Intelligent System Study for Asymmetric Positioning of Personnel, Transport, and Equipment Monitoring in Coal Mines
Abstract
1. Introduction
2. Materials and Methods
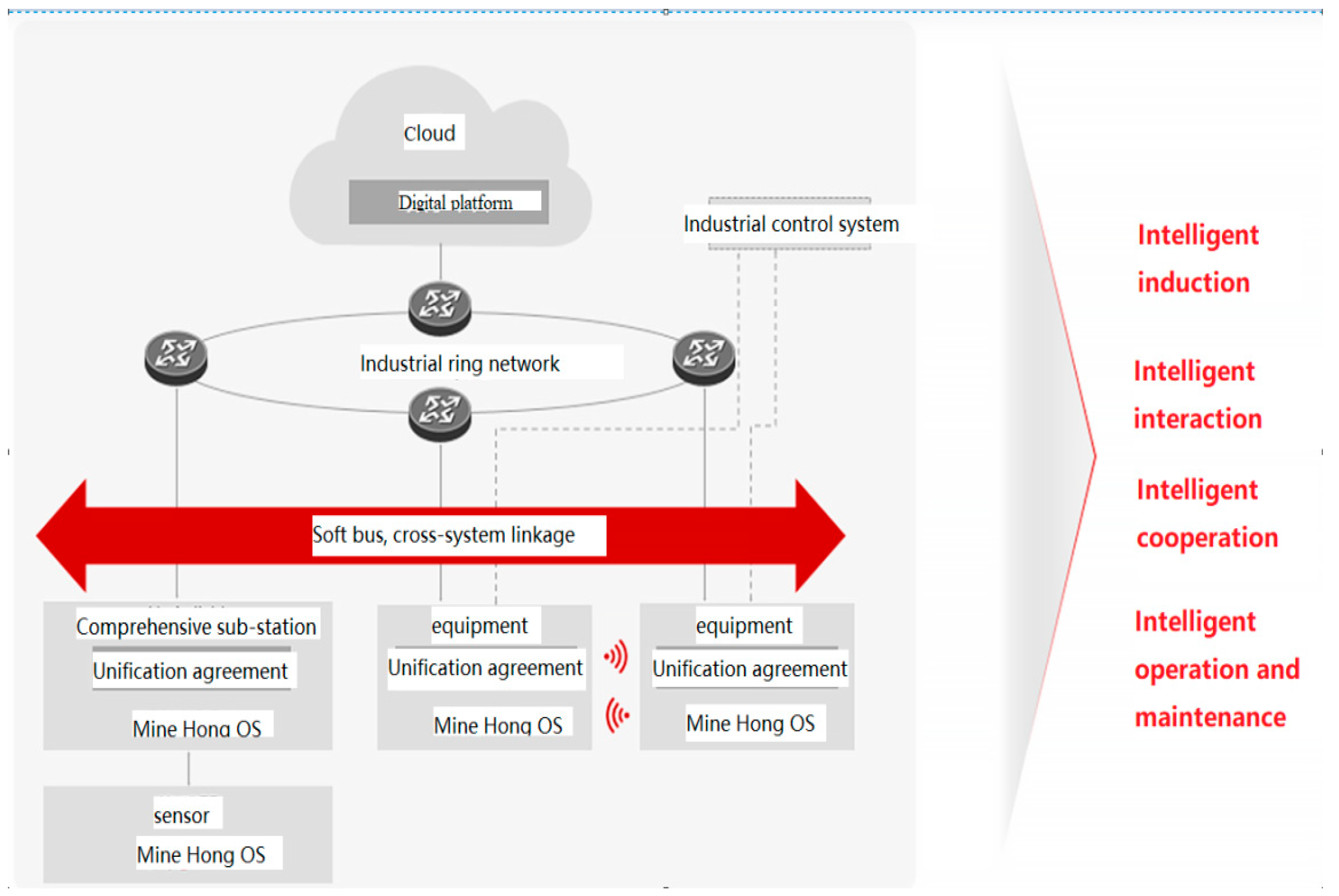
- Intelligent system architecture and functions:
- (1)
- Comprehensive safety: real-time positioning and monitoring functions provide control over personnel and equipment, while hazardous behavior detection and early warning mechanisms effectively reduce accidents.
- (2)
- Efficient resource management: intelligent route planning and optimization greatly improves the efficiency of rock mass transportation, reducing resource wastage and operating costs.
- (3)
- Intelligent operation support: the system’s data recording and analysis function provides a visual report for mine management and supports scientific decision-making and management optimization.
- (4)
- Modular scalability: the system is very flexible and can be expanded according to the actual needs of the mine, such as environmental monitoring, energy management, etc.
- (5)
- This study implements the positioning and fall detection of personnel through video analysis of existing surveillance cameras, without the need to install additional underground positioning equipment, effectively avoiding installation difficulties in special environments.
- (1)
- (2)
- Behavioral safety detection: in conjunction with known hazardous areas in mining areas (such as high-temperature equipment or hazardous work zones), the system calculates the distance between personnel and these hazardous areas and marks them in real time. When a person approaches a hazardous area, the system emits an alarm.
- (3)
- Behavioral analysis and safety early warning: the system utilizes OpenPose technology [18] to analyze the behavior of an identified person, identifying dangerous behaviors such as falling, immobility, etc., and triggering an appropriate safety early warning based on the distance to the danger zone.
- (1)
- The detection of foreign bodies during the transportation of minerals on the conveyor belt: utilizing computer vision and sensor technology to monitor minerals on the conveyor belt in real time, accurately detecting foreign objects or anomalies and ensuring a smooth and safe transfer process;
- (2)
- (3)
- Automatic shutdown and signaling: if foreign objects are detected, the system automatically sounds an alarm and shuts down to prevent equipment damage or accidents;
- (4)
- Data recording and analysis: records the time, location, and category of foreign object detection to provide the data needed to further improve ore sorting and handling processes;
- (5)
- Transport detection and route planning: using positioning technology and a transport planning algorithm [26], the speed and path of mining machines are dynamically tracked and optimized to improve transport efficiency and reduce road safety hazards;
- (6)
- Speed monitoring and warning: using GPS and sensors to monitor vehicle speed in real time, detect dangerous activities such as speeding or emergency stops, and provide timely safety warnings;
- (7)
- Route planning and optimization: intelligent planning of an optimal vehicle route based on real-time traffic data and transport tasks in mining areas reduces congestion and fuel consumption;
- (8)
- Collision avoidance systems: use of UWB sensors or vision sensors to monitor the distance between the vehicle and surrounding objects or people to avoid collisions;
- (9)
- Data visualization and planning: dynamic map of the mining area, real-time display of vehicle location, task status, and transport efficiency, and intuitive management tools for planners.
- Features of system architecture design:
- (1)
- Image input: the system can process a single frame image of the mine area and analyze the position and behavior of people in the image;
- (2)
- Video input: real-time analysis of the location, behavior, and interaction of personnel with hazardous areas using video streams.
- (1)
- Model selection and training: A pre-trained CNN model such as YOLO [29], Faster R-CNN [30], Mask R-CNN [31], or RetinaNet [32] is selected, and further tuned to adapt to the mining scene. To ensure that the model can identify people in different environments, large-scale mining image data are employed;
- (2)
- Image processing: the input image or video frame is pre-processed, including scaling, normalization, and enhancement, to ensure that the input image meets the requirements of the model;
- (3)
- Personnel detection: the processed image is input to the CNN model and the model outputs information about the location (bounding box), type (e.g., workers, visitors, etc.), and confidence level of the personnel;
- (4)
- Transmission of results: the location information of the person is then transmitted for further processing to the module for detection of subsequent behavior and early warning of security breaches.
- (1)
- Define the danger zone: In the geographical information system (GIS) of the mine area, the specific location of the danger zone is marked in advance and the safety radius is defined. For example, for a piece of equipment, define a danger zone within 5 m of the equipment;
- (2)
- Real-time distance calculation: By comparing the location of the person identified by the CNN model and the location of the marked danger zone, the distance between the person and the danger zone is calculated in real time. Simple calculations can be performed using Euclidean distance or Manhattan distance;
- (3)
- Hazard Zone Marking: when personnel enter or approach a hazardous area, the system will highlight the hazardous area and send a warning signal to remind the mine manager to pay attention.
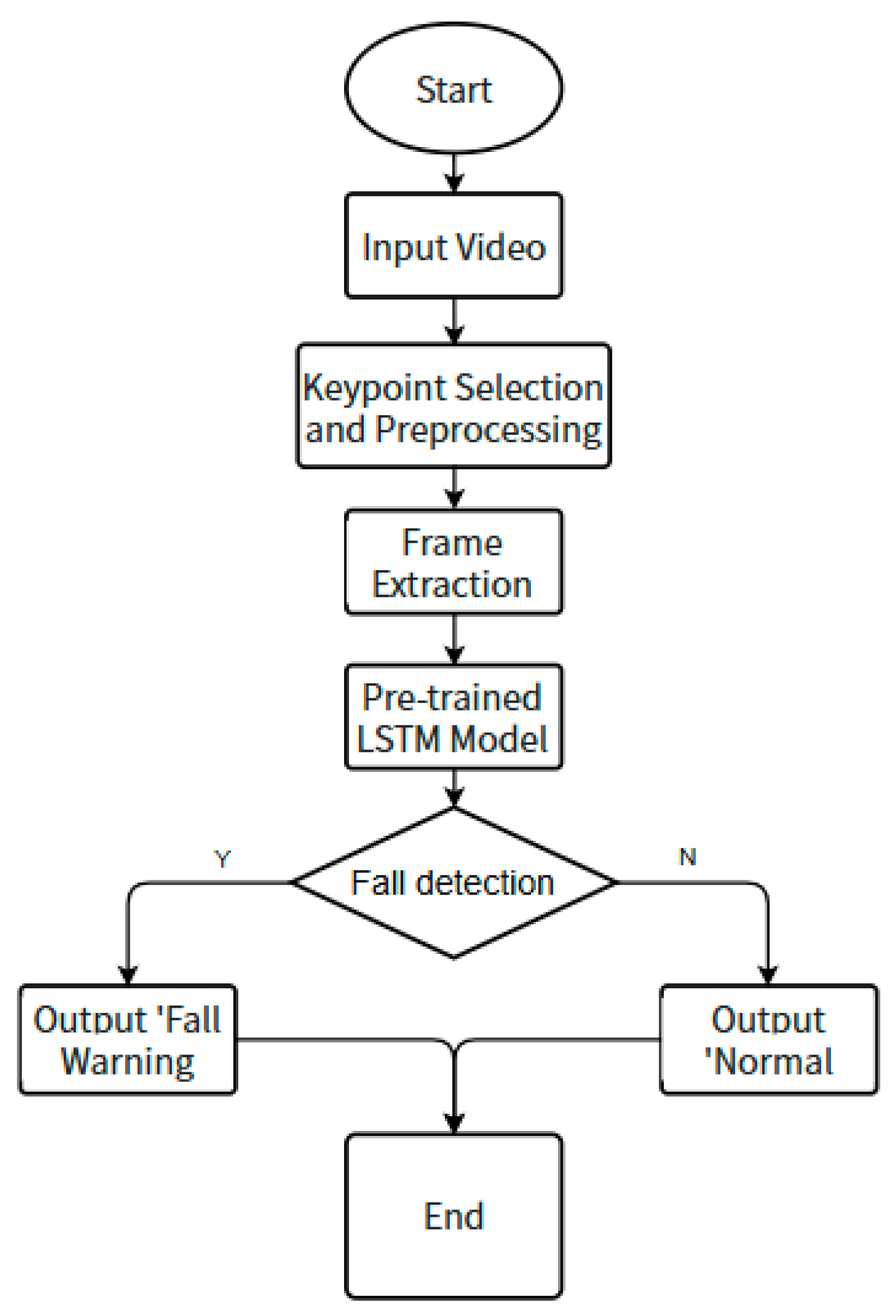
- (1)
- Loading the OpenPose model: using the pre-trained OpenPose model, initialize and load the required parameters;
- (2)
- Pose Recognition: Analyze the pose of the person detected and extract the coordinates of key points, including head, torso, limbs, etc. The OpenPose model is able to identify 18 key points of the human body based on a photo or video frame and generate a human skeleton map based on these points;
- (3)
- Behavioral Analysis: Based on the pose data, the system can determine if a person has abnormal behavior. For example, if a person’s horizontal body posture is detected to be too low (e.g., limbs pressed against the ground), the system can assume that the person has fallen; if a person’s posture is detected to be unchanged for a long time, the system recognizes that the person may be in a motionless state;
- (4)
- Hazard Warning: in combination with the hazardous area analysis in the second step, when a person falls or remains motionless near a hazardous area for a long time, the system issues a hazard warning and notifies the relevant management personnel so that they can take action in time.
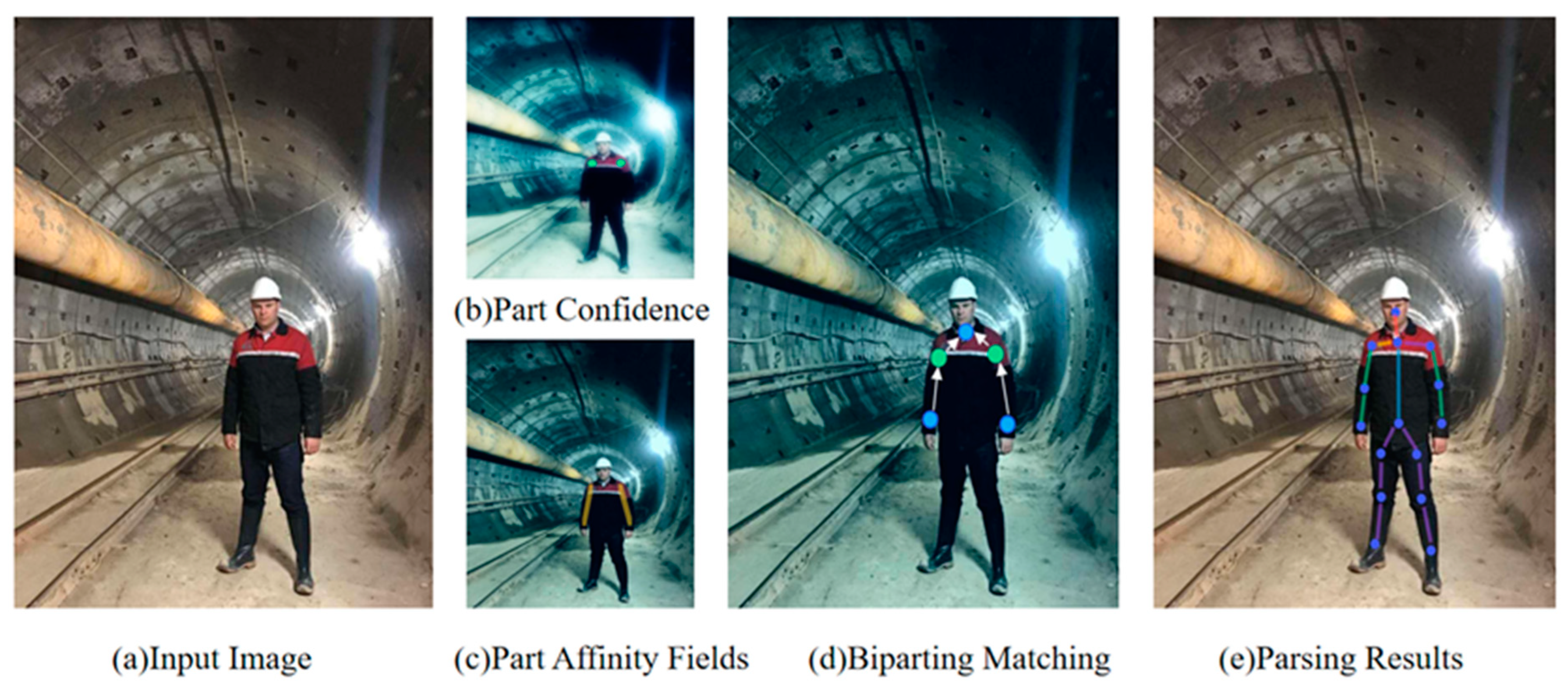
- part (a): first, the whole image is fed to CNN, which generates prediction;
- part (b): confidence maps to locate the body parts;
- part (c): object affinity fields to establish relationships between body parts;
- part (d): using these results, a two-part matching algorithm is applied to connect the detected body parts;
- part (e): finally, the body parts are assembled into full poses of all people in the image.
- (1)
- Candidate points for both body part types (red and blue lines) and all possible connections (gray lines) are identified;
- (2)
- The connections are optimized using midpoints (yellow dots) so that correct connections are represented by black lines and incorrect ones by green lines while satisfying the association constraints;
- (3)
- The final result is obtained using the PAF (yellow arrow), which encodes the position and orientation of the limb, effectively eliminating false connections.
3. Results and Discussions
- Technical implementation details:
- (1)
- CNN model: CNN model for personnel location detection was selected from Faster R-CNN because this model has high detection accuracy and good generalization ability and is suitable for real-time personnel detection in the mining industry;
- (2)
- OpenPose: It was used for pose estimation and behavior analysis. OpenPose analyzes human poses in real time by identifying human key points and is a key tool for behavior detection and early warning of danger;
- (3)
- Python.3,8.3 + OpenCV: A basic framework for image and video processing. OpenCV is a powerful image-processing library that efficiently processes frames and integrates with deep learning models;
- (4)
- PyTorch/TensorFlow: as a deep learning framework for the CNN model and OpenPose model, it provides model loading, training, and inference functions.
- Simulation result:
- (1)
- Accuracy: the accuracy of the inspection model is the primary metric used to ensure that all personnel in the mine are correctly identified and located;
- (2)
- Coverage: evaluation of the model’s ability to detect complex conditions such as illumination changes, occlusion, etc., to fully capture all target individuals;
- (3)
- Response time: it is necessary to ensure that the system has a high level of real time so that monitoring and early warning of mine personnel can be provided in a timely manner, typically requiring each frame to be processed in less than 100 milliseconds.
4. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Chemezov, E.N. Industrial safety principles in coal mining. J. Min. Inst. 2019, 240, 649–653. [Google Scholar] [CrossRef]
- Kabanov, E.I. Analysis of accidents risk in coal mines taking into account human factor. Gorn. Zhurnal 2023, 9, 48–54. [Google Scholar] [CrossRef]
- Kazanin, O.I. Promising technology trends in underground coal mining in Russia. Gorn. Zhurnal 2023, 9, 4–11. [Google Scholar] [CrossRef]
- Safiullin, R.N.; Safiullin, R.R.; Efremova, V.A. Method of complex assessment of on-board information and control systems on mining machines. Min. Informational Anal. Bull. 2023, 9, 49–63. [Google Scholar] [CrossRef]
- Materova, E.S.; Aksenova, Z.A.; Sharafullina, R.R.; Galimova, G.A.; Shilov, M.L. Digitalization of operations in the Russian mining companies. Ugol 2024, 11, 117–121. Available online: https://ugolinfo.ru/artpdf/RU2411117.pdf (accessed on 2 May 2025).
- Sychev, Y.A.; Nazarychev, A.N.; Dyachenok, G.V. Improving the Labor Safety of Mining Dump Truck Drivers by Reducing the Risk of Failure of the Functional Units of the Traction Electric Drive under Operating Conditions. Bezop. Tr. Promyshlennosti 2023, 9, 52–58. [Google Scholar] [CrossRef]
- Efimov, I.; Gabdulkhakov, R.R.; Rudko, V.A. Fine-tuned convolutional neural network as a tool for automatic mostructure analysis of petroleum and pitch cokes. Fuel 2024, 376, 13272. [Google Scholar] [CrossRef]
- Shestakov, A.K.; Petrov, P.A.; Nikolaev, M.Y. Automatic system for detecting visible emissions in a potroom of aluminum plant based on technical vision and a neural network. Metallurgist 2023, 66, 1308–1319. [Google Scholar] [CrossRef]
- Pshenin, V.; Liagova, A.; Razin, A.; Skorobogatov, A.; Komarovsky, M. Robot crawler for surveying pipelines and metal structures of complex spatial configuration. Infrastructures 2022, 7, 75. [Google Scholar] [CrossRef]
- Ramesh, S.H.; Lemaire, E.D.; Cheung, K.; Tu, A.; Baddour, N. Automated Stride Detection from OpenPose Keypoints Using Handheld Smartphone Video. In Proceedings of the IEEE Sensors Applications Symposium (SAS), Ottawa, ON, Canada, 18–20 July 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Solichah, U.; Purnomo, M.H.; Yuniarno, E.M. Marker-less Motion Capture Based on Openpose Model Using Triangulation. In Proceedings of the International Seminar on Intelligent Technology and Its Applications (ISITIA), Surabaya, Indonesia, 22–23 July 2020; pp. 217–222. [Google Scholar] [CrossRef]
- Muratbakeev, E.H.; Kozhubaev, Y.N.; Yao, Y.; Shehzad, U. Symmetrical Modeling of Physical Properties of Flexible Structure of Silicone Materials for Control of Pneumatic Soft Actuators. Symmetry 2024, 16, 750. [Google Scholar] [CrossRef]
- Zemenkova, M.Y.; Chizhevskaya, E.L.; Zemenkov, Y.D. Intelligent monitoring of the condition of hydrocarbon pipeline transport facilities using neural network technologies. J. Min. Inst. 2022, 258, 933–944. [Google Scholar] [CrossRef]
- Klyuev, R.V.; Morgoeva, A.D.; Gavrina, O.A.; Bosikov, I.I.; Morgoev, I.D. Forecasting planned electricity consumption for the united power system using machine learning. J. Min. Inst. 2023, 261, 392–402. [Google Scholar]
- Paliwal, M.; Chawla, S.K.; Soni, P. Digit Recognition by the Implementation of Supervised Learning Using a Convolutional Neural Network. In Proceedings of the 2023 3rd International Conference on Technological Advancements in Computational Sciences (ICTACS), Tashkent, Uzbekistan, 1–3 November 2023; pp. 227–231. [Google Scholar] [CrossRef]
- Pranav, E.; Kamal, S.; Chandran, C.S.; Supriya, M.H. Facial Emotion Recognition Using Deep Convolutional Neural Network. In Proceedings of the 2020 6th International Conference on Advanced Computing and Communication Systems (ICACCS), Coimbatore, India, 6–7 March 2020; pp. 317–320. [Google Scholar] [CrossRef]
- Yang, H.; Yuan, C.; Xing, J.; Hu, W. SCNN: Sequential convolutional neural network for human action recognition in videos. In Proceedings of the 2017 IEEE International Conference on Image Processing (ICIP), Beijing, China, 17–20 September 2017; pp. 355–359. [Google Scholar] [CrossRef]
- Surowka, A. Real-time Multi Pose Trajectory Tracking based on OpenPose Keypoints. In Proceedings of the 2021 11th IEEE International Conference on Intelligent Data Acquisition and Advanced Computing Systems: Technology and Applications (IDAACS), Cracow, Poland, 22–25 September 2021; pp. 813–817. [Google Scholar] [CrossRef]
- Kartik, B. IOT based Smart Helmet for Hazard Detection in mining industry. arXiv 2023, arXiv:2304.10156. [Google Scholar] [CrossRef]
- Bai, Z.; Pei, X.; Qiao, Z.; Wu, G.; Bai, Y. Improved YOLOv7 Target Detection Algorithm Based on UAV Aerial Photography. Drones 2024, 8, 104. [Google Scholar] [CrossRef]
- Duan, S.; Wang, T.; Li, T.; Yang, W. M-YOLOv8s: An improved small target detection algorithm for UAV aerial photography. J. Vis. Commun. Image Represent. 2024, 104, 104289. [Google Scholar] [CrossRef]
- Zhao, Y.; Wang, L.; Lei, G.; Guo, C.; Ma, Q. Lightweight UAV Small Target Detection and Perception Based on Improved YOLOv8-E. Drones 2024, 8, 681. [Google Scholar] [CrossRef]
- Yamsani, N.; Jabar, M.B.; Adnan, M.M.; Hussein, A.H.A.; Chakraborty, S. Facial Emotional Recognition Using Faster Regional Convolutional Neural Network with VGG16 Feature Extraction Model. In Proceedings of the 2023 3rd International Conference on Mobile Networks and Wireless Communications (ICMNWC), Tumkur, India, 4–5 December 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Kalpana, P.; Sitaraman, S.R.; Harakannanavar, S.S.; Alsalami, Z.; Nagaraj, S. Efficient Multimodal Biometric Recognition for Secure Authentication Based on Faster Region-Based Convolutional Neural Network. In Proceedings of the 2024 Second International Conference on Networks, Multimedia and Information Technology (NMITCON), Bengaluru, India, 9–10 August 2024; pp. 1–5. [Google Scholar] [CrossRef]
- Chang, J.; Xiao, J.; Chai, J.; Zhou, Z. An Improved Faster R-CNN Algorithm for Gesture Recognition in Human-Robot Interaction. In Proceedings of the 2019 Chinese Automation Congress (CAC), Hangzhou, China, 22–24 November 2019; pp. 5761–5764. [Google Scholar] [CrossRef]
- Guo, J.; Li, Z.; Dong, H.; Li, R.; Sun, N. Design of intelligent transportation verification platform based on hardware in the loop simulation technology. In Proceedings of the 2022 8th International Conference on Hydraulic and Civil Engineering: Deep Space Intelligent Development and Utilization Forum (ICHCE), Xi’an, China, 25–27 November 2022; pp. 401–405. [Google Scholar] [CrossRef]
- Zhang, Z.; Li, T.; Chen, G.; Xiao, Y.; Li, M.; Wang, J.; Zhao, Y.; Sun, S. Research on 5G Network System Construction of Intelligent Open-pit Mine. In Proceedings of the 2023 IEEE 3rd International Conference on Information Technology, Big Data and Artificial Intelligence (ICIBA), Chongqing, China, 26–28 May 2023; pp. 1425–1429. [Google Scholar] [CrossRef]
- Osokin, D. Real-time 2D Multi-Person Pose Estimation on CPU: Lightweight OpenPose. In Proceedings of the International Conference on Pattern Recognition Applications and Methods, Funchal, Portugal, 16–18 January 2018. [Google Scholar] [CrossRef]
- Liu, C.; Tao, Y.; Liang, J.; Li, K.; Chen, Y. Object Detection Based on YOLO Network. In Proceedings of the 2018 IEEE 4th Information Technology and Mechatronics Engineering Conference (ITOEC), Chongqing, China, 14–16 December 2018; pp. 799–803. [Google Scholar] [CrossRef]
- Liu, Y. An Improved Faster R-CNN for Object Detection. In Proceedings of the 2018 11th International Symposium on Computational Intelligence and Design (ISCID), Hangzhou, China, 8–9 December 2018; pp. 119–123. [Google Scholar] [CrossRef]
- Huiming, Y.; Fuxin, X. A remote sensing image target recognition method based on improved Mask-RCNN model. In Proceedings of the 2021 IEEE 2nd International Conference on Big Data, Artificial Intelligence and Internet of Things Engineering (ICBAIE), Nanchang, China, 26–28 March 2021; pp. 436–439. [Google Scholar] [CrossRef]
- Qi, Z.; Zhang, M.; Li, J.; Bo, C.; Wang, C.; Peng, H. Improved RetinaNet-Based Defect Detection for Engine Parts. In Proceedings of the 2023 42nd Chinese Control Conference (CCC), Tianjin, China, 24–26 July 2023; pp. 7717–7722. [Google Scholar] [CrossRef]
- Vats, V.K.; Saikumar, R.; Prakash, C. Identification of knee angle trajectory in Indian outfit using Pose Analysis. In Proceedings of the 4th International Conference on Artificial Intelligence and Speech Technology (AIST), Delhi, India, 9–10 December 2022; pp. 1–6. [Google Scholar] [CrossRef]
- Lafayette, T.B.; Burle, A.D.; Almeida, A.D.; Ventura, V.L.; Carvalho, V.M.; Gama, A.D.; Teixeira, J.M.; Teichrieb, V. The Virtual Kinect. In Proceedings of the 23rd Symposium on Virtual and Augmented Reality, Virtual Event, Brazil, 18–21 October 2021. [Google Scholar] [CrossRef]
- Cao, Z.; Hidalgo, G.; Simon, T.; Wei, S.-E.; Sheikh, Y. OpenPose: Realtime Multi-Person 2D Pose Estimation Using Part Affinity Fields. IEEE Trans. Pattern Anal. Mach. Intell. 2021, 43, 172–186. [Google Scholar] [CrossRef] [PubMed]
- Han, X.; Wang, Y.; Zhai, B.; You, Q.; Yang, H. COCO is “ALL” You Need for Visual Instruction Fine-tuning. In Proceedings of the 2024 IEEE International Conference on Multimedia and Expo (ICME), Niagara Falls, ON, Canada, 15–19 July 2024; pp. 1–5. [Google Scholar] [CrossRef]
- Puri, D. COCO Dataset Stuff Segmentation Challenge. In Proceedings of the 2019 5th International Conference on Computing, Communication, Control and Automation (ICCUBEA), Pune, India, 19–21 September 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Li, S.; Ding, Z.; Chen, H. A Neural Network-Based Teaching Style Analysis Model. In Proceedings of the 2019 11th International Conference on Intelligent Human-Machine Systems and Cybernetics (IHMSC), Hangzhou, China, 24–25 August 2019; pp. 154–157. [Google Scholar] [CrossRef]




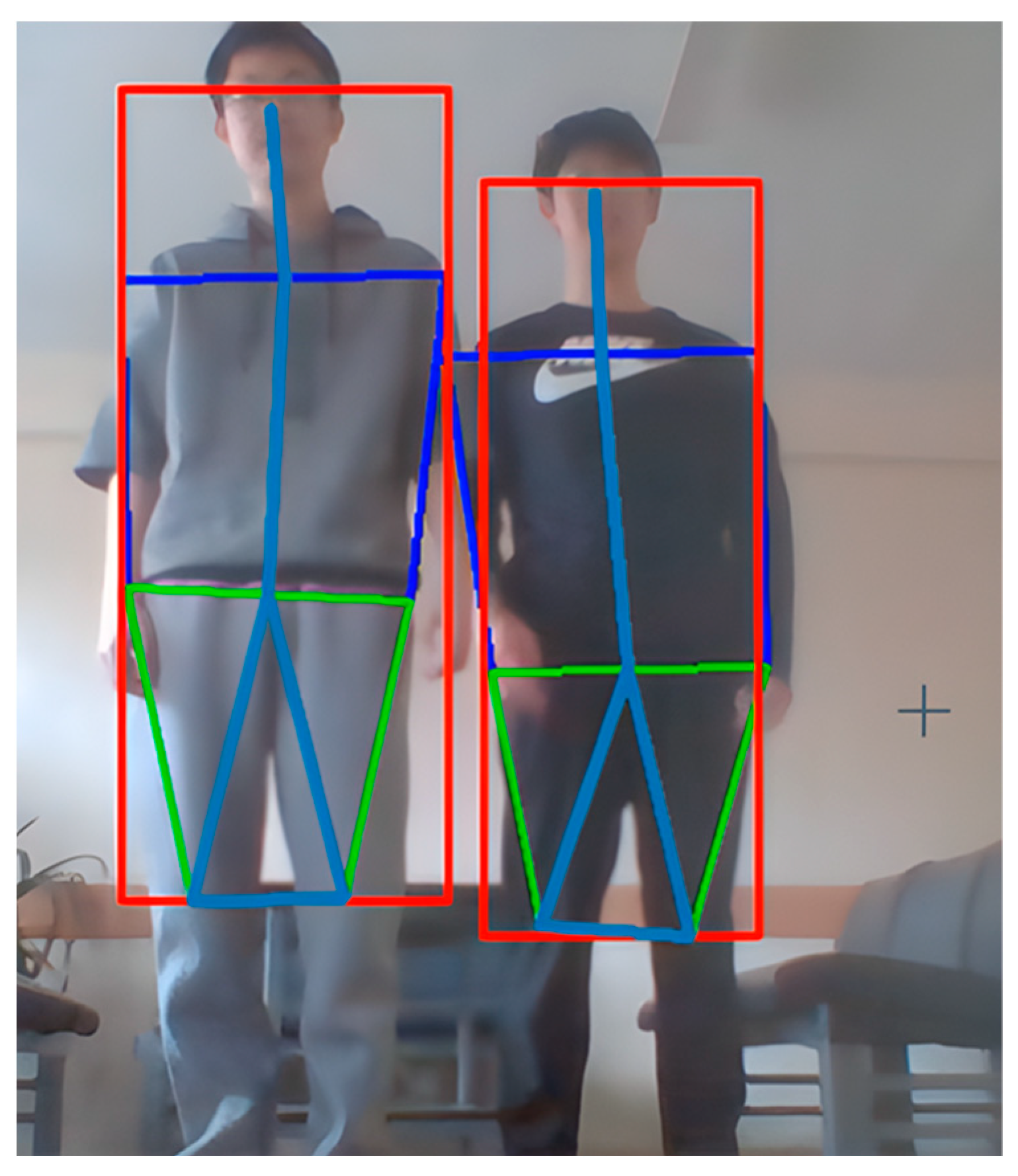


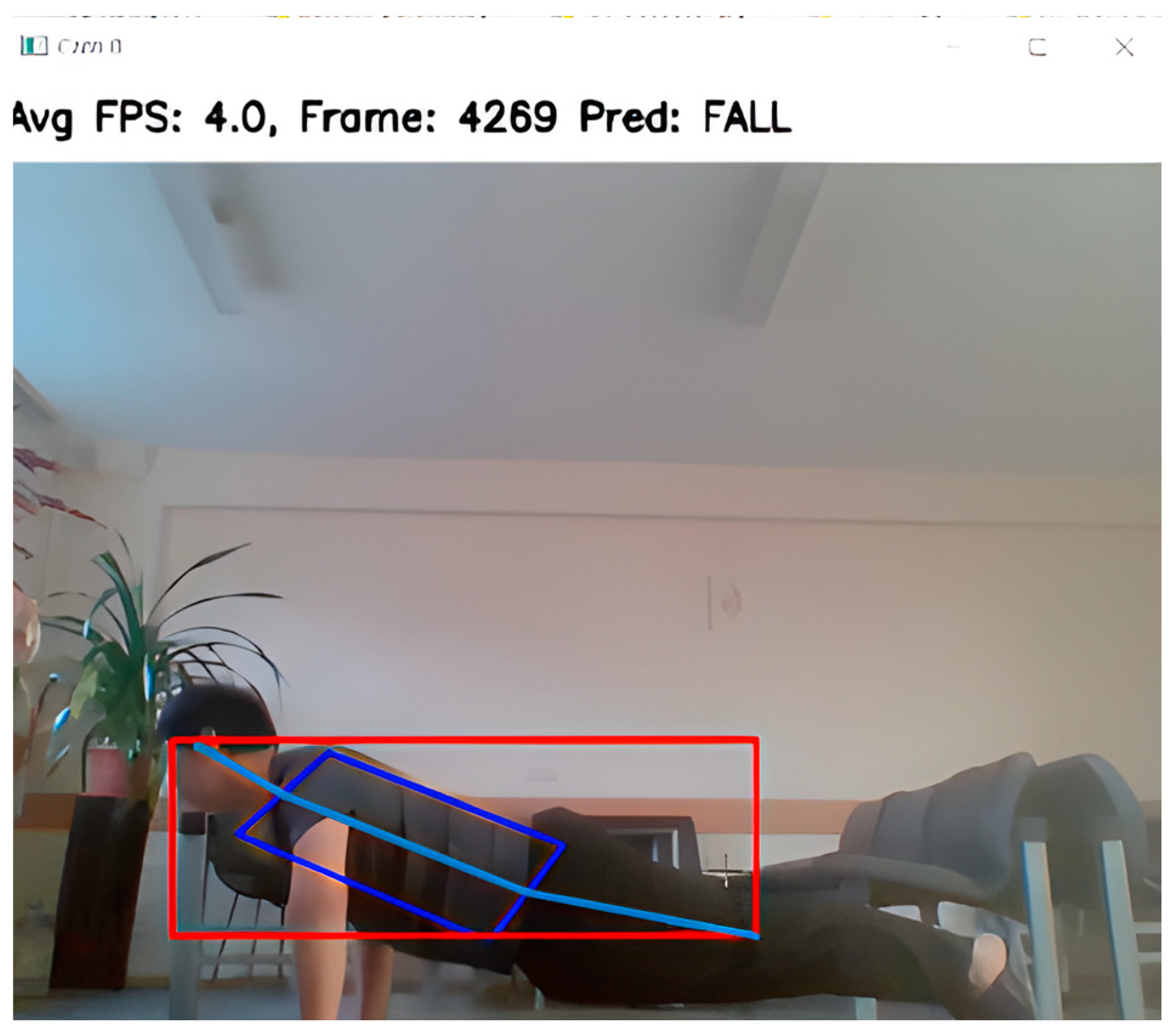
| Frame_ID | Ratio_Bbox | Log_Angle | re | Ratio_Derivative | gf | Label |
|---|---|---|---|---|---|---|
| 1 | 0.81 | 0.39 | 0.88 | 0.05 | 0.9 | 0 |
| 2 | 0.79 | 0.41 | 0.85 | 0.06 | 0.88 | 0 |
| 3 | 0.79 | 0.50 | 0.80 | 0.10 | 0.84 | 0 |
| 4 | 0.68 | 0.70 | 0.73 | 0.15 | 0.76 | 1 |
| 5 | 0.65 | 0.85 | 0.60 | 0.20 | 0.69 | 1 |
| Technology | Key Point Detection | Object Detection | Speed | Suitable for Fall Detection |
|---|---|---|---|---|
| OpenPose | Yes | No | intermediate | Behavior analysis, multi-person posture recognition |
| YOLO | No | Yes | fast | Monitoring, real-time applications |
| Faster RCNN | No | Yes | slow | Accurate detection, small target recognition |
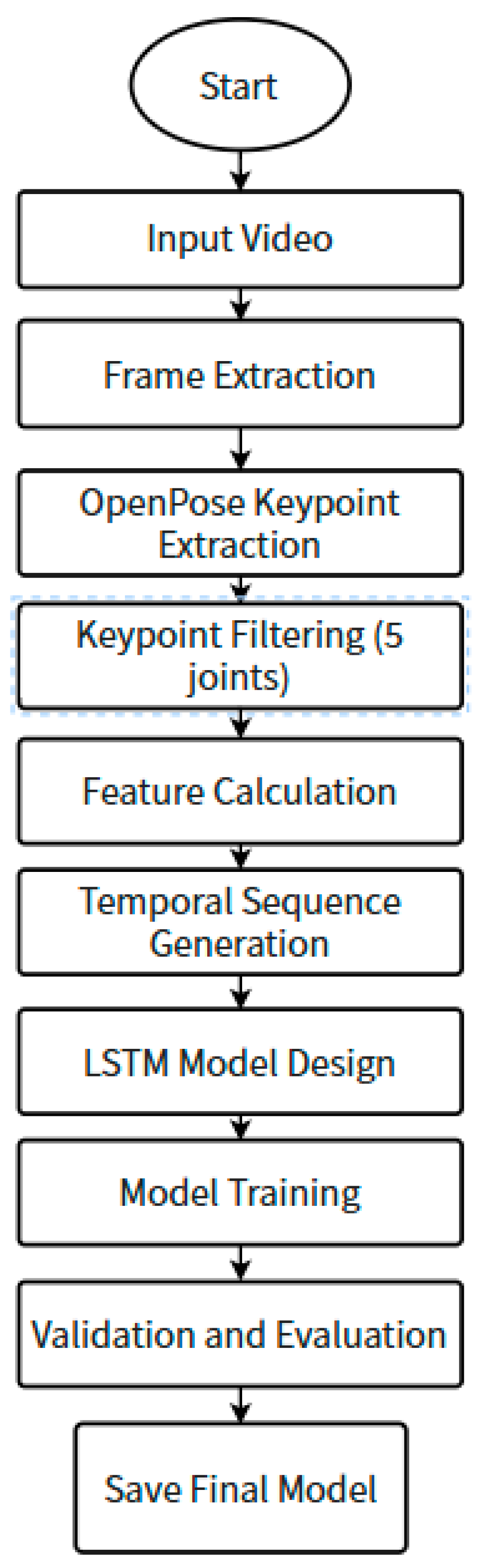
| Key Point Strategy | Accuracy (%) | Inference Time (ms) | Memory Usage (MB) |
|---|---|---|---|
| Full 18-Key point | 91.2 | 120 | 350 |
| Selected 5-Key Point | 89.8 | 65 | 150 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Novak, D.; Kozhubaev, Y.; Kang, H.; Cheng, H.; Ershov, R. Intelligent System Study for Asymmetric Positioning of Personnel, Transport, and Equipment Monitoring in Coal Mines. Symmetry 2025, 17, 755. https://doi.org/10.3390/sym17050755
Novak D, Kozhubaev Y, Kang H, Cheng H, Ershov R. Intelligent System Study for Asymmetric Positioning of Personnel, Transport, and Equipment Monitoring in Coal Mines. Symmetry. 2025; 17(5):755. https://doi.org/10.3390/sym17050755
Chicago/Turabian StyleNovak, Diana, Yuriy Kozhubaev, Hengbo Kang, Haodong Cheng, and Roman Ershov. 2025. "Intelligent System Study for Asymmetric Positioning of Personnel, Transport, and Equipment Monitoring in Coal Mines" Symmetry 17, no. 5: 755. https://doi.org/10.3390/sym17050755
APA StyleNovak, D., Kozhubaev, Y., Kang, H., Cheng, H., & Ershov, R. (2025). Intelligent System Study for Asymmetric Positioning of Personnel, Transport, and Equipment Monitoring in Coal Mines. Symmetry, 17(5), 755. https://doi.org/10.3390/sym17050755






