Detecting Sybil Attacks in Cloud Computing Environments Based on Fail‐Stop Signature
Abstract
:1. Introduction
2. Preliminaries and Related Work
2.1. Sybil Attack
2.2. Related Work
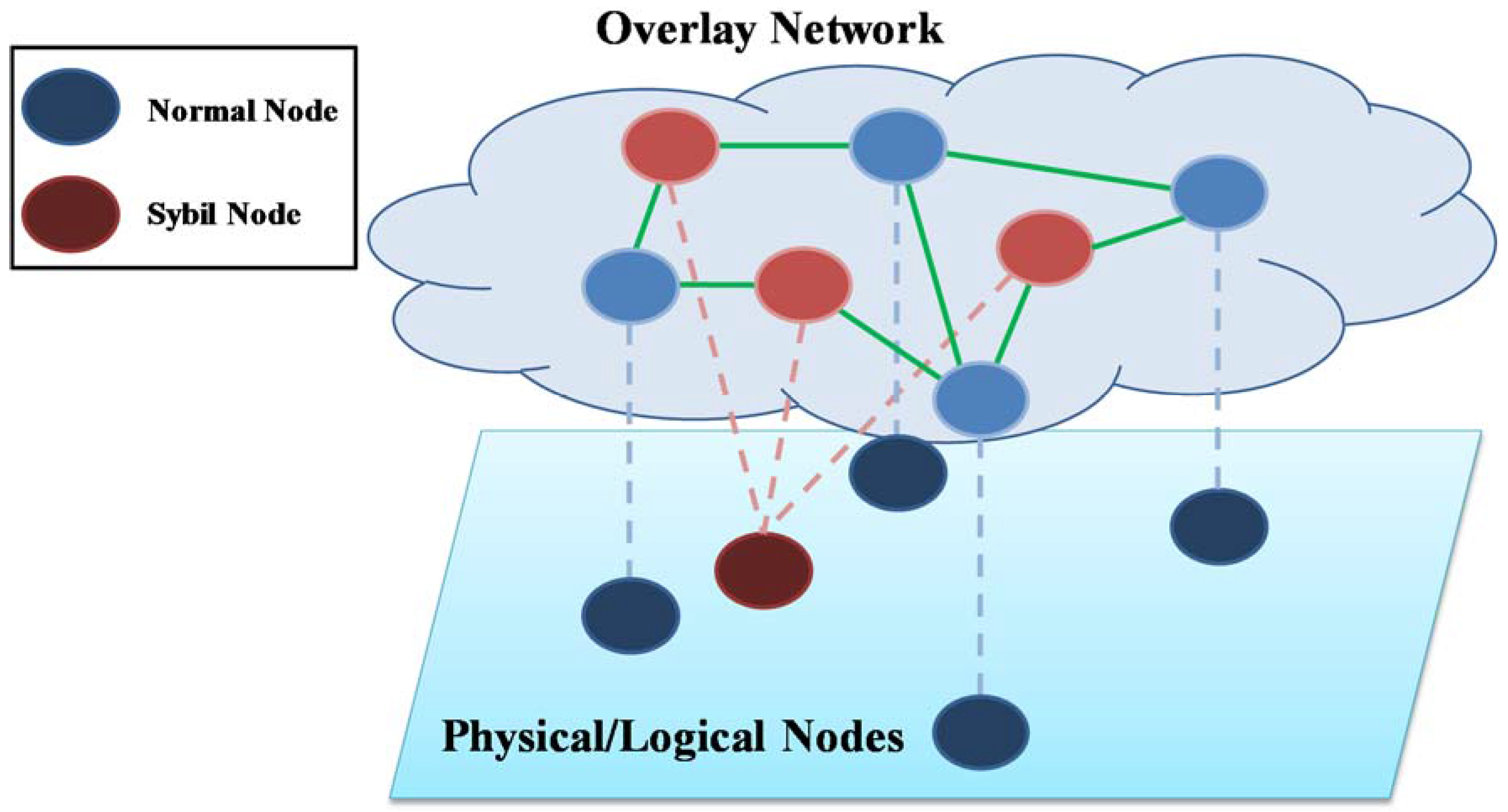
2.3. System Model
2.4. Problem Definition
- Safety: If a normal node (nodei) encounters a Sybil node (nodej) performing the Sybil attack by generating multiple identities, nodei can determine whether nodej is a Sybil node of the network or not.
- Liveness: If a Sybil node (nodej) starts the Sybil attack, normal nodes eventually detect nodej as a Sybil node.
3. The Proposed Sybil Attack Detection Algorithm
| Algorithm 1. Basic Communication Protocol (Active Thread) | |
| 1: | begin at each round |
| 2: | nodetarget ← selectNode(); |
| 3: | if push mode then |
| 4: | send (informationlocal, nodetarget); |
| 5: | end if |
| 6: | if pull mode then |
| 7: | informationtarget ← receive (nodetarget); |
| 8: | updateInformation (informationlocal, informationtarget); |
| 9: | end if |
| 10: | end |
| Algorithm 2. Basic Communication Protocol (Passive Thread) | |
| 1: | repeat |
| 2: | nodetarget ← waitForNode(); |
| 3: | if push mode then |
| 4: | informationtarget ← receive (nodetarget); |
| 5: | updateInformation (informationlocal, informationtarget); |
| 6: | end if |
| 7: | if pull mode then |
| 8: | send (informationlocal, nodetarget); |
| 9: | end if |
| 10: | until forever; |
| Algorithm 3. Sybil Node Detection Algorithm with the Fail-Stop Signature for nodei | |
| 1: | begin initialization |
| 2: | sybilNodes[j] ← null, ∀j∈ {1 … maxnode}; |
| 3: | conflictCheck[j] ← null, ∀j∈ {1 … maxnode}; |
| 4: | end |
| 5: | begin at each round |
| 6: | if checkSybil() then |
| 7: | return; |
| 8: | end if |
| 9: | if checkConflict() then |
| 10: | if verifySignature() then |
| 11: | sybilNodes[nodetarget] ← informationtarget; |
| 12: | return; |
| 13: | end if |
| 14: | end if |
| 15: | update local information according to Algorithms 1 and 2; |
| 16: | end |
| 17: | function checkSybil() |
| 18: | if ∃ nodetarget ∈ sybilNodes[j], ∀j ∈ {1 … maxnode} then |
| 19: | return true; |
| 20: | else |
| 21: | return false; |
| 22: | end if |
| 23: | end function |
| 24: | function checkConflict() |
| 25: | if conflictCheck[nodetarget] != informationtarget then |
| 26: | return true; |
| 27: | else |
| 28: | return false; |
| 29: | end function |
| 30: | function verifySignature() |
| 31: | verify nodetarget‘s signature based on the fail-stop signature |
| 32: | if nodetarget‘s message is forged then |
| 33: | return true; |
| 34: | else |
| 35: | return false; |
| 36: | end if |
| 37: | end function |
4. Proof and Performance Evaluation of the Algorithm
4.1. Proof of the Algorithm
4.2. Experimental Results
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Douceur, J.R. The sybil attack. In Peer-to-Peer Systems: First International Workshop, IPTPS 2002, Cambridge, MA, USA, March 7–8, 2002 Revised Papers; Druschel, P., Kaashoek, F., Rowstron, A., Eds.; Springer: Berlin/Heidelberg, Germany, 2002; pp. 251–260. [Google Scholar]
- Wang, L.; Kangasharju, J. Real-world sybil attacks in bittorrent mainline DHT. In Proceedings of the 2012 IEEE Global Communications Conference (GLOBECOM), Anaheim, CA, USA, 3–7 December 2012; pp. 826–832.
- Wang, L.; Kangasharju, J. Measuring large-scale distributed systems: Case of bittorrent mainline DHT. In Proceedings of the 2013 IEEE Thirteenth International Conference on Peer-to-Peer Computing (P2P), Trento, Italy, 9–11 September 2013; pp. 1–10.
- Yu, H.; Kaminsky, M.; Gibbons, P.B.; Flaxman, A.D. Sybilguard: Defending against sybil attacks via social networks. IEEE/ACM Trans. Netw. 2008, 16, 576–589. [Google Scholar] [CrossRef]
- Ssu, K.-F.; Wang, W.-T.; Chang, W.-C. Detecting sybil attacks in wireless sensor networks using neighboring information. Comput. Netw. 2009, 53, 3042–3056. [Google Scholar] [CrossRef]
- Yu, B.; Xu, C.-Z.; Xiao, B. Detecting sybil attacks in vanets. J. Parallel Distrib. Comput. 2013, 73, 746–756. [Google Scholar] [CrossRef]
- Chang, S.; Qi, Y.; Zhu, H.; Zhao, J.; Shen, X. Footprint: Detecting sybil attacks in urban vehicular networks. IEEE Trans. Parallel Distrib. Syst. 2012, 23, 1103–1114. [Google Scholar] [CrossRef]
- Abbas, S.; Merabti, M.; Llewellyn-Jones, D.; Kifayat, K. Lightweight sybil attack detection in manets. IEEE Syst. J. 2013, 7, 236–248. [Google Scholar] [CrossRef]
- Wang, G.; Musau, F.; Guo, S.; Abdullahi, M.B. Neighbor similarity trust against sybil attack in P2P e-commerce. IEEE Trans. Parallel Distrib. Syst. 2015, 26, 824–833. [Google Scholar] [CrossRef]
- Lim, J.; Suh, T.; Gil, J.; Yu, H. Scalable and leaderless byzantine consensus in cloud computing environments. Inf. Syst. Front. 2014, 16, 19–34. [Google Scholar] [CrossRef]
- Hsu, C.-H.; Ma, J.; Obaidat, M.S. Dynamic intelligence towards merging cloud and communication services. Inf. Syst. Front. 2014, 16, 1–5. [Google Scholar] [CrossRef]
- Javanmardi, S.; Shojafar, M.; Amendola, D.; Cordeschi, N.; Liu, H.; Abraham, A. Hybrid job scheduling algorithm for cloud computing environment. In Proceedings of the Fifth International Conference on Innovations in Bio-Inspired Computing and Applications IBICA 2014; Kömer, P., Abraham, A., Snášel, V., Eds.; Springer International Publishing: Cham, Switzerland, 2014; pp. 43–52. [Google Scholar]
- Zhu, W.; Lee, C. A security protection framework for cloud computing. J. Inf. Process. Syst. 2016, 12, 538–547. [Google Scholar]
- Kar, J.; Mishra, M.R. Mitigating threats and security metrics in cloud computing. J. Inf. Process. Syst. 2016, 12, 226–233. [Google Scholar]
- Hanen, J.; Kechaou, Z.; Ayed, M.B. An enhanced healthcare system in mobile cloud computing environment. Viet. J. Comput. Sci. 2016, 3, 267–277. [Google Scholar] [CrossRef]
- Alharbi, F.; Atkins, A.; Stanier, C. Understanding the determinants of cloud computing adoption in saudi healthcare organisations. Complex Intell. Syst. 2016, 2, 155–171. [Google Scholar] [CrossRef]
- Salam, M.I.; Yau, W.-C.; Chin, J.-J.; Heng, S.-H.; Ling, H.-C.; Phan, R.C.-W.; Poh, G.S.; Tan, S.-Y.; Yap, W.-S. Implementation of searchable symmetric encryption for privacy-preserving keyword search on cloud storage. Hum.-Centric Comput. Inf. Sci. 2015, 5, 19. [Google Scholar] [CrossRef]
- Keegan, N.; Ji, S.-Y.; Chaudhary, A.; Concolato, C.; Yu, B.; Jeong, D.H. A survey of cloud-based network intrusion detection analysis. Hum.-Centric Comput. Inf. Sci. 2016, 6, 19. [Google Scholar] [CrossRef]
- Baker, T.; Mackay, M.; Shaheed, A.; Aldawsari, B. Security-oriented cloud platform for soa-based scada. In Proceedings of the 2015 15th IEEE/ACM International Symposium on Cluster, Cloud and Grid Computing, Shenzhen, China, 4–7 May 2015; pp. 961–970.
- Pfitzmann, B.; Hildesheim, U. Fail-stop signatures; principles and applications. In Proceedings of the Eighth World Conference on Computer Security, Audit, and Control, COMPUSEC ’91, London, UK, 30 October–1 November 1991; Elsevier: London, UK; pp. 125–134.
- Lim, J.B.; Jung, D.; Suh, T.; Yu, H. Unstructured membership management for byzantine fault tolerance in clouds. In Proceedings of the 2014 Workshop Proceedings on Architecture of Computing Systems, ARCS 2014, Lübeck, Germany, 25–28 February 2014; pp. 1–8.
- Dinger, J.; Hartenstein, H. Defending the sybil attack in P2P networks: Taxonomy, challenges, and a proposal for self-registration. In Proceedings of the First International Conference on Availability, Reliability and Security (ARES ’06), Vienna, Austria, 20–22 April 2006; pp. 756–763.
- Sit, E.; Morris, R. Security considerations for peer-to-peer distributed hash tables. In Peer-to-Peer Systems: First Internationalworkshop, IPTPS 2002 Cambridge, MA, USA, 7–8 March 2002 Revised Papers; Druschel, P., Kaashoek, F., Rowstron, A., Eds.; Springer: Berlin/Heidelberg, Germany, 2002; pp. 261–269. [Google Scholar]
- Pecori, R. S-kademlia: A trust and reputation method to mitigate a sybil attack in kademlia. Comput. Netw. 2016, 94, 205–218. [Google Scholar] [CrossRef]
- Danezis, G.; Lesniewski-Laas, C.; Kaashoek, M.F.; Anderson, R. Sybil-resistant dht routing. In Proceedings of the 10th European conference on Research in Computer Security, Milan, Italy, 12–14 September 2005; Springer: Milan, Italy, 2005; pp. 305–318. [Google Scholar]
- Castro, M.; Druschel, P.; Ganesh, A.; Rowstron, A.; Wallach, D.S. Secure routing for structured peer-to-peer overlay networks. SIGOPS Oper. Syst. Rev. 2002, 36, 299–314. [Google Scholar] [CrossRef]
- Javanmardi, S.; Shojafar, M.; Shariatmadari, S.; Ahrabi, S.S. Fr trust: A fuzzy reputation-based model for trust management in semantic P2P grids. Int. J. Grid Util. Comput. 2015, 6, 57–66. [Google Scholar] [CrossRef]
- Newsome, J.; Shi, E.; Song, D.; Perrig, A. The sybil attack in sensor networks: Analysis & defenses. In Proceedings of the 3rd International Symposium on Information Processing in Sensor Networks, Berkeley, CA, USA, 26–27 April 2004; ACM: Berkeley, CA, USA, 2004; pp. 259–268. [Google Scholar]
- Rowaihy, H.; Enck, W.; McDaniel, P.; Porta, T.L. Limiting sybil attacks in structured P2P networks. In Proceedings of the IEEE INFOCOM 2007—26th IEEE International Conference on Computer Communications, Anchorage, AK, USA, 6–12 May 2007; pp. 2596–2600.
- Borisov, N. Computational puzzles as sybil defenses. In Proceedings of the Sixth IEEE International Conference on Peer-to-Peer Computing (P2P ’06), Cambridge, UK, 6–8 September 2006; pp. 171–176.
- Steiner, M.; En-Najjary, T.; Biersack, E.W. Exploiting kad: Possible uses and misuses. SIGCOMM Comput. Commun. Rev. 2007, 37, 65–70. [Google Scholar] [CrossRef]
- Jelasity, M.; Guerraoui, R.; Kermarrec, A.-M.; Steen, M.V. The peer sampling service: Experimental evaluation of unstructured gossip-based implementations. In Proceedings of the Middleware 2004: ACM/IFIP/USENIX International Middleware Conference, Toronto, ON, Canada, 18–22 October 2004; Jacobsen, H.-A., Ed.; Springer: Berlin/Heidelberg, Germany, 2004; pp. 79–98. [Google Scholar]
- Bleumer, G. Fail-stop signature. In Encyclopedia of Cryptography and Security; van Tilborg, H.C.A., Jajodia, S., Eds.; Springer: Boston, MA, USA, 2011; pp. 446–447. [Google Scholar]
- Allavena, A.; Demers, A.; Hopcroft, J.E. Correctness of a gossip based membership protocol. In Proceedings of the Twenty-Fourth Annual ACM Symposium on Principles of Distributed Computing, Las Vegas, NV, USA, 17–20 July 2005; ACM: Las Vegas, NV, USA, 2005; pp. 292–301. [Google Scholar]
- Lim, J.; Suh, T.; Yu, H. Unstructured deadlock detection technique with scalability and complexity-efficiency in clouds. Int. J. Commun. Syst. 2014, 27, 852–870. [Google Scholar] [CrossRef]
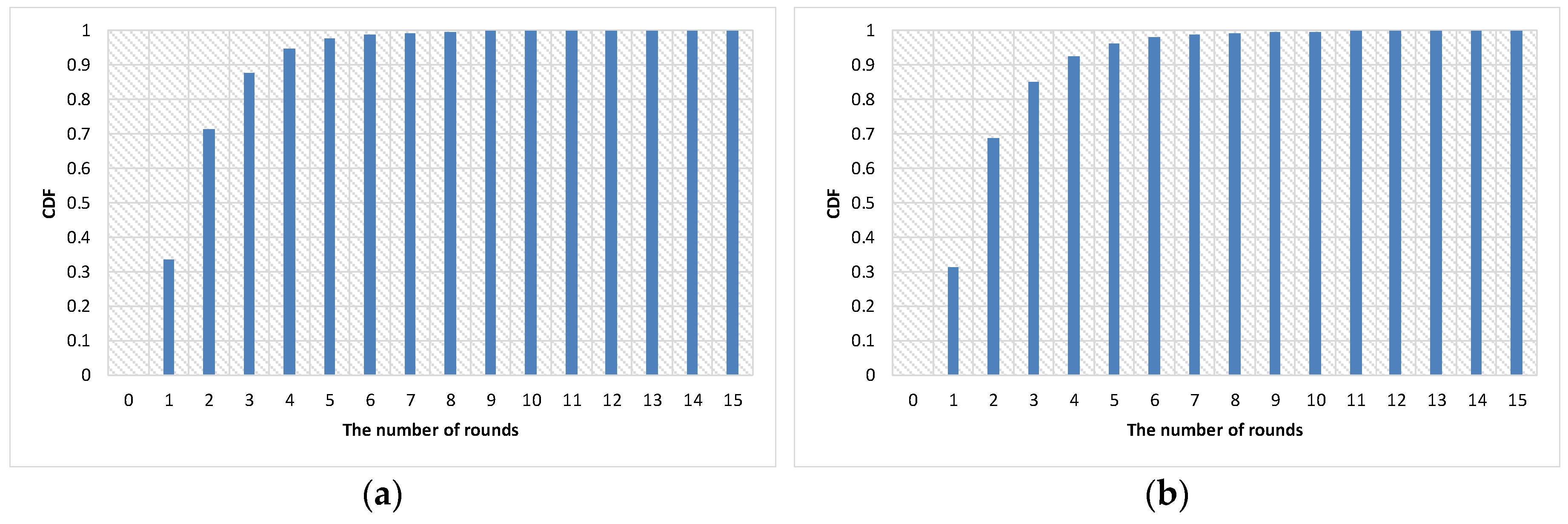
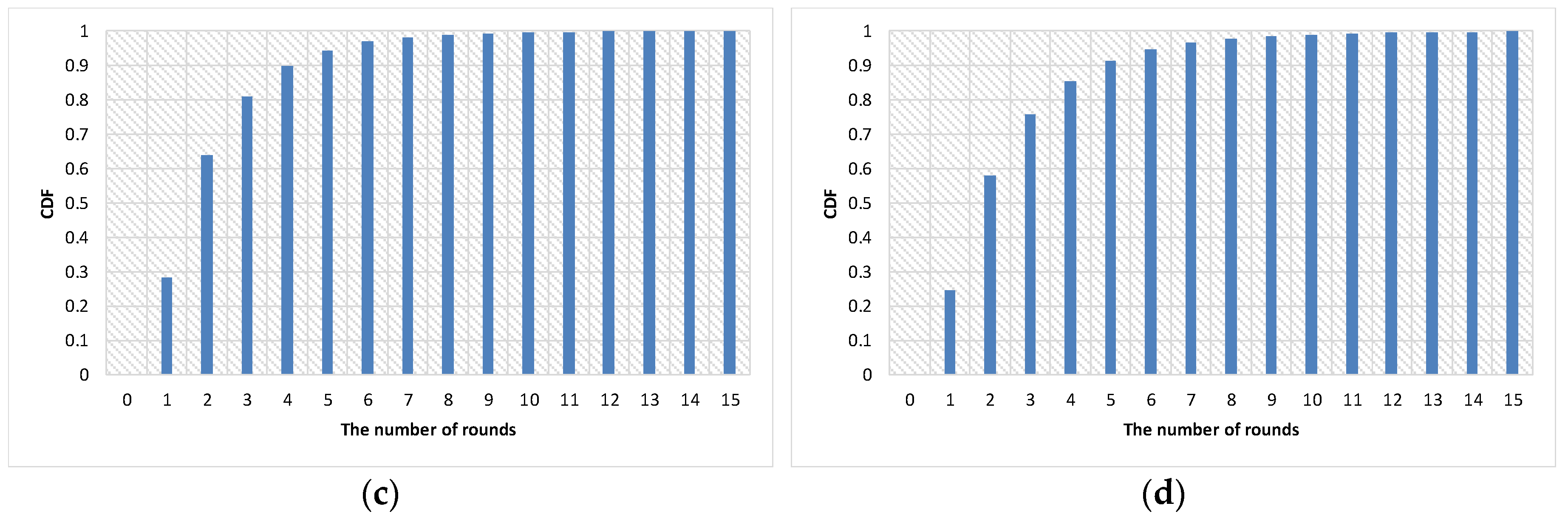
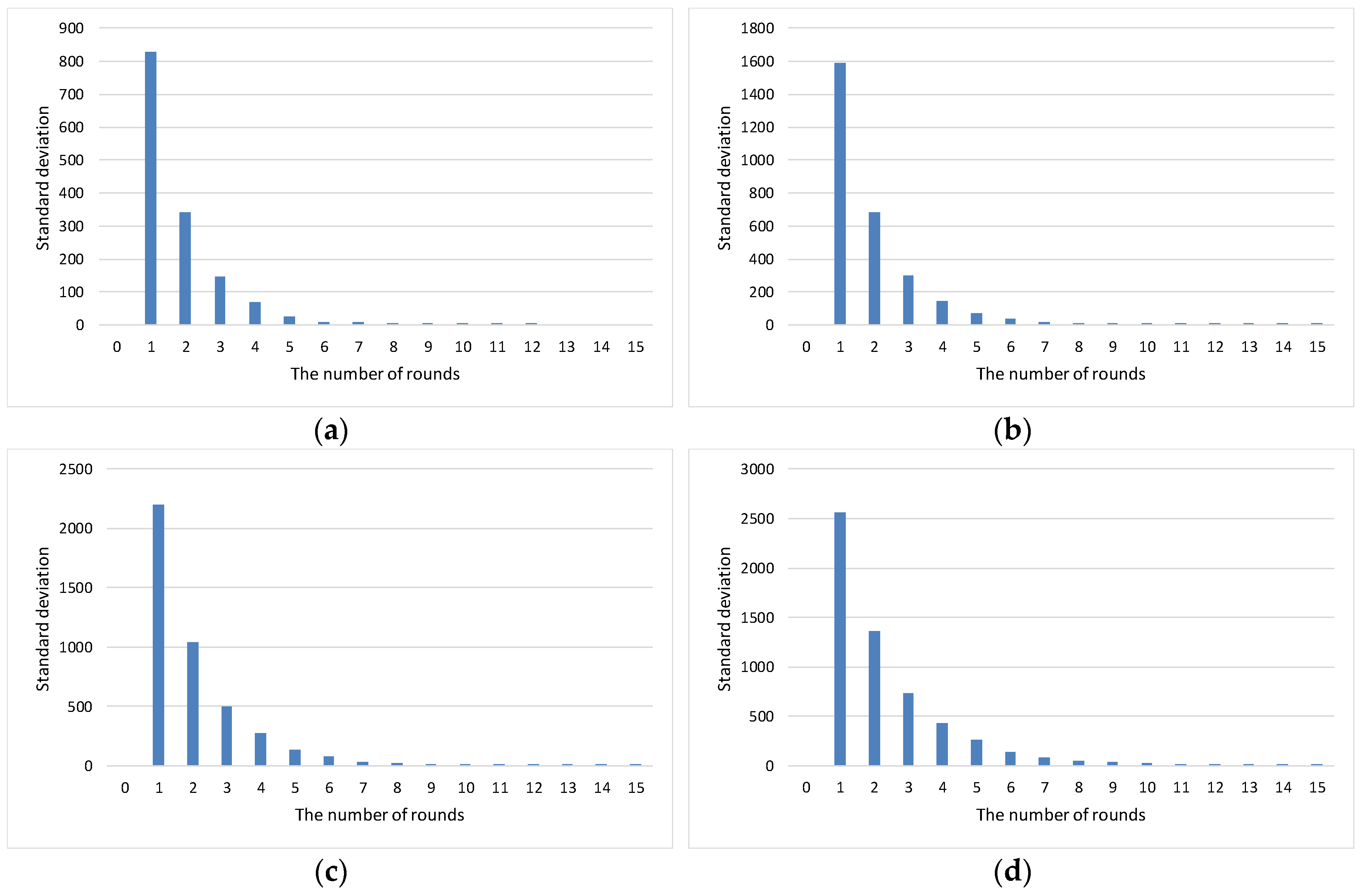
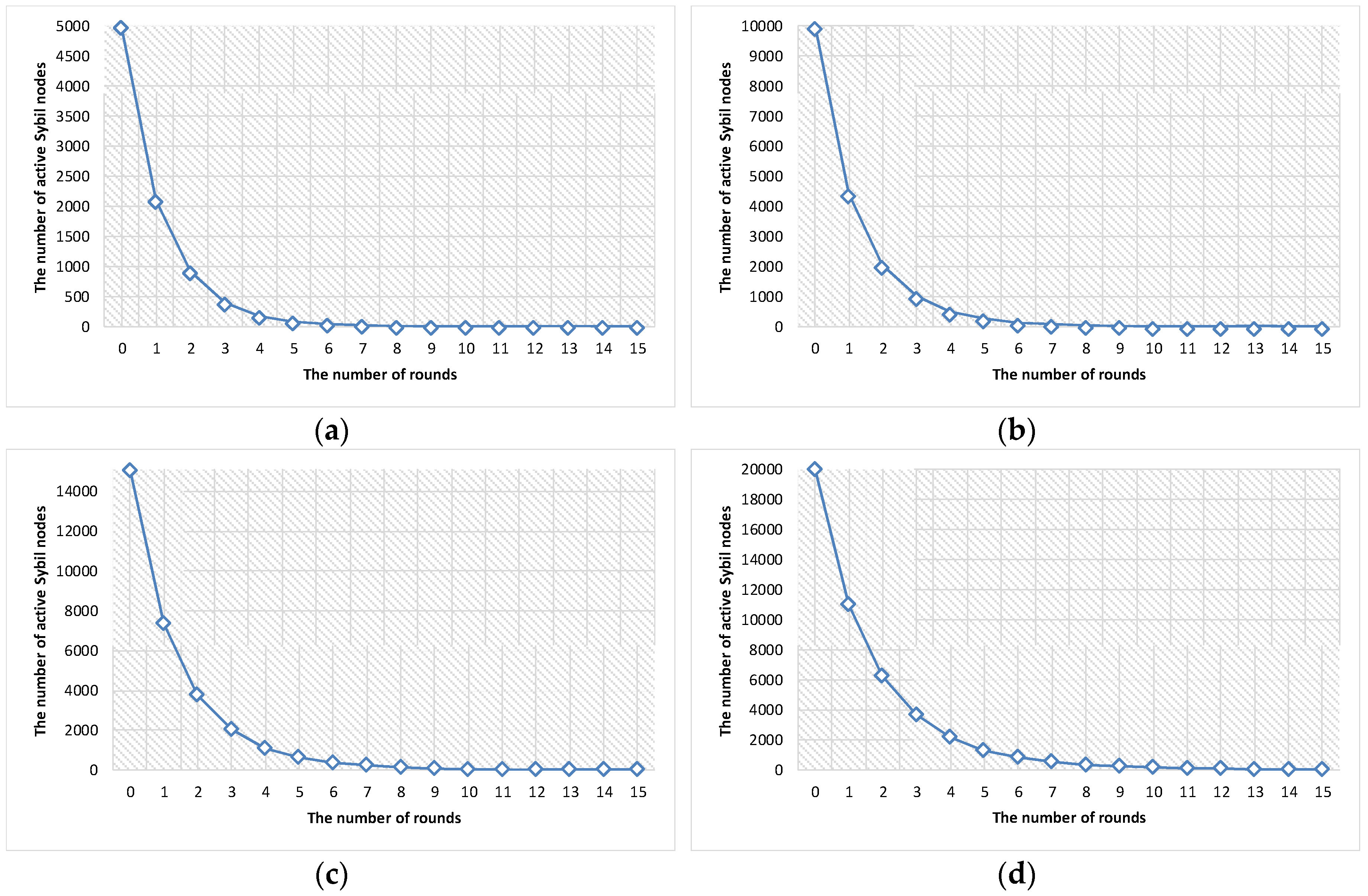
| Parameter | Value |
|---|---|
| Number of nodes | 50,000 |
| Communication mode | Push-pull mode |
| Fanout | 1 |
| Size of local view | 20 |
| Number of rounds | 15 |
| Percentage of Sybil nodes | 0.1, 0.2, 0.3, 0.4 |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license ( http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lim, J.; Yu, H.; Gil, J. Detecting Sybil Attacks in Cloud Computing Environments Based on Fail‐Stop Signature. Symmetry 2017, 9, 35. https://doi.org/10.3390/sym9030035
Lim J, Yu H, Gil J. Detecting Sybil Attacks in Cloud Computing Environments Based on Fail‐Stop Signature. Symmetry. 2017; 9(3):35. https://doi.org/10.3390/sym9030035
Chicago/Turabian StyleLim, JongBeom, HeonChang Yu, and Joon‐Min Gil. 2017. "Detecting Sybil Attacks in Cloud Computing Environments Based on Fail‐Stop Signature" Symmetry 9, no. 3: 35. https://doi.org/10.3390/sym9030035
APA StyleLim, J., Yu, H., & Gil, J. (2017). Detecting Sybil Attacks in Cloud Computing Environments Based on Fail‐Stop Signature. Symmetry, 9(3), 35. https://doi.org/10.3390/sym9030035








