denotes the size of the code stream CS. EC is calculated as EC = 3 × N − 62 bits, where N is the number of .
Figure 8.
Six test grayscale images sized 512 × 512.
In the proposed scheme, m is the parameter that can affect the performance of the proposed scheme; therefore, in Table 1, difference values of m were used to test the results of the proposed scheme. As can be observed in Table 1, the PSNRs of the image were not changed with the difference values of m. Basically, the value of m is only ranged from 3 to 5. This is because when m = 3, it only takes eight bits at most to encode each difference value for either the high mean table or low mean table. In other words, the size of the final code stream of our proposed scheme will be the same as that of conventional AMBTC. Based on the experimental results, we can observe that when the value of m is increased from 3 to 5, the embedding capacity is gained while the value of the bit rate is also increased. Therefore, it is suggested that the value of m should be set to 4 in the proposed scheme to achieve both a high embedding capacity and an acceptable bit rate at the same time.

Table 1.
Performance of the proposed scheme under difference values of m.
To show the efficient performance of the proposed scheme over some previous schemes, we compared our proposed scheme with seven previous schemes, i.e., Chuang and Chang [14], Chang et al. [15], Hong et al. [16], Chen et al. [17], Li et al. [18]. Sun et al. [19], and Hong et al. [20]. Table 2 shows the performance comparison of the proposed scheme and seven previous schemes [14,15,16,17,18,19,20], with the same block size 4 × 4. As can be observed in Table 2, our proposed scheme offers the highest embedding capacity, followed by the schemes of Hong et al. [20] and Sun et al. [19]. As for the image quality of the stego images, the proposed scheme and five previous schemes [15,16,17,18,19] offer precisely similar PNSRs as the results of the traditional AMBTC technique. The main reason is that these five schemes did not modify the AMBTC-compressed images during the data embedding process. However, Table 2 also shows that Chuang and Chang’s scheme [14] offered the worse PSNR among the seven schemes because this scheme was not reversible. It is clear that the proposed scheme obtained the highest embedding capacity among the five schemes. The proposed scheme is based on the high correlation of neighboring values in the two mean tables to embed three bits into each selected mean value, whereas only two bits were embedded in Sun et al.’s scheme, and one bit was embedded in Chang et al.’s scheme. Chuang and Chang’s scheme used each smooth block of BTC-compressed image to embed only one secret bit. Three previous schemes [16,17,18] only embedded one bit into each 4 × 4 block of the BTC-compressed image. Obviously, the performance of Li et al.’s scheme [18] was slightly better than the two other schemes [16,17]. However, if more blocks with the same high mean value and the low mean value were determined in the image, the scheme of Chen et al. provided better embedding capacity than that of the scheme of Hong et al.

Table 2.
Performance comparison of the proposed scheme and seven previous schemes [14,15,16,17,18,19,20].
As can be observed in Table 2, the embedding capacity offered by the proposed scheme, on average, was higher than that of Hong et al.’s [20] and Sun et al.’s scheme [19] by more than 10,000 bits, was nearly 2.53 times higher than Chang et al.’s scheme [15], and was four times higher than four other schemes [14,16,17,18], with a slightly higher bit rate of the proposed scheme. Even though a high bit rate is required, however, Figure 9 presents that the proposed scheme has a much higher efficiency rate than the seven previous schemes. Specifically, the efficiency rate of the proposed scheme, on average, outperformed Sun et al.’s scheme [19] by 2%, while it was two times larger than Chang et al.’s scheme and four times that of four other schemes [14,16,17,18].
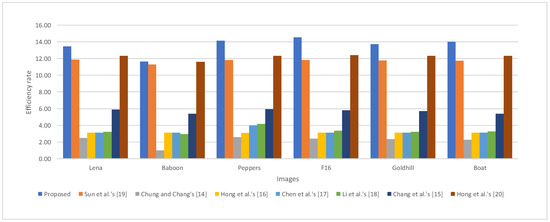
Figure 9.
Comparison of efficiency rate between the proposed scheme and seven previous schemes [14,15,16,17,18,19,20].
To demonstrate our performance on image quality (PSNR), embedding capacity (EC), and embedding efficiency can compete with the latest existing scheme, we compare our proposed scheme with Hong et al.’s scheme [20] in Table 3 To provide fair comparisons, all data related to Hong et al.’s scheme are based on the best combinations of (α, β), and the corresponding (α, β) for each test image, as listed in Table 3. From Table 3, we can observe the average image quality is the same as that of Hong et al.’s scheme since both two schemes are reversible data hiding schemes. However, when m is up to 5, the average hiding capacity will be up to 74,977 bits, which is 10,461 bits higher than that of Hong et al.’s scheme. In other words, the average embedding efficiency offered by our scheme is 0.085 bpp higher than that of Hong et al.’s scheme based on the definition given in Equation (10).

Table 3.
Performance comparison of the proposed scheme and Hong et al.’s scheme [20] on PSNR, EC, and embedding efficiency.
5. Conclusions
In this paper, we introduced a new reversible data hiding scheme for AMBTC-compressed images by depending on the adjacent relation of mean values. To achieve a high embedding capacity and efficiency rate, the high correlation of values in two mean tables was explored and used to embed a secret message. The experimental results demonstrated that the proposed scheme obtained a high embedding capacity while guaranteeing the same PSNRs as the traditional AMBTC algorithm. In addition, the proposed scheme achieved a higher embedding capacity and efficiency rate than those of previous schemes while maintaining an acceptable bit rate. Obviously, the experimental results confirm that the proposed scheme can be used not only to protect secret messages but also as a practical algorithm for real-time applications.
Author Contributions
Conceptualization, C.-C.L. and T.-S.N.; methodology, C.-C.L. and T.-S.N.; software, T.-S.N. and W.-C.C.; validation, C.-C.L., and C.-C.C.; writing—original draft preparation, T.-S.N.; writing—review and editing, C.-C.L.; project administration, C.-C.C.; funding acquisition, C.-C.L. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the Ministry of Science and Technology, Taiwan (grant number MOST 109-2410-H-167-014).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
All test data can be accessed in public repository.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Wang, W.-J.; Huang, C.-T.; Wang, S.-J. VQ Applications in Steganographic Data Hiding Upon Multimedia Images. IEEE Syst. J. 2011, 5, 528–537. [Google Scholar] [CrossRef]
- Chen, S.; Leung, H. Chaotic Watermarking for Video Authentication in Surveillance Applications. IEEE Trans. Circuits Syst. Video Technol. 2008, 18, 704–709. [Google Scholar] [CrossRef]
- Tai, W.-L.; Yeh, C.-M.; Chang, C.-C. Reversible Data Hiding Based on Histogram Modification of Pixel Differences. IEEE Trans. Circuits Syst. Video Technol. 2009, 19, 906–910. [Google Scholar] [CrossRef]
- Nguyen, T.S.; Chang, C.C.; Lin, M.C. Adaptive lossless data-hiding and compression scheme for SMVQ indices using SOC. Smart Comput. Rev. 2014, 4, 230–245. [Google Scholar] [CrossRef]
- Luo, L.; Chen, Z.; Chen, M.; Zeng, X.; Xiong, Z. Reversible Image Watermarking Using Interpolation Technique. IEEE Trans. Inf. Forensics Secur. 2010, 5, 187–193. [Google Scholar] [CrossRef]
- Chang, C.-C.; Nguyen, T.S.; Lin, C.-C. Reversible data embedding for indices based on histogram analysis. J. Vis. Commun. Image Represent. 2014, 25, 1704–1716. [Google Scholar] [CrossRef]
- Hong, W.; Chen, T.-S. A Novel Data Embedding Method Using Adaptive Pixel Pair Matching. IEEE Trans. Inf. Forensics Secur. 2011, 7, 176–184. [Google Scholar] [CrossRef]
- Huang, F.; Huang, J.; Shi, Y.-Q. New Channel Selection Rule for JPEG Steganography. IEEE Trans. Inf. Forensics Secur. 2012, 7, 1181–1191. [Google Scholar] [CrossRef]
- Tseng, H.; Chang, C. High Capacity Data Hiding in JPEG-Compressed Images. Informatica 2004, 15, 127–142. [Google Scholar] [CrossRef]
- Chang, C.C.; Nguyen, T.S.; Lin, C.C. A reversible data hiding scheme for VQ indices based on absolute difference trees. KSII Trans. Internet Inf. Syst. 2014, 8, 2572–2589. [Google Scholar]
- Lee, J.-D.; Chiou, Y.-H.; Guo, J.-M. Lossless data hiding for VQ indices based on neighboring correlation. Inf. Sci. 2013, 221, 419–438. [Google Scholar] [CrossRef]
- Qin, C.; Chang, C.-C.; Chiu, Y.-P. A Novel Joint Data-Hiding and Compression Scheme Based on SMVQ and Image Inpainting. IEEE Trans. Image Process. 2014, 23, 969–978. [Google Scholar] [CrossRef] [PubMed]
- Lin, M.-H.; Chang, C.-C. A novel information hiding scheme based on BTC. In Proceedings of the Fourth International Conference on Computer and Information Technology, Wuhan, China, 16 September 2004; pp. 66–71. [Google Scholar]
- Chuang, J.C.; Chang, C.C. Using a simple and fast image compression algorithm to hide secret information. Int. J. Comput. Appl. 2006, 28, 329–333. [Google Scholar]
- Chang, C.-C.; Lin, C.-Y.; Fan, Y.-H. Lossless data hiding for color images based on block truncation coding. Pattern Recognit. 2008, 41, 2347–2357. [Google Scholar] [CrossRef]
- Hong, W.; Chen, T.-S.; Shiu, C.-W. Lossless Steganography for AMBTC-Compressed Images. In Proceedings of the 2008 Congress on Image and Signal Processing, Sanya, China, 27–30 May 2008; pp. 13–17. [Google Scholar] [CrossRef]
- Chen, J.; Hong, W.; Chen, T.-S.; Shiu, C.-W. Steganography for BTC compressed images using no distortion technique. Imaging Sci. J. 2010, 58, 177–185. [Google Scholar] [CrossRef]
- Li, C.-H.; Lu, Z.-M.; Su, Y.-X. Reversible Data Hiding for Btc-compressed Images Based on Bitplane Flipping and Histogram Shifting of Mean Tables. Inf. Technol. J. 2011, 10, 1421–1426. [Google Scholar] [CrossRef][Green Version]
- Sun, W.; Lu, Z.-M.; Wen, Y.-C.; Yu, F.-X.; Shen, R.-J. High performance reversible data hiding for block truncation coding compressed images. Signal Image Video Process. 2013, 7, 297–306. [Google Scholar] [CrossRef]
- Hong, W.; Ma, Y.-B.; Wu, H.-C.; Chen, T.-S. An efficient reversible data hiding method for AMBTC compressed images. Multimedia Tools Appl. 2016, 76, 5441–5460. [Google Scholar] [CrossRef]
- Lema, M.; Mitchell, O. Absolute Moment Block Truncation Coding and Its Application to Color Images. IEEE Trans. Commun. 1984, 32, 1148–1157. [Google Scholar] [CrossRef]
- Wang, J.-X.; Lu, Z.-M. A path optional lossless data hiding scheme based on VQ joint neighboring coding. Inf. Sci. 2009, 179, 3332–3348. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).