Secure Computation Schemes for Mahalanobis Distance Between Sample Vectors in Combating Malicious Deception
Abstract
1. Introduction
- (1)
- Healthcare: In gene expression analysis and disease diagnosis, Mahalanobis distance enables accurate classification and anomaly detection of pathological samples, contributing to improved diagnostic precision and personalized medical care.
- (2)
- Financial Risk Control: Financial institutions utilize Mahalanobis distance to identify abnormal transactions and potential fraud. This facilitates enhanced risk management and credit evaluation, thus ensuring the stability and security of financial systems.
- (3)
- Pattern Recognition and Computer Vision: In areas such as face recognition and image matching, Mahalanobis distance effectively captures distribution differences in feature spaces, leading to improved algorithm robustness and recognition accuracy.
- (4)
- Secure Collaborative Computing Environments: In scenarios where multiple organizations need to share data without compromising privacy—such as joint diagnoses by medical institutions or cross-department financial risk analysis—secure computation algorithms integrated with Mahalanobis distance become essential. They enable collaborative analysis while protecting sensitive information.
1.1. Related Work
1.2. Motivation and Novelty of the Proposed Method
1.3. Contributions
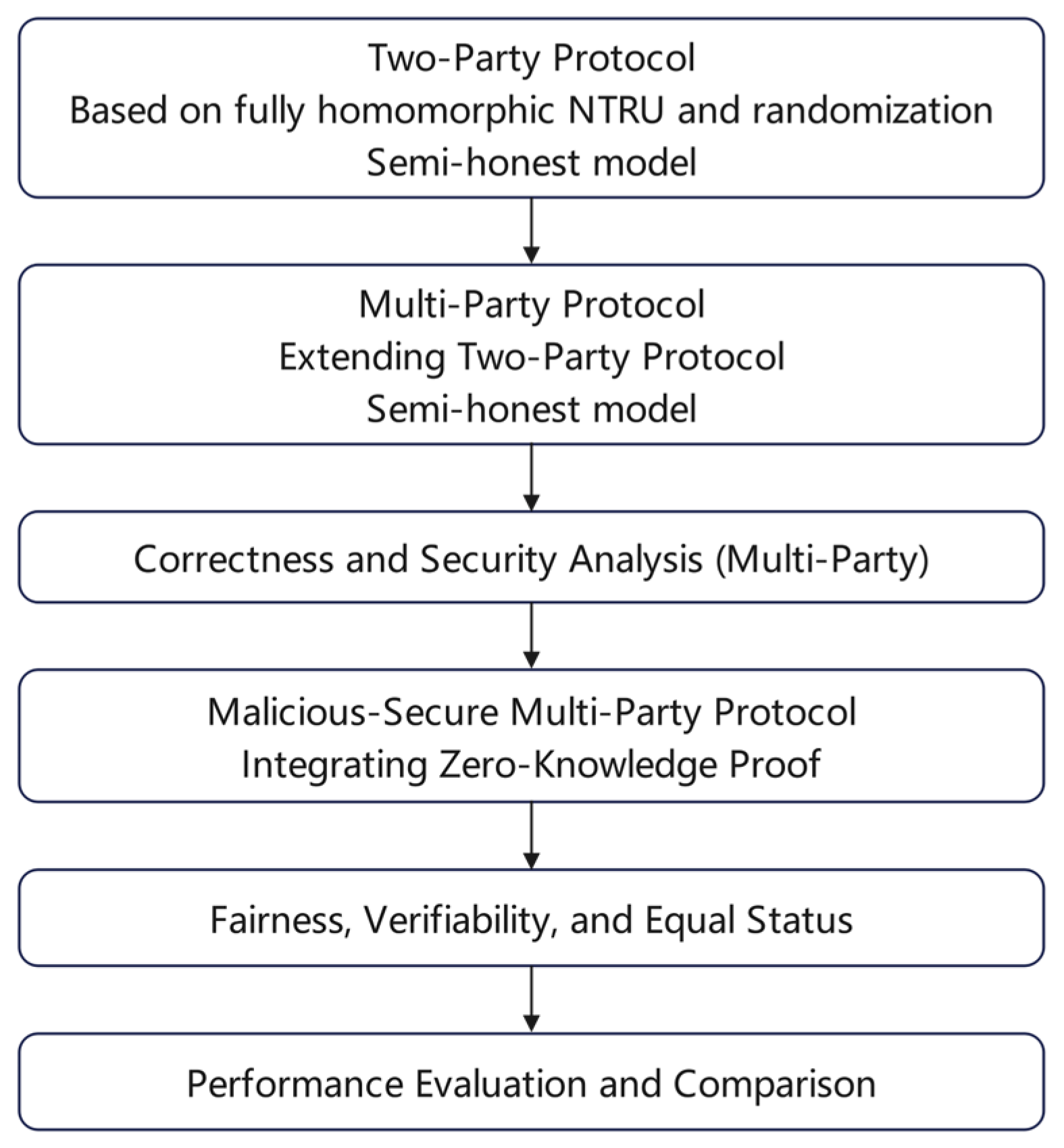
1.4. Structure
2. Preliminary Knowledge
2.1. Fully Homomorphic NTRU Encryption Algorithm
2.2. Security Definition Under Semi-Honest Model
2.3. Mahalanobis Distance
2.4. Zero-Knowledge Proof
- (1)
- selects two sets of random numbers , and , and then performs the following calculations:sends and to .
- (2)
- decrypts and into and , respectively, and then sends and to .
- (3)
- verifies whether holds to determine whether is correctly decrypted and sends and (the proof is omitted). After successful verification, can obtain the information for by calculating or . Specific applications and explanations are provided in Section 5 of this paper.
3. Two-Party Secure Computation Protocol for Mahalanobis Distance Under Semi-Honest Model
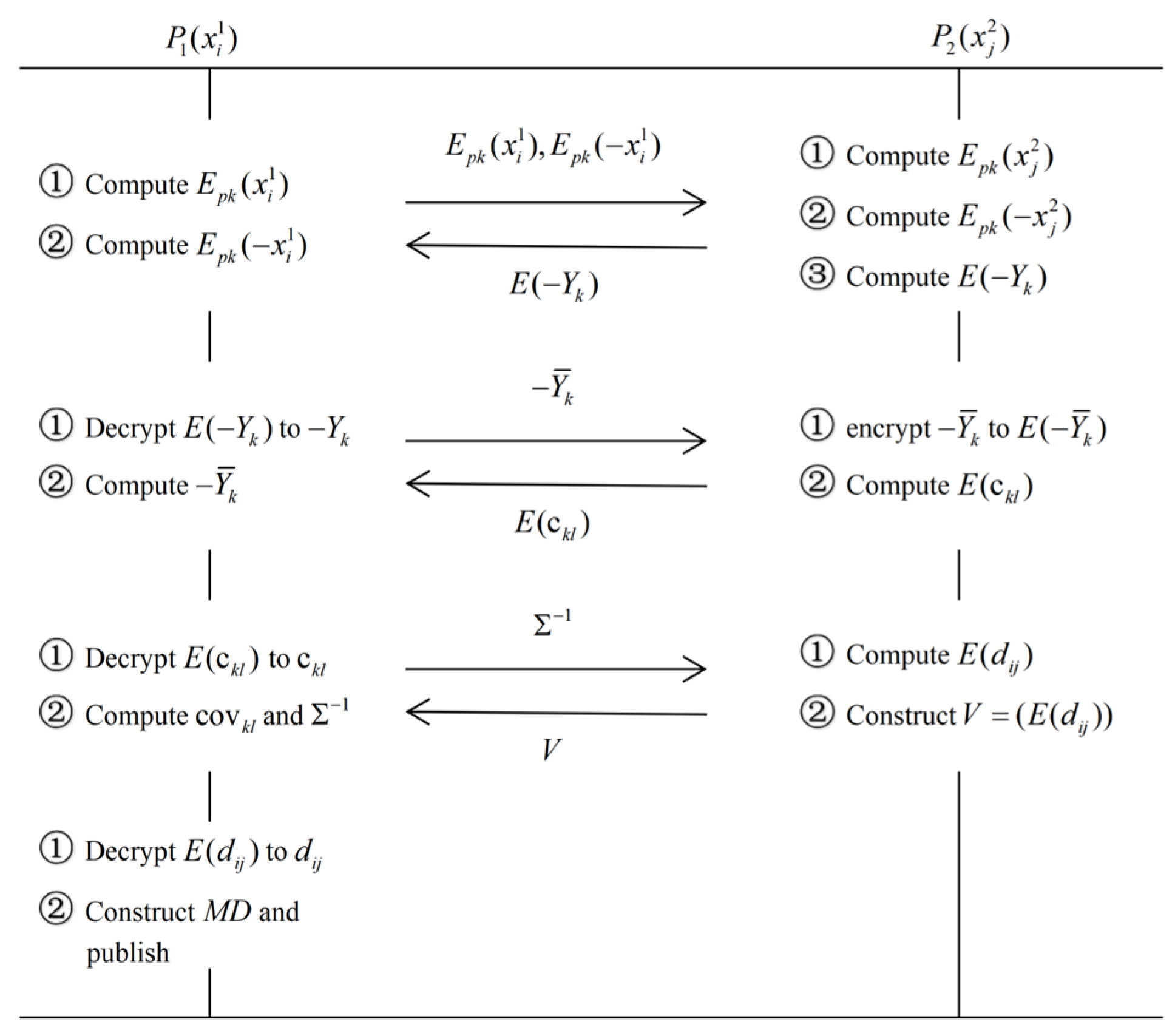
3.1. Specific Protocol
| Algorithm 1: Two-party secure computation protocol for Mahalanobis distance between sample vectors under semi-honest model. |
| Input: Multiple -dimensional private sample vectors and owned by participants and , respectively, where , , , , and . |
| Output: The Mahalanobis distance between each pair of sample vectors and . |
| Preparation: Participant runs the NTRU encryption scheme to generate a public/private key pair and sends the public key to . |
|
|
|
|
|
|
|
|
|
| End of Algorithm 1. |
3.2. Correctness Analysis
3.3. Security Proof
- (1)
- After receiving the input , randomly selects such that .
- (2)
- encrypts each element of vectors and their negated versions using the public key , obtaining and . Similarly, encrypts and their negated versions, obtaining and .
- (3)
- combines all and into a ciphertext matrix of size and all and into a ciphertext matrix of the same size:computesfor .
- (4)
- computes
- (5)
- computes
- (6)
- decrypts to obtain and computesfor and . constructs a main diagonal symmetric plaintext matrix of size :computes the inverse matrix
- (7)
- computesfor and . forms the results into a ciphertext vector:
- (8)
- decrypts each element in to obtain , computes , and forms the vector
4. Multi-Party Secure Computation Protocol for Mahalanobis Distance Between Sample Vectors Under Semi-Honest Model
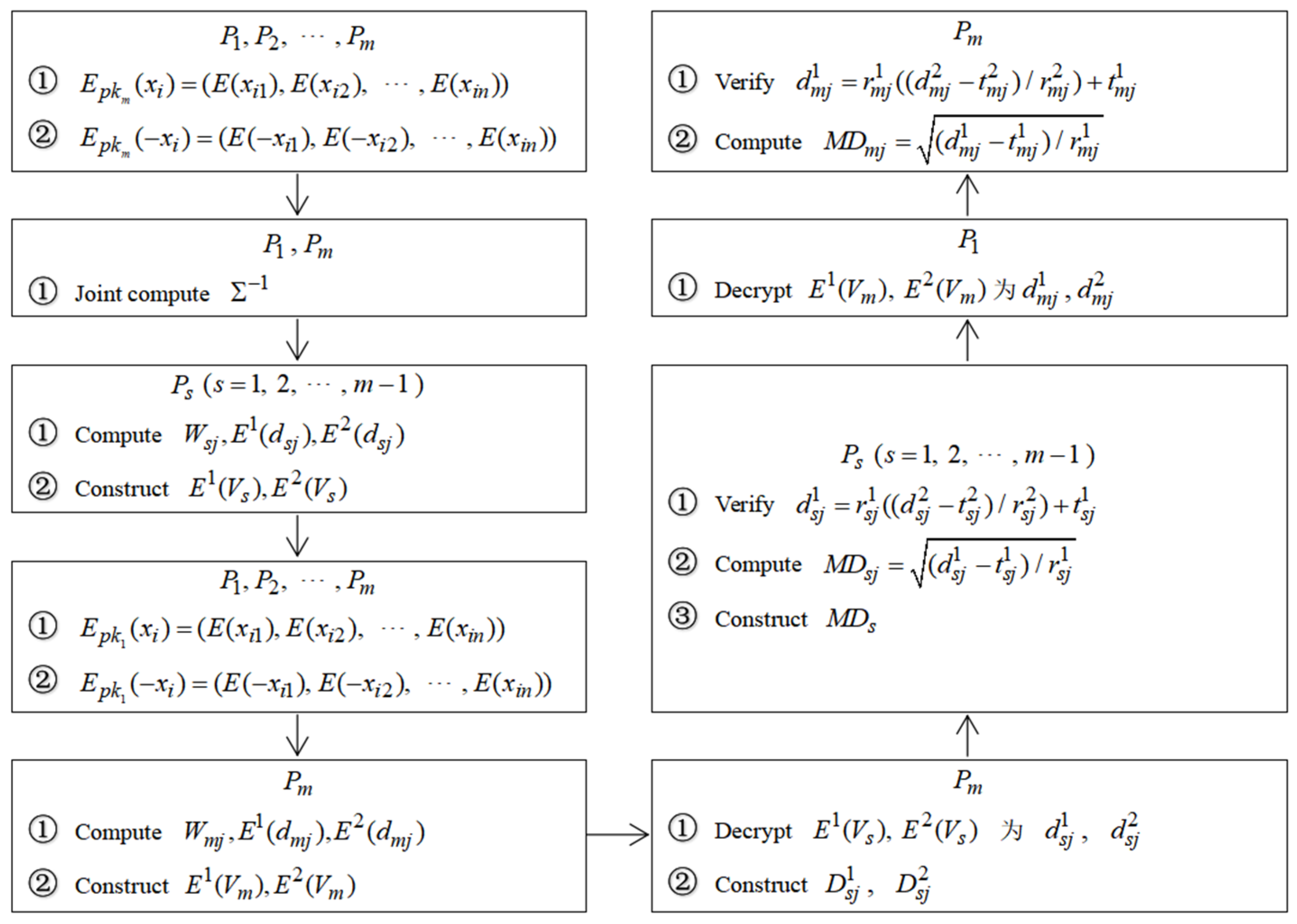
4.1. Specific Protocol
| Algorithm 2: Multi-party secure computation protocol for Mahalanobis distance between sample vectors under semi-honest model. |
| Input: Each participant holds a sample vector ). |
| Output: The Mahalanobis distance between each pair of vectors . |
| Preparation: Participant runs the NTRU encryption scheme to generate a public/private key pair and publishes the public key . |
|
|
|
|
|
|
|
|
| End of Algorithm 2. |
4.2. Correctness Analysis
4.3. Security Analysis
5. Multi-Party Secure Computation Protocol for Mahalanobis Distance Against Malicious Deception
5.1. Specific Protocol
| Algorithm 3: Multi-party secure computation protocol for Mahalanobis distance against malicious deception. |
| Input: Private sample vectors held by participants ). |
| Output: The Mahalanobis distance between each pair of vectors and . |
| Preparation: Participant runs the NTRU encryption scheme to generate a public/private key pair and sends to runs the NTRU encryption scheme to generate a public/private key pair and sends . |
|
|
|
|
|
|
|
|
|
|
|
|
| End of Algorithm 3. |
5.2. Correctness Analysis
5.3. Security Analysis
6. Performance Analysis
6.1. Computational Complexity
6.2. Communication Complexity
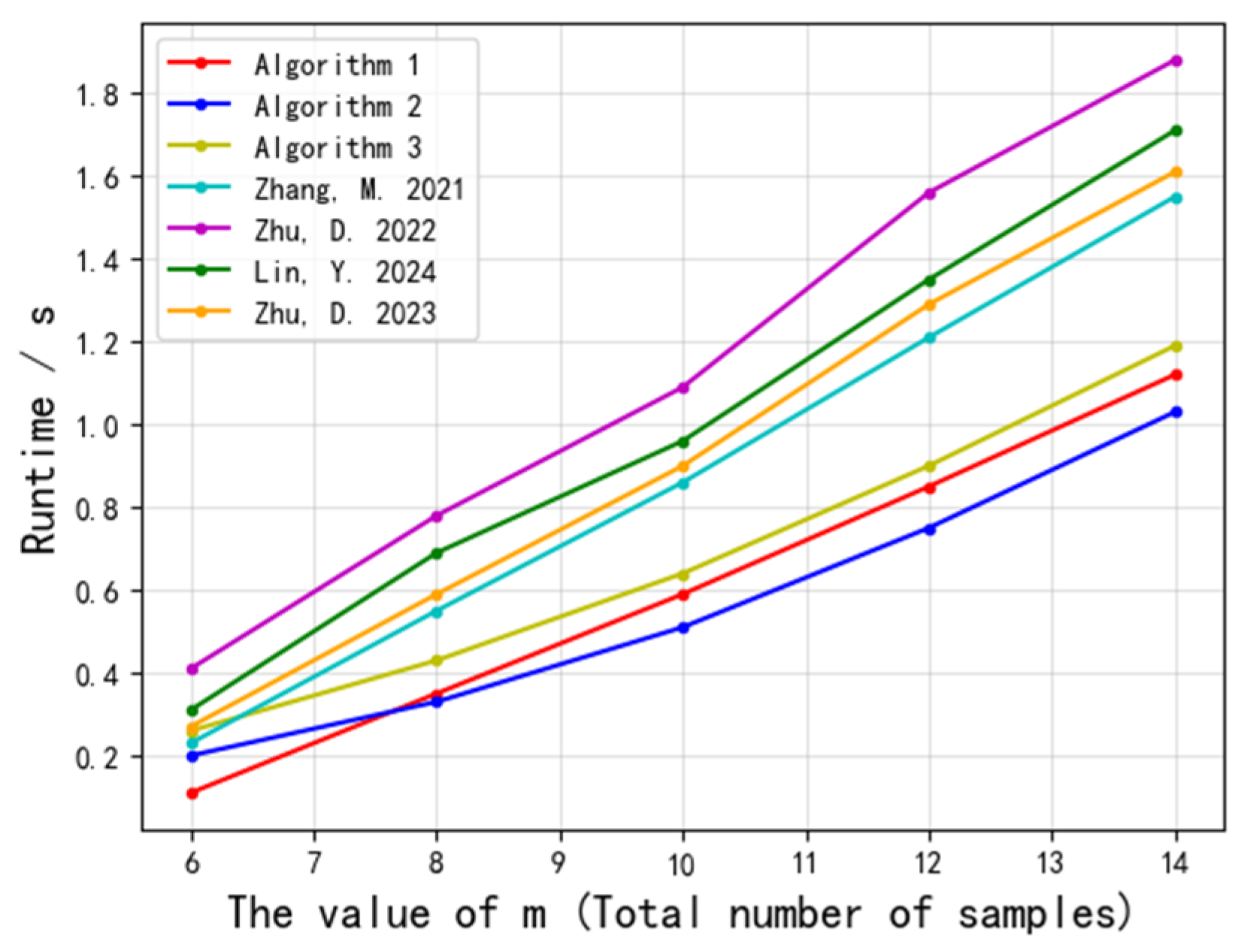
6.3. Experimental Simulation
- (1)
- Encryption and Decryption Overhead: The protocol relies on NTRU-based homomorphic encryption. While NTRU offers high security and quantum resistance, the computational cost for encryption and homomorphic operations increases sharply with both the number of samples and the vector dimensionality, leading to linear or even superlinear growth in computation time and memory usage.
- (2)
- Communication Complexity: Secure multi-party computation schemes require multiple rounds of interaction between parties. As the sample size and the number of participants increase, the number of communication rounds and the amount of data transmitted rapidly scale up, easily causing network bottlenecks.
- (3)
- Resource Constraints: Under current hardware configurations, large-scale datasets may result in memory overflows or significant delays, severely affecting practical usability.
- (1)
- Experiments have not covered large-scale datasets (e.g., >1000 samples, >100 dimensions).
- (2)
- Encryption operations and communication costs increase too rapidly with scale, and no efficient distributed optimization has been developed.
- (1)
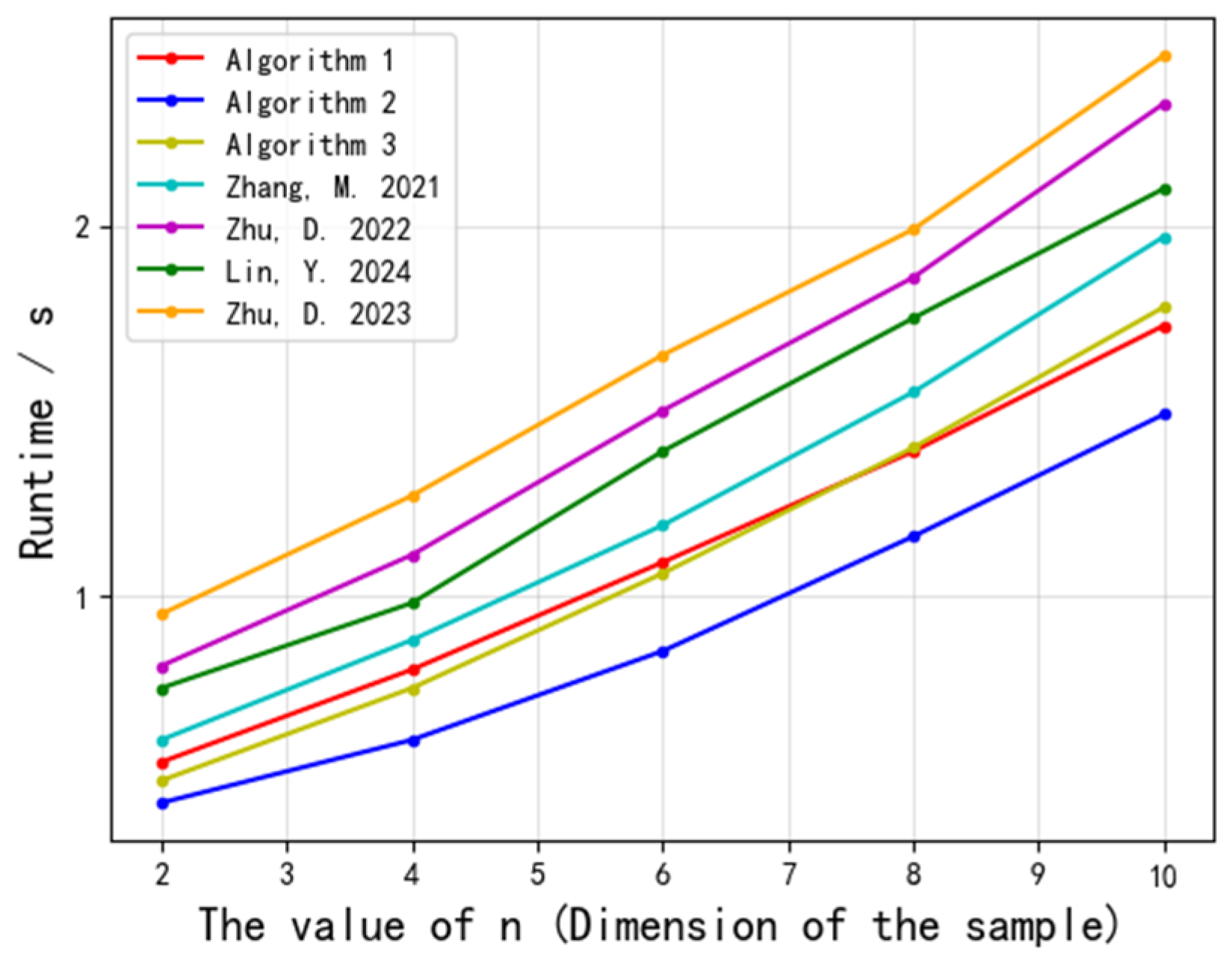
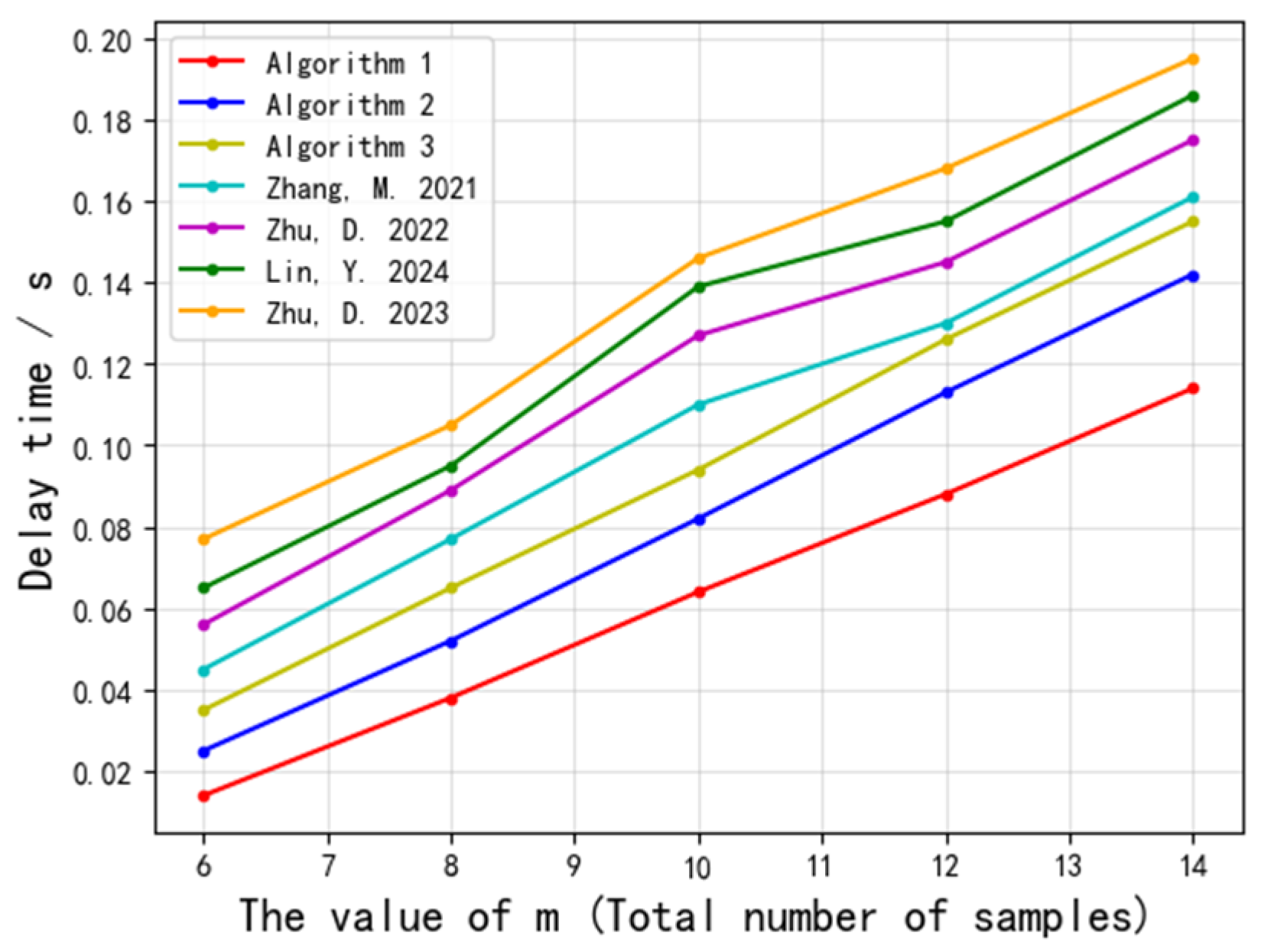
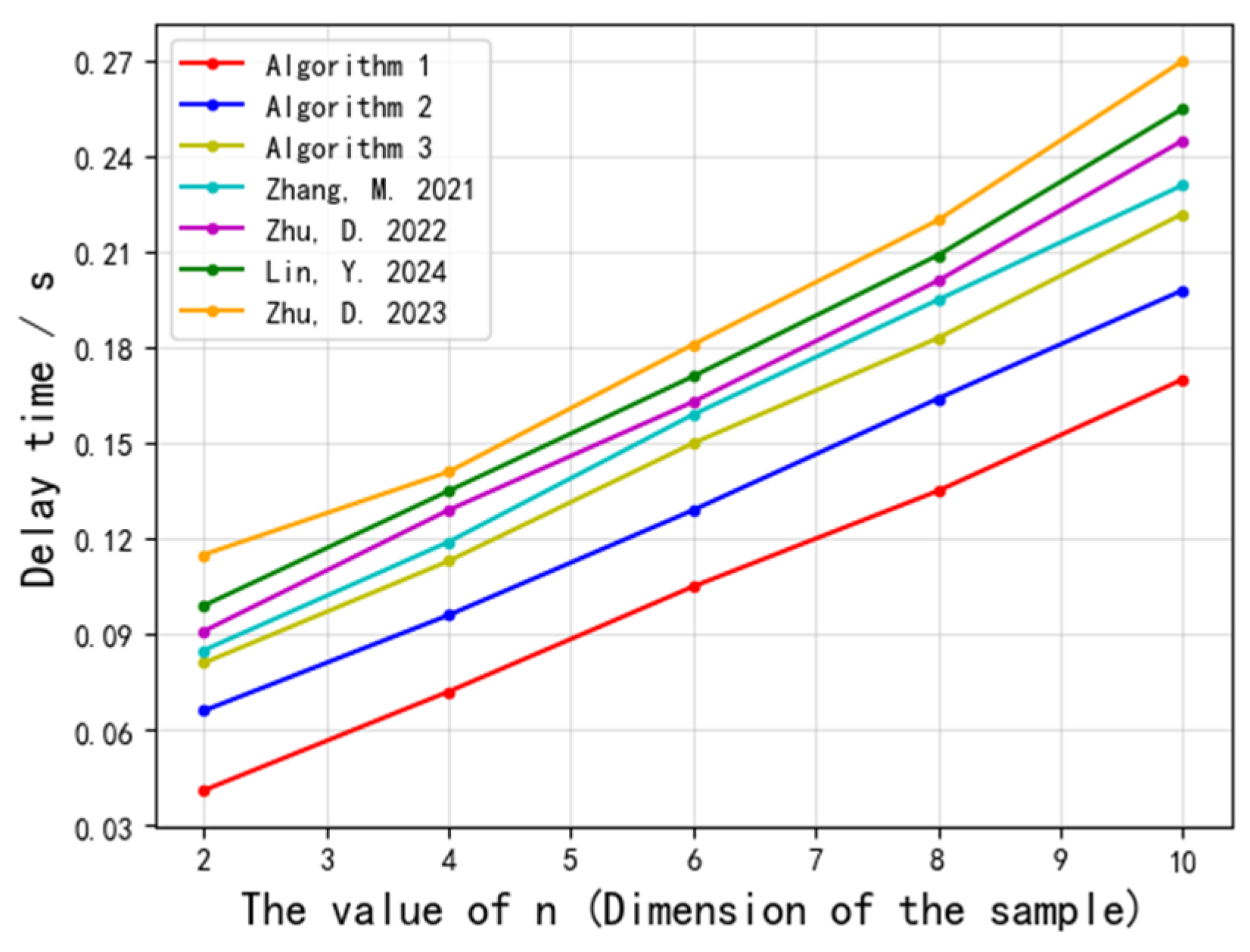
- Execution Time Trends: As shown in Figure 4 and Figure 5, increasing either the number of samples or the dimensionality leads to linear (in sample size) and polynomial (in dimensionality) growth in execution time. While Algorithm 1 exhibits nearly linear growth in execution time with fixed dimensions, it still cannot accommodate extremely large-scale scenarios.
- (2)
- Communication Latency: Our experimental results indicate that communication latency is tied to both the number of participants and the sample size. When the sample size reaches several hundred, the communication overhead becomes significant; in large-scale settings, network costs may become unacceptable.
- (3)
- Scalability Outlook: To support larger datasets, protocol design enhancements such as distributed computation, batch processing, or the adoption of more efficient encryption schemes (e.g., block-based homomorphic encryption or multi-core parallelism) are needed to reduce individual node overhead and improve overall throughput.
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Wang, Q.; Wang, Y.; Zhou, F.; Xu, J.; Zhang, C. Privacy-preserving fair outsourcing polynomial computation without FHE and FPR. Comput. Stand. Interfaces 2025, 91, 103899. [Google Scholar] [CrossRef]
- Zeng, C.; He, D.; Feng, Q.; Yang, X.; Luo, Q. EPAuto: Efficient Privacy-Preserving Machine Learning on AI-powered Autonomous Driving Systems using Multi-Party Computation. ACM Trans. Auton. Adapt. Syst. 2025. [Google Scholar] [CrossRef]
- Park, J. Extremely efficient and privacy-preserving max/min protocol based on multiparty computation in big data. IEEE Trans. Consum. Electron. 2024, 70, 3042–3055. [Google Scholar] [CrossRef]
- Yao, A.C. Protocols for Secure Computations. In Proceedings of the 23rd Annual Symposium on Foundations of Computer Science (SFCS 1982), Washington, DC, USA, 3–5 November 1982; pp. 160–164. [Google Scholar]
- Goldreich, O.; Micali, S.; Wigderson, A. How to play any mental game. In Proceedings of the 19th Annual ACM Symposium on Theory of Computing, New York, NY, USA, 25–27 May 1987; ACM: New York, NY, USA, 1987; pp. 218–229. [Google Scholar]
- Lindell, Y.; Pinkas, B. A proof of security of Yao’s protocol for two-party computation. J. Cryptol. 2009, 22, 161–188. [Google Scholar] [CrossRef]
- Goldwasser, S.; Ben-Or, M.; Wigderson, A. Completeness theorems for noncryptographic fault-tolerant distributed computing. In Proceedings of the 20th Annual ACM Symposium on Theory of Computing (STOC), Chicago, IL, USA, 2–4 May 1988; pp. 1–10. [Google Scholar]
- Liu, X.; Tu, X.; Luo, D.; Xu, G.; Xiong, N.; Chen, X. Secure multi-party computation of graphs’ intersection and union under the malicious model. Electronics 2023, 12, 258. [Google Scholar] [CrossRef]
- Murugeshwari, B.; Selvaraj, D.; Sudharson, K.; Radhika, S. Data Mining with Privacy Protection Using Precise Elliptical Curve Cryptography. Intell. Autom. Soft Comput. 2023, 35, 839–851. [Google Scholar] [CrossRef]
- Issa, W.; Moustafa, N.; Turnbull, B.; Sohrabi, N.; Tari, Z. Blockchain-based federated learning for securing internet of things: A comprehensive survey. ACM Comput. Surv. 2023, 55, 1–43. [Google Scholar] [CrossRef]
- Liao, T.; Peng, C.; Hou, Y. Application of multi-party computation and error correction with image enhancement and convolution neural networks based on cloud computing. IET Image Process. 2023, 17, 1931–1950. [Google Scholar] [CrossRef]
- Tran, A.T.; Luong, T.D.; Karnjana, J.; Huynh, V.N. An efficient approach for privacy preserving decentralized deep learning models based on secure multi-party computation. Neurocomputing 2021, 422, 245–262. [Google Scholar] [CrossRef]
- Nevo, O.; Trieu, N.; Yanai, A. Simple, fast malicious multiparty private set intersection. In Proceedings of the 2021 ACM SIGSAC Conference on Computer and Communications Security, Online, 15–19 November 2021; pp. 1151–1165. [Google Scholar]
- Neelakandan, S.; Beulah, J.R.; Prathiba, L.; Murthy, G.L.N.; Irudaya Raj, E.F.; Arulkumar, N. Blockchain with deep learning-enabled secure healthcare data transmission and diagnostic model. Int. J. Model. Simul. Sci. Comput. 2022, 13, 2241006. [Google Scholar] [CrossRef]
- Fu, A.; Zhang, X.; Xiong, N.; Gao, Y.; Wang, H.; Zhang, J. VFL: A verifiable federated learning with privacy-preserving for big data in industrial IoT. IEEE Trans. Ind. Inform. 2020, 18, 3316–3326. [Google Scholar] [CrossRef]
- Kumar, P.; Kumar, R.; Srivastava, G.; Gupta, G.P.; Tripathi, R.; Gadekallu, T.R.; Xiong, N.N. PPSF: A privacy-preserving and secure framework using blockchain-based machine-learning for IoT-driven smart cities. IEEE Trans. Netw. Sci. Eng. 2021, 8, 2326–2341. [Google Scholar] [CrossRef]
- Khan, N.A.; Jhanjhi, N.Z.; Brohi, S.N.; Almazroi, A.A.; Almazroi, A.A. A secure communication protocol for unmanned aerial vehicles. CMC-Comput. Mater. Contin. 2022, 70, 601–618. [Google Scholar]
- Liu, Y.; Su, Z.; Wang, Y. Energy-efficient and physical-layer secure computation offloading in blockchain-empowered internet of things. IEEE Internet Things J. 2022, 10, 6598–6610. [Google Scholar] [CrossRef]
- Rosulek, M.; Trieu, N. Compact and malicious private set intersection for small sets. In Proceedings of the 2021 ACM SIGSAC Conference on Computer and Communications Security, Online, 15–19 November 2021; pp. 1166–1181. [Google Scholar]
- Chase, M.; Miao, P. Private set intersection in the internet setting from lightweight oblivious PRF. In Proceedings of the Annual International Cryptology Conference, Online, 17–21 August 2020; pp. 34–63. [Google Scholar]
- Chinnasamy, P.; Deepalakshmi, P. HCAC-EHR: Hybrid cryptographic access control for secure EHR retrieval in healthcare cloud. J. Ambient Intell. Humaniz. Comput. 2022, 1–19. [Google Scholar] [CrossRef]
- Zad, S.; Heidari, M.; Hajibabaee, P.; Malekzadeh, M. A survey of deep learning methods on semantic similarity and sentence modeling. In Proceedings of the 2021 IEEE 12th Annual Information Technology, Electronics and Mobile Communication Conference (IEMCON), Vancouver, BC, Canada, 27–30 October 2021; pp. 466–472. [Google Scholar]
- Shi, E.; Aqeel, W.; Chandrasekaran, B.; Maggs, B. Puncturable pseudorandom sets and private information retrieval with near-optimal online bandwidth and time. In Proceedings of the Advances in Cryptology–CRYPTO 2021: 41st Annual International Cryptology Conference, Online, 16–20 August 2021; pp. 641–669. [Google Scholar]
- Xiao, T.; Han, D.; He, J.; Li, K.; de Mello, R. Multi-Keyword ranked search based on mapping set matching in cloud ciphertext storage system. Connect. Sci. 2021, 33, 95–112. [Google Scholar] [CrossRef]
- Poongodi, M.; Malviya, M.; Hamdi, M.; Vijayakumar, V.; Mohammed, M.; Rauf, H.; Al-Dhlan, K. 5G based Blockchain network for authentic and ethical keyword search engine. IET Commun. 2022, 16, 442–448. [Google Scholar]
- Ma, M.; Xu, Y.; Liu, Z. Privacy preserving Hamming distance computing problem of DNA sequences. J. Comput. Appl. 2019, 39, 2636–2640. [Google Scholar]
- McLachlan, G.J. Mahalanobis distance. Resonance 1999, 4, 20–26. [Google Scholar] [CrossRef]
- De Maesschalck, R.; Jouan-Rimbaud, D.; Massart, D.L. The mahalanobis distance. Chemom. Intell. Lab. Syst. 2000, 50, 1–18. [Google Scholar] [CrossRef]
- Mohanta, R.; Gayen, P.; Pal, I.; Sutradhar, A.; Sen, S. Comparison among different dimensions of institutional commitment of secondary school teachers of West Bengal by Mahalanobis distance. Int. Res. J. Mod. Eng. Technol. Sci. 2023, 5, 4088–4093. [Google Scholar]
- Mohanta, R.; Gayen, P.; Pal, I.; Mahato, R.C.; Sen, S. Comparison among different dimensions of organizational climate of secondary school teachers of West Bengal by Mahalanobis distance. EPRA Int. J. Res. Dev. 2023, 8, 129–133. [Google Scholar]
- Sen, S.; Gayen, P.; Pal, I.; Sutradhar, A.; Ansary, K.; Mahato, R.C.; Adhikari, A. Comparison among different leadership styles of head of the institution of West Bengal by Mahalanobis distance. Int. Res. J. Mod. Eng. Technol. Sci. 2023, 5, 5005–5010. [Google Scholar]
- Zhang, M.; Zhang, Y.; Shen, G. PPDDS: A privacy-preserving disease diagnosis scheme based on the secure Mahalanobis distance evaluation model. IEEE Syst. J. 2021, 16, 4552–4562. [Google Scholar] [CrossRef]
- Zhu, D.; Zhu, H.; Wang, X.; Lu, R.; Feng, D. An accurate and privacy-preserving retrieval scheme over outsourced medical images. IEEE Trans. Serv. Comput. 2022, 16, 913–926. [Google Scholar] [CrossRef]
- Lin, Y.; Jiang, Y.; Li, Y.; Zhou, Y. Privacy-preserving batch-based task assignment over spatial crowdsourcing platforms. Comput. Netw. 2024, 241, 110196. [Google Scholar] [CrossRef]
- Zhu, D.; Zhu, H.; Huang, C.; Lu, R.; Feng, D.; Shen, X. Efficient and accurate cloud-assisted medical pre-diagnosis with privacy preservation. IEEE Trans. Dependable Secur. Comput. 2023, 21, 860–875. [Google Scholar] [CrossRef]
- Zhang, Y.M. Research on Privacy-preserving Distance Calculation Protocol and Its Application. Master’s Thesis, Hubei University of Technology, Wuhan, China, 2022. [Google Scholar]
- Jiang, Y.; Pan, S.; Meng, Q. Robust Mahalanobis distance statistic-based multi-sensor integration robust estimation method. Chin. J. Sci. Instrum. 2024, 45, 252–262. [Google Scholar]
- Zhang, J.; Wang, H.; Zhu, X.; Li, J.; Liu, X. Rapid Coal Loading Quality Detection Method Based on Lidar Point Cloud. Coal Sci. Technol. 2024, 52, 199–207. [Google Scholar]
- Guo, G.; Xu, Y.; Shi, L. Photovoltaic Fault Monitoring Based on Singular Value Decomposition and Mahalanobis Distance. Chin. J. Electron Devices 2024, 47, 182–187. [Google Scholar]
- Zhao, H.; Han, J.; Hu, P.; Feng, X. A Digital Twin- Based Method for Equipment State Inference in Active Power Grids. Comput. Simul. 2024, 41, 146–150. [Google Scholar]
- Hoffstein, J.; Pipher, J.; Silverman, J.H. NTRU: A ring-based public key cryptosystem. In Proceedings of the International Algorithmic Number Theory Symposium, Portland, OR, USA, 21 June 1998; pp. 267–288. [Google Scholar]
- Li, Z.; Zhang, J.; Yang, Y.; Zhang, F. A Fully Homomorphic Encryption Scheme based on NTRU. Acta Electron. Sin. 2018, 46, 938–944. [Google Scholar]
- Gentry, C.; Sahai, A.; Waters, B. Homomorphic encryption from learning with errors: Conceptually-simpler, asymptotically-faster, attribute-based. In Proceedings of the Advances in Cryptology–CRYPTO 2013: 33rd Annual Cryptology Conference, Santa Barbara, CA, USA, 18–22 August 2013; pp. 75–92. [Google Scholar]
- Li, S.; Wang, D.; Dai, Y.; Luo, P. Symmetric cryptographic solution Yao’s millionaires’ problem and an evaluation of secure multiparty computations. Inf. Sci. 2008, 178, 244–255. [Google Scholar]
- Li, S.; Wang, W.; Du, R. Protocol for Millionaires’ problem in malicious models. Sci. Sin. Informationis 2021, 51, 75–88. [Google Scholar] [CrossRef]
- Li, S.; Wang, D. Modern Cryptography: Theory, Method and Research Frontiers; Science Press: Beijing, China, 2009; pp. 98–101. [Google Scholar]
| Protocol | Computational Complexity | Communication Complexity |
|---|---|---|
| Algorithm 1 | 4 | |
| Algorithm 2 | 4 | |
| Algorithm 3 | 5 |
| Protocol | Number of Participants | Outsourced | Requires Auxiliary Cloud Server | Security Model | Encryption System | Quantum Attack-Resistant |
|---|---|---|---|---|---|---|
| Algorithm 1 | 2 | No | No | Semi-honest | NTRU | Yes |
| Algorithm 2 | m | No | No | Semi-honest | NTRU | Yes |
| Algorithm 3 | m | No | No | Enhanced semi-honest | NTRU | Yes |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liu, X.; Chen, W.; Guo, X.; Luo, D.; Liang, L.; Zhang, B.; Gu, Y. Secure Computation Schemes for Mahalanobis Distance Between Sample Vectors in Combating Malicious Deception. Symmetry 2025, 17, 1407. https://doi.org/10.3390/sym17091407
Liu X, Chen W, Guo X, Luo D, Liang L, Zhang B, Gu Y. Secure Computation Schemes for Mahalanobis Distance Between Sample Vectors in Combating Malicious Deception. Symmetry. 2025; 17(9):1407. https://doi.org/10.3390/sym17091407
Chicago/Turabian StyleLiu, Xin, Weitong Chen, Xinyuan Guo, Dan Luo, Lanying Liang, Baohua Zhang, and Yu Gu. 2025. "Secure Computation Schemes for Mahalanobis Distance Between Sample Vectors in Combating Malicious Deception" Symmetry 17, no. 9: 1407. https://doi.org/10.3390/sym17091407
APA StyleLiu, X., Chen, W., Guo, X., Luo, D., Liang, L., Zhang, B., & Gu, Y. (2025). Secure Computation Schemes for Mahalanobis Distance Between Sample Vectors in Combating Malicious Deception. Symmetry, 17(9), 1407. https://doi.org/10.3390/sym17091407





