A Secure Architecture for Modular Division over a Prime Field against Fault Injection Attacks
Abstract
1. Introduction
- This paper extends our work in [40] to present a new secure MD architecture that can not only detect, but also locate, the error.
- Twelve combinations of four word-oriented systolic implementations of MFM and three error-detecting schemes with different LAC values were explored to seek the best tradeoff between area, time overheads, and error detection capability. These combinations were modeled using Verilog language and synthesized using Synopsys Design Complier with the TMSC (Taiwan Semiconductor Manufacturing) 90nm CMOS (Complementary metal-oxide-semiconductor) standard cell library. Their functions were also verified using Modelsim.
- Random fault injections were simulated using the C++ program and the simulation result shows that the proposed architecture can detect single-bit error (SBE) with 100% accuracy and locate the erroneous processing element (PE). The detection capability of single-PE error (multiple-bit error is injected into one PE) and multi-PE error vary with the value of LAC. However, it reaches 99.898% when the number of erroneous processing elements is three or more.
- In addition, the proposed architecture can greatly shorten the delay in error reporting.
2. Preliminaries
2.1. The MD Algorithm
| Algorithm1 Equivalent Description of Modular division algorithm over prime field in [31] |
| Input:, |
| Output: |
| 4: // Modular Division Computation |
| 5: |
| 6: i = i + 1 |
| 7: // Control Element |
| 8: |
| 9: |
| 10: |
| 11: |
| 12: |
| 13: //Compute Iteration Output |
| 14: |
| 15: end for |
| 16: end while |
| 17: |
| 18: |
| 19: Return R |
2.2. The Linear Arithmetic Code (LAC)
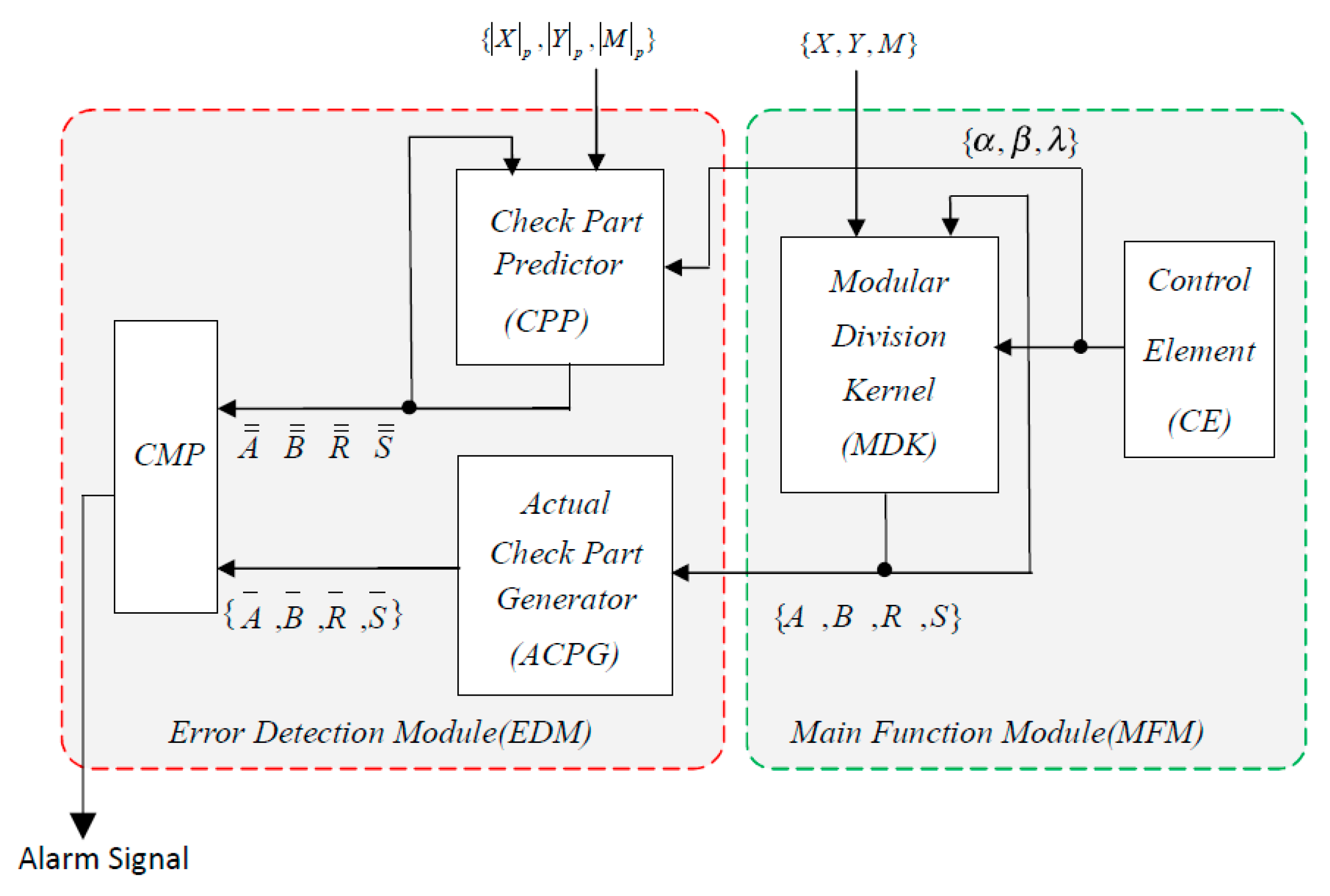
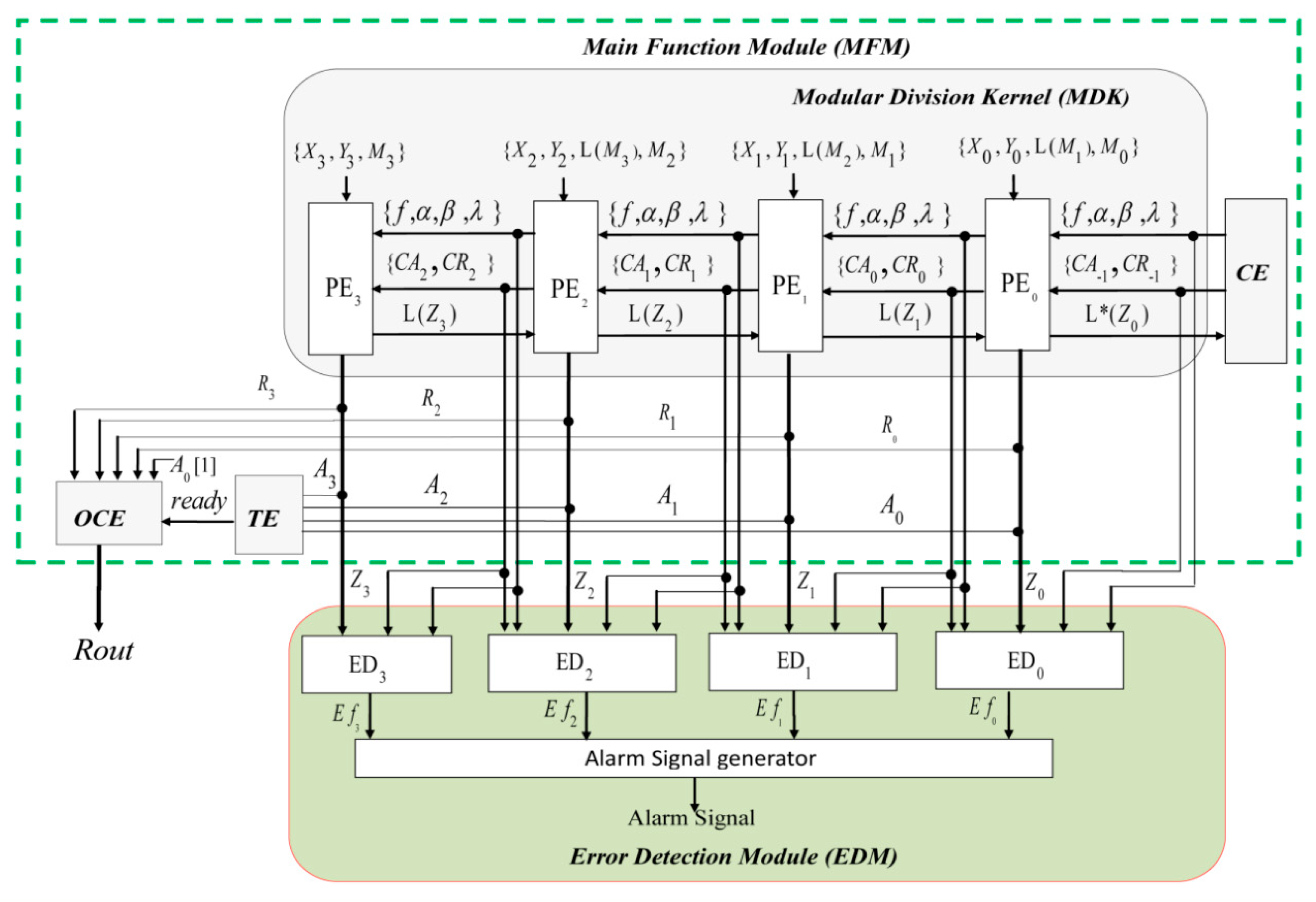
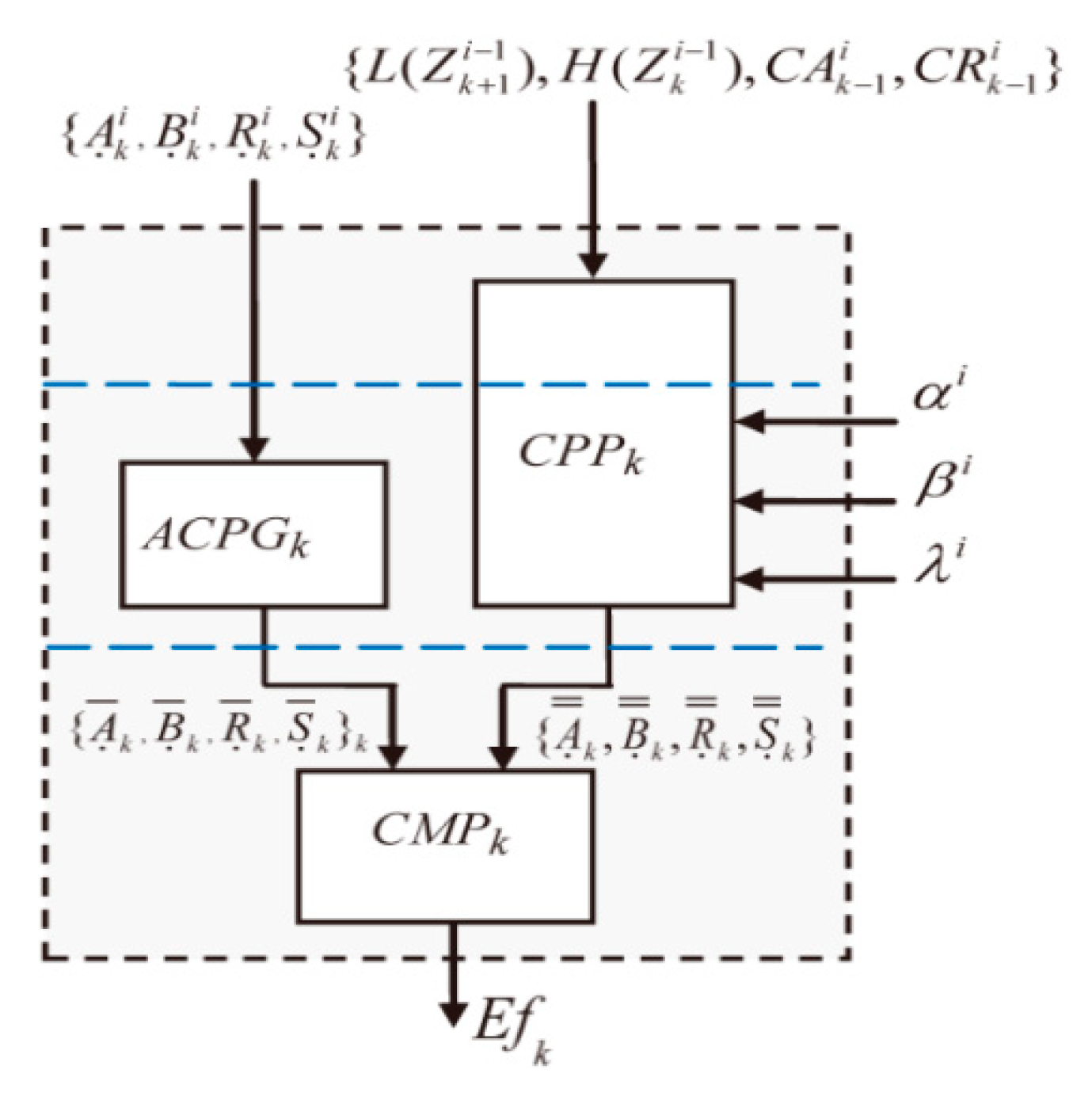
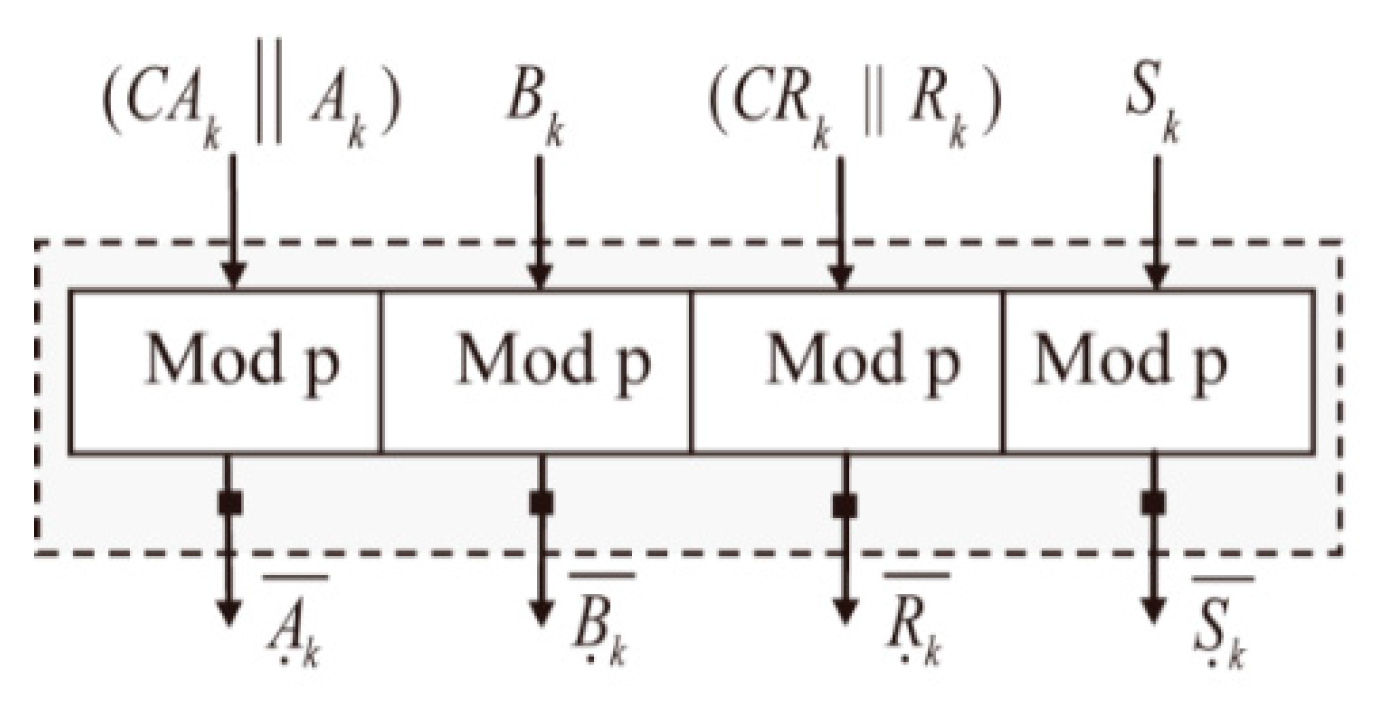
3. Proposed Secure Architecture and Its Algorithm Description
| Algorithm 2 Proposed word-oriented MD Algorithm with concurrent error detection |
| Input: |
| Output: |
4. Testing and Comparison of Error Detection Capability
4.1. Attacker Model
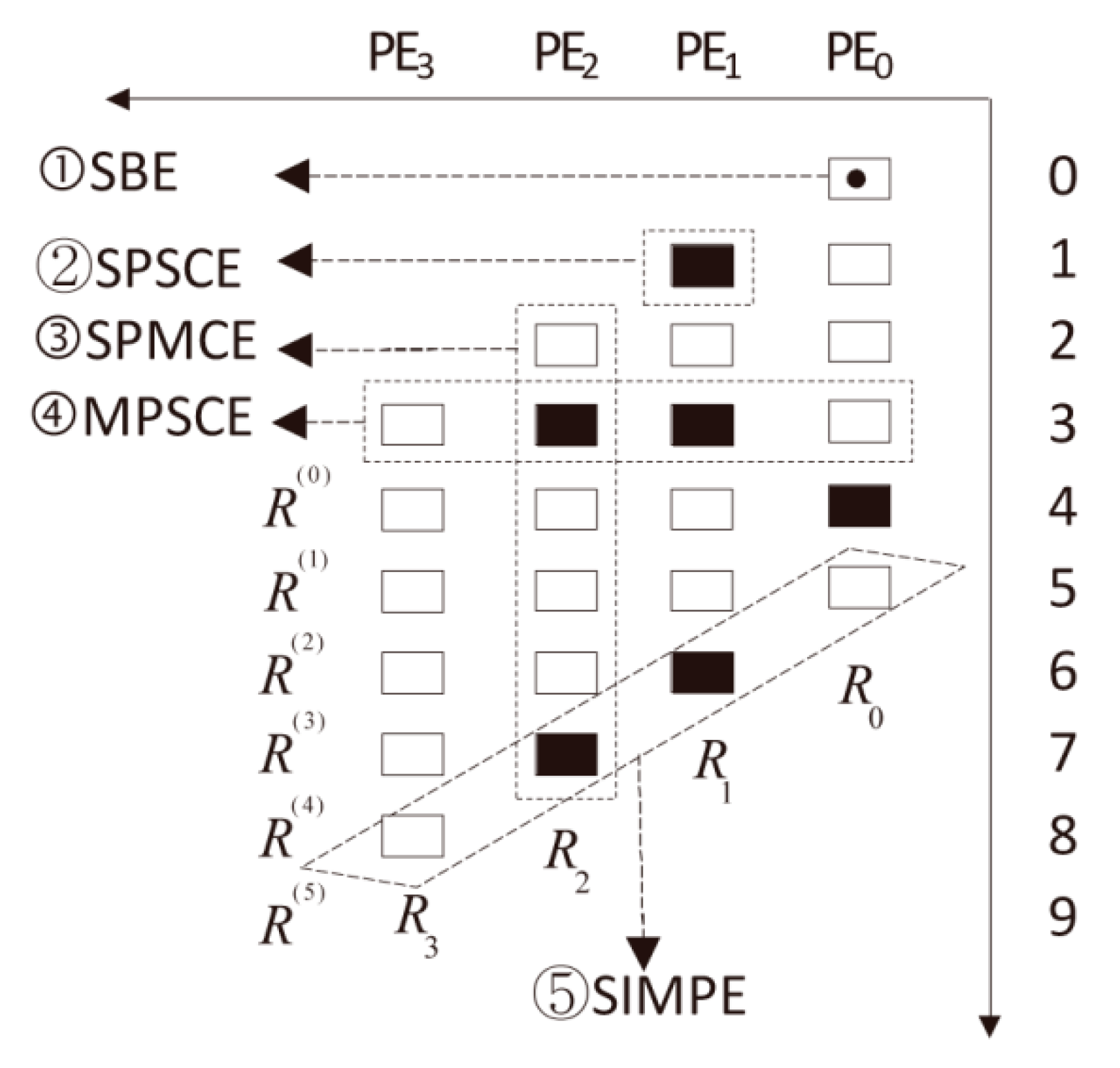
4.2. Five Types of Error Models
4.3. Simulation and Comparison of Error Detection Capabilities
5. Analysis on Time and Area Overheads
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Voyiatzis, A.G.; Serpanos, D.N. A fault-injection attack on Fiat-Shamir cryptosystems. In Proceedings of the 24th International Conference on Distributed Computing Systems Workshops, Tokyo, Japan, 23–24 March 2004; Volume 5, pp. 618–621. [Google Scholar]
- Schmidt, J.M.; Hutter, M.; Plos, T. Optical fault attacks on AES: A threat in violet. In Proceedings of the Sixth International Workshop on Fault Diagnosis and Tolerance in Cryptography, FDTC 2009, Lausanne, Switzerland, 6 September 2009; pp. 13–22. [Google Scholar]
- Trichina, E.; Korkikyan, R. Multi fault laser attacks on protected CRT-RSA. In Proceedings of the 2010 Workshop on Fault Diagnosis and Tolerance in Cryptography, Santa Barbara, CA, USA, 21 August 2010; pp. 75–86. [Google Scholar]
- Karaklajić, D.; Schmidt, J.M.; Verbauwhede, I. Hardware designer’s guide to fault attacks. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2013, 21, 2295–2306. [Google Scholar] [CrossRef]
- Karpovsky, M.; Kulikowski, K.J.; Taubin, A. Robust protection against fault-injection attacks on smart cards implementing the advanced encryption standard. In Proceedings of the 2004 International Conference on Dependable Systems and Networks (DSN 2004), Florence, Italy, 28 June–1 July 2004; pp. 93–101. [Google Scholar]
- Gaubatz, G.; Sunar, B. Robust finite field arithmetic for fault-tolerant public-key cryptography. In Fault Diagnosis and Tolerance in Cryptography, Proceedings of the International Workshop on Fault Diagnosis and Tolerance in Cryptography, Yokohama, Japan, 10 October 2006; Springer: Berlin/Heidelberg, Germany, 2006; pp. 196–210. [Google Scholar]
- Eddine Cherif, B.D.; Bendiabdellah, A.; Tabbakh, M. Diagnosis of an inverter IGBT open-circuit fault by hilbert-huang transform application. Traitement du Signal 2019, 36, 127–132. [Google Scholar] [CrossRef]
- Berzati, A.; Canovas, C.; Goubin, L. In (security) against fault injection attacks for CRT-RSA implementations. In Proceedings of the 2008 5th Workshop on Fault Diagnosis and Tolerance in Cryptography, Washington, DC, USA, 10 August 2008; pp. 101–107. [Google Scholar]
- Dominguez-Oviedo, A.; Hasan, M.A. Error detection and fault tolerance in ECSM using input randomization. IEEE Trans. Dependable Secur. Comput. 2008, 6, 175–187. [Google Scholar] [CrossRef]
- Wang, Z.; Karpovsky, M.; Joshi, A. Secure multipliers resilient to strong fault-injection attacks using multilinear arithmetic codes. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2011, 20, 1036–1048. [Google Scholar] [CrossRef]
- IBM 4764 PCI-X Cryptographic Coprocessor. 2011. Available online: http://www.ibm.com/support/knowledgecenter/9119-FHB/p7hcd/fc474.htm (accessed on 28 February 2020).
- Patel, J.H.; Fung, L.Y. Concurrent error detection in ALU’s by recomputing with shifted operands. IEEE Trans. Comput. 1982, 31, 589–595. [Google Scholar] [CrossRef]
- Johnson, B.W.; Aylor, J.H.; Hana, H.H. Efficient use of time and hardware redundancy for concurrent error detection in a 32-bit VLSI adder. IEEE J. Solid-State Circuits 1988, 23, 208–215. [Google Scholar] [CrossRef]
- Li, J.; Swartzlander, E.E. Concurrent error detection in ALUs by recomputing with rotated operands. In Proceedings of the 1992 IEEE International Workshop on Defect and Fault Tolerance in VLSI Systems, Dallas, TX, USA, 4–6 November 1992; pp. 109–116. [Google Scholar]
- Chiou, C.W.; Lee, C.Y.; Lin, J.M.; Hou, T.W.; Chang, C.C. Concurrent error detection and correction in dual basis multiplier over GF (2m). IET Circuits Devices Syst. 2009, 3, 22–40. [Google Scholar] [CrossRef]
- Lo, J.C.; Thanawastien, S.; Rao, T.R.N. Concurrent error detection in arithmetic and logical operations using Berger codes. In Proceedings of the 9th Symposium on Computer Arithmetic, Santa Monica, CA, USA, 6–8 September 1989; pp. 233–240. [Google Scholar]
- Nicolaidis, M.; Duarte, R.O.; Manich, S.; Figueras, J. Fault-secure parity prediction arithmetic operators. IEEE Des. Test Comput. 1997, 14, 60–71. [Google Scholar] [CrossRef]
- Reyhani-Masoleh, A.; Hasan, M.A. Fault detection architectures for field multiplication using polynomial bases. IEEE Trans. Comput. 2006, 55, 1089–1103. [Google Scholar] [CrossRef]
- Gaubatz, G.; Sunar, B.; Karpovsky, M.G. Non-linear residue codes for robust public-key arithmetic. In Fault Diagnosis and Tolerance in Cryptography, Proceedings of the International Workshop on Fault Diagnosis and Tolerance in Cryptography, Yokohama, Japan, 10 October 2006; Springer: Berlin/Heidelberg, Germany, 2006; pp. 173–184. [Google Scholar]
- Hariri, A.; Reyhani-Masoleh, A. Fault detection structures for the Montgomery multiplication over binary extension fields. In Proceedings of the Workshop on Fault Diagnosis and Tolerance in Cryptography (FDTC 2007), Vienna, Austria, 10 September 2007; pp. 37–46. [Google Scholar]
- Bayat-Sarmadi, S.; Hasan, M.A. On concurrent detection of errors in polynomial basis multiplication. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2007, 15, 413–426. [Google Scholar] [CrossRef]
- Hariri, A.; Reyhani-Masoleh, A. Concurrent error detection in montgomery multiplication over binary extension fields. IEEE Trans. Comput. 2011, 60, 1341–1353. [Google Scholar] [CrossRef]
- Wang, Z.; Karpovsky, M.; Sunar, B. Multilinear codes for robust error detection. In Proceedings of the 2009 15th IEEE International On-Line Testing Symposium, Lisbon, Portugal, 24–26 June 2009; pp. 164–169. [Google Scholar]
- Barenghi, A.; Breveglieri, L.; Koren, I.; Naccache, D. Fault injection attacks on cryptographic devices: Theory, practice, and countermeasures. Proc. IEEE 2012, 100, 3056–3076. [Google Scholar] [CrossRef]
- Khairallah, M.; Sadhukhan, R.; Samanta, R.; Breier, J.; Bhasin, S.; Chakraborty, R.S.; Mukhopadhyay, D. DFARPA: Differential fault attack resistant physical design automation. In Proceedings of the 2018 Design, Automation & Test in Europe Conference & Exhibition (DATE), Dresden, Germany, 19–23 March 2018; pp. 1171–1174. [Google Scholar]
- Stein, J. Computational problems associated with Racah algebra. J. Comput. Phys. 1967, 1, 397–405. [Google Scholar] [CrossRef]
- Brent, R.P.; Kung, H.T. Systolic VLSI arrays for linear time GCD computation. In VLSI ‘83:VLSI Design of Digital System; Elsevier Science Pub. Co.: Amsterdam, The Netherlands, 1983; pp. 145–154. [Google Scholar]
- Takagi, N. A VLSI algorithm for modular division based on the binary GCD algorithm. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 1998, 81, 724–728. [Google Scholar]
- Kaihara, M.; Takagi, N. A Hardware Algorithm for Modular Multiplication/Division. IEEE Trans. Comput. 2005, 54, 12–21. [Google Scholar] [CrossRef]
- Chen, G.; Bai, G.; Chen, H. A New Systolic Architecture for Modular Division. IEEE Trans. Comput. 2007, 56, 282–286. [Google Scholar] [CrossRef]
- Chen, C.; Qin, Z. Efficient algorithm and systolic architecture for modular division. Int. J. Electron. 2011, 98, 813–823. [Google Scholar] [CrossRef]
- Choi, P.; Lee, M.; Kong, J.; Kim, D.K. Efficient Design and Performance Analysis of a Hardware Right-shift Binary Modular Division Algorithm in GF(p). J. Semicond. Technol. Sci. 2017, 17, 425–437. [Google Scholar]
- Chervyakov, N.; Lyakhov, P.; Babenko, M.; Nazarov, A.; Deryabin, M.; Lavrinenko, I.; Chervyakov, N. A High-Speed Division Algorithm for Modular Numbers Based on the Chinese Remainder Theorem with Fractions and Its Hardware Implementation. Electronics 2019, 8, 261. [Google Scholar] [CrossRef]
- Bayat-Sarmadi, S.; Hasan, M. Concurrent Error Detection in Finite-Field Arithmetic Operations Using Pipelined and Systolic Architectures. IEEE Trans. Comput. 2009, 58, 1553–1567. [Google Scholar] [CrossRef]
- Kermani, M.M.; Reyhani-Masoleh, A. Concurrent Structure-Independent Fault Detection Schemes for the Advanced Encryption Standard. IEEE Trans. Comput. 2010, 59, 608–622. [Google Scholar] [CrossRef]
- Mozaffari-Kermani, M.; Azarderakhsh, R.; Lee, C.Y.; Bayat-Sarmadi, S. Reliable Concurrent Error Detection Architectures for Extended Euclidean-Based Division Over GF(2m). IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2013, 22, 995–1003. [Google Scholar] [CrossRef]
- Nicolaidis, M.; Duarte, R. Fault-secure parity prediction Booth multipliers. IEEE Des. Test Comput. 1999, 16, 90–101. [Google Scholar] [CrossRef]
- Yumbul, K.; Erdem, S.S.; Savas, E. On Selection of Modulus of Quadratic Codes for the Protection of Cryptographic Operations against Fault Attacks. IEEE Trans. Comput. 2012, 63, 1182–1196. [Google Scholar]
- Yang, Q.; Hu, X.; Qin, Z. Secure Systolic Montgomery Modular Multiplier Over Prime Fields Resilient to Fault-Injection Attacks. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2014, 23, 1889–1902. [Google Scholar] [CrossRef]
- Hu, X.; Qin, Z.; Yang, Q. A Secure Modular Division Algorithm Embedding with Error Detection and Low-Area ASIC Implementation. J. Signal Process. Syst. 2019, 1–13. Available online: https://link.springer.com/article/10.1007/s11265-019-01481-6 (accessed on 20 February 2020).
- Benso, A.; Prinetto, P. (Eds.) Fault Injection Techniques and Tools for Embedded Systems Reliability Evaluation; Springer Science & Business Media: Berlin, Germany, 2003; Volume 23, pp. 7–39. [Google Scholar]
- Torrance, R.; James, D. The state-of-the-art in IC reverse engineering. In International Workshop on Cryptographic Hardware and Embedded Systems; Springer: Berlin/Heidelberg, Germany, 2009; pp. 363–381. [Google Scholar]
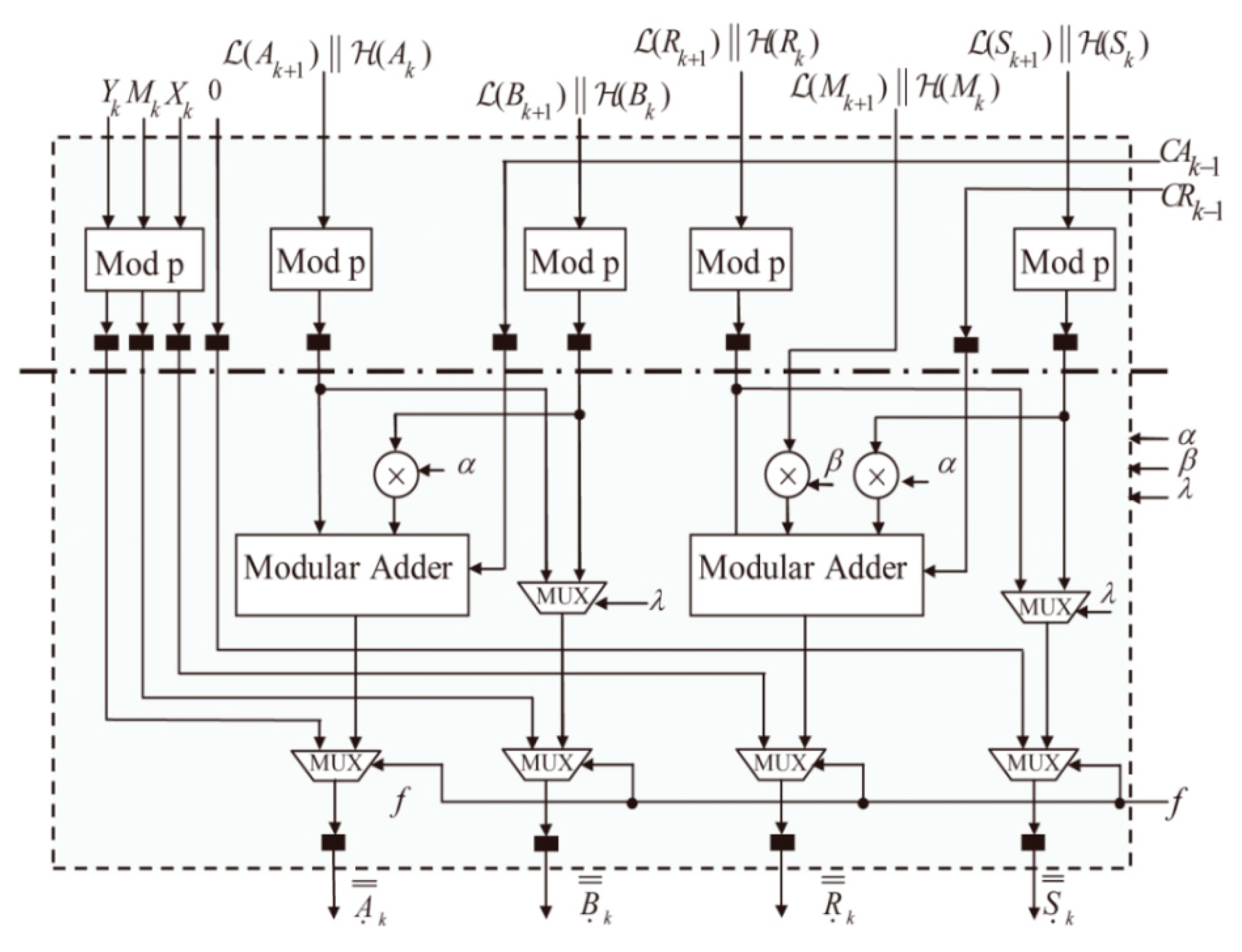
| Symbol | Description |
|---|---|
| p | The check factor of the LAC |
| n | The bit number of modulus M |
| w | The word size of PE (w∈{ 8, 16,32,64}) |
| e | The number of words in operands |
| The value of X at the i-th iteration of Algorithm 2 | |
| The k-th word of X (X can be A, B, R, or S) | |
| The least significant bit (LSB) of Xk | |
| Bits 1 to 0 from X0 | |
| Bits w − 1 to 1 from Xk | |
| Z | The set {A, B, R, S} |
| The set {Ak, Bk, Rk, Sk} | |
| The set | |
| The set | |
| The set | |
| The concatenation of X and Y | |
| The 1-bit carry-out signal from the computation of the k-th word of A | |
| The 2-bit carry-out signal from the computation of the k-th word of R |
| MFM Arch. | Scheme | p | Prob. | Error Model | Error PE Location | |||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| SBE | SPSCE | SPMCE | MPSCE | SIMPE | ||||||||
| One-bit Error | One-PE Error | Two-PE Error | Three-PE Error | Two-PE Error | Three-PE Error | Two-PE Error | Three-PE Error | |||||
| Type-8 | Parity [36] | 8bit | P(%) | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | × |
| Style-I [40] | 28 − 1 | P(%) | 100 | 99.895 | 100 | 100 | 100 | 100 | 100 | 100 | × | |
| Style-II (Ours) | 3 | P(%) | 100 | 85.432 | 97.878 | 99.691 | 97.878 | 99.691 | 97.878 | 99.691 | √ | |
| 7 | P(%) | 100 | 95.227 | 99.772 | 99.898 | 99.772 | 99.898 | 99.772 | 99.898 | √ | ||
| 31 | P(%) | 100 | 99.012 | 99.990 | 100 | 99.990 | 100 | 99.990 | 100 | √ | ||
| Type-16 | Parity [36] | 8bit | P(%) | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | × |
| Style-I [40] | 216 − 1 | P(%) | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | × | |
| Style-II (Ours) | 3 | P(%) | 100 | 85.595 | 97.925 | 99.701 | 97.925 | 99.701 | 97.925 | 99.701 | √ | |
| 7 | P(%) | 100 | 95.293 | 99.778 | 99.990 | 99.778 | 99.990 | 99.778 | 99.990 | √ | ||
| 31 | P(%) | 100 | 99.097 | 99.992 | 100 | 99.992 | 100 | 99.992 | 100 | √ | ||
| Type-32 | Parity [36] | 8bit | P(%) | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | × |
| Style-I [40] | 232 − 1 | P(%) | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | × | |
| Style-II (Ours) | 3 | P(%) | 100 | 85.597 | 97.925 | 99.701 | 97.925 | 99.701 | 97.925 | 99.701 | √ | |
| 7 | P(%) | 100 | 95.294 | 99.778 | 99.990 | 99.778 | 99.990 | 99.778 | 99.990 | √ | ||
| 31 | P(%) | 100 | 99.097 | 99.992 | 100 | 99.992 | 100 | 99.992 | 100 | √ | ||
| Type-64 | Parity [36] | 8bit | P(%) | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | × |
| Style-I [40] | 264 − 1 | P(%) | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | × | |
| Style-II (Ours) | 3 | P(%) | 100 | 85.598 | 97.925 | 99.701 | 97.925 | 99.701 | 97.925 | 99.701 | √ | |
| 7 | P(%) | 100 | 95.295 | 99.779 | 99.990 | 99.779 | 99.990 | 99.779 | 99.990 | √ | ||
| 31 | P(%) | 100 | 99.098 | 99.992 | 100 | 99.992 | 100 | 99.992 | 100 | √ | ||
| MFM Types | Scheme | p | Operand Size (bit) | f (MHZ) | Total Area (K gate) | Extra Overhead | Extra Overhead Ratio | Error-Reporting Delay (ns) | ||
|---|---|---|---|---|---|---|---|---|---|---|
| Extra Cycles | Area (K gate) | Time (%) | Area (%) | |||||||
| Type-8 | Parity [36] | 8bit | 128 | 909 | 61.06 | 3 | 29.96 | 30.82 | 96.33 | 11.00 |
| 256 | 131.16 | 59.68 | 30.11 | 83.50 | 19.80 | |||||
| 512 | 308.49 | 119.12 | 29.76 | 62.90 | 37.40 | |||||
| 1024 | 799.28 | 237.99 | 29.59 | 42.40 | 72.60 | |||||
| Style-I [40] | 28 − 1 | 128 | 1220 | 48.84 | 2 | 17.74 | 1.09 | 57.06 | 8.50 | |
| 256 | 105.70 | 24.22 | 0.54 | 47.88 | 15.30 | |||||
| 512 | 257.57 | 68.20 | 0.27 | 36.01 | 28.90 | |||||
| 1024 | 697.53 | 136.25 | 0.13 | 24.27 | 56.10 | |||||
| Style-II (Ours) | 3 | 128 | 1111 | 50.89 | 2 | 19.79 | 6.65 | 63.64 | 1.80 | |
| 256 | 1052 | 108.84 | 37.33 | 12.17 | 52.23 | 1.90 | ||||
| 512 | 1041 | 264.33 | 74.96 | 13.14 | 39.59 | 1.92 | ||||
| 1024 | 1020 | 705.71 | 150.94 | 15.40 | 27.21 | 1.96 | ||||
| 7 | 128 | 1136 | 63.69 | 2 | 32.59 | 18.50 | 104.80 | 2.00 | ||
| 256 | 980 | 136.67 | 65.19 | 20.43 | 91.20 | 2.04 | ||||
| 512 | 980 | 319.20 | 129.83 | 20.22 | 68.56 | 2.04 | ||||
| 1024 | 952 | 814.37 | 258.60 | 23.64 | 46.80 | 2.10 | ||||
| 31 | 128 | 800 | 83.732 | 2 | 52.632 | 48.13 | 169.24 | 2.50 | ||
| 256 | 800 | 175.26 | 104.78 | 47.59 | 148.68 | 2.50 | ||||
| 512 | 769 | 396.64 | 205.27 | 53.22 | 108.40 | 2.60 | ||||
| 1024 | 769 | 970.66 | 415.89 | 53.08 | 74.97 | 2.60 | ||||
| Type-16 | Parity [36] | 16bit | 128 | 769 | 59.35 | 3 | 32.44 | 49.39 | 120.53 | 7.80 |
| 256 | 122.37 | 64.78 | 58.55 | 112.48 | 13.00 | |||||
| 512 | 266.26 | 129.48 | 48.14 | 94.73 | 23.40 | |||||
| 1024 | 619.91 | 258.88 | 47.93 | 71.71 | 44.20 | |||||
| Style-I [40] | 216 − 1 | 128 | 1136 | 45.06 | 2 | 18.15 | 0.73 | 67.45 | 5.28 | |
| 256 | 97.73 | 36.14 | 0.37 | 62.76 | 8.80 | |||||
| 512 | 207.40 | 70.72 | 0.18 | 51.75 | 15.84 | |||||
| 1024 | 502.41 | 141.38 | 0.09 | 39.16 | 29.92 | |||||
| Style-II (Ours) | 3 | 128 | 909 | 42.22 | 2 | 16.33 | 25.94 | 63.09 | 2.20 | |
| 256 | 833 | 89.89 | 32.69 | 36.87 | 57.15 | 2.40 | ||||
| 512 | 833 | 202.20 | 65.38 | 36.62 | 47.85 | 2.40 | ||||
| 1024 | 833 | 493.96 | 130.77 | 36.49 | 36.01 | 2.40 | ||||
| 7 | 128 | 833 | 54.89 | 2 | 29.06 | 37.39 | 112.49 | 2.40 | ||
| 256 | 800 | 115.27 | 58.12 | 42.57 | 101.72 | 2.50 | ||||
| 512 | 800 | 252.85 | 116.25 | 42.31 | 85.11 | 2.50 | ||||
| 1024 | 800 | 593.55 | 279.32 | 47.86 | 64.41 | 2.60 | ||||
| 31 | 128 | 714 | 60.86 | 2 | 35.02 | 60.28 | 135.59 | 2.80 | ||
| 256 | 714 | 127.32 | 70.18 | 59.68 | 122.81 | 2.80 | ||||
| 512 | 689 | 276.33 | 129.73 | 65.08 | 102.30 | 2.90 | ||||
| 1024 | 689 | 640.35 | 279.32 | 64.92 | 77.37 | 2.90 | ||||
| Type-32 | Parity [36] | 32bit | 128 | 690 | 59.79 | 3 | 35.13 | 46.65 | 142.44 | 5.80 |
| 256 | 114.76 | 64.27 | 45.82 | 122.90 | 8.70 | |||||
| 512 | 237.73 | 123.88 | 45.41 | 108.81 | 14.50 | |||||
| 1024 | 517.68 | 246.09 | 45.20 | 89.91 | 26.10 | |||||
| Style-I [40] | 232 − 1 | 128 | 1000 | 34.11 | 2 | 9.45 | 0.76 | 38.31 | 4.00 | |
| 256 | 71.15 | 19.67 | 0.38 | 38.21 | 6.00 | |||||
| 512 | 151.91 | 38.05 | 0.19 | 33.43 | 10.00 | |||||
| 1024 | 346.06 | 74.47 | 0.09 | 26.96 | 18.00 | |||||
| Style-II (Ours) | 3 | 128 | 800 | 41.95 | 2 | 17.51 | 25.95 | 71.62 | 2.50 | |
| 256 | 740 | 82.24 | 30.82 | 35.51 | 59.94 | 2.70 | ||||
| 512 | 714 | 175.16 | 61.30 | 40.26 | 53.85 | 2.80 | ||||
| 1024 | 714 | 395.10 | 122.51 | 40.13 | 44.94 | 2.80 | ||||
| 7 | 128 | 667 | 45.40 | 2 | 21.01 | 51.14 | 86.13 | 3.00 | ||
| 256 | 667 | 93.43 | 42.02 | 50.57 | 81.75 | 3.00 | ||||
| 512 | 645 | 197.89 | 83.05 | 55.29 | 72.94 | 3.10 | ||||
| 1024 | 645 | 440.67 | 167.95 | 55.14 | 61.59 | 3.10 | ||||
| 31 | 128 | 625 | 51.40 | 2 | 27.01 | 61.22 | 110.71 | 3.20 | ||
| 256 | 625 | 100.38 | 48.97 | 60.60 | 95.28 | 3.20 | ||||
| 512 | 606 | 211.34 | 97.50 | 65.31 | 85.64 | 3.30 | ||||
| 1024 | 606 | 467.46 | 194.89 | 65.15 | 71.50 | 3.30 | ||||
| Type-64 | Parity [36] | 64bit | 128 | 625 | 55.64 | 3 | 31.81 | 47.13 | 133.46 | 3.20 |
| 256 | 111.73 | 63.07 | 46.28 | 129.62 | 6.40 | |||||
| 512 | 228.41 | 125.61 | 45.87 | 122.18 | 9.60 | |||||
| 1024 | 478.77 | 250.68 | 45.66 | 109.90 | 16.00 | |||||
| Style-I [40] | 264 − 1 | 128 | 909 | 34.03 | 2 | 10.19 | 0.77 | 42.78 | 2.20 | |
| 256 | 61.25 | 12.59 | 0.38 | 25.89 | 4.40 | |||||
| 512 | 120.81 | 18.01 | 0.19 | 17.52 | 6.60 | |||||
| 1024 | 256.96 | 28.87 | 0.09 | 12.66 | 11.00 | |||||
| Style-II (Ours) | 3 | 128 | 800 | 39.48 | 2 | 15.64 | 14.51 | 65.66 | 2.50 | |
| 256 | 800 | 79.65 | 30.99 | 14.09 | 63.70 | 2.50 | ||||
| 512 | 740 | 163.94 | 61.14 | 22.96 | 59.47 | 2.70 | ||||
| 1024 | 740 | 360.40 | 122.31 | 22.84 | 53.63 | 2.70 | ||||
| 7 | 128 | 645 | 43.36 | 2 | 19.51 | 41.99 | 81.79 | 3.10 | ||
| 256 | 645 | 87.30 | 39.01 | 41.44 | 80.73 | 3.10 | ||||
| 512 | 645 | 181.10 | 75.99 | 45.73 | 73.70 | 3.20 | ||||
| 1024 | 645 | 385.02 | 153.23 | 45.59 | 66.90 | 3.20 | ||||
| 31 | 128 | 555 | 45.90 | 2 | 18.51 | 64.89 | 92.45 | 3.60 | ||
| 256 | 555 | 93.68 | 45.37 | 64.26 | 93.92 | 3.60 | ||||
| 512 | 540 | 191.73 | 88.62 | 68.50 | 85.95 | 3.70 | ||||
| 1024 | 540 | 402.41 | 173.36 | 68.34 | 75.69 | 3.70 | ||||
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hu, X.; Qin, Z. A Secure Architecture for Modular Division over a Prime Field against Fault Injection Attacks. Appl. Sci. 2020, 10, 1700. https://doi.org/10.3390/app10051700
Hu X, Qin Z. A Secure Architecture for Modular Division over a Prime Field against Fault Injection Attacks. Applied Sciences. 2020; 10(5):1700. https://doi.org/10.3390/app10051700
Chicago/Turabian StyleHu, Xiaoting, and Zhongping Qin. 2020. "A Secure Architecture for Modular Division over a Prime Field against Fault Injection Attacks" Applied Sciences 10, no. 5: 1700. https://doi.org/10.3390/app10051700
APA StyleHu, X., & Qin, Z. (2020). A Secure Architecture for Modular Division over a Prime Field against Fault Injection Attacks. Applied Sciences, 10(5), 1700. https://doi.org/10.3390/app10051700





