Secure D2D Communication for 5G IoT Network Based on Lightweight Cryptography
Abstract
1. Introduction
- We analyze existing typical security threats and secure D2D communication. Then we present security considerations for secure D2D communication for a 5G IoT network.
- We survey and analyze existing research based on our security considerations, including authentication, data confidentiality/integrity, anonymity and efficiency.
- We propose a lightweight and secure D2D communication system. The proposed D2D communication system is designed based on lightweight cryptography. It can be implemented simply and can efficiently process resource-constrained 5G IoT devices.
2. Related Work
2.1. Typical Security Threats of D2D Communication
- Impersonation attack. In this attack the attacker acts like a legitimate user by using an identity such as an international mobile subscriber identity (IMSI). To prevent this attack proper authentication of users has to be considered.
- Eavesdropping. This is a type of attack where the attacker passively listens to communication between users and thereby the attacker can capture the transmitted data and also can fabricate the data. To prevent this attack, data confidentiality and integrity have to be considered.
- Privacy sniffing. D2D communication has to broadcast request messages to search for nearby devices. However, the attacker uses this feature to find and track the victim device. To mitigate this security threat, the devices have to use an anonymous identity, and it has to be authenticated.
- Free riding attack. Selfish devices receive the desired data from other devices but do not share their resources because of energy consumption and because of this they reduce system availability. To mitigate this attack, the user identity has to be authenticated and managed by a base station.
- Location spoofing. In this attack a malicious device may broadcast a request message with wrong or artificial location information to disrupt D2D communication in the device discovery step. To mitigate this attack, the request message has to be processed only from validated devices in D2D communication.
2.2. Security Considerations for a 5G IoT Network
- Authentication. Authentication is a key requirement for securing D2D communication in the 5G IoT network. For most types of attacks, proper user authentication is the most basic and appropriate solution. Every network should be able to verify the identity of users in order to guarantee the security of the network.
- Data confidentiality and Integrity. The data transmitted in the IoT network contains sensitive information, and due to a variety of attacks that can eavesdrop on or modify that information, confidentiality and integrity are a big concern. For providing this, we have to encrypt the transmitted data and use hash functions or message authentication algorithms.
- Anonymity. Anonymity refers to hiding the identity of origin and sensitive information such as location. Anonymity is a necessary security function to prevent attackers from targeting specific users for their purpose. In such cases, when anonymity is not provided, the attacker can choose a specific target for the attack. If you take the example of autonomous vehicles, the attacker may decide to attack a specific car. Therefore, anonymity should be considered extensively.
- Efficiency. Efficiency is the communication system’s ability to be implemented and to operate economically. This consideration is about availability, which means that authorized users can access the information at any time they request it. This consideration is especially critical when it comes to the IoT network because IoT devices have limited resources.
2.3. Existing Research
3. Secure D2D Communication
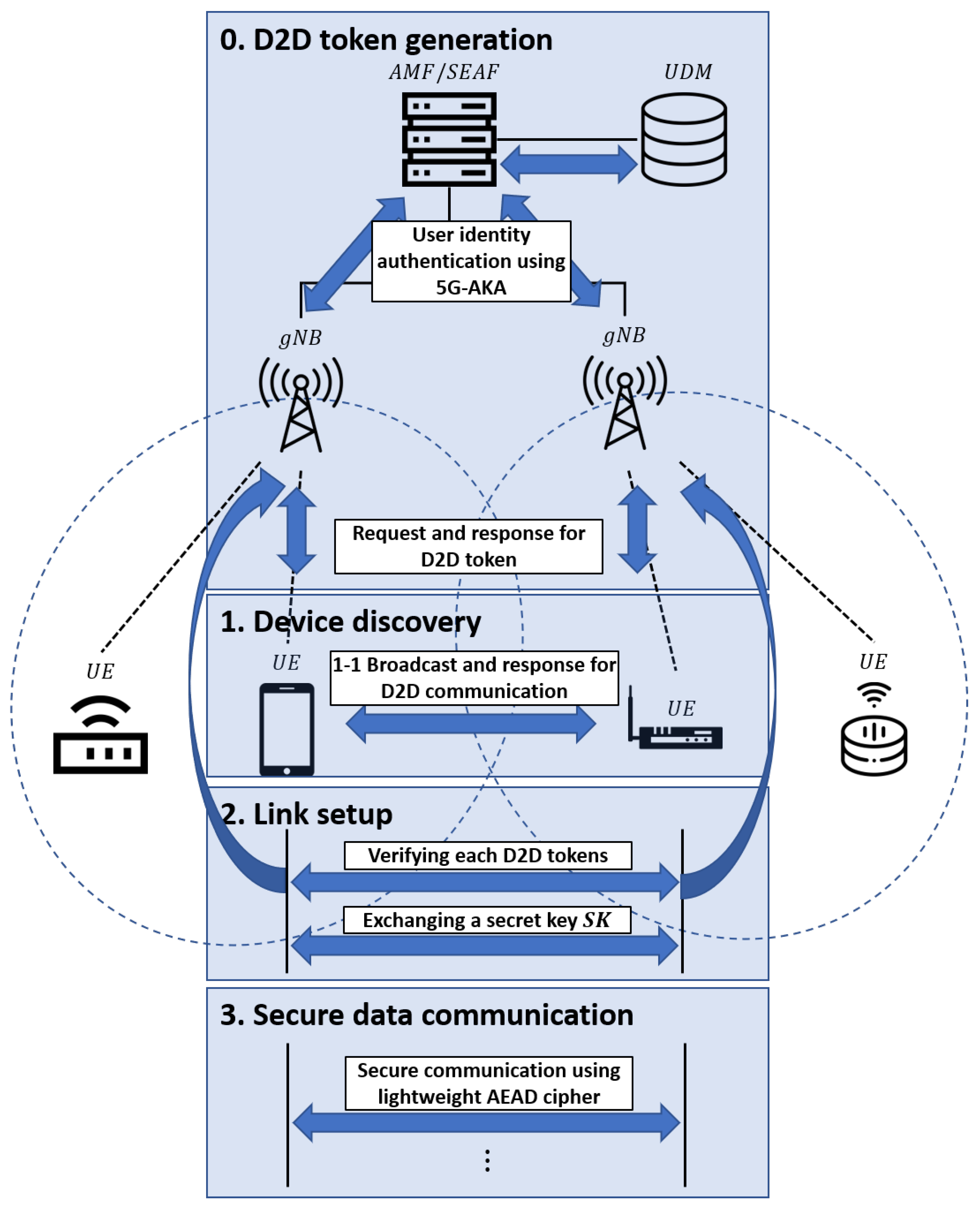
3.1. Proposed D2D System Model
- Device discovery is a process that searches for nearby nodes. In this step, nodes in a network broadcast a request message to discover other nodes. If a node receives a request message, it sends a response message to another node. The broadcast or response message in this process includes each UE’s encrypted identity SUCI and the issued D2D token.
- Link setup is a process for making a peer-to-peer connection between two nodes. During this process, each node sends a verification request to its base station, gNB, with the SUCI and D2D token of the target UE being received in the device discovery phase. After verification, ECDH is used to exchange secret keys for secure data transfer.
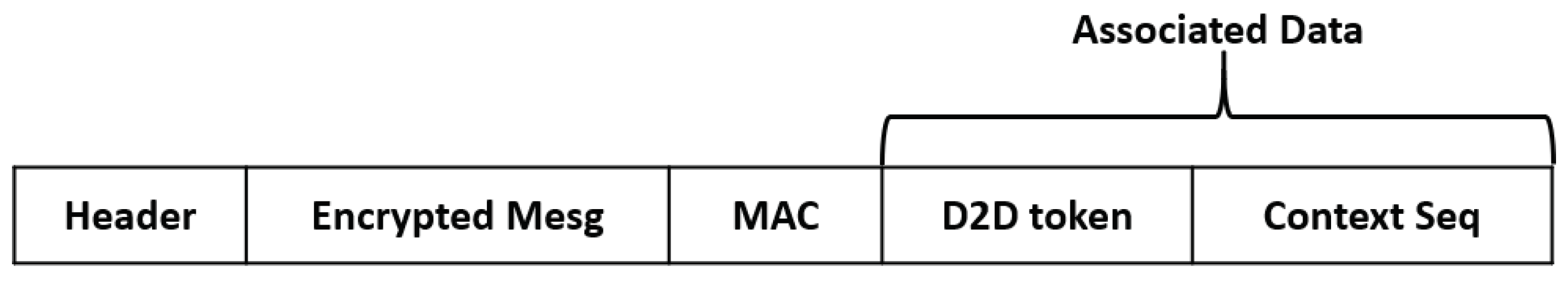
- Secure data transmission is a process where data is transmitted. The main feature of this step is that the data is encrypted using a lightweight AEAD cipher before transmission. In the encryption process, the sender node uses its D2D token identity and context sequence, thereby the confidentiality and integrity of the data are ensured. Moreover, authentication is processed in every transmission.
3.2. Details of Communication Mechanism
4. Simulation Results
5. Security Analysis
5.1. Analysis Based on Security Considerations
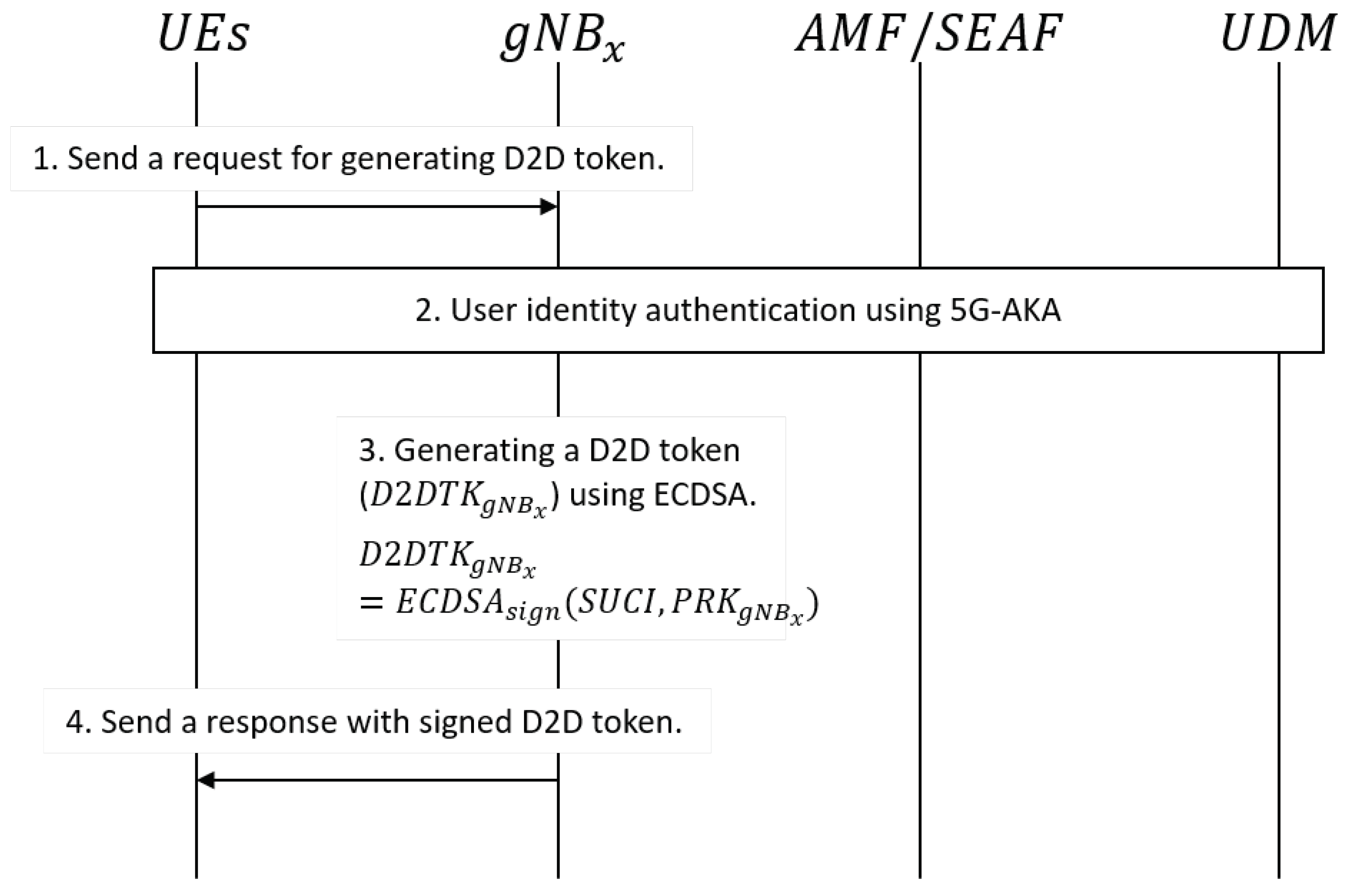
- Authentication: The proposed D2D communication system performs primary authentication using 5G-AKA, which is an authentication framework provided by 5G, to perform authentication for a UE before issuing a D2D token. Moreover, the issued token can perform secondary authentication through verification of the process of creating a link of D2D communication through the gNB’s public key and SUCI. Finally, in the data transmission step, the token is used as an AD to authenticate the other party for each transmission of data. In this way, authentication of the UE is performed in all processes of data communication before issuing a token for D2D communication so that more secure communication can be performed.
- Data confidentiality and integrity: The proposed D2D communication system generates D2D communication using SUCI, which is the encrypted UE identity, and the secret key of the gNB during the D2D generation process. In this process, there is no case where the identity of the unencrypted UE is transmitted. In addition, in the step of actual data transmition after creating a D2D link, encryption is performed using a lightweight AEAD cipher. AEAD cryptography can provide integrity and authentication as well as data confidentiality. Therefore, the proposed D2D communication system can guarantee the confidentiality/integrity of the identity and communication data of the UE.
- Anonymity: In 5G networks, SUCI is an encrypted identity for UE anonymity, which provides anonymity for the UE itself. Moreover, the D2D token used in the proposed D2D communication is a value obtained by signing SUCI with the private key of the gNB, which also provides anonymity by not being able to recognize the identity of the UE directly.
- Efficiency: Both the authentication process and the data encryption process used in the proposed D2D communication system are based on lightweight cryptography. The lightweight ciphers used in this paper are the ECC-based public key cryptosystem and the lightweight AEAD cipher. The ECC-based public key cryptosystem uses a 256-bit key and operates faster than RSA, which uses a 1024-bit key. Moreover, the lightweight AEAD cipher is designed to be efficiently implemented in a resource-constrained environment such as in IoT and provides data confidentiality/integrity and authentication.
5.2. Security against Typical Threats
- Impersonation attack. In D2D the token generation step, each UE is issued a D2D token, which is signed by the gNB. When gNBs generate the token, they authenticate the validity of the UE by comparing the identity of the UE in UDM. After this authentication process, gNBs complete the generation of D2D tokens by using their private key. Because of this procedure, the attacker cannot impersonate other UE.
- Eavesdropping. In a secure data transmission step, every instance of data transmission is protected by the lightweight AEAD cipher. In the AEAD encryption process, UE uses its D2D token and context sequence as associated data. Using this associated data, MAC is generated, and thereby UE can check the integrity of the message and the validity of the sender UE. For these reasons, the attacker cannot eavesdrop and cannot fabricate a message.
- Privacy sniffing. The proposed D2D communication system uses the D2D token, which is generated based on SUCI of UE and digital signature of gNB using ECDSA. The D2D token can provide anonymity as a cryptographic identity. For this reason, the attacker cannot recognize the original identity of the UE.
- Free riding attack and location spoofing. When the D2D token is generated by gNB, the validity of the UE is authenticated. This means that each instance of validating a UE is managed by gNB. The D2D token is authenticated in the link setup step in the proposed D2D communication system, and the data transmission is protected by AEAD encryption using a D2D token. Therefore, if a free-riding attack or location spoofing occurs in D2D communication, gNB can handle these situations by eliminating malicious UE.
6. Conclusions
Author Contributions
Acknowledgments
Conflicts of Interest
References
- Tehrani, M.N.; Uysal, M.; Yanikomeroglu, H. Device-to-device communication in 5G cellular networks: Challenges, solutions, and future directions. IEEE Commun. Mag. 2014, 52, 86–92. [Google Scholar] [CrossRef]
- Jeong, M.; Ahn, S. A network coding-aware routing mechanism for time-sensitive data delivery in multi-hop wireless networks. J. Inf. Process. Syst. 2017, 13, 1544–1553. [Google Scholar]
- Doppler, K.; Rinne, M.P.; Janis, P.; Ribeiro, C.; Hugl, K. Device-to-device communications; functional prospects for LTE-advanced networks. In Proceedings of the 2009 IEEE International Conference on Communications Workshops, Dresden, Germany, 14–18 June 2009; pp. 1–6. [Google Scholar]
- Chen, S.; Hu, J.; Shi, Y.; Peng, Y.; Fang, J.; Zhao, R.; Zhao, L. Vehicle-to-everything (V2X) services supported by LTE-based systems and 5G. IEEE Commun. Stand. Mag. 2017, 1, 70–76. [Google Scholar] [CrossRef]
- Zhang, S.; Wang, Y.; Zhou, W. Towards secure 5G networks: A Survey. Comput. Netw. 2019, 162, 106871. [Google Scholar] [CrossRef]
- Lin, Z.; Du, L.; Gao, Z.; Huang, L.; Du, X. Efficient device-to-device discovery and access procedure for 5G cellular network. Wirel. Commun. Mob. Comput. 2016, 16, 1282–1289. [Google Scholar] [CrossRef]
- Li, S.; Da Xu, L.; Zhao, S. 5G Internet of Things: A survey. J. Ind. Inf. Integr. 2018, 10, 1–9. [Google Scholar] [CrossRef]
- Daoud, W.B.; Obaidat, M.S.; Meddeb-Makhlouf, A.; Zarai, F.; Hsiao, K.F. TACRM: Trust access control and resource management mechanism in fog computing. Hum.-Centric Comput. Inf. Sci. 2019, 9, 28. [Google Scholar] [CrossRef]
- Stallings, W. Cryptography and Network Security: Principles and Practice; Pearson: Upper Saddle River, NJ, USA, 2017. [Google Scholar]
- NIST Computer Security Resource Center. Lightweight Cryptography Project. Available online: https://csrc.nist.gov/projects/lightweight-cryptography (accessed on 8 December 2019).
- Cao, M.; Wang, L.; Xu, H.; Chen, D.; Lou, C.; Zhang, N.; Zhu, Y.; Qin, Z. Sec-D2D: A Secure and Lightweight D2D Communication System With Multiple Sensors. IEEE Access 2019, 7, 33759–33770. [Google Scholar] [CrossRef]
- Abro, A.; Deng, Z.; Memon, K.A. A Lightweight Elliptic-Elgamal-Based Authentication Scheme for Secure Device-to-Device Communication. Future Internet 2019, 11, 108. [Google Scholar] [CrossRef]
- Javed, Y.; Khan, A.S.; Qahar, A.; Abdullah, J. EEoP: A lightweight security scheme over PKI in D2D cellular networks. J. Telecommun. Electron. Comput. Eng. 2017, 9, 99–105. [Google Scholar]
- Mohseni-Ejiyeh, A.; Ashouri-Talouki, M.; Mahdavi, M. An Incentive-Aware Lightweight Secure Data Sharing Scheme for D2D Communication in 5G Cellular Networks. ISeCure 2018, 10, 15–27. [Google Scholar]
- Tan, H.; Song, Y.; Xuan, S.; Pan, S.; Chung, I. Secure D2D group authentication employing smartphone sensor behavior analysis. Symmetry 2019, 11, 969. [Google Scholar] [CrossRef]
- Baskaran, S.B.M.; Raja, G. A Lightweight Incognito Key Exchange Mechanism for LTE-A Assisted D2D Communication. In Proceedings of the 2017 Ninth International Conference on Advanced Computing (ICoAC), Chennai, India, 14–16 December 2017; pp. 301–307. [Google Scholar]
- Sun, Y.; Cao, J.; Ma, M.; Li, H.; Niu, B.; Li, F. Privacy-Preserving Device Discovery and Authentication Scheme for D2D Communication in 3GPP 5G HetNet. In Proceedings of the 2019 International Conference on Computing, Networking and Communications (ICNC), Honolulu, HI, USA, 18–21 February 2019; pp. 425–431. [Google Scholar]
- Carugi, M. Key features and requirements of 5G/IMT-2020 networks. In Proceedings of the ITU Arab Forum on Emerging Technologies, Algiers, Algeria, 14–15 Feburary 2018. [Google Scholar]
- Tschofenig, H.; Pegourie-Gonnard, M.; Unit, I.B. Performance of State-of-the-Art Cryptography on ARM-based Microprocessors. In Proceedings of the NIST Lightweight Cryptography Workshop 2015 Session VII: Implementations & Performance, Gaithersburg, MD, USA, 20–21 July 2015. [Google Scholar]
- Rezvani, B.; Diehl, W. Hardware Implementations of NIST Lightweight Cryptographic Candidates: A First Look. In Proceedings of the NIST Lightweight Cryptography Workshop 2019, Gaithersburg, MD, USA, 4–6 November 2019. [Google Scholar]

| Ref. | Security Function | Considered D2D Step | ||||
|---|---|---|---|---|---|---|
| Conf. / Int. | Auth. | Anon. | D.D. | L.S. | D.T. | |
| Mingsheng Cao et al. [11] | √ | √ | √ | √ | √ | |
| Adeel Abro et al. [12] | √ | √ | √ | √ | √ | |
| Yasir Javed et al. [13] | √ | √ | √ | √ | √ | |
| Atefeh Mohseni-Ejiyeh et al. [14] | √ | √ | √ | √ | √ | |
| Haowen Tan et al. [15] | √ | √ | √ | √ | √ | |
| Sheeba Backia Mary Baskaran et al. [16] | √ | √ | √ | √ | √ | |
| Yunqing Sun et al. [17] | √ | √ | √ | √ | √ | |
| Cadidates | Type | Functionality |
|---|---|---|
| ACE | Permutation based | AEAD and Hashing |
| ASCON | Permutation based | AEAD and Hashing |
| COMET | Block cipher based | AEAD only |
| DryGASCON | Permutation based | AEAD and Hashing |
| Elephant | Permutation based | AEAD only |
| ESTATE | Tweakable block cipher based | AEAD only |
| ForkAE | Tweakable block cipher based | AEAD only |
| GIFT-COFB | Block cipher based | AEAD only |
| Gimli | Permutation based | AEAD and Hashing |
| Grain-128AEAD | Stream cipher based | AEAD only |
| HYENA | Block cipher based | AEAD only |
| ISAP | Permutation based | AEAD only |
| KNOT | Permutation based | AEAD and Hashing |
| LOTUS-AEAD/LOCUS-AEAD | Tweakable block cipher based | AEAD only |
| mixFeed | Block cipher based | AEAD only |
| ORANGE | Permutation based | AEAD and Hashing |
| Oribatida | Permutation based | AEAD only |
| PHOTON-Beetle | Permutation based | AEAD and Hashing |
| Pyjamask | Block cipher based | AEAD only |
| Romulus | Tweakable block cipher based | AEAD only |
| SAEAES | Block cipher based | AEAD only |
| Saturnin | Block cipher based | AEAD and Hashing |
| SKINNY-AEAD/SKINNY-HASH | Tweakable block cipher based | AEAD and Hashing |
| SPARKLE | Permutation based | AEAD and Hashing |
| SPIX | Permutation based | AEAD only |
| SpoC | Permutation based | AEAD only |
| Spook | Tweakable block cipher based | AEAD only |
| Subterranean 2.0 | Permutation based | AEAD and Hashing |
| SUNDAE-GIFT | Block cipher based | AEAD only |
| TinyJambu | Block cipher based | AEAD only |
| WAGE | Permutation based | AEAD only |
| Xoodyak | Permutation based | AEAD and Hashing |
| Step | Transmission Latency | Processing Time of Cryptographic Algorithm | |||
|---|---|---|---|---|---|
| ECDSA-Sign | ECDSA-Verify | ECDH | AEAD | ||
| Step 0 | (2+10) | (1+1) | 1 | - | - |
| Step 1 | (m+1) | - | - | - | - |
| Step 2 | (2+2+2) | - | 2 | 1 | - |
| Step 3 | (n/1460) | - | - | - | 2 |
| Total ( or ) | (19+m+n/1460) | 2 | 3 | 1 | 2 |
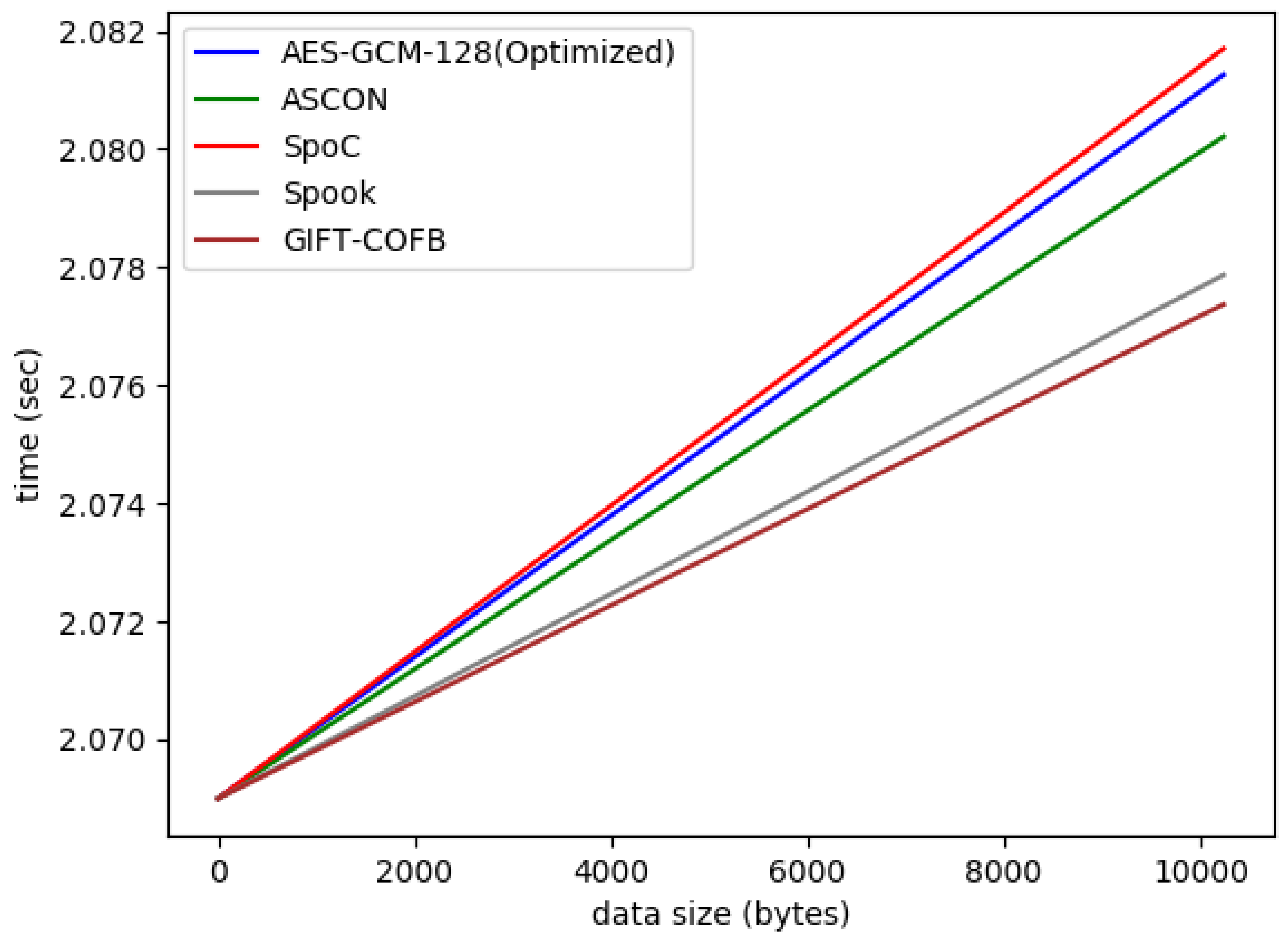
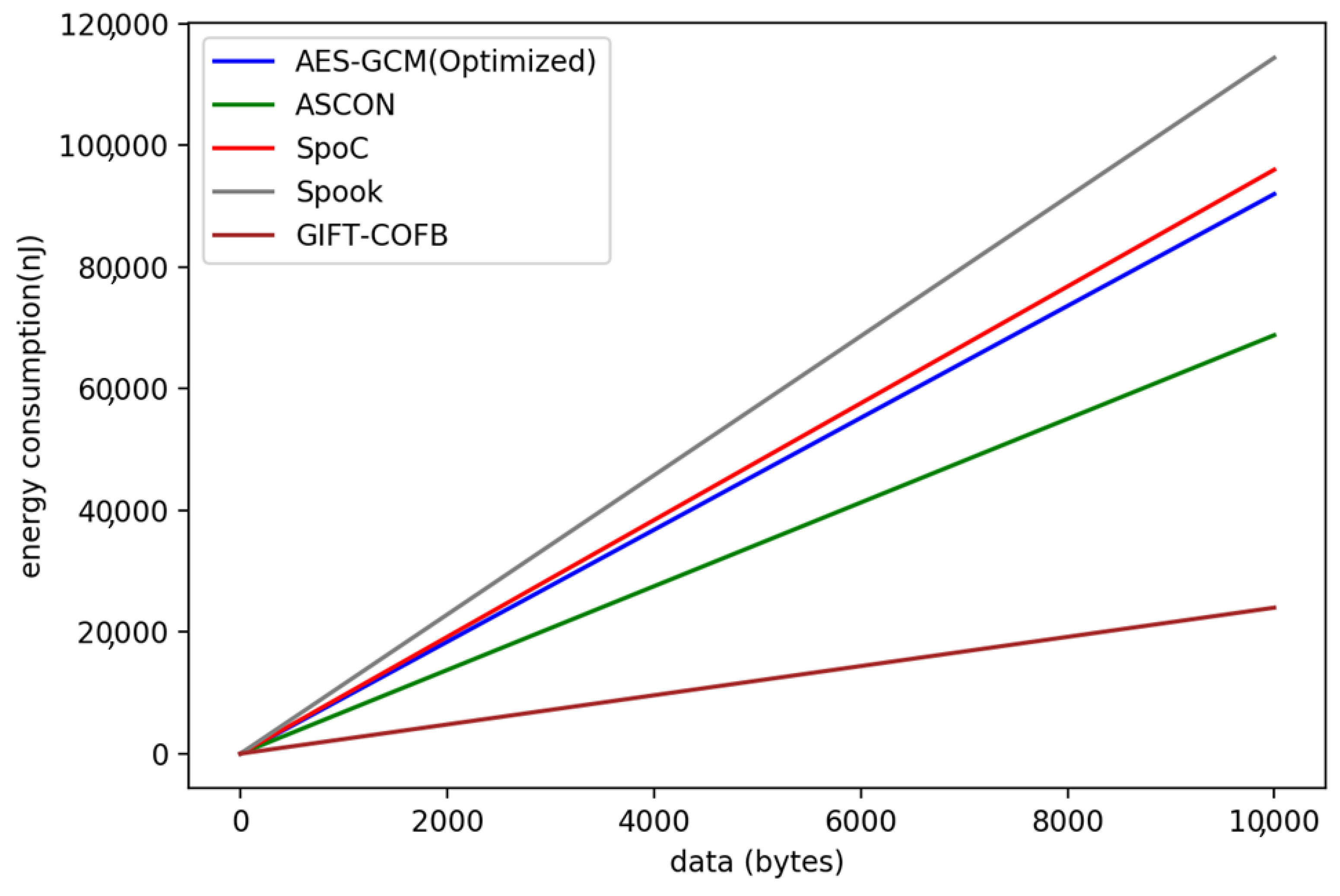
| AEAD Cipher | Area (LUTs) | Power (mW) | Throughput (Mbps) | Energy (nJ/bit) |
|---|---|---|---|---|
| AES-GCM (Optimized) | 1532 | 35.9 | 31.2 | 1.15 |
| ASCON | 1808 | 33.6 | 39.0 | 0.86 |
| SpoC | 1344 | 34.7 | 28.8 | 1.20 |
| Spook | 7082 | 125.9 | 88.3 | 1.43 |
| GIFT-COFB | 2695 | 36.6 | 120.8 | 0.30 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Seok, B.; Sicato, J.C.S.; Erzhena, T.; Xuan, C.; Pan, Y.; Park, J.H. Secure D2D Communication for 5G IoT Network Based on Lightweight Cryptography. Appl. Sci. 2020, 10, 217. https://doi.org/10.3390/app10010217
Seok B, Sicato JCS, Erzhena T, Xuan C, Pan Y, Park JH. Secure D2D Communication for 5G IoT Network Based on Lightweight Cryptography. Applied Sciences. 2020; 10(1):217. https://doi.org/10.3390/app10010217
Chicago/Turabian StyleSeok, Byoungjin, Jose Costa Sapalo Sicato, Tcydenova Erzhena, Canshou Xuan, Yi Pan, and Jong Hyuk Park. 2020. "Secure D2D Communication for 5G IoT Network Based on Lightweight Cryptography" Applied Sciences 10, no. 1: 217. https://doi.org/10.3390/app10010217
APA StyleSeok, B., Sicato, J. C. S., Erzhena, T., Xuan, C., Pan, Y., & Park, J. H. (2020). Secure D2D Communication for 5G IoT Network Based on Lightweight Cryptography. Applied Sciences, 10(1), 217. https://doi.org/10.3390/app10010217




_Park.png)

