A Comparative Analysis of Arabic Text Steganography
Abstract
1. Introduction
- It presents a brief review of existing linguistic text steganography methods.
- It summarizes Arabic text steganography methods from their initiation while identifying their methodologies and analyzing their strengths and weaknesses.
- It provides a comparative analysis of Arabic text steganography based on the key evaluation criteria (i.e., capacity, invisibility, robustness, and security).
- It recommends future path work in Arabic text steganography.
2. Steganography
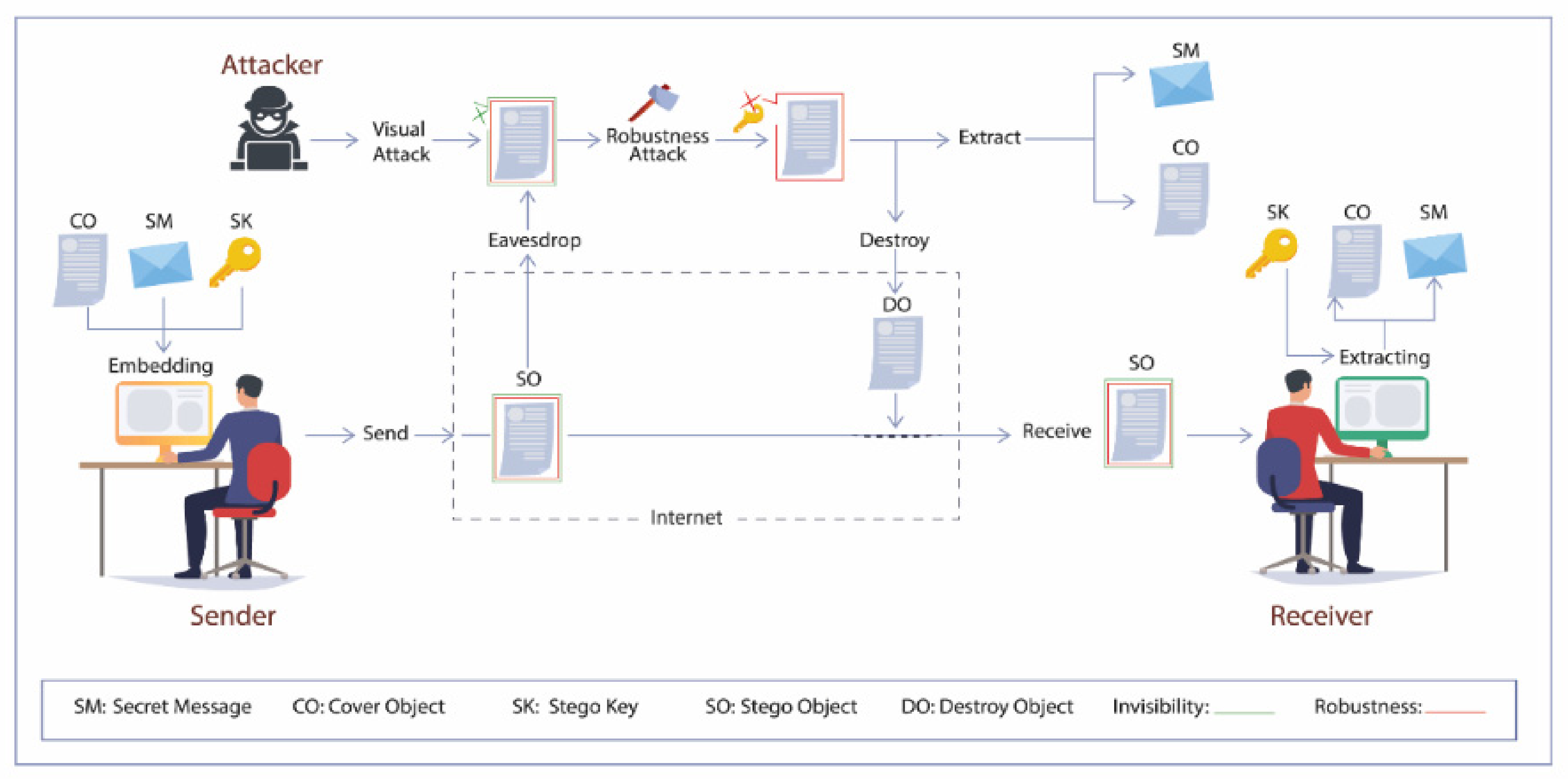
2.1. Steganography Scenario
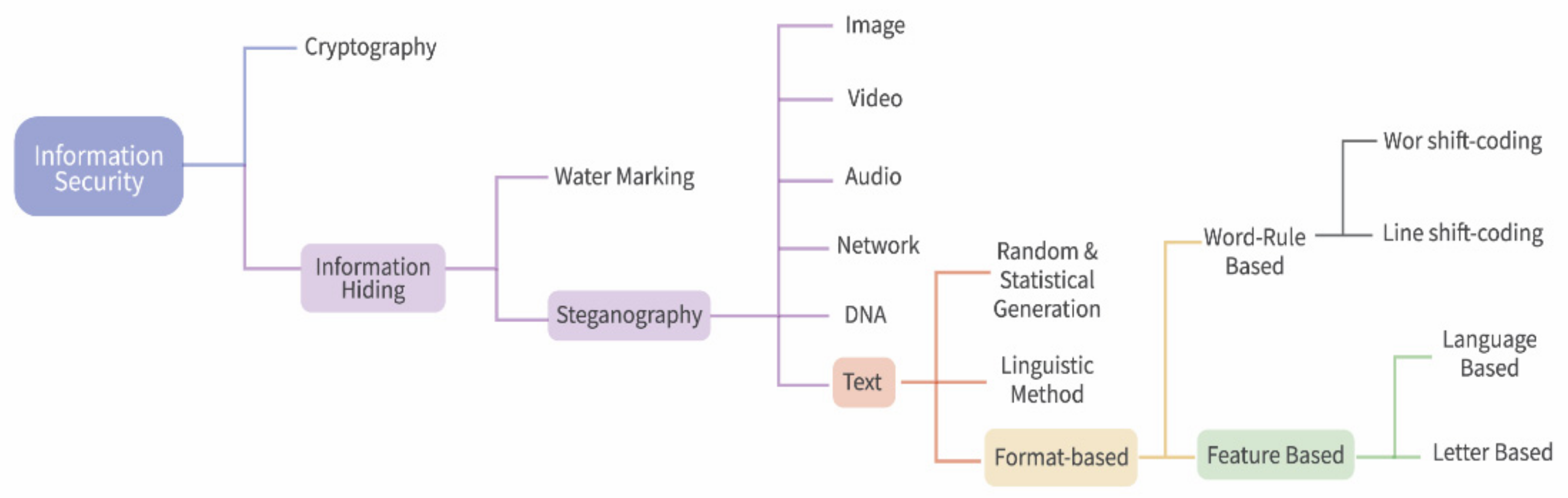
2.2. Steganography Types
2.2.1. Image Steganography
2.2.2. Video Steganography
2.2.3. Audio Steganography
2.2.4. Text Steganography
2.2.5. Network Steganography
2.2.6. DNA Steganography
3. Text Steganography
3.1. Random and Statistical Generation
3.2. Linguistic Steganography
3.3. Format-Based Steganography
3.3.1. English-Based
3.3.2. Chinese-Based
3.3.3. Indian-Based
3.3.4. Polish-Based
3.3.5. Thai-Based
3.3.6. Czech-Based
4. Arabic Text Steganography
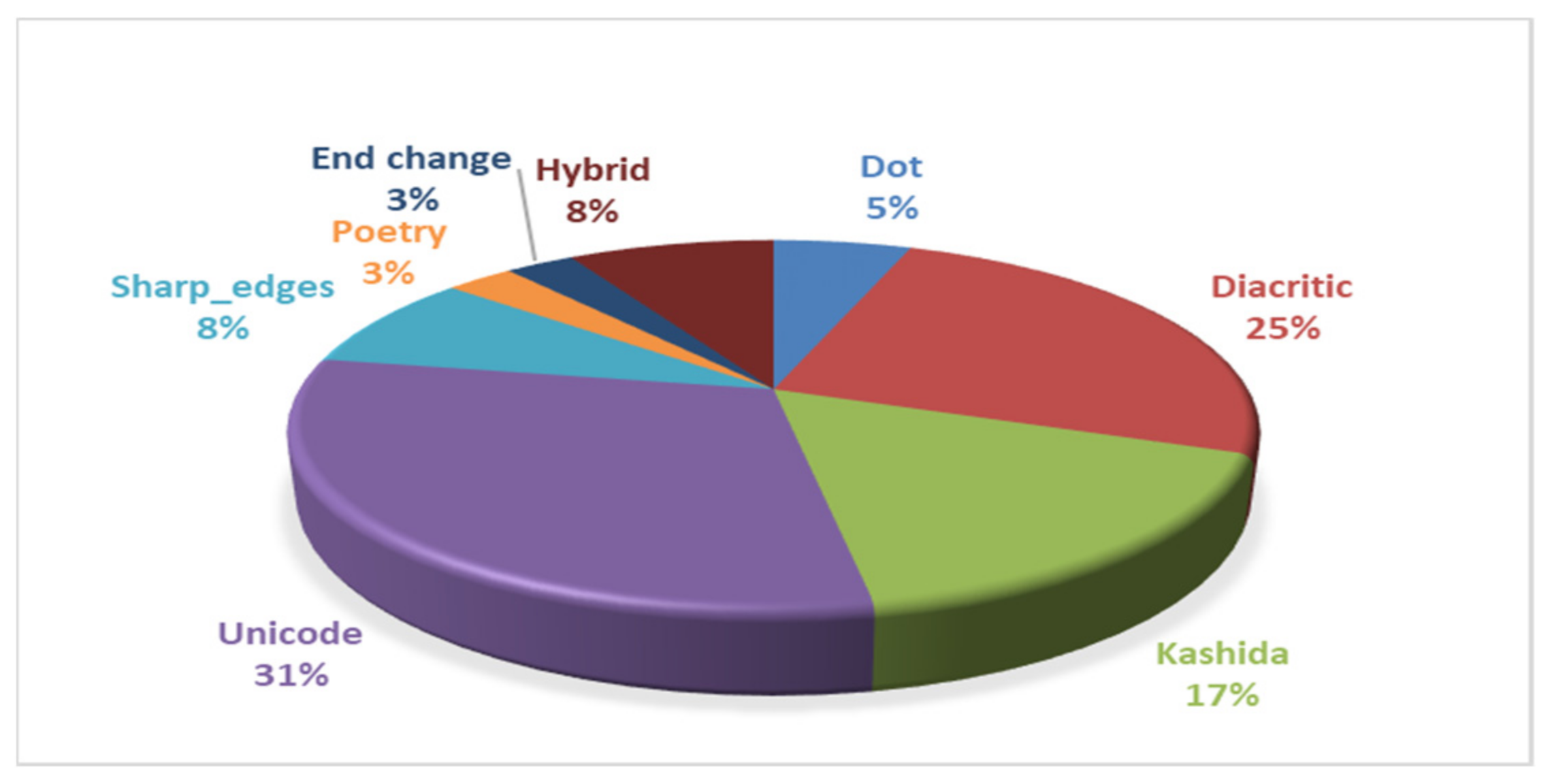
4.1. Dot Method
4.2. Diacritic Method
4.3. Kashida Method
4.4. Unicode Method
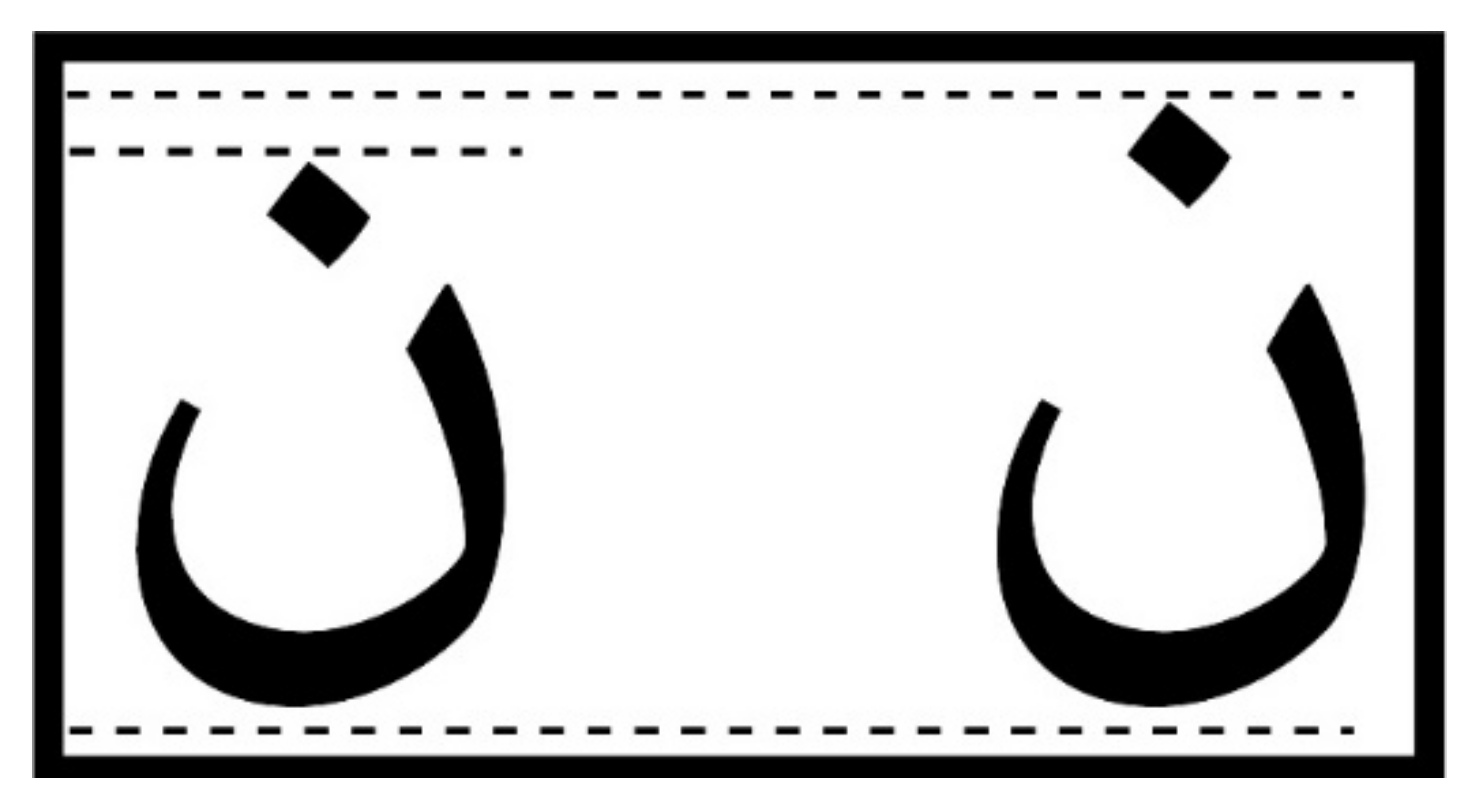
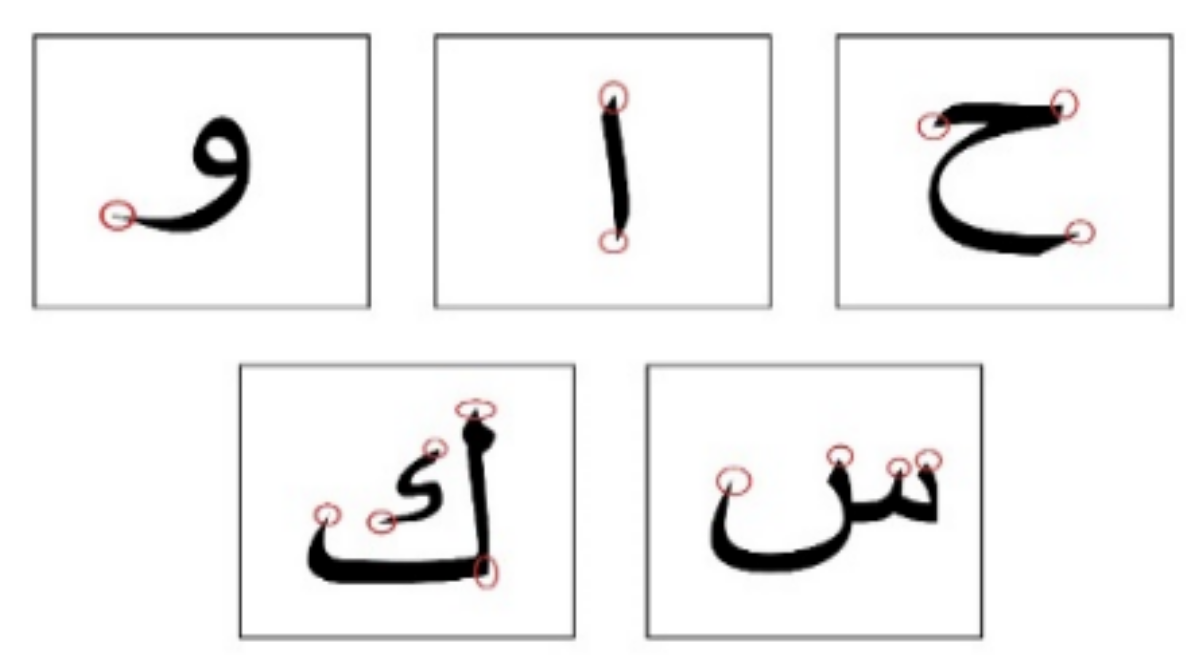
4.5. Sharp Edges Approach
4.6. Poetry Approach
4.7. Hybrid Approach
5. Evaluation Criteria
5.1. Embedding Capacity
5.2. Invisibility
5.3. Robustness
5.4. Security
5.5. Evaluation of Arabic Text Steganography Methods
- Dot method: Although this method enhances invisibility, it is less robust, as the hidden message may be lost if the font format is changed. In addition, the method does not consider the encryption or non-sequence embedding positions to prevent the hidden bits from extraction. Despite using compression, the capacity is still low, with the maximum embedded bits per location are two.
- Diacritics method: Low invisibility is the major drawback of this method. The cover text and stego text are not identical, and the stego text has many ambivalences in using diacritics. Besides that, capacity is still low, where the bits per location ranges from one to four. Whereas this method partially enhances the robustness of the stego text, the secret message is not encrypted and not embedded in non-sequence positions.
- Kashida method: This method is resistant against the copy-paste action but has downsides in terms of capacity, invisibility, and robustness.
- Unicode method: The embedding capacity of this method is decreased even though compression is used in some techniques. However, this method accomplishes high invisibility. The robustness is improved in copy-paste action, font format, and OCR, but encryption and non-sequence embedding are not considered.
- Sharp edges method: This method achieved high invisibility, capacity, and robustness. Adding non-sequence embedding adds more complexity to protect it from the attacker.
- Poetry system method: The method has high invisibility and higher robustness. However, its hiding capacity is limited.
- Integrated method: The primary goal of merging methods is to improve performance and overcome the previous methods’ limitations. Nevertheless, if the methods are not integrated properly, then these drawbacks are inherited.
6. Recommendations for Future Works
- Although some researchers have considered Arabic characters, most of them have not applied their suggested methods to social media. Meanwhile, such media are fertile environments for information hiding, as a large volume of texts is pumped on social networks every day. This volume of texts makes it difficult for the eavesdropper to specifically select any of them that may contain hidden information. Researchers can thus apply some of these methods to social media while facilitating the support for Arabic characters.
- The integration of text steganography methods improves the capacity and increases the difficulty experienced by the eavesdropper in an attempt to trace the embedding algorithm. However, these methods inherit the disadvantages of the methods that make them up. This is especially obvious in the kashida approach, which increases the stego file size which also raising the level of suspicion in specific cases. Therefore, the integration should be well studied to identify which methods achieve the desired objectives while minimizing the constituent methods’ drawbacks.
- A compression method reduces the amount of hidden information, thereby increasing the capacity. It also increases the complexity of extracting the secret message from the cover text. Despite this, only a few researchers have used compression to improve the efficiency of their methods.
- A few of the proposed studies have provided solutions to enhance the protection of secret messages prior to the embedding process by combining both cryptography and steganography methods, especially for protecting the stego key. This combined method constitutes another layer of protection if the embedding algorithm is detected.
- During this survey, it was observed that the use of full diacritics text is lacking, which is the obstacle preventing the exploitation of such diacritics. It is worth noting that students of religious studies or linguistic sciences at all stages adopt this type of text. Similarly, the Quran and Hadiths scripts are omnipresent on the web and social media and widely used as references and an inference.
- Regardless of kashida’s weaknesses, such as increasing the stego file size and thus increasing the suspicion to a reader, utilizing kashida in text watermarking, especially in Quranic scripts, is ideal than text steganography. In text watermarking, kashida is used to protect or copyright the text without affecting the meaning of the text, unlike the diacritics.
- Most Arabic text steganography methods suffer from low capacity because of the limited number of bits per location and usable characters. Integrated Arabic features with font attributes are used to enhance the capacity.
- The selection of the embedding positions sequentially tells the attacker the order of the secret bits. Therefore, it is imperative to propose embedding methods with non-sequence position as the additional security layer.
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Azeem, M.; He, J.; Rana, K.G.; Akhtar, F. A cryptographic data hiding algorithm with high cover text capacity. Int. J. Electron. Secur. Digit. Forens. 2019, 11, 225–244. [Google Scholar] [CrossRef]
- Malik, A.; Sikka, G.; Verma, H.K. A high capacity text steganography scheme based on LZW compression and color coding. Eng. Sci. Technol. Int. J. 2017, 20, 72–79. [Google Scholar] [CrossRef]
- Din, R.; Utama, S.; Hanizan, S.H.; Hilal, M.M.; Hanif, M.A.M.; Zulhazlin, A.; Fazali, G.M. Evaluating the Feature-Based Technique of Text Steganography Based on Capacity and Time Processing Parameters. Adv. Sci. Lett. 2018, 24, 7355–7359. [Google Scholar] [CrossRef]
- Ahvanooey, M.T.; Li, Q.; Hou, J.; Rajput, A.R.; Yini, C. Modern Text Hiding, Text Steganalysis, and Applications: A Comparative Analysis. Entropy 2019, 21, 355. [Google Scholar] [CrossRef] [PubMed]
- Cohen, A.; Holmgren, J.; Nishimaki, R.; Vaikuntanathan, V.; Wichs, D. Watermarking Cryptographic Capabilities. SIAM J. Comput. 2018, 47, 2157–2202. [Google Scholar] [CrossRef]
- Artz, D. Digital steganography: Hiding data within data. IEEE Internet Comput. 2001, 5, 75–80. [Google Scholar] [CrossRef]
- Khosravi, B.; Khosravi, B.; Khosravi, B.; Nazarkardeh, K. A new method for pdf steganography in justified texts. J. Inf. Secur. Appl. 2019, 45, 61–70. [Google Scholar] [CrossRef]
- Rahman, S.A.E.; Nourah, P.; Abdulrahman, B.; Arabia, S. Text Steganography Approaches Using Similarity of English Font Styles; IGI Global: Hershey, PA, USA, 2019; Volume 7, pp. 29–50. [Google Scholar] [CrossRef]
- Aljawarneh, S.A.; Vangipuram, R.; Puligadda, V.K.; Vinjamuri, J. G-SPAMINE: An approach to discover temporal association patterns and trends in internet of things. Futur. Gener. Comput. Syst. 2017, 74, 430–443. [Google Scholar] [CrossRef]
- Alsaadi, H.I.; Al-Anni, M.K.; Almuttairi, R.M.; Bayat, O.; Ucan, O.N. Text steganography in font color of MS excel sheet. In Proceedings of the International Conference on Data Science, E-learning and Information Systems, Madrid, Spain, 1–2 October 2018; pp. 1–7. [Google Scholar]
- Kang, Y.; Liu, F.; Yang, C.; Luo, X.; Zhang, T. Color Image Steganalysis Based on Residuals of Channel Differences. Comput. Mater. Contin. 2019, 59, 315–329. [Google Scholar] [CrossRef]
- Ditta, A.; Yongquan, C.; Azeem, M.; Rana, K.G.; Yu, H.; Memon, M.Q. Information hiding: Arabic text steganography by using Unicode characters to hide secret data. Int. J. Electr. Secur. Digit. Forens. 2018, 10, 61–78. [Google Scholar] [CrossRef]
- Müller, J. Online Activities of Internet Users in Malaysia as of May 2020, by Activity. Available online: https://www.statista.com/statistics/788504/online-activities-of-internet-users-by-activity-malaysia/ (accessed on 24 April 2021).
- Din, R.; Thabit, R.A.; Udzir, N.I.; Utama, S. Traid-bit embedding process on Arabic text steganography method. Bull. Electr. Eng. Inform. 2021, 10, 493–500. [Google Scholar] [CrossRef]
- Gupta, S.; Gupta, D. Text-Steganography: Review Study & Comparative Analysis. Int. J. Comput. Sci. Inf. Technol. 2011, 2, 2060–2062. [Google Scholar]
- Sharma, S.; Gupta, A.; Trivedi, M.C.; Yadav, V.K. Analysis of Different Text Steganography Techniques: A Survey. In Proceedings of the 2016 Second International Conference on Computational Intelligence & Communication Technology (CICT), Ghaziabad, India, 12–13 February 2016; pp. 130–133. [Google Scholar]
- Osman, B.; Yasin, A.; Omar, M.N. An analysis of alphabet-based techniques in text steganography. J. Telecommun. Electron. Comput. Eng. 2016, 8, 109–115. [Google Scholar]
- Hakak, S.; Kamsin, A.; Tayan, O.; Idris, M.Y.I.; Gilkar, G.A. Approaches for preserving content integrity of sensitive online Arabic content: A survey and research challenges. Inf. Process. Manag. 2017, 56, 367–380. [Google Scholar] [CrossRef]
- Krishnan, R.B.; Thandra, P.K.; Baba, M.S. An Overview of Text Steganography. In Proceedings of the 2017 Fourth International Conference on Signal Processing, Communication and Networking (ICSCN), Chennai, India, 16–18 March 2017; pp. 1–6. [Google Scholar]
- Ahvanooey, M.T.; Li, Q.; Shim, H.J.; Huang, Y. A Comparative Analysis of Information Hiding Techniques for Copyright Protection of Text Documents. Secur. Commun. Netw. 2018, 2018, 1–22. [Google Scholar] [CrossRef]
- Baawi, S.S.; Mokhtar, M.R.; Sulaiman, R. A comparative study on the advancement of text steganography techniques in digital media. ARPN J. Eng. Appl. Sci. 2018, 13, 1854–1863. [Google Scholar]
- Narayana, V.L.; Gopi, A.P.; Kumar, N.A. Different techniques for hiding the text information using text steganography techniques: A survey. Ing. Sys. Inf. 2018, 23, 115–125. [Google Scholar] [CrossRef]
- Dhawan, S.; Gupta, R. Analysis of various data security techniques of steganography: A survey. Inf. Secur. J. Glob. Perspect. 2020, 30, 1–25. [Google Scholar] [CrossRef]
- Muhammad, M.H.; Hussain, H.S.; Din, R.; Samad, H.; Utama, S. Review on feature-based method performance in text steganography. Bull. Electr. Eng. Inform. 2021, 10, 427–433. [Google Scholar] [CrossRef]
- Mollin, R.A. An Introduction to Cryptography; CRC Press: Boca Raton, FL, USA, 2000. [Google Scholar]
- Kawaguchi, E.; Eason, R.O. Principles and Applications of BPCS Steganography Multimedia Systems and Applications; International Society for Optics and Photonics: Boston, MA, USA, 1999; Volume 3528, pp. 464–474. [Google Scholar]
- Xiang, L.; Wang, X.; Yang, C.; Liu, P. A Novel Linguistic Steganography Based on Synonym Run-Length Encoding. IEICE Trans. Inf. Syst. 2017, E100D, 313–322. [Google Scholar] [CrossRef]
- Girdhar, A.; Kumar, V. Comprehensive survey of 3D image steganography techniques. IET Image Process. 2017, 12, 1–10. [Google Scholar] [CrossRef]
- Zakaria, A.A.; Hussain, M.; Wahab, A.W.A.; Idris, M.Y.I.; Abdullah, N.A.; Jung, K.-H. High-Capacity Image Steganography with Minimum Modified Bits Based on Data Mapping and LSB Substitution. Appl. Sci. 2018, 8, 2199. [Google Scholar] [CrossRef]
- Singh, T.; Verma, S.; Parashar, V. Securing Internet of Things in 5G Using Audio Steganography. In Proceedings of the International Conference on Smart Trends for Information Technology and Computer Communications, Jaipur, India, 6–7 August 2016; pp. 365–372. [Google Scholar]
- Banik, B.G.; Bandyopadhyay, B.; Kumar, S. Novel Text Steganography Using Natural Language Processing and Part-of-Speech Tagging. IETE J. Res. 2020, 66, 384–395. [Google Scholar] [CrossRef]
- Arya, A.; Soni, S. A literature review on various recent steganography techniques. Int. J. Future Revolut. Comput. Sci. Commun. Eng. 2018, 4, 143–149. [Google Scholar]
- Vijayakumar, P.; Vijayalakshmi, V.; Rajashree, R. Increased level of security using DNA steganography. Int. J. Adv. Intell. Paradig. 2018, 10, 74–82. [Google Scholar] [CrossRef]
- Malathi, P.; Manoaj, M.; Manoj, R.; Raghavan, V.; Vinodhini, R.E. Highly improved DNA based steganography. Procedia Comput. Sci. 2017, 115, 651–659. [Google Scholar]
- Yang, Z.-L.; Guo, X.-Q.; Chen, Z.-M.; Huang, Y.-F.; Zhang, Y.-J. RNN-Stega: Linguistic Steganography Based on Recurrent Neural Networks. IEEE Trans. Inf. Forens. Secur. 2019, 14, 1280–1295. [Google Scholar] [CrossRef]
- Hamdan, A.M.; Hamarsheh, A. AH4S: An algorithm of text in text steganography using the structure of omega network. Secur. Commun. Netw. 2016, 9, 6004–6016. [Google Scholar] [CrossRef]
- Dulera, S.; Jinwala, D.; Dasgupta, A. Experimenting with the Novel Approaches in Text Steganography. Int. J. Netw. Secur. Appl. 2012, 3, 213–225. [Google Scholar] [CrossRef]
- Gaur, M.; Sharma, M. A New PDAC (Parallel Encryption with Digit Arithmetic of Cover Text) Based Text Steganography Approach for Cloud Data Security. Int. J. Recent Innov. Trends Comput. Commun. 2015, 3, 1344–1352. [Google Scholar] [CrossRef]
- Wilson, A.; Blunsom, P.; Ker, A.D. Linguistic steganography on Twitter: Hierarchical language modeling with manual interaction. Media Watermarking Secur. Forens. 2014, 9028. [Google Scholar] [CrossRef]
- Odeh, A.; Elleithy, K.; Faezipour, M. Steganography in Text by Using MS Word Symbols. In Proceedings of the Conference of the American Society for Engineering Education, Bridgeport, CT, USA, 3–5 April 2014; pp. 1–5. [Google Scholar]
- Rafat, K.F. Enhanced Text Steganography in SMS. In Proceedings of the 2009 2nd International Conference on Computer, Control and Communication, Karachi, Pakistan, 17–18 February 2009; Institute of Electrical and Electronics Engineers (IEEE): Piscataway, NJ, USA, 2009; pp. 1–6. [Google Scholar]
- Bhat, D.; Krithi, V.; Manjunath, K.N.; Prabhu, S.; Renuka, A. Information Hiding through Dynamic Text Steganography and Cryptography: Computing and Informatics. In Proceedings of the 2017 International Conference on Advances in Computing, Communications and Informatics (ICACCI), Manipal, India, 13–16 September 2017; Institute of Electrical and Electronics Engineers (IEEE): Piscataway, NJ, USA, 2017; pp. 1826–1831. [Google Scholar]
- Naqvi, N.; Abbasi, A.T.; Hussain, R.; Khan, M.A.; Ahmad, B. Multilayer Partially Homomorphic Encryption Text Steganography (MLPHE-TS): A Zero Steganography Approach. Wirel. Pers. Commun. 2018, 103, 1563–1585. [Google Scholar] [CrossRef]
- Low, S.H.; Maxemchuk, N.F.; Brassil, J.T.; ✗’Gorman, L. Document Marking and Identification Using both Line and Word Shifting. In Proceedings of the INFOCOM’95, Boston, MA, USA, 2–6 April 1995; Institute of Electrical and Electronics Engineers (IEEE): Piscataway, NJ, USA, 2002; pp. 853–860. [Google Scholar]
- Huang, D.; Yan, H. Interword distance changes represented by sine waves for watermarking text images. IEEE Trans. Circuits Syst. Video Technol. 2001, 11, 1237–1245. [Google Scholar] [CrossRef]
- Yang, H.; Kot, A.C. Text Document Authentication by Integrating Inter Character and Word Spaces Watermarking. In Proceedings of the 2004 IEEE International Conference on Multimedia and Expo (ICME), Taipei, Taiwan, 27–30 June 2004; IEEE: Piscataway, NJ, USA, 2004; pp. 955–958. [Google Scholar] [CrossRef]
- Roy, S.; Manasmita, M. A novel approach to format-based text steganography. In Proceedings of the 2011 International Conference on Communication, Computing & Security ICCCS’11, Rourkela, India, 12–14 February; Association for Computing Machinery (ACM): New York, USA, 2011; pp. 511–516. [Google Scholar]
- Kumar, P.; Sharma, V.K. Information Security Based on Steganography & Cryptography Techniques: A Review. Int. J. Adv. Res. Comput. Sci. Softw. Eng. 2014, 4, 246–250. [Google Scholar]
- Mahato, S.; Yadav, D.K.; Khan, D.A. A Modified Approach to Text Steganography Using HyperText Markup Language. In Proceedings of the 2013 Third International Conference on Advanced Computing and Communication Technologies (ACCT), Rohtak, India, 6–7 April 2013; IEEE: Piscataway, NJ, USA, 2013; pp. 40–44. [Google Scholar]
- Bhattacharyya, S.; Indu, P.; Dutta, S.; Biswas, A.; Sanyal, G. Hiding Data in Text Through Changing in Alphabet Letter Patterns (CALP). J. Glob. Res. Comput. Sci. 2011, 2, 33–39. [Google Scholar]
- Sui, X.-G.; Luo, H. A new steganography method based on hypertext. In Proceedings of the 2004 Asia-Pacific Radio Science Conference, Qingdao, China, 24–27 August 2004; pp. 181–184. [Google Scholar] [CrossRef]
- Stutsman, R.; Grothoff, C.; Atallah, M.; Grothoff, K. Lost in just the translation. In Proceedings of the 2006 ACM Symposium on Applied Computing (SAC’06), Dijon, France, 23 April 2006; ACM: New York, NY, USA, 2006; pp. 338–345. [Google Scholar]
- Banerjee, I.; Bhattacharyya, S.; Sanyal, G. Novel text steganography through special code generation. In Proceedings of the International Conference on Systemics, Cybernetics and Informatics (ICSCI-2011), Hyderabad, India, 5–8 January 2011. [Google Scholar]
- Odeh, A.; Elleithy, K.M.; Faezipour, M. Text Steganography Using Language Remarks. In Proceedings of the 2013 ASEE Northeast Section Conference, Northfield, VT, USA, 14–16 March 2013. [Google Scholar]
- Kataria, S.; Kumar, T.; Singh, K.; Nehra, M.S. ECR (encryption with cover text and reordering) based text steganography. In Proceedings of the 2013 IEEE Second International Conference on Image Information Processing (ICIIP-2013), Waknaghat, India, 9–11 December 2013; Institute of Electrical and Electronics Engineers (IEEE): Piscataway, NJ, USA, 2013; pp. 612–616. [Google Scholar]
- Ramakrishnan, B.K.; Thandra, P.K.; Srinivasula, A.V.S.M. Text steganography: A novel character-level embedding algorithm using font attribute. Secur. Commun. Netw. 2016, 9, 6066–6079. [Google Scholar] [CrossRef]
- Shiu, H.-J.; Lin, B.-S.; Huang, P.-Y.; Huang, C.-H.; Lei, C.-L. Data hiding on social media communications using text steganography. In Risks and Security of Internet and Systems; Springer: 2018; Volume 10694, pp. 217–224. In Risks and Security of Internet and Systems; Springer: Berlin/Heidelberg, Germany, 2018; Volume 10694, pp. 217–224. [Google Scholar]
- Zhang, W.Z.; Zeng, Z.Z.; Pu, G.P.; Zhu, Z.H. Chinese Text Watermarking Based on Occlusive Components. In Proceedings of the 2006 2nd International Conference on Information & Communication Technologies, Damascus, Syria, 24–28 April 2006; pp. 1850–1854. [Google Scholar]
- Changder, S.; Debnath, N.C.; Ghosh, D. A New Approach to Hindi Text Steganography by Shifting Matra. In Proceedings of the 2009 International Conference on Advances in Recent Technologies in Communication and Computing, Kottayam, India, 27–28 October 2009; Institute of Electrical and Electronics Engineers (IEEE): Piscataway, NJ, USA, 2009; pp. 199–202. [Google Scholar]
- Alla, K.; Prasad, R.S.R. An Evolution of Hindi Text Steganography. In Proceedings of the 2009 Sixth International Conference on Information Technology: New Generations, Las Vegas, NV, USA, 27–29 April 2009; Institute of Electrical and Electronics Engineers (IEEE): Piscataway, NJ, USA, 2009; pp. 1577–1578. [Google Scholar]
- Changder, S.; Ghosh, D.; Debnath, N.C. LCS based text steganography through Indian Languages. In Proceedings of the 2010 3rd International Conference on Computer Science and Information Technology, ICCSIT 2010, Chengdu, China, 9–11 July 2010; pp. 53–57. [Google Scholar]
- Pathak, M. A new approach for text steganography using Hindi numerical code. Int. J. Comput. Appl. 2010, 1, 199–202. [Google Scholar]
- Changder, S.; Debnath, N.C.; Ghosh, D. A Greedy Approach to Text Steganography Using Properties of Sentences. In Proceedings of the 2011 Eighth International Conference on Information Technology: New Generations, Las Vegas, NV, USA, 11–13 April 2011; Institute of Electrical and Electronics Engineers (IEEE): Piscataway, NJ, USA, 2011; pp. 30–35. [Google Scholar]
- Alam, M.N.; Naser, M.A. Re-evaluating chain-code as features for Bangla script. In Proceedings of the 2013 International Conference on Electrical Information and Communication Technology (EICT), Khulna, Bangladesh, 13–15 February 2014; pp. 1–5. [Google Scholar]
- Khan, S.; Abhijitha, B.; Sankineni, R.; Sunil, B.; Sungkrityayan, K. Polish text steganography method using letter points and extension. In Proceedings of the 2015 IEEE International Conference on Electrical, Computer and Communication Technologies (ICECCT), Tamil Nadu, India, 5–7 March 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 1–5. [Google Scholar]
- Samphaiboon, N.; Dailey, M.N. Steganography in Thai text. In Proceedings of the 2008 5th International Conference on Electrical Engineering/Electronics, Computer, Telecommunications and Information Technology, Krabi, Thailand, 14–17 May 2008; Institute of Electrical and Electronics Engineers (IEEE): Piscataway, NJ, USA, 2008; Volume 1, pp. 133–136. [Google Scholar]
- Khan, S.; Sankineni, R.; Balagurunathan, P.; Shree, N.S.D.; Balasubramanian, A. Czech Text Steganography Method by Selective Hiding Technique. In Proceedings of the World Congress on Engineering, London, UK, 1–3 July 2015. [Google Scholar]
- Elnagar, A.; Al-Debsi, R.; Einea, O. Arabic text classification using deep learning models. Inf. Process. Manag. 2020, 57, 102121. [Google Scholar] [CrossRef]
- Soufan, A. Deep Learning for Sentiment Analysis of Arabic Text. In Proceedings of the ArabWIC 6th Annual International Conference Research Track on ArabWIC 2019, Rabat, Morocco, 7 March 2019; ACM: New York, NY, USA, 2019; pp. 1–8. [Google Scholar]
- Guellil, I.; Saâdane, H.; Azouaou, F.; Gueni, B.; Nouvel, D. Arabic natural language processing: An overview. J. King Saud. Univ. Comput. Inf. Sci. 2019, 33. [Google Scholar] [CrossRef]
- Eldos, T. Arabic Text Data Mining: A Root-Based Hierarchical Indexing Model. Int. J. Model. Simul. 2003, 23, 158–166. [Google Scholar] [CrossRef]
- Al-Salemi, B.; Ayob, M.; Kendall, G.; Noah, S.A.M. Multi-label Arabic text categorization: A benchmark and baseline comparison of multi-label learning algorithms. Inf. Process. Manag. 2019, 56, 212–227. [Google Scholar] [CrossRef]
- Odeh, A.; Elleithy, K.; Faezipour, M. Steganography in Arabic text using Kashida variation algorithm (KVA). In Proceedings of the 2013 IEEE Long Island Systems, Applications and Technology Conference (LISAT), Farmingdale, NY, USA, 3 May 2013; Institute of Electrical and Electronics Engineers (IEEE): Piscataway, NJ, USA, 2013; pp. 1–6. [Google Scholar]
- Shaker, A.A.; Ridzuan, F.; Pitchay, S.A. Text Steganography using Extensions Kashida based on the Moon and Sun Letters Concept. Int. J. Adv. Comput. Sci. Appl. 2017, 8, 286–290. [Google Scholar]
- Shirali-Shahreza, M.H.; Shirali-Shahreza, M. A New Approach to Persian/Arabic Text Steganography. In Proceedings of the 5th IEEE/ACIS International Conference on Computer and Information Science and 1st IEEE/ACIS International Workshop on Component-Based Software Engineering, Software Architecture and Reuse (ICIS-COMSAR’06), Honolulu, HI, USA, 10–12 July; pp. 310–315.
- Odeh, A.; Alzubi, A.; Hani, Q.B.; Elleithy, K. Steganography by multipoint Arabic letters. In Proceedings of the 2012 IEEE Long Island Systems, Applications and Technology Conference (LISAT), Farmingdale, NY, USA, 4 May 2012; pp. 1–7. [Google Scholar]
- Al-Haidari, F.; Gutub, A.; Al-Kahsah, K.; Hamodi, J.; Hamodi, J.M. Improving security and capacity for Arabic text steganography using Kashida extensions. In Proceedings of the 2009 IEEE/ACS International Conference on Computer Systems and Applications, Rabat, Morocco, 10–13 May 2009; Institute of Electrical and Electronics Engineers (IEEE): Piscataway, NJ, USA, 2009; pp. 396–399. [Google Scholar]
- Kadhem, S.M.; Wameedh, D. Proposed Arabic Text Steganography Method Based on New Coding Technique. Int. J. Eng. Res. Appl. 2016, 6, 38–46. [Google Scholar]
- Aabed, M.A.; Awaideh, S.M.; Elshafei, A.-R.M.; Gutub, A.A. Arabic Diacritics based Steganography. In Proceedings of the 2007 IEEE International Conference on Signal Processing and Communications, Dubai, United Arab Emirates, 24–27 November 2007; pp. 756–759. [Google Scholar]
- Gutub, A.; Elarian, Y.; Awaideh, S.; Alvi, A. Arabic text steganography using multiple diacritics. In Proceedings of the WoSPA 2008 International Workshop on Signal Processing and its Applications, Sharjah, United Arab Emirates, 18–20 March 2008. [Google Scholar]
- Gutub, A.; Ghouti, L.; Elarian, Y.; Awaideh, S.; Alvi, A. Utilizing diacritic marks for Arabic text steganography. Kuwait J. Sci. Eng. 2010, 37, 89–109. [Google Scholar]
- Shakir, A.C.; Xuemai, G.; Min, J. Chinese Language Steganography using the Arabic Diacritics as a Covered Media. Int. J. Comput. Appl. 2010, 11, 43–46. [Google Scholar] [CrossRef]
- Bensaad, M.L.; Yagoubi, M.B. High capacity diacritics-based method for information hiding in Arabic text. In Proceedings of the 2011 International Conference on Innovations in Information Technology, Abu Dhabi, United Arab Emirates, 25–27 April 2011; Institute of Electrical and Electronics Engineers (IEEE): Piscataway, NJ, USA, 2011; pp. 433–436. [Google Scholar]
- Memon, M.S.; Shah, A. A Novel Text Steganography Technique to Arabic Language Using Reverse Fatha (الفتحة). Pak. J. Eng. Technol. Sci. 2011, 1, 106–113. [Google Scholar]
- Odeh, A.; Elleithy, K.M. Steganography in Arabic Text Using Full Diacritics Text. In Proceedings of the International Society for Computers and Their Applications, Inc., Bridgeport, CT, USA, 14 November 2012. [Google Scholar]
- Bensaad, M.L.; Yagoubi, M.B. Boosting the Capacity of Diacritics-Based Methods for Information Hiding in Arabic Text. Arab. J. Sci. Eng. 2013, 38, 2035–2041. [Google Scholar] [CrossRef]
- Ahmadoh, E.M.; Gutub, A.A.-A. Utilization of Two Diacritics for Arabic Text Steganography to Enhance Performance. Lect. Notes Inf. Theory 2015, 3. [Google Scholar] [CrossRef]
- Malalla, S.; Shareef, F.R. A New Modified Fatha Method for Arabic Text Steganography Hybrid with Aes Encryption. IOSR J. Comput. Eng. 2016, 18, 37–45. [Google Scholar] [CrossRef]
- Azmi, A.; Alsaiari, A. Arabic typography: A survey. Int. J. Electr. Comput. Sci. 2010, 9, 16–22. [Google Scholar]
- Gutub, A.; Fattani, M. A Novel Arabic Text Steganography Method Using Letter Points and Extensions. In Proceedings of the International Conference on Computer, Information and Systems Science and Engineering (ICCISSE), Vienna, Austria, 25–27 May 2007. [Google Scholar]
- Al-Alwani, W.; Mahfooz, A.B.; Gutub, A.A. A Novel Arabic Text Steganography Method Using Extensions; World Academy of Science, Engineering and Technology: Barcelona, Spain, 2007; pp. 502–505. [Google Scholar]
- Al-Nazer, A.; Gutub, A. Exploit Kashida Adding to Arabic e-Text for High Capacity Steganography. In Proceedings of the 2009 Third International Conference on Network and System Security, Golf Coast, QLD, Australia, 19–21 October 2009; Institute of Electrical and Electronics Engineers (IEEE): Piscataway, NJ, USA, 2009; pp. 447–451. [Google Scholar]
- Gutub, A.A.; Al-Nazer, A.A. High Capacity Steganography Tool for Arabic Text Using ‘Kashida’. ISeCure 2010, 2, 107–118. [Google Scholar]
- Alhusban, A.M.; Alnihoud, O. A meliorated kashida-based approach for Arabic text steganography. Int. J. Comput. Sci. Inf. Technol. 2017, 9, 99–112. [Google Scholar] [CrossRef]
- Malalla, S.; Shareef, F.R. Improving Hiding Security of Arabic Text Steganography by Hybrid AES Cryptography and Text Steganography. J. Eng. Res. Appl. 2016, 6, 60–69. [Google Scholar]
- Al-Oun, S.M.; Alnihoud, J.Q.O. An Efficient Approach to Hide Compressed Voice Data in Arabic Text using Kashida and “La”. J. Comput. Sci. 2017, 13, 48–54. [Google Scholar] [CrossRef]
- Shirali-Shahreza, M. Pseudo-space Persian/Arabic text steganography. In Proceedings of the 2008 IEEE Symposium on Computers and Communications, Marrakech, Morocco, 6–9 July 2008; Institute of Electrical and Electronics Engineers (IEEE): Piscataway, NJ, USA, 2008; pp. 864–868. [Google Scholar]
- Shirali-Shahreza, M.; Shirali-Shahreza, M.H. An Improved Version of Persian/Arabic Text Steganography Using “La” Word. In Proceedings of the 2008 6th National Conference on Telecommunication Technologies and 2008 2nd Malaysia Conference on Photonics, Kuala Lampur, Malaysia, 26–28 August 2008; pp. 372–376. [Google Scholar] [CrossRef]
- Shirali-Shahreza, M.; Shirali-Shahreza, S. Persian/Arabic Unicode Text Steganography. In Proceedings of the 2008 The Fourth International Conference on Information Assurance and Security, Napoli, Italy, 8–10 September 2008; Institute of Electrical and Electronics Engineers (IEEE): Piscataway, NJ, USA, 2008; pp. 62–66. [Google Scholar]
- Shirali-Shahreza, M.H.; Shirali-Shahreza, M. Arabic/Persian text steganography utilizing similar letters with different codes. Arab. J. Sci. Eng. 2010, 35, 213–222. [Google Scholar]
- Mohamed, A.A. An improved algorithm for information hiding based on features of Arabic text: A Unicode approach. Egypt. Inform. J. 2014, 15, 79–87. [Google Scholar] [CrossRef]
- Abbasi, A.T.; Naqvi, S.N.S.; Khan, A.; Ahmad, B. Urdu Text Steganography: Utilizing Isolated Letters. In Proceedings of the 13th Australian Information Security Management Conference, Perth, Western Australia, 30 November–2 December 2015; pp. 37–46. [Google Scholar]
- Obeidat, A.A. Arabic Text Steganography Using Unicode of Non-Joined to Right Side Letters. J. Comput. Sci. 2017, 13, 184–191. [Google Scholar] [CrossRef][Green Version]
- Roslan, N.A.; Mahmod, R.; Udzir, N.I. Sharp-edges Method in Arabic Text Steganography. J. Theor. Appl. Inf. Technol. 2011, 33, 32–41. [Google Scholar]
- Mersal, S.; Alhazmi, S.; Alamoudi, R.; Almuzaini, N. Arabic Text Steganography in Smartphone. Int. J. Comput. Inf. Technol. 2014, 3, 2279–2764. [Google Scholar]
- Roslan, N.A.; Mahmod, R.; Udzir, N.I.; Zurkarnain, Z.A. Primitive Structural Method for High Capacity Text Steganography. J. Theor. Appl. Inf. Technol. 2014, 67, 373–383. [Google Scholar]
- Khan, E. Using Arabic Poetry System for Steganography. Asian J. Comput. Sci. Inf. Technol. 2014, 4, 55–61. [Google Scholar] [CrossRef]
- Al-Nofaie, S.M.; Fattani, M.M.; Gutub, A.A. Merging Two Steganography Techniques Adjusted to Improve Arabic Text Data Security. J. Comput. Sci. Comput. Math. 2016, 6, 59–65. [Google Scholar] [CrossRef]
- Kadhem, S.M.; Ali, D.W.M. Proposed Hiding Text in Text Based on RNA for Encoding Secret Information. Iraqi J. Sci. 2017, 58, 562–573. [Google Scholar]
- Malalla, S.; Shareef, F.R. A Novel Approach for Arabic Text Steganography Based on the “BloodGroup” Text Hiding Method. Eng. Technol. Appl. Sci. Res. 2017, 7, 1482–1485. [Google Scholar] [CrossRef]
- Alshahrani, H.M.S.; Weir, G. Hybrid Arabic text steganography. Int. J. Comput. Inf. Technol. 2017, 6, 329–338. [Google Scholar]
- Taha, A.; Hammad, A.S.; Selim, M.M. A high capacity algorithm for information hiding in Arabic text. J. King Saud. Univ. Comput. Inf. Sci. 2020, 32, 658–665. [Google Scholar] [CrossRef]
- Gutub, A.A.; Alaseri, K. Hiding Shares of Counting-Based Secret Sharing via Arabic Text Steganography for Personal Usage. Arab. J. Sci. Eng. 2019, 45, 1–26. [Google Scholar] [CrossRef]
- Alanazi, N.; Khan, E.; Gutub, A. Inclusion of Unicode Standard seamless characters to expand Arabic text steganography for secure individual uses. J. King Saud. Univ. Comput. Inf. Sci. 2020, (in press). [CrossRef]
- Aman, M.; Khan, A.; Ahmad, B.; Kouser, S. A Hybrid Text Steganography Approach Utilizing Unicode Space Characters and Zero-Width Character. Int. J. Inf. Technol. Secur. 2017, 9, 85–100. [Google Scholar]
- Ahvanooey, M.T.; Li, Q.; Hou, J.; Mazraeh, H.D.; Zhang, J. AITSteg: An Innovative Text Steganography Technique for Hidden Transmission of Text Message via Social Media. IEEE Access 2018, 6, 65981–65995. [Google Scholar] [CrossRef]
- Malik, A.; Sikka, G.; Verma, H.K. A high capacity text steganography scheme based on Huffman compression and color coding. J. Inf. Optim. Sci. 2017, 38, 647–664. [Google Scholar] [CrossRef]
- Al-Azzawi, A.F. A Multi-Layer Hybrid Text Steganography for Secret Communication Using Word Tagging and RGB Color Coding. Int. J. Netw. Secur. Its Appl. 2018, 10, 01–12. [Google Scholar] [CrossRef]
- Altaay, A.A.J.; Sahib, S.B.; Zamani, M. An Introduction to Image Steganography Techniques. In Proceedings of the 2012 International Conference on Advanced Computer Science Applications and Technologies (ACSAT), Kuala Lumpur, Malaysia, 26–28 November 2012; Institute of Electrical and Electronics Engineers (IEEE): Piscataway, NJ, USA, 2012; pp. 122–126. [Google Scholar]
- Cox, I.; Miller, M.L.; Bloom, J.; Fridrich, J.; Kalker, T. Digital Watermarking and Steganography, 2nd ed.; Morgan Kaufmann Publishers: Burlington, MA, USA, 2007. [Google Scholar]
- Korzhik, V.; Fedyanin, I.; Cuong, N.D. Detection of stegosystems using block ciphers for encryption of the embedded messages. In Proceedings of the 2017 20th Conference of Open Innovations Association (FRUCT), Saint Petersburg, Russia, 3–7 April 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 181–186. [Google Scholar]
- Zamani, M.; Manaf, A.B.A.; Ahmad, R.B.; Jaryani, F.; Taherdoost, H.; Zeki, A.M. A Secure Audio Steganography Approach. In Proceedings of the 2009 International Conference for Internet Technology and Secured Transactions (ICITST), London, UK, 9–12 November 2009; Institute of Electrical and Electronics Engineers (IEEE): Piscataway, NJ, USA, 2009; pp. 1–6. [Google Scholar]
- Roslan, N.A.; Udzir, N.I.; Mahmod, R.; Zukarnain, Z.A.; Ninggal, M.I.H.; Thabit, R. Character Property Method for Arabic Text Steganography with Biometric Multifactor Authentication Using Liveness Detection. J. Theor. Appl. Inf. Technol. 2020, 98, 4140–4157. [Google Scholar]
- Morkel, T.; Eloff, J.H.; Olivier, M.S. An overview of image steganography. In Proceedings of the Fifth Annual Information Security South Africa Conference, Sandton, South Africa, 29 June–1 July 2005. [Google Scholar]
- Kouser, S.; Khan, A. A Novel Feature Extraction Approach: Capacity Based Zero-Text Steganography. Int. J. Inf. Technol. Secur. 2017, 3, 85–99. [Google Scholar]
- Zaheer, M. Secure Communication Using Steganography in Image Processing; Air University: Islamabad, Pakistan, 2018. [Google Scholar]
- Ekodeck, S.G.R.; Ndoundam, R. PDF steganography based on Chinese Remainder Theorem. J. Inf. Secur. Appl. 2016, 29, 1–15. [Google Scholar] [CrossRef]
- Afanasyeva, O. Analysis of Aspects of Messages Hiding in Text Environments. J. Konbin 2015, 34, 5–16. [Google Scholar] [CrossRef][Green Version]
- Chao, M.-W.; Lin, C.-H.; Yu, C.-W.; Lee, T.-Y. A High Capacity 3D Steganography Algorithm. IEEE Trans. Vis. Comput. Graph. 2008, 15, 274–284. [Google Scholar] [CrossRef] [PubMed]
- Kour, J.; Verma, D. Steganography techniques–A review paper. Int. J. Emerg. Res. Manag. Technol. 2014, 3, 132–135. [Google Scholar]
- Westfeld, A.; Pfitzmann, A. Attacks on Steganographic Systems. In Proceedings of the 6th European Conference on Computer Vision, ECCV 2000, Dublin, Ireland, 26 June–1 July 2000; pp. 61–76. [Google Scholar]
- Khairullah, M. A novel steganography method using transliteration of Bengali text. J. King Saud. Univ. Comput. Inf. Sci. 2019, 31, 348–366. [Google Scholar] [CrossRef]
- Reinel, T.-S.; Raul, R.-P.; Gustavo, I. Deep Learning Applied to Steganalysis of Digital Images: A Systematic Review. IEEE Access 2019, 7, 68970–68990. [Google Scholar] [CrossRef]
- Jaro, M.A. Advances in record-linkage methodology as applied to matching the 1985 census of Tampa, Florida. J. Am. Stat. Assoc. 1989, 84, 414–420. [Google Scholar] [CrossRef]
- Winkler, W.E. String Comparator Metrics and Enhanced Decision Rules in the Fellegi-Sunter Model of Record Linkage Report; Educational Resources Information Center (ERIC): Washington, DC, USA, 1990; pp. 354–359. [Google Scholar]
- Devi, K.R.; Prabakaran, S. An Enhanced Bilateral Information Security towards a Conventional Cryptographic System using DNA Sequences. Indian J. Sci. Technol. 2016, 9. [Google Scholar] [CrossRef]
- Cheddad, A.; Condell, J.; Curran, K.; Mc Kevitt, P. Digital image steganography: Survey and analysis of current methods. Signal Process. 2010, 90, 727–752. [Google Scholar] [CrossRef]
- Xue, Y.; Zhou, J.; Zeng, H.; Zhong, P.; Wen, J. An adaptive steganographic scheme for H.264/AVC video with distortion optimization. Signal Process. Image Commun. 2019, 76, 22–30. [Google Scholar] [CrossRef]
- Nazari, M.; Ahmadi, I.D. A novel chaotic steganography method with three approaches for color and grayscale images based on FIS and DCT with flexible capacity. Multimed. Tools Appl. 2020, 79, 13693–13724. [Google Scholar] [CrossRef]
- Xiang, L.; Wu, W.; Li, X.; Yang, C. A linguistic steganography based on word indexing compression and candidate selection. Multimed. Tools Appl. 2018, 77, 28969–28989. [Google Scholar] [CrossRef]
- Prabakaran, G.; Bhavani, R.; Rajeswari, P. Multi secure and robustness for medical image based steganography scheme. In Proceedings of the 2013 International Conference on Circuits, Power and Computing Technologies (ICCPCT), Nagercoil, India, 20–21 March 2013; pp. 1188–1193. [Google Scholar]
- Osman, B.B. Message Hiding Technique in Text Steganography using RGB Colour Approach and Random Location. Ph.D. Thesis, Universiti Utara Malaysia, Changlun, Malaysia, 2020. [Google Scholar]
- Xiang, L.; Sun, X.; Luo, G.; Xia, B. Linguistic steganalysis using the features derived from synonym frequency. Multimed. Tools Appl. 2014, 71, 1893–1911. [Google Scholar] [CrossRef]
- Gutub, A.A.; Al-Ghamdi, M. Image Based Steganography to Facilitate Improving Counting-Based Secret Sharing. 3D Res. 2019, 10. [Google Scholar] [CrossRef]
- Hamdani, H.; Ismanto, H.; Munir, A.Q.; Rahmani, B.; Syafrianto, A.; Suprihanto, D.; Septiarini, A. The Proposed Development of Prototype with Secret Messages Model in Whatsapp Chat. Int. J. Electr. Comput. Eng. 2018, 8, 3841–3850. [Google Scholar] [CrossRef]
- Arunkumar, S.; Subramaniyaswamy, V.; Vijayakumar, V.; Chilamkurti, N.; Logesh, R. SVD-based robust image steganographic scheme using RIWT and DCT for secure transmission of medical images. Measurement 2019, 139, 426–437. [Google Scholar] [CrossRef]
- Saravanan, K.; Purusothaman, T.; Velmurugan, T.; Kavitha, K.V.N. Design and Performance Analysis of Diverse Generic Data Hiding Algorithms in Cryptography. ARPN J. Eng. Appl. Sci. 2017, 12, 6423–6429. [Google Scholar]
- Pandya, I.; Jhajj, S.; Pawar, R. A steganographic approach to mitigate password attacks. In Proceedings of the 2017 International Conference on Advances in Computing, Communications and Informatics, ICACCI 2017, Manipal, India, 13–16 September 2017; pp. 248–253. [Google Scholar]
- Liu, J.; Lu, T.; Zhao, Q. Improving the performance of lossless reversible steganography via data sharing. In Proceedings of the IEEE 8th International Conference on Awareness Science and Technology (iCAST 2017), Taichung, Taiwan, 8–10 November 2017; pp. 7–12. [Google Scholar]
- Luo, Z.; Xie, W.; Wang, B.; Tang, Y.; Xing, Q. EasyStego: Robust Steganography Based on Quick-Response Barcodes for Crossing Domains. Symmetry 2019, 11, 222. [Google Scholar] [CrossRef]
- Wijayanto, E.F.; Zarlis, M.; Situmorang, Z. Increase the PSNR of image using LZW and AES algorithm with MLSB on steganography. Int. J. Eng. Technol. 2018, 7, 119–121. [Google Scholar] [CrossRef]
| Year | Reference | Highlights | Scope |
|---|---|---|---|
| 2011 | [15] | Exhibits the performance analysis of the text steganography classes by analyzing the strengths and weaknesses. | Text steganography |
| 2016 | [16] | Classifies text steganography methods into 2 groups based on changes in format and meaning. However, it summarizes the proposed methods without providing comprehensive analysis. | Text steganography |
| 2016 | [17] | Discusses the use of Genetic Algorithm (GA) in text steganography for avoiding suspicion. GA is widely used in image and video steganography compared to text steganography. | GA text steganography |
| 2017 | [18] | Presents a taxonomy of the protection and verifying methods (watermarking, steganography, and cryptography) for integrating the Arabic text using the online Qur’anic content as a case study. | Text preserving and verifying |
| 2017 | [19] | Classifies text steganography methods based on the embedding level into 3 levels: Bit-level, character-level, and mixed-level. | Text steganography |
| 2018 | [20] | This is a comparative study of structural methods in steganography and watermarking that are applied to copyright protection. | Text copyright protection |
| 2018 | [21] | Discusses, in general, the 3 categories in text steganography: Format-based methods, random and statistical generation, and linguistics. | Text steganography |
| 2018 | [22] | Provides the assessment of text steganography methods and discuss the current challenges. | Text steganography |
| 2019 | [4] | Presents an analysis of the security challenges and the pros and cons of structural text hiding methods. | Structural text hiding |
| 2020 | [23] | Addresses steganography methods’ limitations and analyses their performance in each class, such as image, audio, and text video. | Steganography (image, audio, video, and text) |
| 2021 | [24] | Focuses on the comparative analysis of text steganography methods in feature-based category. | Feature-based text steganography |
| Secret Message | Cover Text | Stego Text |
|---|---|---|
| A | “abaca” | “aard aard aard aard aard aard aard aard aard aard aard aard” |
| Secret Message | Cover Text | Stego Text |
|---|---|---|
| Keep the gun under the shed | “Today is the first day of summer which starts with light and cozy sunshine. But eventually the sun becomes scorching and heat goes up. All the rivers and ponds become dried up. People used to wear light clothes and eat less spicy foods. Several summer camps are organized for kids in hilly areas. Trap shooting, swimming, trekking, rock climbing, biking also included as sports. One such popular summer camp is in Shimla. Kids used to leave their belongings and bed beneath the tent. ” | “Today is the first day of summer which starts with light and cozy sunshine. But eventually the sun becomes scorching and heat goes up. All the rivers and ponds become dried up. People used to wear light clothes and eat less spicy foods. Several summer camps are organized for kids in hilly areas. Gun shooting, swimming, trekking, rock climbing, biking also included as sports. One such popular summer camp is in Shimla. Kids used to keep their belongings and bed under the shed.” |
| Secret Message | Cover Text | Stego Text |
|---|---|---|
| 110 | “All birds can fly. This is a bird. Ostrich can also fly.” | “All birds can fly. This is a bird. Ostrich can also fly.” |
| Category | Description |
|---|---|
| Random and Statistical Generation | This method is not based on a specific text. However, the generated text is meaningless and raise suspicions. The computational time is also increased. |
| Linguistic steganography | The invisibility is improved, but the method still suffers from low capacity. Also, searching through a dictionary for a suitable word/letter to match the secret word/letter increases the computational time. |
| Format-based | This method improves invisibility and computational time. Nevertheless, it suffers from low embedding capacity. |
| Language-Based | Characteristics |
|---|---|
| English | Text justification, mark-up language in hypertext, font attributes, substitution, and invisible character are the main characteristics used to hide a secret message in English scripts. Most of these methods can be applied to other languages. |
| Chinese | The main characteristics employed to protect a secret information in Chinese scripts are rearranging the sizes of the rectangular regions’ components in the Chinese alphabets and substitution. This method is language-specific, i.e., it is not applicable to other languages. |
| Indian | Matra, vowels, and substituting are characteristics that have been used to hide the secret message in Indian/Hindi/Bangla scripts. |
| Polish | The dot and extension in the script have been exploited to hide the confidential message. It can be applied to the Polish, Czech, Arabic, Urdu, Jawi, and Persian language. |
| Czech | |
| Thai | The redundancies of alphabet merging with vowel letter and diacritics in Thai scripts used to hide the secret message. This method is not applicable to other languages. |
| Letter | Name of the Letter | Transliteration | Last | Middle | First |
|---|---|---|---|---|---|
| ا | alif | a, u, i,: | ـ ا | ـاـ | اـ |
| ب | ba | b | ـب | ـبـ | بـ |
| ت | ta | t | ـت | ـتـ | تـ |
| ث | tha | th | ـث | ـثـ | ثـ |
| ج | jim | j, g | ـج | ـجـ | جـ |
| ح | ha | h | ـح | ـحـ | حـ |
| خ | kha | kh | ـخ | ـخـ | خـ |
| د | dal | d | ـد | ـدـ | دـ |
| ذ | dhal | dh | ـذ | ـذـ | ذـ |
| ر | ra | r | ـر | ـرـ | رـ |
| ز | za | z | ـز | ـزـ | زـ |
| س | sin | s | ـس | ـسـ | سـ |
| ش | shin | sh | ـش | ـشـ | شـ |
| ص | sad | s | ـص | ـصـ | صـ |
| ض | da | d | ـض | ـضـ | ضـ |
| ط | ta | t | ـط | ـطـ | طـ |
| ظ | dha | dh | ـظ | ـظـ | ظـ |
| ع | 'ain | 'a, 'u, 'i, ' | ـع | ـعـ | عـ |
| غ | ghain | gh | ـغ | ـغـ | غـ |
| ف | fa | f | ـف | ـفـ | فـ |
| ق | qaf | q | ـق | ـقـ | قـ |
| ك | kaf | k | ـك | ـكـ | كـ |
| ل | lam | l | ـل | ـلـ | لـ |
| م | mim | m | ـم | ـمـ | مـ |
| ن | nun | n | ـن | ـنـ | نـ |
| ه | ha | h | ـه | ـهـ | هـ |
| و | wau | w, u | ـو | ـوـ | وـ |
| ي | ya | y, i | ـي | ـيـ | يـ |
| Mon Latter | Sun Latter | ||||||
|---|---|---|---|---|---|---|---|
| 1 | أ | 8 | خ | 1 | ت | 8 | ش |
| 2 | ب | 9 | ف | 2 | ث | 9 | ص |
| 3 | غ | 10 | ع | 3 | د | 10 | ض |
| 4 | ح | 11 | ق | 4 | ذ | 11 | ط |
| 5 | ج | 12 | ي | 5 | ر | 12 | ظ |
| 6 | ك | 13 | م | 6 | ز | 13 | ن |
| 7 | و | 14 | هـ | 7 | س | 14 | ل |
| Authors | Methodology | Pros | Cons |
|---|---|---|---|
| [75] | A pointed character moves its point to conceal “1” and remains untouched to hide “0.” | Improves the robustness by changing the remaining characters randomly. Enhances the capacity by compression. | High computational time. Stego text is fixed for only 1 font type. |
| [76] | A pointed character shifts its point and increases the distance between its dots to hide 2 secret bits in one character. | Converts stego file (text) to image file to overcome the retyping challenge. |
| Authors | Methodology | Pros | Cons |
|---|---|---|---|
| [80] | Multiple embedding scenarios are achieved by changing the font style of diacritics. It considers repeated but invisible diacritics. | Low computational time. Embedding is automated or manual. Improved invisibility. | Stego text is fixed for the use of only 1 font type. |
| [82] | Hides each character in 2 diacritics. | Improved security using RLE. Low computational time. Embedding is automated or manual. Stego file has a flexible format. | |
| [79] | The existence of Fathah hides “1,” and the other diacritics hide “0.” | Low computational time. Embedding is automated or manual. Stego file has a flexible format. | The stego text size is different from the cover text and raises suspicions. |
| [81] | Adds 1 diacritic to hide “1.” | ||
| [83] | Removes the diacritics to hide 0. | ||
| [86] | Removes the diacritic to hide “1” or shows the diacritic when there is a switch between “0” and “1” in a sequence of bits. | ||
| [84] | Reversed Fathah hides “1,” and no change hides “0.” | Embedding is automated or manual. Stego file has a flexible format. | High computational time. |
| [85] | Vertical shifting by 1/200 inches hides “1” and no change hides “0.” | ||
| [87] | Fathah hides “1” on the odd list, and Kasrah hides “1” on the even list. | ||
| [88] | Change the direction of the original Fathah to embed 1 secret bit. | Improved security using AES. |
| Watermarking Bits | 110010 |
|---|---|
| Cover-text |  |
| Output text | 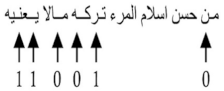 |
| Authors | Methodology | Pros | Cons |
|---|---|---|---|
| [90] | Pointed letters with kashida hide “1.” Unpointed letters with kashida hide “0.” | Embedding is automated or manual. No size increase of stego text. | Limited capacity since all letters cannot be extended. |
| [91] | Uses 1 kashida hide “0” and 2 consecutive kashidas to hide “1.” | Increase in the size of stego file. | |
| [92] | Inserts kashida wherever applicable to hide “1.” | ||
| [77] | Add kashida in a specific location to hide secret numbers. | ||
| [93] | Inserts 1 kashida to hide “0” and 2 consecutive kashidas to hide “1.” | ||
| [74] | Uses 5 scenarios to hide 2 secret bits by inserting kashida after the moon or sun letters. | ||
| [73] | Randomly applies kashida insertion in 4 scenarios to hide a secret bit. | Increases the algorithm complexity and reduces the likelihood of suspicions. | |
| [95] | Uses 4 choices to protect the secret bits based on kashida and dotted letter. | Improves security using AES. Improves the capacity using Gzip. Stego file has a flexible font and format. Low computational time. | |
| [96] | Compresses the secret message then inserts extra kashida after each letter and “La” word to hide “1.” It leaves the letter with the original kashida to hide “0.” | Reduces the size of secret bits using Loss-Less compression algorithm. | |
| [94] | Kashida-based insertion in 4 scenarios while considering pointed and unpointed letters for hiding 2 secret bits. | Improves the capacity using 1 character to hide 2 secret bits. | High computational time. |
| Authors | Methodology | Pros | Cons |
|---|---|---|---|
| [97] | Inserts normal space after pseudo space to hide “1.” No insertion hides “0.” | Stego file has a flexible font and format. Low computational time. | Increase the stego file size. |
| [99] | The shape’s code hides “1” and representative letter’s code hides “0.” | Deficient capacity as the limited identical isolate letter between Arabic and Persian. | |
| [100] | The Arabic character « ك» or « ي» hides “1” and the Persian character « ک» or « ی» hides “0.” | Low capacity due to the limited use of « ك» and « ي» | |
| [98] | The special form of the word “La” hides “1” and the normal form hides 0. | Embedding is automated or manual. Stego file has a flexible font and format. Low computational time. | Very low capacity because of the poor existence of La word. |
| [101] | Changes the Unicode of Arabic isolated letter to hide “1” and leaves it unchanged to hide 0. | Improves security using RLE. Stego file has a flexible font and format. Low computational time. | Low capacity due to the limited appearance of Arabic isolated letter. |
| [102] | Hides the secret bits based on Unicode and non-printed characters. | Improves security using RSA. Stego file has a flexible font and format. Low computational time. | Low capacity due to the limited appearance of Urdu isolated letter. |
| [78] | Changes the Unicode of isolated Urdu letter to hide “1” and leaves it unchanged to hide 0. | Improves the security using RLE. Stego file has a flexible font and format. Low computational time. | Limitation in capacity by considering only unpointed letters. |
| [103] | Uses 3 scenarios to hide secret bit by changing the Unicode of the letter. | Stego text size is not changed. | Limitation in capacity by considering only isolated and initial letters. |
| Number of Sharp-Edges | 1 | 2 | 3 | 4 | 5 |
|---|---|---|---|---|---|
| Letter | ف ق ة ه م و | ا ب ت ث ذض ز ي ظ ن ل ط ر دص ى | ع ء ح غ ج خ | س ش ؤ | ك أ ا ى |
| Char | Unicode | Primitive Structural Method Entities | Num. of Potential Hiding Places | ||
|---|---|---|---|---|---|
| Sharp-Edges | Dot(s) | Typographical Proportion | |||
| أ | \U0627 | 2 | 0 | 1 | 3 |
| ب | \U0628 | 2 | 1 | 3 | 6 |
| ت | \U062A | 2 | 2 | 3 | 7 |
| ث | \U062B | 2 | 3 | 3 | 8 |
| ج | \U062C | 3 | 1 | 5 | 9 |
| Authors | Methodology | Pros | Cons |
|---|---|---|---|
| [104] | Each sharp edge in character embeds one bit, “0” or “1.” Generates reference table for secret bit’s place. | High capacity because all characters can hide bits based on their sharp edges. Stego file has a flexible font and format. | Low security as additional security layers are needed to protect the reference table or code sequence. |
| [105] | The number of sharp edges in each character is utilized to protect the same number of secret bits by converting it to decimal. It generates a code sequence of decimal numbers. | ||
| [106] | Each sharp edge, dot, and typographical proportion can hide “0” or “1.” |
| The verse | ﻭﺃﻻ ﺃّ ﺭﻯ ﻏﻳﺭﻱ ﻟﻪ ﺍﻟﺩﻫﺭَ ﻣﺎﻟﻛﺎ | ﻭﻟﻲ ﻭﻁﻥٌ ﺁﻟﻳﺕ ﺃﻻ ﺃﺑﻳﻌَﻪ ُ |
| How it is pronounced | ﻭﺃﻟﻼ ﺃﺭﻯ ﻏﻴﺮﻱ ﻟﻬﺪﺩﻩ ﺭﻣﺎﻟﻜﺎ | ﻭﻟﻲ ﻭ ﻁﻨﻦ ءﺍﻟﻲ ﺕ ﺃﻟﻼ ﺃﺑﻴﻌﻬﻮ |
| The corresponding feet | ﻓﻌﻮﻟﻦ ﻣﻔﺎﻋﻴﻠﻦ ﻓﻌﻮﻟﻦ ﻣﻔﺎﻋﻠﻦ | ﻓﻌﻮﻝ ﻣﻔﺎﻋﻴﻠﻦ ﻓﻌﻮﻟﻦ ﻣﻔﺎﻋﻠﻦ |
| Binary representation | 01011 0101011 01011 011011 | 1011 0101011 01011 011011 |
| Its classification | Al-Taweel meter | |
| Author | Methodology | Pros | Cons |
|---|---|---|---|
| [107] | This method represented the poetry meters into binary representation to hide the secret bits. | Improved the embedding capacity | Only used of Windows-1256 for the encoding. |
| Authors | Methodology | Pros | Cons |
|---|---|---|---|
| [108] | Adds kashida and consecutive whitespace to hide “1” and single normal space to hide “0.” | Slight improved in capacity using whitespace. | Stego file increases by inserting kashida and whitespace. |
| [109] | Hide 1 secret bit by changing the Unicode of the unpointed isolated letter and add diacritics. | Improves security using RNA. Stego file has a flexible font and format. Low computational time. | Used only the unpointed letters. |
| [110] | Different scenario merges kashida and Unicode methods based on blood group behavior. | Improves security using AES. Enhances the capacity by increasing the usable characters and using a compression algorithm (Gzip). | Stego file size increases by inserting kashida. |
| [111] | Inserts kashida or fathah to hide “1”; the rest to hide “0.” | Improves the capacity by increasing the embedding characters. | Stego file size increases by inserting kashida and diacritics. Suspicion is raised because the included diacritics are not in the proper place. |
| [112] | Integrates kashida with 3 small spaces (Thin, Hair and Six-PRE-EM) to hide secret bits. | Inserting kashida and whitespaces are controlled, which enhance the capacity while maintaining invisibility. | Stego file size increases by inserting kashida and whitespace. |
| [113] | Hybrid kashida with secret sharing. | Improves security using secret sharing. | Stego file size increases by inserting kashida. |
| [114] | Multi types of whitespace are combined with kashida. | Improves the capacity by increasing the usable characters. | Stego file size increases by inserting kashida and whitespace. |
| Authors | Capacity | Security | Robustness | Invisibility | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Bits/Location | Compression | Encryption | Sequence Embedding | Insertion/ Deletion | Copy/Paste | Font Format | OCR | Printing | Retyping | Similarity | Ambiguity | |
| [75] | 1 | ✓ | ✗ | ✓ | ✗ | ✗ | ✗ | ✗ | ✓ | ✗ | High | Low |
| [76] | 2 | ✗ | ✗ | ✓ | ✗ | ✗ | ✗ | ✗ | ✓ | ✗ | High | Medium |
| Authors | Capacity | Security | Robustness | Invisibility | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Bits/Location | Compression | Encryption | Sequence Embedding | Insertion/ Deletion | Copy/Paste | Font Format | OCR | Printing | Retyping | Similarity | Ambiguity | |
| [80] | 1 | ✗ | ✗ | ✓ | ✗ | ✓ | ✗ | ✓ | ✓ | ✗ | low | High |
| [82] | 1 | ✗ | ✗ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | low | High |
| [79] | 4 | ✓ | ✗ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | low | high |
| [81] | 4 | ✗ | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | Low | High |
| [83] | 1 | ✗ | ✗ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | High | Medium |
| [86] | 1 | ✗ | ✗ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | low | high |
| [84] | 1 | ✗ | ✗ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | Medium | Medium |
| [85] | 1 | ✗ | ✗ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | ✗ | Medium | High |
| [87] | 1 | ✗ | ✗ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✗ | Medium | Medium |
| [88] | 1 | ✗ | ✓ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | High | Low |
| Authors | Capacity | Security | Robustness | Invisibility | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Bits/Location | Compression | Encryption | Sequence Embedding | Insertion/ eletion | Copy/Paste | Font Format | OCR | Printing | Retyping | Similarity | Ambiguity | |
| [90] | 1 | ✗ | ✗ | ✓ | ✗ | ✗ | ✓ | ✓ | ✓ | ✗ | High | Low |
| [91] | 1 | ✗ | ✗ | ✓ | ✗ | ✗ | ✓ | ✗ | ✗ | ✗ | Low | Medium |
| [92] | 1 | ✗ | ✗ | ✓ | ✗ | ✗ | ✓ | ✗ | ✗ | ✗ | Low | High |
| [77] | 1 | ✗ | ✗ | ✓ | ✗ | ✗ | ✓ | ✗ | ✗ | ✗ | Low | High |
| [93] | 1 | ✗ | ✗ | ✓ | ✗ | ✗ | ✓ | ✗ | ✗ | ✗ | Medium | High |
| [73] | 1 | ✗ | ✗ | ✓ | ✗ | ✗ | ✓ | ✗ | ✗ | ✗ | Medium | High |
| [95] | 1 | ✓ | ✓ | ✓ | ✗ | ✗ | ✓ | ✗ | ✓ | ✗ | Medium | Medium |
| [96] | 1 | ✓ | ✗ | ✓ | ✗ | ✗ | ✓ | ✗ | ✗ | ✗ | Medium | High |
| [74] | 2 | ✗ | ✗ | ✓ | ✗ | ✗ | ✓ | ✗ | ✗ | ✗ | Medium | Medium |
| [94] | 2 | ✗ | ✗ | ✓ | ✗ | ✗ | ✓ | ✓ | ✓ | ✗ | High | Low |
| Authors | Capacity | Security | Robustness | Invisibility | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Bits/Location | Compression | Encryption | Sequence Embedding | Insertion/ Deletion | Copy/Paste | Font Format | OCR | Printing | Retyping | Similarity | Ambiguity | |
| [97] | 1 | ✗ | ✗ | ✓ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | Medium | Low |
| [98] | 1 | ✗ | ✗ | ✓ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | High | Low |
| [99] | 1 | ✗ | ✗ | ✓ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | High | Low |
| [100] | 1 | ✗ | ✗ | ✓ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | Medium | Low |
| [101] | 1 | ✓ | ✗ | ✓ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | High | Low |
| [102] | 1 | ✗ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | High | Low |
| [78] | 1 | ✓ | ✗ | ✓ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | High | Low |
| [103] | 1 | ✗ | ✗ | ✓ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | High | Low |
| Authors | Capacity | Security | Robustness | Invisibility | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Bits/Location | Compression | Encryption | Sequence Embedding | Insertion/ Deletion | Copy/Paste | Font Format | OCR | Printing | Retyping | Similarity | Ambiguity | |
| [104] | 3 | ✗ | ✗ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | High | Low |
| [105] | 6 | ✗ | ✗ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | High | Low |
| [106] | 6 | ✗ | ✗ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | High | Low |
| Authors | Capacity | Security | Robustness | Invisibility | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Bits/Location | Compression | Encryption | Sequence Embedding | Insertion/ Deletion | Copy/Paste | Font Format | OCR | Printing | Retyping | Similarity | Ambiguity | |
| [107] | 3 | ✗ | ✗ | ✓ | ✗ | ✓ | ✓ | ✓ | ✓ | ✓ | High | Low |
| Authors | Capacity | Security | Robustness | Invisibility | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Bits/Location | Compression | Encryption | Sequence Embedding | Insertion/ Deletion | Copy/Paste | Font Format | OCR | Printing | Retyping | Similarity | Ambiguity | |
| [108] | 1 | ✗ | ✗ | ✓ | ✗ | ✓ | ✓ | ✗ | ✗ | ✗ | Medium | Medium |
| [109] | 1 | ✓ | ✗ | ✓ | ✗ | ✓ | ✓ | ✓ | ✗ | ✗ | Low | High |
| [110] | 1 | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✗ | ✗ | low | low |
| [111] | 1 | ✗ | ✗ | ✓ | ✗ | ✓ | ✓ | ✗ | ✗ | ✗ | Low | High |
| [112] | 1 | ✗ | ✗ | ✓ | ✗ | ✓ | ✓ | ✗ | ✗ | ✗ | Medium | High |
| [113] | 1 | ✗ | ✗ | ✓ | ✗ | ✓ | ✓ | ✓ | ✓ | ✓ | Medium | Medium |
| [114] | 1 | ✗ | ✗ | ✓ | ✓ | ✗ | ✗ | ✓ | ✗ | ✗ | ✓ | ✓ |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Thabit, R.; Udzir, N.I.; Yasin, S.M.; Asmawi, A.; Roslan, N.A.; Din, R. A Comparative Analysis of Arabic Text Steganography. Appl. Sci. 2021, 11, 6851. https://doi.org/10.3390/app11156851
Thabit R, Udzir NI, Yasin SM, Asmawi A, Roslan NA, Din R. A Comparative Analysis of Arabic Text Steganography. Applied Sciences. 2021; 11(15):6851. https://doi.org/10.3390/app11156851
Chicago/Turabian StyleThabit, Reema, Nur Izura Udzir, Sharifah Md Yasin, Aziah Asmawi, Nuur Alifah Roslan, and Roshidi Din. 2021. "A Comparative Analysis of Arabic Text Steganography" Applied Sciences 11, no. 15: 6851. https://doi.org/10.3390/app11156851
APA StyleThabit, R., Udzir, N. I., Yasin, S. M., Asmawi, A., Roslan, N. A., & Din, R. (2021). A Comparative Analysis of Arabic Text Steganography. Applied Sciences, 11(15), 6851. https://doi.org/10.3390/app11156851






