Abstract
The security of cryptographic protocols has always been an important issue. Although there are various verification schemes of protocols in the literature, efficiently and accurately verifying cryptographic protocols is still a challenging research task. In this work, we develop a formal method based on dynamic epistemic logic to analyze and describe cryptographic protocols. In particular, we adopt the action model to depict the execution process of the protocol. To verify the security, the intruder’s actions are analyzed. We model exactly the protocol applying our formal language and give the verification models according to the security requirements of this cryptographic protocol. With analysis and proof on a selected example, we show the usefulness of our method. The result indicates that the selected protocol meets the security requirements.
1. Introduction
The security of cryptographic protocols is crucial in the design of the protocols as cryptographic protocols need to consider attacks from attackers. If there is any security flaw in a cryptographic protocol, the protocol can be attacked by attackers or intruders. Therefore, the security verification of cryptographic protocols is particularly important for checking whether the protocol meets security goals. To verify the security of cryptographic protocols, there are many methods. In these methods, logic-based methods play an important role. There are many works of literature (e.g., [1,2,3,4,5]) on the application of logical methods to analyze and verify cryptographic protocols. The earliest analysis method of logic is based on the Dolev-Yao model [6]. It is well known that the Dolev-Yao model opens the way for the study of formalization. Since then, a variety of cryptographic protocol analysis methods based on logic have come out. Most of the protocols analyzed by epistemic logic are authentication protocols in the existing literature. They use the method of model checking to analyze. For example, in the paper [7], the researchers propose two virtual agents to complete encryption and decryption, and construct a model checker to check the protocol. In other papers, KD45 system’s belief logic is used. It needs to describe the belief logic of the protocol, and then establish reasoning rules to infer the security of the protocol.
In particular, the cryptographic protocol we mentioned here refers to the protocol using classical cryptography. With the research of quantum computer, quantum cryptography is a research trend. The latest development of quantum cryptography was given in the paper [8]. This article introduced a lot about quantum key distribution (QKD). Similarly, Davide Bacco and Beatrice Da Lio et al. were also doing research on quantum key distribution [9]. They illustrated how to use QKD technology to break through the limitation of low key rate and produce high key rate on a 37-core fiber. At present, the wide application of quantum technology has great challenges. Security verification of quantum cryptography protocol may be more challenging. It will be our next research content. Now, we construct an accurate dynamic epistemic logic language to describe the protocol with classical cryptography and give the action model according to the action characteristics. The action model is used to accurately describe the protocol action, and the execution process of the protocol action is the operation process of the protocol. The execution process of action is also expressed clearly and intuitively, so the whole operation process of the cryptographic protocol is completely formalized. Our verification does not need complex rules and reasoning, only through the action description table can get the results.
We summarize our work as follows:
- Applying dynamic epistemic logic, a formal language is developed to describe the cryptographic protocol. The syntax and semantics of this language are given. Cryptographic primitives and special propositions are built.
- The action model is constructed to display action elements. Through update execution, the model is updated. The execution of actions results in changes between models. We model the protocol accurately. In a sense, the logic description is the logic analysis for cryptographic protocols.
- With a logical language and the action model, a specific example is verified. The protocol is that a secret message is transmitted between two users who only have their own key. The goal of the protocol is that only the two users know the secret message and the outside intruder can not know the secret message after the execution of the protocol. We give the goal models. Through analysis and proof, we show that the protocol meets the intended requirements and the protocol is secure.
The rest of the paper is arranged as follows. The second section displays related work about verification and analysis of the cryptographic protocol. The third section demonstrates a logic language we develop and the related basic knowledge. In Section 4, we present a specific cryptographic protocol and formalize it. Section 5 presents the verification process of the cryptographic protocol. In Section 6, we give our conclusion and expectation.
2. Related Work
Since the Dolev-Yao model created a way of logical analysis for the cryptographic protocol, all kinds of logical analysis methods for cryptographic protocol have been introduced. The BAN (Burrows, Abadi and Needham) logic [1] is a pioneer. BAN logic verifies the security of cryptographic protocol by the formal method. This initiative has greatly stimulated the interest of researchers in the formal analysis of cryptographic protocols, and has become a milestone in the analysis of cryptographic protocols. The formalization of BAN logic is built on multiple types of model logic. In the paper [1], they gave a set of reasoning rules firstly based on the BAN logic. They analyzed the security of protocols by beliefs deduction. In the follow up research, many drawbacks in the BAN logic were found. So, the BAN logic is extended to GNY logic [10], VO logic [11] and MB logic [12]. BAN logic is constantly improved in application. Today, BAN logic is still used as a verification tool for security protocols or authentication protocols in radio frequency identification systems [13], Internet of things systems [14,15], and remote authentication protocols [16].
AT logic [17] was proposed by Abadi and Tuttle. The problem of BAN logic is improved in the AT logic in terms of syntax, semantics and rules. The paper [18] and the book [19] employed SVO logic to analyze cryptographic protocols. The SVO logic has more strict definitions about the protocol logic. The protocol model based on the SVO logic has a wider range of applications.
There still are many logics for analyzing cryptographic protocols, such as non-monotonic logic [20], time-dependent cryptographic protocol logic [21], protocol composition logic [22] and so on. In all logic analysis, there are four analysis types to find attacks in cryptographic protocols.
Finding a new attack by inductive proof, the authors of [2] analyzed three protocols: a recursive protocol, Needham–Schroeder protocol, and Otway–Rees. Lowea’s attack and a new attack were discovered. Another paper [23] also analyzed two variants of Yahalom.
The authors of [4] used rewriting calculus to display the Needham–Schroeder Public-Key protocol. With rewrite rules, they gave all actions in the protocol for all agents, including attackers. By these strategies and a set of rewrite rules, they could find attacks in the protocol.
There have been many works of literature (e.g., [24,25,26,27,28]) that employ process calculus. Typed process calculus displays security information (e.g., [29,30,31,32,33]) by the idea of standard static-analysis. On operating cryptographic data, static-analysis has some inadequacies. So, the work in [34] improved the solution of these operations. They described the protocols and gave proof for the security of the protocols based on the typed process calculus.
Model checking is still a widely used method to verify protocol security. The authors of [3] proposed a method that uses abstract data and deductive rules to prove the results of model checkers. Hans van Ditmarsch et al. [7] developed a dynamic epistemic model checker. In the follow-up work (e.g., [7,35,36]), many researchers verified and analyzed security protocols with dynamic epistemic logic. The authors of [37] proposed a variant of epistemic logic methods to verify authentication protocols.
At present, the development and application of logic go far beyond the field of philosophy [38,39,40]. Dynamic epistemic logic has been widely used in philosophy, sociology and computer science [41,42,43,44,45,46,47], and also in the verification and analysis of security protocols (see [7,36,37,48]).
Although many scholars have done a lot of work in this field, none of them is once and for all. Different protocols need different methods to analyze or verify. In this paper, dynamic epistemic logic is used to describe and analyze a specific cryptographic protocol, so as to effectively verify the security of the protocol.
3. A Dynamic Epistemic Language for Cryptographic Protocols
We develop a language based on the dynamic epistemic logic to describe cryptographic protocols. We extend the epistemic logic with the action model (that refers to the paper [49]). The structure of propositions is refined by three predicates ‘has’, ‘const’ and ‘tg’ (‘has’ denotes an agent a certain message, ‘const’ denotes a certain message can be derived from the agent’s information set and ‘tg’ denotes to an action in the cryptographic protocol that has been performed).
We define this language as , where means cryptography, A is a set of agents, and the set of the agents at epistemic states who are participants in the protocol we want to analyze. We use to denote a set of actions.
3.1. Syntax of the Language
Before giving the syntax of the language, we define some basic concepts about this language.
Definition 1
(Message). M is taken as the set of messages.
Message m in the protocol as logic term is defined by:
where n is a nonce or encoding of a message in ASCII; generally, n denotes a plain message. Also, k is crypto-key. is the encryption of m with key k (ciphertext message) and intuitively, represents concatenating of m and .
Definition 2
(Propositions). In this system, the set as the set of basic propositions p that is defined by:
where , and . means agent a possesses message m (the message is received by agent a or initial distribution). means agent a can construct m from the messages he possesses. denotes action σ is tagged. Let , , , be subsets of that contain the above three propositions, respectively. Then, we will define action models.
We will give a definition of about action models according to the idea of the paper [49,50]. The condition of an action execution is called . Without corresponding preconditions, the action can not be executed. In this system, all preconditions belong to , which is a part of the language .
Facts that will hold after the execution of an action are called . Postcondition displays the changing of basic facts after running the action. Postcondition is divided into two parts: the one is that shows changes for the information sets including messages that are sent by the agents, another is , which illustrates the changes for action labels that show the actions have been performed by the agents.
Definition 3
(Action model). Based on the logical language , an action model is a structure: , where is non-empty and finite set of actions, is an equivalence relation (reflexive, symmetric and transitive) on for all . assigns a propositional precondition for every action. We employ the idea of paper [49] to deal with the postcondition. Φ is a set of propositions for the language . For the sake of simplicity of description, we will use a substitution in this model structure. Function is a substitution for . It maps basic propositions of the language to their variant. The ) is taken as a set of substitutions from Φ to . So, gives a substitution for that has property for all and . gives a substitution for , which has the property that for all and .
We replace ‘’ with ‘’ for the substitution mapping to ⊤. Meanwhile, the message m is added to the information set of agent a after the execution of the action.
We write ‘’ to tag current action for the substitution mapping to ⊤, and similarly, we use ‘’ to tag premise action for the substitution mapping to ⊥. This will label (unlabel) σ after the execution of the action. We will use these substitutions to formalize all postconditions in the protocol.
Definition 4
(Syntax of the language ). Given are agents A and atoms . Formulas of the language are defined by:
where , , σ () is an action in the action model .
The meaning of the formulas is the same as that of ordinary dynamic epistemic logic. means agent a knows φ. means after the execution of action σ in , φ holds.
3.2. Semantics of the Language
Definition 5
(Models of the language ). The model is a tuple:
where W is a non-empty set of a possible world, is binary equivalence relations on W for all , I means information sets, means that agent a possesses the set of information at the world w, that is . denotes the action label that is . For , means action σ in the set has been tagged.
I and correspond to the valuation of basic propositions. If , is satisfied at the world w. The m is the message that agent a possesses by receiving or by some initial distribution. Message m is also constructed by the agent from messages in his information set. That is . In the following, we cite the idea of the paper [51] and give the construction rules.
Definition 6
(Construction rules in the cryptography). There are many rules determining which messages an agent can construct from his information set:
where denotes a message m encrypted with key k. denotes concatenation of two messages. In these expressions, above the line is the condition, below the line is the result. The first one says, if an agent has message m and a key k in his information set, he should be able to construct . The others are similar and will not be described.
The satisfaction relations of basic propositions are defined as follows.
Definition 7
(Semantics of basic propositions). Let be a model for .
iff
iff
iff
The first one says if the model satisfies agent a possesses message m in the world w, if and only if (iff), m is in information set of agent a in the world w. The second says agent a constructs m at , if and only if, m can be derived from the information set of agent a at the world w. denotes that can be derived from . The last one illustrates that holds at , if and only if, σ is tagged at the world w.
Having different basic propositions at the different world displays the transformation between models. This updating execution is defined as follows.
Definition 8
(Updated model). Let be a model for and be an action model, the updated model is defined by:
Definition 9
(Semantics of the language ). Given are epistemic state with , and action model . Semantics for formulas of the language are defined by:
iff true
iff
iff
iff for all v, if
iff if
4. Formalizing Cryptographic Protocol
4.1. The Verification Problem of the Cryptographic Protocol
Protocol description: We use to denote the cryptographic protocol. Actually, the execution process of a protocol is a sequence of actions. In cryptography, a protocol is described as the form (agent ‘A sends message m to B’), where is a message that has a certain pattern. These patterns have been defined as definition 1 in the specific system.
Instantiations: Action pattern is an important part in the execution of the cryptography. We usually instantiate action patterns by . is a map from the parameters of the protocol to their respective domain. An execution of a protocol can have several instantiations interleaving. In this system, we employ to denote a set of all instantiations. In this protocol, the number of parameters is finite, and is too.
Network environment: We assume that the network on which the protocol can be run consists of an input-buffer and an output-buffer just as that defined in the work [52]. We take the two parts as two special agents and . In the protocol, the trusted agents can only send a message to . The attacker or intruder could eavesdrop messages from . The trusted agents receive messages from .
The verification model: The verification model is the model for this protocol to archive the goal pattern. After running of the protocol , a requirement () should hold. So, we formalize the verification model as below:
where
- is a model that we have defined previously, including all assumptions at the initial state, and all epistemic information for all the agents.
- denotes the action model. denotes intruder’s actions. This action model consists of all the actions in the protocol and all possible intruder’s actions.
- is an action in the action model (generally the final one).
- is an -formula. The formulas are either static epistemic formulas or propositions.
means after an execution of all possible actions in the model , holds. This is the model of the protocol goals.
4.2. Modeling Action Models
The changes of the language model depend on the action execution in the protocol. That is to say, the action execution results in a change of model. So, we firstly give the action model. We have given the initial model and the action model . Assuming set be the set of agents in this protocol, we will take T as the intruder’s name that performs the intruder’s actions. So, in this system, , and .
We give the action model . Intruder’s actions and actions of the protocol requirement are conducted according to the intruder model and the protocol specification from the set of the actions in .
In the protocol, means that agent a sends message m to agent b. We split the action into two parts: ‘’ and ‘’ . The preconditions of actions for execution are that agent a can construct m from his information set: . Postcondition of the action is . We use or to mark or unmark actions. Similarly, the precondition of action is: . We stipulate that the buffer can not construct any new message. Postcondition of is: and a possible action marking. A specific action in is transformed into a parameterized set of the action model. We will model the intruder’s actions.
Intruder’s actions: In the network model, we assume the intruder can eavesdrop all information from the buffer. So, the form of intruder’s actions is either or . That is to say, on the one hand, the intruder can take any message from the in-buffer; on the other hand, the intruder can construct any message and put it into the out-buffer. These actions are described as parameterized actions in the action model as Table 1.

Table 1.
Action model of the intruder.
Epistemic relations between actions: In the system, an agent can only distinguish the actions that he has performed. The other actions are indistinguishable for the agent. We use to denote indistinguishable epistemic relation between actions for all agent a. We will construct to display indistinguishable actions for the intruder.
Initial Model: In the protocol, at the initial state, details in the model can be described as below.
- W: a non-empty set of worlds.
- : Let if and only if ( is equivalence relations for a or a can not distinguish w from v).
- I: I is the set of information for the agents. We say an agent’s information set is always based on a certain world. So, any agent a (except the buffer) and its information set I define a world w. Generally, we write it as . In the initial state, we stipulate the buffer is empty. Therefore,
- : In the initial model, we let , for all .
In the following, we will analyze a specific cryptographic protocol with the formalization method on the above-mentioned.
4.3. Analysis of a Specific Cryptographic Protocol
In an insecure network, Alice has a secret message m and wants to send it to Bob. They only have their own key. We call Alice as Sender (S) and Bob as Receiver (R). The Sender has her own key . The Receiver has his own key . They only can decrypt data that is encrypted by himself. This protocol is as below.
At the first step, Sender encrypts m with and gets . For simplicity, we write as . Then, the Sender sends to Receiver. After it is recieved, the Receiver encrypts with and gets . is sent back to Sender. Sender decrypts and gets . At the last step, Sender sends to Receiver. Receiver can decrypt and gets m. Finally, m is transmitted from S to R. We apply the encryption that is commutative: . Here, the key can be a symmetric key or asymmetric key. We formalize this protocol. In this protocol, , , where, S is the Sender, R is the Receiver, T is an intruder. At first, we give the initial model figure and then formalize the execution of the protocol according to the actions of the protocol itself.
In the protocol, we have . However, in the initial state, only S has m, others do not have m. We give a figure to display which agent has secret message m. According to , we draw the picture. Each world w is expressed by the agent name that has m. The initial model is shown in Figure 1.
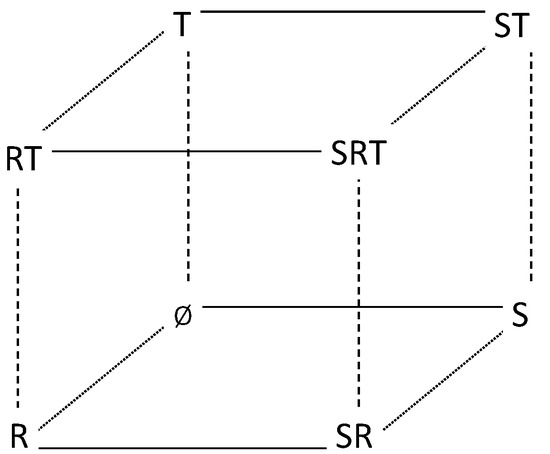
Figure 1.
Initial model of the protocol.
In Figure 1, the solid lines present the worlds at both ends are distinguishable for S, and the dotted lines are for R. The dashed lines are for T. Accordingly, the dotted lines and the dashed lines are indistinguishably a relation for S. The solid lines and the dashed lines are indistinguishably a relation for R. The solid lines and the dotted lines are indistinguishability relation for T.
So, we have in the initial state.
Table 2 describes actions that are stipulated in the protocol. Now, we add actions from intruder(T) in Table 3. We assume the intruder is a weak intruder. He can not do anything but eavesdropping. He only can get all messages from In-buffer and forward it to Out-buffer. He can not construct any other message because he does not have any key.

Table 2.
Action model in the protocol.

Table 3.
Action model including intruder’s actions.
5. Verification of the Protocol
5.1. The Protocol Targets
In the initial state, S and R have their own key. Only S has a secret message m. Our goal is that R will have m but T can not have m after the execution of all actions. So, we give the target formulas.
Target 1: After the execution of the last action , R will have secret message m.
Target 2: T does not have m at the initial state. After execution of the last action , T still does not have secret message m.
If this protocol satisfies Target 1 and 2, then the protocol is secure.
5.2. Verification of the Protocol
Proposition 1.
For any set of message terms M, and any secret message m: without k, if then .
Proof.
From the construction rules, if an agent has and corresponding k then he can compute m. Without k, if m can not be derived form M, then m can not be constructed even if is added, because of lacking a premise condition. According to this proposition, T can not compute secret message m, because all messages he has from the In-buffer are encrypted data and he does not have the corresponding k. □
In this system, messages in the information set for any agent are always increasing and never decreasing or deleting. So, we have:
Proposition 2.
For any message m and any agent a, if agent a can construct message m, then he still can construct message m after the execution of the protocol actions.
Proposition 3.
Target 2 is globally true in the model .
In the initial state, only S has the secret message m and others do not have m. Of course, the intruder has m impossibly because any action is not done yet.
Now, we prove that Target 2 is still true after the execution of the sequence of the actions.
Proof.
We assume there exists a world w that satisfies the below case:
If the above formula holds, then there exists an action sequence such that
From Table 3, we see that:
So, the assumption contradicts it.
The intruder only can get the messages from the In-buffer. So, if then . We list the information in the In-buffer Therefore, all the information T has is encrypted. Without corresponding k, he can not compute and get secret message m. Therefore, Target 2 is satisfied. □
Proposition 4.
Target 1 does not hold in the initial state. But after the running of the last action , Target 1 holds.
Proof.
In the initial state, R does not have m and R only has his own key (that is assumed in the protocol). According to Table 3, the information set of R is Also, R has and . According to the construction rules, R can construct m, namely, .
Therefore, after the execution of all actions, we have:
which conforms to Target 1 (and everybody in the protocol knows that R has an encrypted message and corresponding key and R can construct m). □
Therefore, this protocol is secure.
6. Conclusions and Expectation
We have introduced a formal language based on dynamic epistemic logic to verify the security of the cryptographic protocol. Especially, we use the action model to describe the execution process of a protocol. The updated model displays transformation between models. We have given the verification model and proved that this protocol meets these requirements. Compared with papers [7,48], our method does not need to establish complex models or rules to derive the security of the protocol. We can formalize the whole protocol running process only through an action model. This process is simple, intuitive and efficient.
In the future research, we will extend the frame of the language to make it more expressive and able to express different cryptographic protocols. We should build a complete and sound axiomatization for the extended language. In this protocol, we assumed the attacker is a passive attacker who only can eavesdrop the messages from the network. In the future study, we will assume the attacker is an active attacker and he has more abilities to launch active attacks against the cryptographic protocol, and we plan to build an automatic detection system for security verification including protocols with quantum cryptography as a general modeling tool.
Author Contributions
Conceptualization, X.C. and H.D.; methodology, X.C.; validation, X.C.; formal analysis, X.C.; investigation, X.C.; resources, H.D.; writing—original draft preparation, X.C.; writing—review and editing, H.D.; supervision, H.D.; project administration, X.C. and H.D.; funding acquisition, X.C. and H.D. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the Key Project of Fundamental Research Funds for the Central Universities (No. XDJK2020B035), and Research Project of Education and Teaching Reform of Southwest University in 2020 (No. 2020JY055), and Special Project of Fundamental Research Funds for the Central Universities (No. SWU2009107), and Special Key Project of Technological Innovation and Application Development from Bureau of Science and Technology in Chongqing (No. cstc2019jscx gksbx0103), and the Key Base Project of Chongqing under Grant 16SKB040, and the Great Project of National Social Science Fund under Grant14ZDB016.
Conflicts of Interest
The authors declare no conflict of interest. The funders had no role in the design of the study; in the collection, analyses, or interpretation of data; in the writing of the manuscript, or in the decision to publish the results.
References
- Burrows, M.; Abadi, M.; Needham, R.M. A Logic of Authentication. ACM Trans. Comput. Syst. 1990, 8, 18–36. [Google Scholar] [CrossRef]
- Paulson, L.C. The Inductive Approach to Verifying Cryptographic Protocols. J. Comput. Secur. 1998, 6, 85–128. [Google Scholar] [CrossRef]
- Roscoe, A.W.; Broadfoot, P.J. Proving Security Protocols with Model Checkers by Data Independence Techniques. J. Comput. Secur. 1999, 7, 147–190. [Google Scholar] [CrossRef]
- Cirstea, H. Specifying Authentication Protocols Using Rewriting and Strategies. In Proceedings of the Practical Aspects of Declarative Languages, Third International Symposium, PADL 2001, Las Vegas, NV, USA, 11–12 March 2001; pp. 138–152. [Google Scholar] [CrossRef]
- Lowe, G. Breaking and Fixing the Needham-Schroeder Public-Key Protocol Using FDR. Softw. Concepts Tools 1996, 17, 93–102. [Google Scholar]
- Dolev, D.; Yao, A.C. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–207. [Google Scholar] [CrossRef]
- Van Ditmarsch, H.; Van Eijck, J.; Hernández-Antón, I.; Sietsma, F.; Simon, S.; Soler-Toscano, F. Modelling Cryptographic Keys in Dynamic Epistemic Logic with DEMO. In Highlights on Practical Applications of Agents and Multi-Agent Systems; Springer: Berlin/Heidelberg, Germany, 2012; pp. 155–162. [Google Scholar]
- Pirandola, S.; Andersen, U.L.; Banchi, L.; Berta, M.; Bunandar, D.; Colbeck, R.; Englund, D.; Gehring, T.; Lupo, C.; Ottaviani, C.; et al. Advances in Quantum Cryptography. arXiv 2019, arXiv:1906.01645. [Google Scholar] [CrossRef]
- Bacco, D.; Da Lio, B.; Cozzolino, D.; Da Ros, F.; Guo, X.; Ding, Y.; Sasaki, Y.; Aikawa, K.; Miki, S.; Terai, H.; et al. Boosting the secret key rate in a shared quantum and classical fibre communication system. Commun. Phys. 2019, 2. [Google Scholar] [CrossRef]
- Gong, L.; Needham, R.; Yahalom, R. Reasoning about belief in cryptographic protocols. In Proceedings of the 1990 IEEE Computer Society Symposium on Research in Security and Privacy, Oakland, CA, USA, 7–9 May 1990; pp. 234–248. [Google Scholar]
- van Oorschot, P. Extending Cryptographic Logics of Belief to Key Agreement Protocols. In Proceedings of the 1st ACM Conference on Computer and Communications Security, CCS ’93, Fairfax, VA, USA, 3–5 November 1993; ACM: New York, NY, USA, 1993; pp. 232–243. [Google Scholar]
- Mao, W.; Boyd, C. Towards formal analysis of security protocols. In Proceedings of the Computer Security Foundations Workshop VI, Franconia, NH, USA, 15–17 June 1993; pp. 147–158. [Google Scholar]
- Mansoor, K.; Ghani, A.; Chaudhry, S.A.; Shamshirband, S.; Ghayyur, S.; Mosavi, A. Securing Iot-Based RFID Systems: A Robust Authentication Protocol Using Symmetric Cryptography. Sensors 2019, 19, 4752. [Google Scholar] [CrossRef]
- Boussada, R.; Hamdane, B.; Elhdhili, M.E.; Saïdane, L.A. Privacy-preserving aware data transmission for IoT-based e-health. Comput. Netw. 2019, 162, 106866. [Google Scholar] [CrossRef]
- Ghani, A.; ul Hassan, K.M.; Mehmood, S.; Chaudhry, S.A.; Saqib, M.N. Security and key management in IoT wireless sensor networks: An authentication protocol using symmetric key. Int. J. Commun. Syst. 2019, 32, 1–18. [Google Scholar] [CrossRef]
- Wang, F.; Xu, G.; Gu, L. A Secure and Efficient ECC-Based Anonymous Authentication Protocol. Secur. Commun. Netw. 2019, 2019, 1–13. [Google Scholar] [CrossRef]
- Abadi, M.; Tuttle, M.R. A Semantics for a Logic of Authentication (Extended Abstract). In Proceedings of the Tenth Annual ACM Symposium on Principles of Distributed Computing, PODC’91, Montreal, QC, Canada, 19–21 August 1991; ACM: New York, NY, USA, 1991; pp. 201–216. [Google Scholar]
- Syverson, P.F.; van Oorschot, P.C. On unifying some cryptographic protocol logics. In Proceedings of the 1994 IEEE Computer Society Symposium on Research in Security and Privacy, Oakland, CA, USA, 16–18 May 1994; pp. 14–28. [Google Scholar]
- Syverson, P.; Van Oorschot, P. A Unified Cryptographic Protocol Logic; AD-a464 967; Defense Technical Information Center: Fort Belvoir, VA, USA, 1996. [Google Scholar]
- Moser, L. A logic of knowledge and belief for reasoning about computer security. In Proceedings of the Computer Security Foundations Workshop II, Franconia, NH, USA, 18–20 June 1989; pp. 57–63. [Google Scholar]
- Lei, X.; Xue, R.; Yu, T. A Timed Logic for Modeling and Reasoning about Security Protocols. IACR Cryptol. EPrint Arch. 2010, 2010, 645. [Google Scholar]
- Datta, A.; Derek, A.; Mitchell, J.C.; Roy, A. Protocol Composition Logic (PCL). Electr. Notes Theor. Comput. Sci. 2007, 172, 311–358. [Google Scholar] [CrossRef]
- Paulson, L.C. Relatios Between Secrets: The Yahalom Protocol. In Proceedings of the Security Protocols, 7th International Workshop, Cambridge, UK, 19–21 April 1999; pp. 73–84. [Google Scholar]
- Milner, R.; Parrow, J.; Walker, D. A Calculus of Mobile Processes, I. Inf. Comput. 1992, 100, 1–40. [Google Scholar] [CrossRef]
- Hoare, C.A.R. Communicating Sequential Processes. Commun. ACM 1978, 21, 666–677. [Google Scholar] [CrossRef]
- Milner, R. A Calculus of Communicating Systems; Springer: Berlin/Heidelberg, Germany, 1982. [Google Scholar]
- Huszti, A.; Olah, N. Security analysis of a cloud authentication protocol using applied pi calculus. IJIPT 2019, 12, 16–25. [Google Scholar] [CrossRef]
- Hirschi, L.; Baelde, D.; Delaune, S. A method for unbounded verification of privacy-type properties. J. Comput. Secur. 2019, 27, 277–342. [Google Scholar] [CrossRef]
- Abadi, M. Secrecy by Typing inSecurity Protocols. In Proceedings of the Theoretical Aspects of Computer Software, Third International Symposium, TACS ’97, Sendai, Japan, 23–26 September 1997; pp. 611–638. [Google Scholar]
- Abadi, M.; Blanchet, B. Secrecy types for asymmetric communication. Theor. Comput. Sci. 2003, 298, 387–415. [Google Scholar] [CrossRef][Green Version]
- Gordon, A.D.; Jeffrey, A. Authenticity by Typing for Security Protocols. In Proceedings of the 14th IEEE Computer Security Foundations Workshop (CSFW-14 2001), Cape Breton, NS, Canada, 11–13 June 2001; pp. 145–159. [Google Scholar]
- Gordon, A.D.; Jeffrey, A. Types and Effects for Asymmetric Cryptographic Protocols. In Proceedings of the 15th IEEE Computer Security Foundations Workshop (CSFW-15 2002), Cape Breton, NS, Canada, 24–26 June 2002; pp. 77–91. [Google Scholar]
- Cardelli, L.; Ghelli, G.; Gordon, A.D. Secrecy and Group Creation. In Proceedings of the CONCUR 2000—Concurrency Theory, 11th International Conference, University Park, PA, USA, 22–25 August 2000; pp. 365–379. [Google Scholar]
- Abadi, M.; Blanchet, B. Analyzing security protocols with secrecy types and logic programs. J. ACM 2005, 52, 102–146. [Google Scholar] [CrossRef]
- Gattinger, M.; Van Eijck, J.V. Towards Model Checking Cryptographic Protocols with Dynamic Epistemic Logic. In Proceedings of the LAMAS (LAMAS 2015), Istanbul, Turkey, 4 May 2015; Available online: http://www.irit.fr/~Emiliano.Lorini/LAMAS2015/accepted.htm (accessed on 30 June 2020).
- Chen, X.; Deng, H. Analysis of Cryptographic Protocol by Dynamic Epistemic Logic. IEEE Access 2019, 7, 29981–29988. [Google Scholar] [CrossRef]
- Ahmadi, S.; Fallah, M.S. An Omniscience-Free Temporal Logic of Knowledge for Verifying Authentication Protocols. Bull. Iran. Math. Soc. 2018, 44, 1243–1265. [Google Scholar] [CrossRef]
- Luis Uso-Domenech, J.; Antonio Nescolarde-Selva, J.; Segura-Abad, L. Proposal for the Formalization of Dialectical Logic. Mathematics 2016, 4, 69. [Google Scholar] [CrossRef]
- Uso Domenech, J.L.; Antonio Nescolarde-Selva, J.; Segura-Abad, L. Dialectical Multivalued Logic and Probabilistic Theory. Mathematics 2017, 5, 15. [Google Scholar] [CrossRef]
- Yang, E. Fixpointed Idempotent Uninorm (Based) Logics. Mathematics 2019, 7, 107. [Google Scholar] [CrossRef]
- Smets, S.; Velzquez-Quesada, F.R. The Creation and Change of Social Networks: A Logical Study Based on Group Size. In Proceedings of the International Workshop on Dynamic Logic, Brasilia, Brazil, 23–24 September 2017. [Google Scholar]
- Van Ditmarsch, H.; Knight, S. Announcement as effort on topological spaces. Synthese 2019, 196, 2927–2969. [Google Scholar] [CrossRef]
- Christian, B.J.; Mattias, S. A Dynamic Solution to the Problem of Logical Omniscience. J. Philos. Log. 2019, 48, 501–521. [Google Scholar]
- Philippe, B.; David, F.D.; Emiliano, L. The Dynamics of Epistemic Attitudes in Resource-Bounded Agents. Stud. Log. 2019, 107, 457–488. [Google Scholar]
- Li, Y.; Kooi, B.; Wang, Y. A dynamic epistemic framework for reasoning about conformant probabilistic plans. Artif. Intell. 2019, 268, 54–84. [Google Scholar] [CrossRef]
- Alexandru, B.; Nick, B.; Sonja, S. A Topological Approach to Full Belief. J. Philos. Log. 2019, 48, 205–244. [Google Scholar]
- Badura, C.; Berto, F. Truth in Fiction, Impossible Worlds, and Belief Revision. Australas. J. Philos. 2018, 2, 1–16. [Google Scholar] [CrossRef]
- Al Bataineh, O.; Van Der Meyden, R. Abstraction for Epistemic Model Checking of Dining Cryptographers-based Protocols. In Proceedings of the 13th Conference on Theoretical Aspects of Rationality and Knowledge, Groningen, The Netherlands, 12–14 July 2011; pp. 247–256. [Google Scholar]
- van Ditmarsch, H.P.; Kooi, B.P. Semantic results for ontic and epistemic change. arXiv 2006, arXiv:cs/0610093. [Google Scholar]
- Francien, D.; Yanjing, W. Dynamic epistemic verification of security protocols:framework and case study. In Proceedings of the Workshop on Logic, Rationality and Interaction, Beijing, China, 5–9 August 2007; pp. 129–144. [Google Scholar]
- Paulson, L.C. Proving Properties of Security Protocols by Induction. In Proceedings of the 10th IEEE Workshop on Computer Security Foundations, CSFW ’97, Rockport, MA, USA, 10–12 June 1997; IEEE Computer Society: Washington, DC, USA, 1997; pp. 70–83. [Google Scholar]
- Cremers, C.; Mauw, S. Operational Semantics of Security Protocols. In Models, Transformations and Tools; Leue, I.S., Systä, T., Eds.; Springer: Berlin/Heidelberg, Germany, 2003; Volume 3466, pp. 66–89. [Google Scholar]
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).