Blockchain and IoT Convergence—A Systematic Survey on Technologies, Protocols and Security
Abstract
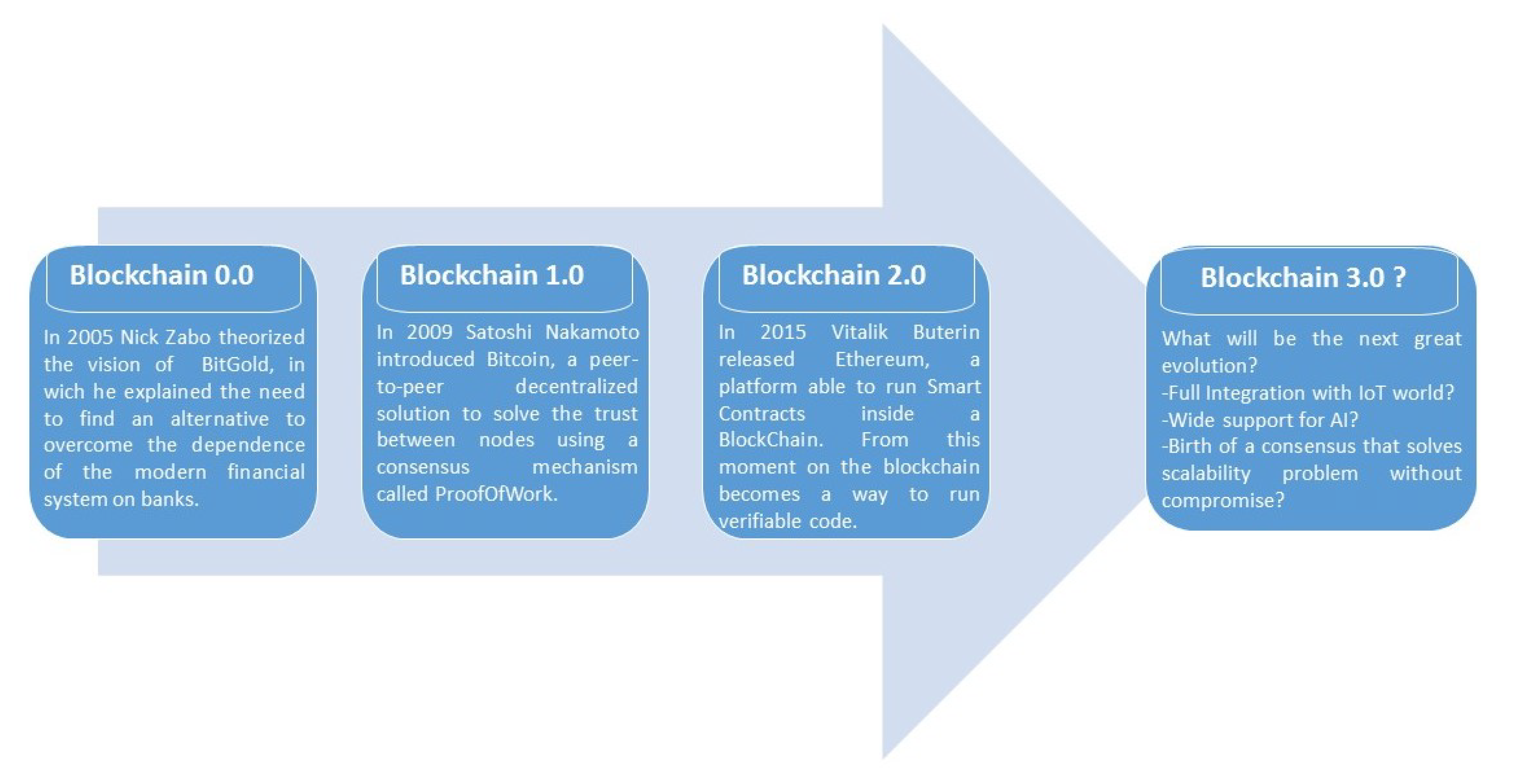
1. Introduction
- Use of encryption to sign transactions between the parties.
- Transactions are stored on a distributed ledger over a peer-to-peer network.
- Reaching consensus using a decentralized approach.
2. Key Contribution
3. Workflow
- Number of citations of whitepapers and related articles on Google scholar, Microsoft academic and semantic scholar.
- Novelty of the proposed solution.
- Market capitalization if any.
4. Internet of Things
4.1. IoT Weaknesses
4.1.1. Cloud Infrastructure
- Wrapping attack: This attack occurs by duplicating the user credentials during the log in process, and the SOAP2 messages that are exchanged during the connection setup between the web browser and the server are modified by the attackers [16].
- Eavesdropping: under the term eavesdropping fall the techniques used to intercept communications that occur within a channel established between two authorized users [16].
- Flooding attack/DOS attack: The goal of a DOS attack is to consume all the available resources of a server to make the system unresponsive to legitimate traffic [16].
- Data Stealing problem. This type of attack involves hacking the data and security of cloud systems by stealing system access credentials.
- Man-in-the-Middle Attack (MITM): in this case the attacker succeeds in gaining access to the communication channel between two legitimate users, being able to both intercept and modify the information without making anyone aware of it [16].
- Reflection Attack: This type of attack is perpetrated in challenge-response type systems that use the same communication protocol in both directions. The idea behind this type of attack is to trick the victim by asking him for a solution (response) to his own challenge [16].
- Replay Attack: The replay attack is a form of cyberattack that targets computer networks in order to take possession of an authentication credential communicated from one host to another, and then propose it again by simulating the identity of the issuer. Usually the action is carried out by an attacker who interposes himself between the two communicating sides or from a spoofed IP [16].
- Brute force/Dictionary attack: in a brute force attack, a series of attempts are made to guess the credentials of a certain system, based on information generated through specific dictionaries or by specific rules.
4.1.2. Sensors and Devices: Perception Layer
- Brute force/Dictionary Attack: This attack is launched by guessing passwords containing all possible combinations of letters, numbers and alphanumeric character or by using precomputed dictionary of passwords [16].
- Social hacking: This attack exploits human weaknesses. Instead of using a generic dictionary, private information of the target person is collected, and a tailored dictionary is created.
- DoS Attack: denial-of-Service attack is accomplished by flooding the targeted machine with superfluous requests from a fake RFID device.
- Eavesdropping: an antenna is used to record communications between legitimate RFID tags and readers. Eavesdropping attacks can be done in both directions: tag to reader and reader to tag
- Skimming: in this case, the attacker observes the information exchanged between a legitimate tag and legitimate reader. Through the extracted data, the attacker attempts to make a cloned tag which imitates the original RFID tag. Very dangerous in case of RFID chips in credit cards, passports and another personal RFID hardware.
- Replay Attack: similar to a MITM attack, in Replay attacks, the communicating signal between the tag and the reader is intercepted, recorded and replayed.
- Phishing attack: phishing is a type of scam carried out on the Internet by a malicious attacker trying to deceive the victim by convincing them to provide personal information, financial data or access codes, pretending to be a reliable entity in a digital communication.
- User Tracking: in case tags use the same unique ID for anti-collision technique, an attacker can easily track them by compromising the secrecy of the entire NFC system.
- Relay attack: this concerns the intrusion within a communication between device and NFC, the ability to read data coming from the source device and send it back to the destination device.
- Eavesdropping: the attack is perpetrated via an antenna used to record communications between NFC devices. Although NFC communication takes place between very close devices, this type of attack is feasible. The purpose of the attack can be two-fold, theft of information or corrupting the information exchanged, making it useless.
- Spoofing: some mobile devices are configured to run automatically the commands received by NFC tags. In a spoofing attack, a third party pretends to be another entity to induce a user to touch his device against the tag programmed specifically to execute malicious code.
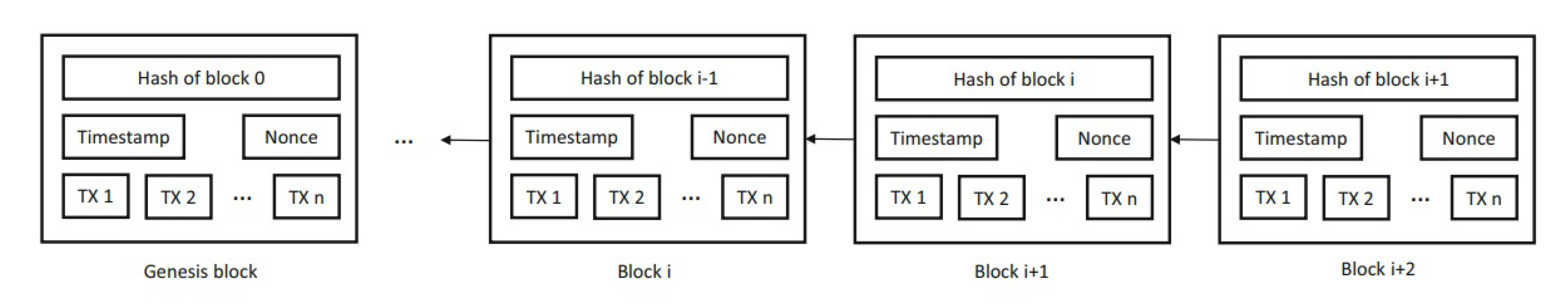
5. Distributed Ledgers
5.1. Blockchain vs. Classical Vulnerability
- Replay attack: In case of a fork in a Blockchain, an attacker can use a signed transaction on the first Blockchain and replicate it as it is on the second since the private keys on both chains are identical. Replay protection is fairly trivial to implement and it has become a de-facto prerequisite for any forked chain. For example, Bitcoin Cash created replay protection for their chain by implementing a unique marker that would allow the Bitcoin Cash nodes to distinguish transactions spent on the legacy Bitcoin chain as independent from the Bitcoin Cash chain.
- Sybil Attack: To create many connections in a Blockchain it is necessary to start many nodes at the same time. An attack of this kind can be used to capture users’ IPs or study the topology of the network, falling back as a type of attack to be very similar to Eavesdropping. Mining process is protected by consensus-building algorithms that are specifically designed to avoid this type of attack.
- MITM (Man-In-The-Middle) attack: There is no way to listen to a transaction and steal data because of the encryption systems used to sign communications within Blockchain networks. It is possible, however, if we expand the mesh of the definition of MITM attack, embracing not only the network but also the software that is part of it, identify some vulnerabilities such as editing the destination wallet in the transactions sent by the hardware ledger wallet or the theft of funds from wallets generated by weak private keys, where an attacker who possess the private key waits “in the middle” for a transaction to steal the funds in the very next block.
- Brute force/Dictionary attack: No way to brute force a private key correctly generated. The problems arise from the unsafe generation of the private key. Unfortunately, some wallets generate private keys directly from user-defined passwords without using any random numbers. This exposes users to this type of attack.
- Phishing attack: There is no architecture that is free from this type of attack because it does not depend on the intrinsic security of the software or hardware used, but exclusively on the human ability to understand and avoid being cheated.
5.2. Consensus
5.2.1. Pow
5.2.2. PoS
5.2.3. DPoS
- Pooling: Many small nodes can share their stakes, thus obtaining a higher chance together to participate in the proposals and in the vote for the next block, and share the rewards afterwards.
- Suitable for Resource-constrained nodes: Nodes with limited resources can choose their delegates and avoid running the node 24 h.
- Haigh availability: Single nodes can choose new delegates for each new block. This flexibility provides a high availability for the network reaching consensus.
5.2.4. pBFT
5.2.5. Others
- Proof of Burn [31]: the probability for a specific node to success in mining new block is directly proportional to the number of coins burned by itself. The burning process consists of sending tokens to a specific address that cannot send tokens. These tokens are thus ’burned’ in the sense that they are no longer in circulation and therefore inaccessible. This is a similar idea to PoW but without wasting real world energy. Proof of burn has many of the same criticisms as PoS; the consensus is determined by the richest nodes in the network.
- Proof of capacity [32,33]: Similar to Proof of Work, but uses storage instead of computation. Cryptographically signed data is written to the local storage according the following rules:
- A very slow hash function is computed and stored. In the process, the hard drives are filled with groups of the precomputed hashes, and each group contains 4096 pairs.
- While mining, a deadline time from a specific pair for each group is calculated. This deadline time represents the time to wait for mining another block after the last one.
- The right to mine the next block is granted to the node who have the shortest deadline.
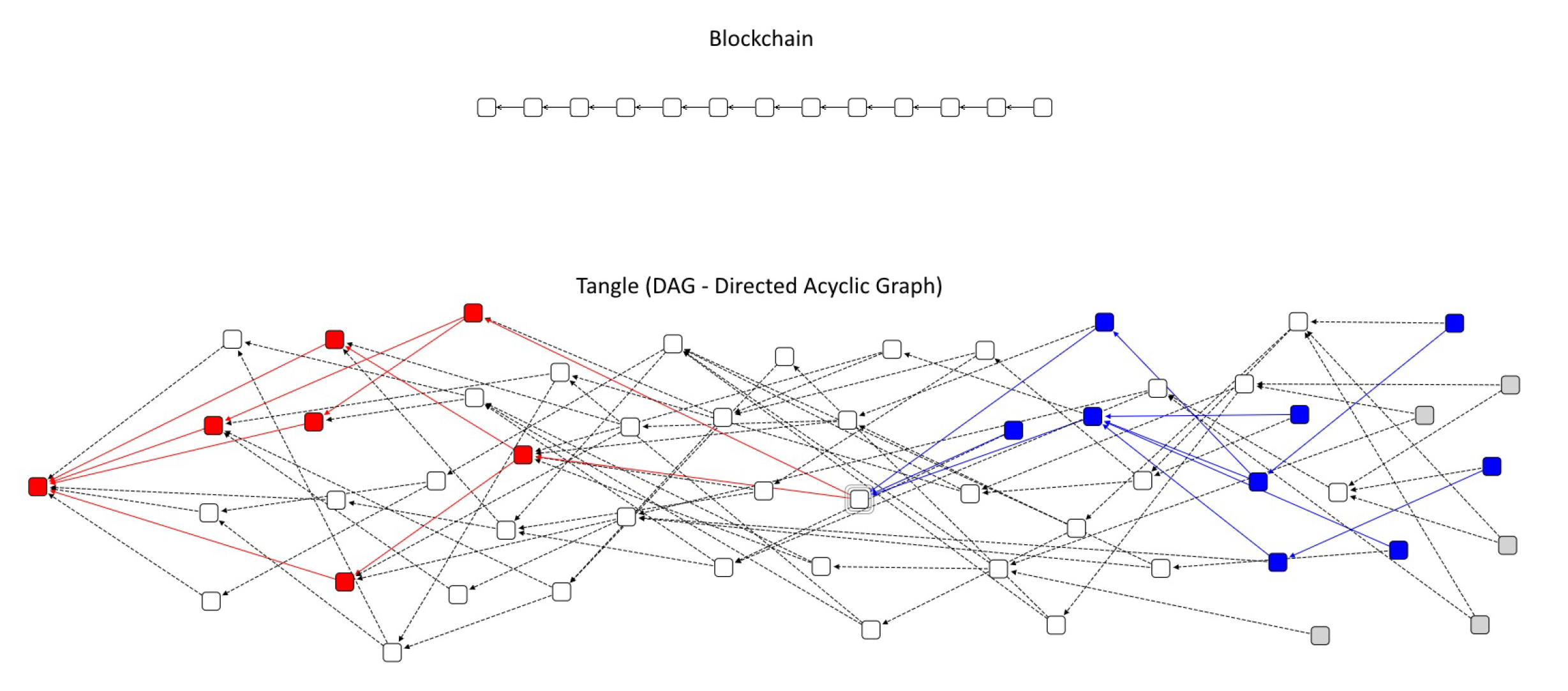
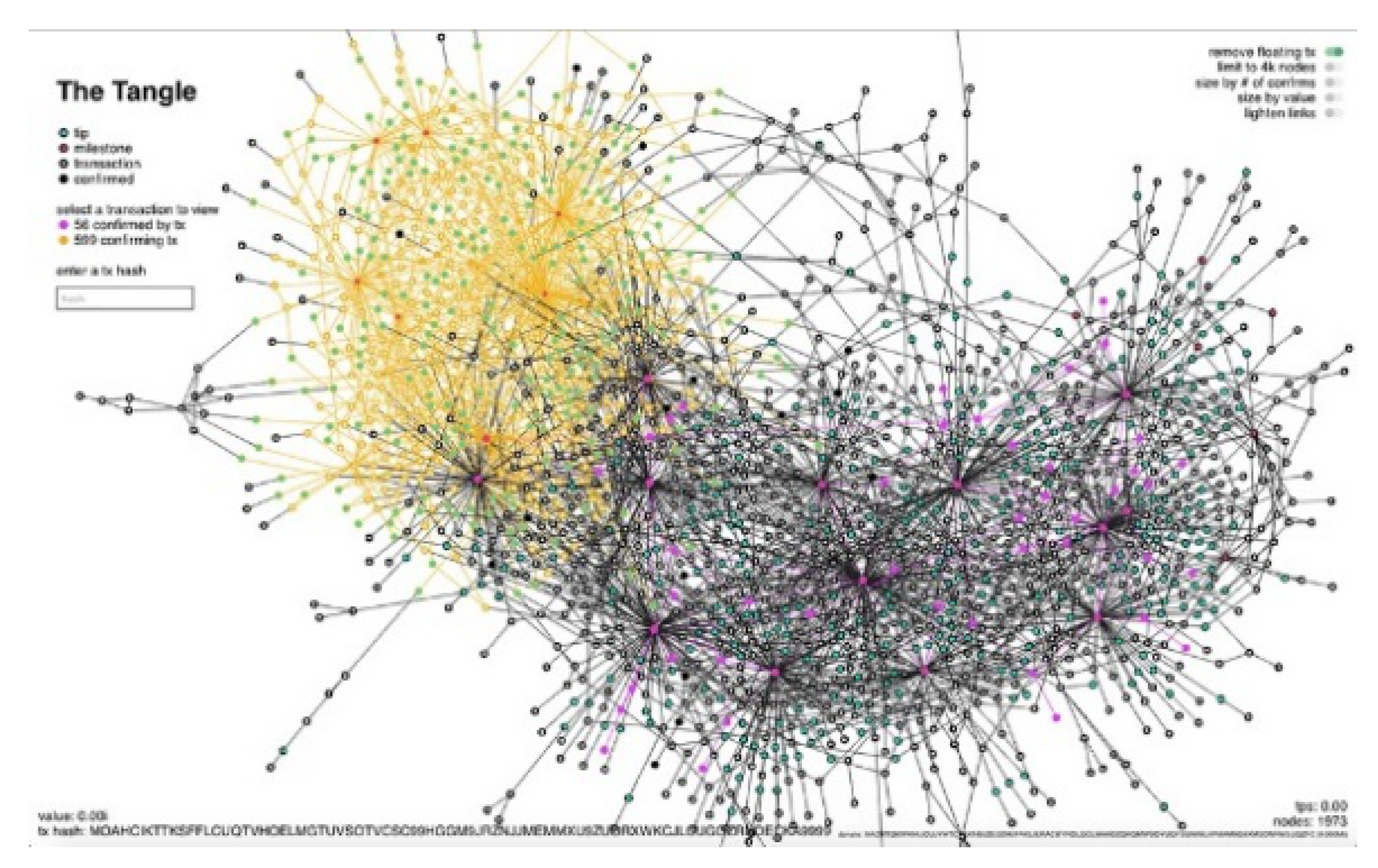
- The Tangle [34,35]: the most famous alternative to standard Blockchain structures, ’The Tangle’ use a DAG (Direct Acyclic Graph) to store transactions. Better explanation of this method used to achieve a different kind of consensus is reviewed in Section 8.1.
- Hashgraph Consensus [36]: Similar to IOTA’s Tangle, a DAG is created but following different rules. The new data structure named Hashgraph uses a gossip protocol to spread information throughout the network, and a virtual voting mechanism to achieve consensus involving random sync and validation between nodes. Any node can view the world from the perspective of any other node since last sync. In this way each node can determine if a given set of information or transactions is valid by checking if at least two thirds of the network’s nodes have witnessed specific transaction.
5.3. Cryptography and Hashing
5.3.1. Cryptographic Hash Algorithm
5.3.2. Asymmetric Encryption Algorithm
6. Blockchain: Strengths and Weaknesses
- Decentralization: As a decentralized and distributed technology, all transactions are decentralized, and verified by the network itself removing any single point of failure in a network of devices.
- Security: The use of public/private key pairs to sign transactions, specific hash functions to link block together and the peculiar consensus algorithms, gives to Blockchain systems a high resistance to tampering.
- Cost reduction: according to a Santander FinTech study [69], distributed ledger technology could reduce financial services infrastructure cost between US$ billion and $20 billion per annum by 2022, providing the possibility to decommission legacy systems and infrastructures and significantly reduce IT costs.
- Privacy & Transparency: The chain and its content are public and readable by anyone. Anyone can read and verify the honesty of every transaction but link a wallet(address) to a specific identity is not allowed by the protocol. There are some hacking strategies, however [70], to link a Blockchain address to a specific IP. To overcome this type of weakness, in addition to the use of Tor or VPN networks, specific Blockchain privacy-oriented projects have been developed [25,39]
- Legal issues: In a decentralized environment where nodes exist around the planet, there is no way to establish a common jurisdiction. Different countries have very different approaches to titles, ownership, contracts, trademarks and liabilities. Some governments have made cryptocurrencies illegal in their territories [72].
- Volatility: All cryptocurrencies are from high to extremely high volatile. Cryptocurrency markets are not regulated, some exchange has suspicious volumes [73], and most of cryptocurrencies has very low volume compared to Bitcoin, exposing them to high speculative activity.
- Storage: Usually, to run a full node, the entire Blockchain should be synchronized locally (i.e., Bitcoin needs 200GB). This high demand for storage space makes adoption in IoT systems extremely complicated.
- Transaction speed: Bitcoin is restricted by mining block time and block capacity to handling up to 7 transactions per second while VISA has the peak capacity to handle 24,000 transactions per second [74]. Actually, no decentralized Blockchain project can reach such an order of magnitude.
- Lack of maturity and standards: Distributed Ledgers is an emerging technology. Many Blockchain projects are not production ready, partially untested, and will require early adopters to accept significantly increased risk levels over the next five to seven years.
7. Blockchain–IoT Projects
7.1. IOTA
- Highly Scalable: Instead of storing transactions in blocks with a limited size, each transaction lives on its own and must approve two other transactions. With this method, the number of transactions that can be handled in a certain amount of time increases with the number of transactions.
- No fees: Each node validates its own and two other transactions. No block-mining required.
- Availability: Very high availability tanks to the Tangle architecture with no transaction to be inserted and mined in blocks with the danger of never being verified.
- Partition-Tolerant: Very High partition-tolerant system except for the presence of Coordinators.
- Quantum Computing resistant: A quantum-resistant algorithm called the Winternitz One-Time Signature Scheme is used to providing much better inherent security against the future quantum computer threat.
- Coordinators: Is meant for assuring security in the early stage of the network as it grows. It will be eventually removed when the network becomes sufficiently large. Presently is a limit for decentralization and for partition-tolerance of the system.
- Milestones: Will be eliminated in the future but are important to avoid attack to the structure. Without them, the size of the ledger would grow to sizes too big to be handled by most nodes, primarily by IoT devices.
- Low consistency: There is no global state which everybody agrees to. Only after milestones, but will be eliminated in the future.
7.2. VeChain
- VeChain Token(VET): Store of value and smart payment currency.
- Thor power(VTHO): Same as gas for Ethereum but using a different coin from the base one. This coin is consumed every time a change to the Blockchain is necessary.
- Authority node: There will only be 101 Authority Nodes and they validate all Blockchain transactions. Specific features are required to be elected as Authority node: KYC process, dedicated hardware and a minimum quantity of 250.000.000 VET blocked till the mainnet launch. There has been a lot of discussion in the VeChain community whether the identity of the 101 Authority Nodes should be publicly known. Single individuals with an Authority node can become a target once their identity gets publicly know. Enterprises that are currently owning an Authority node can also prefer to stay anonymous because they are not ready to publicly announce that they are using Blockchain technology or to stay ahead of competitors. A total of 30% of all gas (VTHO) consumed by Blockchain transaction is rewarded to the 101 Authority Masternode owners. To date no official list of Authority node exists, but only very few actors have confirmed their status: DNV GL [85], CAHrenheit [86].
- Economic node: The VeChain Economy Masternode is different to the Authority Masternode in that it seeks to provide stability to the VeChain ecosystem by acting as a sort of tool to give dividend.
7.3. WaltonChain
7.4. IoTeX
7.5. Ambrosus
- AMB-TRACE: Sensors and devices that generate data
- AMB-EDGE-GATEWAY: Collect, preanalyze and push data
- AMB-NET: Collect data in centralized data bases and in the Ethereum Blockchain
- AMB-DASH: Dashboard tools to visualize data
7.6. HDAC
7.7. IoTChain
7.8. Others
- Vite [93] is one of the few existing projects that use a DAG structure with smart contract mechanism. The project extends the capability of the Solidity language (Solidity++) introducing an asynchronous architecture. The architecture relies on a DAG ledger structure called block-lattice. Like IOTA’s project, VITE generates snapshot but using a new hierarchical HDPoS consensus algorithm; each account chain in the ledger generates local consensus results, and the snapshot chain at the highest level selects the final global consensus from the local consensus results.
- Nucleus Vision [94]: Using a sensor the people who decide to enter a shop are remunerated via mobile app using Nucleus Vision architecture. The sensor can sense mobile Id, temperature, motion, pressure, acceleration and sound. A deep learning infrastructure is used to optimize supply–demand.
- Ruff [95]: Ruff use DPoS for the consensus, specialized node to control the network. They have a development board kit and a JavaScript library to build IoT systems to connect.
- Modum [96]: Modum is a supply-chain system that integrates Blockchain technology, smart contracts and sensory devices into a single, passive solution. Core business of Modum is targeted to pharmaceutical companies that must employ expensive temperature-stabilized trucks and containers via 3rd party logistics providers to transport medicine. Modum offers a solution to substantially reduce these costs, by integrating a temperature sensor into medicinal shipments to monitor its temperature. All data is recorded into the Ethereum Blockchain, ensuring full transparency, accountability and data integrity.
- CPChain [97]: Cyber Physical Chain (CPChain) use a modified Byzantine Fault Tolerance algorithm (LBFT) to reach the consensus. They use an architecture called PDash in which the data is separated from the transactions using distributed data storage (IPFS) for data, and a Blockchain for the transactions.
- Yee [98]: To avoid data overload at node level, Yee project introduces a new concept for the distribution and retrieval of validated data across the network using a distance function and a corresponding routing table rule to retrieve relevant data from the correct nodes. To validate transaction, the project introduces a third-party node called YeeWallet. Therefore, no direct transaction to Blockchain, but a hybrid permissioned/permissionless Blockchain.
8. Blockchain and IoT Main Use Cases
8.1. Smart City/Home Security
8.2. Healthcare
8.3. Industry 4.0 Product Tracking
8.4. Supply-Chain Tracking
9. One Step Forward: Artificial Intelligence in a Blockchain–IoT Architecture: A Disruptive Research Vision
10. Conclusions
- Europe hosts the most important project, but Asia is the most powerful in promoting the link between Blockchain and IoT.
- The number of projects in Blockchain–IoT domain is growing fast and many are already in production stage.
- Big international players like Microsoft, Volkswagen, Fujitsu and countries like China have established important partnerships with existing projects.
- In financial terms, cryptocurrency traded on exchanges suffers extreme volatility, those related to the Blockchain and IoT world are also of a considerable scarcity of volumes.
- Storage: one of the main advantages of the Blockchain is its decentralization, but the ledger must be stored on the nodes themselves and IoT devices have low computational resources and very low storage capacity.
- Processing Power: Encryption and consensus algorithms can be very CPU-intensive and IoT systems have different types of devices which have very different computing capabilities [118], and not all of them will be able to run the same encryption algorithms at the required speed.
- Legal and Compliance: Blockchain is the very first architecture able to connect the entire world without a central control. Connecting countries with different laws without a legal supervision is a serious issue for both manufacturers and service.
- Scalability: In the Blockchain world there is a famous trilemma that says that if you want security and decentralization, it will be necessary to sacrifice scalability. Overcoming the Blockchain trilemma will lead to a new level of adoption for distributed ledgers.
Supplementary Materials
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| PoW | Proof of concept |
| PoS | Proof of Stake |
| DPoS | delegated Proof of Stake |
| pBFT | Practical Byzantine Fault Tolerance |
| IoT | Internet of Things |
| DNS | Domain name server |
| DDoS | Distributed denial-of-service |
| RFID | Radio-frequency identification |
| SOAP2 | Simple object access protocol v.2 |
| MITM | Man-in-the-middle attack |
| SaaS | Software as a service |
| NFC | Near-field communication |
| PoS | Point of Sale |
| PKI | Public key infrastructure |
| DAG | Direct Acyclic Graph |
| KYC | Know your customer |
| IPFS | InterPlanetary File System |
References
- Giuliano, R.; Mazzenga, F.; Neri, A.; Vegni, A.M. Security access protocols in IoT capillary networks. IEEE Internet Things J. 2016, 4, 645–657. [Google Scholar] [CrossRef]
- 3rd Cyberattack ‘Has Been Resolved’ After Hours of Major Outages. 2016. Available online: https://www.nbcnewyork.com/news/local/major-websites-taken-down-by-internet-attack/2040013/ (accessed on 10 August 2020).
- SonicWall. 2018 SonicWall Annual Threat Report. 2018. Available online: https://d3ik27cqx8s5ub.cloudfront.net/sonicwall.com/media/pdfs/resources/2018-snwl-cyber-threat-report.pdf (accessed on 10 August 2020).
- Tawfik, M.; Almadani, A.; Alharbi, A.A. A Review: The Risks And weakness Security on the IoT. IOSR J. Comput. Eng.-(Iosr-Jce) 2017, 12–17, e-ISSN: 2278-0661, p-ISSN: 2278-8727. [Google Scholar]
- Bastiaan, M. Preventing the 51%-Attack: A Stochastic Analysis of Two Phase Proof of Work in Bitcoin. In Proceedings of the 22nd Twente Student Conference on IT, Enschede, The Netherland, 23 January 2015. [Google Scholar]
- Kulkarni, A.; Sathe, S. Healthcare applications of the Internet of Things: A Review. Int. J. Comput. Sci. Inf. Technol. 2014, 5, 6229–6232. [Google Scholar]
- Samaniego, M.; Deters, R. Blockchain as a Service for IoT. In Proceedings of the 2016 IEEE international conference on internet of things (iThings) and IEEE green computing and communications (GreenCom) and IEEE cyber, physical and social computing (CPSCom) and IEEE smart data (SmartData), Berlin, Germany, 4–8 April 2016; pp. 433–436. [Google Scholar]
- Khan, M.A.; Salah, K. IoT security: Review, blockchain solutions, and open challenges. Future Gener. Comput. Syst. 2018, 82, 395–411. [Google Scholar] [CrossRef]
- Minoli, D.; Occhiogrosso, B. Blockchain mechanisms for IoT security. Int. Things 2018, 1, 1–13. [Google Scholar] [CrossRef]
- Novo, O. Blockchain meets IoT: An architecture for scalable access management in IoT. IEEE Int. Things J. 2018, 5, 1184–1195. [Google Scholar] [CrossRef]
- Ding, S.; Cao, J.; Li, C.; Fan, K.; Li, H. A novel attribute-based access control scheme using blockchain for IoT. IEEE Access 2019, 7, 38431–38441. [Google Scholar] [CrossRef]
- Pieroni, A.; Noemi, S.; Brilli, M. Industry 4.0 revolution in autonomous and connected vehicle a non-conventional approach to manage big data. J. Theor. Appl. Inf. Technol. 2018, 96, 10–18. [Google Scholar]
- Scarpato, N.; Pieroni, A.; Di Nunzio, L.; Fallucchi, F. E-health-IoT universe: A review. Management 2017, 21, 46. [Google Scholar] [CrossRef]
- Pieroni, A.; Scarpato, N.; Brilli, M. Performance Study in Autonomous and Connected Vehicles a Industry 4.0 Issue. J. Theor. & Appl. Inf. Technol. 2018, 96. [Google Scholar]
- Arcidiacono, G.; Pieroni, A. The revolution lean six sigma 4.0. Int. J. Adv. Sci. Eng. Inf. Technol. 2018, 8, 141–149. [Google Scholar] [CrossRef]
- Sumitra, B.; Pethuru, C.R.; Misbahuddin, M. A Survey of Cloud Authentication Attacks and Solution Approaches. Int. J. Innov. Res. Comput. Commun. Eng. 2014, 2, 6245–6253. [Google Scholar]
- El Mouaatamid, O.; Lahmer, M.; Belkasmi, M. Internet of Things Security: Layered classification of attacks and possible Countermeasures. Electron. J. Inf. Technol. 2016, 9, 66–80. [Google Scholar]
- Mitrokotsa, A.; Rieback, M.R.; Tanenbaum, A.S. Classifying RFID attacks and defenses. Inf. Syst. Front. 2010, 12, 491–505. [Google Scholar] [CrossRef]
- Van Oort, L. Tap Track, NFC Relay Attacks. 2016. Available online: https://www.taptrack.com/article/blog/nfc-relay-attacks/ (accessed on 10 August 2020).
- Dua, A. How Secure Is NFC Technology? 2019. Available online: https://rfid4u.com/how-secure-is-nfc-technology/ (accessed on 10 August 2020).
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 10 August 2020).
- Housley, R. Public Key Infrastructure (PKI). In Wiley Online Library; 15 April 2004; Available online: https://onlinelibrary.wiley.com/doi/abs/10.1002/047148296X.tie149 (accessed on 10 August 2020).
- Zheng, Z.; Xie, S.; Dai, H.N.; Chen, X.; Wang, H. Blockchain challenges and opportunities: A survey. Int. J. Web Grid Serv. 2018, 14, 352. [Google Scholar] [CrossRef]
- Biryukov, A.; Khovratovich, D.; Pustogarov, I. Deanonymisation of clients in Bitcoin {P2P} network. In Proceedings of the 2014 ACM SIGSAC Conference on Computer and Communications Security, Scottsdale, AZ, USA, 3–7 November 2014. [Google Scholar]
- Sasson, E.B.; Chiesa, A.; Garman, C.; Green, M.; Miers, I.; Tromer, E.; Virza, M. Zerocash: Decentralized anonymous payments from bitcoin. In Proceedings of the 2014 IEEE Symposium on Security and Privacy, San Jose, CA, USA, 18–21 May 2014; pp. 459–474. [Google Scholar]
- Jakobsson, M.; Juels, A. Proofs of Work and Bread Pudding Protocols. In Proceedings of the Secure Information Networks: Communications and Multimedia Security, Leuven, Belgium, 20–21 September 1999; Springer: Berlin, Germany; pp. 258–272. [Google Scholar]
- Cryptoslate. Proof-of-Work Coins. 2019. Available online: https://cryptoslate.com/cryptos/proof-of-work/ (accessed on 10 August 2020).
- GoChain Team. Peercoin Explained: The Proof of Stake Pioneer. Available online: https://bitfalls.com/2018/03/11/peercoin-explained-proof-stake-pioneer/ (accessed on 10 August 2020).
- Castro, M.; Liskov, B. Practical Byzantine Fault Tolerance. In Proceedings of the Third Symposium on Operating Systems Design and Implementation SE - OSDI ’99, New Orleans, LA, USA, 22–25 February 1999; USENIX Association: Berkeley, CA, USA; pp. 173–186. [Google Scholar]
- Castro, M.; Liskov, B. Practical byzantine fault tolerance and proactive recovery. Acm Trans. Comput. Syst. 2002, 20, 398–461. [Google Scholar] [CrossRef]
- Karantias, K.; Kiayias, A.; Zindros, D. Proof-of-burn. In International Conference on Financial Cryptography and Data Security; Springer: Cham, Switzerland, 2020; pp. 523–540. [Google Scholar]
- Gauld, S.; von Ancoina, F.; Stadler, R. The Burst Dymaxion. Available online: https://www.burst-coin.org/wpcontent/uploads/2017/07/The-Burst-Dymaxion1.00.pdf (accessed on 10 August 2020).
- Dziembowski, S.; Faust, S.; Kolmogorov, V.; Pietrzak, K. Proofs of space. In Annual Cryptology Conference; Springer: Berlin/Heidelberg, Germany, 2015; pp. 585–605. [Google Scholar]
- Popov, S. The Tangle, IOTA Whitepaper. White Pap. 2017. Available online: http://www.descryptions.com/Iota.pdf (accessed on 10 August 2020).
- Popov, S. Saa, Finardi, Equilibria in the Tangle. Comput. Ind. Eng. 2019, 136, 160–172. [Google Scholar] [CrossRef]
- Baird, L. The Swirlds Hashgraph Consensus Algorithm: Fair, fast, Byzantine Fault Tolerance; Technical Report SWIRLDS-TR-2016 1; Swirlds, Inc.: Richardson, TX, USA, 2016; Available online: https://www.swirlds.com/downloads/SWIRLDS-TR-2016-01.pdf (accessed on 10 August 2020).
- Buterin, V.; Dryja, T.E. Ethash. Available online: https://eth.wiki/en/concepts/ethash/ethash (accessed on 10 August 2020).
- Lee, C. Litecoin Project. Github. 2019. Available online: https://github.com/litecoin-project/litecoin (accessed on 10 August 2020).
- Van Saberhagen, N. Cryptonote v 2.0. 2013. Available online: https://cryptonote.org/whitepaper.pdf (accessed on 10 August 2020).
- The Hdac Team. Hdac: Transaction Innovation—IoT Contract & M2M Transaction Platform based on Blockchain. 2018. Available online: https://github.com/Hdactech/doc/wiki/Whitepaper (accessed on 10 August 2020).
- The Lynx Team. Technical White Paper 1.1. White Pap. 2019. Available online: http://cdn.getlynx.io/2019-03-17_Lynx_Whitepaper_v1.1.pdf (accessed on 10 August 2020).
- Komodo Team. Komodo: An Advanced Blockchain Technology, Focused on Freedom. Available online: https://komodoplatform.com/wp-content/uploads/2018/05/2018-05-09-Komodo-White-Paper-Full.pdf (accessed on 10 August 2020).
- Octavian Oncescu. Purple Protocol—A Scalable Platform for Decentralized Applications and Tokenized Assets. Available online: https://purpleprotocol.org/whitepaper/ (accessed on 10 August 2020).
- Diaz, D.; Duffield, E. The Dash Whitepaper. Available online: https://github.com/dashpay/dash/wiki/Whitepaper (accessed on 10 August 2020).
- Mazieres, D. The stellar consensus protocol: A federated model for internet-level consensus. Stellar Dev. Found. 2015, 32. Available online: http://www.scs.stanford.edu/~dm/20160606-scp-talk.pdf (accessed on 10 August 2020).
- Kwon, J.; Buchman, E. Cosmos: A Network of Distributed Ledgers. Available online: https://cosmos.network/resources/whitepaper (accessed on 10 August 2020).
- Pike, D.; Nosker, P.; Boehm, D.; Grisham, D.; Woods, S.; Marston, J. Proof-of-Stake-Time Whitepaper. Available online: https://www.vericoin.info/downloads/VeriCoinPoSTWhitePaper10May2015.pdf (accessed on 10 August 2020).
- Shield. PoS Boo, MNs and QP in Detail. Available online: https://medium.com/@shieldxsh/pos-boo-mns-and-qp-in-detail-6b9e61e3acee (accessed on 10 August 2020).
- StakeNet Team. Trustless Proof of Stake (TPoS), Wallet Staking and Pooled Staking. Available online: https://stakenet.io/TPoS_Factsheet.pdf (accessed on 10 August 2020).
- Ren, L. Proof of Stake Velocity: Building the Social Currency of the Digital Age. Self-Published White Paper. Available online: https://www.cryptoground.com/storage/files/1528454215-cannacoin.pdf (accessed on 10 August 2020).
- Kiayias, A.; Russell, A.; David, B.; Oliynykov, R. Ouroboros: A provably secure proof-of-stake blockchain protocol. In Lecture Notes in Computer Science (including subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics), 37th Annual International Cryptology Conference, Santa Barbara, CA, USA, 20–24 August 2017; Springer: Berlin, Germany, 2017; pp. 357–388. [Google Scholar]
- The Tron Foundation. Advanced Decentralized Blockchain Platform. Available online: https://tron.network/static/doc/white_paper_v_2_0.pdf (accessed on 10 August 2020).
- Schuh, F.; Larimer, D. Bitshares 2.0: General Overview. Available online: http://docs.bitshares.org/downloads/bitshares-general.pdf (accessed on 10 August 2020).
- Larimer, D.; Scott, N.; Zavgorodnev, V.; Johnson, B.; Calfee, J.; Vandeberg, M. Steem An Incentivized, Blockchain-based Social Media Platform. 2016. Available online: https://assets.ctfassets.net/sdlntm3tthp6/resource-asset-r407/41cc9041e3d76a683feba1bc33ce5fdf/26069ed0-86be-43a3-9fb2-1523d3b52512.pdf (accessed on 10 August 2020).
- ARK.io. Ark Ecosystem Whitepaper. Available online: https://ark.io/Whitepaper.pdf (accessed on 10 August 2020).
- Beddows, O.; Kordek, M. The Lisk Protocol. Available online: https://lisk.io/documentation/lisk-protocol/index.html (accessed on 10 August 2020).
- Larimer, D. EOS. IO Technical White Paper. Available online: https://github.com/EOSIO/Documentation (accessed on 10 August 2020).
- Team, Z. The Zilliqa Technical Whitepaper. Retrieved Sept. 2017, 16, 2019. [Google Scholar]
- Steeley, L. Introduction to Sawtooth PBFT. Available online: https://www.hyperledger.org/blog/2019/02/13/introduction-to-sawtooth-pbft (accessed on 10 August 2020).
- NEO White Paper: A Distributed Network for the Smart Economy. Available online: https://docs.neo.org/docs/en-us/basic/whitepaper.html (accessed on 10 August 2020).
- Rogaway, P.; Shrimpton, T. Cryptographic hash-function basics: Definitions, implications, and separations for preimage resistance, second-preimage resistance, and collision resistance. In International Workshop on Fast Software Encryption; Springer: Berlin/Heidelberg, Germany, 2004; pp. 371–388. [Google Scholar]
- Wang, M.; Duan, M.; Zhu, J. Research on the Security Criteria of Hash Functions in the Blockchain. In Proceedings of the 2nd ACM Workshop on Blockchains, Cryptocurrencies, and Contracts, ACM Asia Conference on Computer and Communications Security, Incheon, Korea, 4–8 June 2018; Association for Computing Machinery: New York, NY, USA, 2018. [Google Scholar]
- Rachmawati, D.; Tarigan, J.T.; Ginting, A.B.C. A comparative study of Message Digest 5(MD5) and SHA256 algorithm. In Proceedings of the Journal of Physics: Conference Series, 2nd International Conference on Computing and Applied Informatics 2017, Medan, Indonesia, 28–30 November 2017; IOP Publishing: Bristol, UK, 2018. [Google Scholar]
- Gupta, P.; Kumar, S. A comparative analysis of SHA and MD5 algorithm. Architecture 2014, 1, 5. [Google Scholar]
- Eastlake, D.; Jones, P. US Secure Hash Algorithm 1 (SHA1). RFC Editor, USA. Available online: https://dl.acm.org/doi/book/10.17487/RFC3174 (accessed on 10 August 2020).
- Kircanski, A.; Shen, Y.; Wang, G.; Youssef, A.M. Boomerang and slide-rotational analysis of the SM3 hash function. In International Conference on Selected Areas in Cryptography; Springer: Berlin/Heidelberg, Germany, 2012; pp. 304–320. [Google Scholar]
- Boneh, D. Twenty years of attacks on the RSA cryptosystem. Not. AMS 1999, 46, 203–213. [Google Scholar]
- Koblitz, N. Elliptic curve cryptosystems. Math. Comput. 1987, 48, 203–209. [Google Scholar] [CrossRef]
- Belinky, M.; Rennick, E.; Veitch, A. The Fintech 2.0 Paper: Rebooting Financial Services. Santander InnoVentures/Oliver Wyman/Anthemis. 2015. Available online: https://www.oliverwyman.com/content/dam/oliver-wyman/global/en/2015/jun/The_Fintech_2_0_Paper_Final_PV.pdf (accessed on 10 August 2020).
- Kaminsky, D. Black ops of TCP/IP 2011. Black Hat USA 2011. Available online: https://www.slideshare.net/dakami/black-ops-of-tcpip-2011-black-hat-usa-2011 (accessed on 10 August 2020).
- consultancy.uk. Blockchain Technology: How it Works, Main Advantages and Challenges. Available online: https://www.consultancy.uk/news/13484/blockchain-technology-how-it-works-main-advantages-and-challenges (accessed on 10 August 2020).
- coin.dance. Bitcoin Legality by Country. Available online: https://coin.dance/poli/legality (accessed on 10 August 2020).
- TheTIE. Exchange Real Trading Volume Investigation. Available online: https://docs.google.com/spreadsheets/d/13_L5V9elxQ3xps62BeYVyr_Wu-9vfyAyN5tGqLNoV9Y/edit#gid=1415549973 (accessed on 10 August 2020).
- Visa.com. Visa Acceptance for Retailers. Available online: https://usa.visa.com/run-your-business/small-business-tools/retail.html (accessed on 10 August 2020).
- Evans, D. The internet of things: How the next evolution of the internet is changing everything. Cisco White Pap. 2011, 1, 1–11. [Google Scholar]
- Bahga, A.; Madisetti, V.K. Blockchain platform for industrial internet of things. J. Softw. Eng. Appl. 2016, 9, 533–546. [Google Scholar] [CrossRef]
- Pieroni, A.; Scarpato, N.; Di Nunzio, L.; Fallucchi, F.; Raso, M. Smarter city: Smart energy grid based on blockchain technology. Int. J. Adv. Sci. Eng. Inf. Technol. 2018, 8, 298–306. [Google Scholar] [CrossRef]
- Orecchini, F.; Santiangeli, A.; Zuccari, F.; Pieroni, A.; Suppa, T. Blockchain technology in smart city: A new opportunity for smart environment and smart mobility. In International Conference on Intelligent Computing & Optimization; Springer: Cham, Switzerland, 2018; pp. 346–354. [Google Scholar]
- Atlam, H.F.; Alenezi, A.; Alassafi, M.O.; Wills, G. Blockchain with internet of things: Benefits, challenges, and future directions. Int. J. Intell. Syst. Appl. 2018, 10, 40–48. [Google Scholar] [CrossRef]
- Reyna, A.; MartíN, C.; Chen, J.; Soler, D. On blockchain and its integration with IoT. Challenges and opportunities. Future Gener. Comput. Syst. 2018, 88, 173–190. [Google Scholar]
- CoinMarketCap. IOTA Capitalization. Available online: https://coinmarketcap.com/currencies/iota/ (accessed on 10 August 2020).
- Douceur, J.R. The sybil attack. In International Workshop on Peer-to-Peer Systems; Springer: Berlin/Heidelberg, Germany, 2002; pp. 251–260. [Google Scholar]
- Brewer, E. CAP twelve years later: How the“ rules” have changed. Computer 2012, 45, 23–29. [Google Scholar]
- Vechain Whitepaper. Available online: https://whitepaper.io/document/578/vechain-whitepaper (accessed on 10 August 2020).
- DNV GL Buys Stake in VeChain and Announces Authority Masternode Status Medium. Available online: https://medium.com/@bsc44/dnv-gl-buys-stake-in-vechain-and-announces-authority-masternode-status-c42992a16a2e (accessed on 10 August 2020).
- Cahrenheit. Introducing Cahrenheit. Medium. 2018. Available online: https://medium.com/@Cahrenheit/introducing-cahrenheit-cb017bf5dd6b (accessed on 10 August 2020).
- Waltonchain White Paper (V 1.0.4). Available online: https://www.digitalcoindata.com/whitepapers/walton-whitepaper.pdf (accessed on 10 August 2020).
- IoTeX: A Decentralized Network for Internet of Things Powered by a Privacy-Centric Blockchain. 2018. Available online: https://whitepaper.io/document/131/iotex-whitepaper (accessed on 10 August 2020).
- Herrero-Collantes, M.; Garcia-Escartin, J.C. Quantum random number generators. Rev. Mod. Phys. 2017, 89, 015004. [Google Scholar]
- CoinMarketCap. IoTChain Capitalization. Available online: https://coinmarketcap.com/currencies/iot-chain/ (accessed on 10 August 2020).
- IoTChain Whitepaper. Available online: https://iotchain.io/whitepaper/ITCWHITEPAPER.pdf (accessed on 10 August 2020).
- Buterin, V. A next-generation smart contract and decentralized application platform. White Pap. 2014, 3. Available online: https://people.cs.georgetown.edu/~clay/classes/fall2017/835/papers/Etherium.pdf (accessed on 10 August 2020).
- Liu, C.; Wang, D.; Wu, M. Vite: A High Performance Asynchronous Decentralized Application Platform. Available online: https://static.coinpaprika.com/storage/cdn/whitepapers/6393951.pdf (accessed on 10 August 2020).
- The Nucleus Team. Connecting the unconnected. White Pap. 2018. Available online: https://cryptorating.eu/whitepapers/Nucleus-Vision/light-paper.pdf (accessed on 10 August 2020).
- Ruff IoT Blockchain Whitepaper. Available online: https://cryptorating.eu/whitepapers/Ruff-Chain/WhitePaper.html (accessed on 10 August 2020).
- Data Integrity for Supply Chain Operations, Powered by Blockchain Technology. Available online: https://modum.io/sites/default/files/documents/2018-05/modum-whitepaper-v.-1.0.pdf?utm_source=icogrind (accessed on 10 August 2020).
- Decentralized Infrastructure for Next Generation Internet of Things. Available online: https://cpchain.io/download/CPChain_Whitepaper_English.pdf/ (accessed on 10 August 2020).
- Yee: A Blockchain-Powered & Cloud based Social Ecosystem. Available online: https://doc.yeeco.io/YeeCo-V0.2-EN.pdf (accessed on 10 August 2020).
- Li, Z.; Kang, J.; Yu, R.; Ye, D.; Deng, Q.; Zhang, Y. Consortium Blockchain for Secure Energy Trading in Industrial Internet of Things. IEEE Trans. Ind. Inform. 2018, 14, 3690–3700. [Google Scholar]
- Aitzhan, N.Z.; Svetinovic, D. Security and privacy in decentralized energy trading through multi-signatures, blockchain and anonymous messaging streams. IEEE Trans. Dependable Secur. 2018, 15, 840–852. [Google Scholar]
- Griggs, K.N.; Ossipova, O.; Kohlios, C.P.; Baccarini, A.N.; Howson, E.A.; Hayajneh, T. Healthcare blockchain system using smart contracts for secure automated remote patient monitoring. J. Med. Syst. 2018, 42, 130. [Google Scholar]
- Rahman, M.A.; Hossain, M.S.; Loukas, G.; Hassanain, E.; Rahman, S.S.; Alhamid, M.F.; Guizani, M. Blockchain-based mobile edge computing framework for secure therapy applications. IEEE Access 2018, 6, 72469–72478. [Google Scholar]
- Kusiak, A. Smart manufacturing. Int. J. Prod. 2018, 56, 508–517. [Google Scholar]
- Liu, X.L.; Wang, W.M.; Guo, H.; Barenji, A.V.; Li, Z.; Huang, G.Q. Industrial blockchain based framework for product lifecycle management in industry 4.0. Robot.-Comput.-Integr. Manuf. 2020, 63, 101897. [Google Scholar] [CrossRef]
- Mistry, I.; Tanwar, S.; Tyagi, S.; Kumar, N. Blockchain for 5G-enabled IoT for industrial automation: A systematic review, solutions, and challenges. Mech. Syst. Signal Process. 2020, 135, 106382. [Google Scholar] [CrossRef]
- Pillai, A.; Sindhu, M.; Lakshmy, K.V. Securing firmware in Internet of Things using blockchain. In Proceedings of the 2019 5th International Conference on Advanced Computing & Communication Systems (ICACCS), Tamil Nadu, India, 15–16 March 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 329–334. [Google Scholar]
- Kim, H.M.; Laskowski, M. Toward an ontology-driven blockchain design for supply-chain provenance. Intell. Syst. Account. Financ. Manag. 2018, 25, 18–27. [Google Scholar] [CrossRef]
- Kshetri, N. 1 Blockchain’s roles in meeting key supply chain management objectives. Int. J. Inf. Manag. 2018, 39, 80–89. [Google Scholar] [CrossRef]
- Iazeolla, G.; Pieroni, A. Energy saving in data processing and communication systems. Sci. World J. 2014, 2014, 452863. [Google Scholar] [CrossRef] [PubMed]
- Pieroni, A.; Iazeolla, G. Engineering QoS and energy saving in the delivery of ICT services. In Sustaining Power Resources through Energy Optimization and Engineering; IGI Global: Hershey, PA, USA, 2016. [Google Scholar]
- Iazeolla, G.; Pieroni, A. Power management of server farms. Appl. Mech. Mater. 2014, 492, 453–459. [Google Scholar] [CrossRef]
- Bracciale, L.; Loreti, P.; Detti, A.; Paolillo, R. Melazzi Lightweight named object: An ICN-based abstraction for IoT device programming and management. IEEE Internet Things J. 2019, 6, 5029–5039. [Google Scholar] [CrossRef]
- Arcidiacono, G.; De Luca, E.W.; Fallucchi, F.; Pieroni, A. The use of Lean Six Sigma methodology in digital curation. In Proceedings of the First Workshop on Digital Humanities and Digital Curation Co-Located with the 10th Conference on Metadata and Semantics Research (MTSR 2016), Goettingen, Germany, 22 November 2016. [Google Scholar]
- Ferroni, P.; Zanzotto, F.M.; Riondino, S.; Scarpato, N.; Guadagni, F.; Roselli, M. Breast cancer prognosis using a machine learning approach. Cancers 2019, 11, 328. [Google Scholar] [CrossRef]
- Ferroni, P.; Zanzotto, F.M.; Scarpato, N.; Riondino, S.; Nanni, U.; Roselli, M.; Guadagni, F. Risk Assessment for Venous Thromboembolism in Chemotherapy-Treated Ambulatory Cancer Patients. Med Decis. Mak. 2016, 37, 234–242. [Google Scholar] [CrossRef]
- Guadagni, F.; Scarpato, N.; Patrizia, F.; D’Ottavi, G.; Boavida, F.; Roselli, M.; Garrisi, G.; Lisi, A. Personal and sensitive data in the e-health-IoT universe. In International Internet of Things Summit; Springer: Cham, Switzerland, 2015; pp. 504–514. [Google Scholar]
- Cardarilli, G.C.; Nunzio, L.D.; Fazzolari, R.; Giardino, D.; Matta, M.; Patetta, M.; Re, M.; Spanò, S. Approximated computing for low power neural networks. Telkomnika 2019, 17, 1236–1241. [Google Scholar] [CrossRef]
- Cardarilli, G.C.; Di Nunzio, L.; Fazzolari, R.; Re, M.; Silvestri, F.; Spanò, S. Energy consumption saving in embedded microprocessors using hardware accelerators. Telkomnika 2018, 16, 1019–1026. [Google Scholar] [CrossRef][Green Version]

| Attack | Cloud | RFID | NFC | Blockchain |
|---|---|---|---|---|
| Wrapping | X | |||
| Eavesdropping | X | X | X | |
| Flooding | X | |||
| Stealing Account | X | |||
| MITTM | X | X | X | |
| Browser | X | |||
| Reflection | X | |||
| Session Hijacking | X | |||
| Replay | X | X | X | |
| Brute force | X | |||
| DoS/DDoS | X | X | X | |
| Skimming | X | |||
| Phishing | X | X | X | |
| User tracking | X | |||
| Spoofing | X | X |
| PoW | PoS | DPoS | pBFT | |
|---|---|---|---|---|
| Type | Permissionless | Both | Both | Permissioned |
| Scalability | Medium | High | High | Low |
| Finality | Probabilistic | Probabilistic | Probabilistic | Deterministic |
| Transaction/s | Low | High | High | High |
| Project | PoW | ~PoW | PoS | ~PoS | DPoS | ~DPoS | pBFT | ~pBFT |
|---|---|---|---|---|---|---|---|---|
| Bitcoin [21] | SHA256 | |||||||
| Ethereum [37] | Ethash | |||||||
| Litecoin [38] | Scrypt | |||||||
| Monero [39] | CryptoNight | |||||||
| HDAC [40] | EPoW | |||||||
| Lynx [41] | HPoW | |||||||
| Komodo [42] | dPoW | |||||||
| Purple [43] | SSPoW | |||||||
| Dash [44] | X | |||||||
| Stellar [45] | X | |||||||
| Cosmos [46] | X | |||||||
| Vericoin [47] | PoST | |||||||
| Shield [48] | PoS Boo | |||||||
| XSN [49] | TPoS | |||||||
| Reddcoin [50] | PoSV | |||||||
| Cardano [51] | Ouroboros CA | |||||||
| Tron [52] | X | |||||||
| Bitshares [53] | X | |||||||
| Steem [54] | X | |||||||
| Ark [55] | X | |||||||
| Lisk [56] | X | |||||||
| EOS [57] | BFT DPoS | BFT DPoS | ||||||
| Zilliqa [58] | X | |||||||
| Sawtooth [59] | X | |||||||
| Neo [60] | DBFT |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Pieroni, A.; Scarpato, N.; Felli, L. Blockchain and IoT Convergence—A Systematic Survey on Technologies, Protocols and Security. Appl. Sci. 2020, 10, 6749. https://doi.org/10.3390/app10196749
Pieroni A, Scarpato N, Felli L. Blockchain and IoT Convergence—A Systematic Survey on Technologies, Protocols and Security. Applied Sciences. 2020; 10(19):6749. https://doi.org/10.3390/app10196749
Chicago/Turabian StylePieroni, Alessandra, Noemi Scarpato, and Lorenzo Felli. 2020. "Blockchain and IoT Convergence—A Systematic Survey on Technologies, Protocols and Security" Applied Sciences 10, no. 19: 6749. https://doi.org/10.3390/app10196749
APA StylePieroni, A., Scarpato, N., & Felli, L. (2020). Blockchain and IoT Convergence—A Systematic Survey on Technologies, Protocols and Security. Applied Sciences, 10(19), 6749. https://doi.org/10.3390/app10196749







