1. Introduction
Graph theory is one of the fundamental branches of mathematics frequently utilized for problem-solving and modeling in fields such as computer science, network analysis, biology, social sciences, and many other fields. It offers a wide range of opportunities for both theoretical exploration and practical applications, making it well-suited for multidisciplinary studies. Graph theory provides a powerful framework for modeling and analyzing relationships and structures, especially in infrastructural networks [
1,
2,
3].
Let be a simple, finite, and undirected graph, where represents the set of vertices (often referred to simply as V), and denotes the set of edges (or E for short). An edge e is written as , where u and v are the vertices it connects. The open neighborhood of a vertex v is defined as :, while its closed neighborhood is given by ∪. The degree of a vertex is the number of neighbors of vertex . A vertex with a degree of zero is called an isolated vertex, as it has no edges incident to it. A vertex with a degree of one is referred to as a pendant vertex (or leaf vertex), as it is connected to exactly one other vertex. A support vertex is a vertex that is adjacent to at least one pendant vertex, providing its sole connection in the graph. Furthermore, a strong support vertex is a vertex that is adjacent to two or more pendant vertices.
When analyzing network structures such as infrastructural networks, these graph-theoretic concepts become essential for understanding connectivity, robustness, and vulnerability. Graph theoretic techniques provide a convenient and effective framework for investigating such networks. It is well-known that an interconnection network can be represented by a graph where vertices correspond to the nodes or sites of the network, and edges represent the communication or connection links between these sites. Consequently, a wide range of network-related problems can be approached and solved using graph theoretical methods. While solving problems in graph theory, the graph is analyzed using certain graph-theoretic parameters and solution techniques by utilizing the relationships between vertices and edges.
One significant area of study in this field is domination parameters, which play a crucial role in understanding the structural and functional properties of graphs. The theory of domination has emerged as a cornerstone of graph vulnerability studies, offering a robust framework for analyzing and optimizing the structure and functionality of complex networks. Its conceptual richness and adaptability have enabled its application across a wide spectrum of disciplines, including computer science, communication and transportation networks, biological and social systems, operations research, chemistry, economics, engineering, and applied mathematics. In recent years, domination-based research has gained increasing prominence within graph theory, driven by the formulation of novel parameters and variants derived from the classical notion of domination. These advancements have not only deepened theoretical understanding but have also opened new avenues for practical implementations in network design and analysis. Domination parameters focus on identifying specific subsets of vertices, such as dominating sets, which ensure that every vertex in the graph is either part of this subset or adjacent to at least one vertex in it. The domination number of a graph is the minimum size of a dominating set and denoted by Domination parameters can vary depending on the problems they address, and there is a wide variety of such parameters in graph theory.
In this paper, we focus on a newly introduced domination parameter, the paired disjunctive domination number, defined by Henning et al. Additionally, Henning and Goddard previously introduced the concept of disjunctive domination in [
4]. In a graph
G, a set
is called a
b-disjunctive dominating set if every vertex not in
S is either adjacent to a vertex in
S or has at least
b vertices at a distance of two from it. Specifically, for
, the set
S is referred to as a disjunctive dominating set (or
-
). Furthermore, the concept of the paired dominating set was introduced by Haynes and Slater [
5], and it refers to a dominating set in which the induced subgraph contains a perfect matching. To gain more detailed information about domination parameters, the reader is referred to the comprehensive works in the literature, such as [
6,
7,
8,
9,
10].
Expanding on these ideas, in a graph
G without isolated vertices, a set
is defined as a paired disjunctive dominating set (
-
) if
S is a disjunctive dominating set and the subgraph induced by
S,
, contains a perfect matching. The minimum size of such a set is known as the paired disjunctive domination number, denoted by
Additionally, we will adapt the bondage number concept, introduced by Fink [
11], to the paired disjunctive parameter. The bondage number of a graph
G, denoted by
, is defined as the minimum cardinality of a subset
such that
. If such a subset cannot be found, the bondage number is represented using the infinity notation,
∞.
The paired disjunctive domination number, recently introduced by Henning et al., offers a novel blend of disjunctive and paired domination concepts in graph theory. Noticing the absence of studies addressing the vulnerability of this new parameter under structural perturbations, we were motivated to explore its stability characteristics. This led us to define the bondage number associated with the paired disjunctive domination parameter, which quantifies the minimum number of edges whose removal increases the parameter. Our motivation stemmed from a desire to understand the structural robustness of this newly defined domination concept and to contribute to the broader study of domination-based resilience measures. Accordingly, we determine the corresponding bondage numbers for several classes of networks. By this motivation, we introduce the paired disjunctive bondage number (PDBN) which is denoted by
and represents the minimum cardinality among all subsets
that satisfy
. For detailed information about the bondage number and its related invariants, the reader is referred to [
12,
13,
14,
15,
16,
17,
18,
19,
20,
21].
We consider PDBN as a metric for network vulnerability. In this model, we find the critical vertices with an important position in the graph. Edges or vertices associated with a low paired disjunctive bondage number are elements that significantly influence the paired disjunctive domination structure of a graph. In particular, if the removal of certain edges or their adjacent vertices results in an increase in the paired disjunctive domination number, these components can be considered critical in terms of network control, monitoring, or security. Therefore, calculating PDBN involves analyzing the structural impact of specific edges and their connected vertices, which in turn provides valuable insight into identifying key or influential nodes in the graph. Although the paired disjunctive bondage parameter does not directly define the notion of a “critical vertex”, it offers an indirect assessment by highlighting edges—and consequently vertices—that substantially affect the paired disjunctive domination properties of the network. Since PDBN is considered to be a reasonable measure for the vulnerability of graphs, it is of particular interest to evaluate PDBN of different classes of graphs. If a complex network can be decomposed into smaller networks, then under certain conditions, the solutions of optimization problems on smaller networks can be combined to solve the corresponding problem on the larger network. Thus, calculation of PDBN for simple graph types is important.
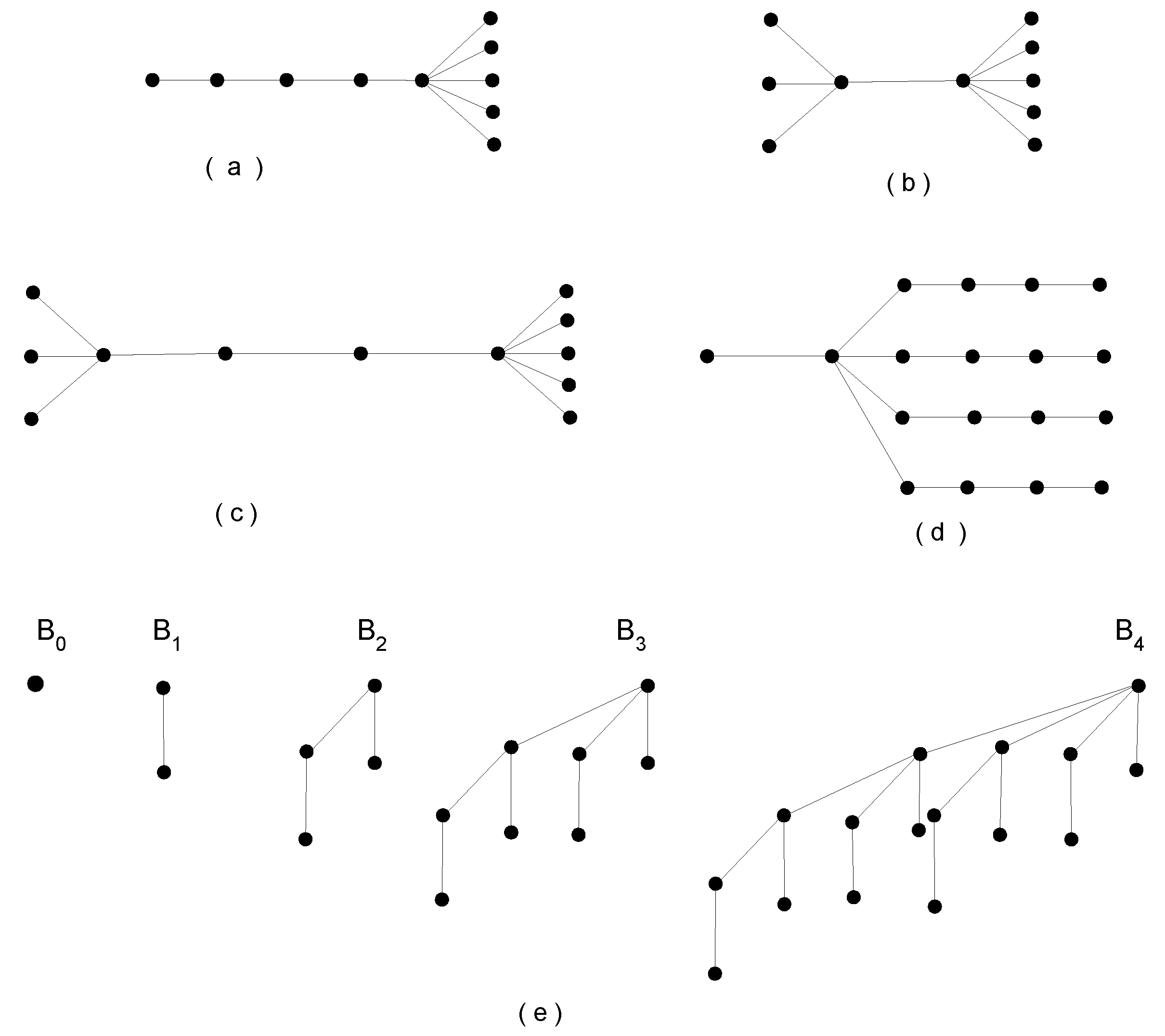
Motivated by this, PDBN has been determined not only for special graph classes but also for certain tree structures, double star, comet, double comet, , and binomial trees, which exhibit hierarchical and partially symmetric configurations. The notion of symmetry in these structural forms provides valuable insight into their vulnerability characteristics. Hence, our analysis contributes to understanding how such structural symmetry impacts vulnerability measures in graph-based models.
A double star,
, is a type of graph that consists of two star graphs with
n and
m pendant vertices joined by an edge between their central vertices. A comet graph,
is a graph consisting of a star graph
(a central vertex connected to
m leaves) and a path graph
where one end vertex of
is connected to the center of the star [
22]. A double comet graph
is formed by a path
on
vertices, where two pendant sets of vertices are attached at the ends of the path: one pendant set consisting of
vertices attached to one end vertex, and another pendant set consisting of
vertices attached to the other end vertex. Here,
and
[
23]. The
tree has
p vertices path graph in
t legs and the graph has
vertices and
edges. A binomial tree
is a recursively defined tree structure used in computer science and graph theory. It has the following properties:
consists of a single vertex and
is formed by linking two
trees, making one the child of the other [
24]. For better clarity, the structures of all the graphs considered in this study are illustrated in the following figures (
Figure 1).
In
Section 2, we reviewed some significant results in the literature related to the paired disjunctive domination number. In
Section 3, we derived paired disjunctive bondage results for certain specific graph structures. In
Section 4, we obtained the paired disjunctive domination and paired disjunctive bondage values for some tree structures.
Section 5 is devoted to an algorithmic analysis of PDBN, including its computational complexity. Finally, in
Section 6, we present a case study focusing on infrastructural networks by examining a specific segment of a metro transportation network. We apply PDBN to this transport network subsection to observe and analyze the behavior of the parameter in a practical, real-world setting.
3. Results About Some Special Networks
In this section, we obtain the paired disjunctive bondage values for special networks. Observing the values of this parameter on fundamental structures is crucial for analyzing graphs in terms of the considered parameter.
Theorem 4. Let be a path graph with . Then,
and where Proof. Let the vertex set of be It is obvious that Therefore, . Let us analyze using two cases.
Case 1: First, let us consider the .
In this case, let , where . From Theorem 1, we have . Thus, . If , then = 6 + . Therefore, . From the lower and upper bounds, we conclude that for .
Case 2: Now, let us analyze the case where
. Let
. In this case,
H contains two sub-path graphs,
and
. Let
. Thus,
from [
25], we have
Therefore, we have
The desired result is proven. □
Theorem 5. Let be a cycle graph with . Then,and provided that Proof. Let be the cycle graph with the vertex set It is easy to check that Therefore, must hold. An analysis will be conducted in three cases.
Case 1: If , then It is known from Theorem 1, This implies that Assume that If two non-adjacent edges are removed from the graph, then provided that In this case . Since the removal of two edges does not cause any change in PDBN, the situation implies that . Assume that three non-adjacent edges are removed from the graph, then we have Hence, we get three structures. Thus, From this, it can be understood that The result is obtained from the lower and upper bounds.
Case
Let
. In this situation, if one edge is removed from the
then
path structure is formed.
for
Case
If
. In this situation, if one edge is removed from the
, then we have
and the path structure is formed. However, it can be calculated using the result of Theorem 1,
for
. Therefore, we have
for
. Let two edges be removed from the
; then it is obtained that
Here,
H,
, and
are divided into two sub-path graphs. Let
. In this case,
, where
.
Hence, for The proof is complete. □
Theorem 6. Let be a wheel graph with . Then, Proof. Let be a vertex set of where c is the center vertex. Assume that one edge, is removed from the as It is obvious that Therefore, this implies that
Now, assume that two edges are removed from the The edges removed from the graph are in the form of , and let where and are the elements of . As a result, is obtained. Thus, holds. From the lower and upper bounds, is yielded. □
Theorem 7. Let be a complete bipartite graph with . Then, Proof. Let us split the vertex set of into two disjoint independent sets and and label the sets as and . Here, each vertex in is adjacent to every vertex in , and there are no edges within each set. It is known from Corollary 1 that and each contains two vertices, one from and the other from .
Without loss of generality, choose and let where If , then it is possible to find a with two vertices. Therefore, PDBN must be . Let the set form with cardinality When we examine , it is obtained that Therefore, it is implied that From lower and upper bounds of we conclude that (same manner is valid for choosing set ). Hence, □
Corollary 2. Let be a star graph. Then, Proof. It is obvious from the structure of the star graph. □
Theorem 8. Let be a complete graph with vertices. Then, Proof. Let be a vertex set of and m be a number of edges. It is known from Corollary 1 that . Assume that all edges incident to and , except the edge connecting to are removed from the graph. Thus, the graph transforms into the structure , and Therefore, it is obtained that .
Assume that Let S be the set of edges that is removed from the graph. To maximally damage a vertex by removing edges, let us remove edges from the graph that are incident to this vertex, leaving it as a pendant vertex. Label this pendant vertex as and its support vertex as . For 2, there must exist a vertex such that . Under this condition, the number of edges between the vertices, except and is at most . Adding the edge to this count, the total number of edges becomes . However, this value is less than , and it is a contradiction. Hence, , which leads . Thus, it follows that . Considering both the lower and upper bounds, it must hold that □
4. Results About Some Trees
In this section, we determined the paired disjunctive domination numbers and the bondage numbers of this parameter for the double star, comet, double comet, , and binomial trees structures, which are commonly used to model hierarchical and infrastructural network structures.
Theorem 9. Let be a double star graph with vertices. Then, the paired disjunctive domination number of is Proof. For ease of expression, let the vertex labeling be represented as
with
n vertices connected to it, and
with
m vertices connected to it, such that the vertex set is denoted as
n,
,
. Let
S be
-
of
Therefore,
is a
-
and
It is also known from [
25] that
Then, we have
□
Theorem 10. Let be a double star graph with vertices. Then, the PDBN of the double star graph is Proof. For ease of expression, let the vertex labeling be represented as with n vertices connected to it, and with m vertices connected to it, such that the vertex set is denoted as n, , . Let be a , where it is known from previous theorem that . Due to the structure of the double graph, leaf edges cannot be removed from the graph. In this case, let , and consider . For this structure, the paired disjunctive domination number satisfies . Thus, □
Theorem 11. Let be a comet graph with and . Then, the paired disjunctive domination number of the comet graph is Proof. Let the vertex labeling of the comet graph be , where for , making these vertices pendants, and and is adjacent to . Thus, the comet graph contains both a path subgraph and a star subgraph. Let S be a - of the graph . To dominate the pendant vertices , ; the strong support vertex must belong to the set S.
Case 1: To ensure the paired property, vertex
can also be added to
S. In this case, all vertices forming the star subgraph of
G are paired disjunctively dominated. Furthermore, since the vertex subset
satisfies
paired disjunctively dominates
, which is a vertex of the path subgraph. Since
,
is partially paired disjunctively dominated, requiring the addition of
to
S to complete its domination. It is known from [
25] that
, and from the proof of
, the support vertex vertex
belongs to the
. For
, only
needs to be added to
S. With the vertex subset
satisfies
; the remaining graph
H is isomorphic to
and
. Therefore, we have
Case 2: To ensure the paired property, a pendant vertex can also be added to Without loss of generality, let the vertex add to Since , the vertex is dominated as paired disjunctively, and the set also contributes to the domination of vertex . As in Case 1, the remaining structure becomes isomorphic to . Therefore, we get When the S values obtained from Case 1 and Case 2 are compared, is obtained. Thus, using Theorem 1, the result is obtained as □
Corollary 3. Let and be comet, star, and path structures, respectively. Then,and the equality holds Theorem 12. Let be a comet graph with vertices. Then, the PDBN comet graph is
Proof. Let the vertex labeling of the comet graph be , where for , making these vertices pendants, and and is adjacent to . According to the form of comet graph, it is known that
Let us assume that by removing the edge
from the graph, the comet graph is split into
and
. From the Corollary 3, when
,
. Therefore,
for
. Now, let us consider the upper bound. Assume that
are the edges removed from the graph
. In this case, the subgraphs
, and
are obtained. Therefore, we have
Thus, we have In consequence, for
When
then it is known from Corollary 3
It follows that
, and the following result holds:
Therefore, for As a result, it is obtained that
This completes the proof. □
Theorem 13. Let be a double comet graph with vertices and . Then, the paired disjunctive domination number of double comet graph is Proof. Let the double comet structure be labeled with the vertex set
Here,
=
, where
,
, and
and
are strong support vertices. Let
S be the
-set of
. To dominate the pendant vertices, it is necessary for the strong support vertices
and their paired vertices to be included in the set
S. To obtain the minimum
-set, the subset
must be part of
S. Considering the remaining structure that is not dominated in a paired disjunctive sense, the following result is obtained for
:
where
□
Corollary 4. Let and be star and comet graphs, respectively, and let be a double comet graph with . Then,the equality holds Theorem 14. Let be a double comet graph with vertices. Then, the PDBN of the double comet graph is Proof. Let the double comet structure be labeled with the vertex set Here, = , where and , and and are strong support vertices. Let , and consider the graph . When is formed, it becomes a graph consisting of a star graph with vertices and a comet graph with vertices. Thus, by Corollary 4, for n . Consequently, for n , holds.
Now, let us consider the upper bound for the PDBN. Assume that the edges in the set
are removed from the graph
. In this case, the graph transforms into a form consisting of the subgraphs
,
, and
. Therefore, we have
Thus, it is obtained that Consequently, and it can be said from upper and lower bounds that = 2 for For , from Corollary 4. If is removed from graph then − for the case n . Hence, is yielded for n □
Theorem 15. Let be a tree containing t times path graphs. Then, the paired disjunctive domination number of graph is Proof. Let us label the graph as follows where , and is the support vertex of . To construct a -set, there are two cases to consider.
Case 1: Let
S be a
-set. In this case,
because it is a support vertex. If we consider one of the
structures, the
structure consisting of the vertices
can be paired disjunctively dominated by number of
vertices. Since
is in
S, it dominates the
vertices in the remaining
legs and is at a distance of two from the
vertices, where
The remaining
vertices in each of the
legs can be disjunctively dominated by
vertices. Therefore, we have
Case 2: In this case, it must also hold that
S. To ensure the paired property of
, let us include
in the set
S. However, this selection creates a disadvantage for dominating the
structures in the
t legs when
. For the case that
, the result
is obtained, which is greater than the result in Case 1. In conclusion,
is obtained. Using Theorem 1 the result follows as
Hence, the desired result is obtained. □
Theorem 16. Let be a tree containing t times path graphs with . Then, the PDBN of is Proof. As in the previous theorem, the vertex set of the graph is Consider the proof in two cases.
Case 1: For
the
-sets
S defined in proof of Theorem 15 provided the same
value. Therefore, if the edge
is removed from the graph for any
then the
value will be increased. In each situation, the vertices
will be added to
Thus, we have
Hence, is yielded.
Case 2: For
as in proof of Theorem 15,
selection will be possible with
In this case, removing the edge
for any
j value does not change the value of
. However, when we remove the edge
,
from the graph, we need to add two vertices to
S according to each choice
j. If the removal edge belongs to the
foot of
graph that includes
, then it is necessary to add vertices
to the set
S. Otherwise, it is necessary to add vertices
. In each situation, we have
Therefore, is obtained. From Case 1 and Case the result for is achieved. □
Lemma 1. Let G be a connected graph and S be a - of G. Suppose v is any support vertex of G, and v has no non-leaf neighbors other than w. In this case, S must include the vertex
Proof. Assume that . Since v has only one non-leaf neighbor, w, there is only a single vertex in G at a distance from the leaf vertices. Hence, if , at least two leaf vertices of v must be added to S to disjunctively dominate the leaf vertices. However, in this case, the paired property cannot be ensured for the vertices in S. If v, as a support vertex, is adjacent to only one leaf, then is not possible. Therefore, . □
Theorem 17. Let be a binomial tree containing vertices, . Then, the paired disjunctive domination number of the graph is Proof. Let
S be a
of
. From Lemma 1, exactly two vertices in the
structure must belong to the set
S. As seen in
Figure 2, label these two vertices as
.
Since
, the paired property does not hold for
. It is obvious that
is the only
for
Then, we have
Due to the recursive structure of the binomial tree graph,
contains
subgraphs that are each isomorphic to
. Thus, the result is obtained as
Theorem 18. Let be a binomial graph containing vertices, Then, the PDBN of the graph is Proof. Let
be a support vertex satisfying Lemma 1, and let
be the non-leaf neighbor of
. For any
, if the edge
is removed from the graph,
is obtained. Thus,
is yielded. □
5. Algorithmic Analysis of PDBN
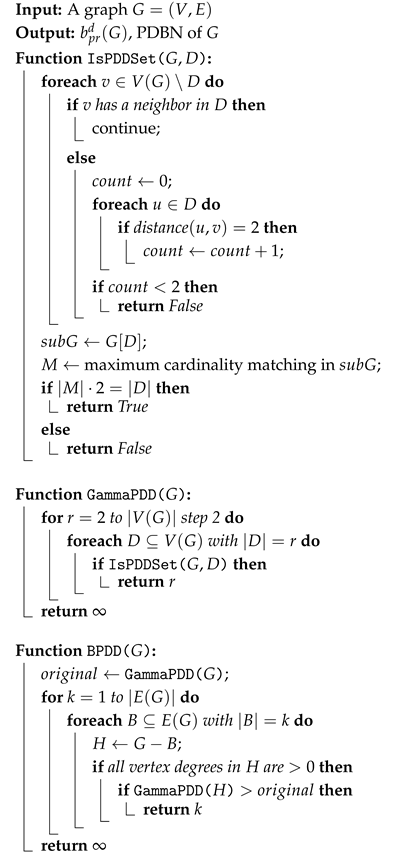
In this section, we transition from the theoretical foundations to a practical perspective by presenting an algorithm for computing the PDBN. We also provide a detailed complexity analysis to assess the computational feasibility and efficiency of the proposed method. The detailed steps of the algorithm are described in Algorithm 1.
| Algorithm 1: Paired Disjunctive Bondage Number (PDBN) of G |
![Symmetry 17 01170 i001 Symmetry 17 01170 i001]() |
The PDBN problem seeks to determine the minimum number of edges whose removal from a graph G increases the size of a minimum paired disjunctive dominating set. In other words, it identifies the minimal set of critical edges that, when deleted, cause the graph to require a larger dominating set that is also paired and disjunctively dominating.
The algorithm operates in two major stages:
First, it computes the parameter , which represents the size of the smallest paired disjunctive dominating (PDD) set in the original graph. This involves checking all even-sized subsets of vertices to find the minimum set satisfying both the disjunctive domination and perfect matching properties.
Second, it exhaustively searches through subsets of edges, starting from size 1 up to , and removes each such subset B to form a new graph . For each , the algorithm checks whether . The smallest such is returned as the PDBN of G.
The computational complexity of the algorithm is driven by two key factors:
- 1.
Computing . For each even-sized vertex subset , the algorithm checks the following:
Whether every vertex not in D is either adjacent to a vertex in D, or has at least two vertices in D at distance two (disjunctive domination check).
Whether contains a perfect matching (using Edmonds’ algorithm in time).
This step has an overall complexity of due to the enumeration of vertex subsets.
- 2.
Computing PDBN. For each to , all subsets of k edges are considered (i.e., possibilities). For each such subset B, the value is recomputed using the above method.
The total time complexity becomes
which is exponential in both the number of vertices
n and edges
m.
The PDBN problem is proven to be NP-hard and even -hard in the parameterized complexity framework. This indicates that it is highly unlikely that an efficient (polynomial-time) or fixed-parameter tractable algorithm exists for general graphs. As a result, exact algorithms are only practical for very small graphs.
Due to its combinatorial explosion in both vertex and edge subsets, the PDBN problem is intractable for large-scale graphs. Therefore, heuristic and approximation algorithms, such as greedy strategies, genetic algorithms, or metaheuristics, are essential for practical applications. The Python 3.11.4 implementation computes the PDBN of a graph G.
7. Discussion
This study introduced and analyzed the concept of the PDBN, a new graph parameter derived from the paired disjunctive domination number, recently proposed by Henning et al. [
25], and further developed through contributions by Tuncel Golpek and Aytac [
26,
27]. While the paired disjunctive domination number encapsulates both structural reachability and pairwise matching conditions in graphs, its bondage variant quantifies the vulnerability of network structures to edge deletions, thereby measuring their structural robustness.
Our findings for various standard graph classes, including path, cycle, complete, and bipartite graphs, confirm that the PDBN behaves consistently with known characteristics of classical bondage numbers. We also observed that complete graphs possess relatively high PDBNs, which indicates their significant resilience to edge deletions.
In the case of tree structures—such as double stars, comets, double comets, , and binomial trees—our results illustrate how hierarchical or recursive structures impact the stability of paired disjunctive domination. The exact values derived for these trees demonstrate that even small structural perturbations (e.g., removal of one or two key edges) can significantly affect the domination properties.
These findings contribute meaningfully to the growing body of knowledge on domination-based resilience in network analysis. The PDBN not only extends classical graph vulnerability measures but also introduces new combinatorial challenges. The alignment of our results with previously established bounds (e.g., for and ) reinforces the mathematical soundness and applicability of this parameter in network vulnerability studies.
Furthermore, some bondage parameters can be compared in terms of their magnitude or relative values for a given graph, which offers insight into their discriminatory power and how restrictive or robust the domination conditions are.
For instance, consider two graphs
and
, each having six vertices and six edges, illustrated in
Figure 4. Their paired bondage and disjunctive bondage numbers are equal, but their PDBNs differ, as shown in
Table 2.
This example highlights that while the classical bondage parameters may coincide for different graphs with the same order and size, the PDBN can distinguish between them, reflecting its greater discriminatory capability. The comparison results are presented in
Table 2. Thus, rather than sensitivity, we emphasize the distinctiveness and comparative scale of these parameters in capturing subtle structural differences.
In conclusion, bondage parameters should be viewed as complementary measures, each offering unique insights into the graph’s domination robustness under different conditions.
Future research could extend this analysis to several types of graph structures and improve our algorithmic approaches for computing efficiently. Furthermore, many problems previously examined in the context of the bondage number and its variants in the literature can be revisited and analyzed through the lens of the paired disjunctive bondage parameter. Moreover, given the computational hardness of the PDBN problem for large-scale graphs, the development of heuristic and approximation algorithms emerges as a significant future research direction. Greedy algorithms, genetic algorithms, and metaheuristic methods such as simulated annealing or tabu search could be explored to obtain near-optimal solutions in reasonable computation time. These approaches may provide practical alternatives for network analysts dealing with real-life large-scale infrastructure networks, where exact computation is infeasible due to exponential complexity.