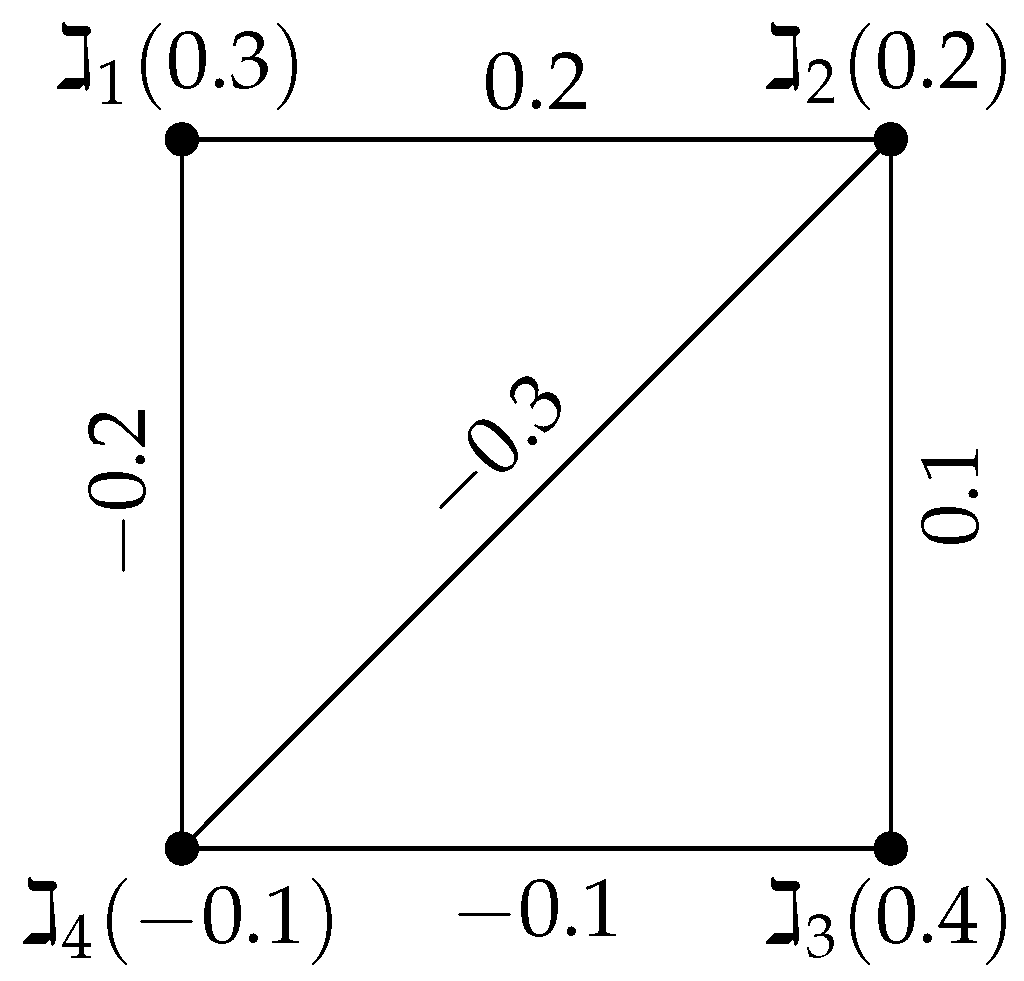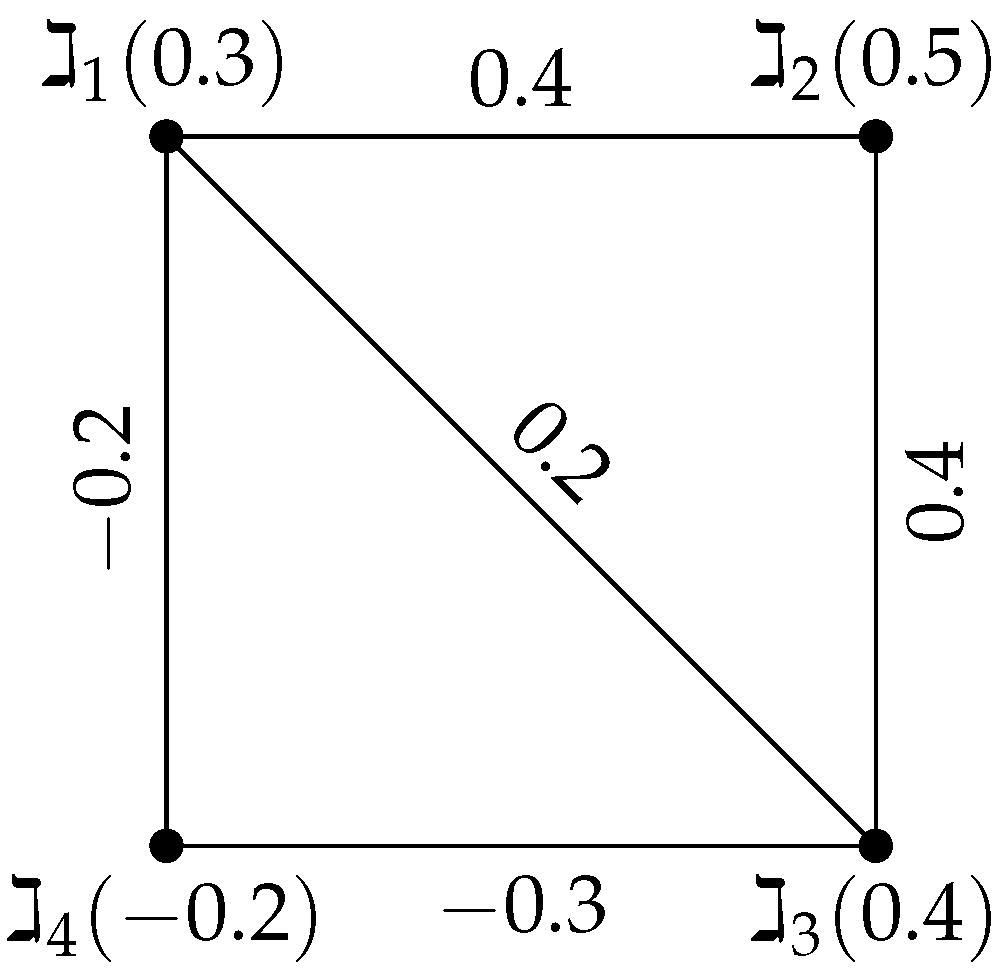1. Introduction
It has long been known that graphs are useful tools for relationship modeling because they provide a simple way to depict connections between items. This framework uses vertices to represent things and edges to represent their relationships. While traditional graph models are valuable in many contexts, they typically rely on binary relationships, where edges either exist or do not. However, real-world scenarios often involve uncertainty or ambiguity in defining objects, their relationships, or both. Examples include the strength of friendships in social networks, the reliability of transportation routes, or the accuracy of sensor data in environmental monitoring, all of which can be variable and unpredictable when modeled using binary edges.
Fuzzy graphs provide a more flexible framework by enabling more precise relationship modeling through the assignment of membership values to vertices and edges. Yet, they lack the ability to represent the binary nature of relationships, which can be either positive (supportive) or negative (antagonistic). This limitation is critical in applications where relationships are not only uncertain but also polarized, such as conflict and cooperation analysis, ecosystems, or wireless sensor networks. For example, communication networks may entail trust and interference, ecosystems may involve symbiosis and predation, and social or political connections may involve cooperation and rivalry.
Fuzzy graphs are expanded upon by signed-FGs, which add polarity to their edges. Each edge in a signed-FG is identified by a sign that indicates whether the relationship is positive or negative, as well as a relationship value that indicates the strength of the link. In systems where both uncertainty and the type of interaction are important, signed-FGs can capture small fluctuations thanks to this dual representation. The addition of polarity to interactions in signed-FGs provides a thorough framework for investigation. Moreover, the concept of symmetry plays a critical role in signed-FGs, where symmetrical structures are often associated with more stable and resilient networks, leading to enhanced domination integrity and balanced interaction dynamics. These models operate together to offer a cohesive and reliable method for researching intricate communication systems in a variety of fields, such as wireless communication, social networks, and environmental monitoring.
A graph [
1] on a nonempty set
ℑ can be regarded as a binary relation. The foundation of fuzzy graphs is the notion of fuzzy relations and fuzzy sets, which Zadeh initially introduced in 1965 [
2]. Rosenfeld extended this concept in 1975 [
3], establishing the connection between fuzzy sets and graph theory, enabling research on fuzzy trees, blocks, bridges, and cut nodes. In his seminal paper [
3], Rosenfeld explored the ideas of blocks, cut nodes, fuzzy trees, and bridges in FGs. Yeh [
4] introduced several connection notions in FGs at the same period. Fuzzy analogues of classic graph theory notions, such as automorphisms of FGs [
5], cycles and cocycles in FGs [
6], fuzzy interval graphs [
7,
8], fuzzy trees [
4,
9], and fuzzy line graphs [
10], have been developed by several scholars since these fundamental works.
In [
4], Yeh defined fuzzy trees compatible with cut-level representations and developed concepts like connectedness and acyclicity degrees for fuzzy trees. By defining boundaries, computing domination numbers for different fuzzy graph sets, and extending the concepts of dominance and absolute domination in fuzzy graphs, Somasundaram [
11,
12] advanced the topic even further. Furthermore, Somasundaram [
13] identified the prevailing parameters of operations on fuzzy graphs, such as union, join, composition, and Cartesian products. Moderson [
9] made a contribution by researching FGs with different levels of connectedness.
It has been demonstrated that operational research problems can be successfully addressed by the structural properties of finite fuzzy graphs. The characteristics of cut nodes, bridges, trees, and fuzzy cycles in fuzzy graphs have all been studied. To show how fuzzy graphs are interconnected, Nagoor Gani [
14] examined the connections between degree, order, and size. Fuzzy end nodes were first proposed by Bhutani [
15], who demonstrated that no node could be both a cut node and a fuzzy end node at the same time. Bhutani also described fuzzy cycles without fuzzy end nodes or cut nodes and investigated the characteristics of fuzzy end nodes in fuzzy trees.
In [
16], the notions of strong arcs and strong paths in fuzzy graphs were initially presented. According to the study, a fuzzy bridge is always strong, while a powerful arc is not always a fuzzy bridge. The authors also defined fuzzy trees using strong paths and explained the use of strong arcs in fuzzy trees. Applications of fuzzy optimal cut edges and vertices are discussed in [
17]. Matroid perspectives were used to expand the fuzzy graph to Plithogenic fuzzy sets in TOPSIS applications [
18] and to analyze single-valued neutrosophic fuzzy graphs in [
19].
External stability, external dominance, and their combinations into FGs were among the ideas that Assia Alaoui [
20] added to the theory. Likewise, Sameena and Sunitha investigated strong arcs in maximum spanning trees [
21] and their use in neural networks [
22,
23]. Database theory, group structure analysis, and chemical systems and applications are just a few of the many domains where fuzzy graphs have been proven useful [
24,
25,
26].
Saravanan [
27] identified vulnerabilities in a 2015 study that concentrated on the integrity features of edges and vertices in fuzzy graphs. Vertex and edge integrity in fuzzy graphs were extensively studied in [
28], with examples and mathematical theorems illustrating their importance in assessing network vulnerability and connectedness. A significant advancement in the field was made in [
29] by studying dominance integrity in graphs with the goal of placing Phasor Measurement Units in electric power networks as optimally as possible to guarantee system stability and observability. Furthermore, the concept of integrity in fuzzy graphs was clarified and examined in more detail, as well as its mathematical properties and consequences for network vulnerability and stability. The notion of domination integrity in fuzzy graphs was presented in [
30,
31,
32], along with its definitions, features, and real-world applications, in order to evaluate the efficacy and stability of network topologies. The span integrity of fuzzy graphs has been used in brain network investigations in [
33], and it has shown potential for improving neural network communication and identifying functional issues. Concepts of signed-FG [
34], mathematical modeling are pertinent to the analysis of vulnerability parameters in these graphs and integrity in vertex connectivity within supply chain networks. According to [
35], edge integrity, applications in agriculture supply chains, and how they handle decision-making issues are facilitated by incorporating membership values and signs to reflect positive and negative consequences.
1.1. Preliminary Concepts
A simple graph consists of a nonempty set of nodes ℑ and edges . This basic terminology was extended to fuzzy graphs by Rosenfield. A fuzzy graph is defined as a pair of functions, where and . For all , . A subgraph of is a fuzzy graph if and for all , and ∑ has a spanning subgraph if both fuzzy graphs have the same nodes. A sequence of distinct nodes such that for all i constitutes a path in ∑ of length n. The minimum membership value of the edges in a path determines its strength. is a connected fuzzy graph if there exists at least one path between every two vertices of the fuzzy graph. The maximum strengths of all paths define the connectedness of the two nodes and , indicated by . In a fuzzy graph, if for all , then it is a strong fuzzy graph. In a complete fuzzy graph, , . The order and size of a fuzzy graph are and , respectively. The complement of a fuzzy graph is , where and for all .
Definition 1 ([
34]).
The definition of vertex integrity in signed-FG is , where and the largest component’s order is . Definition 2 ([
34]).
The definition of edge integrity in signed-FG is , where and the largest component’s order is . A fuzzy graph whose vertex and edge minimum values include either a positive or negative sign is referred to as a signed-FG (signed-FG). It is formally defined as follows: the signed-FG is a pair of functions defined such that and , where for all .
Definition 3. In a signed-FG , if for , this means it is an effective arc.
Definition 4. In a signed-FG , if all arcs are effective, then it is a complete signed-FG.
Definition 5. An edge in a signed-FG is
α-strong if .
β-strong if .
δ-arc if .
1.2. Motivation
Domination in signed-FGs is being investigated to express complex, dynamic, and uncertain real-world interactions. A more flexible approach is required because traditional graph models frequently fall short in capturing the nuances of relationships, such as cooperation and rivalry. By combining both positive and negative associations, signed-FGs fill this gap and allow for a more thorough examination of the connectivity and strength of interactions between vertices. This approach is especially useful in fields like healthcare, because knowing connection integrity can help improve patient care in emergency situations. Furthermore, a key indicator for assessing network resilience is domination integrity (DI). This study provides useful tools to assist practitioners in overcoming operational issues by expanding upon theoretical underpinnings.
1.3. Organization of the Paper
An introduction and a review of the literature are given in
Section 1. In
Section 2, “Domination in signed-FGs”, the fundamental ideas of domination in signed-FGs are examined, with an emphasis on how they might be used to evaluate the resilience and capacity of networks. The novel concept of domination integrity (DI), which examines the connection and stability of hierarchical organizations, particularly in healthcare systems, is introduced. Effective arcs, definitions, and findings pertaining to standard signed-FGs are covered in
Section 3. The relationships between the several nodes that represent healthcare facilities and how they affect the overall connectivity of the network are highlighted in
Section 4. Domination integrity’s practical applications are explored in
Section 5, with a focus on how they contribute to efficient resource management and team-based response tactics in actual circumstances like emergencies or public health crises. Finally, important new information about the dynamics of signed-FGs and their consequences for network stability and management is presented.
2. Algorithm for Classifying Strong Arcs in Signed Fuzzy Graphs and Identifying Signed Fuzzy Trees
Analyzing the structural characteristics of signed-FGs, especially in identifying strong edges and tree topologies, depends heavily on graph connectivity. In this work, we provide basic matrix representations for signed-FGs, including the adjacency matrix, the upper triangular adjacency matrix, and the strength of connectivity matrix. These matrices offer a systematic approach to categorizing strong arcs, measuring connectivity between vertices, and identifying signed fuzzy trees in a signed-FG.
By encoding connection values between vertex pairs, the adjacency matrix, an upper triangular representation, efficiently eliminates redundancy in edge representation. By keeping only important connectivity values that match actual edges in the graph, we are able to refine the adjacency matrix using the connectedness adjacency matrix. The process of classifying strong edges involves determining the highest connectivity values in the connectedness adjacency matrix.
Definition 6. The adjacency matrix of a signed-FG is an matrix that represents the membership values of edges connecting the vertices. The adjacency matrix is defined as follows: Definition 7. The upper triangular adjacency matrix retains only the upper triangular part of the adjacency matrix to avoid redundancy in an undirected signed-FG. Definition 8. The strength of connectedness between two vertices is defined as the strongest weakest link in any path between them as follows:where ℘ represents the set of all paths between and . 2.1. Pseudocode for the Classification of Arcs
Input: Simple signed-FG.
Output: Classification of arcs.
Step 1: The adjacency matrix of the given simple graph.
Step 2: The upper triangular adjacency matrix.
Step 3: The strength of connectedness between two vertices is defined as the strongest weakest link in any path between the vertices.
Step 4: Compare the upper triangular adjacency matrix with the strength of connectedness upper triangular adjacency matrix . If , retain the value. Otherwise, mark the entry as ‘-’.
Classify Strong Arcs as α-Strong or β-Strong:
An arc in the strong upper triangular adjacency matrix is classified as follows:
2.2. Time Complexity
The time complexity of the pseudocode is . Step 1, reading the adjacency matrix, and Step 2, extracting the upper triangular matrix, each take . Step 3, computing the strength of connectedness, and Step 4, classifying strong arcs, dominate with , as they involve graph traversal and checking each element for connectivity or maximum values. Thus, the overall complexity is .
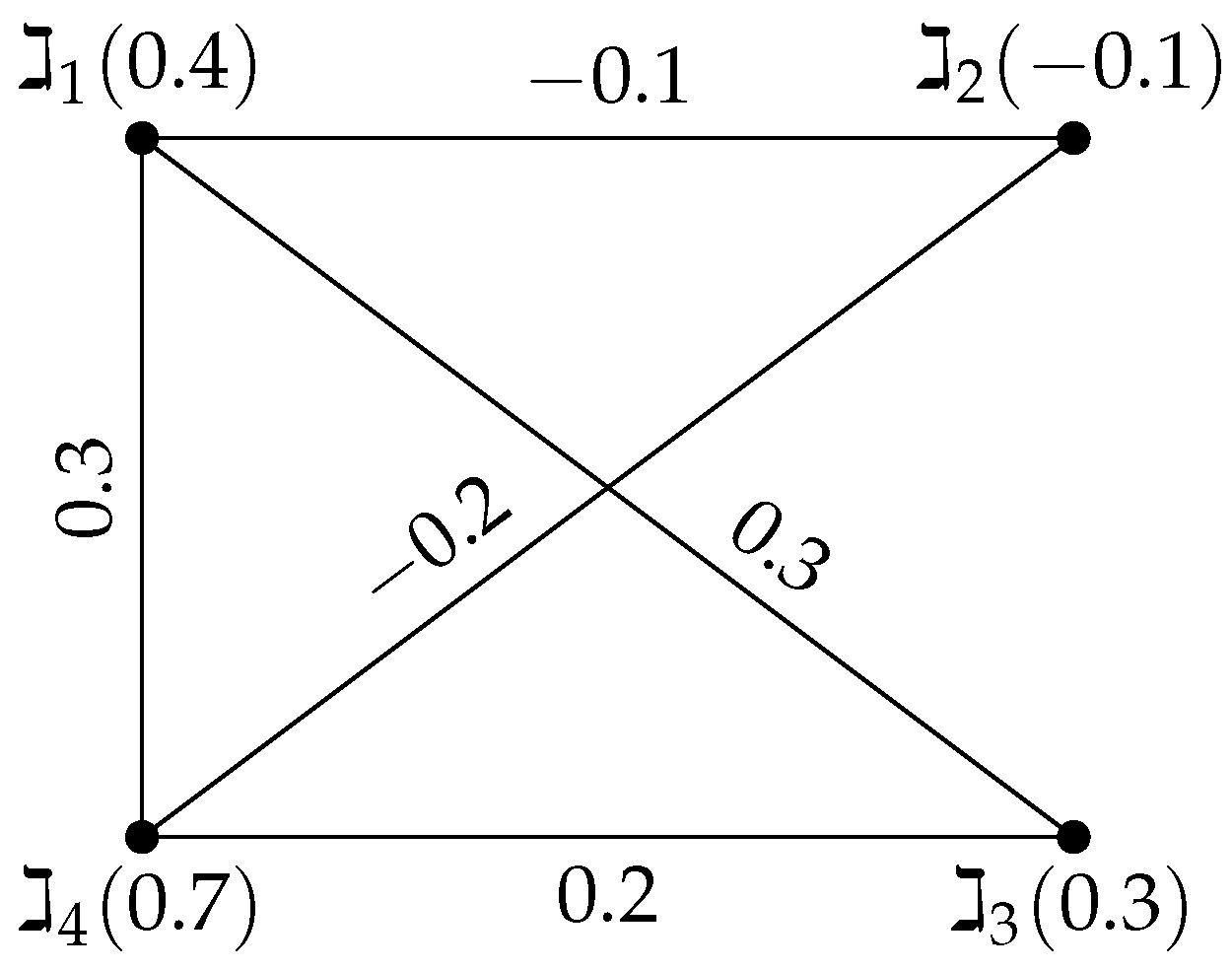
Example 1. Consider a signed-FG with the vertex set , , and edge set with the vertex values listed below , and . According to Figure 1, the edge values are , and . Using Algorithm 1, we now discuss this example. Step 1: The adjacency matrix is expressed as follows:
Step 2: The upper triangular adjacency matrix
Step 3: The strength of connectedness between two vertices is defined as the strongest weakest link in any path between them as follows:
Step 4: Compare the upper triangular adjacency matrix
and the strength of the connectedness of the upper triangular adjacency matrix
. If
; retain the value. Otherwise, mark the entry as ‘-’.
Classify strong arcs as -strong or -strong
An arc in the strong upper triangular adjacency matrix is classified as follows: -strong if its membership value is the maximum in its row or column in and -strong otherwise.
For matrix , the following hold:
is -strong (unique maximum in row/column).
is -strong (unique maximum in row/column).
is -strong.
is -strong.
is -strong (unique maximum in row/column).
Final Summary
Construct the adjacency matrix for a signed-FG.
Convert it into the upper triangular adjacency matrix.
Compute the strength of connectedness upper triangular matrix.
Compare matrices and construct the strong upper triangular adjacency matrix.
Classify strong arcs as -strong or -strong.
This process helps analyze connectivity strength and classification of strong arcs in signed-FG-based applications.
| Algorithm 1 Classification of arcs. |
- 1:
Input: Adjacency matrix of a signed-FG - 2:
Output: Strong upper triangular adjacency matrix and classification of strong arcs - 3:
Step 1: Construct the Upper Triangular Adjacency Matrix - 4:
for to n do - 5:
for to n do - 6:
- 7:
end for - 8:
end for - 9:
Step 2: Compute the Strength of Connectedness Matrix - 10:
for each pair of vertices do - 11:
if is directly connected then - 12:
- 13:
else - 14:
Find all paths from i to j - 15:
Determine max(min(edge weights along paths from i to j)) - 16:
computed value - 17:
end if - 18:
end for - 19:
Step 3: Construct Strong Upper Triangular Matrix - 20:
for to n do - 21:
for to n do - 22:
if then - 23:
- 24:
else - 25:
- 26:
end if - 27:
end for - 28:
end for - 29:
Step 4: Classify Strong Arcs as α-Strong or β-Strong - 30:
for each nonzero element in do - 31:
Find unique maximum in row and column of - 32:
if is unique maximum in its row or column then - 33:
Mark as -strong arc - 34:
else - 35:
Mark as -strong arc - 36:
end if - 37:
end for
|
Definition 9. A connected signed-FG has a signed fuzzy spanning subgraph such that for all arcs not in . Then, is a signed fuzzy tree.
Thus, can be classified as a signed fuzzy tree if all edges not in have lower fuzzy membership values than the connectivity function, ensuring that alone sufficiently represents the strongest connected structure of .
2.3. Pseudocode for Checking Whether a Signed-FG Is a Signed Fuzzy Tree or Not
Input: Simple signed-FG.
Output: Whether it is a signed fuzzy tree or not.
2.4. Time Complexity
The time complexity for checking whether a signed-FG is a signed fuzzy tree is , where n is the number of vertices in the graph. Constructing the upper triangular adjacency matrix requires comparing each pair of vertices, resulting in a time complexity of . After constructing the matrix, checking for the unique maximum value in each row and column also takes time, as each row and column must be scanned individually. Since both steps individually require operations, the overall time complexity of the pseudocode remains .
Example 2. Consider a signed-FG with the vertex set , and and edge set with the vertex values listed below , and . According to Figure 2, the edge values are and . Using Algorithm 2, we now discuss this example. Step 1: The upper triangular adjacency matrix
Step 2: Checking the unique maximum values in each row and column as follows:
Row 1: Max = (Unique).
Row 2: Max = (Unique).
Row 3: Max = (Unique).
Row 4: Max = (Unique).
Column 2: Max = (Unique).
Column 3: Max = (Unique).
Column 4: Max = (Unique).
Column 5: Max = (Unique).
Since each row and each column has a unique maximum, the signed-FG is a signed fuzzy tree.
Example 3. Consider a signed-FG with the vertex set , , and edge set , with the vertex values listed below—, and . According to Figure 3, the edge values are , and . | Algorithm 2 Check if a signed-FG is a signed fuzzy tree. |
-
Input: Adjacency matrix of a signed-FG with n vertices - 2:
Output: “Signed Fuzzy Tree” if valid, otherwise “Not a Signed Fuzzy Tree” Step 1: Construct the Upper Triangular Adjacency Matrix - 4:
for to n do for to n do - 6:
end for - 8:
end for Step 2: Check Row Maximum and Row Minimum - 10:
for each row i in do Extract all nonzero values in row i - 12:
if row has at least one nonzero value then max_value - 14:
min_value if max_value or min_value does not exist then - 16:
return “Not a Signed Fuzzy Tree” end if - 18:
end if end for - 20:
Step 3: If all valid rows have both max and min values return “Signed Fuzzy Tree”
|
Step 1: The upper triangular adjacency matrix
Step 2: Checking the unique maximum values in each row and column as follows:
Column 2: Max = (Unique).
Column 3: Max = (Unique).
Column 4: Max = (Unique).
Since the first row does not have a unique maximum, the signed-FG is not a signed fuzzy tree.
3. The Concept of Domination Integrity in Signed-FGs
In this section, domination in signed-FGs and domination integrity are presented with examples. Two distinct parameters, domination and integrity, describe a graph’s stability under various conditions. A new parameter, domination integrity, is developed, and its upper and lower bounds are established using the strong arc concept. The domination integrity of standard signed-FGs, including paths, cycles, and complete signed-FGs, is investigated in this section.
Definition 10. Let and be members of ℑ, and let be a signed-FG. If is a strong arc, then dominates in . A subset of ℑ is referred to as a domination set of if, for each , there is a that dominates .
Definition 11. A domination set is referred to as a minimum domination set if none of its smaller subsets are also a domination set, and is a signed-FG. The domination number, represented by , is the minimum size of any domination set in a graph . A domination set in a signed-FG has a size of . One term for a minimum domination set is .
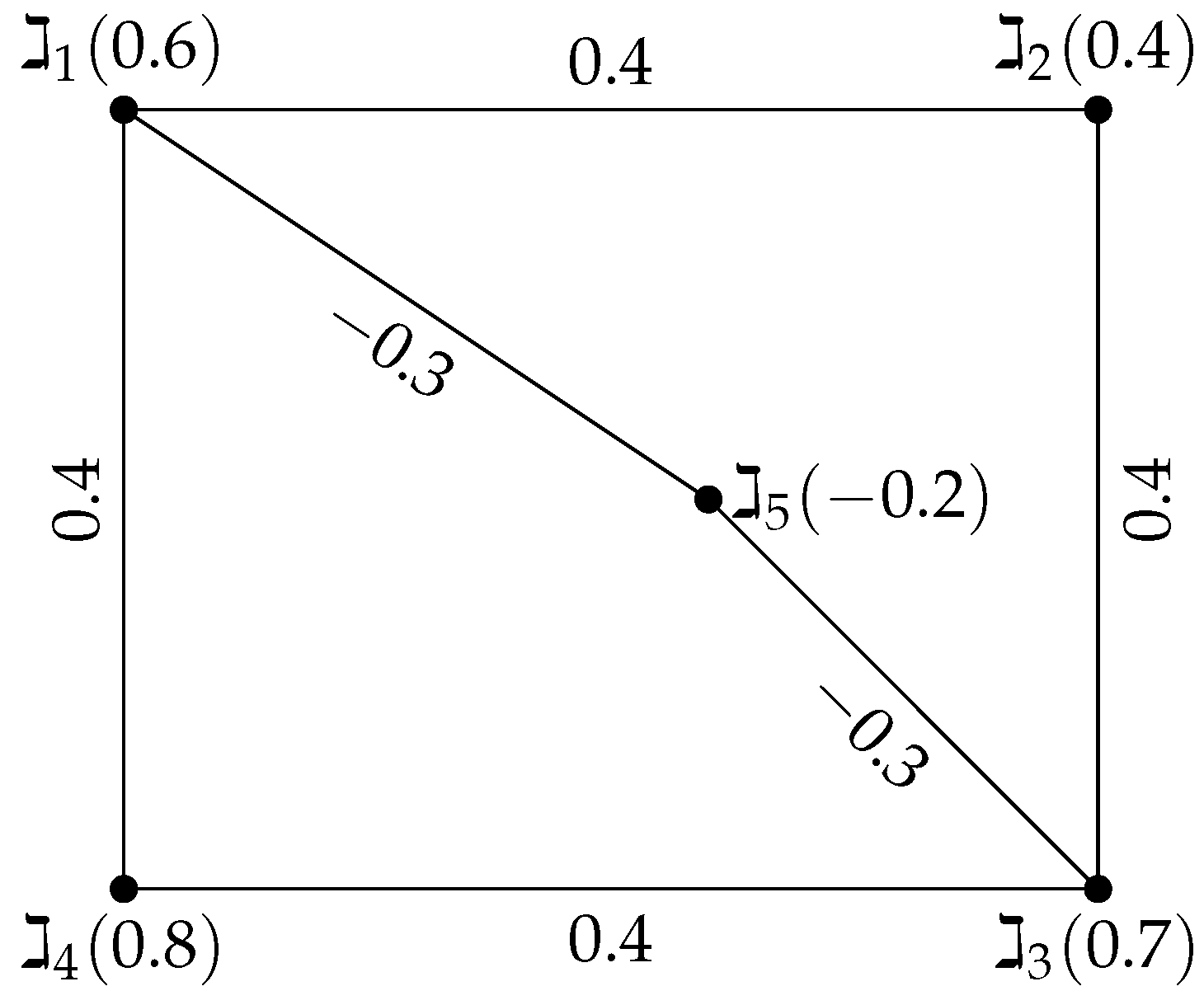
Example 4. Consider a signed-FG with the vertex set , , and edge set , with the vertex values listed below, , and . According to Figure 4, the edge values are , and . , and are the strong arcs. The sets that could be dominating are , , , and . The dominating number of is the minimal cardinality, taken across all domination sets. The minimum domination set is , and the domination number is . Definition 12. Let be a signed-FG. is the definition of the domination integrity of a signed-FG, where denotes the vertex cardinality of S and is the maximum order of . For a signed-FG, is the minimal domination integrity set.
Example 5. Let be a signed-FG, where the vertex set is and edge set have the following vertex values , and . The edge values are , and . As shown in Figure 5, the strong arcs are , and . The domination sets are , and . The domination integrity is calculated in Table 1 and is given by: . Theorem 1. For any signed-FG , .
Proof. The domination number of a signed-FG is determined by the cardinality of the dominating set. The dominating integrity number is determined by the greatest order of the component of that belongs to the dominating set S, implying that . Equality holds if the vertices in the signed-FG are isolated. Since the full set of vertices is the only dominating set in a signed-FG with isolated vertices and , it follows that . Thus, we have . □
Corollary 1. If is a trivial signed-FG, then .
Proof. A trivial signed-FG is a signed-FG that consists of a single vertex and no edges or multiple vertices, with all edge membership values equal to zero.
Case 1. Trivial signed-FG with one vertex
If the signed-FG has only one vertex, say , then the domination number will be k. Similarly, the domination integrity is also k because the integrity set consists of only itself. Since there are no other vertices, the domination integrity is k. Hence, .
Case 2. Trivial signed-FG with Multiple Isolated Vertices
If has multiple vertices but no edges , then the following holds:
Each vertex is an isolated vertex, meaning each vertex must be chosen individually to dominate itself. The domination number is the total number of vertices, since no vertex can dominate another. The is also the total number of vertices, as all vertices are independent (no two are adjacent). Hence, .
Therefore, it can be concluded from both scenarios that is a trivial signed-FG. □
Theorem 2. In a signed-FG , the domination integrity parameter increases monotonically.
Proof. Let be a signed-FG and let be a subgraph of . We aim to show that
By the Definition 12, for any signed-FG, depends on the following two aspects: the size of a minimum dominating set and the structure of the components formed when this set is removed.
Since is a subgraph of , the vertex set and the strong arc set of are subsets of those of . Therefore, any dominating set in will dominate at least as many vertices and arcs as in .
Now, we apply induction on the number of vertices. For graphs with one or two vertices, the domination integrity is trivially satisfied since the subgraph would either be identical or a smaller version, and thus, . WE assume that for all signed-FGs with n vertices, the inequality holds. We consider a signed-FG with vertices, and a subgraph obtained by removing one or more vertices and the associated arcs. Since removing vertices cannot increase the number of connections, and dominating sets must cover fewer vertices or require fewer strong arcs to dominate, it follows that the domination integrity of is less than or equal to that of .
Case 1. The equality holds if and only if the subgraph has the same vertex set and strong arc set as , meaning no actual reduction has occurred.
Case 2. In all other cases, when either vertices or arcs are removed, will be strictly less than .
Hence, by the principle of induction, the domination integrity parameter increases monotonically with respect to subgraphs in signed fuzzy graphs. □
Theorem 3. A complete signed-FG or the complement of a complete signed-FG is . Then, order of signed-FG.
Proof. Assume that is a complete signed-FG. Subsets of ℑ are then all sets that dominate . The graph is reduced to a single component, consisting of all remaining vertices, when any subset of ℑ is eliminated. Therefore, the order of equals the dominating integrity of . Assume that is the signed-FG complement . Then, the vertices of are isolated. For all ℷ in , . The complete vertex set is the only dominating set in . Because S is the dominating set, is zero. Consequently, order is the dominating integrity of . As a result, ℑ is the only dominating set. The order of is thus .
Conversely, suppose that the dominating integrity number equals the order of . Suppose that the dominating set in is S. If contains more than one component, the sum of the cardinality of S and must be less than the order of . must therefore be a single connected component. This is true for all dominating sets, but is particularly true for sets that contain a singleton vertex. Consequently, this singleton vertex set is inferior to all other vertices in . This implies that is a signed-FG that is complete. □
Theorem 4. Let the complete bipartite signed-FG . , if .
Proof. Let the complete bipartite signed-FG be , whose bipartitions are and . One vertex from and another from , or one vertex from and another from , constitute the dominating set S of . is a single linked component if S is one node from and another from , or one node from and another from . if S is . if S is . Hence, . □
Theorem 5. Let be a signed-FG, and assume that the underlying crisp path graph is , where every edge functions as an effective edge. There is then at least one independent dominant set with vertices.
Proof. Let be a signed-FG. whose underlying network is m vertices and a path . The edges in are all effective edges. In order to dominate , we want at least edges. The following represents a way to construct the independent dominant set: When , the vetex set forms the independent dominant set. When , the vetex set forms the independent dominant set. When , the vetex set forms the independent dominant set. The nodes of are not next to each other. Clearly, they are not related to one other. Consequently, a dominating set with nodes is independent. □
Theorem 6. Let a signed-FG be , and let be the crisp cycle graph underneath, with all arcs functioning as effective arcs. There is then at least one independent dominant set with vertices.
Proof. Suppose that
is a signed-FG. We use an underlying network
and
n vertices. Every edge in
is an effective edge. At least
edges are required in order to dominate
. Vertex
is isolated by definition [
24] if
. For any
, a set is said to be independent
. A set is considered independent if there are no adjacencies between any of its vertices.
should be the vertices of
. The independent dominant set can be constructed as follows: If
, then the vetex set
forms the independent dominant set. If
, then the vetex set
forms the independent dominant set. If
, then the vetex set
forms the independent dominant set. A dominant set with
vertices is independent as all of the arcs in
are effective arcs. □
Theorem 7. Assume that is a connected signed-FG. A distinct strong path between any two nodes in is necessary for to be classified as a signed fuzzy tree. A path that has the greatest strength between two points, and , for any , is also considered strong.
Theorem 8. Let the connected signed-FG be . It is a signed fuzzy tree if and only if has a distinct maximum spanning tree.
Theorem 9. If is the maximum spanning tree and is a signed fuzzy tree, then .
Proof. Let be a maximum spanning tree and be a signed fuzzy tree. Theorem 7 states that every arc in is strong. is unique according to the Theorem 8. Consequently, the strong edge set and vertex set are the same as ’s edge set and vertex set. follows as a result. □
4. Efficient Signed-FGs
Each crisp graph clearly belongs to a distinct class of signed-FGs. If the values of and for every node and arcs are equal to 1, the signed-FG is considered crisp. Interestingly, the signed-FG may not match the dominant sets of the underlying crisp graph. Consequently, we develop a new type of signed-FG, the efficient signed-FG.
Definition 13. Any signed-FG, where has the same domination set as its crisp graph, except for ℑ, is regarded as an efficient signed-FG.
Example 6. Let be a signed-FG, where the vertex set and edge set have the following vertex values and . The edge values are , and , as shown in Figure 6. The strong arcs are , and . The domination sets are , and Example 7. Let be a signed-FG, where the vertex set and edge set have the following vertex values and . The edge values are , and , as shown in Figure 7. The strong arcs are , and . The domination sets for crisp graph and are identical. As a result, the signed-FG is efficient. Theorem 10. Let represent a signed-FG and the underlying crisp graph be path . Then, is an efficient signed-FG.
Proof. Let be a signed-FG and assume that represents a path. The vertex and edge sets of and its underlying crisp graph are identical if every arc is effective. Consequently, they share the same dominating set, making a productive signed-FG. Now, suppose that every arc is inefficient. It must be shown that each inefficient arc is also a strong arc. Since there is exactly one path in connecting any two vertices, removing an edge disconnects the graph, thereby reducing the connectivity between neighboring vertices. Hence, such an edge must be a strong edge. Therefore, in , all inefficient edges are strong edges. As a result, is an efficient signed-FG. □
Theorem 11. A signed-FG is considered efficient if it is complete.
Proof. Each set of vertices in a complete signed-FG is a dominant set of . Since the supplied signed-FG is a complete signed-FG, each edge is a strong arc. Thus, and have the same vertex set and edge. As a consequence, they have the same dominating set. Thus, any complete signed-FG is likewise an efficient signed-FG. □
Theorem 12. An efficient signed-FG is any signed-FG that has a constant value.
Proof. When all of the arc values are equal, the arc is said to be strong. The arcs are regarded as -strong arcs in this instance. Each arc has become stronger as a result. As a result, each vertex in the fuzzy and crisp graphs has the same closed neighborhood set. As a result, is an effective signed-FG since it has the same dominating set as . □
Theorem 13. All efficient signed-FG is a strong signed-FG.
Proof. In a strong signed-FG, every arc is an effective edge. Any effective edge is a strong edge. But not every powerful arc qualifies as an effective one. In this case, every edge is an effective edge. Every edge is therefore a powerful edge. This implies that the dominating sets of the signed-FG and its underlying fuzzy graph are the same since the neighborhood set of each vertex is the same for both. Consequently, every strong signed-FG is likewise an efficient signed-FG. □
5. Applications of Integrity in Domination for Signed-FGs
In healthcare systems, hospitals, clinics, and medical personnel are considered nodes, while patient referrals, medical supply chains, and information flows are treated as edges. In real-world healthcare networks, the dependability of these connections can vary depending on whether the interactions are competitive (negative) or cooperative (positive).
During a pandemic like COVID-19, when major hospitals and other critical nodes become overwhelmed, dominance integrity can be used to quantitatively evaluate the resilience of a healthcare network. It measures how well the network can adapt by shifting patients to secondary hospitals, reallocating resources, or strengthening alternative care pathways.
Its application is illustrated through the following real-world examples:
In a mass casualty event, dominance integrity can determine whether the healthcare system maintains patient care by dynamically adjusting patient referrals and resource sharing across institutions.
If major referral hospitals are compromised, the model assesses whether other healthcare centers can sustain the flow and quality of care.
When supply chains fail (e.g., ventilator shortages), the integrity score reflects how effectively alternative sourcing and distribution routes compensate for disruptions.
Thus, dominance integrity serves as a resilience metric, helping administrators design healthcare systems that can withstand shocks, reallocate resources efficiently, and maintain operational effectiveness under pressure. In this context, symmetry within healthcare network structures emerges as a crucial factor, as more symmetrical networks tend to exhibit higher domination integrity, thereby enhancing the system’s robustness and adaptability during crises.
Although this study primarily establishes the theoretical foundation, future work is planned to validate these concepts using real-world healthcare network data, particularly from pandemic response efforts and crisis management scenarios.
Graph Representation for Domination Integrity in Signed-FGs
A signed-FG’s nodes and edges can be used to depict the relationships and interactions among healthcare organizations in a network, . Domination integrity measures the resilience of the network in the event that important components (nodes) are lost or corrupted. The integrity of dominion is provided by the following: At , the minimum of is the minimum and is the maximum order of the components of . The nodes that dominate the network are represented by , which is a subset of all nodes.The total of the set’s membership values is . When is subtracted from , the remaining network is .
Nodes represent various healthcare facilities such as clinics, hospitals, pharmacies, and emergency rooms. Each node is assigned attributes, including a signed fuzzy membership value ranging from to 1. This value reflects the facility’s capacity, reliability, and relevance within the network. For instance, a large hospital with a membership value close to 1 indicates high importance, whereas a small community clinic may have a lower membership value, signifying a more limited role in the network.
Margin represents the relationships or interactions between hospitals. Among these could be patient referrals, which allow one hospital to send patients to another. In order to offer medical staff or equipment between hospitals, shared services collaborate. Planning for emergency response or medical aid is facilitated by communication. Positive dynamics include encounters that are constructive, including successful patient transitions or successful corporate outcomes. Negativity is a symbol for negative interactions, such as site competitiveness or communication breakdowns. The degree or level of confidence in these relationships can be indicated by the signed fuzzy membership.
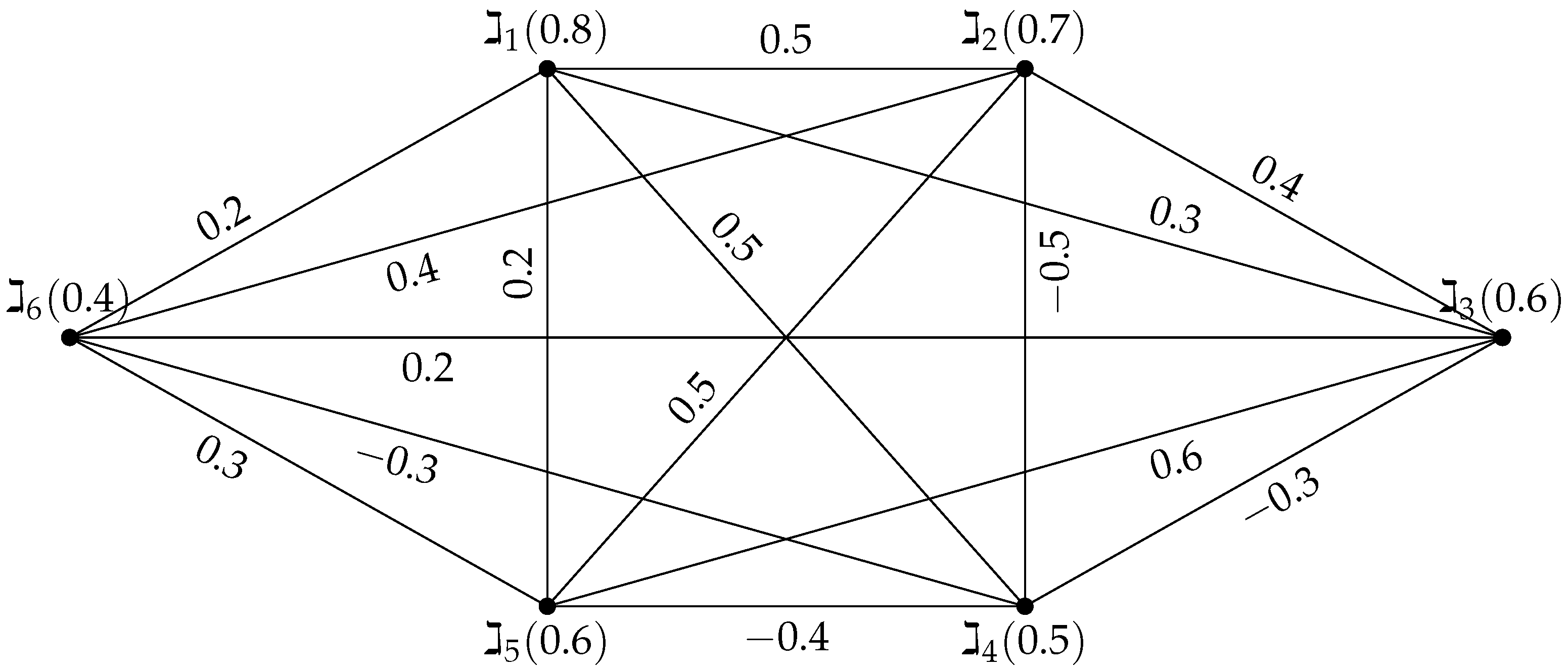
Suppose we have a signed-FG representing a healthcare network with six nodes as follows: denotes a large hospital with a membership value of , denotes a clinic with a membership value of , denotes a specialty care facility with a membership value of , denotes a pharmacy with a membership value of , denotes a rehabilitation facility with a membership value of , and denotes an emergency care facility with a membership value of . The connections between these facilities are depicted as edges, including supply chains, patient referrals, and casework collaboration. With a signed fuzzy membership value (ranging from to 1) and a sign (positive or negative), each edge indicates the reliability and strength of the connection.
Let
be a signed-FG, where the vertex set
and edge set
with the following vertex values:
,
, and
. The edge values are
, and
, as shown in
Figure 8. The strong arcs are
, and
. The possible dominating sets are
,
,
, and
. The domination integrity is
.
Using the above formula, healthcare administrators can apply the concept of dominance integrity in healthcare networks to quantitatively assess and optimize the resilience of their networks. The lowest value of denotes the optimal configuration of key facilities to ensure minimal disruption to network operations, guiding strategic decisions to maintain a dependable and effective healthcare delivery system.