Improved Trust Evaluation Model Based on PBFT and Zero Trust Integrated Power Network Security Defense Method
Abstract
1. Introduction
1.1. Research Background
1.2. Research Problem
1.3. Research Status
1.4. Problems and Gaps in Existing Research
- Most trust management models for power communication networks are static and fail to adapt to dynamic threat conditions. When internal nodes are compromised and used as pivot points for lateral attacks, existing models cannot dynamically reassess trustworthiness or isolate malicious nodes in time [11,12].
- Current defense methods are effective against external intrusions but lack the capability to detect pivot intrusions, disguised nodes, and coordinated internal attacks. Once an attacker manipulates trust scores or forges node identities, the system may misjudge the node as trustworthy, leading to trust hijacking and expanded attack propagation [13]. These gaps highlight the need for a distributed, self-adaptive, and continuously verified trust evaluation mechanism that can jointly defend against both internal and external threats.
1.5. Research Objective and Scope
1.6. Paper Structure
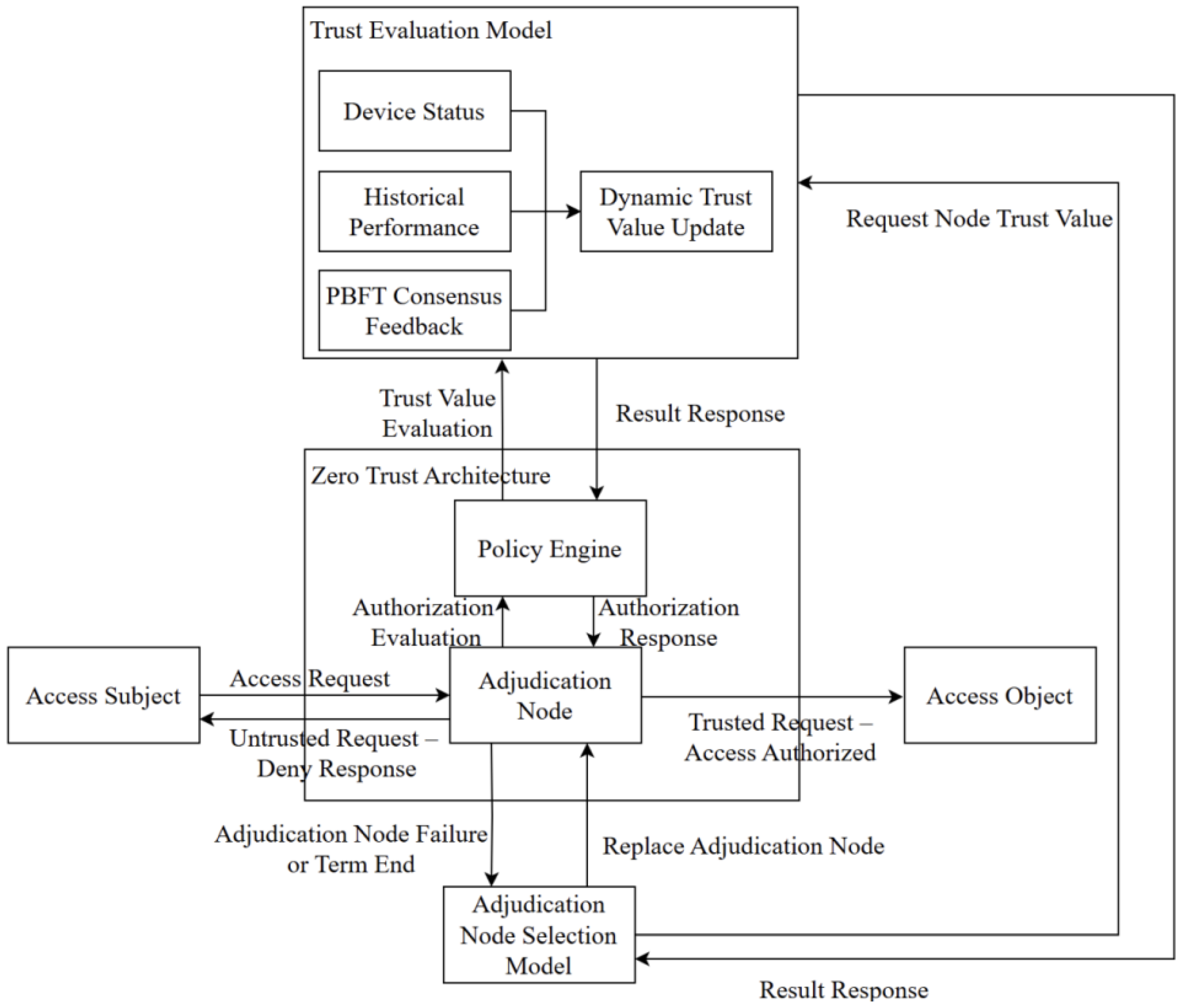
2. System Architecture
2.1. Framework Overview
2.2. Improved Trust Evaluation Model Based on PBFT
2.2.1. Initialization of Node Trust Value
2.2.2. Dynamic Update of Node Trust Value
- Historical Performance:The trust value is updated based on the node’s historical performance. The shorter the time interval between each successful consensus participation, the greater the historical impact on the trust score; conversely, longer intervals reduce the influence of historical behavior. This relationship is described as follows:where represents the time weighting function. represents the consensus time interval. A baseline of 20 ms is used as the reference: if a node has not participated in consensus within 20 ms, its trust value at time i will continuously decay. In contrast, nodes that frequently participate in consensus within the 20 ms threshold will experience rapid trust accumulation. The parameter serves as the adjustment factor for historical influence—larger values of result in a faster decay of the historical impact.
- Trust Value Update: The key to updating the trust value based on a node’s performance in the current consensus round lies in the introduction of positive reward and negative penalty mechanisms, which enable the quantitative assessment of node behavior [17].Positive Reward Mechanism: When a node correctly broadcasts information and efficiently participates in the consensus process, the system grants a positive trust incentive to the node. The positive reward mechanism is described as follows:where represent the current trust value of the node, and denote the magnitude of the reward. is the reward weighting coefficient for the i-th consensus round. Initially, the trust reward is relatively large to allow low-trust nodes to accumulate trust more quickly. As the number of consensus rounds increases, the reward magnitude gradually decreases, slowing the growth of high trust nodes. This mechanism enhances the overall stability of trust within the system. The reward weighting coefficient is described as follows:Negative Penalty Mechanism: When a node exhibits abnormal behavior such as failing to respond within a timeout period, broadcasting forged information, or participating in malicious attacks—the system reduces its trust value based on a penalty factor that reflects the severity of the behavior. This mechanism enables a rapid decline in the trustworthiness of malicious nodes, preventing them from exerting prolonged influence on the system. The penalty mechanism is described as follows:represent the current trust value of the node, and represent the trust value from the previous consensus round, indicates the magnitude of the penalty, while is the penalty weighting coefficient for the i-th consensus round. When a node has a high trust value, any detected malicious behavior results in more severe penalties, preventing high-trust nodes from leveraging their credibility to carry out malicious attacks. Conversely, low-trust nodes receive relatively lighter penalties for the same behavior.The penalty weighting coefficient is described as follows:
- Current Status and Trust Value Update: A node’s status directly determines both the credibility of its contribution to the system and the level of threat it may pose. In this paper, the definition of node status is provided in Table 1:The impact of different current node statuses on the trust value is described as follows:where represent the current trust value of the node, represent the trust value from the previous consensus round, C Represents the value range of penalty magnitude [−1, 0].
- Trust Value Update: By integrating the node current status and historical performance, the trust value is updated according to the following description.
2.2.3. Definition of Node Trust Threshold
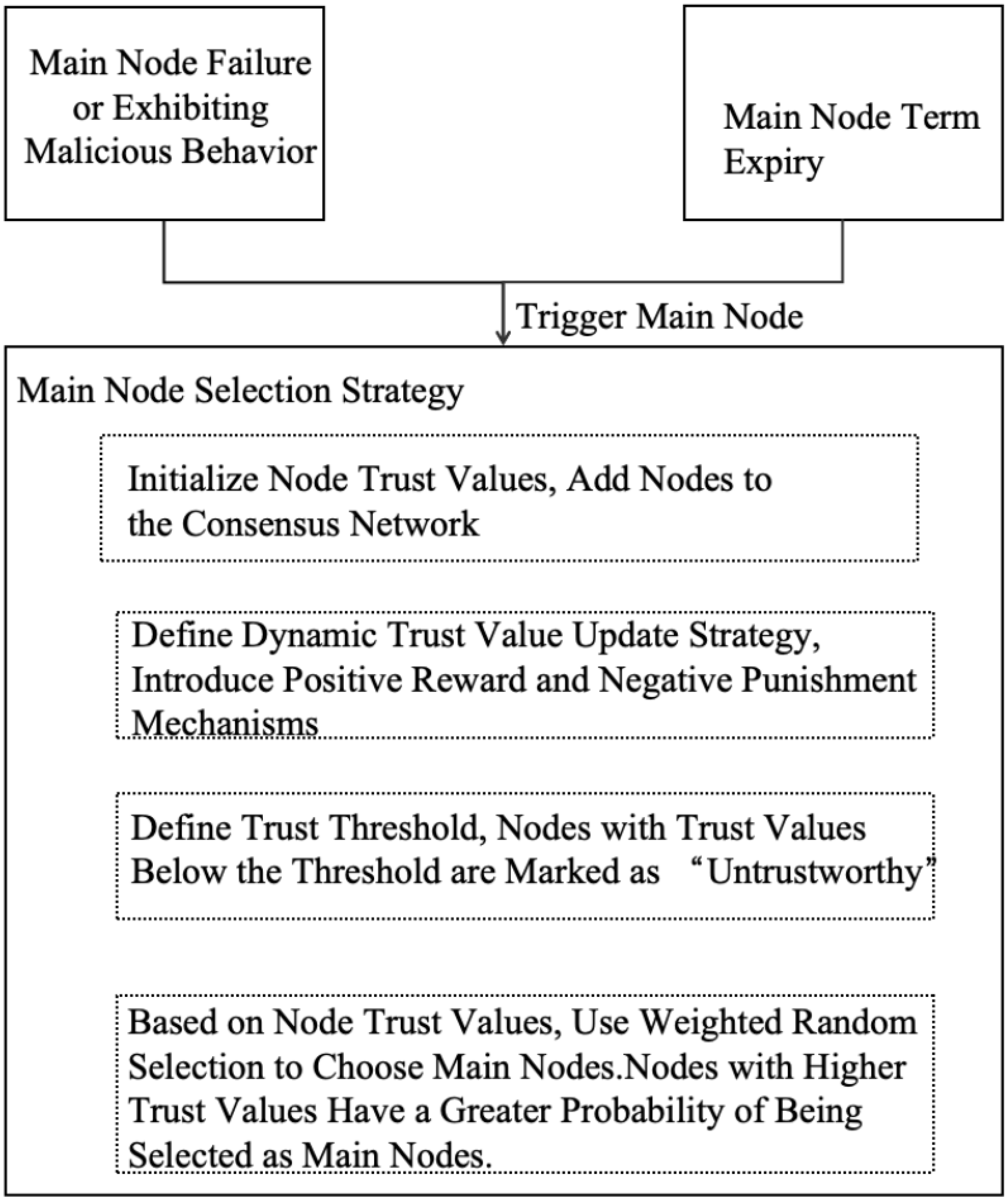
2.3. Adjudicator Node Selection Strategy in Zero Trust Architecture
- Lack of historical behavior and reputation consideration: Nodes with poor performance or malicious behavior may still be elected as primary nodes, leading to frequent primary replacements and reduced overall system efficiency.
- Absence of trust score filtering: Without using trust values as a selection criterion, the system is less capable of filtering out malicious nodes during the election process. Such nodes may more easily enter the core consensus process, potentially disrupting system operations.
- Unreliable node selection in consecutive view changes: If unreliable nodes are repeatedly selected in successive view changes, the system may suffer from prolonged performance degradation or frequent view transitions, negatively impacting business continuity and response stability.
3. Simulation Experiments
3.1. Experimental Environment
3.2. Trust Value Evaluation Experiments
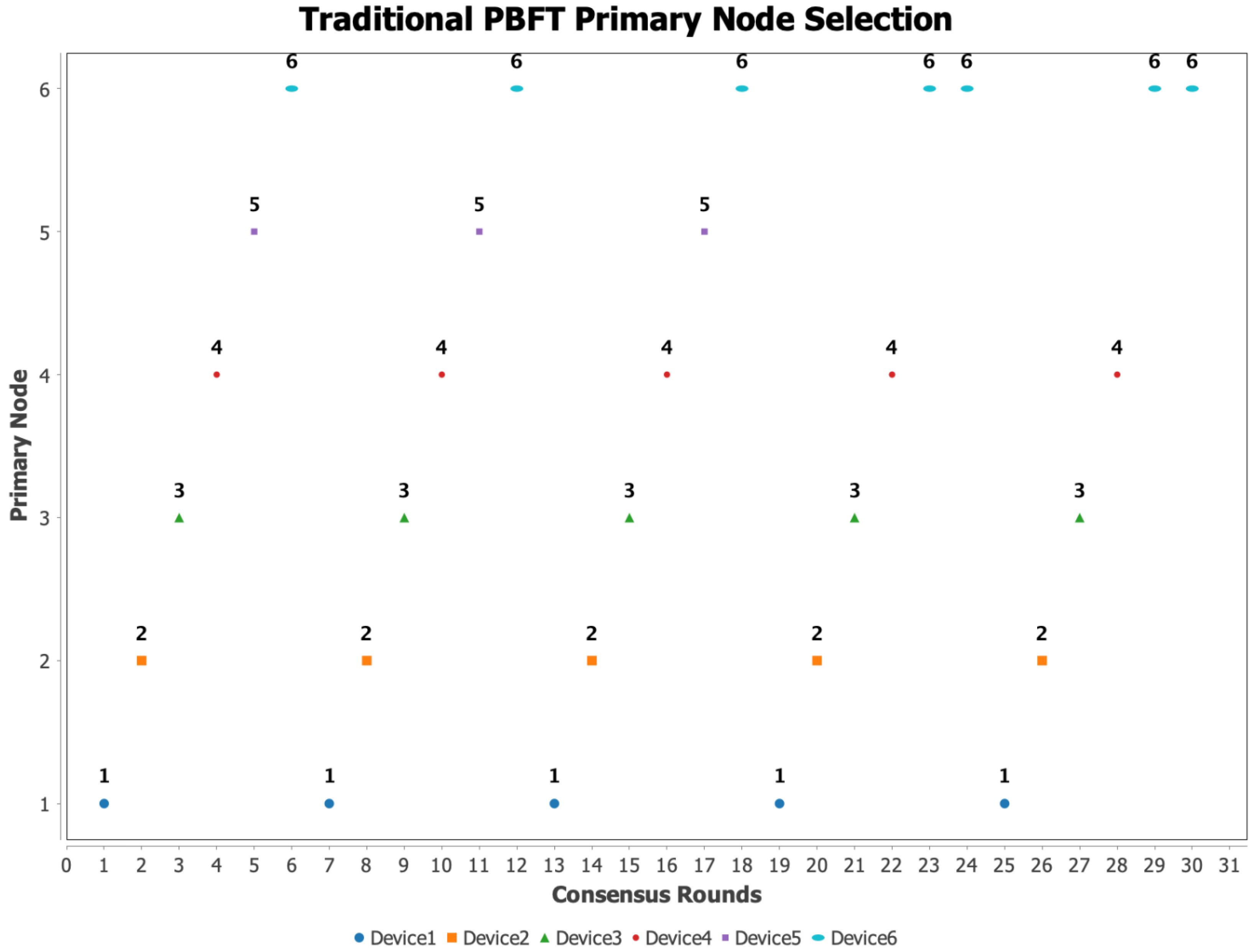
3.3. Adjudicator Node Selection Experiments
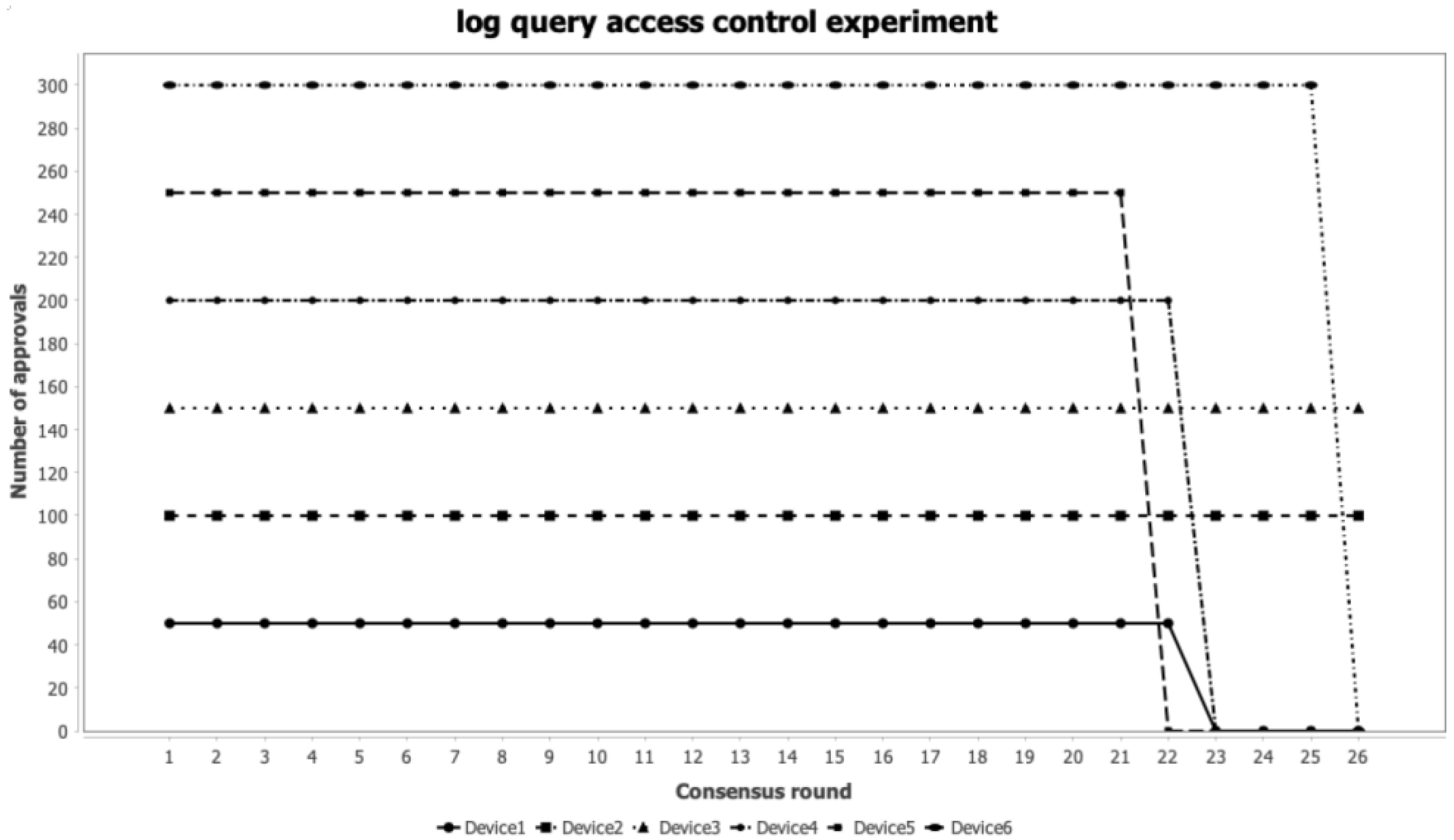
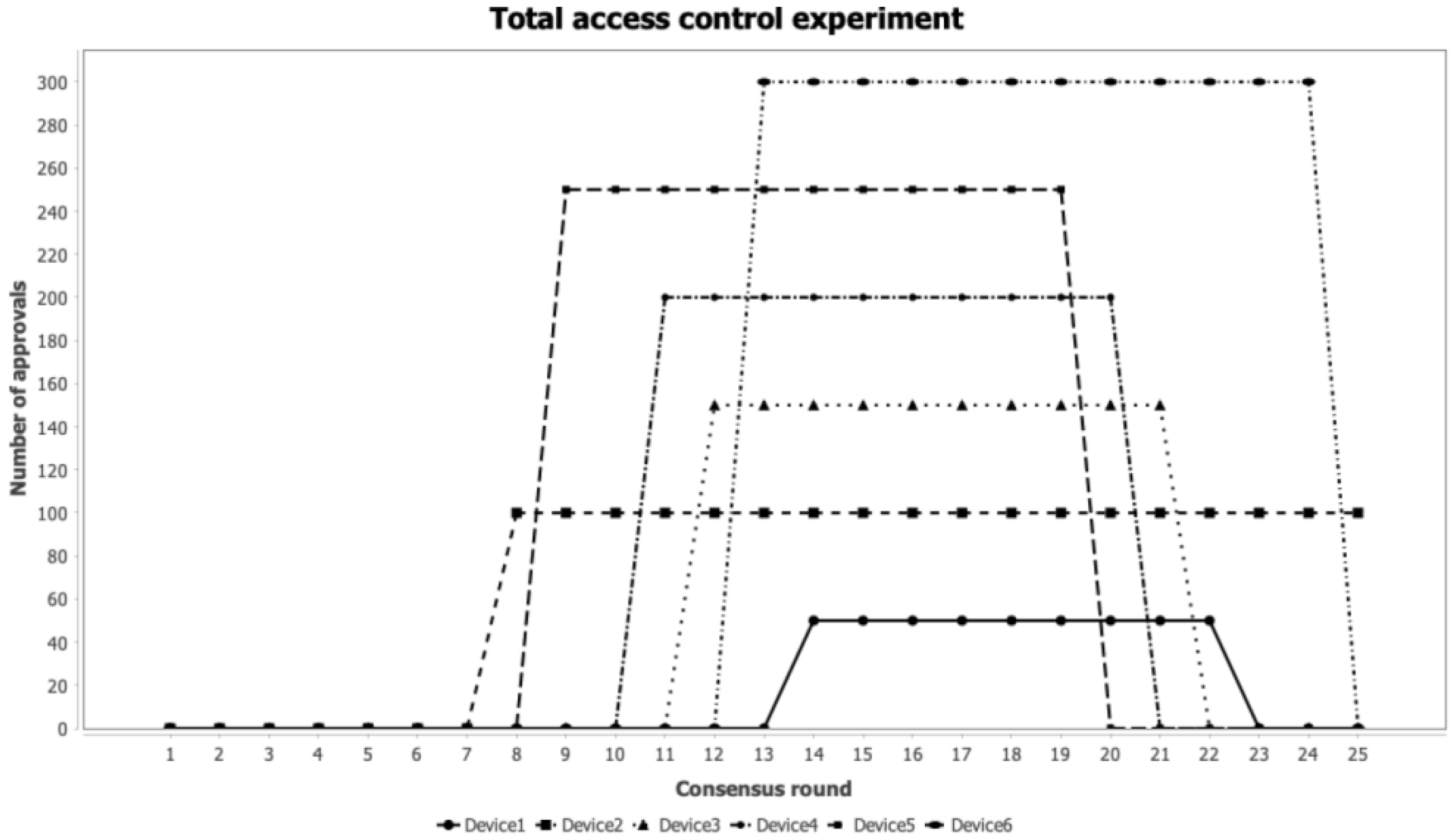
3.4. Access Control Experiments in Zero Trust Architecture
4. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Li, J.; Gu, C.; Xiang, Y.; Li, F. Edge-cloud computing systems for smart grid: State-of-the-art, architecture, and applications. J. Mod. Power Syst. Clean Energy 2022, 10, 805–817. [Google Scholar] [CrossRef]
- Wang, J.; Yan, Z.; Lan, J.; Bertino, E.; Pedrycz, W. TrustGuard: GNN-based robust and explainable trust evaluation with dynamicity support. IEEE Trans. Dependable Secure Comput. 2024, 21, 4433–4450. [Google Scholar] [CrossRef]
- Hammad, A.A.; Ahmed, S.R.; Abdul-Hussein, M.K.; Ahmed, M.R.; Majeed, D.A.; Algburi, S. Deep reinforcement learning for adaptive cyber defense in network security. In Proceedings of the 2024 Cognitive Models and Artificial Intelligence Conference, Dubai, United Arab Emirates, 15–17 March 2024; pp. 292–297. [Google Scholar]
- Khan, M.; Ghafoor, L. Adversarial machine learning in the context of network security: Challenges and solutions. J. Comput. Intell. Robot. 2024, 4, 51–63. [Google Scholar]
- Khan, Z.A.; Namin, A.S. A survey of DDoS attack detection techniques for IoT systems using Blockchain technology. Electronics 2022, 11, 3892. [Google Scholar] [CrossRef]
- Hajian, A.; Chang, H.C. A Blockchain-Based Smart Grid to Build Resilience Through Zero-Trust Cybersecurity; Springer International Publishing: Cham, Switzerland, 2022; pp. 1–19. [Google Scholar]
- Liu, T.; Ma, Y.; Jiang, H.; Wu, S.; Zuo, J.; Peng, T. Research on power grid security protection architecture based on zero trust. Elec. Power Inf. Commun. Technol. 2021, 19, 25–32. [Google Scholar]
- Sousa, J.; Bessani, A.; Vukolić, M. A byzantine fault-tolerant ordering service for the Hyperledger Fabric blockchain platform. In Proceedings of the 2018 48th Annual IEEE/IFIP International Conference on Dependable Systems and Networks, Luxembourg, 25–28 June 2018; pp. 51–58. [Google Scholar]
- Castro, M.; Liskov, B. Practical Byzantine fault tolerance. In Proceedings of the Symposium on Operating Systems Design and Implementation (OSDI), New Orleans, LA, USA, 22–25 February 1999; pp. 173–186. [Google Scholar]
- Zhang, Y.; Gan, Y.; Li, C.; Deng, C.; Luo, Y. Primary node selection based on node reputation evaluation for PBFT in UAV-assisted MEC environment. Wirel. Netw. 2023, 29, 3515–3539. [Google Scholar] [CrossRef]
- Lv, P.; Sun, X.; Huang, H.; Qian, J.; Sun, C.; Dai, H. Dynamic trust continuous evaluation-based zero-trust access control for power grid cloud service. J. Phys. Conf. Ser. 2022, 2402, 012008. [Google Scholar] [CrossRef]
- Wang, R.; Li, C.; Zhang, K.; Tu, B. Zero-trust based dynamic access control for cloud computing. Cybersecurity 2025, 8, 12. [Google Scholar] [CrossRef]
- Syed, N.F.; Shah, S.W.; Shaghaghi, A.; Anwar, A.; Baig, Z.; Doss, R. Zero trust architecture (ZTA): A comprehensive survey. IEEE Access 2022, 10, 57143–57179. [Google Scholar] [CrossRef]
- Hu, V.C.; Kuhn, D.R.; Ferraiolo, D.F.; Voas, J. Attribute-based access control. Computer 2015, 48, 85–88. [Google Scholar] [CrossRef]
- Zhu, X.; Hu, X.; Zhu, W. RGPBFT: A reputation-based PBFT algorithm with node grouping strategy. Arab. J. Sci. Eng. 2025, 50, 11837–11850. [Google Scholar] [CrossRef]
- Gambo, M.L.; Almulhem, A. Zero trust architecture: A systematic literature review. arXiv 2025, arXiv:2503.11659. [Google Scholar]
- Huang, H.; Zhang, J.; Hu, J.; Fu, Y.; Qin, C. Research on distributed dynamic trusted access control based on security subsystem. IEEE Trans. Inf. Forensics Secur. 2022, 17, 3306–3320. [Google Scholar] [CrossRef]
- Arun, G. Zero Trust Evolution: Advanced Architectures for Resilient Cloud-Native IAM Systems. Int. J. Sci. Res. Comput. Sci. Eng. Inf. Technol. 2025, 11, 679–685. [Google Scholar] [CrossRef]




| Node Status | Cause of Status |
|---|---|
| Normal Status | The node functions normally and participates in consensus. |
| Slightly Abnormal Status | May be caused by network jitter; occasional timeout of the node. |
| Abnormal Status | Frequent timeouts, refusal to respond, or inconsistent consensus results. |
| Resource-Deficient Status | The node’s limited resources lead to reduced responsiveness. |
| Malicious Status | The node is explicitly marked as untrustworthy, such as one that has been compromised. |
| Node Trust Status | Node Behavior | Specific Description | Definition |
|---|---|---|---|
| Honest Node | Normal | Node consistently and stably participates in consensus | |
| Trusted Node | Normal | Node normally participates in consensus | |
| Floating Node | Behavior not clearly defined | Newly joined nodes or nodes with consensus timeouts | |
| Faulty Node | Malicious behavior | Nodes identified as malicious or whose consensus results are inconsistent |
| Configuration Item | Specific Parameters |
|---|---|
| Operating System | Ubuntu 20.04.2 LTS |
| Processor | Intel® CoreTM i7-10700H CPU @ 2.9 GHz (8 cores, 16 threads) |
| Memory | 8 GB DDR4 3200 MHz (single channel, 1 GB allocated to each experimental node) |
| Storage | 1 TB SSD (NVMe protocol, read 3500 MB/s, write 3000 MB/s) |
| Network | Gigabit Ethernet, limited to 10 Mbps via router, stable delay 2–5 ms |
| Experimental Equipment | 6 physical servers (same model), simulating Device 1–6, respectively; each server installed with an independent operating system and experimental software |
| Device1 | Device2 | Device3 | Device4 | Device5 | Device6 | |
|---|---|---|---|---|---|---|
| 1 | 11.36 | 10.78 | 10.48 | 18.83 | 13.71 | 18.97 |
| 2 | 19.13 | 16.87 | 15.57 | 16.56 | 17.77 | 15.59 |
| 3 | 18.76 | 12.65 | 14.11 | 17.46 | 19.32 | 11.78 |
| 4 | 16.08 | 13.41 | 16.95 | 13.59 | 10.16 | 18.74 |
| 5 | 18.43 | 12.87 | 12.75 | 13.83 | 15.48 | 18.57 |
| 6 | 16.94 | 14.9 | 18.57 | 16.68 | 18.09 | 18.48 |
| 7 | 11.14 | 14.07 | 19.94 | 11.41 | 15.26 | 17.47 |
| 8 | 19.43 | 16.68 | 18.61 | 14.38 | 12.63 | 14.62 |
| 9 | 14.59 | 10.55 | 16.19 | 18.24 | 11.94 | 11.72 |
| 10 | 18.48 | 10.67 | 17.83 | 16.16 | 12.19 | 13.13 |
| 11 | 18.66 | 17.81 | 15.76 | 11.71 | 15.64 | 19.44 |
| 12 | 14.04 | 11.77 | 18.64 | 19.35 | 19.85 | 19.7 |
| 13 | 19.96 | 15.03 | 16.85 | 12.96 | 11.71 | 12.08 |
| 14 | 10.82 | 10.58 | 14.33 | 17.33 | 11.11 | 18.29 |
| 15 | 11.43 | 10.5 | 16.15 | 14.34 | 15.75 | 19.78 |
| 16 | 17 | 14.69 | 13.99 | 13.24 | 11.27 | 18.61 |
| 17 | 13.78 | 19.23 | 14.83 | 19.24 | 14.48 | 16.08 |
| 18 | 12.9 | 16.35 | 14.94 | 13.8 | 13.11 | 12.88 |
| 19 | 14.75 | 17.43 | 12.61 | 10.27 | 13.32 | 15.37 |
| 20 | 25.63 | 14.02 | 29.68 | 17.02 | 11.86 | 29.19 |
| 21 | 10.49 | 29.7 | 28.5 | 29.39 | 14.84 | 15.87 |
| 22 | 18.48 | 23.46 | 27.73 | 13.24 | 20.67 | 11.01 |
| 23 | 24.24 | 16 | 29.3 | 18.78 | 13.69 | 10.58 |
| 24 | 14.98 | 21.29 | 28.26 | 14.4 | 20.83 | 22.02 |
| 25 | 15.37 | 11.84 | 26 | 24.83 | 18.17 | 22.95 |
| 26 | 23.59 | 19.38 | 17.82 | 12.19 | 10.19 | 19.33 |
| Device1 | Device2 | Device3 | Device4 | Device5 | Device6 | |
|---|---|---|---|---|---|---|
| 1 | 69.26% | 57.17% | 28.86% | 43.86% | 33.36% | 54.74% |
| 2 | 69.64% | 57.51% | 29.52% | 44.57% | 33.61% | 55.26% |
| 3 | 70.16% | 58.27% | 30.11% | 44.97% | 34.16% | 55.89% |
| 4 | 70.27% | 58.76% | 30.83% | 45.32% | 34.78% | 56.32% |
| 5 | 71.38% | 59.16% | 31.09% | 46.11% | 35.05% | 56.76% |
| 6 | 72.17% | 59.55% | 31.42% | 46.62% | 35.71% | 56.90% |
| 7 | 72.76% | 59.73% | 32.05% | 47.29% | 36.29% | 57.35% |
| 8 | 73.12% | 60.04% | 32.49% | 47.75% | 36.78% | 57.75% |
| 9 | 73.90% | 60.55% | 33.09% | 48.36% | 37.18% | 58.17% |
| 10 | 74.39% | 61.16% | 33.53% | 49.03% | 37.57% | 58.69% |
| 11 | 74.85% | 61.57% | 34.08% | 49.72% | 38.30% | 59.10% |
| 12 | 75.29% | 62.03% | 34.50% | 50.04% | 38.77% | 59.48% |
| 13 | 75.77% | 62.66% | 35.04% | 50.68% | 39.40% | 59.91% |
| 14 | 76.11% | 63.35% | 35.55% | 51.26% | 40.09% | 60.31% |
| 15 | 76.55% | 63.95% | 36.32% | 51.63% | 40.85% | 60.82% |
| 16 | 77.15% | 64.75% | 36.81% | 51.88% | 41.11% | 61.45% |
| 17 | 77.65% | 65.08% | 37.19% | 52.56% | 41.33% | 61.94% |
| 18 | 77.99% | 65.72% | 37.79% | 52.89% | 41.78% | 62.70% |
| 19 | 78.48% | 66.26% | 38.46% | 53.30% | 42.36% | 63.48% |
| 20 | 78.71% | 66.81% | 38.89% | 53.67% | 42.64% | 63.99% |
| 21 | 79.20% | 67.39% | 39.33% | 54.23% | 42.97% | 64.18% |
| 22 | 79.78% | 67.84% | 39.97% | 54.94% | 43.50% | 64.80% |
| 23 | 80.26% | 68.57% | 40.35% | 55.57% | 44.11% | 65.31% |
| 24 | 80.96% | 68.70% | 40.88% | 55.97% | 44.61% | 65.54% |
| 25 | 81.30% | 69.25% | 41.42% | 56.78% | 45.26% | 66.07% |
| 26 | 81.52% | 69.80% | 42.04% | 57.24% | 45.66% | 66.07% |
| Device1 | Device2 | Device3 | Device4 | Device5 | Device6 | |
|---|---|---|---|---|---|---|
| 1 | Normal | Normal | Normal | Normal | Normal | Normal |
| 2 | Normal | Normal | Normal | Normal | Normal | Normal |
| 3 | Normal | Normal | Normal | Normal | Normal | Normal |
| 4 | Normal | Normal | Normal | Normal | Normal | Normal |
| 5 | Normal | Normal | Normal | Normal | Normal | Normal |
| 6 | Normal | Normal | Normal | Normal | Normal | Normal |
| 7 | Normal | Normal | Normal | Normal | Normal | Normal |
| 8 | Normal | Normal | Normal | Normal | Normal | Normal |
| 9 | Normal | Normal | Normal | Normal | Normal | Normal |
| 10 | Normal | Normal | Normal | Normal | Normal | Normal |
| 11 | Normal | Normal | Normal | Normal | Normal | Normal |
| 12 | Normal | Normal | Normal | Normal | Normal | Normal |
| 13 | Normal | Normal | Normal | Normal | Normal | Normal |
| 14 | Normal | Normal | Normal | Normal | Normal | Normal |
| 15 | Normal | Normal | Normal | Normal | Normal | Normal |
| 16 | Normal | Normal | Normal | Normal | Normal | Normal |
| 17 | Normal | Normal | Normal | Normal | Normal | Normal |
| 18 | Normal | Normal | Normal | Normal | Normal | Normal |
| 19 | Normal | Normal | Normal | Normal | Normal | Normal |
| 20 | Normal | Normal | Normal | Network Jitter | Response Denied | Normal |
| 21 | Normal | Normal | Normal | Network Jitter | Response Denied | Normal |
| 22 | Normal | Normal | Normal | Network Jitter | Response Denied | Normal |
| 23 | Normal | Normal | Normal | Network Jitter | Response Denied | Normal |
| 24 | Normal | Normal | Normal | Network Jitter | Response Denied | Normal |
| 25 | Normal | Normal | Normal | Network Jitter | Response Denied | Normal |
| 26 | Normal | Normal | Normal | Network Jitter | Response Denied | Malicious Attack |
| T | Device1 | Device2 | Device3 | Device4 | Device5 | Device6 | ||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| C | R | C | R | C | R | C | R | C | R | C | R | |
| 1 | 0.5471 | 50 | 0.5503 | 100 | 0.5519 | 200 | 0.5079 | 250 | 0.5344 | 300 | 0.5072 | 350 |
| 2 | 0.5538 | 50 | 0.5697 | 100 | 0.5788 | 200 | 0.5276 | 250 | 0.5484 | 300 | 0.5320 | 350 |
| 3 | 0.5625 | 50 | 0.6158 | 100 | 0.6158 | 200 | 0.5431 | 250 | 0.5540 | 300 | 0.5795 | 350 |
| 4 | 0.5869 | 50 | 0.6587 | 100 | 0.6366 | 200 | 0.5810 | 250 | 0.6132 | 300 | 0.5058 | 350 |
| 5 | 0.5981 | 50 | 0.7091 | 100 | 0.6862 | 200 | 0.6198 | 250 | 0.6433 | 300 | 0.5059 | 350 |
| 6 | 0.6185 | 50 | 0.7478 | 100 | 0.6978 | 200 | 0.6425 | 250 | 0.6575 | 300 | 0.6099 | 350 |
| 7 | 0.6776 | 50 | 0.7951 | 100 | 0.6999 | 200 | 0.7018 | 250 | 0.6811 | 300 | 0.6273 | 350 |
| 8 | 0.6831 | 50 | 0.8235 | 100 | 0.7113 | 200 | 0.7440 | 250 | 0.7457 | 300 | 0.6638 | 350 |
| 9 | 0.7228 | 50 | 0.9067 | 100 | 0.7405 | 200 | 0.7587 | 250 | 0.8099 | 300 | 0.7227 | 350 |
| 10 | 0.7354 | 50 | 0.9967 | 100 | 0.7583 | 200 | 0.7900 | 250 | 0.8771 | 300 | 0.7757 | 350 |
| 11 | 0.7470 | 50 | 1 | 100 | 0.7928 | 200 | 0.8597 | 250 | 0.9176 | 300 | 0.7816 | 350 |
| 12 | 0.7944 | 50 | 1 | 100 | 0.8025 | 200 | 0.8668 | 250 | 0.9204 | 300 | 0.7855 | 350 |
| 13 | 0.7963 | 50 | 1 | 100 | 0.8325 | 200 | 0.9314 | 250 | 1 | 300 | 0.8518 | 350 |
| 14 | 0.8744 | 50 | 1 | 100 | 0.8825 | 200 | 0.9580 | 250 | 1 | 300 | 0.8680 | 350 |
| 15 | 0.9541 | 50 | 1 | 100 | 0.9187 | 200 | 1 | 250 | 1 | 300 | 0.8714 | 350 |
| 16 | 0.9845 | 50 | 1 | 100 | 0.9768 | 200 | 1 | 250 | 1 | 300 | 0.8850 | 350 |
| 17 | 1 | 50 | 1 | 100 | 1 | 200 | 1 | 250 | 1 | 300 | 0.9217 | 350 |
| 18 | 1 | 50 | 1 | 100 | 1 | 200 | 1 | 250 | 1 | 300 | 0.9911 | 350 |
| 19 | 1 | 50 | 1 | 100 | 1 | 200 | 1 | 250 | 1 | 300 | 1 | 350 |
| 20 | 0.9466 | 50 | 1 | 100 | 0.9091 | 200 | 0.8153 | 250 | 0.6698 | 300 | 0.9135 | 350 |
| 21 | 1 | 50 | 0.9089 | 100 | 0.8364 | 200 | 0.5437 | 250 | 0.2979 | 300 | 0.9533 | 350 |
| 22 | 1 | 50 | 0.8794 | 100 | 0.7756 | 200 | 0.3837 | 250 | 0 | 300 | 1 | 350 |
| 23 | 0.1598 | 50 | 0.9168 | 100 | 0.7083 | 200 | 0.1906 | 250 | 0 | 300 | 1 | 350 |
| 24 | 0 | 50 | 0.9064 | 100 | 0.6538 | 200 | 0.0045 | 250 | 0 | 300 | 0.9813 | 350 |
| 25 | 0 | 50 | 0.9849 | 100 | 0.6175 | 200 | 0 | 250 | 0 | 300 | 0.9542 | 350 |
| 26 | 0 | 50 | 0.9924 | 100 | 0.6328 | 200 | 0 | 250 | 0 | 300 | 0 | 350 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liao, X.; Yang, S.; Xu, J.; Liu, L.; Liang, W.; Yu, S.; Ji, Y.; Liu, S. Improved Trust Evaluation Model Based on PBFT and Zero Trust Integrated Power Network Security Defense Method. Symmetry 2025, 17, 1982. https://doi.org/10.3390/sym17111982
Liao X, Yang S, Xu J, Liu L, Liang W, Yu S, Ji Y, Liu S. Improved Trust Evaluation Model Based on PBFT and Zero Trust Integrated Power Network Security Defense Method. Symmetry. 2025; 17(11):1982. https://doi.org/10.3390/sym17111982
Chicago/Turabian StyleLiao, Xiaoyun, Sen Yang, Jun Xu, Li Liu, Wei Liang, Shengjie Yu, Yimu Ji, and Shangdong Liu. 2025. "Improved Trust Evaluation Model Based on PBFT and Zero Trust Integrated Power Network Security Defense Method" Symmetry 17, no. 11: 1982. https://doi.org/10.3390/sym17111982
APA StyleLiao, X., Yang, S., Xu, J., Liu, L., Liang, W., Yu, S., Ji, Y., & Liu, S. (2025). Improved Trust Evaluation Model Based on PBFT and Zero Trust Integrated Power Network Security Defense Method. Symmetry, 17(11), 1982. https://doi.org/10.3390/sym17111982







