1. Introduction
In military wireless communication systems, the bit-error rate (BER) in a receiver is degraded when a transmitted signal is jammed [
1,
2]. Military wireless communications need to mitigate jammers to attain reliability. To reduce jamming, several antijam techniques, such as frequency-hopping spread spectrum (FHSS) and direct-sequence spread spectrum (DSSS), were researched [
3,
4,
5,
6,
7,
8,
9,
10,
11,
12,
13,
14,
15]. When jammer power is large, the FHSS is known to be more effective [
16], but BER degradation remains.
FHSS randomly changes carrier frequency according to time within a transmission-frequency band, which reduces jammer probability for a slot. As a jammer to FHSS, a partial-band noise jammer (PBNJ) was considered in this study [
17,
18]. When jamming occurs, the BER of jammed slots is so large that the receiver may not be able to decode the transmitted information. To overcome the jammer problem, a duplication method was studied where several slots with the same data are transmitted and combined to increase signal-to-jammer-plus-noise ratio (SJNR) [
19]. However, when the jammer was strong, the SJNR was still small. A selective combining method was developed [
19], and the detection of jammed slot methods was also researched [
20,
21]. In FHSS systems, however, multipath channels cause frequency-selective fading, and nonlinear devices at the transmitter also generate an unequal frequency response. Since the unequal frequency response makes the detection of jammed slots difficult, a solution for measuring jammer power on all empty slots and detecting jammed slots was developed [
21]. This full search of all empty slots requires large computational complexity.
To overcome jammer-detection and -mitigation problems, we developed a proposal for a noise-jammer power estimator (NJPE), a jammer detector based on gamma distribution, and a slot combiner for nonjammed slots. The proposed NJPE estimates the pure power of the noise and jammer of each slot regardless of transmitted-symbol existence and unequal frequency response. The probability distribution of the NJPE output was approximated as gamma distribution on the basis of simulations, and the jammer detector based on gamma distribution was developed to precisely detect the jammer. The normalized Cramér–Rao bound (NCRB) of the proposed NJPE was also derived to theoretically prove estimation performance. Computer simulations demonstrated that the normalized mean squared error (NMSE) of the proposed NJPE was well-matched with the derived NCRB, and the detection performance of the jammer detector based on gamma distribution was better than those of conventional jammer detectors. The BER of the proposed method indicated better performance than that of conventional methods.
This paper consists of five sections:
Section 2 discusses how the proposed NJPE works;
Section 3 analyzes how to assess the performance of the proposed NJPE;
Section 4 compares the NCRB of the proposed scheme with NMSE and BER performance using computer simulations; and
Section 5 concludes the paper.
2. Proposed Estimator and Detector
In FHSS systems for military communications, the same data are repeatedly transmitted over several slots and combined in the receiver to mitigate jammers. When jammer power is strong, and jammed slots are not discarded, BER performance degrades. Thus, the detection of jammed slots is important. In FHSS systems, however, frequency-selective fading and unequal frequency responses cause different slot powers and make the detection of jammed slots difficult. In this section, we show the developed NJPE and the jammer detector based on gamma distribution of NJPE. The proposed detector can detect both narrowband and wideband jammers.
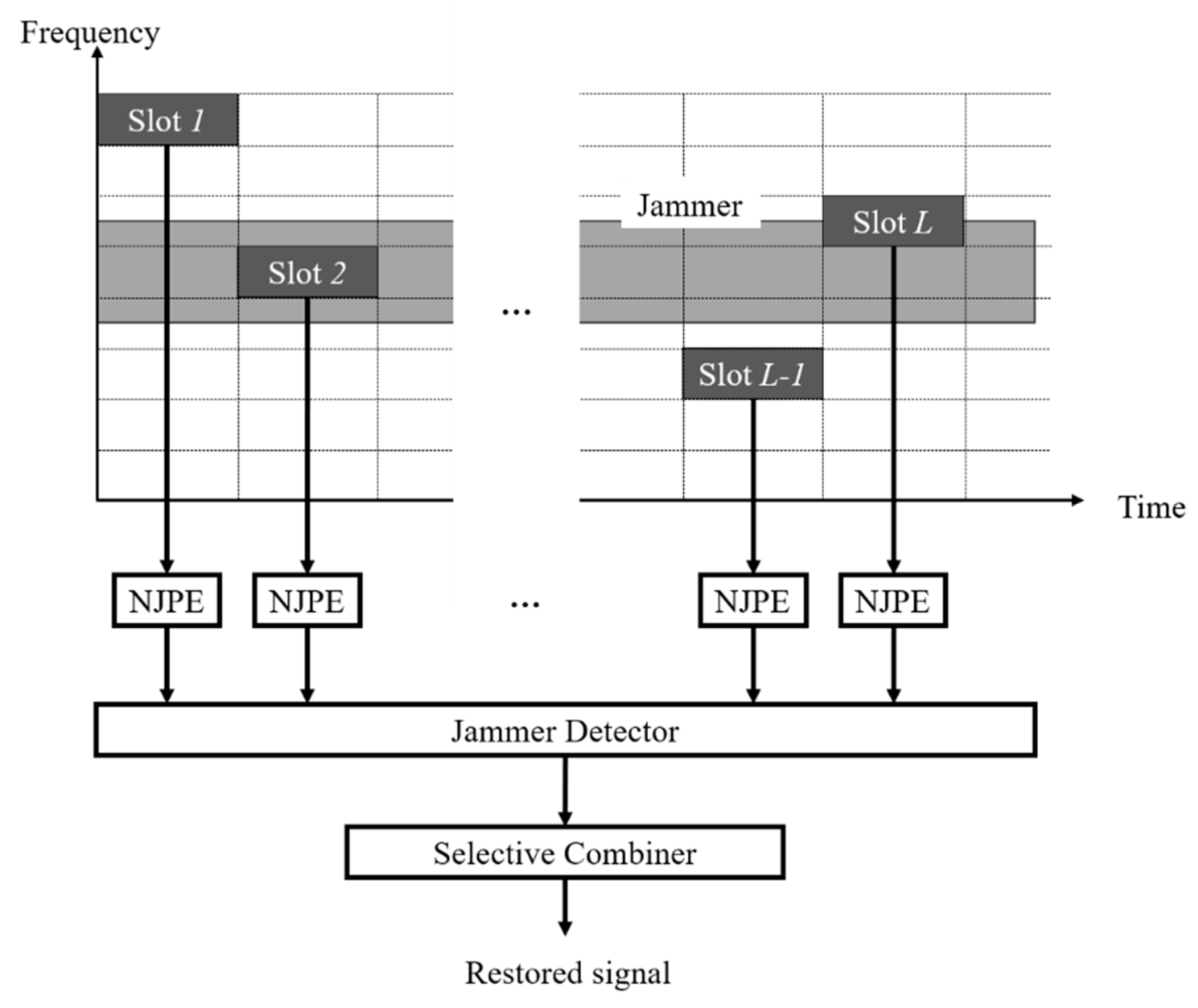
Figure 1 demonstrates the proposed method that detects and discards jammed slots, and combines the remaining slots.
2.1. Noise-Jammer Power Estimator
In order to estimate pure noise-jammer power regardless of transmitted-symbol power, the received symbol was multiplied by its conjugation, and its mean and variance were calculated. With a simple manipulation of mean and variance, the pure noise-jammer power was easily estimated.
Assume that the data of a slot are copied and repeatedly transmitted to
L slots, the received symbol of the
l-th slot is
, and
is the multiplication of
and its conjugation
. Then,
can be written as
where
denotes a channel coefficient of the
l-th slot,
denotes a transmitted symbol of the
l-th slot, and * denotes a complex conjugate.
is uncorrelated to other channel coefficients by frequency-selective fading.
denotes noise with or without jammer on the
l-th slot, which is defined by
where
and
denote pure noise and the jammer on the
l-th slot, respectively.
To develop the proposed NJPE, the mean and variance of
in Equation (1) were calculated. Assume that noise, transmitted symbol, and channel gain are independent. The PBNJ was modeled as zero-mean Gaussian noise [
22,
23]. Therefore, the mean of
was obtained as
where
and
denote the pure noise power and jammer power on the
l-th slot, respectively, and
denotes a symbol power. Next, the variance of
was obtained as
Equation (4) was classified as with- or without-jammer since
had with- or without-jammer cases in Equation (2). In FHSS, the length of each slot was designed to be shorter than coherence time, and channel gain was assumed as constant in a slot. Then, Equation (4) was simplified as
Equations (3) and (5) both have noise, symbol, jammer powers, and channel gain. To estimate the pure noise-jammer power regardless of channel gain,
in Equation (3) needed to be removed.
was calculated by taking the square root of
, which was obtained by subtracting the squared Equation (3) from Equation (5). Then, the proposed NJPE could be derived as
In Equation (6), if a jammer existed, NJPE estimated the sum of pure noise and jammer power; if not, NJPE only estimated pure noise power. Because the noise was generated from a low-noise amplifier (LNA) at the receiver, the noise powers of all slots were similar. Therefore, jammed slots were easily detected by comparing with other slots. The estimation performance of the proposed NJPE is explained in
Section 3.
2.2. Jammer Detector wirh Gamma Distribution
Jammer detectors determine a jammed slot when an estimated noise power of a slot is greater than those of the other slots. A robust jammer-detection method is the constant false-alarm-rate (CFAR) detector, which calculates a threshold obtained from a given false-alarm-rate probability () and compares the threshold with a test sample. The conventional CFAR detector of radar systems assumes that background noise follows Gaussian distribution. However, the output distribution of the proposed NJPE was not Gaussian because of the square and square-root terms in Equation (6).
In this study, we approximated that the NJPE output followed gamma distribution on the basis of simulations, and derived the jammer detector based on gamma distribution. In the experiment section, we demonstrate that the detection performance of the derived jammer detector attained better detection probability than those of conventional Gaussian-distribution-based detectors.
To calculate a relationship between threshold and false-alarm rate
, let an actual and an estimated noise-jammer power be
and
z, respectively. The conditional probability-density function (PDF) of
z given
(
), follows gamma distribution and is given as (see
Appendix A)
where
and
denote
where
N denotes the number of samples, and
denotes a received symbol power of the
l-th slot (
) from Equation (3). Then, a relationship between
and threshold
of the proposed jammer detector is obtained as
where
denotes an upper incomplete gamma function by
Thus, for a given , is calculated by Equation (10), and a jammed slot can be determined.
After detecting all jammed slots, the index set (
) of the combining slots is obtained as
where
denotes the estimated power of the noise and jammer in the
l-th slot from Equation (6). If the only nonjammed slots based on
were combined, a larger signal-to-noise ratio (SNR) and a better BER could be attained.
3. Proposed-Method Analysis
For NJPE, the limited number of symbols in a slot is utilized for calculation, which causes an estimation error. In this section, we derived the NCRB of the proposed NJPE, analyzed the detection performance of the proposed jammer detector, and calculated the detection probability.
The characteristic of the NCRB of the proposed NJPE is described in Lemma 1.
Lemma 1. The estimation error of NJPE is inversely proportional to the number of symbols in a slot. When the SNR is large, the estimation error only depends on the number of symbols.
Proof. Let the estimated noise power of the proposed NJPE be
for actual power
. The variance of
is bounded by Fisher information (
), which is given as [
24]
where
is calculated as (see
Appendix B for detail derivation)
where
N denotes the number of symbols, and
denotes the received symbol power. Thus, the Cramér–Rao bound (CRB) is obtained as
NCRB is defined as
[
25]. NCRB is written as
where
, which is SNR. In Equation (16), NCRB is inversely proportional to
N and is functional of
. When
is large, NCRB becomes
. □
The detection probability (
) of the proposed jammer detector was calculated from threshold
, which was obtained from
. Because the proposed NJPE followed gamma distribution,
needed to be calculated on the basis of the conditional probability of the gamma function in Equation (7). If the jammer existed in the observation slot,
in Equation (7) became the sum of the noise power and jammer power (
). Then,
with threshold
was obtained by an integration over the region greater than
, which was given as
where
and
were defined as in Equations (8) and (9), respectively. Thus, in Equation (17), as
increased and
decreased,
increased. In other words, a larger SNR provided better detection probability. In the next section, we outline the computer simulations that were executed to show the detection performance of the proposed and conventional schemes.
4. Computer Simulations
The validation of gamma approximation and the derived NCRB were verified through computer simulations. The detection probability and the BER of the proposed methods were evaluated alongside conventional schemes. For the validation of gamma approximation, the distribution of the NJPE output was fitted to gamma, normal, and Weibull, and the root mean squared errors (RMSEs) of moments for the three fitted distributions were compared to select best-fit distribution. The derived NCRB was compared with the NMSE of the proposed NJPE. The detection probability of the proposed jammer detector based on gamma distribution was compared with those of the conventional cell average (CA)-CFAR, smallest of (SO)-CFAR, and differential jammer rejection (DJR) [
20,
21]. The BERs of the combining slots without jammed slots were tested alongside conventional methods.
Experiment parameters are shown in
Table 1, where
denotes the ratio of the bandwidths of FHSS system and jammer. A small
indicates a strong and narrowband jammer for the same jammer power.
In order to verify gamma approximation, maximum-likelihood estimation was utilized to fit the distribution of the NJPE output to gamma, normal, and Weibull distributions [
26], and the RMSEs of the
n-th moment from 1 to 4 were compared to select the best-fit distribution.
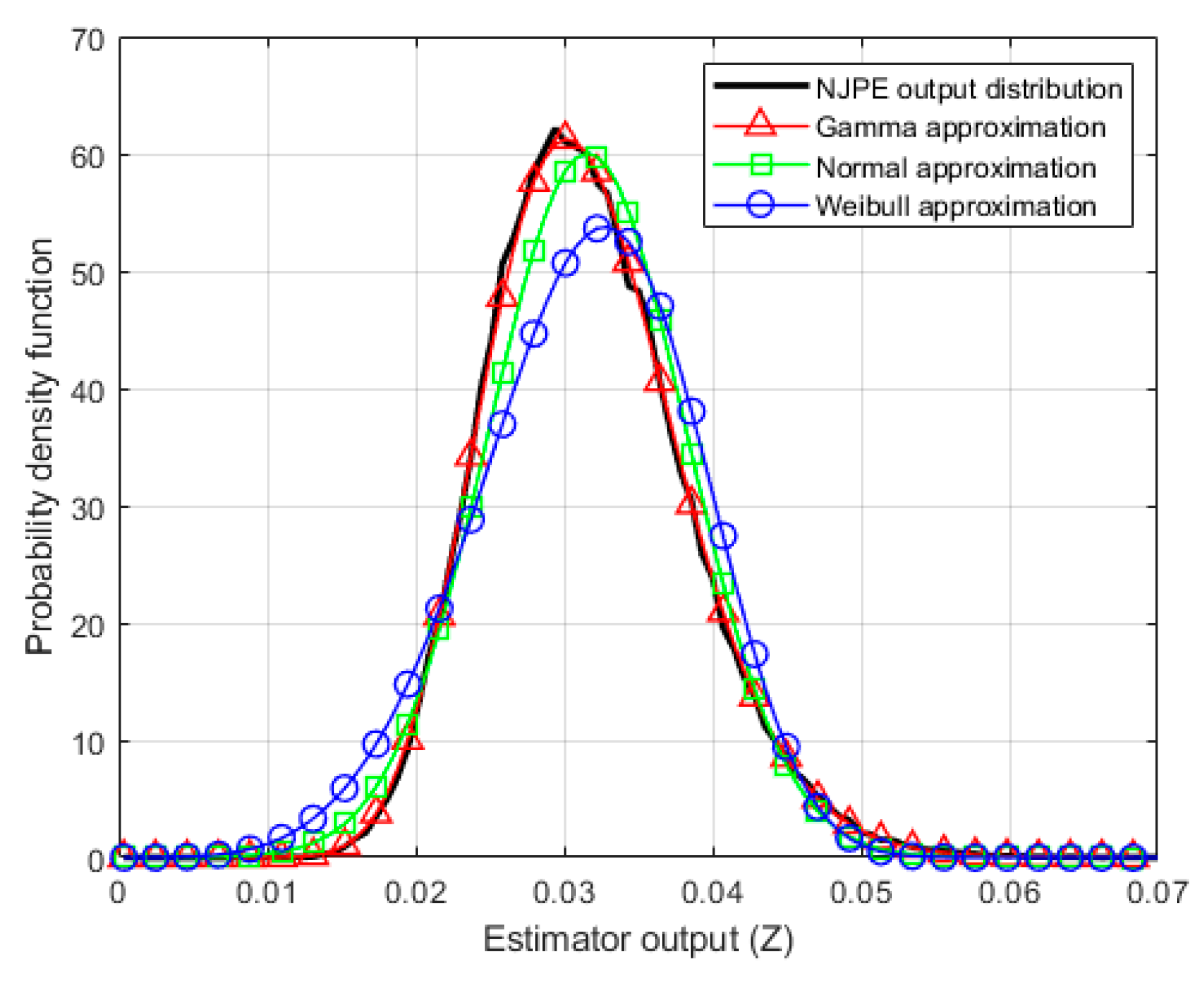
The PDFs of the three fitted distributions and the RMSEs are shown in
Figure 2 and
Table 2, respectively. In
Figure 2, the black solid line denotes the PDF of the output of NJPE. Red-triangle, green-square, and blue-circle lines denote the PDFs of the fitted distributions with gamma, normal, and Weibull, respectively. Gamma distribution was well-matched with the distribution of the NJPE output. In
Table 2,
denotes the
n-th moment, and the gamma distribution displayed the smallest RMSEs from the three fitted distributions.
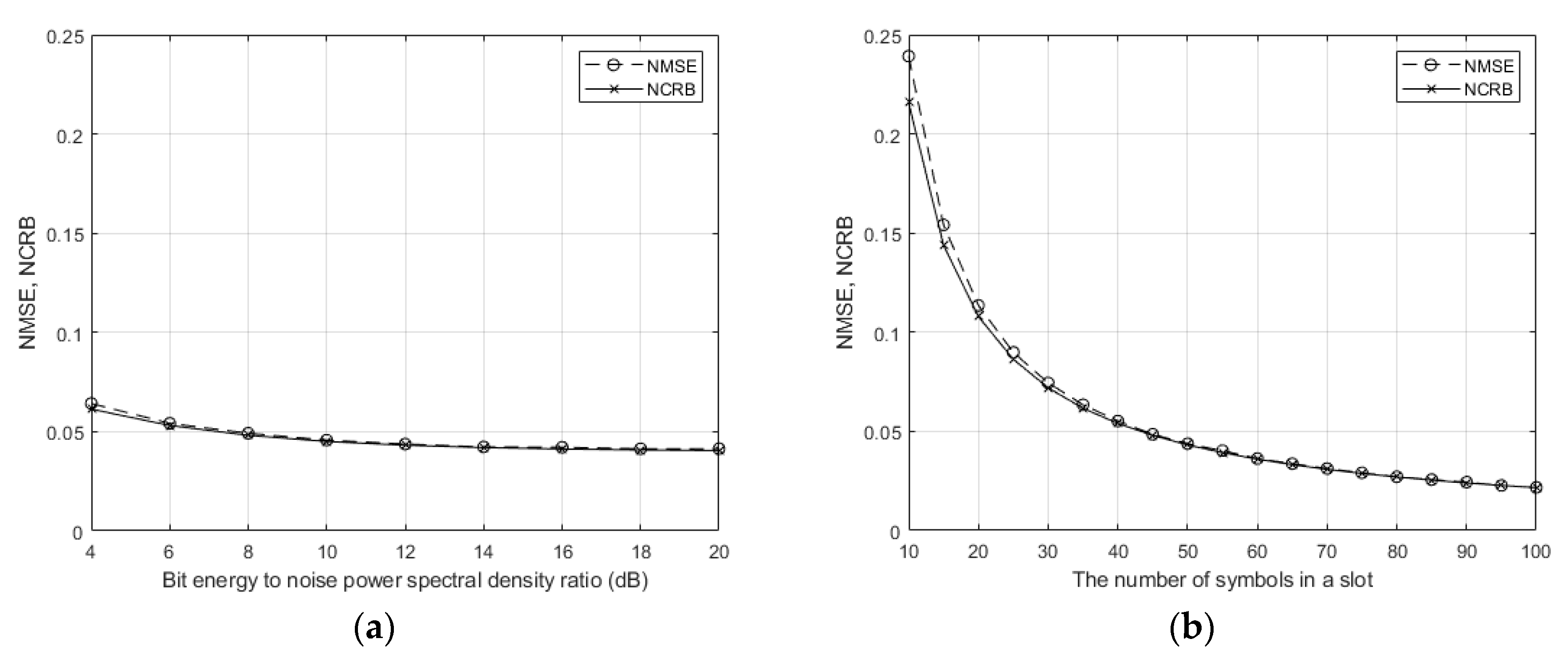
In
Figure 3, the NCRB of the proposed NJPE was compared with the NMSE of the simulated NJPE according to bit-energy-to-noise-power spectral-density ratio (
) with
, and according to
N with
dB. In
Figure 3a, for a large SNR region, NMSE and NCRB converged to 0.04, which was also calculated by
. In
Figure 3b, NMSE and NCRB were inversely proportional to the number of symbols. These results were well-matched with Lemma 1.
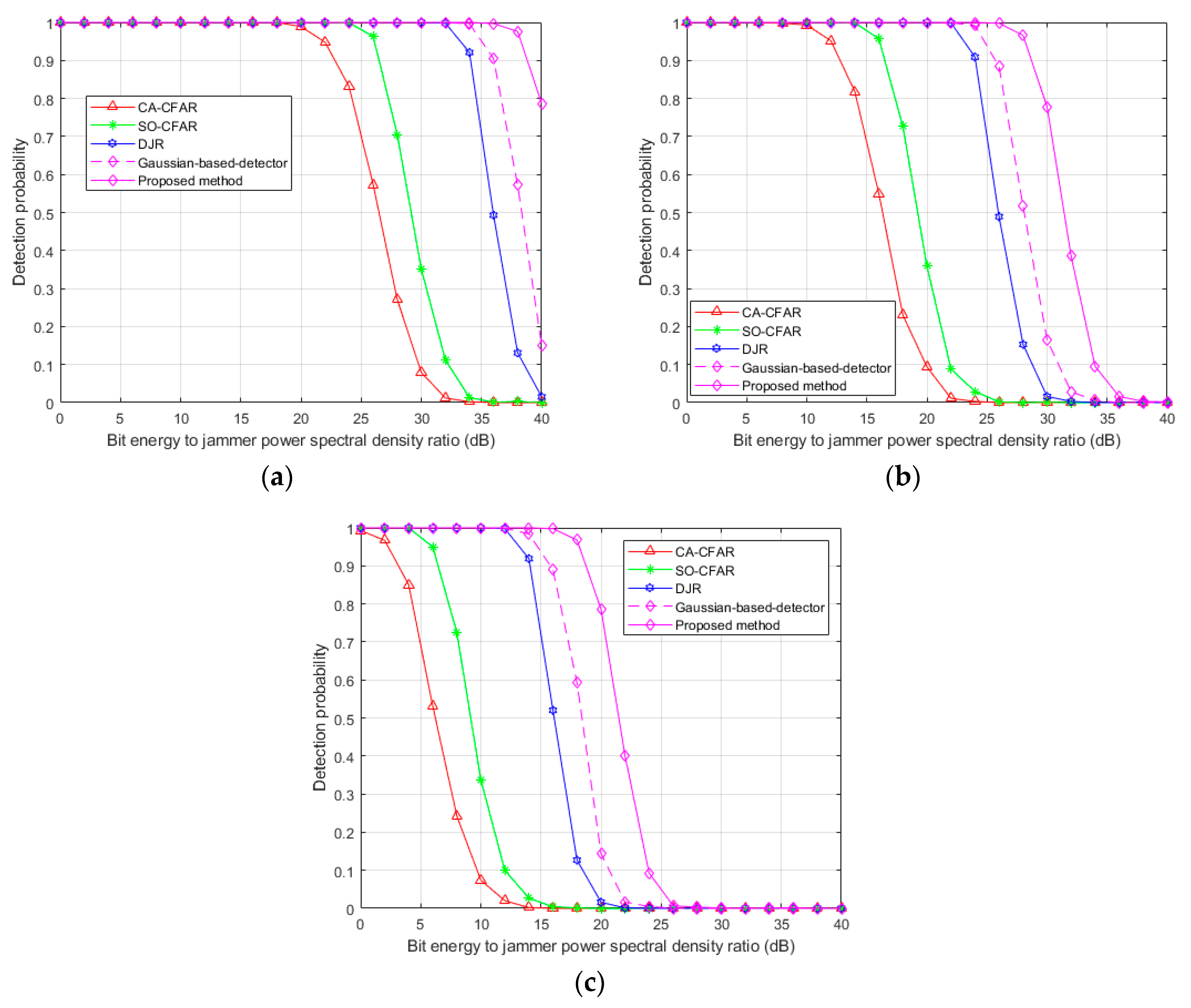
In
Figure 4, the detection probabilities of the proposed jammer detector based on NJPE versus bit-energy-to-jammer-power spectral-density ratio (
) at
are shown for
0.0005, 0.005, and 0.05. The jammer with
0.0005 was a strong and narrowband signal. The red-triangle line denotes CA-CFAR, the green-asterisk line denotes SO-CFAR, the blue-hexagram line denotes DJR, and the magenta-diamond line denotes the proposed detector. The Gaussian-distribution-based detector is also depicted as a dotted-magenta-diamond line for comparison with the proposed gamma-distribution-based detector. When
was small, i.e., large jammer power, the jammer was easily detected, and the detection probability of jammer was close to 1; the inverse was also true. For the same
, a small
in
Figure 4a demonstrates larger detection probability than a large
in
Figure 4c. The proposed method had about 15, 13, and 5 dB detection-probability gain, respectively, compared to the conventional CA-CFAR, SO-CFAR, and DJR. In addition, the proposed gamma-distribution-based detector had about 3 dB better gain than the Gaussian-distribution-based detector.
In
Figure 5, the receiver-operating-characteristic (ROC) curves of the proposed method and the conventional methods were evaluated to show detection probability according to various
. In
Figure 5, the proposed method exhibited greater detection probability than conventional methods at small
regions, and required a smaller
for specific detection probability. As seen in
Figure 4 and
Figure 5, the proposed detector demonstrated the best detection performance.
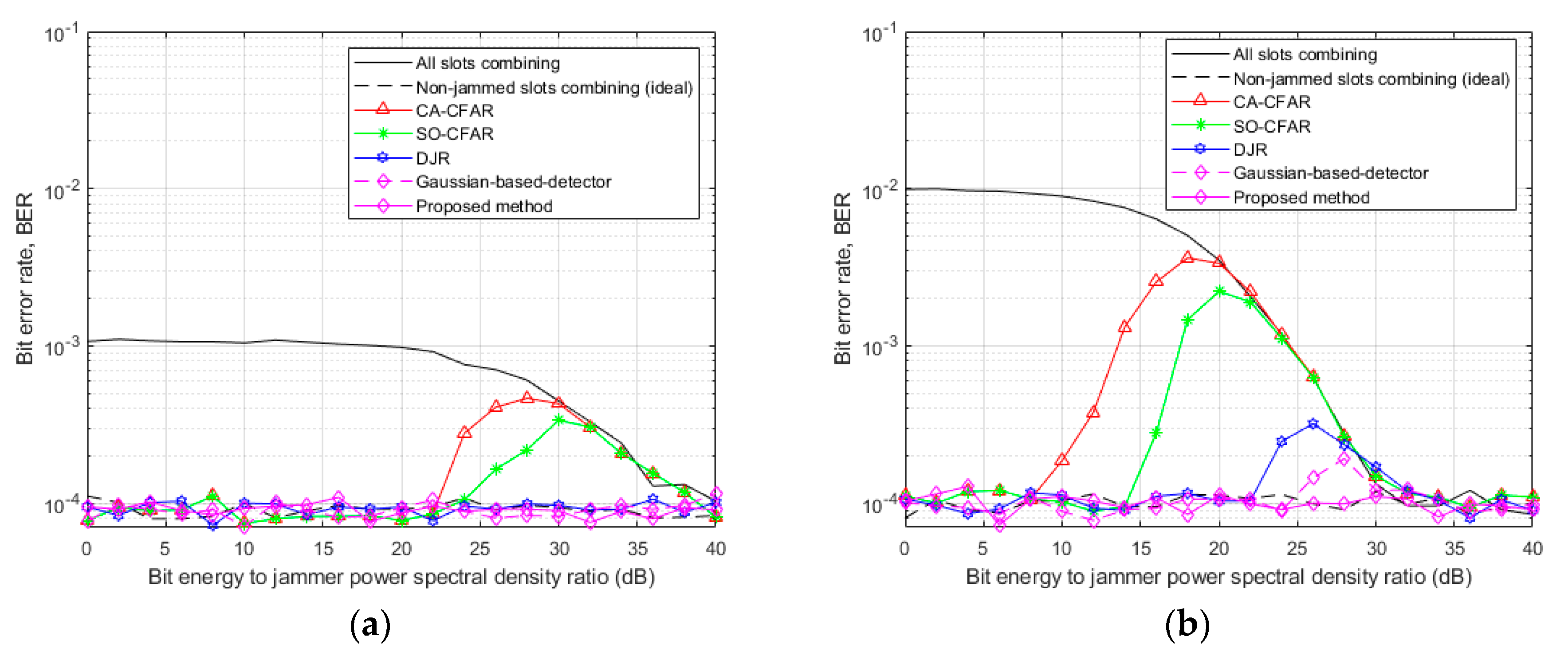
Figure 6 illustrates the BER performance of the combining slots without jammed slots versus
at
for
0.0005, 0.005, and 0.05. The tested detection methods were the same as in
Figure 4. For reference comparison, the BER from combining without- and with-discard of known jammed slots is also plotted with a black solid line and a dashed line, respectively. If perfectly jammed slots were discarded, the BER was about
regardless of
. If not, when
was less than 5 dB, and
was 0.0005, 0.005, and 0.05, the BER from combining all slots increased up to 0.001, 0.009, and 0.07, respectively. These results demonstrated that rejecting jammed slots by the jammer detector was important in increasing BER performance in FHSS systems.
In
Figure 6, the methods ranked by increasing BER performance are CA-CFAR, SO-CFAR, DJR, and the proposed method. This result matched with detection performance in
Figure 4. In
Figure 6b, when
was 0.005 and
varied from 10 to 30 dB, the BER performance of the proposed method was similar to that of perfect jammer detection, while the BER performance of other detectors decreased at the
region. When
was larger than 30 dB, the BER of all schemes encountered an error floor. In this case, even though jammer power was small, BER performance did not increase at all for all cases. As seen in BER comparisons, the proposed method demonstrated the best BER performance.