Hash-Chain-Based Cross-Regional Safety Authentication for Space-Air-Ground Integrated VANETs †
Abstract
:1. Introduction
- Using the uniqueness and non-repudiation of RF fingerprints, the physical layer features are used as the identity of the vehicle node, so that it cannot be tampered with or forged.
- We Simplify the critical technologies of the blockchain and propose a hash-chain-based cross-regional security authentication scheme for space–air–ground integrated VANETs. We replace the traditional consensus mechanism with Kafka distributed message processing to implement the verification and backup of the records on the block.
- Combined with SAGIN to meet the needs of highly intelligent assisted driving, the hash-chain template is redefined according to the characteristics of network transmission.
- Using OMNet ++, SUMO, and Veins joint simulation platforms to generate transactions for cross-regional traffic flow, Kafka [11], and Practical Byzantine Fault Tolerance Algorithm (PBFT) [12] consensus algorithms are compared. The experimental results show that the average delay of a single transaction generation block is about 0.9ms, which meets the needs of efficient and low-latency authentication.
2. Related Work
2.1. Traditional Cross-Regional Authentication Network
2.2. Blockchain-Based Security Authentication
2.3. Physical Layer RF Fingerprint Features
3. Hash-Chain
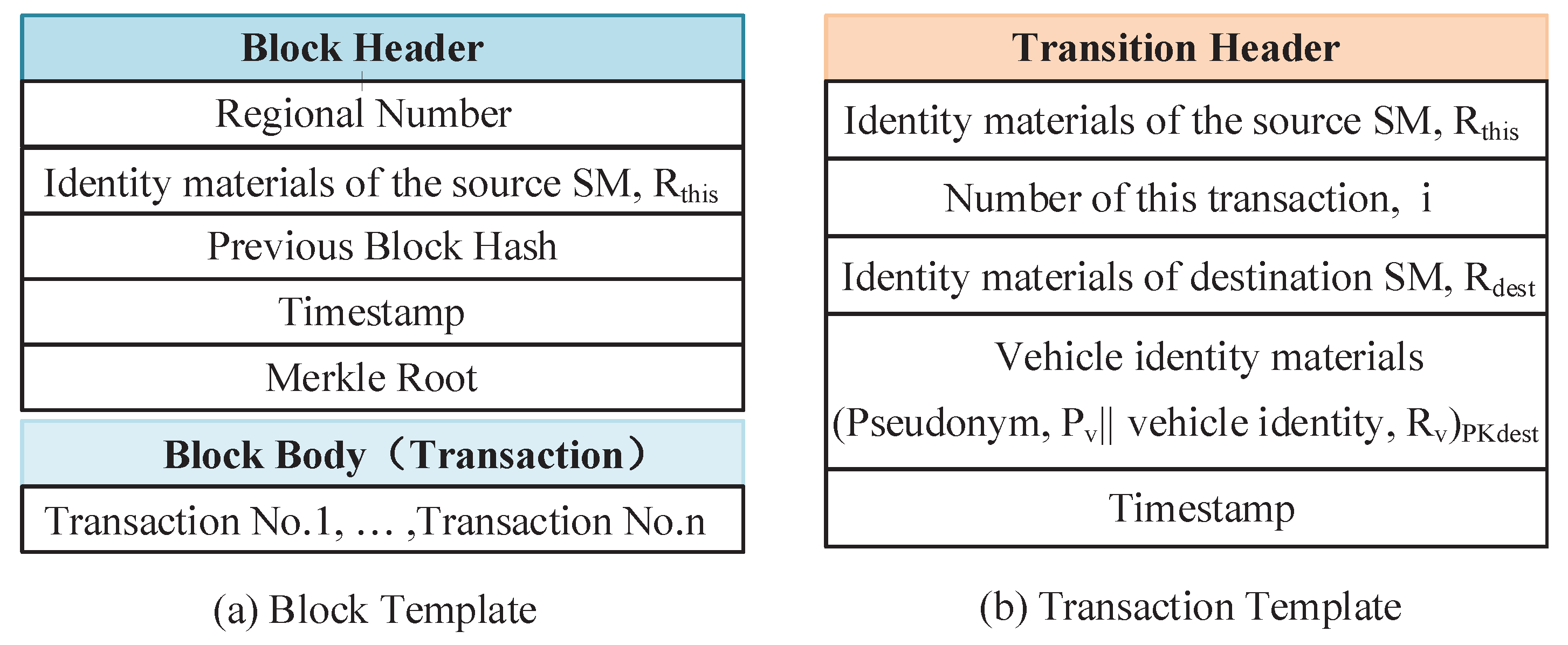
3.1. Structure of the Hash Chain
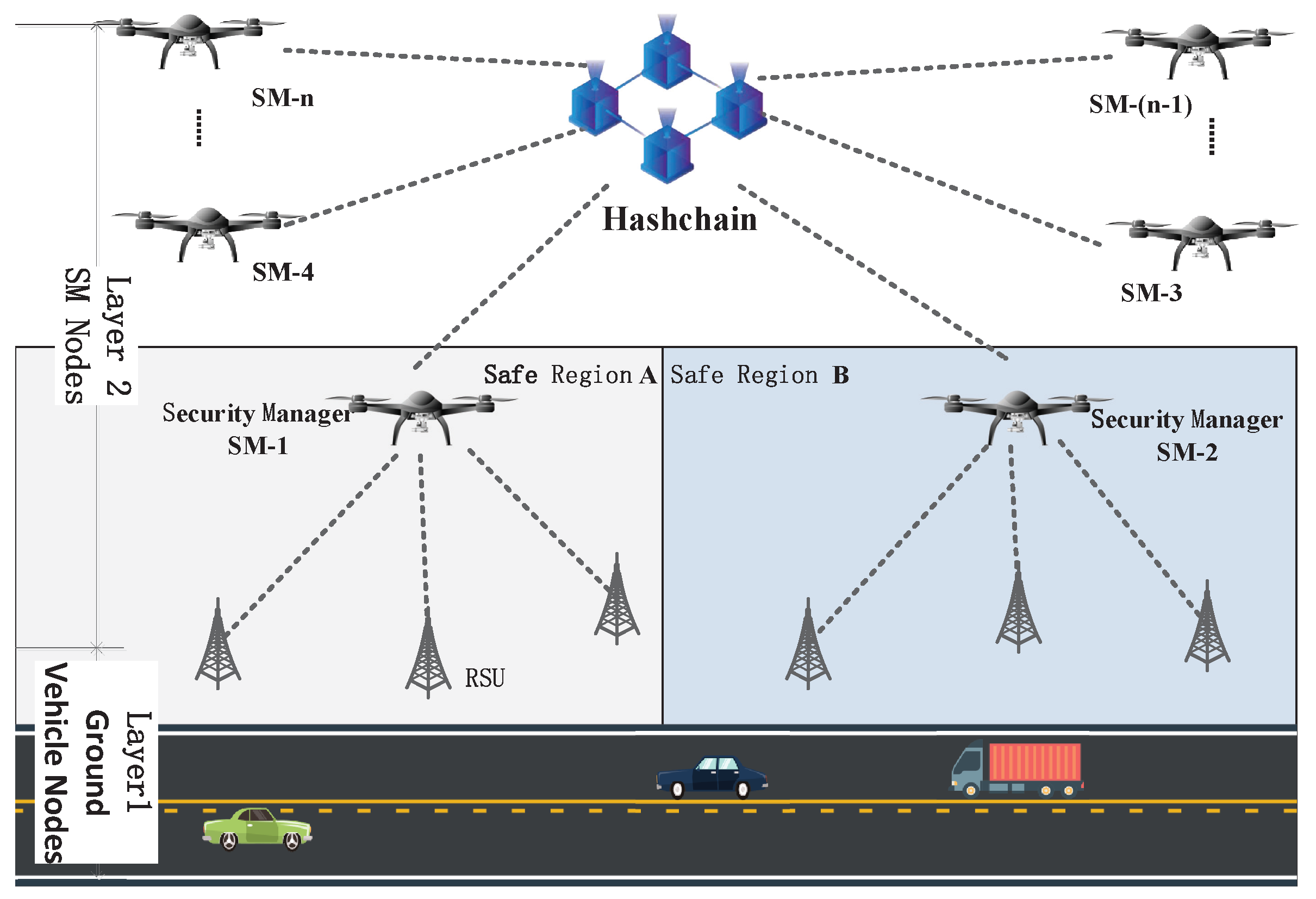
3.2. Node Function and Role Classification of Hash-Chain System
4. Cross-Regional Identity Authentication Model Based on the Hash Chain
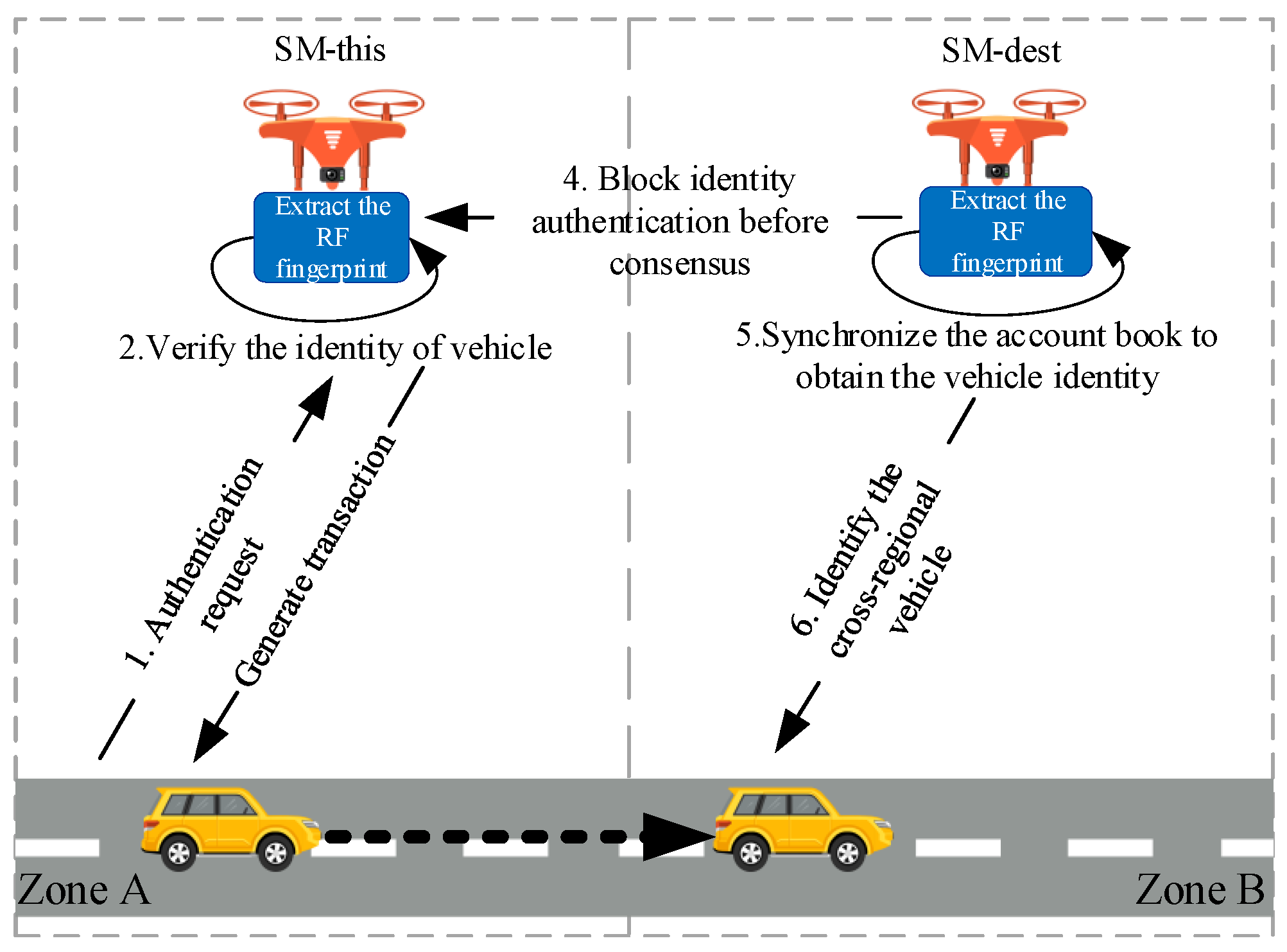
4.1. Authentication Process
4.2. Consensus Algorithm
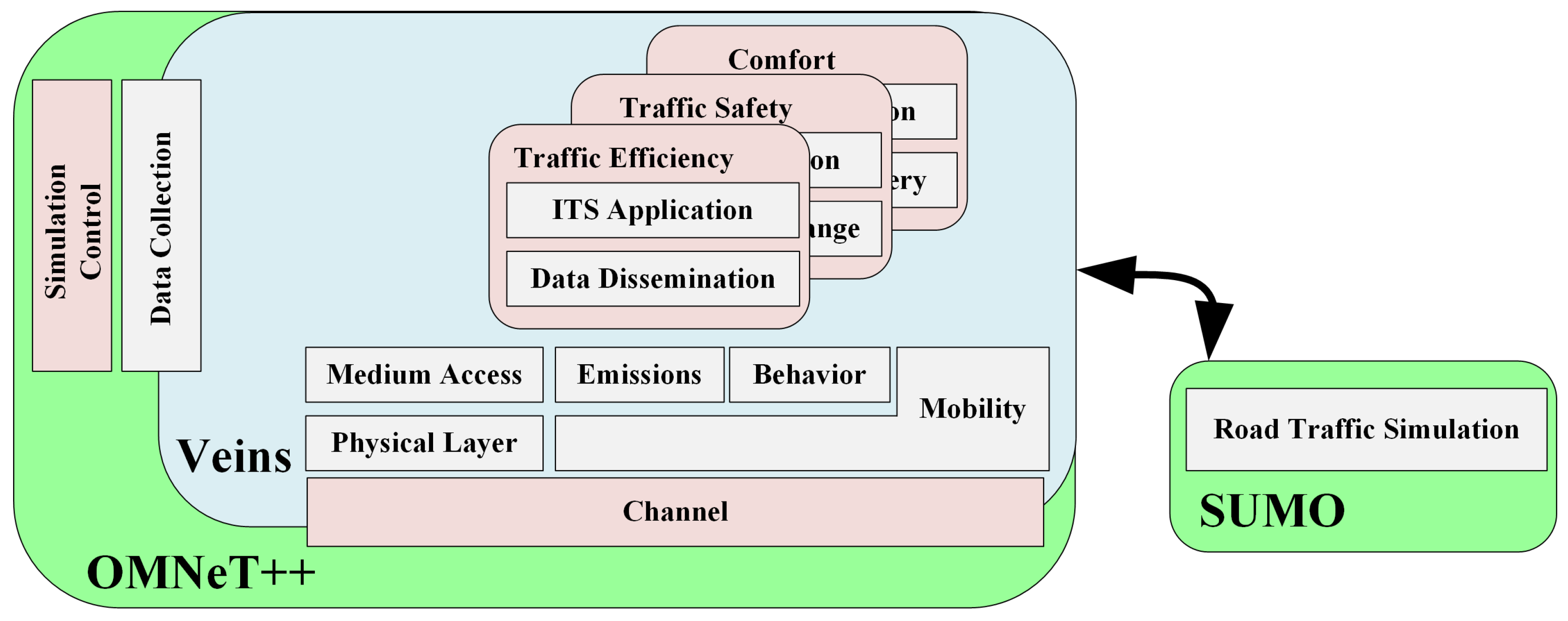
5. Experiment
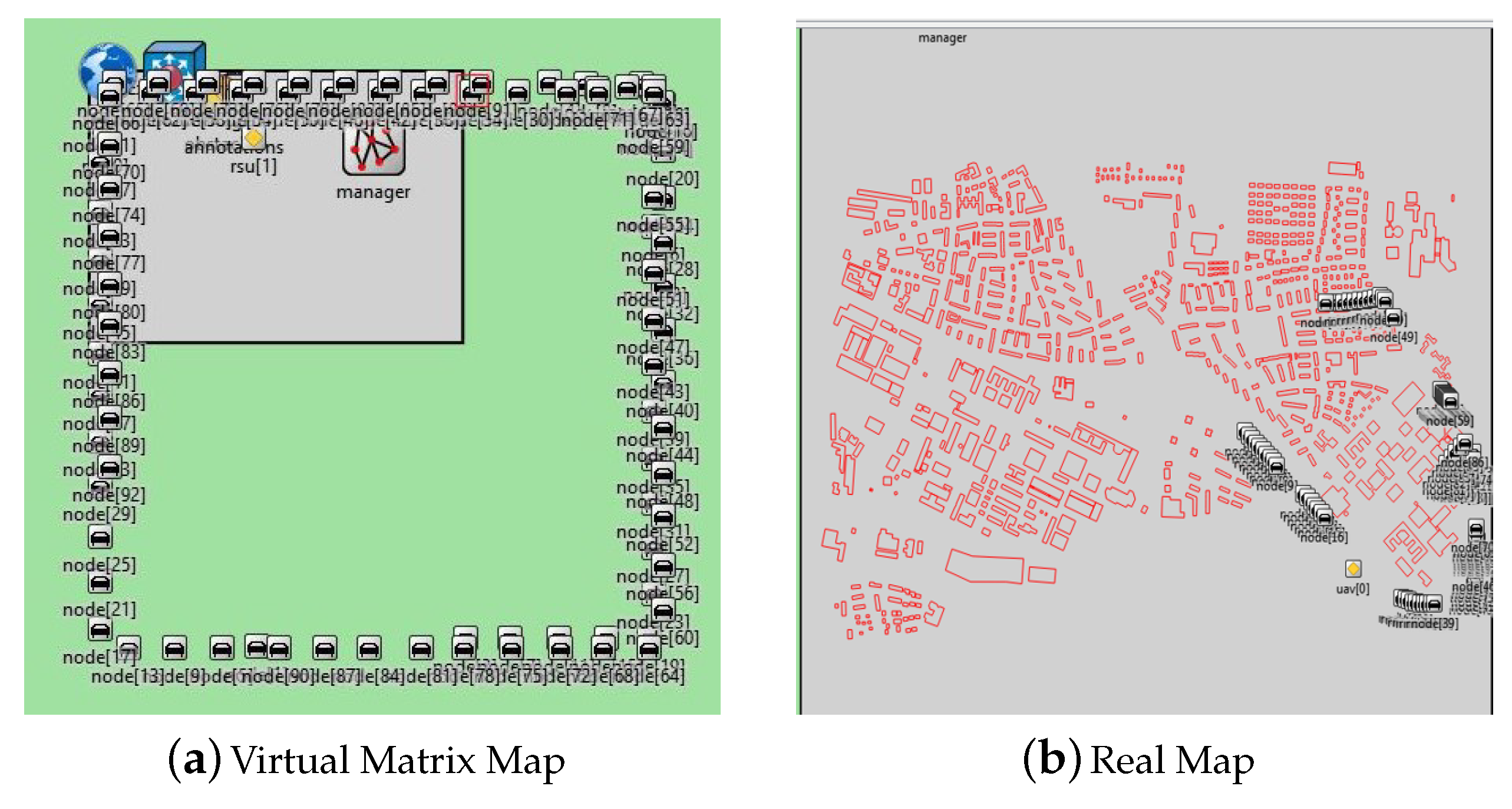
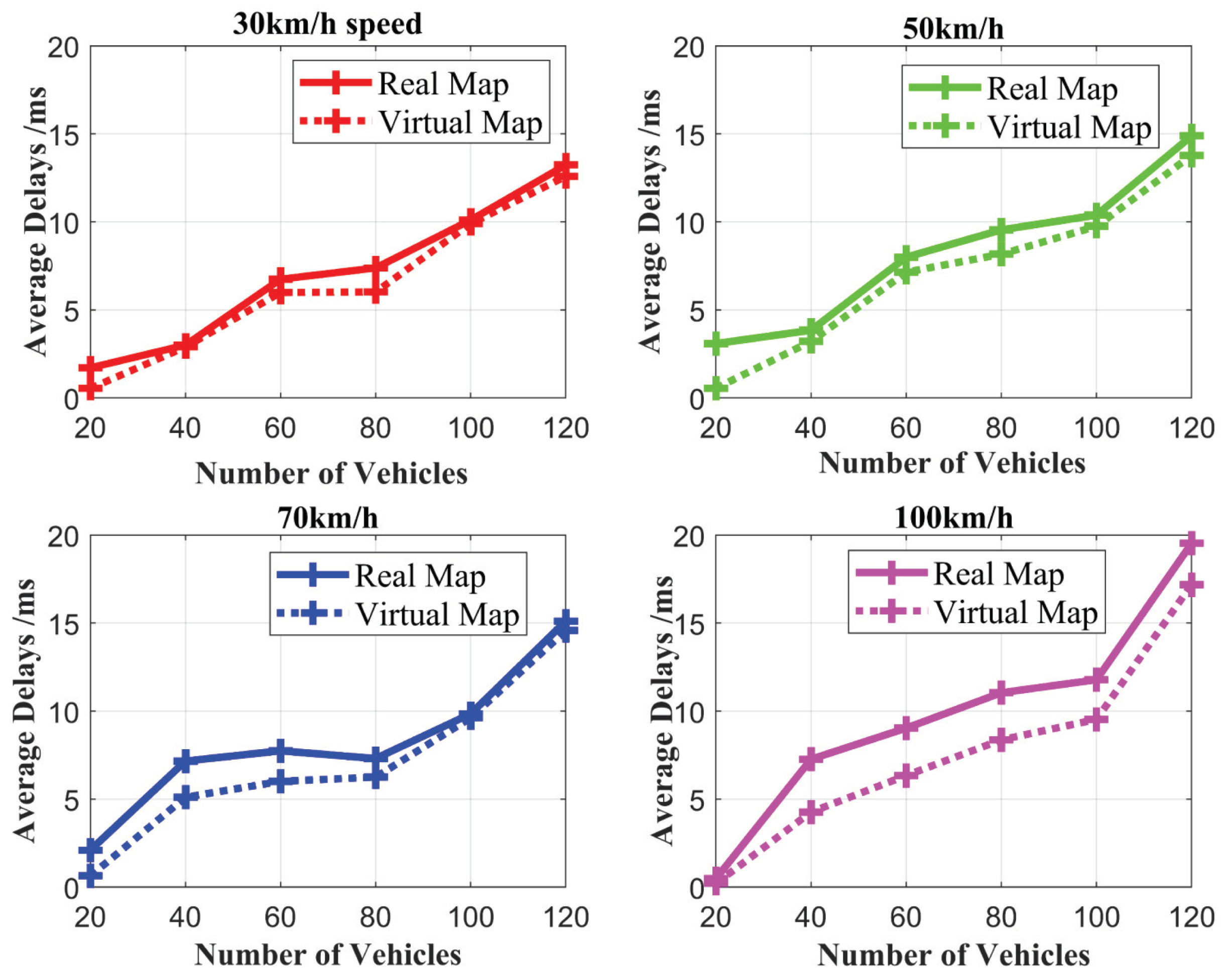
5.1. Traditional Vehicle Cross-Regional Authentication Simulation
5.1.1. Simulation Parameter Setting
5.1.2. Simulation Results
5.2. Hash-Chain-Based Vehicle Cross-Regional Authentication Simulation
5.2.1. Distributed Network Based on the Kafka Consensus
5.2.2. Distributed Network Based on the PBFT Consensus
5.2.3. Comparison Experiment of Hash Block Authentication and Traditional Authentication
6. Conclusions
Author Contributions
Acknowledgments
Conflicts of Interest
References
- Horng, S.J.; Tzeng, S.F.; Huang, P.H.; Wang, X.; Li, T.; Khan, M.K. An efficient certificateless aggregate signature with conditional privacy-preserving for vehicular sensor networks. Inf. Sci. 2015, 317, 48–66. [Google Scholar] [CrossRef]
- Zhang, N.; Zhang, S.; Yang, P.; Alhussein, O.; Zhuang, W.; Shen, X.S. Software defined space-air-ground integrated vehicular networks: Challenges and solutions. IEEE Commun. Mag. 2017, 55, 101–109. [Google Scholar] [CrossRef] [Green Version]
- Kato, N.; Fadlullah, Z.M.; Tang, F.; Mao, B.; Tani, S.; Okamura, A.; Liu, J. Optimizing space-air-ground integrated networks by artificial intelligence. IEEE Wirel. Commun. 2019, 26, 140–147. [Google Scholar]
- Wang, C.; Zhu, L.; Gong, L.; Zhao, Z.; Yang, L.; Liu, Z.; Cheng, X. Channel State Information-Based Detection of Sybil Attacks in Wireless Networks. J. Internet Serv. Inf. Secur. 2018, 8, 2–17. [Google Scholar]
- Zhao, B.; Liu, P.; Wang, X.; You, I. Toward efficient authentication for space-air-ground integrated Internet of things. Int. J. Distrib. Sens. Netw. 2019, 15, 1550147719860390. [Google Scholar] [CrossRef] [Green Version]
- Albarqi, A.; Alzaid, E.; Al Ghamdi, F.; Asiri, S.; Kar, J. Public key infrastructure: A survey. J. Inf. Secur. 2014, 6, 31. [Google Scholar] [CrossRef] [Green Version]
- Lu, Z.; Qu, G.; Liu, Z. A survey on recent advances in vehicular network security, trust, and privacy. IEEE Trans. Intell. Transp. Syst. 2018, 20, 760–776. [Google Scholar] [CrossRef]
- Salem, A.H.; Abdel-Hamid, A.; El-Nasr, M.A. The case for dynamic key distribution for PKI-based VANETS. arXiv 2016, arXiv:1605.04696. [Google Scholar] [CrossRef]
- Tan, H.; Ma, M.; Labiod, H.; Boudguiga, A.; Zhang, J.; Chong, P.H.J. A secure and authenticated key management protocol (SA-KMP) for vehicular networks. IEEE Trans. Veh. Technol. 2016, 65, 9570–9584. [Google Scholar] [CrossRef] [Green Version]
- Lastinec, J.; Keszeli, M. Analysis of realistic attack scenarios in vehicle ad-hoc networks. In Proceedings of the 2019 7th International Symposium on Digital Forensics and Security (ISDFS), Barcelos, Portugal, 10–12 June 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–6. [Google Scholar]
- Castro, M.; Liskov, B. Practical Byzantine fault tolerance and proactive recovery. ACM Trans. Comput. Syst. (TOCS) 2002, 20, 398–461. [Google Scholar] [CrossRef]
- Kreps, J.; Narkhede, N.; Rao, J. Kafka: A distributed messaging system for log processing. In Proceedings of the NetDB, Athens, Greece, 12–16 June 2011; Volume 11, pp. 1–7. [Google Scholar]
- Lei, A.; Cruickshank, H.; Cao, Y.; Asuquo, P.; Ogah, C.P.A.; Sun, Z. Blockchain-based dynamic key management for heterogeneous intelligent transportation systems. IEEE Internet Things J. 2017, 4, 1832–1843. [Google Scholar] [CrossRef] [Green Version]
- Liu, J.; Shi, Y.; Fadlullah, Z.M.; Kato, N. Space-air-ground integrated network: A survey. IEEE Commun. Surv. Tutor. 2018, 20, 2714–2741. [Google Scholar] [CrossRef]
- Zheng, Z.; Xie, S.; Dai, H.; Chen, X.; Wang, H. An overview of blockchain technology: Architecture, consensus, and future trends. In Proceedings of the 2017 IEEE International Congress on Big Data (BigData Congress), Honolulu, HI, USA, 25–30 June 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 557–564. [Google Scholar]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System; Technical Report; Manubot; CoinDesk: New York, NY, USA, 2019. [Google Scholar]
- Buterin, V. A next-generation smart contract and decentralized application platform. White Paper, January 2014; Volume 3. [Google Scholar]
- Cachin, C. Architecture of the hyperledger blockchain fabric. In Proceedings of the Workshop on distributed cryptocurrencies and consensus ledgers, Chicago, IL, USA, 25 Junly 2016; Volume 310, p. 4. [Google Scholar]
- Sun, J.; Yan, J.; Zhang, K.Z. Blockchain-based sharing services: What blockchain technology can contribute to smart cities. Financ. Innov. 2016, 2, 1–9. [Google Scholar] [CrossRef] [Green Version]
- Dorri, A.; Kanhere, S.S.; Jurdak, R. Blockchain in internet of things: Challenges and solutions. arXiv 2016, arXiv:1608.05187. [Google Scholar]
- Lu, Z.; Liu, W.; Wang, Q.; Qu, G.; Liu, Z. A privacy-preserving trust model based on blockchain for VANETs. IEEE Access 2018, 6, 45655–45664. [Google Scholar] [CrossRef]
- Lasla, N.; Younis, M.; Znaidi, W.; Arbia, D.B. Efficient distributed admission and revocation using blockchain for cooperative ITS. In Proceedings of the 2018 9th IFIP international conference on new technologies, mobility and security (NTMS), Paris, France, 26–28 February 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–5. [Google Scholar]
- Dorri, A.; Steger, M.; Kanhere, S.S.; Jurdak, R. Blockchain: A distributed solution to automotive security and privacy. IEEE Commun. Mag. 2017, 55, 119–125. [Google Scholar] [CrossRef] [Green Version]
- Wu, Y.; Khisti, A.; Xiao, C.; Caire, G.; Wong, K.K.; Gao, X. A survey of physical layer security techniques for 5G wireless networks and challenges ahead. IEEE J. Sel. Areas Commun. 2018, 36, 679–695. [Google Scholar] [CrossRef] [Green Version]
- Ureten, O.; Serinken, N. Wireless security through RF fingerprinting. Can. J. Electr. Comput. Eng. 2007, 32, 27–33. [Google Scholar] [CrossRef]
- Baldini, G.; Steri, G. A survey of techniques for the identification of mobile phones using the physical fingerprints of the built-in components. IEEE Commun. Surv. Tutor. 2017, 19, 1761–1789. [Google Scholar] [CrossRef]
- Zhao, C.; Shi, M.; Huang, M.; Du, X. Authentication Scheme Based on Hashchain for Space-Air-Ground Integrated Network. In Proceedings of the ICC 2019-2019 IEEE International Conference on Communications (ICC), Shanghai, China, 20–24 May 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–6. [Google Scholar]
- Jakobsson, M.; Leighton, T.; Micali, S.; Szydlo, M. Fractal Merkle tree representation and traversal. In Cryptographers’ Track at the RSA Conference; Springer: Berlin/Heidelberg, Germany, 2003; pp. 314–326. [Google Scholar]
- Bentov, I.; Lee, C.; Mizrahi, A.; Rosenfeld, M. Proof of activity: Extending bitcoin’s proof of work via proof of stake [extended abstract] y. ACM SIGMETRICS Perform. Eval. Rev. 2014, 42, 34–37. [Google Scholar] [CrossRef]
- King, S.; Nadal, S. Ppcoin: Peer-to-Peer Crypto-Currency with Proof-of-Stake. Self-Published Paper. Available online: https://decred.org/research/king2012.pdf (accessed on 19 August 2012).
- Kapoor, V.; Abraham, V.S.; Singh, R. Elliptic curve cryptography. Ubiquity 2008, 2008, 1–8. [Google Scholar] [CrossRef]
- Johnson, D.; Menezes, A.; Vanstone, S. The elliptic curve digital signature algorithm (ECDSA). Int. J. Inf. Secur. 2001, 1, 36–63. [Google Scholar] [CrossRef]
- Zhao, C.; Chen, C.; He, Z.; Wu, Z. Application of Auxiliary Classifier Wasserstein Generative Adversarial Networks in Wireless Signal Classification of Illegal Unmanned Aerial Vehicles. Appl. Sci. 2018, 8, 2664. [Google Scholar] [CrossRef] [Green Version]
- Ma, Z.; Zhang, J.; Guo, Y.; Liu, Y.; Liu, X.; He, W. An Efficient Decentralized Key Management Mechanism for VANET with Blockchain. IEEE Trans. Veh. Technol. 2020. [Google Scholar] [CrossRef]




| Requirements | Solutions |
|---|---|
| Authenticity | The RF fingerprint of the wireless signal is unique and non-cloneable, ensuring a reliable node identity. |
| Data security | The data recorded on the hash chain have the characteristics of traceability, non-tampering, and non-repudiation. |
| High efficiency | Improve network throughput and reduce block generation delay through Kafka distributed message queues. |
| Against attacks | In the hash-chain system, because the hash value of the block is different from other nodes, it can be discovered in time when the node is attacked; even if the node is broken, there is a backup of the data about the node. |
| Privacy protection | Use asymmetric encryption technology to protect the critical information of the block |
| Number of Nodes | Number of Transactions | |||||||
|---|---|---|---|---|---|---|---|---|
| 10 | 20 | 50 | 100 | 150 | 200 | 250 | 300 | |
| 4 | 26.356 | 25.342 | 27.708 | 33.708 | 25.53 | 31.881 | 26.511 | 34.902 |
| 6 | 27.138 | 26.241 | 25.908 | 34.331 | 25.866 | 33.241 | 28.186 | 33.98 |
| 8 | 27.202 | 25.313 | 26.464 | 36.392 | 25.957 | 36.395 | 25.267 | 36.191 |
| 10 | 27.317 | 26.541 | 26.457 | 37.045 | 26.757 | 37.425 | 26.847 | 36.754 |
| 12 | 26.15 | 26.952 | 26.796 | 38.281 | 28.26 | 38.434 | 27.461 | 40.098 |
| Number of Nodes | Number of Transactions | |||||||
|---|---|---|---|---|---|---|---|---|
| 10 | 20 | 50 | 100 | 150 | 200 | 250 | 300 | |
| 4 | 24.778 | 25.53 | 26.942 | 31.318 | 25.733 | 30.238 | 27.42 | 29.311 |
| 6 | 25.305 | 25.27 | 26.511 | 34.866 | 25.981 | 33.238 | 28.902 | 36.238 |
| 8 | 28.181 | 26.15 | 26.952 | 41.434 | 26.066 | 41.216 | 28.864 | 42.271 |
| Consensus | Number of Nodes | ||||
|---|---|---|---|---|---|
| Algorithm | 4 | 6 | 8 | 10 | 12 |
| Kafka | 23.21% | 24.67% | 25.20% | 25.94% | 28.69 |
| PBFT | 23.20% | 41.70% | 78.50% | - | - |
| Process | Average Single Processing Delay /(ms) |
|---|---|
| ECIES encryption, | 0.52412 |
| ECIES decryption, | 0.74753 |
| ECDSA signature, | 0.51124 |
| ECDSA authentication, | 1.13411 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Luo, G.; Shi, M.; Zhao, C.; Shi, Z. Hash-Chain-Based Cross-Regional Safety Authentication for Space-Air-Ground Integrated VANETs. Appl. Sci. 2020, 10, 4206. https://doi.org/10.3390/app10124206
Luo G, Shi M, Zhao C, Shi Z. Hash-Chain-Based Cross-Regional Safety Authentication for Space-Air-Ground Integrated VANETs. Applied Sciences. 2020; 10(12):4206. https://doi.org/10.3390/app10124206
Chicago/Turabian StyleLuo, Gege, Mingxian Shi, Caidan Zhao, and Zhiyuan Shi. 2020. "Hash-Chain-Based Cross-Regional Safety Authentication for Space-Air-Ground Integrated VANETs" Applied Sciences 10, no. 12: 4206. https://doi.org/10.3390/app10124206
APA StyleLuo, G., Shi, M., Zhao, C., & Shi, Z. (2020). Hash-Chain-Based Cross-Regional Safety Authentication for Space-Air-Ground Integrated VANETs. Applied Sciences, 10(12), 4206. https://doi.org/10.3390/app10124206





